Chief Information Security Officer
advertisement

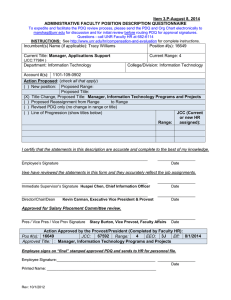
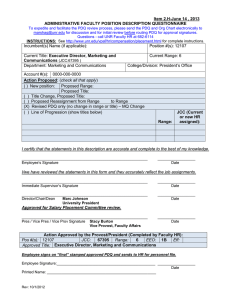
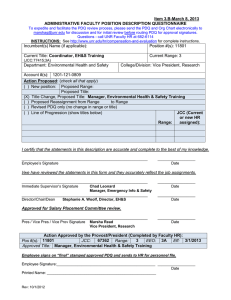
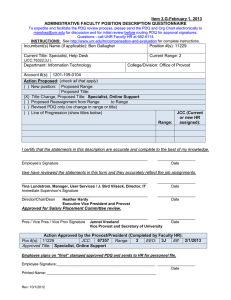
Item 3.Q-August 8, 2014 ADMINISTRATIVE FACULTY POSITION DESCRIPTION QUESTIONNAIRE To expedite and facilitate the PDQ review process, please send the PDQ and Org Chart electronically to marshag@unr.edu for discussion and for initial review before routing PDQ for approval signatures. Questions - call UNR Faculty HR at 682-6114 INSTRUCTIONS: See http://www.unr.edu/hr/compensation-and-evaluation for complete instructions. Incumbent(s) Name (if applicable): Jeff Springer Position #(s): 11107 Current Title: Information Security Officer (JCC: 67469) Department: Information Technology Current Range: 5 College/Division: Provost Account #(s): 1101-109-0902 Action Proposed: (check all that apply) ( ) New position: Proposed Range: Proposed Title: (X) Title Change, Proposed Title: Chief Information Security Officer ( ) Proposed Reassignment from ( ) Revised PDQ only (no change in range or title) ( ) Line of Progression (show titles below) Range: JCC (Current or new HR assigned): I certify that the statements in this description are accurate and complete to the best of my knowledge. ____________________________________________________________ Jeff Springer __________________ Date I/we have reviewed the statements in this form and they accurately reflect the job assignments. ____________________________________________________________ Immediate Supervisor’s Signature Huapei Chen, Chief Information Officer __________________ Date ____________________________________________________________ Director/Chair/Dean Kevin Carman, Executive Vice President & Provost __________________ Date Approved for Salary Placement Committee review. ____________________________________________________________ __________________ Pres / Vice Pres / Vice Prov Signature Stacy Burton, Vice Provost, Faculty Affairs Date Action Approved by the Provost/President (Completed by Faculty HR): 67593 Range: 5 Pos #(s): 11107 JCC: EEO: 3J Eff: 8/1/2014 Approved Title: Chief Information Security Officer Employee signs on “final” stamped approved PDQ and sends to HR for personnel file. Employee Signature:_______________________________________________ __________________ Date Printed Name: ____________________________________________________ Rev: 10/1/2012 Position Description – Chief Information Security Officer Page 2 1. Summary Statement: State the major function(s) of the position and its role in the university. Attach an organizational chart with positions, ranges, and names for the division which reflects the position in it as well as those supervised in the department. (This section is used for advertisement of the position.) The Chief Information Security Officer (CISO) directs staff in identifying, developing, implementing and maintaining processes across the University of Nevada, Reno to reduce information and information technology (IT) risks, respond to incidents, establish appropriate standards and controls, and consults, advises and directs the establishment and implementation of policies and procedures at all levels within the organization up to and including the President. The position is responsible for campus-wide information-related compliance as it relates to federal, state, and local regulatory requirements. In addition to the information security related duties, the individual is in charge of all centralized identity management processes and systems. The CISO supervises and manages administrative IT security faculty. The position reports to the Chief Information Officer (CIO) in Information Technology. 2. List the major responsibilities, including percentage of time devoted to each. Provide enough detail to enable a person outside the department to understand the job (percentage first with heading and then bulleted information). 30% - Security Management Work with both administrative and academic units to improve the overall information security posture of the University, to develop new and innovative systems to address emerging threats, and to increase awareness of the importance of cyber security Respond in a timely manner to all levels of information security related incidents and requests, which may include both internally and externally identified threats and compromises along with requests for information from General Counsel or law enforcement agencies Supervise and evaluate direct report IT security administrative faculty Work closely with University General Counsel on all IT related discovery requests to protect the privacy of faculty and students while ensuring the institution meets its legal obligations 25% - Identity Management Manage the centralized Active Directory systems and the processes that synchronize accounts with upstream systems Provide leadership to staff and administrators to ensure proper authorization and accounting of users and their access to University resources 25% - Security Policy and Process Management Work closely with the CIO, IT managers, and constituents to create appropriate and applicable policies and procedures that ensure the security of the IT infrastructure and data Ensure compliance with all appropriate regulations and enforce appropriate access mechanisms while also ensuring that our core business processes are not negatively impacted 20% - Vulnerability and Security Assessments Conduct regular security vulnerability assessments on University IT assets to verify compliance with campus security policies When cases of identified vulnerabilities are found, work with the impacted units to develop a remediation plan or, in the case of a critical or immediate threat, authorize the removal of network access Position Description – Chief Information Security Officer Page 3 3. Describe the level of freedom to take action and make decisions with or without supervision and how the results of the work performed impact the department, division and/or the university as a whole. Level of Freedom: The CISO works independently with little direction or supervision to identify and resolve key IT security issues. Issues are routinely handled in the best interest of the University without direction. Issues of great import or consequence are discussed with the CIO. Impact: The individual makes high level strategic decisions that impact all aspects of computing and network communications on campus. Policies and procedures implemented by the position have a broad influence on all campus activities that rely on any form of electronic communications including but not limited to email, internet browsing, payroll and file storage. Additionally, the position works closely with University General Counsel on all IT related discovery requests and must protect the privacy of faculty and students while ensuring the institution meets its legal obligations. Ineffective performance of any of the duties associated with the position can result in the University being vulnerable to malicious IT attacks to the entire campus infrastructure and incidences of identity or information theft of University information. 4. Describe the knowledge, skills (to include cognitive requirement and verbal and written communication), and abilities (to include task complexity, problem solving, creativity and innovation) essential to successful performance of this job (in bullet format). Knowledge Networking hardware and software including, but not limited to, Ethernet, switching, routing firewalls, access control lists All modern Operating Systems including Solaris, Linux, Windows 2012, 2008, 8 Internet Protocols including, but not limited to, HTTP,TCP/IP,SQL,DHCP,DNS,NTP, LDAP, Kerberos Security threats including, but not limited to, Advanced Persistent Threats (APT), Virus, Spyware, etc. IT security systems, i.e., Authentication servers, Firewalls, Intrusion Prevention systems, Antivirus servers, System Information and Event Management (SIEM) products, and wireless network security Regulatory environments including, but not limited to, Federal Information Security Management Act (FISMA), Procurement Card Industry (PCI), Family Educational Rights and Privacy Act (FERPA), and Health Insurance Portability and Accountability Act (HIPAA) Skills Excellent verbal and written communication to relay complex ideas clearly to non-technical individuals Analytical, decision-making, and problem-solving skills - research issues/situations, develop and provide solutions, make appropriate decisions, and implement solutions; bring concerns to management Complex data analysis Excellent organizational skills in order to effectively program and maintain computer systems in a complex computer environment Lightweight Directory Access Protocol (LDAP) Directory Management Excellent documentation skills, including the ability to write reports, summarize complex issues and exercise professional judgment in the communication of responses in an appropriate and sensitive manner Supervisory skills, including an ability to teach and mentor staff Position Description – Chief Information Security Officer Page 4 Ability to: Make business-critical decisions in a timely manner Provide relevant input to the policy development process Stay current in discipline and security trends by seeking out and learning new information pertinent to performance of duties Maintain confidentiality of highly sensitive information Develop and sustain effective working relationships with faculty, staff, colleagues and other members of the campus community Work with diverse populations and be sensitive to gender, disabilities, and cultural and ethnic diversity issues Contribute to and support the department, college, and university strategic plan 5. Describe the type of personal contacts encountered in performing the duties of the job. Explain the nature and purpose of these contacts: i.e., to provide services, to resolve problems, to negotiate. Internal University administrators and administrative and classified staff Higher level university administrators, directors, assistance vice presidents, and vice presidents IT Staff Reason for Contact To provide policy interpretation, answer questions, respond to needs and provide solutions to IT security problems External Campus computing professionals, internal and external auditors Vendors Reason for Contact To plan, coordinate, and report on IT security initiatives and activities To provide set direction, guidance, advice and consultation on all IT security related issues and projects To identify vulnerability points prior to a system compromise, develop solutions and implement resolutions To make decisions regarding acquisition and improvement of equipment and software; negotiate contracts with regard to security 6. Indicate the minimum qualifications which are necessary in filling this position should it become vacant. Please keep in mind the duties/responsibilities of the position rather than the qualifications of the incumbent. a. Minimum educational level, including appropriate field, if any. Bachelor’s Degree from a regionally accredited institution with emphasis or major in Computer Information Systems or a related field b. Minimum type and amount of work experience, in addition to the above required education necessary for a person entering this position. Bachelor’s Degree and six years, or Master’s Degree and four years, of relevant administration experience with large scale security-related projects and systems Position Description – Chief Information Security Officer Preferred Licenses or Certifications: Certified Information Systems Security Professional (CISSP) c. Indicate any license or certificate required for this position. None Page 5