import javax.microedition.lcdui.
advertisement

In the name of Allah, the most gracious, the most merciful
Q1. Critically evaluate the strength and weakness of web services and give at least two items
each. Critically discuss how service description works in Web Service Architecture.
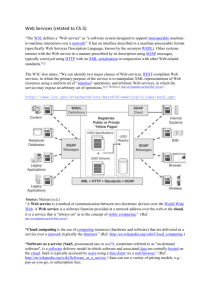
Web services are powered by XML and three other core technologies: WSDL, SOAP, and UDDI.
Before building a Web service, its developers create its definition in the form of a WSDL document
that describes the service's location on the Web and the functionality the service provides. Information
about the service may then be entered in a UDDI registry, which allows Web service consumers to
search for and locate the services. Based on information in the UDDI registry, the Web services client
developer uses instructions in the WSDL to construct SOAP messages for exchanging data with the
service over HTTP.
The standardized nature of Web service solve many problems related to intersystem communication.
For example:
The HTTP standard is allowing more systems to communicate with one another.
SOAP (built on XML) standardizes the messaging capability on different systems.
UDDI standardizes the publishing and finding of Web services.
WSDL standardizes the description of Web services so providers and requesters are
speaking the same language.
WSDL (Web Services Description Language)
WSDL is an XML-based format for describing Web services. Clients (Applications/Services) wishing
to access a Web service can read and interpret its WSDL file to learn about the location of the service
and its available operations. In this way, the WSDL definition acts as the initial Web service interface,
providing clients with all the information they need to interact with the service in a standards-based
way.
A WSDL file is an XML document that describes a Web service using six main elements:
1. Port type – groups and describes the operations performed by the service through the
defined interface.
2. Port – specifies an address for a binding, i.e., defines a communication port.
3. Message – describes the names and format of the messages supported by the service.
4. Types – defines the data types (as defined in an XML Schema) used by the service for
sending messages between the client and server.
5. Binding – defines the communication protocols supported by the operations provided by the
service.
6. Service – specifies the address (URL) for accessing the service.
The WSDL document that describes a Web service acts as a contract between Web service client
and server.
Source : http://www.altova.com/whitepapers/webservices.pdf
Strengths : Consuming, Interoperability, Choice of Platform, Usability, Deployment
1. Consuming - Web services presents an opportunity to take advantage of services offered by
other platforms and infrastructures and the opportunity to make your applications available to
others as a Web service.
2. Interoperability - This is the most important benefit of Web Services. Web Services typically
work outside of private networks, offering developers a non-proprietary route to their
solutions. Services developed are likely, therefore, to have a longer life-span, offering better
return on investment of the developed service.
3. Choice of Platform - Web Services also let developers use their preferred programming
languages. In addition, due to the use of standards-based communications methods, Web
Services are virtually platform-independent.
4. Usability - Web Services allow the business logic of many different systems to be exposed
over the Web. This gives your applications the freedom to chose the Web Services that they
need. Instead of re-inventing the wheel for each client, you need only include additional
application-specific business logic on the client-side.
5. Deployment - Web Services are deployed over standard Internet technologies. This makes it
possible to deploy Web Services even over the fire wall to servers running on the Internet on
the other side of the globe. Also thanks to the use of proven community standards, underlying
security (such as SSL) is already built-in.
Weakness
1. Complexity - XML and its extensions have regularly been criticized for verbosity and
complexity. JSON is a good alternative.
2. Heavy Data - Web services use plain text protocols that use a fairly extensive method to
identify data. This means that Web service requests are larger than requests encoded with a
binary protocol. The extra size is really only an issue over low-speed connections, or over
extremely busy connections.
3. Not suitable for long term sessions - Although HTTP and HTTPS (the core Web protocols) are
simple, they weren't really meant for long-term sessions. Typically, a browser makes an
HTTP connection, requests a Web page and maybe some images, and then disconnects.
4. Stateless Protocols - The problem with HTTP and HTTPS when it comes to Web services is
that these protocols are "stateless"—the interaction between the server and client is typically
brief and when there is no data being exchanged, the server and client have no knowledge of
each other. More specifically, if a client makes a request to the server, receives some
information, and then immediately crashes due to a power outage, the server never knows
that the client is no longer active.
5. Timeout overheads - A server usually rely on a timeout mechanism to determine that a client
is no longer active. If a server doesn't receive a request from a client after a predetermined
amount of time, it assumes that the client is inactive and removes any client information it was
keeping. This extra overhead means more work for Web service developers. Source:
http://www.altova.com/whitepapers/webservices.pdf
Q2. Critically evaluate different kinds of parsers used in the XML ? And critically discuss the
difference between them.
An XML Parser is a parser that is designed to read XML and create a way for programs to use XML.
There are different types, and each has its advantages. Unless a program simply and blindly copies
the whole XML file as a unit, every program must implement or call on an XML parser.
The main types of parsers : SAX, DOM and pull.
SAX stands for (Simple API for XML) is an event sequential access parser API for XML documents.
SAX provides a mechanism for reading data from an XML document that is an alternative to that
provided by the Document Object Model (DOM). Where the DOM operates on the document as a
whole, SAX parsers operate on each piece of the XML document sequentially.
Its main characteristic is that as it reads each unit of XML, it creates an event that the calling
program can use. This allows the calling program to ignore the bits it doesn't care about, and just
keep or use what it likes.
The disadvantage is that the calling program must keep track of everything it might ever need. SAX is
often used in certain high-performance applications or areas where the size of the XML might exceed
the memory available to the running program.
Unlike DOM, there is no formal specification for SAX. The Java implementation of SAX is considered
to be normative (standard).
SAX processes documents state-independently, in contrast to DOM which is used for statedependent processing of XML documents.
DOM stands for Document Object Model.
The Document Object Model (DOM) is a cross-platform and language-independent convention for
representing and interacting with objects in HTML, XHTML and XML documents. Objects in the DOM
tree may be addressed and manipulated by using methods on the objects.
DOM differs from SAX in that it builds the entire XML document representation in memory and
then hands the calling program the whole chunk of memory. DOM can be very memory intensive.
The XML DOM contains methods to traverse XML trees, access, insert, and delete nodes.
Pull Parser : A Pull parser returns XML events to a client on request.
SAX is a push parser, since it pushes events out to the calling application. Pull parsers, on the other
hand, sit and wait for the application to come calling. They ask for the next available event, and
the application basically loops until it runs out of XML.
Q3. Web services offer a number of security challenges. Critically evaluate 3 of these.
Web Services - Security Concerns
Web Services operate on the same structure used by normal web applications. The beginning is a
request forwarded by an application viewed in a web browser, which for Web Services is a SOAP
request over HTTP. Since SOAP data is received by the server, initially, one can understand that the
threat is primarily aimed at the server itself. The following are methods of attack, and how Web
Services can be exploited to these attacks:
1. Buffer Overflow 2. XML Injections 3. Session Hijacking 4.Insecure Communication
5. Information Leakage
1. Buffer Overflows:
Common Effects: DOS (Denial of Service), Data corruption, Malicious code execution.
An attacker can craft XML data causing the XML to call upon itself repetitively therefore constantly
increasing in size. This causes a memory overflow, or trigger error messages which reveal information
about the application.
A DoS attack can be caused by forcing a server to parse an abnormally long XML file, which in
essence uses up much more resources then actually generating one, and can crash the application.
Another type of attack consists of sending a block of data to an application, which is stored in a buffer
of insufficient size. This block of data can then overwrite genuine data and cause a function return
which gives control to the malicious code in the hacker’s data block.
2. XML Injections:
Common Effects: Command execution, data theft and deletion, schema poisoning.
SQL Injection is a high-risk exploit which may be performed using SOAP messages. If a server does
not validate data correctly, a SOAP message can easily be used to create XML data which inserts a
parameter into an SQL query and have the server execute it with the rights of the Web Service. SQL
Injection is only one of the threats a server is exposed to if data is not validated.
Another such example is Schema Poisoning. A schema file is what an XML parser uses to
understand the XML’s grammar and structure, and contains essential pre-processor instructions. An
attacker may damage the XML schema or replace it with a modified one which would then allow the
XML parser to process malicious SOAP messages and specially crafted XML files to inject OS
commands on the server or database.
3. Session Hijacking:
Common Effects: Obtaining of user privileges within application or network
Session hijacking involves gaining illegal control of a legal user’s session state. It occurs when an
attacker steals a valid session ID (valid session cookie), and uses it to gain that particular user’s
privileges in the application. By intercepting or sniffing SOAP messages, an attacker can hijack a
user’s session in the same ways as with normal web application attacks, however once a hacker is
authenticated as a valid user he may perform more dangerous activities.
4. Insecure Communications:
Common Effects : Attackers can steal or modify information if not protected
while in transit.
Mitigations : Use the latest versions of SSL or TLS, to protect the content of messages in
point-to-point transactions. Requiring mutual authentication between the client and server raises
the level of trust before processing messages and generally decreases the attack surface of
the service.
5. Information Leakage - Web Services that generate verbose fault messages are useful to
developers and system administrators.
However, the same messages can give away too much information in operational
environments.
This issue also affects Web Services that use a WSDL to provide a description of a service
and its interface. A WSDL contains server directory information, internal IP address
information, available services and methods, and other critical information valuable to an
attacker.
Source: http://www.nsa.gov/ia/_files/factsheets/SOA_security_vulnerabilities_web.pdf
Q4. Critically evaluate the different components required by cloud architecture.
Cloud computing architecture refers to the components and subcomponents required for cloud
computing. These components typically consist of
1- Front end platform (Client - fat client, thin client, mobile device),
2- Back end platforms (servers, storage), a cloud based delivery, and a network (Internet,
Intranet, Intercloud).
Backend comprises of huge data storage, virtual machines, security mechanism, services,
deployment models, servers, etc.
Combined, these components make up cloud computing architecture.
High Level Components
SaaS (Software as a Service), PaaS (Platform as a Service), IaaS (Infrastructure as a Service)
DBaaS (Database as a Service) - is a type of SaaS
11 major categories or patterns of cloud computing technology:
1. Storage-as-a-service
2. Database-as-a-service
3. Information-as-a-service
4. Process-as-a-service
5. Application-as-a-service
6. Platform-as-a-service
7. Integration-as-a-service
8. Security-as-a-service
9. Management/governance-as-a-service
10. Testing-as-a-service
11. Infrastructure-as-a-service
Source : http://www.informit.com/articles/article.aspx?p=1398772&seqNum=6
Low Level Components
Here are some of the typical components you’ll find in many private clouds.
Load Balancing
Increase application or site availability and performance by distributing traffic across local or globally
diverse resources.
Content Delivery Network
Put content on many nodes throughout the cloud, keeping it closer to end users geographical location
to minimize the distance the data has to travel. E.g Amazon EU, ASIA Servers for customers in these
regions.
Application Servers
Power applications with robust physical dedicated servers for fast response times.
Hardware Firewall
Protect servers from malicious activity with high-grade firewalls provisioned on demand.
Web Servers
Scale virtual cloud servers on-demand to meet site load requirements during traffic spikes.
Engineers
Dedicated qualified engineering staff.
Source: http://www.softlayer.com/private-clouds
Public Cloud Components
Management
OS
Q5. A. Critically discuss SSL VPN in the cloud computing, and show how this will be needed to
secure remote access solution with a standard web browser.
A SSL VPN (Secure Sockets Layer - Virtual private network) is a form of VPN that can be used
with a standard Web browser to access the server (cloud).
It provides a Remote, Authenticated Access to Applications and Data behind the cloud.
Today's busy remote workers require a quick, flexible, reliable, and completely secure way to connect
to internal business applications, information, and network resources. They want to do this from
anywhere in the world, at any time, from any suitable device. The SSL VPN provides the security and
connectivity to deliver this access, via a web browser or mobile device (iPad, Tablets etc).
The SSL VPN is an integrated hardware and software solution that enables secure, clientless,
remote access to internal network resources. Accessible from any web browser on any operating
system, the SSL VPN provides all the features needed to enable network resource access through a
powerful policy-based permissions framework. The SSL VPN also integrates with third-party
authentication mechanisms to provide granular access control with single sign-on capabilities.
Unlike traditional IPsec-based VPNs that require client software installed on remote machines, the
SSL VPN provides secure remote access to network resources from any web browser. This
removes the overhead of installing and maintaining clients and permits secure access from any
operating system that can support a standard web browser.
SSL technology also eliminates some of the deployment issues around IPsec VPN technology like
IP-address conflicts, NAT traversal, and DNS problems.
Policy-Based Resource Management
The SSL VPN integrates a powerful policy engine that enables administrators to selectively authorize
traffic to approved resources. The device integrates with Active Directory, LDAP, or other user
databases permitting administrators to define granular policies allowing specific users and groups to
access network resources without any changes to the resource itself.
Network Access Control
Remote users can access network resources from a variety of endpoints or client machines including
shared computers. The SSL VPN provides extensive network access control methods that will
ensure a computer requesting remote access adheres to established security policies based on the
operating system, web browser version, and other connection parameters before permitting network
access.
Secure Client Access
All files uploaded during a SSL VPN session to the network file system or from a proxied Internet web
application are automatically scanned for viruses, spyware, and other forms of malware.
The SSL VPN also includes a cache cleaning utility that clears traces of a secure session from the
web browser cache, history, and a virtual keyboard to protect users against keyloggers. This is
especially useful when users access the SSL VPN from shared computers.
Source :
https://www.barracuda.com/assets/docs/White_Papers/Barracuda_SSLVPN_WP_Advantage.pdf
A SSL VPN consists of one or more VPN devices to which the user connects by using his Web
browser. The traffic between the Web browser and the SSL VPN device is encrypted with the SSL
protocol or its successor, the Transport Layer Security (TLS) protocol.
There are two major types of SSL VPNs:
1. SSL Portal VPN: This type of SSL VPN allows for a single SSL connection to a Web site so the
end user can securely access multiple network services.
2. SSL Tunnel VPN: This type of SSL VPN allows a Web browser to securely access multiple
network services, including applications and protocols that are not Web-based, through a tunnel that
is running under SSL.
Also ...
Cloud VPN services fit best in enterprises "where you have a remote user population that will fluctuate
between regions of the world, especially where their access network is not unified.
Q.5.B. Critically evaluate the REST and how it is used in data communications technology and
international standardisation to specify the protocols and services for each of the following
clouds: (THINK, twitter, flickr, salesforce.com, amazon and youtube)
REST (REpresentational State Transfer) is a simple stateless architecture that generally runs over
HTTP.
REST is simpler to use than the well-known SOAP (Simple Object Access Protocol) approach,
which requires writing or using a provided server program (to serve data) and a client program
(to request data).
REST is often used in mobile applications, social networking Web sites, mashup tools and automated
business processes.
Main implementation is JSON.
REST defines a set of architectural principles by which you can design Web services that focus on a
system's resources, including how resource states are addressed and transferred over HTTP by a
wide range of clients written in different languages. twitter, flickr, salesforce.com, amazon and
youtube all expose their API in REST form.
REST asks developers to use HTTP methods explicitly and in a way that's consistent with the protocol
definition. This basic REST design principle establishes a one-to-one mapping between create, read,
update, and delete (CRUD) operations and HTTP methods. According to this mapping:
To retrieve a resource, use GET.
To create a resource on the server, use POST.
To change the state of a resource or to update it, use PUT.
To remove or delete a resource, use DELETE.
(Think JSON functionality)
Exposing a system's resources through a RESTful API is a flexible way to provide different kinds of
applications with data formatted in a standard way. It helps to meet integration requirements that are
critical to building systems where data can be easily combined (mashups) and to extend or build on a
set of base.
ref : http://www.ibm.com/developerworks/webservices/library/ws-restful/
Cloudant offers DataBase as a Service DBaaS - cloudant uses JSON as storage for data. Documents
are accessed via HTTP using a RESTful web services API.
Q6. How does cloud computing contribute towards achieving universal availability of
information ? Perform a brief case study on the deployment of cloud computing using Google
as an example. Explore the main performance and security concerns that users may have
while using these services.
Cloud computing provide users with a number of different benefits.
Many businesses large and small use cloud computing today either directly (e.g. Google or Amazon)
or indirectly (e.g. Twitter) instead of traditional on-site alternatives. There are a number of reasons
why cloud computing is so widely used among businesses today.
Universal Access
CLOUD services COULD BE ACCESSED FROM ANYWHERE IN THE WORLD. CLOUD SERVICE
PROVIDER MAKE THEIR SERVICES AVAILABLE FOR CONSUMERS TO CONSUME IT.
Google cloud services :
Computing : It offers Google App Engine, And Google Compute Engine.
Storage : It offers Google Cloud Database , BigData implementation as BigQuery , Google Drive for
Sharing Data on all mobile devices from anywhere.
Google also offers its Cloud services as Google Docs, Gmail, Calendar , Translate Services as API which are for enterprise and normal consumers.
Benefits of Cloud Computing
- Reduction of costs – unlike on-site hosting the price of deploying applications in the cloud can be
less due to lower hardware costs from more effective use of physical resources.
- Universal access - cloud computing can allow remotely located employees to access applications
and work via the internet.
- Up to date software - a cloud provider will also be able to upgrade software keeping in mind
feedback from previous software releases.
- Choice of applications. This allows flexibility for cloud users to experiment and choose the best
option for their needs. Cloud computing also allows a business to use, access and pay only for what
they use, with a fast implementation time
- Choice of Payments Models
Users can pay for only the usage, per hour or monthly subscriptions. So this is a huge benefits for
those who need a pay as you go model.
- Easy to Start - New starters love cloud model. Just plug and play model
- Potential to be greener and more economical - the average amount of energy needed for a
computational action carried out in the cloud is far less than the average amount for an on-site
deployment. This is because different organisations can share the same physical resources securely,
leading to more efficient use of the shared resources.
- Flexibility – Cloud computing allows users to switch applications easily and rapidly, using the one
that suits their needs best. However, migrating data between applications can be an issue.
Example of Clouds
- Google App Engine (IaaS) is a service offered by Google to develop and deploy apps on the
Google cloud. It offers a platform to create and run an App without having to work on the underlying
infrastructure.
- Khan Academy (SaaS) is an initiative which offers free online interactive tuition services around the
world. Millions use it for educational purposes which are unable to pay high tuition in main stream
educational institutes. The site uses cloud based services to scale itself to cater the needs of millions.
This is new landmark in education made possible with cloud based services.
- iTunes (SaaS)
Security Concerns for Cloud
1.
2.
3.
4.
5.
6.
Network Availability
Privacy Concern
Loss of Data
Cloud vendor locking
Unauthorised access
Legal issues
Q7. WSDL supports four operations, critically evaluate the four operation types.
WSDL builds on XML Schema by making it possible to describe Web services in terms of messages,
operations, interfaces (portTypes), bindings, and service endpoints. Simply put, the WSDL file is the
key communicative agent between the various entities exchanging service messages, and
instructions between them.
A WSDL document describes a web service using these major elements:
Element
Description
<types>
A container for data type definitions used by the web service
<message>
A typed definition of the data being communicated
<portType>
A set of operations supported by one or more endpoints
<binding>
A protocol and data format specification for a particular port type
Operation Types
The request-response type is the most common operation type, but WSDL defines four types:
Type
Definition
One-way
The operation can receive a message but will not return a response
Request-response
The operation can receive a request and will return a response
Solicit-response
The operation can send a request and will wait for a response
Notification
The operation can send a message but will not wait for a response
Request-Response Operation Example
A request-response operation example:
<message name="getTermRequest">
<part name="term" type="xs:string"/>
</message>
<message name="getTermResponse">
<part name="value" type="xs:string"/>
</message>
<portType name="glossaryTerms">
<operation name="getTerm">
<input message="getTermRequest"/>
<outp.ut message="getTermResponse"/>
</operation>
</portType>
In the example above, the portType "glossaryTerms" defines a request-response operation called
"getTerm".
The "getTerm" operation requires an input message called "getTermRequest" with a parameter called
"term", and will return an output message called "getTermResponse" with a parameter called "value".
Q8. A. Critically evaluate the impact of cloud computing in future perspective in term of next
stage of internet world AND also analyze its characteristics and the main feature of cloud
services?
Talk about the Cloud and Internet in context with future and emerging trends in :
Genome sequencing, DNA Analysis and Genetics
Social Behaviour Analysis
Medicine Research - BioMedical and Biomedical engineering (Stem Cell Research)
Academics and Education
Neural Networks and AI
Space exploration
Epidemic predictions
Meteorology , Cosmology, Geology
Cloud Delivery Models are :
Private, Public, Hybrid, Community
Cloud implementations are :
SaaS example : Dropbox , Office365 , iTunes, Google and Bing Translate
PaaS example : Google App Engine, Google Docs, Gmail, Storage etc
IaaS example: Amazon EC2 , Google BigQuery, Microsoft Azure
CaaS : Unified Communications hosted over the cloud , Have the service provider or system
integrator deliver unified communications services over the cloud. e.g. Cisco
Google - Mobile, Local, Social
IBM - Cloud, Mobile, Data
Q.8.B. Critically discuss why the Communication as a service (CaaS) is not considered as a
standard leasing?
Communications as a Service (CaaS) is an outsourced enterprise communications solution
that can be leased from a single vendor. Such communications can include Voice over IP (VoIP or
Internet telephony), Instant Messaging (IM), Collaboration and Videoconference Applications
using fixed and mobile devices. CaaS has evolved along the same lines as Software as a
Service (SaaS).
Example are Microsoft Lync, Cisco Unified Communications etc
The CaaS vendor is responsible for all hardware and software management and offers guaranteed
Quality of Service (QoS). CaaS allows businesses to selectively deploy communications devices and
modes on a pay-as-you-go, as-needed basis. This approach eliminates the large capital
investment and ongoing overhead for a system whose capacity may often exceed or fall short of
current demand.
CaaS has found its implementation in video conferencing, IP communications, Mobile
Applications, Customer Care, Telepresence, Interactive Whiteboards, Speech Recognition, IP
Telephony, Web Collaboration, Unified Messaging, Mobile Collaboration, B2B Collaboration,
Customer care with Self Service , Intelligent Routing, Enterprise Social Software and interactive
Communications.
Second Definition
Cloud communications refers to enterprises’ increasingly popular move to internet-based or cloudbased voice and data communications services, where telecommunications applications, switching,
and storage are managed generally by third parties.
These services can include capabilities that range from Voice over IP (VoIP) communications to
hosted PBX and unified communications delivering voice, fax, video, and data requirements.
Provisioning for these services is known as Communication as a Service (CaaS).
Drawbacks
However CaaS has concerns due to privacy and data protection.
One potential drawback to the CAAS model is that the service provider determines the capabilities,
so you may not have all the features available to you that you would if you owned and managed the
system yourself. However, if you work with a systems integrator, you can have input into functions.
Despite Budget Constraints, Unified Communications Implementation Is Proceeding
Limited resources, demands for greater efficiency and responsiveness, the need to differentiate in a
highly competitive market, less travel but more customer interaction, the need to move faster and with
more accuracy to become an on-demand business - these are the complexities of today’s business
environment and the reasons why unified communications and collaboration are more relevant than
ever.
Growing Interest in Communication Services
Business complexity is also causing companies to consider new deployment models for anything that
is not a core area of expertise. This is why a growing number of companies are evaluating managed
services. When compared to company-owned-and-operated collaboration, managed services allow
companies to focus less on IT and more on core competencies.
Q9. Critically evaluate SOAP and discuss its role in the provision of web services.
The Web service uses Simple Object Access Protocol (SOAP) messaging to send text-based
commands over a network. These commands take the form of XML text that is sent over the World
Wide Web using HTTP. By using SOAP as its communication protocol, the Web service allows
applications and components to exchange data with each other using an open and widely accepted
infrastructure.
SOAP messages are XML documents that contain some or all of the following elements:
Envelope – specifies that the XML document is a SOAP message; encloses the message
itself.
Header (optional) – contains information relevant to the message, e.g., the date the message
was sent, authentication data, etc.
Body – includes the message payload.
Fault (optional) – carries information about a client or server error within a SOAP message.
Data is sent between the client(s) and the Web service using request and response SOAP messages,
the format for which is specified in the WSDL definition. Because the client and server adhere to the
WSDL contract when creating SOAP messages, the messages are guaranteed to be compatible.
http://www.altova.com/whitepapers/webservices.pdf
Q.10 A bookshop wants to list books and their prices. An example of content would be, A
bookshop has one or more books. A book has a title, one isbn, one or more authors,
publisher(name, address, phone), and one or more prices(new, old) . Use XML to best describe
this data. Ur XML should contain some dummy data.
<?xml version="1.0" encoding="UTF-8"?>
<bookshop>
<book isbn="bk101">
<title>Don't be Sad</title>
<author>Al Qarni</author>
<publisher>
<name>Islamic Publishing</name>
<address>123 Dubai</address>
<phone>0800123</phone>
</publisher>
<price>
<new>15</new>
<old>20</old>
</price>
</book>
<!--Comment1-->
<book isbn="bk102">
<title>The Ideal Muslimah</title>
<author>Dr Al Hashimi</author>
<publisher>
<name>Islamic Publishing</name>
<address>123 Makkah</address>
<phone>01234567</phone>
</publisher>
<price>
<new>10</new>
<old>20</old>
</price>
</book>
<!--Comment2-->
</bookshop>
Source: http://support.microsoft.com/kb/296560
Q11. Critically evaluate the possible states of a Midlet? After the midlet constructor is called
what is the state of a midlet?
MIDlet States
The MIDlet state machine is designed to ensure that the behavior of an application is consistent and
as close as possible to what device manufactures and users expect, specifically:
The perceived startup latency of an application should be very short.
It should be possible to put an application into a state where it is not active.
It should be possible to destroy an application at any time.
The valid states for MIDlets are:
State Name
Description
The MIDlet is initialized and is inactive. It should not be holding or using any
shared resources. This state is entered:
After the MIDlet has been created using new. The public no-argument
constructor for the MIDlet is called and returns without throwing an
exception. The application typically does little or no initialization in this
step. If an exception occurs, the application immediately enters the
Destroyed state and is discarded.
From the Active state after the MIDlet.pauseApp() method returns
successfully.
From the Active state when the MIDlet.notifyPaused() method returns
successfully to the MIDlet.
From the Active state if startApp throws
an MIDletStateChangeException.
Paused
The MIDlet is functioning normally. This state is entered:
Active
Just prior to calling the MIDlet.startApp() method.
The MIDlet has released all of its resources and terminated. This state is
entered:
When the MIDlet.destroyApp() method returns except in the case when
the unconditional argument is false and
aMIDletStateChangeException is thrown. The destroyApp() method shall
release all resources held and perform any necessary cleanup so it may
be garbage collected.
When the MIDlet.notifyDestroyed() method returns successfully to the
Destroyed
application. The MIDlet must have performed the equivalent of
theMIDlet.destroyApp() method before calling MIDlet.notifyDestroyed().
Note: This state is only entered once.
The state of midlet is Paused after the constructor is created.
Q11.b. Critically discuss the difference between a server and client MessageConnection?
When do you use a Server and a client MessageConnection?
javax.wireless.messaging
public interface MessageConnection extends Connection
The MessageConnection interface defines the basic functionality for sending and receiving
messages. It contains methods for sending and receiving messages, factory methods to create a new
Message object, and a method that calculates the number of segments of the underlying protocol that
are needed to send a specified Message object.
This class is instantiated by a call to Connector.open(String). An application SHOULD call
Connection.close() when it is finished with the connection. An IOException is thrown when any
method (except close()), which is declared to throw an IOException, is called on the
MessageConnection after the connection has been closed.
Messages are sent on a connection. A connection can be defined as server mode or client
mode.
In a client mode connection, messages can only be sent. A client mode connection is
created by passing a string identifying a destination address to the Connector.open()
method. This method returns a MessageConnection object.
In a server mode connection, messages can be sent or received. A server mode connection
is created by passing a string that identifies an end point (protocol dependent identifier, for
example, a port number) on the local host to the Connector.open() method. If the requested
end point identifier is already reserved, either by some system application or by another
Java application, Connector.open() throws an IOException. Java applications can open
MessageConnection connections for any unreserved end point identifier, although security
permissions might not allow it to send or receive messages using that end point identifier.
The scheme that identifies which protocol is used is specific to the given protocol. This interface does
not assume any specific protocol and is intended for all wireless messaging protocols.
An application can have several MessageConnection instances open simultaneously; these
connections can be both client and server mode.
The application can create a class that implements the MessageListener interface and register an
instance of that class with the MessageConnection object(s) to be notified of incoming messages.
With this technique, a thread does not have to be blocked, waiting to receive messages.
Q12. When do you define a CommandListener in your MIDlet? Critically discuss the method of
this interface that you must implement.
javax.microedition.lcdui
Interface CommandListener
public interface CommandListener
This interface is used by applications which need to receive high-level events from the
implementation. An application will provide an implementation of a CommandListener (typically by
using a nested class or an inner class) and will then provide the instance to
the addCommand method on a Displayable in order to receive high-level events on that screen.
The specification does not require the platform to create several threads for the event delivery. Thus,
if a CommandListener method does not return or the return is not delayed, the system may be
blocked. So, there is the following note to application developers:
the CommandListener method should return immediately.
Method Summary
void commandAction(Command c, Displayable d)
Indicates that a command event has occurred on Displayable d.
public void commandAction(Command c, Displayable d)
Indicates that a command event has occurred on Displayable d.
Parameters:
c - a Command object identifying the command. This is either one of the applications have
been added to Displayable with addCommand(Command) or is the implicit
SELECT_COMMAND of List.
d - the Displayable on which this event has occurred
Source: http://docs.oracle.com/javame/config/cldc/refimpl/midp2.0/jsr118/javax/microedition/lcdui/CommandListener.html
Q.13
mport javax.microedition.lcdui.Alert;
import javax.microedition.lcdui.AlertType;
import javax.microedition.lcdui.Command;
import javax.microedition.lcdui.CommandListener;
import javax.microedition.lcdui.Display;
import javax.microedition.lcdui.Displayable;
import javax.microedition.lcdui.TextBox;
import javax.microedition.lcdui.TextField;
import javax.microedition.midlet.MIDlet;
public class TwoAlert extends MIDlet implements CommandListener {
private Display mDisplay;
private TextBox mTextBox;
private Alert mTimedAlert;
private Alert mModalAlert;
private Command aboutCommand, goCommand, exitCommand;
public TwoAlert() {
aboutCommand = new Command("About", Command.SCREEN, 1);
goCommand = new Command("Go", Command.SCREEN, 1);
exitCommand = new Command("Exit", Command.EXIT, 2);
mTextBox = new TextBox("TwoAlerts", "", 32, TextField.ANY);
mTextBox.addCommand(aboutCommand);
mTextBox.addCommand(goCommand);
mTextBox.addCommand(exitCommand);
mTextBox.setCommandListener(this);
mTimedAlert = new Alert("Network Error", "A network error occurred. Please try again.",
null,
AlertType.INFO);
mModalAlert = new Alert("CopyRight Info",
"A simple MIDlet that demonstrates the use of Alerts.", null, AlertType.INFO);
mModalAlert.setTimeout(Alert.FOREVER);
}
public void startApp() {
mDisplay = Display.getDisplay(this);
mDisplay.setCurrent(mTextBox);
}
public void pauseApp() {
}
public void destroyApp(boolean unconditional) {
}
public void commandAction(Command c, Displayable s) {
if (c == aboutCommand) {
mDisplay.setCurrent(mModalAlert);
}
else if (c == goCommand) {
mDisplay.setCurrent(mTimedAlert, mTextBox);
}
else if (c == exitCommand) {
notifyDestroyed();
}
}
}
//////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Q.14
/*
* To change this template, choose Tools | Templates
* and open the template in the editor.
*/
import javax.microedition.midlet.*;
import javax.microedition.lcdui.*;
/**
* @author U
*/
public class Commander extends MIDlet {
public void startApp() {
Displayable d = new TextBox("TextBox", "Commander", 20, TextField.ANY);
Command c = new Command("Exit", Command.EXIT, 0);
d.addCommand(c);
d.setCommandListener(new CommandListener(){
public void commandAction(Command c, Displayable s)
{
notifyDestroyed();
}
});
Display.getDisplay(this).setCurrent(d);
}
public void pauseApp() {
}
public void destroyApp(boolean unconditional) {
}
}
SYNOPSIS
Leveraging The power of cloud computation (case study)
Schrödinger turned to Amazon Web Services. Without any up-front investment in
infrastructure, Schrödinger leveraged software from Amazon Web Services partner
Cycle Computing (cyclecomputing.com) to provision a fully secured cluster of 50,000
cores, powered by the Intel® Xeon® processor E5 family.
This configuration enabled the team to run 16 million molecular simulations an hour.
These simulations, which would have tied up Schrödinger's limited number of
in-house servers for weeks, took just eight hours.
http://www.powerof60.com/en/see-it-in-action/schrodinger
New
http://www.smartinsights.com/mobile-marketing/mobile-marketing-analytics/mobile-marketingstatistics/
1.2 trillion searches. 146 languages. In 2012 on Google.
New
Moore’s Law, which describes the long-term trend that computing capability doubles every
18 months to two years.
“Now, the maths of that is interesting,” “Doubling every 18 months is roughly a factor of 10
in five years. In 10 years that’s a factor of 100. In 25 years it’s roughly a factor of 100,000.
“So when you go back and you look at things 15 years or 10 years ago, understand that we
were operating in the context of 1,000 times less computation, thinking, networking, data
analysis – we just couldn’t do it.
“We couldn’t do the maps. We couldn’t do the searches. We couldn’t physically do it. You
couldn’t get enough hardware. You couldn’t get enough power, whereas now it is trivial. So
50 years from now, people will think of us the way we think of the conversion from black
and white to colour television. They will think: 'Why couldn’t they do these extraordinary
things?’ ”
From http://www.telegraph.co.uk/technology/google/8303847/Googles-Eric-Schmidt-predicts-thefuture-of-computing-and-he-plans-to-be-involved.html
//////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
- There are about 1.5 billion Users online - from around 6.3 billion population of the whole world.
- Another 1 billion more people will be online by 2016 (Point to consider is that these billion people are
those who literally have no connection to the connected world right now via internet) so these are new
comers –
-There are over 1 Billion PC’s connected to the internet, that number is to increase as well.
- We have about 4 Billion Telephone terminations, 3 Billion Mobile phones of any kind- World wide –
out of which 1 billion are Smart phones – All or most smart phone are now connected with one way or
another to the internet.
- Another 1 billion mobile phone users will come online in next 2 to 3 years and they will have their
first introduction/access to the internet via their mobile phone!!!
- Mobile internet adoption rate is faster than anything else we have seen in traditional media, Internet
Mobile growth is 8 times faster than then traditional internet on desktops and PC’s
- 120 thousand blogs being created every day
- 15 hours of video gets uploaded to youtube every minute
- Sales of CD declined by 20 % cos of iTunes and other Cloud Based Music software,
people stream it online and use subscription models
Rate of underlying technology innovation is not slowing down in next decade, a technology
base case would offer that Moor’s Law – which is the rule that semiconductors double in
capacity or speed every 18 months is going to continue for atleast next 10 years.
So CPU rates will increase by a factor of 100 in next ten years
Another law – kryder's law says that memory(digital storage space) doubles every 12
months. (from http://youtu.be/dTZKNcx9sBA?t=9m20s)
42 % of internet users (between the age of 18 - 29) use internet as their primary source of news
information.
32 % of internet users (between the age of 18 - 29) use video sharing sites – DAILY
- From a case study: For 50 million users in North America, it took almost 37 years for radio, 15 years
for television, 6 years for cable, and 3 years for internet to reach and adopt. Now the rates of
adoption are becoming much less slower due to time compression so for mobile internet adoption, it is
assumed to be less than 2 years.
- Most time spend on the internet (Online) is on social networking sites, 1 out of every 6 minutes
spent online is spent on social networks like face book, and twitter etc.
- The Ecommerce industry is in the order of about 14 Trillion dollars. Soon most businesses will be
online.
- Advertising Business worldwide is about 700~800 billion dollar industry
- Another important statistics is that the amount of data that was produced from the birth of
Adam(Aliyeh AsSalam)(Dawn of humanity) till 2003 was about 5 Exabyte (1 Exabyte ~ 1 billion
gigabyte)- now the same amount of data is being produced roughly every 2 days. (i.e. explosion of
information)
These statistics worry me that we r not in this game,
And when we put all these in prespective,
we see
(1) Mobile Apps – Thats what users will be using on these new devices
and
(2) Internet on Mobile - as more people connected to Internet – and then spending time on social
networks and other geo targeted / geo aware services helping them, surely after watching videos and
playing games people would like to be part of some social network(so I am thinking along lines of a
muslim version of facebook/twitter with added muslim functionality essence) , Buying Selling (this is
also something as tabrez bhai pointed out, is still room),
Geo Aware services(too hot for me to handle)
Rough Research Work
Axis is used for Projects that need to consume or expose Web services that use SOAP encoding.
SOAP encoding has been deprecated and is no longer supported by modern Web service
frameworks. However, there are still legacy services that use type of encoding.
Apache Axis is an Open Source SOAP server and client. SOAP is a mechanism for inter-application
communication between systems written in arbitrary languages, across the Internet. SOAP usually
exchanges messages over HTTP: the client POSTs a SOAP request, and receives either an HTTP
success code and a SOAP response or an HTTP error code.
SOAP messages are XML messages. These messages exchange structured information between
SOAP systems. Messages consist of one or more SOAP elements inside an envelope, Headers and
the SOAP Body.
http://axis.apache.org/axis/java/install.html
Service Broker
Companies interested in setting up Web Services will likely use a Service Broker as the backend to
their Web Services protocol interfaces (UDDI, SOAP).
Service Broker is made up of the following components:
A Business Process Manager (BPM) Component.
Middleware connectors.
Content-based Routing and Transformations for messages.
Security Mapping.
Process State Management.
Connector Discovery Mechanisms. Currently, UDDI is the best-known example of such a
facility. It implements white (lookup by name), yellow (lookup by type), and green (lookup by
interface supported) searches over the available registered connectors.
Transaction Monitor.
Source :http://www.theserverside.com/news/1365392/Proprietary-vs-Standard-Solutions-NotAlways-a-Clear-Choice
A WSDL file contains information about the different components and their respective messages,
the message format being used, and the network protocol over which the messages are being
communicated.