CPSC 558 Advanced Computer Networking
advertisement

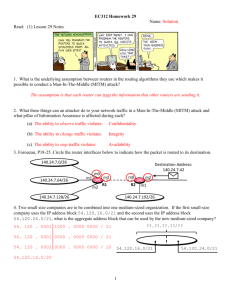
Name: Student ID: CPSC 558 Advanced Computer Networking Midterm Examination (October 26, 2004) Multiple Choices: (30%) 1. What option below about “Store-and-Forward” technology is correct? (C) a. The host(s) is used to stored and forward the packets b. There is a dedicated path maintained in a network for this purpose c. It is mainly used in a packed switching network d. It is mainly used in a circuit switching network e. The major reason to use this technique is for network security. 2. What issues about STDM and FDM below is true?(C) a. Both are the techniques used for network routing purposes b. The max number of network flow is adjustable and resizable c. The data flow for these two techniques are subject to under utilization d. STDM is used for circuit switching and FDM is used in VC networking e. STDM and FDM’s data flow is transferring on demand. 3. Which option below about digital encoding could be a potential problem? (D) a. Encode makes 0 as low signal and 1 as high signal b. Encode is to modulate electromagnetic waves c. Signals propagate over a physical medium d. Low signal (0) may be interpreted as no signal e. There could be alternative encoding methods 4. Which option below about representing network as graph is wrong? (B) a. Nodes are part of the components of the graph b. Node costs is used to represent values related to physical distance, capacity, delay, etc c. Routers is used to support the protocols and algorithm in the dynamic approach d. The assumption of edge cost in dynamic approach is known. e. The distance vector algorithm maintaining the next hop value for every destination. 5. Which of the following option about ATM is wrong? (B) a. ATM is a connection-oriented packet-switched network b. The Cells in ATM network are variable length. c. ATM used in both WAN and LAN settings d. Different ATM AAL (ATM Adaptation Layer) provides different services for network applications e. Segmentation and Reassembly (SAR) are necessary processes in ATM 1 Name: Student ID: 6. Which one below about limitation of a Learning Bridge is wrong? (E) a. Learning Bridge uses Spanning Tree Algorithm to remove loops b. There is limited scalability capability for Learning Bridge c. There could be a transparency problem for Learning Bridge d. Learning Bridge use VLAN to support scalability e. It is easy for different types of network structures can be interconnected using Learning Bridge. 7. Which one below about Datagram Switching Network is wrong? (A) a. Connection setup phase is needed b. Every packet contains the complete destination address c. This is sometimes called connectionless model d. Each Switch maintains a routing table for packets e. Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up 8. Which one below about VC (Virtual Circuit) Network is wrong? (D) a. Typically wait full RTT for connection setup before sending first data packet. b. If a switch or a link in a connection fails, the connection is broken and a new one needs to be established. c. Each data packet contains only a small identifier d. Include only Outgoing Interface for packets transfer e. It contains connection setup and data transfer phases 9. Which one below about Network Channels is wrong? (C) a. Request/reply (client/server) channel Used by the file transfer and digital library application. b. Message Stream channel could be used by both video-on-demand and videoconferencing applications c. Request/reply (client/server) channel has no need to guarantee all messages are delivered d. Message Stream channel support both one or two-way traffic and delay properties e. Message Stream channel needs to ensure that messages are delivered arrives in the same order in which they were sent. 10. Which one below is NOT a network function? (E) a. Provide Connectivity b. Addressing c. Resource Sharing d. Switching and Data Forwarding e. Server Application Supports 2 Name: Student ID: Questions and Answers: (30%) (Please provide a short/concise answer for each question.) 1. What are two Network Channels and what are the major applications used by these two channels? Briefly explain it. Request/reply (client/server) channel Used by the file transfer and digital library application. Guarantee every message sent by one side is received by the other side and only one copy of each message is delivered. Message Stream channel Could be used by both video-on-demand and videoconferencing applications Support both one or two-way traffic and delay properties No need to guarantee all messages are delivered Need to ensure that messages are delivered arrive in the same order in which they were sent. (To avoid displaying frame out of sequence.) 2. Compare datagram packet switching and VC packet switching (list four different points) See lecture slide on Chapter 1 (Part 1) 3. Briefly explain what is congestion Data packets could not continue forwarding due to the conflicts in the communication link or switch is busy of serving other packets. 4. Briefly explain what is a Layered Network Architecture See lecture slide on Chapter 1 (Part 2) 5. What are two problems of Internetworking? Briefly explain it. Heterogeneity and scaling. See lecture slide on Chapter 4 (Part 1) 6. What are three methods of source routing? Briefly explain it. See lecture slide on Chapter 3 (Part 1) Computations and Derive Questions (40%) – Extra paper allowed if you need 1. Suppose a computer B receives a message in hexadecimal format from a computer A. The message contains the payload “B246B” and the 32-bit CRC “00000107” a. What is a polynomial represented for this 32-bit CRC b. Does computer A receive a correct message? Show work and explain. c. Can computer B detect the error if the payload contains an 11-bits error? Explain why. 2. Suppose that a TCP message that contains 1964 bytes of data and 20 bytes of TCP header is passed to IP for delivery across three networks of the Internet (i.e. from the source host to a first router to a second router to the destination host). The first network uses 14-byte headers and has a MTU (maximum transmission unit) of 1024 bytes; the second uses 8-bytes headers with a MTU of 512 bytes; the third uses 16-bytes headers with a MTU of 4500 bytes. Each network’s MTU gives the total packet size that may be sent, including the network header. Give the sizes 3 Name: Student ID: and offsets of the sequences of fragments delivered to the network layer at the destination host. Assume all IP headers are 20 bytes. 3. A company has a network as the figure follows: 128.96.34.130 128.96.34.140 R1 H1 128.96.34.240 128.96.34.240 128.96.34.240 H3 R2 128.96.33.14 H2 128.96.33.1 The hosts H1, H2, H3 has the subnet masks 255.255.255.192, 255.255.255.192, and 255.255.255.0 respectively. a. What network class does this network belong to? What is network id of this network? b. How many subnets does this network have? What are subnet Ids? c. H1 has a routing table. Fill in the entries of routing table as follows: Subnet Number Subnet Mask Next hop (router) Interface 0 R1 R1 d. R1 has a routing table. Fill in the entries of routing table as follows: Subnet Number Subnet Mask Next hop (router) Interface 0 Interface 1 R2 4 Name: Student ID: 4. Give the steps as in following table in the forward search algorithm as it builds the routing database for node B in the network shown in figure as follows: A 3 4 Step Confirmed list 1 2 3 4 5 6 7 8 9 (B,0,-) 10 1 B C 6 1 1 E F 1 D Tentative list 5. (Extra Credit Question) a. What layers does ISO reference model have? Give the short description of any two layers. b. What layers does a host (end-user computers) support? c. What layers does a router support? Give the name of a protocol that each layer of router supports. (Answer) 1. a. C(x) = x^8 + x^2 + x + 1 b. C(x) = x^8 + x^2 + x + 1 CRC = 0x00000107 = 0000 0000 0000 0000 0000 0001 0000 0111 C(x) = 100000111 M(x) = 0xB246B = 1011 0010 0100 0110 1011 5 Name: Student ID: 1011 0010 0100 0110 1011 1000 0011 1 0011 0001 110 10 0000 111 01 0001 0010 1 0000 0111 00001 0101 0110 1 0000 0111 0 0101 0001 10 100 0001 11 001 0000 0111 1 0000 0111 0 0000 0000 c. Yes. It can detect any odd number of errors because C(x) contains (x+1) 2. TCP message = payload + TCP header = 1964 + 20 = 1984 bytes First network: MTU = 1024 = link header + IP header + payload = 14 bytes + 20 bytes + TCP data TCP data = 990 bytes but 990 is not in multiples of 8. TCP data fragment must be 984 which is in multiples of 8. Therefore the first network generates three fragments (size, offset) = (984, 0), (984, 123) Second network: MTU = 512 = link header + IP header + payload = 8 bytes + 20 bytes + TCP data TCP data = 484 bytes but 990 is not in multiples of 8. TCP data fragment must be 480 that is in multiples of 8. Therefore the second network generates 6 fragments (size, offset) = (480, 0), (480, 60), (24, 120), (480, 123), (480, 183), (24, 243) Third network: The third network only forwards 6 fragments (size, offset) = (480, 0), (480, 60), (24, 120), (480, 123), (480, 183), (24, 243) to the destination host because its MTU is 4500 bytes, that is larger than the size of incoming packets. 3. A company has a network as the figure follows: 128.96.34.130 128.96.34.140 H1 128.96.34.240 R1 6 Name: Student ID: The hosts H1, H2, H3 has the subnet masks 255.255.255.192, 255.255.255.192, and 255.255.255.0 respectively. d. What network class does this network belong to? What is network id of this network? 1.Class B because the first two bits of 128.96.34.240 are “10” 2.Network id is 128.96. e. How many subnets does this network have? What are subnet Ids? 1.3 subnets 2.Subnet Ids are 128.96.34.128 (H1), 128.96.34.192 (H2), 128.96.33.0 (H3) f. H1 has a routing table. Fill in the entries of routing table as follows: Subnet Number 128.96.34.128 128.96.34.192 128.96.33 Subnet Mask 255.255.255.192 255.255.255.192 255.255.255. Next hop (router) Interface 0 R1 R1 g. R1 has a routing table. Fill in the entries of routing table as follows: Subnet Number 128.96.34.128 128.96.34.192 128.96.33.0 Subnet Mask 255.255.255.192 255.255.255.192 255.255.255.0 Next hop (router) Interface 0 Interface 1 R2 4. Give the steps as in table below in the forward search algorithm as it builds the routing database for node B in the network shown in figure as follows: A 3 4 C 6 1 10 1 B 1 E F 1 D 7 Name: Student ID: Step Confirmed list 1 2 3 4 5 6 7 (B,0,-) (B,0,-) (B,0,-), (E,1,E) (B,0,-), (E,1,E), (A,2,E) (B,0,-), (E,1,E), (A,2,E), (D,2,E) (B,0,-), (E,1,E), (A,2,E), (D,2,E) (B,0,-), (E,1,E), (A,2,E), (D,2,E), (C,3,E), (B,0,-), (E,1,E), (A,2,E), (D,2,E), (C,3,E), (F,8,E) 8 Tentative list (A,3,A), (C,4,C), (E,1,E) (A,2,E), (C,4,C), (D,2,E), (F,11,E) (C,4,C), (F,8,E) (C,4,C), (F,8,E) (C,3,E), (F,8,E) (F,8,E) 5. Extra Question ISO Ref Model layer Physical Link Host X X Network Transport Session Presentation Application X X X X X Router X X = PPP, Ethernet frame X = IP 8