Chapter 15 Study Guide(Jay Xiong)
___________________________
Name
___________________________
Date
IT ESSENTIALS MOD 15
ADVANCED NETWORKS
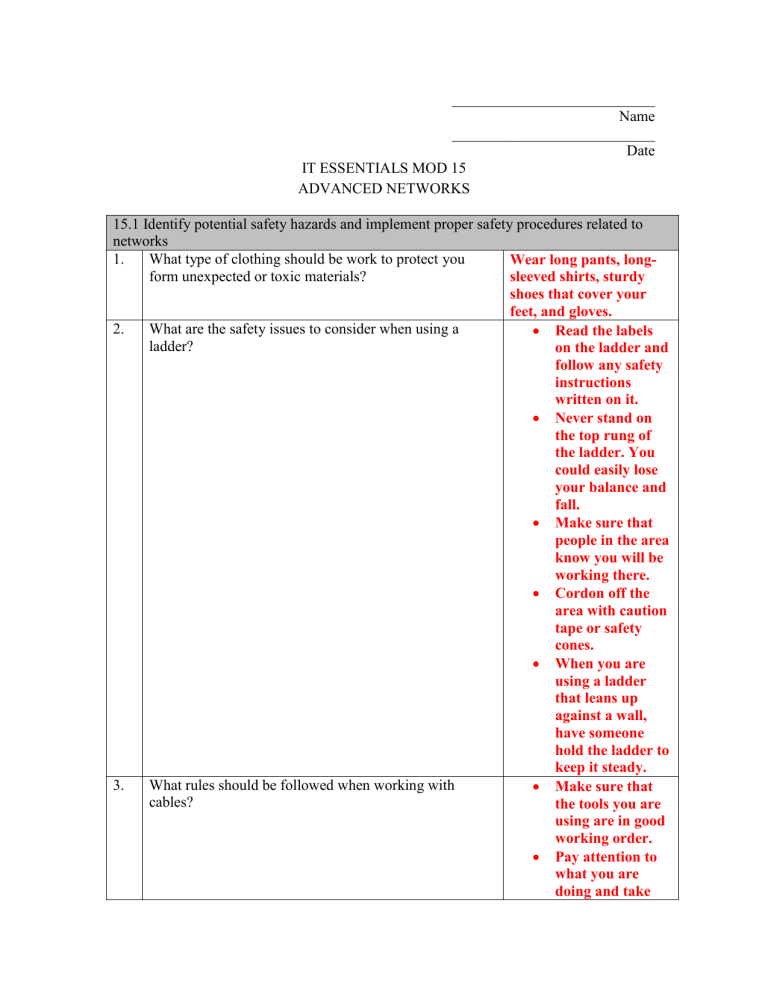
15.1 Identify potential safety hazards and implement proper safety procedures related to networks
1. What type of clothing should be work to protect you form unexpected or toxic materials?
2. What are the safety issues to consider when using a ladder?
Wear long pants, longsleeved shirts, sturdy shoes that cover your feet, and gloves.
Read the labels on the ladder and follow any safety instructions written on it.
Never stand on the top rung of the ladder. You could easily lose your balance and fall.
Make sure that people in the area know you will be working there.
Cordon off the area with caution
3. What rules should be followed when working with cables? tape or safety cones.
When you are using a ladder that leans up against a wall, have someone hold the ladder to keep it steady.
Make sure that the tools you are using are in good working order.
Pay attention to what you are doing and take
your time. Make sure that you do not cut yourself or place anyone in danger.
Always wear safety glasses when cutting, stripping, or splicing cables of any kind. Tiny fragments can injure your eyes.
Wear gloves whenever possible and make sure to dispose of any waste.
15.1.1 Explain fiber-optic safety
4. What kind of hazards are associated with fiber optics? Chemicals and Glass
Splinters
5. How should you pick up fiber-optic fragments? Use tape to pick up small fragments and dispose of them properly
15.1.2 Explain cable, cable cutters, and cable cutting safety hazards
6. Why should you always wear safety goggles when working with cable?
Because the small copper strands can puncture your skin or cut you
15.2 Design a network based on a customer’s needs
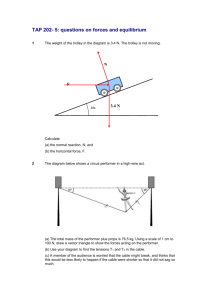
7. What kind of network works best?
15.2.1 Determine a topology
8. What issues should be discussed with the customer?
Topology
9.
10.
What is a site survey?
What is a logical topology?
Cable and wireless types
Expandability
Number and location of users
A physical and logical topology of the network
Actual method by which different computers and other equipment in a network communicate with one another
11. What determines the initial physical and logical topology of the network?
Numbers of users and the estimated amount of future growth
12. What factors should be considered when planning the layout of the network?
13. Identify the following network topologies:
A floor pan or blueprint
Bus Topology Ring Topology Star
Topology
Extended Star Topology Hierarchical Topology Mesh
Topology
15.2.2 Determine protocols and network applications
14. Which suite of protocols is the dominate standard of TCP/IP internetworking?
15. Which protocol suite was originally employed by
Novell?
16. Which protocol cannot be routed or used by routers to
IPX/SPX talk to each other?
NetBEUI
17. Which protocol governs how files such as text, graphics, sound and video are exchanged on the world wide web?
HTTP
18. Which protocol is used to securely connect to a remote computer?
SSH
19. Which protocol is used to send e-mail to a remote eemail server?
20. What protocol is associated with each of the following ports?
80
443
25
23/22
20/21
53
67
21. Which protocol automates assignment of IP addresses on a network?
22. Which protocol translates URLs to IP addresses?
SMTP
HTTP
HTTPS
SMTP
Telnet/SSH
FTP
DNS
DHCP
DHCP
DNS
Protocol Worksheet
15.3 Determine the components for your customer’s network
23. What determines the type of device, cables, and network interfaces that will be required to construct the network?
The choice of network topology
15.3.1 Select cable types
24. What cable type should be selected?
25. What determines the type of network cable that will be used?
26. What is the most common type of cable used in a network?
27. What is the most recent type of twisted-pair cable?
28. What is the distance limitation of UTP cabling?
29. Which type of network is more secure?
15.3.2 Select ISP Connection Type
30. What are the three main considerations for an Internet connection?
The cable type that is the most beneficial and cost effective for users and services that will connect to the network
The size of the network
Cat5e
Cat6A
330 feet (100m)
A wire network
31 What service offers faster connection time and faster speed than dial-up and allows multiple devices to share a single telephone line?
32. What are the limitations of DSL?
Speed
Reliability
Availability
ISDN
Service is not available everywhere
Works better and faster the closer the installation is to the telephone provider’s
Central
Office(CO).Fa
ster when receiving data over the internet than sending it
The lines that are in place to
Satellite carry telephone signals do not technically qualify to carry DSL signals
33. What is considered an “always on” technology?
Worksheet – ISP Connections
15.3.3 Select Network Cards
34. Are Ethernet NICs backward compatible?
35. How do you select wireless NICs?
15.3.4 Select the Network Device
36. Why do you use a hub?
37. What is one advantage of a hub?
38. What determines the maximum speed of the network?
39. Does a switch segment network traffic?
40.
41.
What is contained in a switching table?
What do routers do?
Network Devices Activity – Figure 2
15.4 Implement the customer’s network
42. What is on the installation checklist?
If you have a
10/100 Mbps NIC and a hub that is only 10 Mbps, the
NIC will operate at 10 Mbps
If you have a
10/100/1000
Mbps NIC and a switch that is only operating at 100
Mbps, the NIC will operate at
100 Mbps
You should select wireless NIC’s based on the type of wireless network that is installed.
To share data between multiple devices on a section of the network
It regenerates the data that passes through it
Switches
Yes, it switches filter and segment network traffic by sending data only to the device to which it is sent
Switches
Connect networks together
All the parts are
15.4.1 Install and test the customer’s network
43. What is the process for physically creating a network? available at the site
The installation is scheduled
The customer’s data backups are current and available
You have access to needed passwords
You have extra supplies
Install the components
Test the components
To install the cable in ceilings and behind walls, you perform a cable pull. One person pulls the cable, and another feeds the cable through the walls. Make sure to label the ends of every cable.
Follow a labeling scheme that is already in place, or follow the guidelines outlined in
TIA/EIA 606-A
After the cables have been terminated at both ends, use a cable tester to make sure that there are no shorts or interference.
Make sure that the network interfaces are properly installed in the desktops, laptops, and network printers.
After the network interfaces have been installed, configure the client software and the IP address information on all of the devices.
Install switches and routers in a secured, centralized location. All of the LAN connections terminate in this area. In a home network, you may need to install these devices in separate locations, or you may have only one device.
Install an
Ethernet patch cable from the wall connection to each network device. Check to see if you have a link light on all network interfaces and on each network device port that connects to a device.
When all devices are connected and all link lights are functioning, test the network for connectivity.
Use the ipconfig
/all command to view the IP configuration on each workstation.
Use the ping command to test basic connectivity. You should be able to ping other computers on the network, including the default gateway and remote computers. After you have confirmed basic connectivity, you must configure and test network applications, such as e-mail and an
Internet browser.
44. What command will allow you to view the IP configuration on each workstation?
45. What command do you use to test basic connectivity?
15.4.2 Configure the customer’s Internet and network resources
46. Why are temporary Internet files stored on your computer? ipconfig /all ping
Because when the browser can load content faster the next time you visit the same website
Read 47. Which permission allows the user to view the file and subfolder names, navigate to subfolders, view data in files and run program files?
48. What permission allows you to change permission in the file or folder and take ownership of the file or folder?
49. What is the maximum of simultaneous file-sharing
Change
10
connection in Windows XP?
Lab – Browser Configuration
Lab – Network Resource Sharing
15.5 – Upgrade the customer’s network
15.5.1 – Install and Configure Wireless NIC
50. What must your computer have to connect to a wireless network?
Lab – Wireless NIC Installation
15.5.2 Install and Configure Wireless Router
51. Where is the best place for a wireless access point?
Wireless adapter
At the center of the area you are covering, with line of sight between the wireless devices and the access point.
192.168.1.1 52. What is the default address for router configuration and management?
53. What is the default password for router configuration and management?
Lab – Wireless Router Installation
15.5.3 Test Connection
54. What is the easiest way to test for an Internet connection? admin
55.
56.
What are packets?
What is the difference between a static address and a dynamic address?
Open a web browser and see if the Internet is available.
The communication between the computer and the network device
Static address assigns manually and dynamic address assign automatically. ipconfig 57. What command line tool is used to verify that the connection has a valid IP address?
58. What command line tool is used to test connectivity between devices? ping
59. How do you know if your adapter is working properly? Test network by using ping
60. What command line tool traces the route that packets take from your computer to a destination address?
Lab – Wireless NIC connection test
Tracert
15.6 Describe installation, configuration and management of a simple mail server
61. What are the two protocols associated with email? POP(Post Office
Protocol)
IMAP(Internet Message
Access Protocol)
62. What is SMTP?
63. What port does SMTP use?
64. What port does POP use?
65.
66.
67.
68.
69.
70.
71.
What port does IMAP use?
What are the characteristics of SMTP?
What is an e-mail server?
What is an active directory server?
What is native mode?
What should you do before installing Exchange?
What is IIS (Internet Information Services)?
15.7 Describe preventive maintenance procedures for networks
72. What type of preventive maintenance should you do? Develop a plan to perform scheduled maintenance and cleaning at regular intervals
15.8 Troubleshoot the network
Simple Mail Transfer
Protocol – sends e-mail client to an e-mail server, or from one email server to another
25
110
143
Simple, textbased protocol
Sent over TCP using port 25
Must be implemented to send e-mail
Message is sent after recipients are identified are verified
A computer that can send and receive e-mail on behalf of e-mail clients.
A computer that hosts a database that allows centralized administration over an enterprise network
Exchange must be installed on a domain where every computer runs at least Windows
2000.
Test the environment
A server that has programs used for building and administering website services
73.. What is the first step to troubleshooting a network problem?
74. What are the six steps in the troubleshooting process?
Identify the problem
Identify the
Problem
Establish a theory of Probable
Causes
Determine an
Exact Cause
Implement a
Solution
Verify Solution and Full System
Functionality
Document findings
15.8.1 – Review the Troubleshooting process
75. What are the obvious issues you should verify? Solution and full system functionality.
Document Findings 76. What steps are required to close with the customer?
15.8.2 Identify common problems and solutions
77. If you are experiencing an unreliable network printer, what is a possible solution?
78. What is one possible solution if your network has become slow as more users are added—all users connect to a 24-port hub?
Check your router, restart the router and reconfigure the router.
Increase the maximum number of simultaneous
FTP users on the FTP server.
15.8.3 Apply troubleshooting skills
Lab – Network Problems
Lab – Remote Technician Network Problems