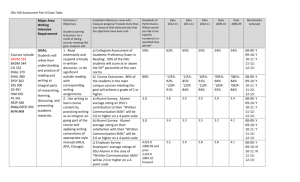
Linux+ Guide to Linux Certification
advertisement

91.580.203 Computer & Network Forensics Xinwen Fu Chapter 1 Computer Forensics and Investigations as a Profession Outline Understand computer forensics Prepare for computer investigations Understand enforcement agency investigations Understand corporate investigations Maintain professional conduct 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 2 Understanding Computer Forensics Computer forensics involves obtaining and analyzing digital information from individual computers for use as evidence in civil, criminal, or administrative cases Network forensics yields information about how a perpetrator or hackers gained access to a network The Fourth Amendment to the U.S. Constitution protects everyone’s rights to be secure in their person, residence, and property from search and seizure What happened in O.J. Simpson’s case? 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 3 Understanding Computer Forensics (continued) When preparing to search for evidence in a criminal case, include the suspect’s computers and its components in the search warrant Computer forensics is a very complicated process; there are legal, political, business and technical factors that will shape every investigation Prison Break - politics 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 4 CSIRT: Computer Security Incident Response Team Manage investigations and conduct forensic analysis of systems Draw on resources from those involved in vulnerability assessment risk management network intrusion detection incident response Resolve or terminate all case investigations 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 5 Components of CSIRT Vulnerability assessment and risk management Computer investigations & network intrusion detection Incident response CSIRT 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 6 Vulnerability Assessment and Risk Management Test and verify the integrity of standalone workstations and network servers Examine physical security of systems and the security of operating systems (OSs) and applications Test for known vulnerabilities of OSs Launch attacks on the network, workstations, and servers to assess vulnerabilities 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 7 Computer Investigations Involves scientifically examining and analyzing data from computer storage media so that the data can be used as evidence in court The evidence can be inculpatory or exculpatory – Duke lacrosse team rape charge Objective is different from that of data recovery or disaster recovery Investigating computers includes: Securely collecting/searching computer data Examining suspect data to determine details such as origin and content Presenting computer-based information to courts Applying laws to computer practice 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 8 Network Intrusion Detection and Incident Response Functions Detect intruder attacks using automated tools and monitoring network firewall logs manually Track, locate, and identify the intruder Deny further access to the network Collect evidence for civil or criminal litigation against the intruders 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 9 Course Outline CSIRT: Computer Security Incident Response Team Incident occurs: Point-in-Time or Ongoing Investigate the incident pre-incident preparation Formulate Detection Initial Response of Response Strategy Incidents 91.580.203 INFA721/CIS418-BIS@DSU Data Data Reporting Collection Analysis Resolution Recovery Dr. Xinwen Fu Implement Security Measures 10 A Brief History of Computer Forensics Mainframe era Well-known crimes ― one-half cent $12.234 PC era By the early 1990s, specialized tools for computer forensics were available ASR Data created the tool Expert Witness for the Macintosh Recover deleted files and file fragments EnCase by one member of ASR Data FTK (Access Data's Forensic Toolkit) iLook (reading disk images) 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 11 Outline Understand computer forensics Prepare for computer investigations Understand enforcement agency investigations Understand corporate investigations Maintain professional conduct 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 12 Computer Investigations and Forensics Public investigations Target criminal cases Conducted by government agencies Follow the law of search and seizure/enforcement www.usdoj.gov/criminal/cybercrime Private or corporate investigations Target civil cases Conducted by private companies/lawyers Follow private or corporate policies 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 13 Outline Understand computer forensics Prepare for computer investigations Understand enforcement agency investigations Understand corporate investigations Maintain professional conduct 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 14 Understanding Enforcement Agency Investigations Understand local city, county, state, and federal laws on computer-related crimes Until 1993, laws defining computer crimes did not exist States have added specific language to their criminal codes to define crimes that involve computers "Computers and networks are only tools that can be used to commit crimes and are, therefore, no different from the lockpick a burglar uses to break into a house" Possible computer crimes: data theft, child molestation images, drug transaction information on a hard disk 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 15 Legal Process for Computer Crimes A criminal case follows three stages: Complaint Investigation Someone files a complaint A specialist investigates the complaint Prosecution Prosecutor collects evidence and builds a case Complaint 91.580.203 INFA721/CIS418-BIS@DSU Investigation Dr. Xinwen Fu Prosecution 16 Levels of Law Enforcement Expertise for a Police (CTIN) Level 1 (street police officer) Level 2 (detective) Acquiring and seizing digital evidence Managing high-tech investigations Teaching the investigator what to ask for Understanding computer terminology What can and cannot be retrieved from digital evidence Level 3: (computer forensics expert) Specialist training in retrieving digital evidence 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 17 Typical Affidavit of Search Warrant for Seizing Evidence 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 18 Outline Understand computer forensics Prepare for computer investigations Understand enforcement agency investigations Understand corporate investigations Maintain professional conduct 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 19 Understanding Corporate Investigations Business must continue with minimal interruption from your investigation Investigation is secondary to stopping the violation and minimizing the damage or loss to the business Can Microsoft shutdown their servers for forensics purposes? 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 20 Establishing Company Policies Company policies are built in order to avoid litigation Without defined policies, a business risks exposing itself to litigation by current or former employees Policies provide: Rules for using company computers and networks 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 21 Displaying Policy Warning Banners Avoid litigation displaying a warning banner on computer screens A banner: Informs users that the organization can inspect computer systems and network traffic at will Voids right of privacy Establishes authority to conduct an investigation 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 22 Displaying Warning Banners (continued) 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 23 Displaying Warning Banners (continued) Types of warning banners: For internal employee access (intranet Web page access) External visitor accesses (Internet Web page access) 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 24 Displaying Warning Banners (continued) Examples of warning banners: Access to this system and network is restricted Use of this system and network is for official business only Systems and networks are subject to monitoring at any time by the owner Using this system implies consent to monitoring by the owner Unauthorized or illegal users of this system or network will be subject to discipline or prosecution 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 25 Banner Example in Reality Recall: why do we need policies and warning banners? Courts have ruled that company-owned equipment does not contain any “personal information” Without them, your authority to inspect might conflict with the user's expectation of privacy, and a court might have to determine the issue of authority to inspect 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 26 Mercury.cs.uml.edu Banner 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 27 Texas A&M CS Department Banner 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 28 SSHD Banner By default sshd server turns off this feature Login as root user; then create your login banner file 91.580.203 Edit /etc/ssh/sshd-banner Edit /etc/sshd/sshd_config and add Banner /etc/ssh/sshd-banner Save file and restart the sshd server /etc/init.d/sshd restart Dr. Xinwen Fu 29 INFA721/CIS418-BIS@DSU http://www.cyberciti.biz/tips/how-to-force-sshd-server-to-display-login-banner-before-login-change-the-ssh-server-sshd-login-banner.html Linux Console Login Banner File /etc/issue, default information 1. Fedora Core release 3 (Heidelberg) 2. Kernel \r on an \m \r – OS release such as “Kernel 2.6.17” \m – Machine such as “i686” 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 30 Windows XP Logon Warning Message 1. Click Start/Control Panel 2. Double-click Administrative Tools / Local Security Policies / Security Options 3. Set Interactive Logon: Message text for users attempting to log on 4. Set Interactive Logon: Message title for users attempting to log on 5. Logoff/Logon to test 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu http://www.ciac.org/ciac/bulletins/j-043.shtml 31 http://www.windowsnetworking.com/kbase/WindowsTips/Windows2000/RegistryTips/Miscellaneous/LogonBanner-DisplayingWarningMessage.html Designating an Authorized Requester Not everyone should be an investigator Establish a line of authority Specify an authorized requester who has the power to conduct investigations Groups who can request investigations: Corporate Security Investigations Corporate Ethics Office Corporate Equal Employment Opportunity Office Internal Auditing The general counsel or legal department 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 32 Conducting Security Investigations Public investigations search for evidence to support criminal allegations Private investigations search for evidence to support allegations of abuse of a company’s assets and criminal complaints Abuse or misuse of corporate assets E-mail abuse/Malicious e-mail Excessive private Internet abuse Employee company startup Porn site 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 33 Employee Abuse of Computer Privilege 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 34 Distinguishing Personal and Company Property PDAs and personal notebook computers Employee hooks up his PDA device to his company computer Company gives PDA to employee as bonus What is your opinion of company policies on those items? 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 35 Outline Understand computer forensics Prepare for computer investigations Understand enforcement agency investigations Understand corporate investigations Maintain professional conduct 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 36 Maintaining Professional Conduct Professional conduct determines credibility Ethics Morals Standards of behavior Conduct with integrity Maintain objectivity and confidentiality Enrich technical knowledge 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 37 Maintaining Objectivity Sustain unbiased opinions of your cases Avoid making conclusions about the findings until all reasonable leads have been exhausted you considered all the available facts Ignore external biases to maintain the integrity of the fact-finding in all investigations 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 38 Keep the Case Confidential Until you are designated as a witness or required to release a report at the direction of the attorney or court 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 39 Enrich Technical Knowledge Stay current with the latest technical changes in computer hardware and software, networking, and forensic tools Learn about the latest investigation techniques that can be applied to the case Record fact-finding methods in a journal Include dates and important details that serve as memory triggers Develop a routine of regularly reviewing the journal to keep past achievements fresh 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 40 Enrich Technical Knowledge (continued) Attend workshops, conferences, and vendor-specific courses conducted by software manufacturers Monitor the latest book releases and read as much as possible about computer investigations and forensics Computer Technology Investigators Northwest (CTIN) High Technology Crime Investigation Association (HTCIA) LISTSERV or Majordomo: mailing lists Certificate: EC-Council - CHFI Computer Hacking Forensic Investigator 91.580.203 INFA721/CIS418-BIS@DSU Dr. Xinwen Fu 41