Basics of Linux Networking
advertisement

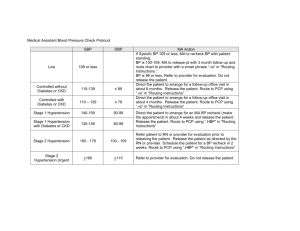
Basics of Linux Networking July 13 Reserved Network Numbers: o There is a standard reserved block of addresses for use in private networks. These are networks that will never be connected directly to any other public network. The concept of private networks applies to all OSs, not just Linux. o The private networking standard is shown below: Network Class Address Range 10.0.0.0 – 10.255.255.255 A 172.16.0.0 – 172.31.255.255 B 192.168.0.0 – 192.168.255.255 C o Routers on the Internet are designed not to “route” private network addresses. If a router encounters a data packet destined for a private network, it simply drops it. This is the reason why private network addresses are also called “non-routable” addresses. o In short, the basic purpose of private networks is to allow companies to establish LANs without the cost or bother of acquiring public IP addresses. o Here’s how we are going to set up our network in this class. Since we have only a handful of computers, we will only need to use a Class C address. I just randomly chose the Class C private network addresses of 192.168.208.0 and 192.168.209.0. (Remember that Class C addresses share the same first three numbers.) There is probably a network somewhere in the world with this address. Since private networks don’t connect to the outside world, there is absolutely no possibility of conflict. All of the workstations in this room will get an IP address on the 192.168.208.0 network. I have chosen to use the following scheme: 192.168.208.X, where X represents the computer number. For instance, we will assign the network address, 192.168.208.3 to the third computer. The Network Interface Card: o On an Ethernet-based network, the NIC in Linux uses a device name of eth0. However, if we used a different type of network such as token ring, this would be different. Token ring would be denoted as tr0. o The ifconfig utility is used to configure many of the settings for your network interface card, such as its IP address and subnet mask. Enter the command below and press ENTER. ifconfig eth0 192.168.208.1 netmask 255.255.255.0 The above command will assign an IP address of 192.168.208.1 and a subnet mask of 255.255.255.0 to the NIC. IP addresses entered with the ifconfig utility at the command prompt are temporary and last only until reboot. Enter the command below and press ENTER. ifconfig –a The above command will display the status of all interfaces including information such as IP address, MAC address, Interrupt, etc. Enter the command below and press ENTER. ifconfig eth0 down The above command will temporarily disable the NIC. Enter the command below and press ENTER. ifconfig eth0 up The above command will temporarily enable the NIC. Ping command: o Before starting, let’s talk about the ping command. It is probably the most popular networking command for Linux, as well as Windows. o The ping command sends out data packets to another computer and then waits for that computer to respond. The ping command will tell two important pieces of information: Number of packets that got successful responses and the number of packets that were “lost”. Amount of time (in milliseconds) that it took for the packet to make it to its destination and back. o The computer will continue to send out data packets until you press Ctrl+C. Loopback Device: o The loopback device isn't really a hardware device. o Its function is to happily allow you to connect to yourself and to test network software without actually having to be connected to a network of any kind. You can write and test the code locally and then when you are ready to test it on a live network o By convention, the loopback device always has an IP address of 127.0.0.1. The loopback device for Linux is called `lo'. o All Linux systems have a configured loopback device. Routing Table: o The kernel on every Linux kernel maintains a routing table. This table is used by the kernel to see what needs to be done to each data packet as it leaves the host. o The route utility can be used to view and edit the routing table. Enter the command below and press ENTER. route The above command will display a list of all network addresses, “routes,” that your computer may send data to. The routing table has eight columns. Let’s focus on the following. Destination – indicates the route destination Gateway – indicates the gateway through which packets to the destination are sent. An asterisk means that packets will be sent directly to the host. Genmask – this is the subnet mask. Flags – basically looking for the U which indicates that route is up. Metric – indicates distance to the destination. Since this number is dynamic and ever-changing, the routing table typically displays it as 0. Ref – not used. Use – number of times the kernel has performed a lookup for this route. Iface – name of interface through which packets directed to this route will be sent. Since network routes go through the NIC, they should read eth0. The loopback device route reads lo. Enter the command below and press ENTER. route del –net 192.168.208.0 netmask 255.255.255.0 eth0 The above command will delete the network address 192.168.208.0 from the routing table. At this point, will you be able to ping other computers on the 192.168.208.0 from the routing table? Enter the command below and press ENTER. route add –net 192.168.208.0 netmask 255.255.255.0 eth0 The above command will add the network address 192.168.208.0 from the routing table. At this point, will you be able to ping other computers on the 192.168.208.0 from the routing table?