AIC
advertisement

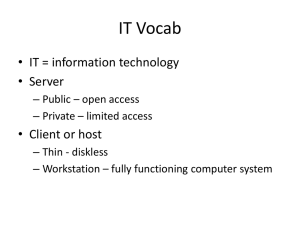
IT Vocab • IT = information technology • Server – Public – open access – Private – limited access • Client or host – Thin - diskless – Workstation – fully functioning computer system IT Vocab • A computing system : a configuration of one or more computers along with the software and data. Tenets of IT Security CS5493 AIC • Availability - assets are available in a timely manner. • Integrity – assets remain in their expected states. • Confidentiality - assets have access controls What are assets? • An asset is something of value: – Hardware – Software – Data – Employees – Equipment – Etc. AIC and Threat Categories • Denial or destruction threats • Alteration threats • Improper disclosure threats The Domains of IT Infrastructure 1. 2. 3. 4. 5. 6. 7. User domain Workstation domain LAN domain LAN-to-WAN domain WAN domain Remote Access domain Server (System)/Application domain Domain Breakdown • The IT infrastructure is broken into different domains so security policy can be organized effectively. IT Domain Security Policy • A comprehensive security plan can be devised by considering each separate domain. • Identify the threats and vulnerabilities • Devise a strategy for eliminating the vulnerabilities. Vulnerabilities Examples: • User – lack of awareness or concern for security policy. • Workstation domain – unauthorized access • LAN – spreading of malicious software • WAN – malicious attacks by anonymous sources • Remote access – Data leakage due to loss or theft of electronic devise • Server/App – Data loss due to software and hardware failures. Domain Threat Targets 1. 2. 3. 4. User – misuse of resources, social engineering Workstation – OS, applications LAN – hubs, cables, supporting software, etc. WAN – routers, firewalls, supporting software, etc. 5. Remote Access – VPN 6. Server Application – e-mail, file services, database, etc.