Ethereal
advertisement

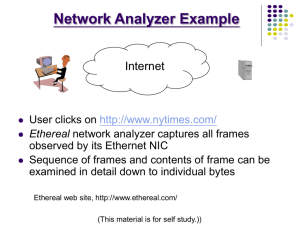
Ethereal.
Freeware sniffing tool.
Captures live network traffic.
The user interface separates it
from other sniffers.
1
Download Instruction.
Need to download two components.
WinPcap.
www.ethereal.com/distribution/win32/
http://winpcap.polito.it/install/default.htm
Ethereal (main program).
http://www.ethereal.com/distribution/win32/
2
Brief Technical Details.
Ethereal can read files of other software that is
used for sniffing. (Tcpdump, Microsoft's
Network Monitor etc.)
Can show 442 different protocols in a user
friendly way. This means that you don’t have
to know all the protocols. (you can click your
way to find the TTL for example)
3
First look at Ethereal.
1. Shows the packets
that have been
captured.
2. Shows details of a
selected packet.
3. The packet’s data
in HEX.
4
Starting with Ethereal.
5
The second window.
6
Using options while capturing.
1.
2.
3.
4.
Captures first 68 bytes of the
packet by default. This can be
changed to allow variation.
This allows you to capture all
the packets in the wire. If it is
not set then Ethereal will only
capture packet going from or to
this machine. If the option is set
off and interface is in
promiscuous you will still catch
the network traffic.
Allows to save the captured
data in a specified file. The file
name is entered in the space
indicated by 15.
Rotates Captured file by the
amount time specified in the
space marked 17.
7
Using options while capturing.
5.
6.
7.
8.
9.
This specifies that the packets
captured should be in the first
window as soon as they are
picked up.
Scroll down the first window to
keep up with the latest packet.
Specifies the number of packet
the user wants to capture in
the space marked 18.
Specifies the kilobytes(s) the
user wants to capture in the
space marked 19.
Specifies the time for which the
user wants to capture in the
space marked 20.
8
Using options while capturing.
10. Translates the MAC address to
specify the name of the
manufacturer.
11. Specifies the IP address into
domain names.
12. Translates the port into
protocol names.
13. Specify the name of the
interface that you want to
capture packets. Usually there
is only one name except for
multi-homed machine.
14. The user can write down the
preference here in this space
while capturing packets
9
FILTERING COMMAND.
Allows the user to enter specific command
on what packets to capture.
10
[src|dst] host <host>
Specifies the host
whose packets to
capture.
Example:host
192.168.2.100:
11
[src|dst] port <port>
This allows
ethereal to capture
packet from or to
the port specified.
Example port 139
12
[src|dst] net <net> [{mask <mask>}|{len <len>}]
This allows you to filter
on network numbers.In
addition, you can specify
either the netmask or the
CIDR prefix for the
network if they are
different from your own.
Example :net 192.168.2.0
mask 255.255.255
13
less|greater <length>
This allows you to filter on
packets whose length was less
than or equal to the specified
length, or greater than or equal
to the specified length,
respectively.
Example: greater 40
14
ether|ip broadcast|multicast
This allows you to filter on
either Ethernet or IP
broadcasts or multicasts.
Example: ip broadcast.
15
ip|ether proto <protocol>
This primitive allows
you to filter on the
specified protocol at
either the Ethernet layer
or the IP layer.
Example:ip proto ICMP
16
Ethereal features.
Ethereal has lots of cool features to
aid the user in analyzing the packets
captured.
Filters after capturing.
Visual effects.
17
Filtering after capture.
Ethereal has option of filtering the
captured data. This is specially
useful since the amount of data
captured is large. There are a large
number of filters most of them can
be figured out by clicking the Add
Expression button.
For example sake I have shown few
of the filter in the next few slides.
18
Filters.
Ip.addr == <IP Address>
Shows only the packets from or to the IP Address specified.
Example: Ip.addr == 192.168.2.102
19
Filters.
Frame.pkt._len > <size>
Shows packets greater than the
size specified. This can be used
with
as also less than (<).
Example:
Frame.pkt._len > 70
20
Filters.
Tcp.flags.<name>
Shows packets the flag bit set.
EXAMPLE : Tcp.flags.ack
21
Filters.
You can make a complex filter by adding
AND, OR, XOR, NOT.
Example: ip.addr == 192.168.2.102 and tcp.flags.ack
There are some other operators called
substring operators. There functions are:
[x:y]
specifies the range.
[x:]
specifies the range starting
from x to the end of the sequence.
[x,y,z] specifies compound range.
Example:eth.src[0:3,1-2,:4,4:,2] == 00:00:83:00:83:00:00:83:00:20:20:83
22
Visual effects.
You can specific filters to
colour the type of
packets you are
interested. To do this you
have to click view>coloring rules.
23
Visual effects.
For example I have chosen
the packets with ack bit set.
I want them to noticeable.
Then all I do is.
View-> coloring rules > new -> add
expression. After adding
the expression. Press OK.
Set the colours (I have set
it to green). Then the result
would look like something
like this.
24
Visual effects. (The results)
25
Following TCP streams.
If you want to see
the data on a TCP
session without
you trying to figure
them out. You can
start by clicking
analyze->follow
tcp stream
26
SUMMARY
I have learnt the basic use of
ethereal.
All the test here was in a private
network. So nothing very interesting.
One should understand this only a
tool not a means.
One needs vast knowledge and
dedication for the proper use of this
kind of tools.
27
Questions
Kazi Nasim Faisal
1st march 2004
28