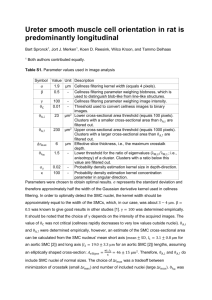
poster - Piotr Mardziel
Annual Fall Meeting of ITA
2013
Knowledge inference for optimizing and enforcing secure computations
Drawing on work appearing at ACM PLAS’12, PLAS’13, and JCS’13
P. Mardziel , M. Hicks , J. Katz , M. Hammer , A. Rastogi (University of Maryland, College Park), M. Srivatsa (IBM T.J. Watson Research Center)
______________________________________________________________________________
SMC Belief Tracking
An alternative is to perform knowledge-based enforcement as part of the SMC itself . This approach is strictly more expressive , but less efficient, than belief sets since SMC is already inefficient and knowledge tracking is also expensive.
Executive Summary
Sharing information across multiple coalition domains is critical for mission success . Such sharing can be done safely by performing guarded query processing , e.g., on ITA technologies such as the Gaian DB, the information fabric, and the controlled English store. Consider: P
1
might only answer sensor P
2
queries if doing so does not reveal too much about its sensor network. Our approach develops a provably sound knowledge-oriented query analysis , using probabilistic computation, to ensure query safety for both client/server
(section I) and multiparty (section II) queries. The analysis can also optimize multiparty computations , netting 30x speedups (section III).
I. Knowledge Tracking
For knowledge-oriented security enforcement
We can model a change in an querier P
2
’s knowledge about
P
1
’s secret s
1
, referenced as x
1
in a program Q . P
1
executes Q probabilistically using distribution δ as an estimate of the prior knowledge of P
2
. It refuses to return the result o increases P
2
’s knowledge too much. We have implemented probabilistic computation using a novel abstract domain, probabilistic polyhedra , with several optimizations.
Figure 2(a): Belief sets Figure 2(b): SMC knowledge tracking
Ongoing work : We are extending our techniques to work for continuous distributions (to model sensors) and to optimize
SMC to support efficient SMC belief tracking.
III. SMC Knowledge Inference
For optimizing SMC
Figure 1(a): Formal definitions Figure 1(b): Security enforcement
II. Security Enforcement for SMC
Secure Multiparty Computation (SMC)
SMC is a technique by which two or more principals P i
can compute a function Q over their respective secrets as if Q were computed by a trusted third party P
T
. We can enforce knowledge-oriented security for SMC using either belief sets , or
SMC belief tracking . We have proved that both techniques correctly bound information release.
Belief Sets
In this technique, each principle P i
estimates the possible knowledge of each other participant P j
, and if there is a possibility of any of them learning too much, P i
refuses to participate. To implement this, we generalized our probabilistic computation approach to sets of beliefs Δ.
SMC is slow. However, in the median program above (where
P
1
provides a1 and a2 and P
2
provides b1 and b2 ) we can actually run lines 5 and 8 as separate SMCs, and lines 6, 7, and 9 locally at either P
1
or P
2
and reveal no additional knowledge than what is already implied by the result. Doing so nets a speedup of 30 times.
We have formalized and implemented two techniques for inferring which intermediate variables (here x1 and x2 ) are implied by the output, and this information permits splitting the computation so as to optimize it as described above.
International Technology Alliance in Network and Information Sciences