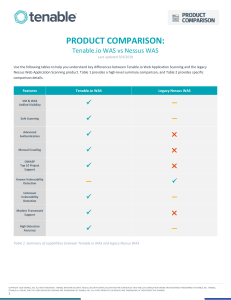
Product Features and Technical Specifications
Passive Vulnerability Scanner
The T
V
k
f
u
n
n
ef
n
n ude .
Passive Vulnerability Scanner Features
Encryption Detection
> All TLS or SSL services
> Enumeration of SSL certificates
> Alerting of expired SSL certificates
> Detection of encrypted services based
on randomness
Example Client Applications Detected
> Chrome
> Internet Explorer
> iTunes
> Firefox
> Mozilla
> Outlook
> Skype
> Thunderbird
Passive Vulnerability Plugin Families
> Backdoors
> CGI
> Database
> DNS Servers
> Finger
> FTP Servers
> Generic
> Operating System Detection
> IMAP Servers
> Internet Messagers
> IRC Clients
> Peer to Peer
> POP Server
> RPC
> Samba
> SMTP Clients
> SMTP Servers
> SNMP Traps
> SSH
> Web Clients
> Web Servers
> Class B license supports multiple PVS
instances within a unique /16
> Class C license supports multiple
PVS instances within a unique /24
Example Libraries Detected
> Java
> PHP
Real-time File and Data Logging Support
> Files shared over SMB
> Files downloaded over HTTP
> Files server and downloaded over FTP
> Files shared over FTP
> SQL database inserts, deletes and
other commands
> Each file share is logged locally or via syslog
Supported Vulnerability Standards
> Bugtraq
> CVE
> CPE
> CVSS
> Public Exploits
> OSVDB
Passive Network Discovery Methods
> Ethernet address tracking
> Observing UDP or TCP traffic
> Report on open and browsed ports
Hardware Requirements
> Typical 3Ghz, 8Gb memory systems
monitor 500–1000 Mb/s
> 100 Mb/s and 1Gb/s network interfaces
> Can be deployed in virtual environments
Deployment Options
> Red Hat 4 and 5
> CentOS 4 and 5
> Windows 2003 or 2008
> Tenable Virtual Appliance
> Tenable Hardware Appliance
Licensing
> Single PVS instance can monitor
unlimited IP addresses
Supported Protocol Analysis
> DNS
> FTP
> HTTP
> HTTP Proxy
> IMAP
> IPv4
> IRC
> LDAP
> NTP
> NFS
> POP
> SCADA
> SQL
> SPF
> SMB – Windows file sharing
> SMTP
> SNMP
> SSL
> SSH
> TFTP
> TLS
> Time To Live
> X Windows
Web Application Auditing
> Port independent web server discovery
> Expired SSL certificates
> Identification of active web sites on
each web server
> Sampling of hosted web content
> Identification of hostile ActiveX controls
> Passive discovery of web forms
and variables
> Harvesting of links and email addresses
Copyright © 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security, Inc.
The ProfessionalFeed is a trademark of Tenable Network Security, Inc. All other products or services are trademarks of their respective owners.
Tenable Network Security, Inc.
7063 Columbia Gateway Drive
Suite 100
Columbia, MD 21046
410.872.0555
sales@tenable.com
www.tenable.com