Argus Hardware and Software Complex for Detecting Computer
advertisement

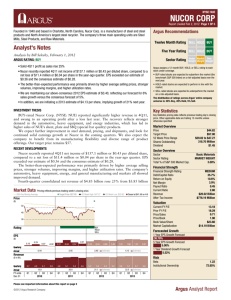
Argus Hardware and Software Complex for Detecting Computer Attacks The hardware and software complex for detecting computer attacks Argus is meant for detecting intrusions and suspicious actions, which may inflict harm to the most critical components of Automated Information Systems (AIS), i.e. operation systems, applications, implementing network services of information systems, as well as data, stored and processed in the network. Together with another company’s product, the system for recording, analyzing and monitoring of information security events (RAMS ISE), this complex reliably prevents intrusions at a channel rate up to 1 Gb/s. To detect computer attacks Argus performs a signature analysis of the network traffic, protocol analysis, analysis of abnormalities over cumstat for protocols of 3-7 levels of the Open Systems Interconnection/Reference Model (ISO/OSI reference model). Argus includes integrated user interfaces for ISE analysis and report preparation by complex operators and administrators. The complex enables to obtain an extensive wide set of statistical data in the form of diagrams and tables, which are available for analysis through a Web-interface. Below is shown a screen hard copy of the control console with one of examples An example of a Netflow-statistics report, available through the Web-interface. The complex includes Netflow- statistics report sets for analyzing the following data: hosts, which use a large percentage of the network bandwidth; hosts with a large numbers of contacts with other network hosts; hosts, which use forbidden protocols, or hosts, incorrectly using permitted protocols; total used protocols percentage, including traffic ratio for TCP and UDP protocols; overall traffic performance: number of packages, volume of traffic; total traffic distribution over ports TCP and UDP; list of active hosts in the network with individual common host traffic characteristics (size, packages, used protocols, TCP/UDP sessions and TCP/UDP ports); network load within specified time periods; total traffic percentage between local subnet hosts, local and external hosts; LAN host matrix with the volume of traffic they exchange. Using the listed data a DoS / DDoS attack detection is possible, as well as identification of hosts, included in botnets, host scanning as well as other net interaction abnormalities. To achieve higher flexibility and setting precision of the Complex the interpretable scenario language is used. The scenarios’ mechanism is designed for defining logics and patterns to be found in the data traffic, as well as the determination of registered events response method. One may distinguish capabilities of the signature object, which encapsulates input data for the signature analysis: To determine correlations between signatures within a connection (i.e., the current signature validation condition is activation of another signature, set for the server’s error message); To set multiple regular expressions; To set regular expressions only for packet heading or package body; The signature object has access to the connection context for application protocols, therefore it is possible to set parameters of the connection, within which respond is expected: direction, status, port, address, protocol. Using scenarios, it is possible to obtain access to data of Argus’s protocol analyzers and describe, what should be done in the event handler. The event handlers can control and update information on the entire system status, generate new events, launch functions, generate notifications, containing alarms, and send them to external recipients via e-mail or SMS. The scenario setting mechanisms allow to reduce manual editing, the number of introduced errors and the Complex’s setting time. The scenarios and signatures are delivered by Special System Engineering Center LLC and may also reconfigured or developed by organizations’ security managers. The scenario mechanism allows to set currently supported protocol analyzers of the Complex: transport level: ARP, IP, ICMP, TCP, UDP; application level: DHCP, SunRPC, DCE_RPC, DNS, Finger, Gnutella, FTP, HTTP, Ident, IRC, Netbios-SSN, NCP, NFS, NTP, POP3, Portmapper, RSH, Rlogin, SMB, SSH, SSL, SMTP, Telnet. Basing on the scenarios, it is possible to establish security policies, which will be meant to control traffic for: Java-applets, ActiveX-scenarios, macro viruses, Internet-worms and other malicious objects; Specified character sequences and key words in package heading or body; Use of network applications (Web, ICQ etc.); Bruteforce attacks (direct-search brute force method) for HTTP, FTP, SMB, SSH, Telnet and other protocols; Protocol encapsulation to create tunnels; Protocol operation abnormalities and RFC deviation based on the statistical and heuristic analysis; Time-phased attacks, which use different protocols; Fragmented traffic attacks; Trojan Horse software traffic. Therefore, the use of Argus is highly effective as tool for detecting computer attacks and suspected actions, as well as incident investigations, identification of unsecure services and organization’s network sections, as well as network performance determination. Argus complies with the requirements of the Federal Security Service of Russia (FSB) regarding computer attack detection systems, having certification from the Federal agency on technical and export control, what allows using it for confidential information protection and in personal data systems. Argus has been successfully implemented and used for confidential information protection in automated information systems of a number of Russian public and commercial organizations. _________________________________________________________________________ Special System Engineering Center LLC Russia, 117105, Moscow, Varshavskoye Highway, 33 Phone (495) 978-6620, Phone/fax(495) 657-9948, www.ssec.ru