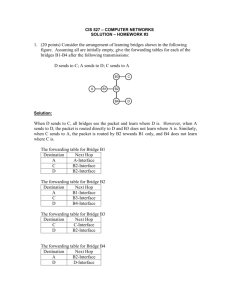
sol
advertisement

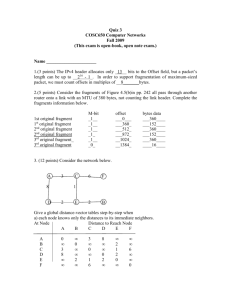
Chapter 8 A. Book Exercise (Chapter 8) : 10, 12, 13, 15, 17, 25 B. Briefly Explain Public key cryptography and its algorithm C. Briefly Explain RSA and give an example D. What is Authentication and which way may be the best way to perform authentication? E. Briefly introduce “digital signature” and how many ways we can implement this technique? F. Briefly introduce KDC and CA. Give an example of each technique and why we need to implement these two techniques. Answer (Chapter 8) A. (Question 10) An eavesdropper may have intercepted the messages exchanged in a previous transaction, and may be replaying the client’s earlier responses. Until the real client has successfully decrypted the server’s new challenge and sent back evidence of this, the server cannot be sure such a replay attack isn’t in progress. (Question 12) (Question 13) For a two-way authentication, the one-way authentication given in the chapter is done in both directions. That is, the client sends random number x to the server encrypted with the server’s public key, which the server decrypts with its private key and sends back unencrypted; at about the same time, the server encrypts random number y with the client’s public key, which the client decrypts with its private key and sends back. (Question 15) We have password[N] = g(password[N - 1]); the essential property of g is that it be believed that knowing g(x) does not provide any information that can be used to find x. (Question 17) The FAQ at www.rsasecurity.com explains: The Diffie-Hellman key exchange is vulnerable to a man-in-the-middle attack. In this attack, an opponent Carol intercepts Alice’s public value and sends her own public value to Bob. When Bob transmits his public value, Carol substitutes it with her own and sends it to Alice. Carol and Alice thus agree on one shared key and Carol and Bob agree on another shared key. After this exchange, Carol simply decrypts any messages sent out by Alice or Bob, and then reads and possibly modifies them before re-encrypting with the appropriate key and transmitting them to the other party. This vulnerability is present because DiffieHellman key exchange does not authenticate the participants. Possible solutions include the use of digital signatures and other protocol variants. (Question 25) (a) An internal telnet client can presumably use any port _ 1024. In order for such clients to be able to connect to the outside world, the firewall must pass their return, inbound traffic. If the firewall bases its filtering solely on port numbers, it must thus allow nbound TCP connections to any port greater or equal to 1024. (b) If the firewall is allowed access to the TCP header Flags bits, then to block all inbound TCP connections it suffices to disallow inbound packets with SYN set but not ACK. This prevents an outside host initiating a connection with an inside host, but allows any outbound connection. No port filtering is needed. Question B.-F. : See Power Point Slide of Chapter 8 for answers. Chapter 5 Problem 2: The maximum value of UDP Message Length field (2 bytes) is 65535 (2^16 –1). The Offset field of IP header is only 13 bits that represents a number of 2^13. Therefore in order to support the fragmentation of a maximum packet, the offset field must represent in multiples of 2^16 – 2^13 = 2^3 = 8 bytes. Problem 4: TCP message = payload + TCP header = 2048 + 20 = 2068 bytes First network: MTU = 1024 = link header + IP header + payload = 14 bytes + 20 bytes + TCP data TCP data = 990 bytes but 990 is not in multiples of 8. TCP data fragment must be 984 which is in multiples of 8. Therefore the first network generates three fragments (size, offset) = (984, 0), (984, 123), (100, 246). Second network: MTU = 512 = link header + IP header + payload = 8 bytes + 20 bytes + TCP data TCP data = 484 bytes but 484 is not in multiples of 8. TCP data fragment must be 480 that is in multiples of 8. Therefore the second network generates six fragments (size, offset) = (480, 0), (480, 60), (24, 120), (480, 123), (480, 183), (24, 243), (100, 246) Problem 6: a. The first and second transmissions are independent. Therefore the probability of packet loss of both transmissions is 0.01 * 0.01. b. The first and second transmissions are not independent because the first transmission can use the fragments of second transmission for assembling the packets. Therefore the probability of packet loss is 0.01 * 0.01 * 10. (Seriously math reasoning: P(A|B) = P(A And B) / P(B) = 0.1 * 0.1 /0.1 ) c. (a) Identification for each transmission is different (b) Identification of both transmissions is the same Problem 7: If the timeout value is too small, senders must often send ARP request to find the physical address of IP. If the timeout value is too large, it may be invalid if the physical adapter is replaced or broken. Problem : a. A B C D E F A 0 3 8 - B 0 2 - C 3 0 1 6 D 8 0 2 - E 2 1 2 0 - F 6 0 A 0 3 8 4 9 B 0 3 4 2 - C 3 3 0 3 1 6 D 8 4 3 0 2 - E 4 2 1 2 0 7 F 9 6 7 0 A 0 6 3 6 B 6 0 3 4 C 3 3 0 3 D 6 4 3 0 E 4 2 1 2 F 9 9 6 9 b. A B C D E F c. A B C D E F Problem 17. Step 1 2 3 4 5 6 7 4 9 2 9 1 6 Confirmed List (D, 0, -) (D, 0, -) (D,0,-) , (E,2,E) (D,0,-) , (E,2,E) , (C, 3, E) (D,0,-) , (E,2,E) , (C, 3, E), (B,4,E) (D,0,-) , (E,2,E) , (C, 3, E), (B,4,E), (A,6,E) (D,0,-) , (E,2,E) , (C, 3, E), (B,4,E), (A,6,E), (F,9,E) 2 9 0 7 7 0 Tentative list (A,8,A), (E,2,E) (A,8,A), (B,4,E), (C,3,E) (A,6,E), (B,4,E), (F,9,E) (A,6,E), (F,9,E) (F,9,E) Problem 21: a. 128.96.39.10/Interface 0 b. 128.96.40.12/R2 c. 128.96.40.151/R4 d. 192.4.153.17/R3 e. 192.4.153.90/R4 Problem 27: “No packets time out” assumes that each node increments its sequence number only when there is some change in the state of its local links. The LSP data for each node is as follows: Nodes Seq # Seq # Seq# Seq# after Seq # Seq # Connects to before after after node D is after a after the the link the node H added new link B-F B-F is link B- is with a link A- is broken F is added connection D is restored broken to C added A 1 1 1 1 2 2 B, C, D B 1 2 2 2 2 3 A, C C 1 1 1 2 2 2 A, B, D D 0 0 0 1 2 2 A, C F 1 2 2 2 2 3 G G 1 1 2 2 2 2 F, H H 0 0 1 1 1 1 G Problem 28. Step Confirmed List 1 (A, 0, -) 2 (A, 0, -) Tentative list (B,5,B), (D,2,D) 3 4 5 (A, 0, -), (D,2,D) (A, 0, -), (D,2,D), (B,4,D), (A, 0, -), (D,2,D), (B,4,D), (E,6,D), (A, 0, -), (D,2,D), (B,4,D), (E,6,D), (C,7,D) 6 (E,7,D) (E,6,D), (C,8,B) (C,7,D) Problem 30: a. The link changed state recently and one of the two LSP’s was old. b. It takes sometime for both B and C having the same state Problem 40: a. Class A can represent 255 hosts for a network. 7-bit host ID are needed to represent 72 hosts Subnet ID 200.1.1.0 (0000 0000) 200.1.1.128 (1000 0000) 200.1.1.192 (1100 0000) 200.1.1.224 (1110 0000) Subnet mask 255.255.255.128 No Hosts/Max 72 hosts/128 Department A 255.255.255.192 35 hosts/64 B 255.255.255.224 20 hosts/32 C 255.255.255.224 18 hosts/32 D b. If department D grows to 34 hosts, the subnet of department A is split into 2 subnets as follows: Subnet ID 200.1.1.0 (0000 0000) 200.1.1.64 (0100 0000) 200.1.1.128 (1000 0000) 200.1.1.192 (1100 0000) 200.1.1.224 (1110 0000) Subnet mask 255.255.255.192 No Hosts/Max 64 hosts/64 Department A 255.255.255.192 34 hosts/64 D 255.255.255.192 35 hosts/64 B 255.255.255.224 20 hosts/32 C 255.255.255.224 8 hosts/32 A