Section B - Annex A2 - Cisco Reference Example
advertisement
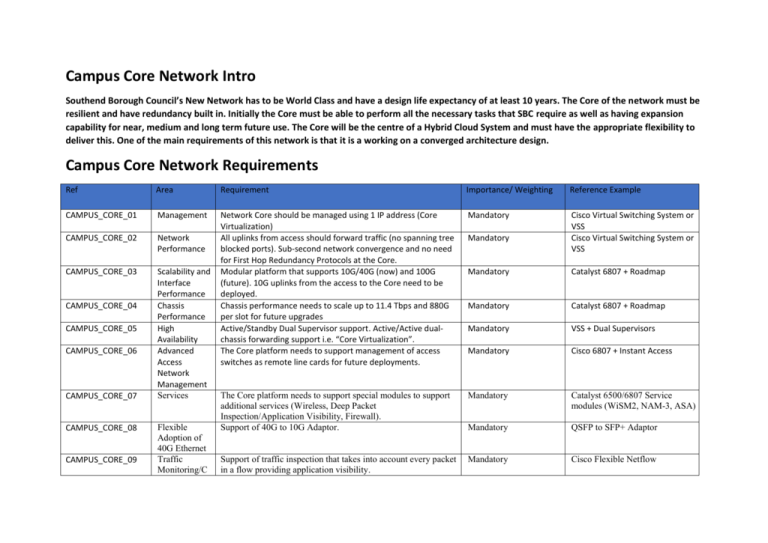
Campus Core Network Intro Southend Borough Council’s New Network has to be World Class and have a design life expectancy of at least 10 years. The Core of the network must be resilient and have redundancy built in. Initially the Core must be able to perform all the necessary tasks that SBC require as well as having expansion capability for near, medium and long term future use. The Core will be the centre of a Hybrid Cloud System and must have the appropriate flexibility to deliver this. One of the main requirements of this network is that it is a working on a converged architecture design. Campus Core Network Requirements Ref Area Requirement Importance/ Weighting Reference Example CAMPUS_CORE_01 Management Mandatory CAMPUS_CORE_02 Network Performance Cisco Virtual Switching System or VSS Cisco Virtual Switching System or VSS CAMPUS_CORE_03 Scalability and Interface Performance Chassis Performance High Availability Advanced Access Network Management Services Network Core should be managed using 1 IP address (Core Virtualization) All uplinks from access should forward traffic (no spanning tree blocked ports). Sub-second network convergence and no need for First Hop Redundancy Protocols at the Core. Modular platform that supports 10G/40G (now) and 100G (future). 10G uplinks from the access to the Core need to be deployed. Chassis performance needs to scale up to 11.4 Tbps and 880G per slot for future upgrades Active/Standby Dual Supervisor support. Active/Active dualchassis forwarding support i.e. “Core Virtualization”. The Core platform needs to support management of access switches as remote line cards for future deployments. CAMPUS_CORE_04 CAMPUS_CORE_05 CAMPUS_CORE_06 CAMPUS_CORE_07 CAMPUS_CORE_08 CAMPUS_CORE_09 Flexible Adoption of 40G Ethernet Traffic Monitoring/C Mandatory Mandatory Catalyst 6807 + Roadmap Mandatory Catalyst 6807 + Roadmap Mandatory VSS + Dual Supervisors Mandatory Cisco 6807 + Instant Access The Core platform needs to support special modules to support additional services (Wireless, Deep Packet Inspection/Application Visibility, Firewall). Support of 40G to 10G Adaptor. Mandatory Catalyst 6500/6807 Service modules (WiSM2, NAM-3, ASA) Mandatory QSFP to SFP+ Adaptor Support of traffic inspection that takes into account every packet in a flow providing application visibility. Mandatory Cisco Flexible Netflow Ref CAMPUS_CORE_10 Area apacity Planning/Visi bility Online Diagnostics Requirement The switch platform proposed should be able to test and verify its hardware functionality while the switch is connected to a live network. Importance/ Weighting Reference Example Mandatory Supervisor 2T Online Diagnostics Campus Access Network (Switching) To ensure that SBC and its staff can function at the required levels the Civic Centre is to have new fibres run to each floor allowing for a minimum of a 10 Megabit backbone across the LAN. The equipment used must allow for current requirements and future expansion such as higher speed to the desktop and Wave II wireless. The switching must not produce any inherent delays in the overall network. The whole network must be manageable as a” single pain of glass” Campus Access Network (Switching) Ref Area Requirement Importance/ Weighting Reference Example ACCESS_SWITCHING_01 Deployme nt Mandatory ACCESS_SWITCHING_02 Interface Downlinks 3850 can mix in the same stack copper and fibre interfaces and different speeds 1G, 2.5G, 5G, 10G 3850 MG and Fibre versions ACCESS_SWITCHING_03 Interface Uplinks Platform proposed should be able to support stacking and allow to mix different types of interfaces within a stack (copper, fibre and different downlink/uplink speeds) 1G downlink copper interfaces required for this deployment. In addition to that the switching family proposed needs to support also fibre downlinks (1G,10G) and 2.5G, 5G copper interfaces (for future mixed stack deployments). These interfaces can be supported by other models of the same switch family, Uplinks should be modular and 2x10G to the Campus Core. Lower and Higher speed uplinks need to be listed for the Mandatory Mandatory 3850 supports 2x10G as well as 4x1G, 4x10G, 2x 40G, 8x 10G Ref ACCESS_SWITCHING_04 ACCESS_SWITCHING_05 ACCESS_SWITCHING_06 ACCESS_SWITCHING_07 ACCESS_SWITCHING_08 ACCESS_SWITCHING_09 ACCESS_SWITCHING_10 Area High Availabilit y (Power) Traffic Monitorin g/Capacity Planning/ Visibility Power Over Ethernet HW Performan ce & OS Wireless Stack Managem ent, High Availabilit y, Convergen ce & Backplane Performan ce Online Diagnostic s Importance/ Weighting Reference Example Mandatory 3850 Stackpower Traffic inspection that takes into account every packet in a flow providing L2-L7 visibility is required. Also native Wireshark support on the switching platform proposed is required for additional traffic inspection and troubleshooting. Mandatory 3850 + Flexible Netflow + Wireshark PoE is required (15W) for the deployment. Support for 30W or 60W PoE is required for the switching family proposed (for future mixed stack deployments). Multicore CPU and Modern/Modular Operating System that supports hosted applications and separate memory allocation for each process. The access platform should support integrated wireless controller function and RFID tag tracking. Application visibility for wireless traffic should be achieved by using Deep Packet Inspection technology in addition to technologies such as Netflow. Plug & Play stack member removals and additions. Very fast stack convergence upon stack main unit failure (few milliseconds). Stack performance in terms of bandwidth needs to be provided and explained. Mandatory 3850 supports PoE, PoE+ and Cisco UPoE Mandatory 3850 IOS XE Modular Operating System Mandatory 3850 Converged Access and Application Visibility with NBAR2 protocol (DPI) Mandatory 3850 Stackwise 480 Mandatory 3850 Online Diagnostics Requirement switching family proposed (for future mixed stack deployments) Redundant Power supply support and power should also be able to be shared across stack members The switch platform proposed should be able to test and verify its hardware functionality while the switch is connected to a live network. Campus Access Network (Wireless) Intro All areas of the Civic Centre must have a coherent wireless solution that can be centrally managed and able to use the latest technology and AC Wave 11 when available. Campus Access Network (Wireless) Requirements Ref Area Requirement Importance/ Weighting Reference Example ACCESS_WIRELESS_01 Deployment Mandatory ACCESS_WIRELESS_02 Controller Performanc e Access Point The solution needs to be controller based on-premise and support 802.11ac standard. The controller needs to support minimum the following specs; 20Gbps throughput full duplex, up to 1500 access points, up to 20,000 clients and 4096 VLANs. Modular Access Point platform to support 802.11ac and 802.11ac Wave 2. Any additional modules supported need to be mentioned and what functionality they support. The controller deployment needs to support high availability and seamless operation upon failure. Mandatory Aironet 5520 Controller or better and 3700 Access point Aironet 5520 Controller or better Mandatory Aironet 3700 Access Point Mandatory 2x 5520 in an HA pair ACCESS_WIRELESS_03 ACCESS_WIRELESS_04 High Availability Sub-second access point and client failover for uninterrupted application availability. Redundant 1 Gigabit Ethernet or 10 Gigabit Ethernet connectivity Solid-state device-based storage - no moving parts. Redundant, hotswappable power supply with no incremental system downtime. Enhanced system uptime with fast system restarts. Ref Area Requirement Importance/ Weighting Reference Example ACCESS_WIRELESS_05 Application visibility for wireless traffic should be using Deep Packet Inspection technology for additional granularity. Support for Mandatory 5520 + NBAR2 protocol (DPI) Hardware Based Wi-Fi interference and Rogue AP/ Denial-ofService detection should be supported. The wireless network needs to be self-healing and self-optimizing. Mandatory Cisco CleanAir Optimized system performance of mixed-client wireless networks offering enhanced downlink throughput and improved uplink communication providing a better user experience during web browsing, email, and file downloads. No additional network parameters needed – should be chipset feature. Mandatory Cisco ClientLink 3.0 feature Able to support robust performance in dense and variable client environments with different applications (unified communications, video, bidirectional traffic). Mandatory Cisco HDX & Video Stream ACCESS_WIRELESS_09 Traffic Monitoring/ Capacity Planning/Vi sibility Interference and Rogue AP protection Mixed client Environmen t Performanc e High Density Environment Performance & High Performance Video Support Analytics Mandatory Cisco CMX ACCESS_WIRELESS_10 ACCESS_WIRELESS_11 Services Management The wireless solution needs to support location analytics and RFID tagging/tracking. Bonjour and Chromecast support. Mandatory Mandatory 5520 WLC Datasheet 5520 WLC GUI & Prime Infrastructure Support ACCESS_WIRELESS_12 Miscellaneo us Features Mandatory 5520 ACCESS_WIRELESS_06 ACCESS_WIRELESS_07 ACCESS_WIRELESS_08 marking, prioritizing, and blocking to conserve network bandwidth and enhance security. Simplified GUI wizard for quick setup and intuitive dashboards for monitoring and troubleshooting. Compatibility with unified wired/wireless network management tools. Support for centralized, distributed, and mesh deployments. Centralized control, management, and client troubleshooting. Seamless client access in the event of a WAN link failure (local data switching). Highly secure guest access. Efficient access point upgrade that optimizes the WAN link utilization for downloading access point images. Ref Area Requirement Importance/ Weighting Reference Example Support for corporate wireless service for mobile and remote workers with secure wired tunnels to indoor access points. Data Centre Network Fabric Southend Borough Council needs a Network Fabric which enables high speed connectivity from the end device to the servers and the cloud Data Centre Network Fabric Requirements Ref Area Requirement Importance/ Weighting Reference Example DATA_CENTE R_NETWORK_ 01 Deployment Mandatory Nexus 9k/ACI DATA_CENTE R_NETWORK_ 02 DATA_CENTE R_NETWORK_ 03 Performance The Network Fabric needs to support 2-Tier Leaf and Spine architecture (low latency, 10G/40G/100G, non-blocking). Scale Up and Out architecture. Minimum interface scalability specs 192x 1/10G BASE-T ports or 572x 10GE fibre ports or 144x 40GE fibre ports or 32x 100GE fibre ports for the Spine Tier. A controller based solution managing the fabric policies, provisioning, monitoring and troubleshooting is required (application centric deployment). The Data Center Spine Tier needs to be a very high performance platform (15Tbps switching capacity full duplex). The Spine Tier switching family proposed needs to scale up to 60 Tbps (future). The Network Fabric should support VXLAN and have a control plane that automates its provisioning. In addition to that it should be able to track VM mobility and changes to the VM configuration (seamless VM mobility within the Network Fabric). Automated Installation of SW Images and Configuration Files needs to be supported. Mandatory Nexus 9504 and Nexus 9500 family Mandatory Nexus 9k VM Tracker + MP-BGP EVPN Mandatory Cisco Nexus 9k Power-On Auto Provisioning DATA_CENTE R_NETWORK_ 04 Network Microsegmentation & VM Mobility Patching/SW Upgrades Ref Area Requirement Importance/ Weighting Reference Example DATA_CENTE R_NETWORK_ 05 Power Efficiency Mandatory Nexus 9k 80 Plus Platinum Power Supply Certification – No mid-plane on Nexus 9500 DATA_CENTE R_NETWORK_ 06 DATA_CENTE R_NETWORK_ 07 DATA_CENTE R_NETWORK_ 08 Flexible Transition from 10G to 40G Mandatory Cisco Bidi Optics Mandatory Nexus 9k/ACI Programmability Mandatory Cisco Nexus 9k NX-OS operating system DATA_CENTE R_NETWORK_ 09 Management The system proposed needs to be power efficient and certified (for example 80 Plus Platinum Certification). The Spine Tier should have a design without a mid-plane to optimize front-to-back airflow and reduce power consumption. Flexible transition from 10G DC Access to 40G DC Access without changing existing 10G cabling i.e. support for 40G interfaces converted to 10G. The Network Fabric should be fully programmable (Open APIs, Python, REST, Chef, Puppet, XMPP). Openstack and Linux Containers need to be supported. Modern and Modular operating system to support MultiCore CPUs, MultiThreading, Process Survavibility, Stateful Failover – the latter for the Spine Tier switching platform. The Switch OS should able to be patched without any interruption in switch operations. Network Fabric/Switch management through remote procedure calls (RPCs), JavaScript Object Notation (JSON), or XML over an HTTP or HTTPS infrastructure. CLI, scripting (Python) and GUI should be supported on any controller which is part of the Network Fabric. Mandatory Cisco Nexus 9k NX-OS operating system DATA_CENTE R _10 High Availability Programmability/Aut omation/Orchestrati on Operating System Very high MTBF that exceeds 1 million hours for the Spine Tier Nexus 9504 has 1 million hours MTBF. Nexus 9k supports BFD, Non-Stop Forwarding switching platform. Bidirectional Forwarding Detection (BFD) and Routing Protocol Stateful Restart. Online diagnostics need to be supported. DATA_CENTE R_NETWORK_ 11 Timestamping and Event Logging DATA_CENTE R_NETWORK_ 12 Control Plane Security Precision Time Protocol (IEEE 1588 Standard) to provide nanosecond accuracy to facilitate precise timestamping for log/event correlation, compliance and digital forensics is required. Nexus 9k Data Broker Nexus 9k Storm Control Protection from L2 broadcast “storms” and control plane policing Ref Area Requirement Importance/ Weighting Reference Example is required. DATA_CENTE R_NETWORK_ 13 DATA_CENTE R _14 DATA_CENTE R_NETWORK_ 016 DATA_CENTE R_NETWORK_ 017 Openflow Openflow 1.3 needs to be supported Nexus 9k Monitoring of traffic flow SLAs Network/Application Provisioning Platform should able to monitoring and evaluate the performance of SLAs (voice, video, data traffic). Data-model-based declarative provisioning using Applicationcentric network policies from a central point/controller. Nexus 9k/NX-OS IP SLA Application Monitoring & Troubleshooting ACI Atomic Counters etc DATA_CENTE R _018 DATA_CENTE R_NETWORK_ 018 DATA_CENTE R_NETWORK_ 019 DATA_CENTE R_NETWORK_ 020 Hypervisor/Virtualiza tion Support L4-L7 Services Embedded Healthscores for applications (latency, packet loss per application/tenant) and ease of correlation when troubleshooting. This should be done from a central point (controller) which also allows fault, event and performance management. The Network Fabric needs to be hypervisor agnostic. Seamless, programmable and automated integration of L4-L7 services into the Network Fabric. ACI Switching platforms should be able to monitor higher-volume and business-critical traffic for efficient use of security, compliance, and application performance monitoring tools. Support for Hardware Based Load Balancing and Traffic Steering is required. Nexus 9k Data Broker Data Broker Switching Hardware Load balancing ACI ACI Nexus 9k Intelligent Traffic Director Data Centre Network Interconnect Requirements Ref Area Requirement Importance/ Weighting Reference Example DATA_CENTER_INT ERCONNECT_01 Deployment Built-in 6x 1GE and 2 X 10 GE SFP based ports. Mandatory ASR 1000 Router DATA_CENTER_ INTERCONNECT _02 DATA_CENTER_ INTERCONNECT _03 DATA_CENTER_ INTERCONNECT _04 Performance Pay as you grow performance 2.5, 5, 10, 20 Gbps. Mandatory ASR 1000 Router Operating System Modern & Modular OS - Expanded container app support support for future virtual applications and services. Mandatory ASR 1000 Router Services High-performance security for crypto, firewall, and Mandatory ASR 1000 Router Mandatory ASR 1000 Router Mandatory ASR 1000 Router Redundant power supply. Network Address Translation (NAT) sessions. VPN services support. DATA_CENTER_ INTERCONNECT _05 DATA_CENTER_ INTERCONNECT _06 Application Visibility Netflow-based and DPI-based traffic inspection (application visibility). Data Center Interconnect Technologies Support for VXLAN, LISP, VPLS and OTV. Data Centre Servers Requirements Ref Area Requirement Importance/ Weighting Reference Example DATA_CENTER _SERVERS_01 DATA_CENTER _SERVERS _02 Deployment Blade Server based architecture for virtualized and non-virtualized environments. Programmable, Automated and Policy based using service templates/profiles via CLI, GUI and XML API – Stateless compute and pool of resources approach. Auto-discovery, Dynamic Pooling and Multiple Server provisioning. 160 Servers in a management domain and management of multiple geographically distributed domains via a single pane of glass should be supported. Blade and Rack server mix in a management domain is required to be supported. Server pre-provisioning is required to support flexible upgrades, new deployments and failure scenarios. Built-in architecture resiliency/redundancy required. Blade failover support. The Server I/O should be virtualized, consolidated and integrated with the physical network to provide VM visibility. High IOPS are required. VXLAN and ease of workload mobility is required (virtual and non-virtual). Other required supported features; RDMA over Converged Ethernet (RoCE), Performance-optimization applications such as Virtual Machine Queue (VMQ), Intel Data Plane Development Kit (DPDK), and Netflow. Mandatory UCS B series Mandatory UCS Manager Service Profiles Mandatory UCS Central/UCS Director Mandatory UCS Pre-Provisioning using Service Profiles Mandatory UCS VIC Card 1300 series Management/Provisi oning DATA_CENTER _SERVERS _03 Management Scalability & Flexibility DATA_CENTER _SERVERS _04 High Availability & Architecture Flexibility DATA_CENTER _SERVERS _05 Server I/O DATA_CENTER _SERVERS _06 DATA_CENTER _SERVERS _07 DATA_CENTER Hypervisor & Operating System Security (access) Hypervisor and OS agnostic solution. Mandatory UCS Hypervisor and OS Agnostic Role-based access is required. Mandatory UCS Manager supports Role Based Access Cabling Convergence Single Cable for LAN/SAN traffic should be Mandatory Cisco UCS Single Connect Technology Ref _SERVERS _08 DATA_CENTER _SERVERS _09 Area Requirement Blade HDD/SSD/CPU/Me mory supported. Each server blade should equipped with the appropriate type of memory/cpu/disks to enable an Enterprise Class/IoT capable Datacenter for Southend Borough Council. Importance/ Weighting Reference Example Mandatory UCS B series can support up to 2x 18-core Intel Xeon processors, DDR4 memory and either HDD or SDD drives. Data Centre Security Requirements Ref Area Requirement Importance/ Weighting Reference Example DATA_CENTER_ SECURITY_01 Deployment Mandatory ASA 5585-X and ASAv DATA_CENTER_ SECURITY _02 Performance Mandatory ASA 5585-X Clustering DATA_CENTER_ SECURITY _03 Physical Appliance Management Partitioning High Availability High performance security solution using Next Generation FW and IPS - modular physical appliance(s) for North to South traffic. Virtual appliance(s) should also provide security for the virtualized workloads (East to West traffic). The physical appliance needs to scale up to 640 Gbps by device grouping techniques. The virtual appliance should scale up and out by software upgrades or spinning new virtual appliances. The physical appliance needs to be “virtualized” i.e. partitioned in “virtual” appliances for management purposes. Active/Active and Active/Standby deployments support is required for the physical appliance proposed. The security solution needs to support advanced security features URL Fitering, Application Visibility, Anti-Malware and Threat Detection/Protection. Remote Access VPN, Web-based or without the need of client application, client-based and network-tonetwork VPN are required to be supported. Seamless integration of the security solution proposed into the network fabric proposed to facilitate programmable/automated deployment (mainly for VM layer security). Mandatory ASA 5585-X Multiple Contexts Mandatory ASA 5585-X Mandatory ASA 5585-X with FirePower Services Mandatory ASA 5585-X Mandatory ASAv DATA_CENTER_ SECURITY _04 DATA_CENTER_ SECURITY _05 Advanced Security DATA_CENTER_ SECURITY _06 VPN Support DATA_CENTER _SECURITY _07 Integration with Network Fabric Data Centre – Hybrid Cloud Intro SBC require an agnostic Hybrid Cloud Solution allowing them to access resources across any available platform and mix between private and public cloud offerings. Data Centre – Hybrid Cloud Requirements Ref Area Requirement Importance/ Weighting Reference Example DATA_CENTE R_HYBRID_CL OUD_01 Deployment Mandatory Cisco Intercloud Fabric DATA_CENTE R_HYBRID_CL OUD _02 Security Mandatory Cisco Intercloud Fabric DATA_CENTE R_HYBRID_CL OUD _03 Management Mandatory Cisco Intercloud Fabric DATA_CENTE R_HYBRID_CL OUD _04 Flexibility Mandatory Cisco Intercloud Fabric DATA_CENTE R_HYBRID_CL OUD _05 DATA_CENTE Traffic Visibility & Control Hypervisor and Cloud Provider Agnostic Hybrid Cloud Solution i.e. Consistent architecture across heterogeneous environments – any hypervisor to any cloud. Freedom to to place workloads across heterogeneous Clouds. Security policies need to be extended from the Private Cloud to the Public Cloud. Secure communications between private and public cloud and between VMs in the public cloud. Role Based Access using existing security practices to protect access to cloud workloads is required. Traffic needs to be encrypted between Private and Public Clouds and within Cloud Provider. Single point of cloud connection management (eliminate Shadow IT) and unified workload management across clouds. Policy-based deployment/governance in the cloud. Workload portability – Image conversion and VM migration. Bidirectional Workload mobility and VM Lifecycle Management across private and public clouds Control and visibility of traffic within the public cloud and between VMs is required (using technologies such as Netflow or SPAN). Northbound APIs to allow easy integration with Mandatory Cisco Netflow and ERSPAN Mandatory Cisco Intercloud Fabric Integration with Ref Area Requirement R_HYBRID_CL OUD _06 additional management tools additional management tools in order to offer additional services is required. Importance/ Weighting Reference Example Campus Network Management Requirements Ref Area Requirement Importance/ Weighting Reference Example CAMPUS_NETWORK_ MANAGEMENT_01 Manageme nt & Deployment Options Single Pane of Glass for Wired/Wireless Network. Mandatory Prime Infrastructure 3.0 CAMPUS_NETWORK_ MANAGEMENT _02 CAMPUS_NETWORK_ MANAGEMENT _03 Network Lifecycle Application Visibility Mandatory Prime Infrastructure 3.0 Mandatory Prime Infrastructure 3.0 CAMPUS_NETWORK_ MANAGEMENT _04 Network Maps & Network Device Groups Provisioning /Configurati on Network Device Lifecycle Management, end-of-life and security incident reports. Application, granular traffic flow visibility. Top devices, clients and applications by traffic volume need to be reported as well as how much bandwidth they consume. Network Topology, Wireless heat maps and logical device grouping need to be supported. Mandatory Prime Infrastructure 3.0 Template Based Configuration. Validated design Mandatory Prime Infrastructure 3.0 Mandatory Prime Infrastructure 3.0 CAMPUS_NETWORK_ MANAGEMENT _05 Network discovery, inventory, configuration, monitoring, troubleshooting, reporting, and administration. Intuitive GUI and Dashboard/Dashlets. Best practices for configurations/deployments integrated with the tool. Virtual machine or appliance deployment options. configuration templates support to enable quick and easy device and service deployment. Packaging of individual templates into larger, reusable, configurations built for more consistent and quicker network designs. Role Based Access and flexible authentication, authorization, and accounting (AAA) services should allow for local, RADIUS, TACACS+, and single sign-on options. CAMPUS_NETWORK_ MANAGEMENT _06 Security CAMPUS_NETWORK_ MANAGEMENT _07 Reports, Events and Alarms List all the different types of reports and alarms supported by the network management tool. Explain how the alarms work. Dashboards, Troubleshooting and Alarms should be centralized. Mandatory Prime Infrastructure 3.0 CAMPUS_NETWORK_ Monitoring Monitoring policy creation support. Monitoring policies Mandatory Prime Infrastructure 3.0 Ref Area CAMPUS_NETWORK_ MANAGEMENT _12 CAMPUS_NETWORK_ MANAGEMENT _13 Importance/ Weighting Reference Example should be activated or deactivated through an intuitive workflow and push changes to devices without disrupting service MANAGEMENT _08 CAMPUS_NETWORK_ MANAGEMENT _09 CAMPUS_NETWORK_ MANAGEMENT _10 CAMPUS_NETWORK_ MANAGEMENT _11 Requirement Operations Licensing portability is required. Option for High Availability needs to be supported. Mandatory Prime Infrastructure 3.0 3rd Party and API Support Network Access Control Integration Location Analytics Integration Wireless Security 3rd Party Devices and RESTful APIs should be supported. Mandatory Prime Infrastructure 3.0 Integration with Network Access Control physical or virtual appliances must be supported. Mandatory Prime Infrastructure 3.0 Integration with location analytics engines/physical or virtual appliances to provide location-based tracking services for discovered endpoints. Prime Infrastructure 3.0 Automated detection of the switch port that a Rogue AP is connected. Prime Infrastructure 3.0 Network Access Control Requirements Ref Area Requirement Importance/ Weighting Reference Example NETWORK_ACCESS _CONTROL_01 Deployment Mandatory ISE NETWORK_ACCESS _CONTROL_02 Network Access Minimum required deployment needs to have AAA, Guest Management, Link Encryption (MACSec), Network Access Microsegmentation using tags, API Support is required. Appliance or VM options – Web based/GUI management. Option for centralized and distributed deployment. Policy Based/Software Defined/Context-Aware Network Access taking into account the user role, end-device type, time, location and end-device configuration. All policies need to be managed from a central point of management across different parts of the network (wired/wireless/VPN). Integration with Active Directory/LDAP required. Real time policy provisioning. Mandatory ISE NETWORK_ACCESS _CONTROL_03 End-Point Discovery The network needs to be able to discover endpoints automatically (iPhones, Android devices etc.) and present them in a GUI. Built-in and custom device profiles need to be supported. Mandatory ISE Profiling NETWORK_ACCESS _CONTROL_04 End-Point Assessment Mandatory ISE Endpoint Protection Service NETWORK_ACCESS _CONTROL_05 End-Point Policy Enforcement Mandatory ISE Posturing/Enforcement NETWORK_ACCESS _CONTROL_06 Authentication The network needs to be able assess the configuration/OS version/patches of end-points (iPhones, Android devices etc.). Misconfigured devices need to be reported. The network needs to be able to enforce policies to end-points (iPhones, Android devices etc.) based on their configuration and compliance rules. Actions such as blacklist, whitelist, remote wipe and integration with MDM are required. The GUI of the NAC solution needs to show user authentications as they happen (live authentication). Drill-down capability for Mandatory ISE Live Authentications Ref Area NETWORK_ACCESS _CONTROL_07 Reports, Monitoring & Troubleshooting NETWORK_ACCESS _CONTROL_08 Guest Access NETWORK_ACCESS _CONTROL_09 NETWORK_ACCESS _CONTROL_10 Network Access Microsegmentation Network Wide Context Sharing NETWORK_ACCESS _CONTROL_11 Integration with NMS NETWORK_ACCESS _CONTROL_12 PKI & Certificates Requirement additional info per authentication. Extensive reports on authentication, devices, users etc. which can be also customized. Real time monitoring and ease of troubleshooting. Different Guest Access types need to be supported. Hotspot, Self Service, Self Service Sponsor Approved, Sponsored. Customizable Guest Portals and Bring-Your-Own-Device (BYOD) support. Network Microsegmentation beyond VLANs and IP Subnet using numbered tags. Support for multivendor, cross-platform network system collaboration among parts of the IT infrastructure such as security monitoring and detection systems, network policy platforms, asset and configuration management, identity and access management platforms, and virtually any other IT operations platform. The Network Access Control solution needs to fully integrate with the Network Management System proposed. PKI & Certificate support is required. Importance/ Weighting Reference Example Mandatory ISE Reporting Mandatory ISE Guest Access Mandatory Cisco TrustSec/Security Group Tags Mandatory Cisco pxGrid and ISE Mandatory ISE + Prime Infrastructure Mandatory ISE PKI Support Converged Infrastructure Management Requirements Ref Area Requirement Importance/ Weighting Reference Example CAMPUS_CO RE_01 Management Mandatory UCS Director CAMPUS_CO RE_02 Orchestration/Autom ation Mandatory UCS Director CAMPUS_CO RE_03 CAMPUS_CO RE_04 Virtualization Single Point of management for Data Center Network, Compute, Storage. Management of virtual and nonvirtual (bare-metal) workloads in a multitenant Data Center environment. Model-Based Orchestration and Policy based automation of provisioning and de-provisioning of data center resources (compute, networking, storage) using automated workflows. Built-in and custom workflow support – create once and use as needed. Bare-metal and virtual. Hypervisor Agnostic Solution Mandatory UCS Director Infrastructure Discovery The infrastructure should be discovered automatically and the physical and logical relations stored in a database as well as represented on an infrastructure map. Mandatory UCS Director CAMPUS_CO RE_05 Infrastructure Change Tracking The solution should detect and reflects changes and movements within infrastructure that could impede workflow completion and notify the IT staff. Resource pooling should prevent changes to one group from adversely affecting other groups. Mandatory UCS Director CAMPUS_CO RE_06 CAMPUS_CO RE_07 3rd Party Support Support for 3rd party elements should be listed and briefly explained. Support of REST API, Windows Powershell, Java API, Inventory and Reports Mandatory UCS Director Mandatory UCS Director Programmability & Development Service Catalogue Intro SBC’s applications will be provided our Customers based on a service catalogue specifying technical requirements, availability requirements, and resource requirements. It will also identify Business Continuity requirements per individual application. Service Catalogue/Portal Requirements Ref Area Requirement Importance/ Weighting Reference Example SERVICE_CAT ALOGUE_01 Ordering & Automation Mandatory Prime Service Catalogue SERVICE_CAT ALOGUE _02 SERVICE_CAT ALOGUE _03 SERVICE_CAT ALOGUE _04 Control Self-service on-demand, automated and simple to use ordering portal. Shop and order data center and IT workplace services quickly just by clicking through a menu. Unified menu of services that appear in categories. Coverage for an extremely diverse range of services including data center infrastructure resources, cloud applications, platform application or general business services such as BYOD or device services. Policy-based controls and approvals. Mandatory Prime Service Catalogue Dashboards to quickly establish user entitlements and role-based access to services Lifecycle management and tracking throughout the service existence. Track open orders or access order history. Financial and demand management with pricing, quota, and lease management established at the time of service order Use built-in analytics on current active services to complete lifecycle operations such as maintain or upgrade services. Mandatory Prime Service Catalogue Mandatory Prime Service Catalogue Mandatory Prime Service Catalogue Mandatory Prime Service Catalogue Administrator Interface Service Lifecycle SERVICE_CAT ALOGUE _05 Billing SERVICE_CAT ALOGUE _06 Maintainance & Upgrades WAN Network Intro Southend will be building a new dark fibre infrastructure and this equipment will be used to enable the WAN. WAN Network Requirements (Core/Aggregation) Ref Area Requirement Importance/ Weighting Reference Example WAN_CORE_ 01 Deployment Mandatory ASR 9000 WAN_CORE_ 02 WAN_CORE_ 03 WAN_CORE_ 04 WAN_CORE_ 05 WAN_CORE_ 06 WAN_CORE_ 07 Chassis Performance Modular platform with 1G/10G/40G. Four integrated 10G SFP+ ports. 2 Module slots required. MPLS & Carrier Ethernet Services support is required. 120 Gbps chassis performance Mandatory ASR 9000 Power Redundant AC/DC power supplies Mandatory ASR 9000 Operating System Modern Carrier Class Modular Operating System – GUI support, process restartability. GPS stratum-1 input, Building Integrated Timing Supply Mandatory ASR 9000 Mandatory ASR 9000 NEBS, ETSI, EMC and list Immunity and Safety standards Mandatory ASR 9000 L2VPN, L3VPN, Layer 2 and Layer 3 multicast; IP over , Ethernet operations, administration, and maintenance (EOAM) and MPLS OAM, Layer 2 and Layer 3 access control lists (ACLs), hierarchical quality of service (HQoS) Control Plane and Routing High Availability. Support for MPLS TE-FRR. Mandatory ASR 9000 Mandatory ASR 9000 Segment Routing support is required. Mandatory ASR 9000 WAN_CORE_ 08 WAN_CORE_ 09 Clock Sync and Timing Compliance Transport/VPN Services & QoS High Availability SDN Based MPLS (BITS) ports, IEEE 1588 hardware-based support WAN Network Requirements (Remote Sites/CPE) Ref Area Requirement Importance/ Weighting Reference Example WAN_ACCESS _01 WAN_ACCESS _02 WAN_ACCESS _03 WAN_ACCESS _04 WAN_ACCESS _05 WAN_ACCESS _06 WAN_ACCESS _07 WAN_ACCESS _08 WAN_ACCESS _09 Deployment Two dual-purpose (10/100/1000 and SFP) ports, two SFP uplinks. Triple play services (ETTH/ETTB) support. Mandatory ME 3400 Chassis Performance Carrier Ethernet support and UNI/ENI/NNI interfaces. Mandatory ME 3400 Power AC/DC Power Supply. Mandatory ME 3400 Operating System & Management Software CLI, Web Interface/GUI Mandatory ME 3400 Different Levels of Software Image support for functionality flexibility NEBS, MEF 9 & 14 Mandatory ME 3400 Mandatory ME 3400 ACLs, IEEE 802.1x, Configuration File Security Mandatory ME 3400 Quality of Service Advanced QoS and Rate Limiting Mandatory ME 3400 Denial of Service Security Control Plane Security, L2 Broadcast storm contain, port security, per VLAN MAC learning Mandatory ME 3400 Compliance, Certifications Network Security