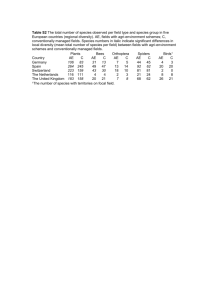
Efficient Authentication and Key Management Mechanisms for Smart
advertisement
Efficient Authentication and Key Management Mechanisms for Smart Grid Communications Abstract: we propose an efficient key management protocol based on our enhanced identity-based cryptography for secure SG communications using the public key infrastructure. Secure key distribution schemes for group communications allow to establish a secure multi cast communication between a group manager and group members through an unreliable broadcast channel. Our proposed mechanisms are capable of preventing various attacks while reducing the management overhead. The improved efficiency for key management is realized by periodically refreshing all public private key pairs as well as any multicast keys in all the nodes using only one newly generated function broadcasted by the key generator entity.The article classifies, analyzes and compares the most significant key distribution schemes, by looking at the selective key distribution algorithms, at the predistributed secret data management, and at the self-healing mechanisms. It reviews polynomial-based algorithms, exponential arithmetic based algorithms, hash-based techniques, and others. Propose classification of schemes based on the applied cryptographic primitives. Self-healing group key distribution schemes can be used in various network scenarios, thus, to make their analysis and comparison easier, we introduce an abstract model of the network in which these schemes are applicable. We identified three elements, or building blocks, of self healing key distribution scheme which can be used to classify and compare the existing solutions Existing System: 1) Insecure mechanisms provided in the existing network. 2) Almost none of the schemes is suitable for large scale WSN in real- world applications. 3) Existing solutions usually present some trade-off between scheme performance and security level. 4) Identifies basic building blocks of the scheme and describes in details all major types of existing solutions. 5) It also contains a thorough security and efficiency analysis of each solution, and points out issues not identified. Proposed System: 1) Functionality of the scheme is decomposed into three separate aspects, namely: selective key distribution mechanism, predistributed secret data management and self-healing mechanism, which are used to classify and compare schemes. 2) Self-healing group key distribution schemes can be used in multi-cast networks with smart grid systems, which are established over a networksl, such as machine-to-machine systems, cellular networks and wireless networks. 3) Communications security is achieved by message encryption and authentication using shared symmetric secret group key. 4) A prospective group key distribution scheme should satisfy the following requirements: • The scheme should prevent adversaries or unauthorized user nodes, which are not in G, from learning the group key. • Key distribution scheme has to provide fresh keys. Software Requirements: Platform : JAVA(JDK 1.6) Front End : JAVA Swing Back End : MySQL IDE : Net Beans 6.9 Operating System : Microsoft Windows XP Hardware Requirements: Processor : Pentium IV Processor RAM : 512 MB Hard Disk : 10GB Monitor : 14” VGA COLOR MONITOR