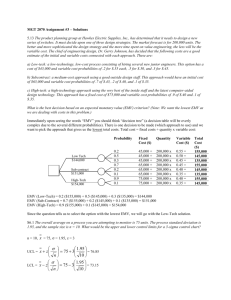
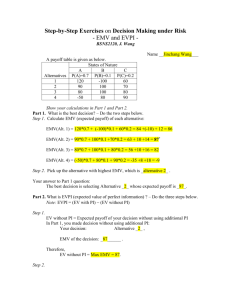
FRB Dallas Payments Fraud Survey
advertisement

Payment Trends: Fraud, Risk Management, & EMV Rocky Mountain AFP Jan. 22, 2014 Matt Davies, AAP, CTP, CPP Federal Reserve Bank of Dallas 1 FRB Dallas Payments Fraud Survey FRB Dallas, collaboration w/ other FRBs, and ICBA of America Addressed payments-related fraud experiences of banks and businesses Help us better understand new or continuing challenges with payments fraud, and methods used to reduce fraud risk Five TX AFP/TMA chapters, and SWACHA, distributed to members Survey results: Dallas District: http://www.dallasfed.org/assets/documents/banking/firm/fi/fraud_survey.pdf National: http://www.minneapolisfed.org/about/whatwedo/payments/2012-paymentsfraud-survey-consolidated-results.pdf 2 FRB Dallas Payments Fraud Survey Payment-related fraud remains a significant concern for financial institutions (FIs) & corporates For FIs, signature debit card is the payment instrument most vulnerable to attempted fraud & FI losses Over half of FIs reported that signature debit card losses from fraud exceeded their investment in mitigation to prevent such fraud – Perhaps a cost-effective opportunity to increase fraud prevention investments FRB Dallas Payments Fraud Survey For non-FIs, check continues to be the payment instrument most vulnerable to attempted fraud & losses Corporate account takeover can result in significant losses, but was not identified as a commonly-occurring fraud scheme that affected a high percentage of respondents to this survey* Most FIs & others report total fraud losses that represent less than 0.3% of their annual revenues Strategies to detect & prevent fraud effectively require the use of multiple mitigation methods & tools – i.e., a “layered” strategy FRB Dallas Payments Fraud Survey Two-thirds of respondents that reduced their fraud losses cited as factors: – Enhanced fraud monitoring systems – Employee education & training Offering risk mitigation services to customers is a growing area of opportunity for FIs Cost is the main barrier that prevents FIs & others from investing more in mitigating payments fraud FIs & others are focused now on the need for alternatives to magnetic stripe authentication technology to secure card payments [=EMV] AFP Fraud Survey 2013 AFP Payments Fraud and Control Survey – Organizations generally do not change out affected bank accounts after experiencing fraud. Instead: • Rely on established controls to identify additional incidences (38%), or • Make adjustments such as changing the check series or adding new controls (24%) – Best practice: Daily reconciliation – Best practice: Segregating accounts: 74% of organizations maintain separate accounts for different payment methods and types. Check/Check 21 Fraud Prevention Traditionally, organizations relied upon physical security features of a paper check (watermarks, microprint, or special ultraviolet ink). These features are rendered useless for verifying the authenticity of check images. As a result, organizations need to use acceptable alternative methods for detecting fraud, without using the original physical check C21 Indemnity Provision - Claim can be filed if: – Orig paper check had security features NOT visible after imaging – FI would have physically reviewed the item Check/Check 21 Fraud Prevention Positive Pay/Reverse Positive Pay/Positive Pay with Payee Verification – 2010 check fraud case: Cincinnati Insurance Co. v. Wachovia Bank Make large dollar payments electronically. Avoid using laser checks. Use a controlled stock of high security checks, with safety features such as a true watermark, thermochromatic (heat sensitive) ink and reactivity to various chemicals. FIs: Lower sight review thresholds, and re-train inspectors to look for physical security features Mobile RDC Risk mitigation: – FIs that offer mobile RDC should have protections in place to block duplicate deposits – Do not have to offer mobile RDC to all customers; “qualify” – Typically limit the dollar amount that can be deposited (daily, monthly) Risk: “Double Dipping” (or Triple, etc.) Hacks waged against mobile will likely increase. – As more FIs launch mobile RDC, those threats will grow. – If users save check images they capture with their mobile-phone cameras, that creates more risk. – Mobile-banking apps that transmit check images also can be compromised with malware. Corporate Account Takeover Account takeovers have grown more common, as fraudsters go after smaller businesses and smaller banks, where security is often weaker. – Many small business owners are no more savvy about risks than the average consumer 10 Corporate Account Takeover Individual Americans are protected by Reg E & are liable for a maximum $50 if a cyber-thief strikes. Companies have no such guarantees. In the US, corporate customer liability is governed by the Uniform Commercial Code (UCC). Companies are responsible for stolen funds if: – they have agreed to a security procedure with the bank, – the bank followed it, and – the procedure was ‘commercially reasonable.’ 11 FFIEC Guidance FFIEC Supplemental Guidance on Internet Authentication – Released June 2011 – Supplement to Authentication in an Internet Banking Environment guidance issued October 2005 – Lays out three broad steps banks should take to guard against malware attacks. – Reaffirms the need for banks to conduct risk assessments at least once a year – Establishes minimum requirements for educating customers about online fraud. FFIEC Guidance Prescribes layered security for business accounts – Including the ability to detect and respond to suspicious activity when logging in and initiating transactions. – Stop relying on tokens, passwords and cookies – Use “layered security,” including software that flags unusual behavior such as multiple transfers within minutes to new recipients Directs FIs to add security for business bank accounts, including enhanced controls over admin functions Does not endorse any specific technology for doing so FI should make clear to business customers they are not protected by Reg E Corporate Account Takeover Experi-Metal - Small parts supplier for US auto industry, based in Michigan Signed up for online banking in 2000 “Regularly received e-mails from the bank with instructions” Jan. 22, 2009 – Controller received a fraudulent e-mail appearing to come from Comerica directing him to fill out a ‘Comerica Business Connect customer form,’ including his user name, password and pin from a token (7:35 a.m.) Comerica vs. Experi-Metal By 2:02pm, 93 payment orders had been issued in Controller’s name, sending $1.9m to accounts in Russia, Estonia and other places where Experi-Metal had never done business (acc. to court records, had sent such wire transfers only twice in the previous two years) Four hours into events, JPMC, party to 6 transfers destined for customer accounts at Alfa-Bank, Moscow, called with suspicions. Still, a further hour and ½ passed before Comerica stopped the transfers Fraudulent wire transfers totaled more than $1.9m; Company lost $560,000 Comerica vs. Experi-Metal Experi-Metal sued Comerica; case tried in Detroit in 2011. Experi-Metal and Comerica had had good relations until the incident. Case hinged on whether: – Comerica’s practices were “commercially reasonable”; – any reasonable practice must include forthright behavior or “fair dealing”; – whether Comerica’s defenses and response on the day were so lax as to be objectively unfair. Comerica vs. Experi-Metal Experi-Metal’s expert witness on bank security testified that most banks could spot anomalies, a point which Comerica disputed. Comerica said it should not have been expected to do so; it had no obligation to monitor what was happening in customer accounts. “Comerica’s employees did not purposefully allow any fraudulent wires to leave the bank once the fraud was confirmed,” adding that the bank was “entitled to rely on its customer’s assurance that it would keep confidential its login ID, password and secure token number.” Comerica vs. Experi-Metal Judge disagreed: – Though the regulatory guidance then in effect did not require better monitoring, Comerica was not acting in good faith if it merely had a “pure heart and empty head.” – Citing numerous oddities about the transactions and the slow reaction when JPMC called, the judge concluded that he was “inclined to find that a bank dealing fairly with its customer, under these circumstances, would have detected and/or stopped the fraudulent wire activity earlier.” Ordered Comerica to reimburse Experi-Metal $560,000; settled in August 2011 for an undisclosed amount. PATCO v. People’s United PATCO Construction (Maine) vs. former Ocean Bank (now Peoples United) – Court delivered a different legal outcome. – Case spurred by the fraudulent ACH transfer of $545,000 in May 2009 – Magistrate sided with the bank – PATCO appealed the ruling PATCO v. People’s United 7/3/2012: First Circuit Court of Appeals, Boston, reversed the district court’s 2011 ruling in PATCO…; ruled in favor of PATCO Further recommended that the two parties pursue an out-of-court settlement of the case. Ruling describes the bank’s security procedures as “commercially unreasonable”; bank should have detected and stopped the fraudulent transactions PATCO v. People’s United Decision demonstrates that effective data security is not just about the technology; it is equally about people. The bank’s system allowed for: – Used by the bank: UID & password, customer device recognition by IP address & cookie, transaction risk profiling, challenge-response based upon shared secrets, dollar amt. threshold for invoking challengeresponse, access to intelligence from the eFraud Network including IP addresses of known hostile systems – Not used by the bank: one-time-password tokens, out-of-band authentication, user-selected image for recognizing the bank, risk scoring reports PATCO v. People’s United Court’s decision: The heart of the problem was not with the technology, but with the decisions made by the bank. – Bank triggered challenge questions for any transaction over $1. • This increased the frequency with which a user was required to enter answers to challenge questions; increased the chance that authentication info could be stolen by hackers (e.g. through a keylogger or other malware). – When the system triggered warnings that fraud was likely occurring, bank personnel did not monitor transactions, or provide notice to customers before allowing transactions. – Bank personnel did not monitor risk-scoring reports. – Bank did not conduct regular reviews of transactions that generated high risk scores. PATCO v. People’s United Bank employees should have been aware of the increased risk of compromised security; at the time in question, keylogging malware was a “hot topic” in the financial industry (and continues to be). Bank personnel should have understood that triggering the same challenge questions for all transactions (highrisk and ordinary) was not effective as a stand-alone backstop to password/ID entry. PATCO v. People’s United Bank’s decision to set dollar amount rule at $1 for all customers ignored legal requirement that security procedures take into account “the circumstances of the customer” known to the bank. – Instead, bank was using OSFA approach – Bank did nothing with the info generated by comparing the fraudulent transactions against the customer’s profile. Other banks’ clients using the same security product employed manual reviews or some other security measure to protect against the type of fraud that occurred in this case. PATCO v. People’s United Takeaways: – Review the items outlined above and compare for your organization; these factors could lead a court to conclude that your security procedures are not commercially reasonable. – When purchasing a technology solution for info security, it must be robust & commercially reasonable – Human factors are important for properly implementing/using a system. – Do not set system alerts or alarms to be overly-sensitive (“boy who cried wolf”) PATCO v. People’s United Continually review your system & personnel procedures to ensure they continue to meet with industry standard security measures, & are appropriate to meet continually changing risks and threats. Security is not OSFA: – Should be configured to your organization; AND – Procedures/actions taken in response to security system outputs must take into account each customer’s own unique circumstances Ensure that personnel are properly trained on info security systems, and that they monitor its outputs through manual reviews and similar procedures. SOURCE: “Appellate Court Decision Demonstrates Security Is Not Just about Technology – It’s about People,” Foley & Lardner LLP 8/16/2012 Choice Escrow & BancorpSouth 2010: Choice Escrow & Land Title, victim of hackers who obtained its online banking details using malware and wired $440,000 to a bank in Cyprus. Later that year, Choice sued BancorpSouth for failing to provide “commercially reasonable security,” demanding damages and recovery of losses related to the attack. 2012: The bank filed a counter-suit, arguing that Choice should be held responsible for losses, damages and legal costs. US district court in Missouri dismissed the counter-claim, though judge said it was a “very close call.” Choice Escrow & BancorpSouth March 2013: U.S. District Court for the Western District of Missouri rejected Choice’s suit against BSB. Court’s decision was based on the fact that Choice declined to use security measures BSB had encouraged it to use. When Choice adopted online banking in 2009, BSB usually required that customers use dual control. Choice declined dual control on two different occasions: it preferred convenience; the employee who handled wire transfers was often in the office by herself. Choice Escrow is appealing (as of June 2013). Dual Control Alternatives for customers that are too small to have dual custody (e.g., a company only has two employees)? – E.g., Wells Fargo this year introduced a feature called secure validation. – When a customer submits a payment, the bank can text or call the user’s mobile device and provide a number that the customer then has to enter in a field on the site. Park Sterling Bank/Wallace & Pittman Park Sterling Bank, Charlotte ($2bn) Suing law firm Wallace & Pittman to recover funds the firm sent electronically to Russia after an e-mail purporting to be from an industry group lured someone at the firm to surrender user name and network password • Fraudsters hijacked W&P’s account and instructed Park Sterling to transfer roughly $336,600 through JPMC to a recipient in Moscow. • W&P asked Park Sterling to stop the transfer after receiving confirmation of it, but the request allegedly came too late. • Park Sterling initially refunded the sum stolen but later demanded its return. Park Sterling/Wallace & Pittmann Park Sterling claims W&P failed to use dual control, and that the agreement governing the firm’s account put the risk of loss on the firm. W&P claims PSB should have flagged the transfer, as it was the first international transfer W&P made, and that the bank should have warned customers about phishing attacks. Efficient Services Escrow Group July 2013: AP reports that the bank account of a California escrow firm, Efficient Services Escrow Group, was hacked in December 2012 and January 2013, with three payments totaling $1.5 million wired to accounts in China and Russia. Only $432,215 was recovered, and the company was shut down. Future Trends Trends in Corporate Account Takeover: – Malware Goes Mobile – Same-Day ACH/”Faster Payments”? Prevention A wealth of info online about corporate account takeover. – Basic principles a company should follow to prevent takeover: daily account recon, employee education, security, use of multifactor authentication and dedicated PC(s) for performing online banking functions. Perhaps less emphasized: – Preparedness: A company’s risk profile/risk assessment should include information about corporate account takeover. – How will you attempt to prevent it (operational)? – How will you mitigate the risks associated with it (financial/reputational)? – No one-size-fits-all solution; each organization’s plan will likely vary. Prevention Security: – Use of firewalls, antivirus, anti-spyware, anti-malware, etc., is often touted for preventing corp. acct. takeover. Are you using these? – More importantly, are you using products that form a “suite”? “Security programs from multiple companies sometimes do not work well together, often working against each other.” [NACHA] – Minimize the number of employees user accounts with admin rights; many malware programs can infect a PC only if the user has admin rights. – Restrict use of flash drives to those provided by your IT dept. NACHA, “Sound Business Practices for Companies to Mitigate Corporate Account Takeover” (Spring 2011): https://www.nacha.org/userfiles/File/Sound%20Business%20PracticesBusinessesFinal04281 1.pdf “In Case of Emergency. . .” Employee education is crucial; employees should know whom to notify and how regarding any suspicious activity. Corporates should work with FI to ensure online access to user accounts is disabled; all online banking users will need to change online banking passwords, or open new accounts, if necessary. Review all recent transactions and authorizations on the account; if any are suspicious, cancel or reverse them as soon as (and if) possible. Beyond reviewing transactions, FI should ensure that hackers have not created any new users or payees, requested a change address/phone number/etc., changed access levels of any user, altered ACH batch or wire transfer templates, or ordered new cards, checks or other documents. “In Case of Emergency. . .” File a police report regarding the event. – May help you in working with FIs, insurance companies or other entities that may need to be involved in subsequent investigations. – Keep detailed records of what has happened and steps you have taken to resolve the situation. You may need to take additional action if your organization accepts credit cards. Texas Texas Bankers Electronic Crimes Task Force (Texas Banking Commissioner; U.S. Secret Service) Best Practices: Reducing the Risks of Corporate Account Takeovers (September 2011) – Protect – Detect – Respond DDoS Attacks Distributed Denial of Service May be used to distract/confuse security staff at financial institutions to initiate fraudulent wire transfers NOT like the high-volume DDoS attacks which, over the last year, have brought down many U.S. FIs’ sites – No thefts have been associated with those attacks; politically motivated DDoS Attacks 2/2013: Brian Krebs, security blogger, reported a 12/24/2012 event at Bank of the West, in which DDoS was used as a distraction; $900,000 loss. Once the DDoS was underway, hackers took over of the payment switch (e.g., wire application), using a privileged user account with access to it. Then, instead of having to get into one customer account at a time, the criminals can simply control the master payment switch and move money from many accounts. If you are/your FI is under a DDoS attack, pay attention to wire system Tax Return Fraud Identity thieves file fake federal returns using taxpayers’ SSNs; taxpayer who files subsequently finds his or her return rejected because someone already received a return using that identity. 641,052 taxpayers affected by ID theft in 2011, more than double the number affected in 2010 IRS detected 940,000 fake returns for 2010, in which ID thieves tried to obtain $6.5 billion in refunds Tax Return Fraud Prevention: – IRS now uses a code to identify taxpayers who have died, so their numbers cannot be used by thieves – IRS has issued more than 250,000 identity protection numbers to ID theft victims to use to prove they are the legitimate taxpayers when they file returns. – IRS will be implementing measures to resolve cases faster. – Taxpayers should guard SSN, and file tax returns as early as possible SOURCE: Eileen Ambrose, “Protect Your Tax Return from Identity Thieves,” The St. Louis Post-Dispatch, Sunday, May 27, 2012, p. D2 Internal Fraud Liberty Bell Bank, New Jersey – $170 million in assets – In 2011, an employee stole $301,000 from the bank. – The bank did not have insurance coverage, so its bottom line took a direct hit; in its 2011 annual report filed with the FDIC, the bank would have reported net income of $375k for the year, but instead reported a full-year profit of $74,000. Andy Peters, “Liberty Bell Bank [NJ] Suffers $301,000 Loss from Employee Theft,” Americanbanker.com, April 13, 2012 Data Breaches Many FIs and corporates do not have a written plan for dealing with breaches; all should have one. Plan should identify what executives are involved and how Should be as detailed as a plan for handling a robbery, branch fire, etc. FIs need to be able to act quickly, using fraud analysis technologies. EMV Europay, MasterCard, and Visa 1994: Founded the global standard for credit and debit payments based on chip card technology. Today, Europay is owned by MC; EMV standards are set by EMVCo, a joint venture of Visa, MC, AmEx, JCB, Discover and UnionPay. 45 EMV “Chip cards,” “chip and PIN cards,” and “smart cards” are used interchangeably. – Plastic cards that contain an integrated circuit, or microprocessor, that contains payment-related information protected by layers of security. 46 EMV EMV cards include a microchip that sends a dynamic protected value unique to each transaction Further security features embedded in the chip will support additional validation by PIN, based on the card issuer’s requirements. – PIN is most common in other countries EMV EMV standards have been adopted in many other countries, but the U.S. has lagged behind. – Reluctance due to the cost of changing payment terminals to accept chip payments. – Some American card issuers have begun issuing cards containing EMV chips, e.g., to frequent international travelers so that they don’t have payments problems abroad), but many have yet to move in that direction. – The cost of terminal and card migration may be as high as $12bn (Javelin). 48 EMV Two Ways of Accepting Chip Card Payments Contact (“dipping” the card): Cardholder inserts card into POS device. Card remains in device until completion of the transaction. If a customer removes the card before the charge is approved, the transaction will fail and the customer will be required to provide the card again. Contactless (“tap-and-go”): Cardholder waves the card by the chip card-enabled POS device to provide payment information. Once the transaction has been authorized, customer might then be prompted to enter PIN or sign a receipt. Dynamic Authentication EMV relies on dynamic authentication: use of changing variables unique to each individual card transaction When traditional mag-stripe cards are swiped at POS terminal, mag-stripe data, such as primary account number (PAN) and expiration date, are transmitted to the card issuer. The data is “static data”—it remains the same for each transaction. Dynamic Authentication In EMV transactions that use dynamic auth., the chip generates a unique cryptogram using transaction data each time the card is inserted into the chip terminal. The cryptogram is sent to the card issuer, which uses its keys and codes to calculate a cryptogram based on the same transaction data. If the two cryptograms match, the issuer knows the data is from a valid card. Effectively, you have a different number being sent each time. Dynamic auth. makes the chip almost impossible to counterfeit. PIN Authentication In many countries, EMV cards are also authenticated by PINs. PINs are static data, and are actually less secure, primarily used in cases where offline authorization/ authentication are used—e.g. areas where there is no or limited availability of online (real-time) authorization. – Areas or countries with unreliable or under-developed phone land-lines. Dynamic Authentication PINs are often used in European countries with chip cards because real-time auths are either expensive or not available. The U.S. has an extensive, reliable telecomm infrastructure for processing online transactions, so dynamic auth may become the standard. – Some unattended POS (kiosks, vending machines) may not have online capabilities allowing for real-time auth of the PIN Will allow for faster transactions if you are just sending details online to the issuer to do the auth, instead of having the auth conducted offline between the card and the terminal first. EMV can support chip-and-signature transactions and chip- and-PIN, with both backed by dynamic authentication. Benefits of EMV Reduction in counterfeit card fraud (for all players) – Reduce copying (“skimming”/cloning of mag-stripe cards Worldwide deployments have shown chip cards are more secure than mag-stripe cards – According to Financial Fraud Action UK, after introduction of EMV cards and readers, overall credit card fraud in the UK was reduced by 32.5 % between 2004 and 2011, with fraud from lost or stolen cards decreasing 56.3%. – Counterfeit magnetic stripe cards dropped 72.5 % during the same time period As U.S. prepares to move to EMV, other countries may accelerate their own EMV initiatives; as this would reduce mag-stripe fraud in the U.S., fraudsters would have to look to other non-EMV countries. 54 Additional Benefits of EMV Merchants – Visa TIP program (end mandate for validation of PCI compliance) – Potential reduction in interchange rates due to reduced fraud Acquirers – Leverage platforms and technologies deployed in other EMV markets U.S. Card Issuers – Consumers can use cards issued (avoid difficulty using mag-stripe cards abroad) Consumers – More secure transactions – Global use of smart cards (U.S. consumers have had difficulty using mag-stripe cards abroad) 55 Costs of EMV Merchants – Capital and resource investments Acquirers – Migrate merchants, processes and technology to EMV – Reduced revenue from fewer chargebacks and non-PCI compliance fees U.S. Issuers – Issue new, more expensive cards – Train consumers to use new cards Consumers – Possibly learning to enter PIN for credit (and remembering a perhaps infrequently-used PIN that is different from the customer’s PIN debit/ATM card) 56 Card Associations & EMV Visa roadmap to EMV (August 2011) – Expand TIP: Visa will expand its Technology Innovation Program (TIP) to merchants in the U.S. • TIP ends the mandate for merchants to validate compliance with the PCI Data Security Standard (PCI DSS) for any year in which 75% of the merchant’s Visa transactions stem from chip-based terminals. • To accommodate the Visa mandate, merchants must use terminals that support both contact and contactless chip technology. • “Qualifying merchants must continue to protect sensitive data in their care by ensuring their systems do not store track data, security codes or PINs, and that they continue to adhere to the PCI DSS standards as applicable.” 57 Card Associations & EMV Build Infrastructure: Visa required U.S. acquirer processors and sub-processors to support merchant acceptance of chip transactions by April 1, 2013. – Chip acceptance requires service providers to be able to carry and process additional data included in chip transactions, including the cryptographic message that makes each transaction unique Card Associations & EMV Liability Shift: Visa will institute a U.S. liability shift for domestic and cross-border counterfeit card-present POS transactions, eff. Oct. 1, 2015. – Fuel-selling merchants have until Oct. 1, 2017, for transactions at automated fuel dispensers, due to the added expense of updating. Encourages EMV adoption: – Currently, POS counterfeit fraud is largely absorbed by card issuers. – With liability shift, if a contact chip card is presented to a merchant that has not adopted contact chip terminals, liability for counterfeit fraud may shift to the merchant’s acquirer. – The acquirer will likely shift that liability down to the merchant. 59 Card Associations & EMV Visa’s plan is somewhat controversial; it downplays PIN in favor of dynamic authentication, despite the PIN’s popularity with merchants and EFT networks. – Some of the early EMV chip cards from U.S. issuers use signature rather than PIN authentication. Differs from Visa’s approach elsewhere (e.g. Australia) Card Associations & EMV MasterCard & ATMs – As of April 19, 2013, all ATMs that accept MasterCard’s Maestro international card must be made compatible with EMV cards – In Oct. 2016, a liability shift hierarchy will be introduced for ATM transactions in the U.S. • All ATMs that accept any MasterCard card need to be EMV compliant • After October 2016, FIs can hold ATM operators liable for fraudulent withdrawals and cash advances from debit and credit cards. – It costs approximately $2,000 to upgrade an ATM to be EMV-capable (Aite). Card Associations & EMV Visa & ATMs (January 2013) – Oct. 1, 2017 deadline to shift liability for counterfeit-card fraud to owners of machines not equipped to accept EMV cards. • One year later than the deadline set by MC. – Visa will also require ATM processors to be capable of handling EMV transactions by April 1, 2015. • Many ISOs that drive ATMs are not ready to support EMV at this time Card Associations & EMV MasterCard and Card-Not-Present (CNP) Transactions – Adoption of EMV at POS can divert criminals to online card fraud instead. – MC will announce an EMV-related liability shift for online and other CNP transactions. – Merchants that haven’t adopted acceptance technology that supports chip cards will assume from issuers the liability for counterfeit-related fraud. Card Associations & EMV MasterCard and CNP Transactions (cont’d): – Possible technologies consumers might use for online EMV transactions include: • a chip-equipped “display card” • a special fob that can read chip cards. • In either case, consumers could generate a unique code they could enter to secure an online transaction Card Associations & EMV Discover EMV plan (March 2012): – Discover calls its EMV payment specification “D- Payment Application Specification” (“D-PAS”) – The mandate applies not only in U.S., but also Canada, Mexico. – Oct. 1, 2015: Liability shift for Discover and Pulse (debit/ATM network) – Jan. 2012: Discover processed its first U.S. EMV transactions at some locations of Wal-Mart, which is D-PAS certified in the U.S. and Canada. 65 Card Issuers & EMV BofA – Chip and PIN – Cards available to commercial customers Jan. 2012. – First EMV card application - T&E cards; eventually will add EMV capabilities for purchasing cards – BofA feels that with chip and signature, a user may still have problems using an EMV card at unattended terminals and train ticket kiosks [in Europe]. Citi – Chip and PIN JPMC – Chip and Signature U.S. Bancorp – Chip and Signature Wells Fargo – Pilot enabled both Signature and PIN-based cardholder verification. Commerce Bank (Kansas City; $22bn) 66 Merchants & EMV Merchants ultimately will bear the cost of new POS hardware, software, and changes in their payment-processing operations to accept chip cards. Only 3% of the POS terminals in the U.S. are EMV ready (Aite, April 2012) Wal-Mart has been pushing for EMV adoption for years. Oct. 2011: Wal-Mart turned on EMV acceptance at fewer than 100 stores (of approx. 3,600 in U.S.) – Most in areas that draw foreign visitors, such as Orlando, FL. – Payment cards in EMV countries typically still come with a mag-stripe. When a foreign visitor in a Wal-Mart store equipped with EMV terminals tries to swipe a chip card at a terminal, which would activate the mag-stripe, the terminal prompts the cardholder to “dip” the card into the device so that it reads the chip. Wal-Mart, Home Depot and AMC Theaters all prefer PIN in U.S. EMV scheme 67 Issues (ASC X9) EMV’s age EMV is a proprietary standard – Governments and other entities around the world are looking for open, non-proprietary standards Ability of eventual U.S. implementations to interoperate with deployments overseas Issuers, merchants, or processors to have a say in how the standard works Outstanding Issue Unlike mag-stripe cards, the global EMV standard doesn’t allow for the Durbin Amendment’s requirement that debit cards must offer merchants a choice of at least 2 unaffiliated networks on which to route transactions. – Each EMV application is proprietary to a card brand, so while multiple payment methods may be available on the app, it supports only one network. – In the EMV specification, the application identifier (AID) is a string of characters that identifies both the network brand and the specific type of card (e.g. credit or debit). – Applications run under the AID and control such functions as online and offline authorization and security. Outstanding Issue 3/19/2013: SRPc announced it would adopt a common U.S. debit AID by licensing Discover’s D-Payment Application Specification (D-PAS). Discover solution has been in the market for 4 years and has millions of EMV cards from international issuers using it Coalition members include 10 of the largest EFT networks: AFFN, ATH, Co-Op Financial Services, Jeanie, NETS, NYCE, Presto!, Pulse, Shazam, and Star. – Account more than half of U.S. PIN-debit transactions – Additional networks expected to join in the future – The largest PIN-debit network missing: Visa’s Interlink – Also missing: MasterCard’s Maestro; Fiserv Inc.’s Accel Outstanding Issue Visa and MC have agreed to share their technology, while independent debit networks have said that Visa and MC applications are welcome on their Discoverbased common AID. The common AID tries to “preserve what happens today” in debit routing, because if all networks had their own application, it would call for “a lot of intelligence in the terminal” to route the transactions to the proper network. Solution – SRPc/Discover • Under Durbin, it is up to merchants to decide how a transaction made on an EMV debit card will be routed. • If the merchant chooses an EFT network associated with the SRPc, the Discover technology will allow the transaction to be routed “just like a mag-stripe transaction.” Solution – All? July 2013 - SRPC has agreed to allow EMV applications other than its own to work on chip cards in the US. Opens the door for chip applications from Visa and MC, which the SRPc had previously barred. SRPc continues to insist that ownership of the common AID must be held equally by all networks, with each network having an equal share in governance. As of August 2013, with the ruling against the Fed's debit interchange regulations, issuing banks aren’t sure what the ruling will mean for the work that has been completed on establishing a common AID. Business Case? “Fraud is a small, albeit growing, expense on an issuers' income statement.”—Douglas King, Payments Risk Expert, FRB Atlanta – E.g., Discover reported $93 million in fraud losses for 2012; (about $8 million more than it spent on postage). – Net charge-offs from credit card debt cost: Over $1.2bn in 2012; as much as $3.7 billion in 2010. CNP fraud continues to rise; EMV does not effectively prevent it in today’s online environment. Will EMV Work? Karen Webster, “PYMNTS Prophecies: Our Take On Eight 2013 Predictions” http://www.pymnts.com, Jan. 1, 2013 “EMV as a technology standard won’t make it in the U.S…I know that there is a liability shift expected in 2015, but that date will shift since there is no way that merchants in the US will be able to comply—and there’s precedent everywhere in the world for that to happen. Once it does…Merchants will make the point that the problem that EMV was intended to solve a decade or two ago in Europe doesn’t exist in the U.S. today, and a smart alternative will emerge to leapfrog the EMV deployments as they are currently envisioned. It is hard to imagine the U.S., on a wholesale basis, spending tens of billions of dollars to implement an ‘old’ technology. Rather, this smart alternative will pave the way for a global standard that will enable the global compatibility that it is argued EMV would provide. This also means the future of NFC in the US will remain uncertain, since there won’t be a critical mass of terminals at merchants for some time to come.”