modeling lane dynamics
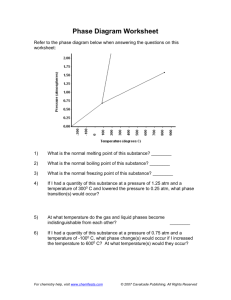
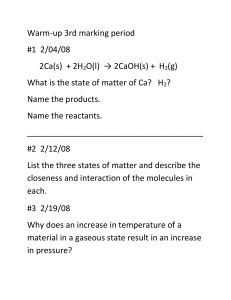
advertisement

7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
MODELING LANE DYNAMICS
ABDUL MALIK KHAN & ANDREW P. PAPLIŃSKI
Faculty of Information Technology
Monash University
Clayton Campus, Wellington Road, Vic 3800
AUSTRALIA
{Malik.Khan, Andrew.Paplinski}@infotech.monash.edu.au
Abstract: - In campuses and other medium organizations, ATM networks co-exist with newer networks such as
Fast Ethernet, Gigabit and legacy Ethernet & Token-Rings. Such networks use ATM LAN emulation
(asynchronous transfer mode LANE) to access the ATM network. The need to have intelligent answers to questions
of cost, performance, and the direction of growth (trend analysis and capacity planning) that frequently arise
throughout the life cycle of the network drives network design experts to model and simulate the network. The
purpose of this paper is to study the details of the ATM LANE protocol in order to include, in a simulation model,
the required dynamics of the LANE traffic. Many simulation tools have no built-in modeling elements to simulate
networks with multiple ATM Emulated LANS (ELANs). The research work has resulted in a state-wise description
of the network operations in emulated LAN environment that helps create objects that could be used to model and
simulate LANE so as to improve the performance and interaction of ATM with newer generation of networks.
Key-Words: - Modeling, LAN Emulation, ATM Networks, LANE, LEC, LAD, ELAN.
1
INTRODUCTION
LAN Emulation and Configuration Server
(LECS).
ATM Switch: An ATM Switch is capable of
switching VCs and VPs.
LAN Emulation Server (LES). LAN Emulated
Server serves generic network applications such
as Web, Email etc. running over LANE. A client
running applications over LANE can connect to
the LANE server. LANE uses ATM as the data
link layer for transmitting data over an ATM
network
Broadcast and Unknown Server (BUS).
LAN Access Devices (LADs) or proxy-LECs.
These devices are the LAN access routers to the
legacy networks.
The tool used in this research work to model and
simulate the network is COMNET. The model's
topology consists of a number of nodes and links.
The nodes directly attached to the ATM switches
represent LECs, which are directly part of the
ELAN. They are assumed to have a LANE module
in their respective protocol stack modeled as session
source LANE-D, application source LANE-I, which
is described on the next page LES and BUS are
independent servers. A LAD is connected to both the
ELAN (ATM side) as well as a traditional Ethernet
LAN. All these nodes are modeled using a
COMNET [5] Computer & Communications node.
They are connected to the ELAN through point-topoint OC-3 or DS-1 links. Apart from the LAD,
workgroups are also connected to the Ethernet LAN,
using a COMNET Computer Group. [5, 7]
2
LAN Emulation (LANE)
2.1
LAN Emulation Components
Together, these components allow the formation
of an ELAN. The interactions between these ELAN
components are as follows: upon receipt of a traditional
LAN frame from the higher layer protocols, the LEC
performs its address resolution function. Each LEC
maintains a mapping (ARP cache) of known MAC
addresses to ATM addresses. However, this mapping
might not be exhaustive and furthermore is purged
periodically. When a frame is received with an unknown
MAC/ATM address, the LEC sends an address
resolution request to the LES. Each member of the
ELAN has to register its MAC/ATM address with the
LES upon joining the ELAN. If the LES has an entry for
the required ATM address, it replies to the LEC, which
is then able to set up a direct connection to the
destination using the connectionless AAL5 service. The
LAN Emulation and Configuration Server (LECS)
maintain information about all the ELANs. [7]
In LANE, a typical ELAN consists of the
following components:
LAN Emulation Clients (LECs). LANE
workstation is an Ethernet client, which has
generic network applications such as Web,
Email etc. running over LANE. It uses ATM
as the data link layer for transmitting data
over an ATM network.
ISBN: 978-960-6766-49-7
1
262
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
In the case where the LEC has to request the
address from the LES, only a single packet is
sent to the BUS for flooding.
The congestion is perceived to be in the internal
traffic of the network under study as opposed to
the traffic that is external to the network.
Within the transit network ELAN; the ATM
switches are interconnected by OC-3/DS-1 links.
Each legacy LAN (Ethernet) is terminated by a
computer object, which form’s a workgroup of 5
clients (approximated).
The network ELAN consists of 20-30 LAN
Emulation Clients (LECs). Four subnets are
identified as having LECs in the network area.
Each subnet consists of 5 LECs with traffic
sources and sinks.
In some cases, however, even the LES may
not have an entry for the MAC/ATM address pair; in
particular, if the destination MAC is hidden behind a
LAD or if it is part of another ELAN. For this
reason, the LEC also sends the first few frames of
the transmission to the BUS, which floods these
frames to all the members in the ELAN. At the same
time, the LES initiates an address resolution
protocol, possibly prompting other LESs for the
requested address. Should one of these flooded
frames reach the destination, possibly through an
LAD, the destination informs the LES about its
address. Again, once the address resolution is
completed, the source LEC establishes a data direct
VCC ATM connection to the destination using
AAL5 [1, 2].
This paper is organized as follows. A brief
introduction into the elements and operations of
LAN Emulation is provided followed by list of
assumptions made in the research. Following this are
the sections that detail the network under study and
enumerate the parameters for analyzing emulated
LANs. The details of the dynamics of LAN
emulation that result in a discrete, state-wise
description of the steps involved, follow in the next
section followed by a conclusion summarizing the
salient points.
2.2
Assumptions
The assumptions underlying the model are
as follows:
All the devices in the ATM part of the
model are included as members of the
ELAN. Total of four ELANs are defined.
The explicit address resolution protocol of
the server is not modeled. Instead, the
process is modeled by a time delay of 0.05
seconds. This simplification ignores some of
the network traffic, which is generated by
the ARP process. However, this traffic is
considered insignificant with respect to the
other traffic load in the network.
A LEC is assumed to have the destination
ATM addresses cached in 50% of all
transmissions. The other 50% of the
transmissions have to go through the LANE
process, as outlined above, simulating the
cases where the cache entry has either been
purged or when the destination is hidden
behind a LAD. Equal number of LEC’s and
Legacy LAN clients are defined.
ISBN: 978-960-6766-49-7
3
The Network Model
The ELAN itself is modeled by a COMNET
transit net. A single ATM switch or a group of
interconnected ATM switches represent the physical
aspects of the ELAN in the model. All the nodes of the
ELAN are connected to this switch through the OC-3 or
DS-1 links. The transit net retains its default network
service class and its default connection type [1].
However, the protocol of this connection is set to ATM
AAL5 with the following parameter values:
Basic protocol: Data bytes 48, overhead bytes 16 & other
parameters default.
Flow control: none, Policing: none & Rate control: none.
A number of COMNET default traffic sources define the
ELAN traffic. The LECs generate direct and indirect
traffic, the former representing those frames where the
LEC has the destination address cached; the latter
representing the case where the LEC has to go through
the LES. The direct traffic with suffix LANE-D is
generated using an COMNET node session source. The
destination of this direct message source is either the
remaining LEC, or the LAD. A COMNET node
application source is also associated with each LEC.
This source models the indirect traffic, which has to go
through the LES. [5, 7]
Traffic components of LEC are as follows:
LANE-D:
Traffic source to model direct ATM connections (the
LEC has the MAC address of the destination in its
cache). Modeled as a message source.
Destination: Random list of all LECs and LADs of that
ELAN
LANE-I:
Traffic source to model indirect ATM connections
(wherein the LEC does not have the MAC address of
the destination in its cache). Modeled as an application
source.
263 2
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
Sequence of commands:
SendARP – sends ARP request of 28bytes
Broadcast
Await Response – Responds to any default received
message text
Setup LANE
The first command sends a 30-byte message
to the LES to simulate the address resolution
request. This command is defined as a global
transport command, and hence it is available to all
the application sources in the model. At the same
time, the application sends a message to the BUS by
executing the command „Broadcast‟. After these two
transmissions, the application then waits for a
response from the LES. This is implemented in the
model in the form of a global filter command. The
message to wait for is set to „ARP‟, which
corresponds to the message text by which the LES
responds to the request. Upon arrival of such a
message, indicating that the address resolution
request has been terminated, the LEC then
establishes a connection with either the other LEC or
the LAD. This is modeled using a local session
command, the parameters of which are identical to
those outlined under the direct transmission above
[1, 2, 5, and 7].
Connected to the LES is a single COMNET
process response source. This source is triggered
upon arrival of the 28-byte message, which is
generated by the execution of the command „send
ARP‟ on the LECs. After the delay of 0.05 sec for
address resolution, the response source returns a 28byte message to the requesting LEC. This message is
associated with the text „ARP‟, which, upon arrival
at the LEC, triggers the continuation of the LEC‟s
command sequence.
LES
A response source “ARP” is used to model the address
resolution on the LES.
Scheduling: By received messages generated by the
LECs for address resolution.
A single COMNET process model message
source named „Flood‟ is attached to the BUS. This
source is responsible for flooding a single packet.
The source is triggered by the message „Broadcast‟,
which is sent by executing the command „Broadcast‟
on the LEC. Upon arrival of such a message, the
source then forwards the incoming message to all the
members on the ELAN. The model can easily be
modified to simulate the flooding of several packets,
not just a single packet, as indicated in the list of
assumptions. To determine the destination of this
flooded message, the „multicast‟ algorithm is used.
ISBN: 978-960-6766-49-7
The list contains all the nodes, which are part of the
ELAN.
BUS
A message source “Flood” is used to model the broadcast
operation in LANE. A broadcast is sent to a multicast list
comprising all LECs, LADs & Ethernet workgroups.
Scheduling: By received broadcast request from the LECs.
The interactions of the ELAN with the
traditional Ethernet LAN are modeled at the LAD. The
process node model is associated with three process
traffic sources labeled „LANE‟, „LANE-FwI‟, and
„LANE-FwD‟. The principal function of these sources is
to convert the protocol stack between the Ethernet LAN
and the ELAN. The two sources, „LANE-FwI‟ and
„LANE-FwD‟, handle the traffic from Ethernet to the
ELAN. The source, „LANE‟, handles the traffic in the
other direction.
The message source, „LANE‟, is triggered by
indirect and direct messages from the LECs,
respectively. Notice that the LECs' operations, as
described above, do not establish a connection with the
workstations on the traditional LAN directly. Instead,
the direct and indirect traffic is transmitted to the LAD,
since the connection-oriented ATM protocol cannot be
part of the traditional Ethernet LAN. The source,
„LANE‟, is triggered by any message originating from
either LECs, then assembles the message and transmits it
in a connectionless mode to any one or more of the
workstations on the traditional LAN. The parameter
settings for this traffic source are as follows:
LAD (LAN Access Device)
A message source, a session source, and an application
source are used to model the traffic to and from the
LAD.
LANE:
A message source, LANE, models the traffic from the
LECs to the Ethernet workgroups. Scheduled by
received message “LANE” from the LECs.
Routing class: Standard; Transport protocol: Ethernet.
Destination: Random list of Ethernet workgroup
computers across the corresponding LAD.
LANE-FwD:
A process session source model, LANE-FwD, is used
to model the direct traffic from the Ethernet workgroup
computers to the LECs.
LANE-FwI:
An application process source, LANE-FwI, is used to
model the indirect traffic from the Ethernet workgroup
computers to the LECs. The command sequence for
this application is as follows:
SendARP – sends ARP request of 28 bytes to the
corresponding LES
264 3
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
Broadcast
Await Response – Responds to any default received
message text
Setup LANE – Messages to a random list of all LECs
and corresponding LADs
Similarly, the workstations on the traditional
LAN do not directly establish a connection with the
LECs. Instead, they transmit their messages to the
LAD. This is indicated in the model through the two
COMNET process message sources with the
suffixes ‘LANE/D’ and ‘LANE/ I’, respectively,
which are connected to the computer group icon.
These sources generate a connectionless traffic to
the LAD using the Ethernet protocol. The only
difference between both sources is the name of the
source, which is subsequently used as a trigger at the
LAD. The process source with the suffix ‘LANE/D’
triggers the COMNET session source named
‘LANE-FwD’, whereas the process source with the
suffix ‘LANE/I’ triggers the application process
source named ‘LANE-FwI’. The two forwarding
sources are very similar to the sources connected to
the LECs. ‘LANE-FwD’ generates messages with
one of the LECs as destination following the
Ethernet protocol. Like above, the Ethernet frames
are segmented into ATM AAL5 cells on the ELAN.
Similarly, the message source, ‘E-LANE/I’, triggers
the application source, ‘LANE-FwI’, which again
executes the command sequence of commands:
Send ARP
Broadcast
Await Response
LANE
LEGACY WORKGROUP COMPUTERS
Two process messages sources – one each for direct
and indirect, are used to model the traffic from legacy
LANs to the LECs.
With the suffix LANE /D:
Traffic source to model direct ATM connections
(wherein the MAC address of the destination is with
the LAD). Modeled as a process message source.
Destination: Corresponding LAD
With the suffix LANE /I:
Traffic source to model indirect ATM connections
(wherein the MAC address of the destination is not
with the LAD). Modeled as a message source.
Destination: Corresponding LAD
The parameters for these commands are
identical to those described above. Here, the
modules defining the ELAN are no longer associated
with dedicated physical nodes. Instead, they are
represented by the traffic sources only. The ELAN is
thus modeled through the relationships between the
ISBN: 978-960-6766-49-7
sources that are established through triggers and the
destination lists of the sources.
Figures 14 and 15 show the snapshots of model
developed. These models represent the traffic
engineering and LANE dynamics.
4
Dynamics of ELAN traffic
Traffic flow dynamics were modeled using the
node model, process model and interface attributes for
message response and session source objects.
Application configuration and User configuration
objects are used to model different combinations of
traffic parameters and types with user profiles. A typical
example of the most common activities on the network
includes email, web browsing, video audio streaming
and videoconferencing. Dynamics of LANE are shown
in figure 1.
The email transactions at the client side were
split into two traffic types – one corresponding to a user
sending email and the other corresponding to the user
receiving email. On COMNET, these were respectively
represented by a message source that sends the email to
the mail server and another message source that triggers
the mail server to send the mail. The email transactions
on the mail server side were split into two traffic types –
one corresponding to the mail server receiving and
storing the mail and the other corresponding to the mail
server reading and sending the mail. In COMNET, these
were respectively represented by an application source
that responds to the client mail send requests and
receives the email, and another application source that
responds to the client mail receive requests and transfers
the mail.[5,7]
The web service at the client side is modeled
using a traffic message source that requests web pages
through a proxy server and sets up a web session. At the
proxy server, the response to this request is modeled
using an application source.
The proxy LECs serve the edge devices, local
LAN, and remote LAN. Each of these routers supports
Token-Ring and Ethernet segments. All the segments are
terminated with a set of workgroup computers, each
having 10 users. Each user generates email, web, and
audio video streaming traffic requests from the services
that are attached to the network ELAN.
All the traffic generated from the Token-Ring
and Ethernet segments are directed to the proxy LEC.
The routers use ATM adaptation layer protocol AAL5 to
forward the traffic from the legacy Token-Ring/Ethernet
side to the ATM side.
265 4
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
Traffic profiles were decided on the basis of access
patterns of typical users in the network. Two
workload components are considered in the model:
e-mail, and web. The traffic parameter values of
each traffic scenario are summarized in Table 1. The
workload intensity parameters are described below:
E-mail:
E-mailRequestSize
E-mailInterarrival
E-mailSize
Web:
WebRequestSize
WebInterarrival
WebPageSize
an application source that is used to model the process of
the LAD forwarding the mail request from the client to
the server. This application source, called ‘Email Send
LANE-FwD’, generates the message called ‘Email-Send’
destined for the mail server and of size
‘EmailRequestSize’. At the mail server, an application
Low Load
Medium Load
Heavy Load
100 bytes
Exp 720 sec
Exp (1 KB)
100 bytes
Exp 360 sec
Exp (3 KB)
100 bytes
Exp 180 sec
Exp (5 KB)
100 bytes
Exp 360 sec
Exp (30 KB)
100 bytes
Exp 120 sec
Exp (100 KB)
100 bytes
Exp 120 sec
Exp (200 KB)
Table 1 Workload components and traffic parameters under different loads
E-mailRequestSize: It is the size of the
initial packet generated by a mail client.
This packet represents the request initiated
by the client to read or receive the email
from the mail server.
E-mailInterarrival: It is the rate at which
emails are sent or received by a mail client.
E-mailSize: For a mail client, this variable
represents the size of the email sent to the
mail server. For the operation of a mail
receive, this means the size of the email
received from the mail server.
WebRequestSize: It is the size of the packet
generated by a web client. This packet
represents the request to retrieve a web page
from the web server.
WebInterarrival: It is the rate at which a
client generates web requests (http, ftp etc).
WebSize: The size of the web page
requested by a web client and provided by
the web server.
4.1
Dynamics of Email transactions:
Typically, mail transactions consist of mail
send and receive activities. The process of sending
and receiving email is modeled separately.
A message source is used to model the process of a
client sending email. The client generates an email
send request called ‘EmailSendRequest’ of size
‘EmailRequestSize’. The frequency of this is
governed by the parameter ‘EmailInterarrival’. On
any LEC, the message text of this message is
‘Email-Send’ and the destination is the mail server.
On a node attached to a legacy LAN, this request is
destined to the corresponding LAD or the proxyLEC. At the LAD, the ‘EmailSendRequest’ triggers
ISBN: 978-960-6766-49-7
source is used to model the process of receiving the user
mail and storing it. This application source ‘Exchange
Store’ is triggered by the message with message text
‘Email-Send’.
A message source is used to model the process
of a client generating an email receive request. This
request, called ‘E-mailReceiveRequest’, is generated
every ‘E-mailInterarrival’ seconds and its size is ‘EmailRequestSize’. On any LEC, the message text of this
message is set to ‘E-mail-Receive’ and the destination is
the mail server. On a node attached to a legacy LAN,
this request is destined to the corresponding LAD or
proxy-LEC. At the LAD, the ‘E-mailReceiveRequest’
triggers an application source ‘E-mail Receive LANEFwD’ that is used to model the process of the LAD
requesting the user mail from the mail server. This
application source generates a message with text ‘Email-Receive’ and size ‘E-mailRequestSize’ destined for
the mail server. At the mail server, a response source is
used to model the process of processing the mail request
and then delivering the mail. This response source
‘Exchange Transfer’ is triggered by the message with
message text ‘E-mailReceive’, which in return sets the
text of its reply to ‘UserMail’. The response source
responds by replying to the node at which the message
originated. LECs receive the requested emails directly.
For the clients on the legacy LANs, the email receive
request is forced to go through the LAD to reach the
mail server. Hence, the response source always sends the
mail to the LAD from which the request originated. At
the LAD, a message source, ‘Email-LANE’, is used to
transfer the messages received from the mail server to
the client. This message source triggers on the arrival of
the message with text ‘UserMail’, which is generated by
the mail server and which represents the message with
the user mail in it. For the purpose of collecting and
monitoring statistics, the application type of all email
transactions is set to ‘Email’. [6, 7]
266 5
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
A processing node models the behavior of
the Exchange mail server with a storage capacity of
20 Gigabytes. This source models the Exchange
Store, which saves the mails of all users on its local
hard disk & Exchange Transfer, which reads and
transfers the mails of individual clients.
The time sequence diagram of the mail
exchange operation of legacy LAN clients is shown
in Figure 2, and a similar diagram for the mail
exchange operation of the LAN emulation clients is
shown in Figure 3.
4.2
collecting and monitoring statistics, the application type
of all web transactions is set to „Web‟.
A processing node with default parameters
achieves the modeling of web servers. To fully
understand the interactions between a web client and a
proxy server, please refer to the time sequence diagram
of the web application shown in Figures 4 and 5.
5
Simulation Scenarios
The simulation was executed with the following
three “what-if” scenarios as shown in the above Table 1:
Dynamics of Web Transactions
5.1
Typically, a web transaction consists of a
client requesting a web page from a web server. The
server is directly attached to the ELAN. Two web
servers are used in this model and any one of
them can service a particular client request. A
message source is used to model the process of a
client sending a web request. The client generates a
web page retrieve request called „Web E-LANE/D‟
of size „WebRequestSize‟. The frequency of this is
governed by the parameter, „WebInterarrival‟. On
any LEC, the message text of this message is
„WebClient‟ and the destination is the web servers.
On a node attached to a legacy LAN, this request is
destined to the corresponding LAD or the proxyLEC. At the LAD, the „Web E-LANE/D‟ triggers a
session source that is used to model the process of
the LAD forwarding the web request from the client
to the servers. This session source, called „Web
LANE-FwD‟, generates the message called
„WebClient‟ destined for the web servers and of size
„WebRequestSize‟. At the web server that receives
the request, a response source is used to model the
process of receiving the user web page request and
sending the web page to the requester. This response
source, „ProxyResponse‟, is triggered by the
message with the message text, „WebClient‟. Itself
sets the text of its reply to „UserWebPage‟. The
response source responds by replying to the node at
which the message originated. LECs receive the
requested web page directly. For the clients on the
legacy LANs, the web page request is forced to go
through the LAD to reach the web server. Hence, the
response source always sends the web page to the
LAD from which the request originated. At the
LAD, a message source „Web LANE‟ is used to
transfer the web pages received from the web
server(s) to the clients. This message source triggers
on the arrival of the message with text
„UserWebPage‟ which is generated by the web
server(s) and which represents the message with the
user requested web page in it. For the purpose of
ISBN: 978-960-6766-49-7
Scenario-1: Low Email and Web Load
Typically, an email client generates 5 emails per
hour exponentially distributed and of the size 1KB. A
web client requests web pages of size 30KB at the rate of
10 pages per hour exponentially distributed.
5.2
Scenario-2: Medium Email & Web Load
Typically, an email client generates 10 emails
per hour exponentially distributed and of the size 3KB.
A web client requests web pages of size 100KB at the
rate of 30 pages per hour exponentially distributed.
5. 3
Scenario-3: Heavy Email and Web Load
Typically, an email client generates 20 emails
per hour exponentially distributed and of the size 5KB.
A web client requests web pages of size 200KB at the
rate of 30 pages per hour exponentially distributed.
6
Conclusion
This paper has presented ways to model and
simulate emulated LANs in ATM networks using
COMNET. A detailed state-wise description of the LAN
emulation process has been achieved. Test simulation
runs have been done on different traffic scenarios and
results obtained.
The results of the above scenarios are shown in
the following figures (figure-6 to 13). In all the above
scenarios the link utilization for different links were
studied. Expectedly the results inferred from our study
show the link utilization for slower links (T1, E1, etc) is
much higher when compared to the high-speed links.
The link utilization and performance was also compared
as the load was increased from medium to heavy. The
results we got were what we expected. The results also
show successful modeling of LANE dynamics, the
results shown in figures-6 to 13 show clients from ATM
networks (LANE client) and legacy Ethernet and TokenRing networks. The LAN clients successfully
communicated with the Application server serving those
267 6
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
applications. Similarly the LEC‟s which are
connected and assigned different ELAN‟s also
communicated across ELAN‟s and the server.
8
Figures
This paper has described the LAN emulation over
ATM client/server model. LAN emulation is an
ATM service that provides the migration from
existing LANs to an ATM environment. LAN
emulation does what its name implies; it emulates
the operation of traditional LANs, and in doing so,
makes the connection-oriented nature of ATM
transparent to existing applications on all end-user
workstations. This paper also describes the
functions, frame formats and protocols used by LAN
emulation as specified by the ATM Forum. It shows
how to model and implement LAN emulation over
ATM.
Ways to improve this work would be to
extend the methodology to include quality-of-service
parameters in the model. A significant result could
be achieved by having a real-time network topology
and traffic integrated into the network model to
validate and increase the accuracy of the modeled
network.
7
Figure 1 Time Sequence diagram representing modeling
of LANE
References
[1]
Modeling ATM networks with ATM Forum
Technical Committee: LAN Emulation over ATM,
Version 4.0, af-lane-0021.000, January 2001.
[2]
H.J.R. Dutton and P. Lenhard, ATM
Technical Overview, Prentice Hall, New Jersey,
2005.
[3]
J. M. Pitts, J. A. Schormans, Introduction to
ATM Design and Performance: With Applications
Analysis Software, John Wiley & Sons, 2000.
[4]
D. D. Kouvatsos, International Federation
for information, ATM Networks: Performance
Modeling and Analysis, Chapman & Hall, 1996.
[5]
COMNET III is a performance analysis
tool for communications networks from CACI
[6]
Matthew
J.
Castelli,
Network
Consultants Handbook, Cisco press 2003.
[7]
Campus ATM LAN Emulation and
Classical IP Implementation Guide, IBM
Technical support Organization, 2004
Figure 2 Time sequence diagram of mail exchange
operation of legacy LAN clients
ISBN: 978-960-6766-49-7
268 7
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
Figure 5 The time sequence diagram of the web page
request operation by LECs
Figure 3 Time sequence diagrams of the mail
exchange operation of the LECs
Figure 6 VCC count for the three scenarios. Note that
the VCC count is same for all scenarios
Figure 4 The time sequence diagram of the web
page request operation by legacy LAN clients
ISBN: 978-960-6766-49-7
Figure 7 LANE throughputs in bits/sec for the three
scenarios. Note that the throughput varies for all the
scenarios
269 8
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
Figure 8 Ethernet delay for the three scenarios. Note
that the Ethernet delay increases as the traffic load
increases.
Figure 11 HTTP Web page response time for Low,
Medium and High load. Note that the time response
increases as the load increases.
Figure 9 ATM AAL5 delay for the three scenarios.
Note that the ATM AAL5 delay increases as the
traffic load increases.
Figure 12 Graph of top link Utilization. Link T1 and
link E1 which has the highest utilization (average 10%).
The graph is for Low Load of Web
Figure 10 ATM AAL5 delay Variation for the three
scenarios. Note that the ATM AAL5 delay variations
increases as the traffic load increases.
ISBN: 978-960-6766-49-7
Figure 13 Graph of top link Utilization. Which has the
highest utilization (reaches saturation on an Average of
99%). The graph is for High Load Web.
270 9
ISSN: 1790-5117
7th WSEAS Int. Conf. on APPLIED COMPUTER & APPLIED COMPUTATIONAL SCIENCE (ACACOS '08), Hangzhou, China, April 6-8, 2008
Figure 14 Snapshot of the Network model with LANE dynamics and traffic engineering.
Figure 15 Snapshot of the network model with LANE dynamics, traffic engineering and interfacing
ISBN: 978-960-6766-49-7
27110
ISSN: 1790-5117