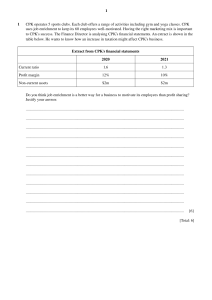
Introduction the CPK

Introduction the CPK
► Ad Hoc Networks Security Mechanism Based on CPK
► International Conference on Computational Intelligence and Security Workshops, 15-19 Dec. 2007 Page(s):522 - 525
► Lei Feng-Yu; Cui Guo-Hua; Liao Xiao-Ding
► A New Key Management and Authentication Method for WSN Based on CPK
► 08. ISECS International Colloquium on Computing, Communication, Control, and Management, Volume 2, 3-4 Aug. 2008
Page(s):486 - 490
► Li, Jingjing; Tan, Le; Long, Dongyang
97/09/15 H.-H. Ou
CPK
CPK (Combined Public Key)
A bounded Identity based encryption based on ECC integrates the public key technique with identity-based technique and uses the user’s identity to generate public key.
Patented
Publication Number WO/2006/074611
NAN, Xiang-Hao and CHEN, Zhong
Originally described as ECC based system, but equally valid in discrete log.
2 H.-H. Ou 2008/09/15
CPK Technique based on ECC (1/2)
Assuming that an Elliptic Curve over a prime field satisfies the equation E: y2 = (x3 + ax + b)mod p
Parameters T = {a, b, G, n, p} , where a, b ∈ F p are the coefficients of the elliptic curve equation, which satisfies 4a 3 + 27b 2 ≠ 0 ,
G= (x
G
, y
G
) is the base point of the Elliptic Curve E(F p
) , n is the order of G and p is a prime number which is the order of prime field F p
.
The private key is an integer r and the corresponding public key is rG , denoted as (x r
, y r
) , which is a point on E(F p
) .
The matrix size of both SSK (Secret Seed Key Matrix) and PSK (Public Seed
Key Matrix) = (m × h).
SSK is an integer matrix (r ij
) where r ij is random chosen integer in F p
.
PSK is composed of corresponding points (r ij
G) = (x ij
, y ij
) on E(F p
).
3 H.-H. Ou 2008/09/15
CPK Technique based on ECC (2/2)
h(ID) = m
1
, m
2
, m
3
…, m h m
1
, m
2
, m
3
…, m h as row numbers
SK = (r m11
+ r m22
+ …+ r mhh
) mod n
PK = ( (x m11
, y m11
)+(x m22
, y m22
)+…+(x mhh
, y mhh
) ) mod p = (r m11
+ r m22
+ …+ r mhh
)G
Ex: h(ID)= 1325, SK= (r m11
(x m32
, y m32
)+(x m45
, y m45
+ r m23
+ r m32
+ r m45
) mod n, ( (x m11
, y m11
) ) mod p
)+(x m23
, y m23
)+
4 H.-H. Ou 2008/09/15
Applications
CPK can achieve security authentication similarly to PKI but does not need fixed infrastructure.
5 H.-H. Ou 2008/09/15
Comments
It is a good idea on the situation of mobile computing.
The restriction of storage space with the PSK on the mobile node.
How do establish a related PSK? End-users can reconstruct by oneself from a seed.
6 H.-H. Ou 2008/09/15
Our propose
Key pool scheme
Server have a key pool and keep its secret.
Client’s secret key is composed with the some sub-key that his ID mapping to the key pool.
ID
254
‘s secret key g a12+a25+a24 mod p
Advances
Like the password table but a reduction on the key size.
a a
.
11
21 a a
.
12
21 a a m 1 m 2
...
...
.
...
a a a
.
1 n
2 n mn
7 H.-H. Ou 2008/09/15