Control user access
advertisement

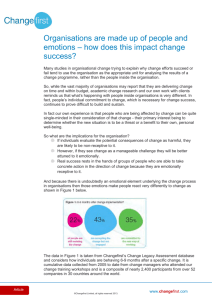
Provide secure access to network resources Control user access User groups and control mechanisms 2 2 Document the created file system 5 Set network file system controls 5 Test user access 6 Establish virus protection for a network 7 Maintain security access registers 8 Summary 9 Check your progress 9 Reading: Provide secure access to network resources 1 2005 Control user access It is very inefficient to control access for every user. The most common way of administering users is to create groups and put users into the appropriate groups. Each group is then given or denied certain access rights (or privileges) which flows onto the members of that group. It is possible for a user to be a member of more than one group and this introduces more complexity. Note, the terms access ‘rights’ and ‘privileges’ are both used in networking to mean the same thing. User groups and control mechanisms To which type of group should users be added and what mechanisms might be employed for doing this? Various server operating systems offer various types of groups. Organisational units Organisational units are designed to reflect the manner in which an organisation arranges the divisions of its business. An organisational unit (OU) in a Windows environment is more like a Context in a Novell environment. In an international organisation an OU might be a country or a global region with subordinate OUs such as Accounting, Production and so forth underneath. By default in Windows 2003 the only OU set is the domain controller. See Figure 1. 2 Reading: Provide secure access to network resources 2005 Figure 1: Default organisational unit in Windows 2003 Domain local, global and universal group scope Domains are based on hierarchical tree structures like simple organisational charts. The scope of a user’s access authority will be based upon the scope of the group of which they are a member (remembering that users can be members of more than one group). A range of levels exist for the scope of a group, for example: lowest level — domain local, eg ‘server1.au.forth.com.au’ intermediate level — global scope, eg ‘au.forth.com.au’ highest level — universal scope, eg ‘forth.com.au’. Most smaller networks consist of a single, or lowest level, domain and consequently only have domain local available as a choice. Note, in Figure 2 below where there are options available, that the scope is selected by a radio button, so only one option is available at a time. For example, if the domain is single level then the global and universal scope are disabled (greyed out). Reading: Provide secure access to network resources 2005 3 Figure 2: Domain local, global and universal group scope Individual workstation connections Windows 2000 Professional and Windows XP workstations are known as ‘secure clients’ and contain functionality to facilitate secure connection to a server as a specific unit. Windows 9X clients, however, are not secure clients and therefore may allow users to attempt connection from regions not allowed by organisational guidelines. To resolve this potential threat, user configuration can be set to allow access from only particular workstations. Logon times It may be an organisational guideline that users may connect only at certain times of the day and specific days of the week. Most server systems allow for these timing requirements to be set for each user. 4 Reading: Provide secure access to network resources 2005 Document the created file system A network file system (NFS) allows administrators to manage files on several computers inside a network — as if they were on the local hard disk. So, there’s no need to know where the files are physically located in order to access them. It’s always important to have documentation for all IT systems, but very much so for the file system. Don’t rely on the characteristics of the operating system structure residing on the computer. If a computer fails it is important to be able to confirm that the restoration process has worked correctly. Additionally, when a decision is made to update a server system, it is important to recognise the structure of the existing system. All of this requires accurate documentation. Set network file system controls How would an administrator set the network file system controls and which operating systems support network file systems (NFS)? An administrator gives users and groups access rights to files and directories. These access rights can be as restrictive as ‘read only’ through to ‘changing and deleting files and directories’. The level of access control depends very much upon the operating system controlling the objects. For example, Novell and Linux allow total control of these objects down to the file level, whereas Windows allows total control of file access only on NFSformatted partitions. The higher the degree of detail, the simpler it is to completely replicate the file system. Therefore, if each access process is documented at the time it is performed, then the overall file system documentation is relatively simple to manage. Reading: Provide secure access to network resources 2005 5 Test user access Testing user access is to ensure that: users have access to the resources they should be able to access users are being denied access according to organisational guidelines. There is nothing worse for network staff than to have users complaining about being unable to access resources that they know they should be able to access. Testing user access should be complete, that is to say, testing for user connection locally is only half the story. On a domain, many users may need to have access via remote desktop, a virtual private network (VPN) or remote access via a modem. Telecommuting and roaming is a growing means of network access. Reflect Consider a situation where you have to test the access of six different classes of users. How might the user and group structure be configured to help you carry out tests efficiently? Feedback Setting users into appropriate groups and giving access privileges to the groups will help you to streamline the tests. This is the manner in which the users should be configured at all times for efficiency. Once a class of user has been tested for correct access then all other users in that group will have similar access privileges — as long as any particular user has not been given any other privileges elsewhere. Therefore, it is important to document any privileges given to individual users as well as the access rights for each group. 6 Reading: Provide secure access to network resources 2005 Establish virus protection for a network Virus infection can have a devastating effect on the functioning of networks and can cause irretrievable damage to data and other resources on a network. It is imperative to develop mechanisms to avoid virus infection. Detecting viruses and WORMs (Write Once Read Many), a virus-like class of infection, is a very sophisticated and well-defined process. Consequently, Network Administrators have to rely on third party products to manage this process. There are a variety of third party software packages available such as Symantec Anti-virus, McAffee and PC-Cillin. Symantec Corporate Antivirus is a commonly-used product by systems network managers. Reflect Consider a network with 20 workstations and one server. All the workstations are used during the standard working day and on occasions Saturdays. How would you protect the network resources from virus infection? Feedback Many people believe that virus infections are due to Internet activity but this is not necessarily so. Users may bring floppy disks, CDs or USB memory sticks to the work environment and contaminate the network in that way. It is for this reason that some network managers choose to disable the floppy disk drive while others choose to have completely diskless workstations. There are two basic methods to test for virus infections: 1 Firstly, virus scanning software can be installed on each machine, licensed and updated from each machine to facilitate up-to-date scanning. 2 Secondly, specialised virus scanning software, specifically designed for server management, automatically deploys and updates all configured clients with the appropriate scanning applications. Reading: Provide secure access to network resources 2005 7 Maintain security access registers A security access register contains the details of users who have privileges to access the network. The register holds the user’s personal details and other relevant data related to the organisational guidelines. Registers are often managed by a database, or, they may be a ‘pen and paper’ journal. They are usually maintained by a member, or members, of the IT network staff within the organisation. Reflect We have discovered that relevant data, according to organisational guidelines, will be kept about users and access privileges. What would be useful specific data about users and access configuration that can be kept in a security access register? Feedback It is important that a clear and transparent audit trail be available about users and their access privileges so that an organisation can gauge the level of security available. It’s also important to be able to defend the organisation’s position with regard to complaints from staff about too many or too few privileges, or even privacy issues. On privacy issues, many organisations will issue a disclaimer to staff stating that the organisation’s network is for organisational data and any private data stored cannot be guaranteed to be private. Specific data such as: user name, logon, who created the configuration for a user, who authorised the configuration, and the date of configuration might be headings used in a security register. These registers become important tools in managing security audits. 8 Reading: Provide secure access to network resources 2005 Summary In this reading we have covered the following aspects of providing secure access to network resources: Controlling user access — the methods built into the operating system that will allow you to take control Documenting the created file system — considering which file system is most appropriate and applicable and identify folder directory parameters Testing user access — creating procedures to test all the user needs in a variety of access scenarios Establishing virus protection for a network — methods and software packages that are used to prevent or minimise virus infection Maintaining security access registers — why such a register is needed and specific data it holds. All of this information needs to be interpreted by you into the context of whatever network operating system you are called to administer. Check your progress Now you should try to do the Practice activities in this topic. If you’ve already tried them, have another go and see if you can improve your responses. When you feel ready, try the ‘Check your understanding’ activity in the Preview section of this topic. This will help you decide if you’re ready for assessment. Reading: Provide secure access to network resources 2005 9