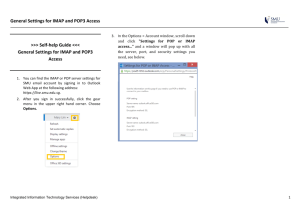
File
advertisement

Email, VoIP and Wired and Wireless Networks By Sam Heighes Definitions • Store and forward is a telecommunications technique in which information is sent to an intermediate station where it is kept and sent at a later time to the final destination or to another intermediate station. • An address book or a name and address book (NAB) is a book or a database used for storing entries called contacts. • An attachment is a file that you want to include with your email message. You can add many attachments to an email message. • Carbon copy (Cc) – enter it here if the email needs to be seen by this person but is not addressed to them. • Blind carbon copy (Bcc) – enter it here to prevent other recipients knowing you’ve sent it to this person. Print screen of an email message Advantages of Emails • It’s quick and easy to use. An email typically arrives seconds after it’s sent. • Unlike letters, a single email can be sent to multiple people at no extra cost. • Emails can have text, images, audio and video in them. • Files can be sent with an email, as attachments. • Emails can be forwarded. This is when you send an email you’ve received on to someone else. • All email providers work together. Regardless of provider, if you have a person’s email address you can send them an email. • It doesn’t cost to send an email. The costs are covered by your internet service provider (ISP) or by advertisements. Disadvantages of email • Because it’s so quick, it’s easy to send an email you might later regret, or to send one to the wrong person entirely. • Emails can be misunderstood. A rushed email may be interpreted as rude by the recipient. Emoticons can help but are best avoided in formal or professional emails. • Email overload - because it’s so easy to send an email it’s possible to receive lots of emails every day, sometimes far too many to deal with. • Spam and junk mail – emails you haven’t asked for and don’t want. A good spam filter will stop most of these from reaching your inbox but sometimes mail that isn’t junk may slip into your junk mail unnoticed. It is always worth checking your junk mail if an email you are expecting doesn’t arrive. • Attachments may contain viruses that can damage your computer. • There is no way of knowing if a recipient received an email unless a read receipt is used. A read receipt is sent to the sender when the recipient opens the email. • It’s rare to receive an instant response to an email as they may be treated as less urgent than a phone call. Simple Mail Transfer Protocol (SMTP) • Simple Mail Transfer Protocol (SMTP) is an Internet standard for electronic mail (e-mail) transmission. First defined by RFC 821 in 1982, it was last updated in 2008 with the Extended SMTP additions by RFC 5321 - which is the protocol in widespread use today. • SMTP by default uses TCP port 25. The protocol for mail submission is the same, but using port 587, and SMTP connections secured by SSL, known as SMTPS, default to port 465. • While electronic mail servers and other mail transfer agents use SMTP to send and receive mail messages, user-level client mail applications typically use SMTP only for sending messages to a mail server for relaying. For receiving messages, client applications usually use either the POP3 or the IMAP. • While proprietary systems (such as Microsoft Exchange and Lotus Notes/Domino) and webmail systems (such as Hotmail, Gmail and Yahoo! Mail) use their own non-standard protocols to access mail box accounts on their own mail servers, all use SMTP when sending or receiving email from outside their own systems. Post Office Protocol • In computing, the Post Office Protocol (POP) is an application-layer Internet standard protocol used by local e-mail clients to retrieve email from a remote server over a TCP/IP connection. POP has been developed through several versions, with version 3 (POP3) being the current standard. • Virtually all modern e-mail clients and servers support POP3, and it along with IMAP (Internet Message Access Protocol) are the two most prevalent Internet standard protocols for e-mail retrieval, with many webmail service providers such as Google Mail, Microsoft Mail and Yahoo! Mail also providing support for either IMAP or POP3 to allow mail to be downloaded. Internet Message Protocol • The Internet Message Access Protocol (commonly known as IMAP) is an Application Layer Internet protocol that allows an e-mail client to access e-mail on a remote mail server. The current version, IMAP version 4 revision 1 (IMAP4rev1), is defined by RFC 3501. An IMAP server typically listens on well-known port 143. IMAP over SSL (IMAPS) is assigned well-known port number 993. • • IMAP supports both on-line and off-line modes of operation. E-mail clients using IMAP generally leave messages on the server until the user explicitly deletes them. This and other characteristics of IMAP operation allow multiple clients to manage the same mailbox. Most e-mail clients support IMAP in addition to Post Office Protocol (POP) to retrieve messages; however, fewer e-mail services support IMAP.[1] IMAP offers access to the mail storage. Clients may store local copies of the messages, but these are considered to be a temporary cache.[2] • • Incoming e-mail messages are sent to an e-mail server that stores messages in the recipient's e-mail box. The user retrieves the messages with an e-mail client that uses one of a number of e-mail retrieval protocols. Some clients and servers preferentially use vendor-specific, proprietary protocols, but most support SMTP for sending e-mail and POP and IMAP for retrieving e-mail, allowing interoperability with other servers and clients. For example, Microsoft's Outlook client uses MAPI, a Microsoft proprietary protocol to communicate with a Microsoft Exchange Server. IBM's Notes client works in a similar fashion when communicating with a Domino server. All of these products also support POP, IMAP, and outgoing SMTP. Support for the Internet standard protocols[citation needed] allows many e-mail clients such as Pegasus Mail or Mozilla Thunderbird to access these servers, and allows the clients to be used with other servers. History of Email • Ray Tomlinson is credited with inventing email in 1972. Like many of the Internet inventors, Tomlinson worked for Bolt Beranek and Newman as an ARPANET contractor. He picked the @ symbol from the computer keyboard to denote sending messages from one computer to another. So then, for anyone using Internet standards, it was simply a matter of nominating name-of-the-user@name-of-the-computer. Internet pioneer Jon Postel, who we will hear more of later, was one of the first users of the new system, and is credited with describing it as a "nice hack". It certainly was, and it has lasted to this day. VoIP acronym • VOIP Voice over Internet Protocol • VOIP Voice over Internet Packet • VOIP Video Over IP (Internet Protocol) Plugin (software) Definition of VoIP • voice messaging technology: a technology that enables voice messages to be sent via the Internet, often simultaneously with data in text or other forms. Software required of Codec • Codecs are utilities that are required to read a digital media file's streams. In order to properly stream a digital media file, a user's computer must be equipped with all the necessary codecs. For instance, it is possible that a digital media file cannot be streamed through a media player although its format is supported by the application. It is also possible that a user can stream a digital media file's audio, but not its video (or vice versa). When this occurs, users should analyze the digital media file with codec information software. In addition to indicating which codecs are required to stream a digital media file, codec information software can also be used to obtain the necessary utilities. Internet Packets • VoIP endpoints usually have to wait for completion of transmission of previous packets, before new data may be sent. Although it is possible to pre-empt (abort) a less important packet in midtransmission, this is not commonly done, especially on high-speed links where transmission times are short even for maximum-sized packets. An alternative to pre-emption on slower links, such as dialup and digital subscriber line (DSL), is to reduce the maximum transmission time by reducing the maximum transmission unit. But every packet must contain protocol headers, so this increases relative header overhead on every link traversed, not just the bottleneck (usually Internet access) link. Hardware need for a VoIP call • Above all else, VoIP is basically a clever "reinvention of the wheel." In this article, we'll explore the principles behind VoIP, its applications and the potential of this emerging technology, which will more than likely one day replace the traditional phone system entirely. • The interesting thing about VoIP is that there is not just one way to place a call. There are three different "flavors" of VoIP service in common use today Type UTP/STP Coaxial Fibre Optic Infrared 14 Tera bits per second 115 Kbit/s Maximum Range 160km 120m Benefits Quick Cheap Limitations Expensive Low Bandwidth Example of how it is used Telephone Exchange Bluetooth Microwave Satellite (high frequency to 50 GHz range, radio signals) Details Maximum Data Transfer Rate 100 Mbps 1 Gbit/s 1cm 6,000km Advantages and Disadvantages of Wireless Network Advantages Disadvantages • Easily integrated into existing wired-Ethernet networks. • Access and accessibility improved. • Backwards compatible as standards improve. • Speed of installation. • Cost Savings. • Disadvantages of Wi-Fi. • Transmission speeds can fluctuate. • Conflict of ‘standards’. • Security LAN and WAN • LAN- A local area network (LAN) is a computer network that user interconnects computers in a limited area such as a home, school, computer laboratory, or office building using network media. • WAN- A wide area network (WAN) is a network that covers a broad area (i.e., any telecommunications network that links across metropolitan, regional, or national boundaries) using private or public network transports.