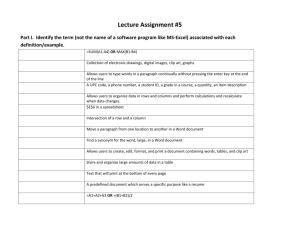
SEC307
Internet Security Best
Practices: 20 Tips
Jesper M. Johansson, Ph.D.
Security Program Manager
Security Business Unit
Microsoft Corporation
jesperjo@microsoft.com
Why?
The world is full of guidebooks, best
practices, prescriptive architectures…
We want to add to the collection!
Information overload, anyone?
Specific recommendations derived from
our participation in OpenHack 4
Stuff you can use today
OpenHack 4
eWeek Magazine's annual contest
This year—
Application-level security focus
Goal: modify information in database
82,500 attempted attacks over 2 ½ weeks
Microsoft entry wasn’t compromised
Reasonably skilled administrators and
developers can build Windows environments
that are secure and resilient against attack
Architecture
router
Administrator
IIS
SQL
RRAS
TS
Application details
Built similar to eWeek’s eXcellence Awards web
site
User sets up account
Enters a product or service for judging
Submits a credit card number to pay entry fee
Read information about award
Used .NET Framework
ASP.NET
ADO.NET
Cryptography class libraries
Our
20 tips
System
components
26
3 Windows 2000 AS
7 IIS 5.0
6 SQL Server 2000
4 Web application
2 IPSec policies
3 Remote management and monitoring
1 Passwords
Keep this in mind: we used no firewalls!
Windows 2000
Advanced Server
Windows 2000 AS
Updated service packs and security
patches
Disable unused OS services
Various registry-based tightening
Updated software
As critical as it’s always been and always
will be
Methods
Windows Update
Software Update Services
Systems Management Server with Software
Update Services Feature Pack
Unused services
Baseline template disables these:
Alerter
Appmgmt
Bits
Browser
Clipsrv
Dfs
Dhcp
Fax
Ismserv
Kdc
Messenger
Mnmsrvc
Msdtc
Netdde
Netddedsdm
Ntfrs
Rasauto
Rasman
Remoteregistry
Sharedaccess
Spooler
Tapisrv
Tlntsvr
Trksvr
Trkwks
Utilman
Winmgmt
Wmi
Wuauserv
Unused services
SQL Server
Lanmanserver—manual
Sqlserveragent—disabled
Terminal server
Lmhosts—disabled
Web server
Lanmanserver—disabled
VPN server
Rasauto, Rasauto, Lmhosts, Tapisrv,
Remoteregistry—automatic
Reg tweaks—NoLMHash
HKLM\System\CurrentControlSet\
Control\LSA
Prevents Windows from storing LM hash
format passwords
Susceptible to decryption
Key in Windows 2000; value in Windows
XP and Server 2003
NoDefaultExempt
HKLM\System\CurrentControlSet\
Services\IPSec
IPSec normally exempts Kerberos traffic
from policy engine
Change default so that no traffic is allowed
from source port 88
See IPSec section for more details
DisableIPSourceRouting
HKLM\System\CurrentControlSet\
Services\Tcpip\Parameters
Prevents an application from specifying a
route in an IP packet
Enforces use of computer’s default gateway
Eliminates certain man-in-the-middle
attacks
SynAttackProtect
HKLM\System\CurrentControlSet\
Services\Tcpip\Parameters
Limits system resources allocated to
incoming requests
Prevents certain SYN-flood attacks and
denials of service
Internet Information
Services 5.0
IIS 5.0
Updated service packs and security patches
Moved default web site
Ran IISLockDown tool
Installed and updated .NET Framework
Remapped extensions
Configured account privileges and permissions
Installed URLScan
Added ACLs to application folder and logs
Default web site location
Move out of %systemdrive%\inetpub
Put in different folder on different volume
Attacker needs to see directory tree now
Can’t access the system drive with ..\
IISLockDown
Use static web server template
No need for dynamic content types in this app
Will modify in a bit
Get it now:
http://microsoft.com/technet/securit
y/tools/tools/locktool.asp
.NET Framework
Redistributable:
http://msdn.microsoft.com/downloads/sample.asp?url=
/msdn-files/027/001/829/msdncompositedoc.xml
Service pack 2:
http://msdn.microsoft.com/netframework/downloads/up
dates/sp/default.asp
Latest hotfix (cred strengthening):
http://support.microsoft.com/default.aspx?scid=kb;e
n-us;Q329250
MDAC 2.7:
http://www.microsoft.com/data/download.htm
Remove extension mappings
Need only .aspx and a few static content
types
Remap other application extensions to
404.dll extension
Included with IISLockDown
Account privs and perms
Use default local ASPNET service account
Created during Framework installation
Placed in Users local group
Also receives—
temporary ASP.NET folder: full
%windir%\temp: full
Framework installation folder: read
Account privs and perms
Add this account to local Web
application group created by
IISLockDown
This group can’t run executables
Update group’s perms to run the C# compiler
and resource converter
URLScan
Part of IISLockDown
Parser examines URL before passing it to
IIS
Configuration—
Allow only the app’s extensions
Block long requests
More details:
http://www.microsoft.com/technet/sec
urity/tools/tools/urlscan.asp
Folder and log ACLs
Web content folders—
ASP.NET worker process: read
Anonymous: read-only on served content
Log folders—
System account and Administrators group
only
All others: deny
IIS and URLScan logs
demo
IISLockDown
URLScan
SQL Server 2000
SQL Server 2000
It’s all about reducing the “surface area”
exposed to attackers
Installed software
Authentication
Service account
Communications protocols
Recovery actions
Application permissions
Installed software
Service pack 3
Omit—
Upgrade tools
Debug symbols
Replication support
Books online
Development tools
Disable—
Msdtc
SQL Server agent
Microsoft search
Authentication
Modified local security policy to allow
NTLMv2 only
Configure for Windows only
No need to store SA ID/password on web
server
Set huge SA password
In case someone “accidentally” changes authN
Authentication
Set audit level to “Failure”
Good evidence of attempted attack forensics
But if attacker did figure out password, how
would you know…?
Maybe should audit success and failure
Service account
Default is LocalSystem
Has too many permissions!
Create local user account for SQL service
Strong password
User can’t change
No TS access
Or can use domain user account if network
access is necessary
A couple others
Communications protocol
In server network utility: hide SQL Server from
client broadcasts
Remove named pipes protocol (need TCP/IP
only)
Recovery actions
Set to “restart the service”
In service properties page
More of a reliability thing…
Application permissions
Delete sample Northwind and Pubs
databases
Create application database
Grant app account permissions on stored
procedures but not on the tables themselves
Prevents execution of ad hoc SQL queries
Ensure this account has no permissions
anywhere else in SQL Server
Web application security
Forms authentication
POST user name and password over SSL
Use encrypted cookie to keep logon
session
Unauthenticated users can access home
page (and a couple others)
Requests to secure pages get redirected to
logon page
Page protection
Request forms authN with 3 lines of code
<system.web> section of Web.config file in
application’s root folder
Applies to all pages in application
Protect certain pages in subfolder with a little
more code
Add another Web.config here
Inherits authN info from top-level file
Denies access to unauthenticated users
Request authN
<authentication mode="Forms">
<forms loginUrl="Login.aspx"
name="OPSAMPLEAPP"/>
</authentication>
Wrapper for required authN
<?xml version="1.0" encoding="utf-8"
?>
<configuration>
<system.web>
<authorization>
<deny users="?" />
</authorization>
</system.web>
</configuration>
Account creation and login
New account
Encrypt password with 3DES
Store in database with user name
Login to existing account
Encrypt password with 3DES
Compare with encrypted password in database
Create cookie and send to user
System.Web.Security.FormsAuthentication
class
Input validation
You can’t trust any input!
Ensure user input doesn’t change
application’s behavior
Helps guard against—
Buffer overruns
Cross-site scripting
Malicious code execution
Four checks
Assume one or more could be circumvented
Input validation
Four checks
Validate all field input
Validate query string portion of URL
Use stored procedures with type-checked
parameters
HTML-encode all data sent to users
1: Validate all field input
Two ASP.NET classes
RegularExpressionValidator
RequiredFieldValidator
Limited input characters to space,
apostrophe, comma, period, letters,
numbers
Other characters blocked
Just like a firewall ruleset
Commonly used to upload malicious code
2: Validate query part of URL
Parse URL query string
System.Text.RegularExpressions.Regex
Validate input with regular expression
Allow numbers only
Regex isNumber = new Regex("^[0-9]+$");
if(isNumber.Match(inputData) ) {
// use it
}
else {
// discard it
}
3: Stored procedures only
Use stored procedures for data access
Limits app’s interaction with database
Strongly-typed and type-checked parameters
Allowing web app to dynamically build
queries is baaaaad!
Whacked web server arbitrary code injection
SQL injection (C#)
string Status = "No";
string sqlstring ="";
try {
SqlConnection sql= new SqlConnection(
@"data source=localhost;" +
"user id=sa;password=password;");
sql.Open();
sqlstring="SELECT HasShipped" +
" FROM detail WHERE ID='" + Id + "'";
SqlCommand cmd = new SqlCommand(sqlstring,sql);
if ((int)cmd.ExecuteScalar() != 0)
Status = "Yes";
} catch (SqlException se) {
Status = sqlstring + " failed\n\r";
foreach (SqlError e in se.Errors) {
Status += e.Message + "\n\r";
}
} catch (Exception e) {
Status = e.ToString();
}
Why string concat is wrong
Good guy
ID: 1001
SELECT HasShipped
FROM detail
WHERE ID=‘1001'
Not so good guy
ID: 1001' or 1=1 -SELECT HasShipped
FROM detail
WHERE ID=‘1001' or 1=1 -- '
Why string concat is wrong
Really bad guy
ID: 1001’ drop table orders -SELECT HasShipped
FROM detail
WHERE ID= ‘1001' drop table orders -- '
Downright evil guy
ID: 1001’ exec xp_cmdshell(‘fdisk.exe’) -SELECT HasShipped
FROM detail
WHERE ID= ‘1001' exec xp_cmdshell(‘fdisk.exe’)--'
4: HTML-encode output
HTML encode all data sent back to user
HtmlEncode method in System.Web.HttpServerUtility
class
Prevents cross-site scripting attacks
Compromise database enter script in records
return to user execute in browser
Script commands translated to harmless text
SomeLabel.Text =
Server.HtmlEncode(username);
Storing secrets
Need to protect two kinds here
Database connection/login string
User password and credit card information
Use different approaches for each
Connection string
Web app needs to authenticate to database
Typical: store ID/password in code
Holy grail for an attacker
You don’t have any “SA/password” in your
code, do you?
Connection string
Use integrated Windows authN
String contains only server location and DB
name
Stored in “code-behind” file—core app logic
Not user interface definition files
Still not enough
Attacker on physical machine could read file
So…
Connection string
Encrypt string using data protection API
(DPAPI) functions
CryptProtectData and
CryptUnprotectData
Encrypts secrets without having to manage or
store keys
Store string in registry and ACL the key
Administrators
ASPNET worker process
User info
DPAPI is less useful here
Keys based on local machine information
Each web server in the farm would have its
own key; can’t access shared info this way
User info
Generate 3DES encryption key and
initialization vector
TripleDES class in
System.Security.Cryptography
Symmetrically encrypt password and
credit card number stored in DB
Salt: cryptographically strong random first
block
Encrypt key and IV with DPAPI and store
in ACLed registry on each web server
Remote management
and monitoring
Remote management
An OH requirement is to show it’s possible
to update the app during the contest
Our solution:
L2TP+IPSec remote-access VPN
Terminal Services
Restricted file shares
L2TP+IPSec VPNs
L2TP is the tunnel; IPSec encrypts it
Remote administrator needs—
Computer certificate trusted by RRAS server
Remote access account credentials
Achieve trusted computer and user
Computer certificate is non-exportable
We know where the user is coming from
User account to log on to RRAS (and TS)
We know who the user is
Terminal Services
Individual accounts on each computer (no
domain here)
Password strength described later
TS access limited to OHTS computer only
Carried over the VPN
Although TS traffic is already encrypted
From OHTS can connect to TS on other
computers
“Nesting” TS works just fine
File shares
“inbox” share
To drop off changed site content
Write-only
“outbox” share
To retrieve files for analysis
Read-only
IPsec policies
IPsec policy requirements
router
Permit 443
Administrator
L2TP+IPsec
IIS
RRAS
SHA1 2443
SQL
SHA1/3DES 445, 3389
TS
Permit 445, 3389
Protection
Use digital certificates for authentication
Standalone CA taken offline after machine
enrollment
Signed (SHA-1)
Between all computers; enforces machine-tomachine authentication
Protects integrity
Encrypted (3DES)
To/from management server
Protects confidentiality of internal traffic if frontend were compromised
Policy properties
Initial config on all servers
Block all IP and all ICMP traffic
Web server SQL Server
“Authenticate and sign” action: IPsec AH
Mgmt server everything
“AuthN, sign, encrypt” action: IPsec ESP+AH
Internet web servers
Permit
Passwords
Passwords
Do we even need to mention this?
Include characters from at least three—
Lowercase alphabet
Uppercase alphabet
Numbers
Non-alphanumerics
The super-paranoid should use all four plus
ALT+???? symbols
Go for length
Next Steps
Every deployment is unique, but certain
principles apply everywhere
Use, adapt, modify as necessary
Need to state the obvious here (after all,
this is a PowerPoint presentation…)
The obvious
Plan for security in the original design
Always install latest service packs and patches (design
should include plan for this)
Always use complex non-intuitive passwords
Reduce surface area by disabling unnecessary
functionality
Adhere to the principle of least privilege
Anticipate failure; practice defense in depth
Always run IISLockDown and URLScan on IIS
Validate all input data
Use only parameterized stored procedures on a database
Community Resources
Newsgroups
microsoft.public.dotnet.framework
microsoft.public.dotnet.security
microsoft.public.win2000.security
microsoft.public.win2000.ras_routing
Ask The Experts
Get Your Questions Answered
Jesper will be at the Ask The Experts area
from 12:30 to 14:30 on July 2
Suggested Reading And Resources
The tools you need to put technology to work!
TITLE
Available
Microsoft Windows 2000 Security
Technical Reference
Today
Writing Secure Code, 2/e
Today
Other Resources
Tools:
Registry Monitor and File Monitor
http://www.sysinternals.com
For technical information:
Security information on Microsoft Produts
http://www.microsoft.com/technet/security
Windows Server 2003
http://www.microsoft.com/windowsserver2003/
Threats and Countermeasures in Windows
Server 2003 and Windows XP
http://go.microsoft.com/fwlink/?LinkId=15160
MBSA
http://www.microsoft.com/technet/security/tools
/Tools/mbsahome.asp
Open Hack IV Hardening
http://msdn.microsoft.com/library/enus/dnnetsec/html/openhack.asp
For training and
certification questions:
Microsoft Training and Certification
http://www.microsoft.com/training
For Security Guidance And Training
Windows 2000 Security Hardening Guide
http://www.microsoft.com/technet/security/pr
odtech/Windows/Win2kHG.asp
Windows Server 2003 Security Guide
http://go.microsoft.com/fwlink/?LinkId=14846
Windows XP Security Guide
http://go.microsoft.com/fwlink/?LinkId=14839
Threats and Countermeasures: Security
Settings in Windows Server 2003 and
Windows XP
http://go.microsoft.com/fwlink/?LinkId=15159
Community Resources
Community Resources
http://www.microsoft.com/communities/default.mspx
Most Valuable Professional (MVP)
http://www.mvp.support.microsoft.com/
Newsgroups
Converse online with Microsoft Newsgroups, including Worldwide
http://www.microsoft.com/communities/newsgroups/default.mspx
User Groups
Meet and learn with your peers
http://www.microsoft.com/communities/usergroups/default.mspx
evaluations
© 2003 Microsoft Corporation. All rights reserved.
This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.