SNMP : Simple Network Management Protocol What is Network
advertisement
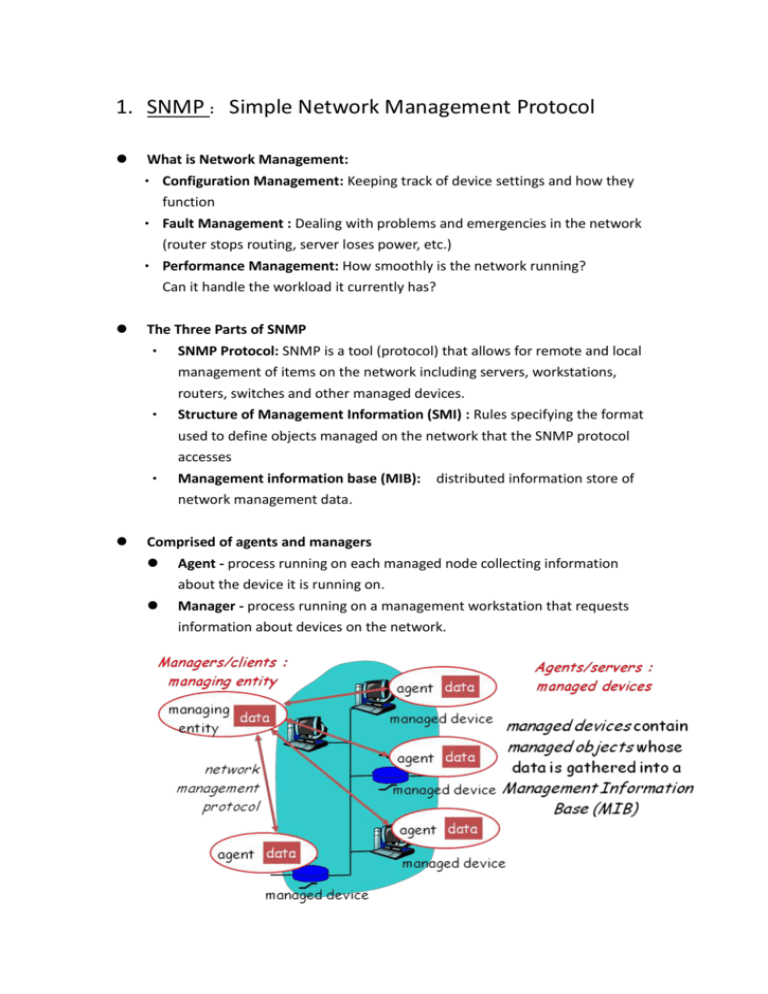
1. SNMP : Simple Network Management Protocol What is Network Management: • Configuration Management: Keeping track of device settings and how they function • Fault Management : Dealing with problems and emergencies in the network (router stops routing, server loses power, etc.) • Performance Management: How smoothly is the network running? Can it handle the workload it currently has? The Three Parts of SNMP • SNMP Protocol: SNMP is a tool (protocol) that allows for remote and local management of items on the network including servers, workstations, • • routers, switches and other managed devices. Structure of Management Information (SMI) : Rules specifying the format used to define objects managed on the network that the SNMP protocol accesses Management information base (MIB): distributed information store of network management data. Comprised of agents and managers Agent - process running on each managed node collecting information about the device it is running on. Manager - process running on a management workstation that requests information about devices on the network. Client Pull & Server Push • SNMP is a “client pull” model : The management system (client) “pulls” data from the agent (server). • SNMP is a “server push” model : The agent (server) “pushes” out a trap message to a (client) management system (Many events can be configured to signal a trap, like a network cable fault, failing NIC or Hard Drive, a “General Protection Fault”, or a power supply failure) Question to think about: Why does SNMP be called a “Client Pull & Server Push” model ? And when does Server Push happen ? What is the security concern of SNMP ? Hint: MIB objects being communicated contain critical information about network devices. We don't want just anyone “snooping” into our network to find out our IP addresses, or how long our machines have been running, or whether our links are down, or pretty much anything else. Without security protection, strangers might be able to control or interfere with our managed devices by issuing bogus commands to change MIB objects that control device operation! Or, many TRAPS floods to managing entity to cause DoS attacks. 2. DNS: Domain Name Systems Application-layer protocol host, routers, name servers to communicate to resolve names (address/name translation). The domain name system is usually used to translate a host name into an IP address. Map between IP addresses and name. • IP Addresses are great for computers • • IP address includes information used for routing. IP addresses are tough for humans to remember. Distributed database implemented in hierarchy of many name servers . 13 root name servers worldwide Domain names comprise a hierarchy so that names are unique, yet easy to remember. Why not centralize DNS? • • • single point of failure traffic volume distant centralized database • maintenance no server has all name-to-IP address mappings local name servers: • each ISP, company has local (default) name server • host DNS query first goes to local name server authoritative name server: • for a host: stores that host’s IP address, name • can perform name/address translation for that host’s name Simple DNS example host surf.eurecom.fr wants IP address of gaia.cs.umass.edu 1. contacts its local DNS server, dns.eurecom.fr 2. dns.eurecom.fr contacts root name server, if necessary 3. root name server contacts authoritative name server, dns.umass.edu, if necessary Efficiency : Using Cache to increase efficiency Security Issue: Information Leakage, Dynamic Update Vulnerabilities, Cache Poisoning Question to think about: Why does DNS use distributed architecture instead of a centralized one ? 3. DHCP: Dynamic Host Configuration Protocol Goal: allow host to dynamically obtain its IP address from network server when it joins network • Can renew its lease on address in use • Allows reuse of addresses (only hold address while connected an “on”) • Support for mobile users who want to join network (more shortly) DHCP overview: • host broadcasts “DHCP discover” msg • DHCP server responds with “DHCP offer” msg • host requests IP address: “DHCP request” msg • DHCP server sends address: “DHCP ack” msg Question to think about: If the number of users is far more than the number of available IPs, Dynamic or fixed IP is better and why ? 4. SSL SSL use PKI (public key and private key) to negotiate a session key between 2 parties and then use symmetric key cryptography to encrypt and decrypt data transmitted. Please check Slides for Week 11 : Internet Security . 1. Alice connects to Bob's server 2. Bob's server returns certificate (signed by VeriSign), plus something encrypted with Bob.private_key Alice can verify certificate is valid Uses Bob’s public key to decrypt token Bob authenticated Alice makes one time session key k Encrypts with Bob's public key, sends to Bob Now, can use symmetric key cryptography 3. 4. 5. 6. 7. Question to think about: 1. In PKI (Public Key Infrastructure), Bob and Alice both have their own pair of public and private keys. In other words, Bob has bob.public_key and bob.private_key, and Alice has Alice.public_key and Alice.private_key, respectively. Please figure out how it works in the following 2 scenarios: Bob need to sign the message, and Alice need to authenticate it is Bob Bob need to encrypt the message, and such that only Alice can read the message. 2. Why does SSL first use PKI to exchange a shared session key k between 2 parties, and then use k to perform symmetric cryptography? 5. SIP & RTP First of all, SIP is a signaling protocol handling the call control like inviting to a call, cancel (hang up while ringing), hanging up after ended call and so on. SIP can also include additional information, for example related to how to set up a call with an audio or video stream (called SDP, Session Description Protocol). The SDP information will result in one or more RTP streams (or sessions) to be set up, normally directly between the two user agents. RTP streams are by nature bandwidth and processing intensive. Finally, the Real-Time Control Protocol (RTCP) communicates information about the RTP streams between the user agents (RTCP will either use the specified RTP port + 1 or the port indicated in the SDP message). RTP: Real-Time Protocol, RFC 1889 RTP specifies a packet structure for packets carrying audio and video data RTP packet provides payload type identification, packet sequence numbering, timestamping RTP runs in the end systems. RTP packets are encapsulated in UDP segments Interoperability: If two Internet phone applications run RTP, then they may be able to work together RTP runs on top of UDP RTP Example Consider sending 64 kbps PCM-encoded voice over RTP. Application collects the encoded data in chunks, e.g., every 20 msec = 160 bytes in a chunk. The audio chunk along with the RTP header form the RTP packet, which is encapsulated into a UDP segment. RTP header indicates type of audio encoding in each packet sender can change encoding during a conference. RTP header also contains sequence numbers and timestamps. RTP Header Payload Type (7 bits): Indicates type of encoding currently being used. If sender changes encoding in middle of conference, sender informs the receiver through this payload type field. • Payload type 0: PCM mu-law, 64 kbps • Payload type 3, GSM, 13 kbps • Payload type 7, LPC, 2.4 kbps • Payload type 26, Motion JPEG • Payload type 31. H.261 • Payload type 33, MPEG2 video Sequence Number (16 bits): Increments by one for each RTP packet sent, and may be used to detect packet loss and to restore packet sequence. Timestamp field (32 bytes long). Reflects the sampling instant of the first byte in the RTP data packet. • For audio, timestamp clock typically increments by one for each sampling period (for example, each 125 usecs for a 8 KHz sampling clock) • if application generates chunks of 160 encoded samples, then timestamp increases by 160 for each RTP packet when source is active. Timestamp clock continues to increase at constant rate when source is inactive. SSRC field (32 bits long). Identifies the source of the RTP stream. Each stream in a RTP session should have a distinct SSRC. RTP and QoS RTP does not provide any mechanism to ensure timely delivery of data or provide other quality of service guarantees. RTP encapsulation is only seen at the end systems: it is not seen by intermediate routers. Routers providing best-effort service do not make any special effort to ensure that RTP packets arrive at the destination in a timely matter. SIP: Session Initiation Protocol • All telephone calls and video conference calls take place over the Internet • People are identified by names or e-mail addresses, rather than by phone numbers. • You can reach the callee, no matter where the callee roams, no matter what IP device the callee is currently using. SIP Services Setting up a call Provides mechanisms for caller to let callee know she wants to establish a call Provides mechanisms so that caller and callee can agree on media type and encoding. Provides mechanisms to end call. Determine current IP address of callee. Maps mnemonic identifier to current IP address Call management Add new media streams during call Change encoding during call Invite others Transfer and hold calls SIP messages can be sent over TCP or UDP; Default SIP port number is 5060. SIP is a single component. Works with RTP, but does not mandate it. Can be combined with other protocols and services.








