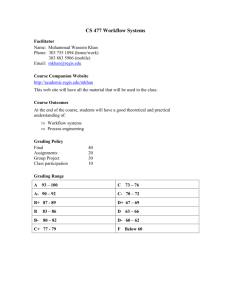
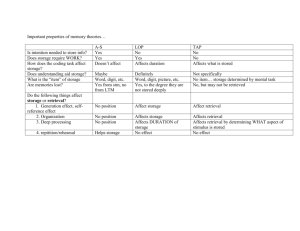
A Summary of the Top Papers, Key Researchers, Important Theories
advertisement

A Summary of the Major Issues, Important Theories, Top Papers, Key Researchers, and Future Research Problems of Management Information Systems By Dongjoo Kang, Fang Chen, Haidong Bi, Inder Singh, James Hwang, Jennifer Xu, Jing Zhang, Jinwei Cao, Jongseo Kim, Kathy Broneck, Matt Hacking, Ming Lin, Theo Song, Wei Gao, Wingyan Chung, Yunchu Huang, and Zan Huang For Dr. Nunamaker’s MIS 696A Course Fall Semester 2000 Table of Contents: MIS Model .......................................................................................................................... 1 Artificial Intelligence .......................................................................................................... 2 Important Theories and Trends ....................................................................................... 2 Future Research .............................................................................................................. 2 Key People ...................................................................................................................... 3 Herbert A. Simon ........................................................................................................ 3 John McCarthy ............................................................................................................ 3 Raj Reddy.................................................................................................................... 3 Edward A. Feigenbaum .............................................................................................. 4 Roger C. Schank ......................................................................................................... 4 Hsinchun Chen ............................................................................................................ 4 Key Papers ...................................................................................................................... 4 CMC/HCI/Communication/Visualization .......................................................................... 6 Introduction ..................................................................................................................... 6 Most Important Theories................................................................................................. 6 Key Issues, Conflicts, And Major Research Problems ................................................... 6 Key Researchers.............................................................................................................. 6 Frank Biocca ............................................................................................................... 6 Robert Kraut................................................................................................................ 6 Jakob Nielsen .............................................................................................................. 7 Judy Olson .................................................................................................................. 7 Ben Shneiderman ........................................................................................................ 7 Sherry Turkle .............................................................................................................. 8 Joseph Walther ............................................................................................................ 8 Suzie Weisband........................................................................................................... 8 Key Papers ...................................................................................................................... 8 Computing Policy ............................................................................................................. 11 Introduction ................................................................................................................... 11 Most Important Theories............................................................................................... 11 Key Issues, Conflicts, and Major Research Problems .................................................. 11 Key Researchers............................................................................................................ 13 Barbara Simons ......................................................................................................... 13 Peter G. Neumann ..................................................................................................... 13 Seymour E. Goodman ............................................................................................... 13 Eli M. Noam.............................................................................................................. 14 Robert Kling.............................................................................................................. 14 Peter J. Denning ........................................................................................................ 15 Dorothy E. Denning .................................................................................................. 15 Pamela Samuelson .................................................................................................... 15 Sharon Eisner Gillett ................................................................................................. 16 Key Papers .................................................................................................................... 16 Database ............................................................................................................................ 18 Introduction ................................................................................................................... 18 Key Theories ................................................................................................................. 18 i Key Issues ..................................................................................................................... 18 Future Research ............................................................................................................ 18 Key Researchers............................................................................................................ 19 Peter P. Chen ............................................................................................................. 19 Edgar F. Codd ........................................................................................................... 19 Won Kim................................................................................................................... 19 Stuart E. Madnick ..................................................................................................... 19 Salvatore T. March.................................................................................................... 20 Sudha Ram ................................................................................................................ 20 Joseph S. Valacich .................................................................................................... 21 Key Papers .................................................................................................................... 21 E-Commerce ..................................................................................................................... 23 Introduction ................................................................................................................... 23 Key Issues, Conflicts, and Major Research Problems .................................................. 23 Key Researchers............................................................................................................ 24 Lynda M Applegate .................................................................................................. 24 Andrew B. Whinston ................................................................................................ 24 Vladimir Zwass ......................................................................................................... 24 Yannis Bakos ............................................................................................................ 25 Haim Mendelson ....................................................................................................... 25 Key papers .................................................................................................................... 25 Group Support System (GSS) ........................................................................................... 27 Introduction and Key Theories ..................................................................................... 27 Key Issues and Conflicts ............................................................................................... 27 Major Research Problems in the Future........................................................................ 27 Key Researchers............................................................................................................ 28 Jerry DeSanctis ......................................................................................................... 28 R. Brent Gallupe ....................................................................................................... 28 Sara Kiesler ............................................................................................................... 28 Jay F. Nunamaker, Jr. ............................................................................................... 29 Wanda J. Orlikowski................................................................................................. 29 Judy Olson ................................................................................................................ 29 Sirkaa L. Jarvenpaa ................................................................................................... 30 Douglas R. Vogel ...................................................................................................... 30 Key Papers .................................................................................................................... 30 Information Economics ..................................................................................................... 33 Key Issues and Conflicts ............................................................................................... 33 Most Important Theories............................................................................................... 33 Key Researchers............................................................................................................ 34 Erik Brynjolfsson ...................................................................................................... 34 Charles H. Kriebel .................................................................................................... 34 Tridas Mukhopadhyay .............................................................................................. 34 Andrew B. Whinston ................................................................................................ 34 Key papers .................................................................................................................... 34 Information Retrieval ........................................................................................................ 38 Key Issues ..................................................................................................................... 38 ii Trends ........................................................................................................................... 38 Key People .................................................................................................................... 38 Gerard Salton ............................................................................................................ 38 Karen Sparck Jones ................................................................................................... 38 Gary Marchionini ...................................................................................................... 39 Edward A. Fox .......................................................................................................... 39 W. Bruce Croft .......................................................................................................... 39 Key Papers .................................................................................................................... 39 Knowledge Management .................................................................................................. 41 Introduction ................................................................................................................... 41 Categories of Knowledge Management Research ........................................................ 41 Key Theories and Methodologies ................................................................................. 42 Key Issues ..................................................................................................................... 42 Future Research Trends ................................................................................................ 42 Key Researchers............................................................................................................ 42 Christine L. Borgman................................................................................................ 42 Hsinchun Chen .......................................................................................................... 42 W. Bruce Croft .......................................................................................................... 43 Daniel E. O'Leary ..................................................................................................... 43 Gerard Salton ............................................................................................................ 43 Key Articles .................................................................................................................. 43 Operation Research ........................................................................................................... 46 Introduction ................................................................................................................... 46 Key People .................................................................................................................... 46 Hau L. Lee ................................................................................................................ 46 Marshall Fisher ......................................................................................................... 46 James B. Orlin ........................................................................................................... 47 George Nemhauser.................................................................................................... 47 Ellis Johnson ............................................................................................................. 47 Moshe Dror ............................................................................................................... 47 Key Papers .................................................................................................................... 47 Social/Ethical/Psychological Issues .................................................................................. 50 Introduction ................................................................................................................... 50 Most Important Theories............................................................................................... 50 Key Issues, Conflicts, and Major Research Problems .................................................. 50 Key Researchers............................................................................................................ 51 Mary J. Culnan .......................................................................................................... 51 Sara Kiesler ............................................................................................................... 51 Robert Kling.............................................................................................................. 51 Donald Norman ......................................................................................................... 51 Gary Olson ................................................................................................................ 52 Lee Sproull ................................................................................................................ 52 Key Papers .................................................................................................................... 52 Supply Chain Management ............................................................................................... 55 Most Important Theories............................................................................................... 55 Key Issues and Conflicts ............................................................................................... 55 iii Key researchers ............................................................................................................. 56 Gerard P. Cachon ...................................................................................................... 56 Fangruo Chen ............................................................................................................ 56 Hau L. Lee ................................................................................................................ 56 Paul H. Zipkin ........................................................................................................... 56 Key papers .................................................................................................................... 56 Systems Analysis and Design ........................................................................................... 59 Key Issues ..................................................................................................................... 59 Key Researchers............................................................................................................ 59 Tom DeMarco ........................................................................................................... 59 Grady Booch ............................................................................................................. 59 Michael Fagan ........................................................................................................... 60 Roger S. Pressman .................................................................................................... 60 Watts S. Humphrey ................................................................................................... 60 Edward Yourdon ....................................................................................................... 61 Key Papers/Books ......................................................................................................... 61 Telecommunication........................................................................................................... 63 Key Theories and Issues ............................................................................................... 63 Future Work .................................................................................................................. 63 Key Researchers............................................................................................................ 63 Robert E. Kahn.......................................................................................................... 63 Ted Nelson ................................................................................................................ 64 David Clark ............................................................................................................... 64 Deborah Estrin .......................................................................................................... 65 Roch Guerin .............................................................................................................. 65 Key Articles .................................................................................................................. 65 Workflow .......................................................................................................................... 68 Introduction ................................................................................................................... 68 The Evolution of Workflow .......................................................................................... 68 Trends ........................................................................................................................... 68 Key People .................................................................................................................... 69 Christoph Bussler ...................................................................................................... 69 Clarence Ellis ............................................................................................................ 69 Stefan Jablonski ........................................................................................................ 69 Amit P. Sheth ............................................................................................................ 69 J. Leon Zhao.............................................................................................................. 69 Key Papers .................................................................................................................... 70 Appendix A ....................................................................................................................... 72 iv MIS Model Management Information Systems is one of the most dynamic fields of study in academia. In comparison to other fields of study, it is a young, applied research discipline. However, what exactly is MIS? Elements of MIS may include computerbased systems, networks, people, processes, data, and software. This paper proposes that MIS is a new and previously unknown junction of reference disciplines. Many reference disciplines tend to conduct more basic research while MIS performs more applied research. The reference disciplines for MIS include Electrical and Computer Engineering, Computer Science, Management and Organizational Behavior, Systems and Industrial Engineering, Cognitive Psychology, and Economics. How does MIS relate to reference disciplines? Some reference disciplines, such as accounting, management, and economics, are related to business and compete more directly with MIS for resources and credibility. However, MIS does something no reference discipline does, or it wouldn't exist at all! As will be shown by the following review of major issues, important theories, top papers, key researchers, and future MIS research areas, MIS integrates many disciplines. MIS CS KM AI IR DB Telecom EC EE ORG GSS SS WF CMC/HCI/VIS Soc/Eth/Psy Policy Info Econ ECON OR MS Overview of MIS Artificial Intelligence Important Theories and Trends The original goal of AI (Artificial Intelligence) is to understanding and implementing intelligence. Herbert A. Simon further paints a broad picture of AI as a discipline constantly pursuing computational creations that challenge the uniqueness of biologically grounded intelligence. John McCarthy gives 12 branches of AI, namely, logic, learning, searching, representation, pattern recognition, inference, common sense knowledge, planning, epistemology, ontology, heuristics, and genetic programming. The controversies of AI fall into the following three major categories: (1) Knowledge representation and reasoning: A longstanding view of the role of logic in AI is that logic is an abstracted, hence simpler form of natural language. Thus it provides an ideal medium for a first approximation. This view is attacked with a variety of arguments [Wolfgang Bibel]. Drew McDermott argues that AI’s success arises not from sophisticated representation and reasoning methods, but rather from simple representations and tractable algorithms. Another controversy concerning knowledge representation and reasoning is whether intelligence is derived primarily from logical reasoning or from knowledge. The controversy is not about whether common sense is necessary but how much it should be built into the logic or into the knowledge base [Bruce Buchanan]. (2) Machine learning: The problem is whether computers should attempt to model how people or whether computers should follow methods did that no person things that no person could ever do and that might actually improve on people. [Roger Schank]. Oliver Selfridge suggests that AI software should be more concerned with being changeable than with satisfying specifications. (3) The practice of AI: There is a conflict between methodology-driven and phenomenon-driven research in AI, as well as the conflict between quantitatively valuable research and the more creative and often less quantifiable research necessary for a constantly growing discipline [Jerry Feldman]. Future Research (1) The decline in complex knowledge representations and the success of prepositional or probabilistic competitors [Drew McDermott]; (2) Machine learning and automation of deductive reasoning [Donld Michie]. 2 (3) Building intelligent systems that will let people access and utilize enormous amounts of information generated by modern societies in various forms for making informed decisions [Ryszard Michalski]. (4) Multi-Agent Systems, application for data mining, knowledge Management. Key People Herbert A. Simon Description Professor, Carnegie-Mellon University, Pittsburgh, PA Alfred Nobel Memorial Prize in Economic Sciences in 1978 for "pioneering research into the decision-making process within economic organizations” ACM: AM Turing Award, 1975 Research interests Building and testing theories of human cognition, using computer simulation models. The usage of different representations to draw inferences from information, especially reasoning from diagrammatically and pictorially presented information, and comparing the effectiveness for communication purposes of different representations. John McCarthy Description Professor of Computer Science at Stanford University The inventor of LISP. ACM/A.M. Turing Award, 1971. Research Interests His research is mainly in artificial intelligence. Long ago he originated the Lisp programming language and the initial research on general purpose time-sharing computer systems Raj Reddy Description Herbert A. Simon University Professor, Computer Science and Robotics in the School of Computer Science at CMU. He served as the founding Director of the Robotics Institute from 1979 to 1991. He served as the Dean of School of Computer Science at CMU from 1991 to 1999. He was awarded the ACM Turing Award in 1994 Research Interests Dr. Reddy's research interests include the study of human-computer interaction and artificial intelligence. His current research projects include spoken language systems; invisible computing, gigabit networks; universal digital libraries; and distance learning on demand 3 Edward A. Feigenbaum Description Professor of Computer Science and Co-Scientific Director of the Knowledge Systems Laboratory at Stanford University. Dr. Feigenbaum served as Chief Scientist of the United States Air Force from 1994 to 1997. He was a recipient of the 1994 ACM Turing Award. Research Interests Knowledge-Based Systems Research and Applications; Computer Industry Research; Defense Technology and Technology Policy Roger C. Schank Description Roger C. Schank, director of the Institute for the Learning Sciences (ILS) at Northwestern University, is a leader in the field of artificial intelligence and multimedia-based interactive training. Research Interests His work stresses the value of learning from experts, developing skills rather than perfecting routines, and applying the benefits of "just-in-time" training Hsinchun Chen Background Professor, MIS Department. University of Arizona He received the Ph.D. degree in Information Systems from New York University in 1989. He is author of more than 70 articles covering semantic retrieval, search algorithms, knowledge discovery, and collaborative computing in leading information technology publications. Research Interests Digital Libraries, Knowledge Management, Multi-lingual and Distributed Information Retrieval Key Papers Computer Machinery and Intelligence, A. M. Turing This paper address the question of “Can machine think?” Turing takes a behavioristic posture relative to the question. The question is to be decided by an unprejudiced comparison of the alleged “thinking behavior” of the machine with normal “think behavior” of human beings. hw propose an experiment-commonly called “Turing test”-in which the unprejudiced comparison could be made. Though the test has flaws, it is the best that has been proposed to date. Understanding The Natural and the Artificial Worlds, Herbert A. Simon. The Science of Artificial Intelligence, 1996, pp 1-24. Understanding the natural and the artificial worlds, The psychology of thinking: embedding artifice in nature, The science of design: creating the artificial, The 4 architecture of complexity. "Artificial" denotes systems that have a given form and behavior because they adapt to their environment in reference to goals or purposes. Some Philosophical Problems from the Standpoint of Artificial Intelligence, John McCarthy and Pat Hayes, 1969 in Machine Intelligence 4. It is the basic paper on situation calculus. This paper looks at some philosophical issues concerning artificial intelligence, which includes how the concept of ability and belief could be given formal definition in the metaphysically adequate automaton model and indicates the correspondence between these formal concepts and the corresponding commonsense concepts, construction of epistemologically adequate system. Instead of given formal definitions, formal notions are introduced by informal natural language descriptions with examples of their use to describe situations and possibilities for action they present. Intelligence without Robots, oren Etzioni, AI Magazine, Winter 1993, vol. 14, no. 4, pp.713. In his recent papers, entitled "Intelligence without Representation and "Intelligence without Reason," Brooks argues for studying complete agents in real-world environments and for mobile robots as the foundation for AI research. This article argues that, even if we seek to investigate complete agents in real-world environments, robotics is neither necessary nor sufficient as a basis for AI research. The article proposes real-world software environments, such as operating systems or databases, as a complementary substrate for intelligent-agents research, and considers the relative advantages of software environments as test beds for AI. Natural Language Processing, Roger C. Schank, Eugene Charniak, Yorick Wilks, Terry Winograd, William A. Woods: IJCAI 1977: 1007-1013 5 CMC/HCI/Communication/Visualization Introduction Computer-mediated-communication (CMC), human-computer-interaction (HCI), communication and visualization of design interface impacts the research within MIS. This body of literature’s research tries to understand how humans interact and communicate with one another using different computerized technologies. It is important to understand how people interact with the computer and with one another in order to better understand prototypes that MIS researchers may design. The communication amongst these modes needs to also be taken into consideration as research has suggested that decisions, communication, and usage of technologies differ via computers than in face-to-face (FTF) settings. Most Important Theories Some important theories, hypothesis, and models to come from this area of research are Interactivity Model, The Postrepresentational Model (HCS), Artificial Morality, SIDE Theory. Key Issues, Conflicts, And Major Research Problems The current key issues in this area are the visualization of dynamic processes in network and the interaction metaphor for dynamic processes. It consists of the integration of tactile sensing, vision, and sound. Key Researchers Frank Biocca Contact Information 404 Communication Arts and Sciences Michigan State University Department of Communications East Lansing, MI (517) 355-5073; e-mail: biocca@msu.edu Research areas Dr. Biocca studies computer design and visualizations. He is a leader in research surrounding multi-modal sensory information. The focus of his research is being able to understand if when interfaces become more anthropomorphic and/or interactive if users engage in higher levels of consciousness. Robert Kraut Contact Information 3515 Newell-Simon Hall Carnegie Mellon University 6 5000 Forbes Avenue Pittsburgh, PA 15213-3891 (412) 268-7694; e-mail: robert.kraut@cmu.edu Research areas Dr. Kraut studies emerging information technologies and how they in turn affect human communication. Specifically, he focuses on individuals and organizations performance in coordinating tasks, prototyping designs, Video communication systems, and technology on quality of work. Currently, Dr. Kraut is working on the influence of networks and communication technology. He is also involved in the HomeNet project. Jakob Nielsen Contact Information 2704 Fairbrook Dr. Mountain View, CA 94040 E-mail: jakob@useit.com Research areas Currently he is working on the designs of websites and information architecture and task design. He has published in the ACM, serves on journal editorial boards, and was listed as one of the web’s most influential people. Judy Olson Contact Information University of Michigan 701 Tappan Street C-2420 Bus. Ad. Ann Arbor, MI. 48109-1234 (734) 647-4606; e-mail: jsolson@umich.edu Research areas Her focus is on Human-computer-interaction and the design and evaluation issues of software. She has worked for Bell laboratories and is currently a Professor in the School of Information. Her achievements include over 50 books and articles involving human psychology, computers, and visualization design. Ben Shneiderman Contact information Department of Computer Science University of Maryland College Park, MD 20742 (301) 405-2680; e-mail: ben@cs.umd.edu Research areas Dr. Shneiderman’s research pertains to areas involving human-computer-interaction and psychology. He also participates in visualization information representation and design. His achievements include being a Fellow of the ACM, the founding director of Human Computer Interaction Laboratory, and hosting an annual satellite presentation of User Interface Strategies. 7 Sherry Turkle Contact Information Program in Science, Technology, and Society, MIT E51-296c 77 Massachusetts Ave. Cambridge, MA 02139-4307 (617) 253-4068; e-mail sturkle@media.mit.edu Research areas Dr. Turkle has been researching communication on the Internet along with psychological impacts of computational objects. Her interests have involved computer culture, sociology, and psychology with regards to new technologies, specifically the Internet. Her research has been funded by organizations such as the NFS, Guggenheim Foundation, and the Rockefeller Foundation. Joseph Walther Contact Information Dept. of Language, Literature, and Communication Rensselaer Polytechnic Institute 110 8th Street Troy, NY 12180-3590 (518) 276-2557; e-mail: walthj@rpi.edu Research areas His research focuses on computer-mediated-communication and its effects in teaching, teams and social relationships. He draws in psychological and social issues of Internetbased communication into collaborative work across countries. Dr. Walther has won awards in NCA for his works on technological communities and interpersonal communication. Suzie Weisband Contact Information Department of Management Information Systems Eller College of Business and Public Administration The University of Arizona Tucson, Arizona 85721 (520) 621-8303; E-mail: weisband@bpa.arizona.edu Research areas Dr. Weisband’s research includes social and behavioral impacts of technology on people. She has participated in research involving communication among groups using various technological platforms and interactivity. Dr. Weisband has also been involved in GSS research, F-t-F interactions, and melding disciplines such as MIS, Communication, Sociology, and Psychology into her research. Key Papers 8 Biocca, F., Kim, T., and Levy, M. R. (1995). Chapter 1: The vision of virtual reality. In F. Biocca’s Communication in the age of virtual reality (pp. 3-14). Hillsdale, NJ: Erlbaum. The chapter looks at if virtual reality would make for a better medium of communication. They suggest that VR is the ultimate form of media technology. If this is the case, MIS researchers need to look at different areas of design integrating VR. Daft, R. L. and Lengel, R. H. (1986). Organizational information requirements, media richness and structural design. Management Science, 32(5), 554-571. The article primarily discusses that uncertainty and equivocality are the primary factors why organization processes information. It attempted to integrate equivocality with uncertainty and argue that structural characteristics are used to help organization to cope with these two factors. The authors proposes models that show how organization can be design to meet the information needs of technology, interdepartment relations, and the environment. Galagher and Kraut. (1994). Computer mediated communication for intellectual teamwork. Information Systems Research, 5(2), 110-138. This article analyzes contingency theory’s prediction that using computer mediated communication to accomplish complex collaboration work will be difficult, especially for tasks that require interactive, expressive communication. The author conducted experiments with sixty-seven three person groups of students that completed two collaborative writing projects under either computer only, computer plus phone or face to face communications. The findings tend to confirm the contingency hypothesis regarding the difficulty of accomplishing work that involves ambiguous goals, multiple perspectives, and information that is susceptible to multiple interpretations without an interactive multiperson communication medium, such as face-to-face meetings. Kramer, R. and Tyler, T. (1996). Trust in organizations: Frontiers of theories and research. Sage Publications Laudauer, T. K. (1995). The troubles with computers: Usefulness, usability, and productivity. MIT Press, Cambridge, MA. The book explains and illustrates why computers are in trouble and why investments on computing have not resulted in productivity. The author argues that the conditions are the result of the fact that computers rarely improve efficiency of the information work because they are too hard to use and do too little that is sufficiently useful. The author proposed that the use of user centered development technique through task analysis, iterative design, trial use, and evaluation, computer systems can be powerful tools. Reeves and Nass. (1996). The media equation : How people treat computers, television, and new media like real people and places. Cambridge University Press, Cambridge, UK. The book involves numerous studies conducted by Reeves and Nass to understand how people treat media such as computers, television, and other new technologies. They found that people tend to have biases and opinions about the medium they are interacting with. Changes in voice or display can result in the changes of attitudes towards the mechanism 9 they are interacting with. While there has been much academic discussion as to whether or not the results found in the book are correct, it poses an area of research that had not been looked at before that MIS researchers should be aware of. If there is truth to the findings of people, then how MIS designs systems needs to be wary of the findings. If people respond in different ways to small characteristics such as male versus female voice and credibility attributions of interactions that ensue, then small design issues of choosing voice automated systems can impact user satisfaction. Sproull, L. and Kiesler, S. (1991). Connections: New waysof working in the networked organization. MIT Press, Cambridge, MA. Within the book, the authors demonstrate the effect of new technologies in organizational communication and how people's thinking and working habits change in lieu of these technologies. They give guideline criteria as to how people utilize technology, such as email, to form better networks and how visions and goals of the organization should in turn be shaped. The book gives a good basis for understanding users within an organization, what impact inventions can have on a user, and the different characteristics of how people use the technology. Since MIS involves organizations and communicative functions within, understanding how their prototypes and designs effect an organization and its people is beneficial. When designing prototypes, audience characteristics need to be taken into consideration. Walther, J. (1995). Relational aspects of CMC: Experimental observations over time. Organization Science, 6( 2), 186-203. This article looked at computer conferencing and its effects on people's perceptions of the relational messages found within. Dr. Walther suggests that past research about CMC relational research is inconsistent and that some areas of interpersonal communication are actually better when done over CMC than in face-to-face groups. It is important for MIS researchers to understand when it is better to engage in group work over CMC versus face-to-face to achieve better results in their proposed designs for task related situations. 10 Computing Policy Introduction The discipline is not well established till present. Papers in this field can be found in many journals such as Communication of the ACM, Computers andSociety, Science, Technology and Human Values, and etc. But there is no key journal for this filed, which is also true for debate about the social roles of information technology as mentioned in Rob Kling’s book, Computerization and Controversy: Value Conflicts and Social Choices. The discipline is closely related to research in social and ethics issues of computing, which is come from the close relationship between social science, ethics and policy science. Rob Kling divided theoretical perspectives adopted by Social Analysts of Computing into two major categories, and Policy research was included into this scheme. Social Analysis of Computing Systems Rationalism Rational Structural Human Relations Segmented Institutionalism Interactionist Organizational Politics Class Politics The suitable definition for “policy” from Webster for this domain is “a high-level overall plan embracing the general goals and acceptable procedures especially of a governmental body ”. Policy issues research is different from social and ethics issues research. Social and ethics research focus on the roles of information technology in social or ethical settings, and policy research focuses on the high-level relationship between different participants/actors in the social environment, and power and goal are the key issues. Government is usually involved in research of this discipline, and because of the difference between different countries on social organization and government roles, international view should be taken to describe the who picture. Most Important Theories Theories in this field is from economics, policy and technology, and it is hard to address key theories for this not well defined field. Key Issues, Conflicts, and Major Research Problems Universal Access Intellectual Property Encryption and Computer Security Free Speech and the Internet Funding for Scientific Research 11 Privacy Electronic Commerce: Taxation, Supply chain/Industrial structure Policy aspects (WTO, International Telecommunication Union, Federal Communications Commission, Harmonization) Regulatory Frameworks General Political Milieu The role of the state/government From TIPI(Telecommunications and Information Policy Institute, University of Texas, Austin TX 78712, USA) Emerging Issues in the International Telecommunications and Information Environment: Research Topics 1. TELECOMMUNICATIONS * A. Policy Aspects * World Trade Organization * International Telecommunication Union * Federal Communications Commission * Special focus: Harmonization * B. Access and Equity * Universal Access * Digital Divide * C. Subsidies * D. Regulatory Frameworks * E. General Political Milieu * F. The role of the state/government * G. Structure * H. Rates * I. Procurement * J. Technologies * Convergence * Innovation * K. Services * 2. INNOVATION CLUSTERS/TECHNOPOLES * A. Space and Place * B. Agglomeration * Institutional Frameworks * Other importance factors include: * Cultural Conditions * Demand * "Environmental" Conditions * Labor * C. Agglomeration is not a sufficient condition * D. Software Development * 3. ELECTRONIC COMMERCE * A. Space/Place * 12 B. Taxation * C. Supply chain/ Industrial structure * D. Technological Bases * Transaction Security * Privacy * E. Intellectual Property * Key Researchers Barbara Simons simons@acm.org , http://barbara.simons.org Dr. Simons was elected President of ACM in 1998, the same year in which she also won the Electronic Frontier Foundation Pioneer Award. Selected by c-net in 1995 as one of its 26 Internet "Visionaries," and named one of the "Top 100 Women in Computing" by Open Computing in 1994, she holds several patents and has authored numerous technical papers. Dr. Simons is a member of the President's Export Council's Subcommittee on Encryption and is also a Fellow of ACM and the American Association for the Advancement of Science. Education Ph.D. in computer science from the University of California, Berkeley, in June 1981 thesis advisor Richard Karp. My dissertation, Scheduling with Release Times and Deadlines, solved a major open problem in scheduling by developing the first known algorithm for the problem. Research areas Policy Issues, Scheduling Theory, Compiler Optimization, Fault Tolerant Distributed Computing, Communicating Sequential Processes Peter G. Neumann Principal Scientist at SRI International Computer Science Laboratory http://www.csl.sri.com/neumann/neumann.html Neumann@csl.sri.com Education He spent eight years at Harvard (1950-58, with his A.B. in Math in 1954, S.M. in Applied Math in 1955, and PhD in 1961 after returning from his two-year Fulbright in Germany (1958-60), where he received the German Dr rerum naturarum in 1960. Research areas His main research interests continue to involve security, crypto applications, overall system survivability, reliability, fault tolerance, safety, software-engineering methodology, systems in the large, applications of formal methods, and risk avoidance. Seymour E. Goodman goodman@cc.gatech.edu Seymour (Sy) E. Goodman has been Professor of MIS (1981) and a member of the Center for Middle Eastern Studies at the University of Arizona, and Carnegie Science Fellow (1994) and head of the Program on the Information Technologies and International Security at the Center for International Security 13 and Arms Control, Stanford University. Earlier tenured and visiting appointments have been at the University of Virginia (Applied Mathematics and Computer Science), Princeton University (Mathematics and the Woodrow Wilson School of Public and International Affairs), and the University of Chicago (Economics). Education He did his undergraduate work at Columbia University, and obtained his Ph.D. from the California Institute of Technology. Research Areas Prof. Goodman's research interests include international developments in the information technologies (IT), technology diffusion, IT and national security, and related public policy issues. Areas of geographic interest include the former Soviet Union and Eastern Europe, Latin America, the Middle East, Southeast Asia, and parts of Africa. Earlier research had been in areas of statistical and continuum physics and combinatorial algorithms. Eli M. Noam noam@columbia.edu http://www.citi.columbia.edu/elinoam Director, Columbia University Institute for Tele-Information; 1983-1987, 1991present Professor of Finance and Economics, Columbia Business School; 1976-present Education Harvard: A.B. 1970 (Phi Beta Kappa); A.M. 1972; J.D. 1975; Ph.D. Economics, 1975, Dissertation adviser: Martin Feldstein. Research Areas Communications, information, public choice, public finance, and general regulation. Robert Kling kling@indiana.edu http://www.slis.indiana.edu/kling/ In August 1996, he moved to Indiana University - Bloomington as Professor of Information Science and Information Systems. He directs a new interdisciplinary research center at IU, the Center for Social Informatics and also directs the Master of Information Science degree program. Between 1966 and 1971 he held a research appointment in the Artificial Intelligence Center at the Stanford Research Institute. He held his first professorship in Computer Science at the University of Wisconsin-Madison between 1970-1973. He was on the faculty of UC-Irvine from 1973-1996 and held professorial appointments at UCI's Center for Research on Information Technology and Organizations and Graduate School of Management. Education He completed his undergraduate studies at Columbia University (1965) and his graduate studies, specializing in Artificial Intelligence, at Stanford University (1967, 1971). Research Areas Social Informatics; Organizational Informatics; Information Systems; Information Technology and Social Change 14 His research focuses upon the social consequences of computerization and the social choices that are available to people. He has studied these issues in and around organizations that have invested in various information systems, desktop computing, computerized manufacturing environments, digital libraries, instructional computing, etc. He believes that we have to understand information technologies in terms of their associated social structures and politics, and in meaningful social contexts -- not just as "information tools." Peter J. Denning pjd@cs.gmu.edu http://www.cs.gmu.edu/faculty/denning/ Peter J. Denning is Professor of Computer Science and University Coordinator for Process Reengineering at George Mason University. Since joining GMU in 1991, he served as vice provost for continuing professional education, associate dean for computing, and chair of the Computer Science Department in the School of Information Technology and Engineering. He is founding director emeritus of the Hyperlearning Center, formerly the Center for the New Engineer, which he founded in 1993. Research Areas Operating Systems, Workflow Management, High Performance Computing, Security, Performance Modeling Dorothy E. Denning denning@georgetown.edu. http://www.cs.georgetown.edu/~denning/ Dorothy E. Denning is professor of Computer Science at Georgetown University and director of the Georgetown Institute for Information Assurance. She is also affiliated with the Communication, Culture and Technology program and the Science and Technology in International Affairs program. Her area of specialty is information warfare and information assurance. Research Areas Information warfare and information assurance Education B.A. and M.A. degrees in mathematics from the University of Michigan, Ph.D. degree in computer science from Purdue University Pamela Samuelson pam@sims.berkeley.edu http://www.sims.berkeley.edu/~pam/ Pamela Samuelson is a Professor at the University of California at Berkeley with a joint appointment in the School of Information Management and Systems and the School of Law. She is also Co-Director of the Berkeley Center for Law and Technology. Research Areas Intellectual Property Law, Copyright Law 15 Education Yale Law School: J. D. 1976, University of Hawaii at Honolulu: M. A. 1972, Political Science, B. A. 1971, History Sharon Eisner Gillett Sharon Eisner Gillett is the Executive Director of the MIT Internet and Telecoms Convergence Consortium and a Research Associate at the MIT Center for Technology, Policy, and Industrial Development. Ms. Gillett is the author of numerous articles about the Internet and telecommunications, including, "Connecting Homes to The Internet: An Engineering Cost Model of Cable vs. ISDN," and "The Self-Governing Internet: Coordination by Design" (with Mitchell Kapor). From 1982-92 she worked as a software engineer and manager at BBN Communications Corp. and Thinking Machines Corp. Research Telecommunication Policy Education Ms Gillett received her MBA and MS in Technology and Policy from MIT in 1995, and her AB in Physics from Harvard-Radcliffe in 1982. Key Papers Social Analyses Of Computing - Theoretical Perspectives In Recent Empirical-Research Kling R. Computing Surveys. 12: (1) 61-110 1980, 172. The Global Diffusion Of The Internet - Patterns And Problems Goodman Se, Press Li, Ruth Sr, Rutkowski Am Communications Of The ACM 37: (8) 27-31 Aug 1994 14 This paper concerns about the international diffusion of the internet technology. Several models are identified to cover most of the forms of international proliferation of Internet technology. Patterns identified include building national backbones, grass root nets, commercial carriers and resellers. Issues about the impediments to network diffusion are also addressed in this paper. Computerization And Social Transformations. Kling R. Science Technology and Human Values. 16: (3) 342-367 SUM 1991, 31. This paper examines the relationship between the use of computer-based systems and transformations in parts of the social order. Answers to this question rest heavily on the way computer-based systems are consumed -- not just produced or disseminated. The discourse about computerization advanced in many professional magazines and the mass media is saturated with talk about "revolution" -- and yet, substantial social changes are often difficult to identify in carefully designed empirical studies. The paper examines qualitative case studies of computerization in welfare agencies, urban planning, accounting, marketing, and manufacturing to examine the ways that computerization alters social life in varied ways: sometimes restructuring relationships and in other cases, reinforcing existing social relationships. The paper also examines some of the theoretical 16 issues in studies of computerization, such as drawing boundaries. It concludes with some observations about the sociology of computer science as an academic discipline. 17 Database Introduction Database systems continue to be a key area in many fields including business, computer science, and engineering. Representing knowledge within a computer is one of the central challenges of the field. Database research has focused primarily on this fundamental issue. Many universities have faculty investigating these problems and offer courses that teach the concepts developed by this research program. Today, the Internet is considered by many to be one large database. Database research has migrated from a study of data modeling for a centralized data store, to studies on highly distributed, heterogeneous, dynamic, and enormous collections of multimedia data. Key Theories E.F. Codd and Peter Chen developed several early key theories in database research. E.F. Codd developed the relational model for databases and Peter Chen introduced the entityrelationship model. These theories are covered in greater detail under the respective researcher. More recent database theories adopt an object-oriented design and respond to the effects of distributed databases, such as the Internet, and larger and faster data storage capabilities. Key Issues There continues to be active and valuable research on representing and indexing data, adding inference to data search, compiling queries more efficiently, executing queries in parallel, integrating data from heterogeneous data sources, analyzing performance, and extending the transaction model to handle long transactions and workflow (transactions that involve human as well as computer steps). The availability of very-large-scale (tertiary) storage devices has prompted the study of models for queries on very slow devices. Future Research There is great interest and direction in unifying object-oriented concepts with the relational model. New data types (image, document, drawing) are best viewed as the methods that implement them rather than the bytes that represent them. By adding procedures to the database system, one gets active databases, data inference, and data encapsulation. This object-oriented approach is an area of active research in academe and in industry. Continuing research is creating the ideas and training the people for the next product generation. As storage devices continue to become larger and faster, new data models will need to be developed to efficiently represent and process the data. The development of ultra-high-density data storage such as holographic data storage is a promising innovation in the field of database research. 18 Key Researchers Peter P. Chen Contact Information Louisiana State University, Department of Computer Science 298 Coates Hall Baton Rouge, LA 70803, USA (225) 578-2483; chen@bit.csc.lsu.edu Research areas Dr. Chen is well known as the originator of the Entity-Relationship Model (ER Model), which serves as the foundation of many systems analysis and design methodologies, computer-aided software engineering (CASE) tools, and repository systems. Dr. Chen is currently a member of several XML working groups that are investigating the linkage between the hypertext concept and the main ERD concept. Edgar F. Codd Contact Information IBM Research Laboratory San Jose, California Research areas Dr. Codd invented the relational data model in a series of research papers published commencing in 1970. The relational data model is particularly well suited for business data management. In this model, data are organized into tables. The data can be manipulated using a relational algebra. SQL is a standard language for talking to a relational database. Dr. Codd also introduced the concept and rules of data normalization. Won Kim Contact Information CEO of Cyber Database Solutions, Inc., Austin, Texas won.kim@cyberdb.com Research Areas Dr. Kim’s research interests lie in object-oriented databases and modern database systems. He is a founder of UniSQL and recently published a white paper describing a framework with which to evaluate the completeness of a product's compliance with seven major categories of capabilities of object relational databases. Stuart E. Madnick Contact Information Address: E53-321 Department: School Of Management Title: John Norris Maguire Professor of Information Technology Email: smadnick@MIT.EDU Phone: (617) 253-6671 URL: http://mit.edu/smadnick/www/home.html 19 Research Areas Dr. Madnick’s current research interests include connectivity among disparate distributed information systems, database technology, software project management, and the strategic use of information technology. He is presently co-director of the PROductivity From Information Technology (PROFIT) Initiative and co-heads the Total Data Quality Management (TDQM) research program. He has been the Principal Investigator of a large-scale DARPA-funded research effort on Context Interchange which involves the development of technology that helps organizations to work more cooperatively, coordinated, and collaboratively. As part of this effort, he is the recent co-inventor on the patent applications "Querying Heterogeneous Data Sources over a Network Using Context Interchange" and "Data Extraction from World Wide Web Pages." He has been active in industry, making significant contributions as a key designer and developer of projects such as IBM's VM/370 operating system and Lockheed's DIALOG information retrieval system. He has served as a consultant to many major corporations, such as IBM, ATandT, and Citicorp. He has also been the founder or co-founder of several high-tech firms, including Intercomp (acquired by Logicon), Mitrol (acquired by General Electric's Information Systems Company), and Cambridge Institute for Information Systems (subsequently re-named Cambridge Technology Group), and currently operates a hotel in the 14th century Langley Castle in England. Salvatore T. March Contact Information University of Minnesota, Carlson School of Management 3-418 Humphrey Center (612) 624-2017 smarch@csom.umn.edu Research Areas Dr. March’s research interests lie in database design, information system development, and distributed systems. His current research includes distributed database design and methodology evaluation. Sudha Ram Contact Information Management Information Systems College of Business and Public Administration University of Arizona ram@bpa.arizona.edu Research Areas Dr. Ram's research deals with modeling and analysis of database and knowledge based systems for manufacturing, scientific and business applications. Her research has been funded by IBM, NCR, US ARMY, NIST, NSF, NASA, and ORD (CIA). Specifically, the research deals with interoperability among distributed and heterogeneous database systems, semantic modeling, data allocation, schema and view integration, intelligent agents and digital libraries for data management, and automated tools for database design. E-Business infrastructure and strategy is also one of her favored areas. 20 Joseph S. Valacich Contact Information College of Business and Economics Todd Hall 240D Washington State University Pullman, WA 99164-4736 jsv@wsu.edu (509) 335-1112 Research Interests His current research interests include electronic commerce, the diffusion of technology in organizations, group decision behavior, and distance learning. Key Papers E. F. Codd: A Relational Model of Data for Large Shared Data Banks. CACM 13(6): 377-387 (1970) Future users of large data banks must be protected from having to know how data is organized in the computer (the internal representation). Activities of users at terminals and most application programs should remain unaffected when the internal representation of data is changed and even when some aspects of the external representation are changed. Modifications to data representation will often be needed as a result of changes in query, update, and report traffic and natural growth in the types of stored information. Peter P. Chen: The Entity-Relationship Model: Toward a Unified View of Data. ACM Transactions on Database Systems: Vol. 1, Issue 1, Pages 9-36 (1976) A data model, called the entity-relationship model, is proposed in this model. This model incorporates some of the important semantic information about the real world. A special diagrammatic technique is introduced as a tool for database design. An example of database design and description using the model and the diagrammatic technique is given. Some implications for data integrity, information retrieval, and data manipulation are discussed. Salvatore T. March, M.J. Prietula: Form and Substance in Physical Database Design: An Empirical Study. Information Systems Research. December 1991 “Data model issues for object-oriented applications”; Jay Banerjee, Hong-Tai Chou, Jorge F. Garza, Won Kim, Darrell Woelk, Nat Ballou and Hyoung-Joo Kim; ACM Trans. Inf. Syst. 5, 1 (Jan. 1987), Pages 3 – 26 “Semantics and implementation of schema evolution in object-oriented databases”; Jay Banerjee, Won Kim, Hyoung-Joo Kim and Henry F. Korth; Proceedings of the ACM SIGMOD Annual Conference on Management of data, 1987, Pages 311 – 322 “A distributed object-oriented database system supporting shared and private databases”; Won Kim, Nat Ballou, Jorge F. Garza and Darrell Woelk; ACM Trans. Inf. Syst. 9, 1 (Jan. 1991), Pages 31 – 51 21 "Semantic Model Support for Geographic Information Systems", Sudha Ram with J. Park and G. Ball. IEEE Computer, Vol. 32, No. 5, May 1999, pp. 74-81. "Collaborative Conceptual Schema Design: A Process Model and a Prototype Systems", Sudha Ram with V. Ramesh. ACM Transactions on Information Systems, Vol. 16, No. 4, Oct. 1998, pp. 347-371. "Database Allocation in a Distributed Environment: Incorporating Concurrency Control and Queuing Costs", Sudha Ram with S. Narasimhan. Management Science Vol. 40, No. 8, August 1994. “Metadata Jones and the Tower of Babel: The Challenge of Large-Scale Semantic Heterogeneity”, Stuart E. Madnick. 1999 IEEE Meta-Data Conference, April 6-7, 1999 “Properties of storage hierarchy systems with multiple page sized and redundant data”; Chat-Yu Lam and Stuart E. Madnick; ACM Trans. Database Syst. 4, 3 (Sep. 1979), Pages 345 – 367 “Lessons learned from modeling the dynamics of software development”; Tarek K. Abdel-Hamid and Stuart E. Madnick; Commun. ACM 32, 12 (Dec. 1989), Pages 1426 – 1438 22 E-Commerce Introduction Electronic commerce technologies are the fundamental infrastructure for commerce, communication and communities in the digital age. Basic advancements in engineering and computer technologies are spawning an astounding array of new applications which extend the use of computers and networking into all aspects of economic, social and political activities. While the vision of a networked, digital society is most compelling, the continuing process of technological developments and applications poses a serious challenge in defining research priorities that sufficiently address both the emerging vision of the future and the need to foster and impart basic scientific body of knowledge. The goal of basic research in electronic commerce is to foster advances in related areas, to maximize the synergistic, to increase interdisciplinary understanding of how electronic commerce technologies affect market processes and welfare, and to assure that electronic commerce applications achieve their promised efficient outcomes. Key Issues, Conflicts, and Major Research Problems 1. Infrastructure and system architecture area: Current efforts are focused on developing secure and reliable transaction infrastructure and pricing regimes. Critical applications being researched and refined include search and recommendation algorithms that lay the foundation for commercial interactions. The lack of interoperability in system architecture and application software highlights the need for net-centric, component-based technologies. The areas for future research initiative focus on technologies and applications that facilitate real time interactions among users and computers, including the use of software agents and intermediaries, human-computer interface design, and system architecture for remote and real-time interactions. In addition to technology developments, adequate models and measurements must be developed to be informed about the status, performance and effect of the underlying system. 2. The interplay between technological infrastructure and commercial environment: This interplay results in a number of issues that have economic and social ramifications. For example, the digital online environment has made privacy and intellectual property rights the most discussed topic in electronic commerce. Nevertheless, current discussions are carried out in separate circles that focus on technological choices, legalities or other limited aspects of these issues. It is critical to understand emerging conflicts in a broader, interrelated solution space and to promote interdisciplinary dialogue and collaboration in order to provide guidance for design and rule making within the context of online environment. 23 Key Researchers Lynda M Applegate Harvard University Graduate School of Business Administration Web site: http://www.people.hbs.edu/lapplegate/research.html Research areas Lynda M. Applegate's research focuses on the influence of information technology on markets and organizations. Her findings on the evolution of electronic commerce and on the role of information technology as an enabler of flexible and adaptive organizational designs and innovative management control systems have been widely published in the Harvard Business Review, Management Systems Quarterly, Organizational Computing, Information Systems and Decision Processes, and Operations Research, among other journals. Applegate recently authored a custom-published casebook, Managing in an Information Age, and co-author of Corporate Information Systems Management: The Issues Facing Senior Executives. Andrew B. Whinston Center for Research in Electronic Commerce College and Graduate School of Business University of Texas at Austin Web site: http://crec.bus.utexas.edu/abw/main.html Research areas His current research spans various realms of Electronic Commerce, its impact on business protocols and processes, on organizational structure and corporate networks, electronic publishing, electronic education, complementarity of convergent computational paradigms and business value of IT. Through diverse initiatives, various aspects and consequences of the emergent economies over the Internet and corporate Intranets are studied. Vladimir Zwass School of Computer Science and Information Systems Fairleigh Dickinson University Web site: http://inside.fdu.edu/pt/zwass.html He is the Editor-in-Chief of the Journal of Management Information Systems, a leading journal in the field, and of the International Journal of Electronic Commerce, the first scholarly journal fully devoted to E-commerce. Tridas Mukhopadhyay Professor of Industrial Administration Director, Institute for eCommerce Carnegie Mellon University http://www.gsia.cmu.edu/afs/andrew/gsia/ workproc/roster/fulltime/mukhopadhyay.html Prof. Mukhopadhyay's research centers on the business value of information, EDI technology, residential use of the Internet and software cost management. 24 Yannis Bakos Leonard N. Stern School of Business New York University Web site: http://www.stern.nyu.edu/~bakos/ Professor Bakos is an internationally acclaimed expert on electronic commerce, having pioneered research on the impact of information technology on markets, and in particular on how internet-based electronic marketplaces will affect pricing and competition. Professor Bakos is also currently studying pricing strategies for information goods. Haim Mendelson Codirector, center for electronic business and commerce Stanford University Web site: http://gobi.stanford.edu/facultybios/bio.asp?ID=104 Organizing for e-business, electronic commerce, electronic networks, financial markets Key papers 1. Malone, T. W., Yates, J., and Benjamin, R. I. (1987). Electronic Markets and Electronic Hierarchies. Communications of the ACM, 30(6), 484-497. By reducing the costs of coordination, information technology will lead to an overall shift toward proportionately more use of markets-rather than hierarchies-to coordinate economic activity. 2. Applegate, L. M., Holsapple, C. W., Kalakota, R., Radermacher, F. J., and Whinston, A. B. (1996). Electronic commerce: building blocks of new business opportunity. Journal of Organizational Computing and Electronic Commerce, 6(1), 1-10. There is much uncertainty in the emerging world of electronic commerce. This uncertainty spans a variety of areas-management, consumer behavior and technology-but this is good news. History provides numerous examples where market uncertainty has created potential for shaping new products, creating markets, and building a loyal customer base. A good case study of uncertainty management is Microsoft, which in the turbulent days of the early PC software market shaped an entire industry and continues to reap the benefits. We are on the brink of changes that are projected to rival in impact the Industrial Revolution of the 18th and 19th Centuries. Much more than making entirely new knowledge-based products possible, it is clear that electronic commerce will lead to a fundamental redefinition of the way business is conducted. All participants in the business community need to wake up to, understand and adapt to electronic commerce. They need to redefine their business philosophies and approaches so as to position their organizations to rise with the tide. 3. Vladimir Zwass. Structure and Macro-level impacts of electronic commerce: From technological infrastructure to electronic marketplaces 25 Electronic commerce (E-commerce) is sharing business information, maintaining business relationships, and conducting business transactions by means of telecommunications networks. Traditional E-commerce, conducted with the use of information technologies centering on electronic data interchange (EDI) over proprietary value-added networks, is rapidly moving to the Internet. The Internet's World Wide Web has become the prime driver of contemporary E-commerce. This paper presents a hierarchical framework of E-commerce, consisting of three meta-levels: infrastructure, services, and products and structures, which, in turn, consist of seven functional levels. These levels of E-commerce development, as well as of analysis, range from the widearea telecommunications infrastructure to electronic marketplaces and electronic 4. Frederick J. Riggins and Tridas Mukhopadhyay "Overcoming EDI Adoption and Implementation Risks," International Journal of Electronic Commerce, Volume 3, Number 4, Summer 1999, The emergence of the Internet as a business-to-business communications tool enables a new wave of adoption of EDI and other interorganizational systems. Initiators of these trading-partner relationships must develop concrete strategies for managing the adoption and implementation risks associated with EDI. They may have to subsidize both the initial adoption and subsequent internal usage of these systems by their trading partners if they are to maximize their benefits from the technology. EDI can create strategic value in certain circumstances. To improve internal processes and thus produce operational benefits, it must improve the information flow between trading partners to the point where it exceeds the threshold level. Finally, because the operational benefits of EDI are context-specific, initiators should require their trading partners to develop specific metrics to measure its effect. 5. Bakos, Y. "A Strategic Analysis of Electronic Marketplaces," MIS Quarterly, Volume 15, No. 3, September 1991, pp. 295-310. Information systems can serve as intermediaries between the buyers and the sellers in a vertical market, thus creating an "electronic marketplace". A major impact of these electronic market systems is that they typically reduce the search costs buyers must pay to obtain information about the prices and product offerings available in the market. Economic theory suggests that this reduction in search costs plays a major role in determining the implications of these systems for market efficiency and competitive behavior. This article draws on economic models of search and examines how prices, seller profits, and buyer welfare are affected by reducing search costs in commodity and differentiated markets. This reduction results in direct efficiency gains from reduced intermediation costs and in indirect but possibly larger gains in allocational efficiency from better-informed buyers. Because electronic market systems generally reduce buyers' search costs, they ultimately increase the efficiency of interorganizational transactions, in the process affecting the market power of buyers and sellers. The economic characteristics of electronic markets, in addition to their ability to reduce search costs, create numerous possibilities for the strategic use of these systems. 26 Group Support System (GSS) Introduction and Key Theories Group Support Systems (GSS) are interactive computer-based environments that support concerted and coordinated team effort toward completion of joint tasks. GSS allow groups to work in parallel, typically under anonymous conditions; which allows for high volume and high quality of deliverable output. GSS can radically change the dynamics of group interactions by improving communication, by structuring and focusing problem solving efforts, and by establishing and maintaining an alignment between personal and group goals. GSS has been used to benefit to many group processes such as brainstorming, idea generation, SAandD, JAD, and process modeling. As a result, GSS research is a field of great breadth that involves not only technological aspects, but also facts such as teaming, facilitation, and group dynamics. One important effect of GSS is its role of increasing intellectual bandwidth. According to Dr. Jay Nunamaker, information flows into knowledge management systems (KM) and group support systems (GSS), and these two systems work synergistically to leverage intellectual bandwidth. Key Issues and Conflicts Distributed collaboration is viewed as the major issue. A distributed group support system has to enable both the facilitator and the participants to perform their tasks. The facilitator needs a way to monitor the interactions in order to control the collaboration process. The participants also need a means for communicating with the facilitator as well as other participants. Another key issue for distributed collaboration is whether the distributed users can develop the level of awareness and trust required for effective collaboration. Furthermore, connectivity is a key technological issue for the success of distributed meetings. Connectivity is especially important for the web-based collaborations because of the heterogeneity of distributed sites. Major Research Problems in the Future The following are key issues and research problems need to be addressed:(this part is summarized from the article Lessons from a Dozen Years of Group Support Systems Research: A Discussion of Lab and Field Findings, please see key paper 3 for more information) GSS research of distributed groups across different geographical areas (including distributed facilitation research); Research of integration of GSS with video conferencing; Research of integration of GSS with automatic language translation to support multilingual groups; Research of GSS transfer and adoption in cultures other than English-speaking countries; research of GSS to support heterogeneous group; sophisticated GSS software to support group communication and writing; Possible uses of GSS in the classroom 27 Key Researchers Jerry DeSanctis Fuqua School of Business, Duke University Awards Outstanding teacher award, Texas Tech University, 1980 Award for Distinguished Contributed Paper in MIS at the National meeting of the American Institute for Decision Sciences, 1983 Top Three paper at the Annual Meeting of the International Communication Association, Human Communication Technology Interest Group, May 1988 (with R. Watson and M. S. Poole) Invited member of the doctoral consortium faculty, International Conference on Information Systems, December 1988 Top Three paper in the Annual Meeting of the International Communication Association, Human Communication Technology Interest Group, May 1989 (with M.S. Poole) Invited Chair of the Doctoral Consortium, Thirteenth International Conference on Information Systems, 1992 Received Best Paper Award, 24th Annual Hawaii International Conference on System Sciences Collaboration Technology Track, "Using Computing to Improve the Quality Team Process: Preliminary Observations from the IRS-Minnesota Project," 1991 Current Research Organizational computing, computer-supported cooperative work and management of information systems R. Brent Gallupe Queens University, School of Business Current Research Electronic brainstorming, the history of information systems, E-commerce management issues, Knowledge management systems, Evaluation of information systems. Sara Kiesler Carnegie Mellon University Current Research The social and behavioral aspects of computers and computer-based communication technologies, the emotional and social effects of computing technology on individuals, teams, and families; (detailed research areas include: influence of computer networking on group dynamics and communication in organizations, the research of the causes of "flaming", the conditions for social equalization on computer networks, the benefits and costs of open communication on networks, the illusion of electronic privacy, the uses and misuses of electronic surveys, the formation and conduct of electronic groups, information sharing on networks, and the impact of computer communication on peripheral or marginal organizational groups). Current projects: investigations of household technologies and e-commerce, an NSF-sponsored study on interdisciplinary collaboration; HomeNet, a field study of families using the Internet 28 Key paper Galagher, J., Sproull, L., and Kiesler, S. (1998). Legitimacy, authority, and community in electronic support groups. Written Communication, 15, 493-530. Jay F. Nunamaker, Jr. Center for the Management of Information, University of Arizona Awards Regents Professor / Soldwedel Chair, 1994 - Present. Received the DPMA EDSIG Distinguished IS Educator Award. GroupSystems software received the Editor's Choice Award from PC Magazine, June 14, 1994. GroupWare Achievement Award, GroupWare Conference, San Jose, 1993 GroupSystems: best of show in the GDSS category, GroupWare Conference, San Jose, 1993. Arthur Andersen Consulting Professor of the Year Award, 1992 Professional Activity Editorial board of six journals. Chairman, ACM Curriculum Committee on Information Systems, 1976-1991. Track Chairman, Data and Knowledge Bases, Decision Support Systems and Information Systems, Hawaii Conference 1990 - 1997. Founding member of International Conference on Information Systems, 1980. Served on Faculty at AACSB Basic and Advanced Institutes for faculty retraining, 198391. Current Research Computer supported collaboration and decision support to improve productivity and communication. Wanda J. Orlikowski MIT Sloan School of Management Current Research Organizational changes associated with the use of information technology; the ongoing relationship between information technologies and organizing structures, work practices, communication, culture, and control mechanisms; the use of groupware technologies in organizations; the social and technological aspects of working virtually. Key paper “The Duality of Technology: Rethinking the Concept of Technology in Organizations”, Organization Science, vol. 3, no. 3, August 1992: 398-427. Judy Olson School of Information, University of Michigan Awards Amoco Award for Outstanding Teaching, 1980 Administrative Internship, University of Michigan, Office of the President, 1980 Council: Association for Computing Machinery 29 National Research Council Committee on Human Factors, 1982-89 Professional Activity Editorial Board: Journal of Experimental Psychology: Applied, 1994-present Editorial Board: Management of Information Systems Quarterly, 1990-94 Editorial Board: Organizational Computing, 1990-present Editorial Board: Human Computer Interaction, 1982-present Editorial Board: Psychological Review, 1980-82 Editorial Board: Memory and Cognition, 1977-78 Current Research Collaboration technology, Human-computer interaction, software design process Applications of cognitive psychology to business computing and communication Key paper "Group Work Close Up: A Comparison of the Group Design Process With and Without a Simple Group Editor" (with G. M. Olson, M. Storrsten and M. Carter). ACM: Transactions on Information Systems, 1993. Sirkaa L. Jarvenpaa McCombs School of Business, University of Texas at Austin Awards Distinguished Visiting Scholar, University of Melbourne, Australia, 1997 Harvard Business School Grant, 1995 The Center for International Business and Education Grant, 1995 Current Research Clicks and mortars, customer insight, e-commerce, information systems, communication and trust in global virtual teams Key Paper "Is Anybody Out There?: The Antecedents of Trust in Global Virtual Teams," (with K. Knoll and D. Leidner), Journal of Management Information Systems, 1998 Douglas R. Vogel Department of Information Systems, City University of Hong Kong Current Research Group support systems, business process improvement, executive support systems, technology support for learning environments, electronic commerce, virtual organization Key Paper Vogel, D. and Nunamaker, J., "Group Decision Support System Impact: MultiMethodological Exploration", Information and Management (1990), 15-28. Key Papers 1. DeSanctis, G., and Gallupe, R. B. (1987). A Foundation for the Study of Group Decision Support Systems. Management Science, 33(5), 589-609. The paper identifies the need of GDSS research, and presents a conceptual overview of GDSS based on an information-exchange perspective of decision-making. Three levels of systems are described, representing varying degrees of intervention into the decision 30 process. The paper describes the evolution of GDSS. A multidimensional taxonomy of systems is proposed as an organizing framework for research in the area. The paper also identifies three critical environmental contingencies to GDSS design: group size, member proximity, and the task confronting the group. Potential impacts of GDSS on group processes and outcomes are discussed, and important constructs in need of study are identified. 2. Gallupe, R. B., Dennis, A. R., Cooper, W. H., Valacich, J. S., Bastianutti, L. M., and Nunamaker, J. F. (1992). Electronic Brainstorming and Group Size. Academy of Management Journal, 35(2), 350-369. This article summarizes research to determine whether or not group size has an effect on electronic brainstorming by using different group size. The authors found that larger groups using GSS indeed generated more, high-quality ideas and experienced higher levels of satisfaction than groups that did not use technology. However, in small groups (e.g. 2 group members) technology did not act as a catalyst for higher productivity; primarily because there was no anonymity and not much production blocking (two primary reasons larger GSS group succeeded). 3. Nunamaker, J. F., Briggs, R. O., Mittleman, D. D., Vogel, D. R., and Balthazard, P. A. (1997). Lessons from a Dozen Years of Group Support Systems Research: A Discussion of Lab and Field Findings. Journal of Management Information Systems, 13(3), 163-207. The paper presents an overview of GSS research conducted in University of Arizona, where researchers have built 6 generations of group support systems software, conducted over 150 research studies and facilitated over 4,000 projects. The paper reports research results and lessons learned from the studies. The paper also proposes Groupware Grid, which is a theory-based heuristic model for evaluating the contributions of groupware technology to team productivity. Research results and lessons are presented from 9 key areas: 1. GSS in organizations, 2. cross-cultural and multicultural issues, 3. designing GSS software, 4. collaborative writing, 5. electronic polling, 6. GSS facilities and room design, 7. leadership and facilitation, 8. GSS in classroom, and 9. business process reengineering. 4. Nunamaker, J. F., Dennis, A. R., Valacich, J. S., Vogel, D. R., and George, J. F. (1991). Electronic Meeting Systems to Support Group Work. Communications of the ACM, 34(7), 40-61. This is a "classic" GSS article written by Dr. Nunamaker, et al. This is one of the fundamental, early guides to GSS. The article explains the group losses and gains of a group meeting, discusses the potential benefits of using GSS by increasing group gains and decreasing group losses. GSS utilizes four mechanisms to support a meeting: process support, process structure, task support, and task structure. The paper also discusses the specific implementation of GSS through GroupSystems, a GSS software developed at the University of Arizona. Three facilitation styles are discussed, and how GSS strongly supports an integrative facilitation style is illustrated. 31 5. Fjermestad, J., and Hiltz, S. T. (1999). An assessment of Group Support Systems Experimental Research: Methodology and Results. Journal of Management Information Systems, Vol. 15 No. 3, Winter 1999 7-150 This landmark paper summarizes the methods and results of the whole area of experimental GSS studies published in the English language in referred academic journals. The paper specifically excludes case studies from the field, focusing on analyzing experimental results. The paper presents an exhaustive list of authors, editors, reviewers, and major GSS researchers at press time. In addition to the exhaustive bibliography, the authors offer clear, readable tables summarizing each experiment, and detailing research methods, hypotheses, and results for 200 experiments. The authors also offer a classification scheme for the dependent and independent variables in these experiments, examining which are initial causes, which are intervening variables, and which are outcome variables. This paper can serve as an outstanding pedagogical resource for courses in MIS research and research methodologies. 6. Nunamaker, J. F., Chen, M., and Purdin, T.D.M. Systems Development in Information Systems Research. Journal of Management Information Systems, Vol. 7, No.3, Winter 1990-1991, 89-106 The paper discusses the methodology of MIS research such as theory building, experimentation, observation and system development. The contribution of the paper is that it discusses the validity of MIS research as a research domain and proposes system development as a valid and critical research methodology in MIS. The paper illustrates MIS research is multimethodological and multidimensional, integration of system development and traditional research methodology can lead to fruitful MIS research. 32 Information Economics Key Issues and Conflicts The interdisciplinary research of information economics draws on principles of information science, economics, management, political science, public policy, organizational theory, psychology, ethics, and computer science to propose answers to the tough new questions confronting the networked society: When does sharing proprietary information improve a firm’s competitive stance? Does information technology encourage or impede information equality? When does it make economic sense to give away information products for free? Does the Internet require a new regulatory paradigm? What business models work for information commerce, and how should information goods be priced [1]? Most Important Theories Information asymmetry Bayes, decision theory, and choice Principal-agent models Moral hazard Adverse selection Revelation mechanisms Concepts of information Shannon entropy Turing machine (instructional/computational) Information pricing Value Hedonics Options Packaging information Macroeconomic effects Growth theory Information markets Intellectual property Creation incentives vs. monopoly costs Patents and copyrights Information and social policy [2] References: [1] University of Michigan School of Information, http://www.si.umich.edu/academics/iemp/ [2] University of Michigan School of Information, http://www.si.umich.edu/Classes/646/#itopics 33 Key Researchers Erik Brynjolfsson Massachusetts Institute of Technology Email: erikb@mit.edu Webpage: ebusiness.mit.edu/erik Research area: Information technologies and productivity, Internet implications for pricing, organizational change Charles H. Kriebel Carnegie Mellon University Email: ck04@andrew.cmu.edu Research area: Computers and information systems, information economics, telecommunications, management science, operations management, robotics, applied economics, productivity, manufacturing systems, information resource management. Tridas Mukhopadhyay Carnegie Mellon University Email: tridas@andrew.cmu.edu Research area: Business value of information technologies, business-to-business commerce, residential use of the Internet, software cost management. Andrew B. Whinston University of Texas at Austin Email: abw@uts.cc.utexas.edu Webpage: cism.bus.utexas.edu Research area: Artificial intelligence, e-commerce, information systems, the new economy Key papers Masuda Y. “Conceptual Framework Of Information Economics.” IEEE-Transactions-onCommunications, October 1975, 23: (10) 1028-1040. Information economics is a new system of economics, overriding the classical school of economics, and at the same time it is a future economics. Three basic concepts of economics constitute the framework of information economics. The first of them is the spirit of globalism-the ideas of spaceship, quality of time, and coexistentialism. The second is information productivity. The development of computer and communication technologies has made possible mass production of objective-oriented, logical, normative information. The third is time value-a new view of values. By time value is meant the value that is created through objective-oriented utilization of free time at the disposal of human beings. Just as each new theory of economics has a new vision, information economics has a vision-Global Futualization Society as the society where a large variety 34 of voluntary communities will flourish on a global scale at a time, and the individual will seek to realize self-acturalization in each community. Barua, A., Kriebel, C.H., Mukhopadhyay, T. “An Economic Analysis of Strategic Information Technology Investments.” MIS Quarterly, September 1991, Vol. 15, Iss. 3, 313-332. The strategic impacts of information technology (IT) investment are studied through the development of a formal economic model. In particular, the study focuses on IT-related quality competition in a duopoly, where the services may not be priced initially and where the benefits may come indirectly. A firm may have to invest in IT, regardless of its underlying cost structure, as a response to its competitor's investment level. Both firms prefer sequential over simultaneous investments, even when both have the required technology. While the IT-inefficient firm has followership incentives, the leadership incentives for the IT-efficient firm depend on the difference in IT cost structures and on the degree of substitutability between the services of the 2 firms. For dynamic markets with new consumers, the negative effect of switching cost on the welfare of existing consumers is reduced when the IT-efficient firm moves first. Clemons E., Kleindorfer P. “An Economic-Analysis Of Interorganizational Information Technology.” Decision Support System, September 1992, 8: (5) 431-446. This paper first reviews some basic results on the economics of information technology (IT) and strategy. These results begin by developing a model of interorganizational IT, focusing on supplier-buyer interactions and the costs and benefits of IT in facilitating such interactions. The modeling framework incorporates economies of scale and scope, transactions specific sunk costs of IT development, and related issues of bargaining and opportunism. Results of the model are applied to the increasingly important topic of interorganizational information systems, addressing some of the risks of cooperative ventures that are frequently overlooked in the MIS literature. Kriebel C., Barua A. and Mukhopadhyay T. “Information Technologies and Business Value: An Analytical and Empirical Investigation.” Information Systems Research, March 1995, Vol. 6, Iss. 1, 3-24. An important management question today is whether the anticipated economic benefits of information technology (IT) are being realized. In an analysis, this problem is considered to be measurement related, and a new process-oriented methodology for ex post measurement is proposed and tested to audit IT impacts on a strategic business unit (SBU) or profit center's performance. The IT impacts on a given SBU are measured relative to a group of SBUs in the industry. The methodology involves a 2-stage analysis of intermediate and higher level output variables that also accounts for industry and economy wide exogenous variables for tracing and measuring IT contributions. The data for testing the proposed model were obtained from SBUs in the manufacturing sector. The results show significant positive impacts of IT at the intermediate level. The study provides a practical management tool to address the question of why (or why not) certain IT impacts occur. 35 Nadiminti R., Mukhopadhyay T., Kriebel C.H. “Risk aversion and the value of information.” Decision Support System, March 1996,16: (3) 241-254. Determining the value of information is a fundamental research problem for information system scientists. Unfortunately, very little research exists that examines the relationship between risk aversion and the value of information. This is surprising because empirical studies show that most managers are risk averse rather than risk neutral. Moreover, the small literature that exists appears to be in conflict. We have developed a framework to examine the relationship between the value of information and risk aversion. We show that the method of payment for information must be considered in determining this relationship. We have used the Arrow-Pratt measure of risk aversion to derive explicit conditions under which the value of information increases (decreases) with risk aversion. From our analysis it is clear that earlier work has depicted a limited view of the relationship between risk aversion and value of information. Our analysis is applicable to the ex-post evaluation of transaction processing systems and a subset of decision and expert support systems. Brynjolfsson, E. and Hitt, L. “Paradox Lost? Firm-level Evidence on the Returns to Information Systems Spending.” Management Science, April 1996. The "productivity paradox" of information systems (IS) is that, despite enormous improvements in the underlying technology, the benefits of IS spending have not been found in aggregate output statistics. One explanation is that IS spending may lead to increases in product quality or variety which tend to be overlooked in aggregate output statistics, even if they increase sales at the firm-level. Furthermore, the restructuring and cost-cutting that are often necessary to realize the potential benefits of IS have only recently been undertaken in many firms. Our study uses new firm-level data on several components of IS spending for 1987-1991. Our results indicate that IS have made a substantial and statistically significant contribution to firm output. Hitt, L. and Brynjolfsson, E. “Productivity, Profit and Consumer Welfare: Three Different Measures of Information Technology's Value.” MIS Quarterly, June 1996. The business value of information technology (IT) has been debated for a number of years. While some authors have attributed large productivity improvements and substantial consumer benefits to IT, others report that IT has not had any bottom line impact on business profitability. In this paper, we focus on the fact that while productivity, consumer value and business profitability are related, they are ultimately separate questions. Accordingly, the empirical results on IT value depend heavily on which question is being addressed and what data are being used. Applying methods based on economic theory, we are able to define and examine the relevant hypotheses for each of these three questions, using recent firm-level data on IT spending by 370 large firms. Our findings indicate that IT has increased productivity and created substantial value for consumers. However, these benefits have not resulted in supernormal business profitability. We conclude that while modeling techniques need to be improved, these results are consistent with economic theory. Thus, there is no inherent contradiction between increased productivity, increased consumer value and unchanged business profitability. 36 Brynjolfsson, E. “The contribution of information technology to consumer welfare.” Information Systems Research, September 1996 Vol. 7, Iss. 3 pg. 281, 20 pgs. Over the past 2 decades, US businesses have invested heavily in information technology (IT) hardware. Managers often buy IT to enhance customer value in ways that are poorly measured by conventional output statistics. Further, because of competition, firms may be unable to capture the full benefits of the value they create. This undermines researchers' attempts to determine IT value by estimating its contribution to industry productivity or to company profits and revenues. An alternative approach estimates the consumers' surplus from IT investments by integrating the area under the demand curve for IT. Using data from the US Bureau of Economic Analysis, 4 measures of consumers' surplus are estimated: 1. Marshallian surplus, 2. Exact surplus based on compensated (Hicksian) demand curves, 3. a nonparametric estimate, and 4. a value based on the theory of index numbers. All 4 estimates indicate that in the base year of 1987, IT spending generated approximately $50 billion to $70 billion in net value in the US and increased economic growth by about 0.3% per year. According to conservative estimates, IT investments generate approximately 3 times their cost in value for consumers. 37 Information Retrieval Key Issues The techniques used in information retrieval are as follows: (1) Automatic Text Analysis - concerns how the text of a document is represented inside a computer. (2) Automatic Classification - looks at automatic classification methods. (3) File Structures - from the point of view of someone primarily interested in information retrieval. (4) Search Strategies - search strategies when applied to document collections structured in different ways. (5) Probabilistic Retrieval - a formal model for enhancing retrieval effectiveness by using sample information about the frequency of occurrence and co-occurrence of index terms in the relevant and non-relevant documents. Trends (1). (2). (3). (4). (5). (6). Multimedia Information Retrieval Collaborative Information Retrieval Multilingual Information Retrieval Semantic Web (linked concept) Text Mining, Web Mining Mobile /Wireless Computing Key People Gerard Salton Description Professor, Computer Science at Cornell University. Founder of Information Retrieval, died of cancer on 28 August, in Ithaca, NY (1927-1995). ACM Award for Outstanding Contributions in 1983 (The first such award was given to G. Salton) Research Interests Natural language processing, information retrieval Karen Sparck Jones Description Computer Laboratory, University of Cambridge Interests She has worked in automatic language and information processing research since the late fifties, beginning her career at the then Cambridge Language Research Unit. She has many publications including several books. Her work in the last decade has been on document retrieval including speech applications, database query, user and agent modeling, summarizing, and information and language system evaluation. 38 Gary Marchionini Description Current Position: Professor, College of Library and Information Services Research Interests Information seeking, human-computer interaction, digital libraries, information design, information policy. Edward A. Fox Description Professor, Computer Science, Virginia Polytechnic Institute and State University. Research Interests Multimedia information storage and retrieval; digital libraries; hypertext/hypermedia; electronic publishing and text processing; educational technology and distance learning; library automation; artificial intelligence. W. Bruce Croft Description Professor, Department of Computer Science at the University of Massachusetts, Amherst. Research Interests His research interests are in formal models of retrieval for complex, text-based objects, text representation techniques, the design and implementation of text retrieval and routing systems, and user interfaces. He has published more than 100 articles on these subjects. This research is also being used in a number of operational retrieval systems. Key Papers Automatic Text Structuring and Summarization. Gerard Salton, Amit Singhal, Mandar Mitra, Chris Buckley: Information Processing and Management 33(2): 193-207 (1997) In recent years, information retrieval techniques have been used for automatic generation of semantic hypertext links. This study applies the ideas from the automatic link generation research to attack another important problem in text processing - automatic text summarization. An automatic 'general purpose' text summarization tool would be of immense utility in this age of information overload. Using the techniques used (by most automatic hypertext link generation link algorithms) for inter-document link generation, we generate intra-document links between passages of a document. Based on the intradocument linkage pattern of a text, we characterize the structure of the text. We apply the knowledge of text structure to do automatic text summarization by passage extraction. We evaluate a set of fifty summaries generated using our techniques by comparing them to paragraph extracts constructed by humans. The automatic summarization methods 39 perform well, especially in view of the fact that the summaries generated by two humans for the same article are surprisingly dissimilar. Automatic Construction of Networks of Concepts Characterizing Document Databases, Chen, H., and Lynch, K. J. (1992).. Paper presented at the IEEE Transactions on Systems, Man, and Cybernetics. We report results of a study that involved the creation of knowledge bases of concepts from large, operational textual databases. Two East-bloc computing knowledge bases, both based on a semantic network structure, were created automatically using two statistical algorithms. With the help of four East-bloc computing experts, we evaluated the two knowledge bases in detail in a concept-association experiment based on recall and recognition tests. In our experiment, one of the knowledge bases that exhibited the asymmetric link property out-performed all four experts in recalling relevant concepts in East-bloc computing. The knowledge base, which contained about 20,000 concepts (nodes) and 280,000 weighted relationships (links), was incorporated as a thesaurus-like component into an. (12 citations) Interfaces and tools for the Library of Congress National Digital Library, Program.Marchionini, G., Plaisant, C., and Komlodi, A. (1998). Information Processing and Management, 34(5), 535-555. This paper describes a collaborative effort to explore user needs in a digital library, develop interface prototypes for a digital library and suggest and prototype tools for digital librarians and users at the Library of Congress (LC). Interfaces were guided by an assessment of user needs and aimed to maximize interaction with primary resources and support both browsing and analytical search strategies. Tools to aid users and librarians in overviewing collections, previewing objects and gathering results were created and serve as the beginnings of a digital librarian toolkit. The design process and results are described and suggestions for future work are offered. (2 citations) Theory of term importance in automatic text analysis. Salton, G., Yang, C., and Yu, C. (1975). Journal Am. Soc. Inform. Sci., 26(1), 33-44. Evaluating natural language processing systems, Karen Sparck Jones, J.R. Galliers , springer, 1996. This report presents a detailed analysis and review of NLP evaluation, in principle and in practice. Part 1 examines evaluation concepts and establishes a framework for NLP system evaluation. This makes use of experience in the related area of information retrieval and the analysis also refers to evaluation in speech processing. Part 2 surveys significant evaluation work done so far, for instance in machine translation, and discusses the particular problems of generic system evaluation. The conclusion is that evaluation strategies and techniques for NLP need much more development, in particular to take proper account of the influence of system tasks and settings. Part 3 develops a general approach to NLP evaluation, aimed at methodologically sound strategies for test and evaluation. 40 Knowledge Management Introduction As the attention of human beings becomes the most critical resource in the information age, the need to manage vast amount and different levels of knowledge (see Figure 1) becomes apparent. Knowledge management is a discipline that promotes an integrated approach to identifying, capturing, retrieving, sharing and evaluating an enterprise’s information assets. These information assets may include databases, documents, policies and procedures as well as the un-captured, tacit expertise and experience resident in individual workers. KMS Understanding Hierarchy Context Wisdom Principles High Knowledge Patterns Information Relations Low Data Symbols Noise Detection Easy Difficult Figure 1. KMS Understanding Hierarchy Categories of Knowledge Management Research Knowledge management investigates areas such as visualization, categorization, representation of data, information, knowledge and wisdom to enable transfer and sharing of knowledge and information to other groups and people. This discipline is essentially divided into technical aspect and behavioral aspect. The technical aspect is composed of four categories, namely, information retrieval, digital library, collaboration, and data mining. The behavioral aspect is composed of four categories, namely, consulting in knowledge management, best practices, organizational memory, knowledge networking / integration. 41 Key Theories and Methodologies Knowledge Management is a cross-disciplinary research area. The key theories and methodologies in the behavioral side include cognitive psychology theories, human communication theories, and group theories. The key theories and methodologies in the technical side include statistical theories, self-organizing map, mathematical representation schemes, automatic text processing methods, workflow technologies, agent theory, ontology, meta-data and various visualization techniques. Key Issues The technical aspect of knowledge management is concerned with how to capture semantic knowledge and meanings, how to visualize knowledge, how to integrate knowledge, and how to deal with multilingual knowledge. The behavioral aspect of knowledge management is concerned with what are the best practices, organizational change and reward, case studies in knowledge management, and social and human aspect of knowledge management. The technical and behavioral aspects drive each other to enhance the field of knowledge management. Future Research Trends Relevance -- having all the available, relevant knowledge available for decision-making. Dynamism -- knowledge about the state of multiple processes operating in parallel and affecting each other in a coordinated way. Community -- a collective environment that actively supports sharing through automatic capture in sharable form and explicit policies and open cultures that promote sharing. Key Researchers Christine L. Borgman Contact Information Department of Information Studies Graduate School of Education and Information Studies University of California, Los Angeles http://dlis.gseis.ucla.edu/cborgman/ Research Areas Her research interests include digital libraries, human-computer interaction, information seeking behavior, and scholarly communication and bibliometrics, as well as information technology policy in Central and Eastern Europe. Hsinchun Chen Contact Information MIS Department, McClelland Hall 430Z Karl Eller Graduate School of Management University of Arizona http://ai.bpa.arizona.edu/html/faculty.html 42 Research areas Professor Chen’s research interests include digital library, intelligent information retrieval, automatic categorization and classification, concept space generation, automatic thesaurus browsing and traversal, inductive query by examples, machine learning for IR, large-scale information analysis and visualization, internet resource discovery, multilingual IR, collaborative systems, intelligence systems. W. Bruce Croft Contact Information Director, Center for Intelligent Information Retrieval Department of Computer Science University of Massachusetts, Amherst http://www.cs.umass.edu/faculty-bios/croft.html Research Areas Professor Croft's research interests are in formal models of retrieval for complex, textbased objects, text representation techniques, the design and implementation of text retrieval and routing systems, and user interfaces. He has published more than 100 articles on these subjects. This research is also being used in a number of operational retrieval systems. Daniel E. O'Leary Contact Information School of Business University of Southern California http://www.usc.edu/schools/business/atisp/oleary.html Research areas His current research examines issues in the areas of Electronic Commerce, Enterprise Resource Planning Systems, Knowledge Management, Reengineering and Workflow, and Virtual Organizations. His research employs a number of methodologies, including analytic, artificial intelligence/expert systems, empirical and case studies. Gerard Salton He was (1927-1995) one of the first programmers for the Harvard Mark IV computer. The “Father” of Information Retrieval. Research areas His research interests are natural language processing and information retrieval. He began the SMART information retrieval system in the 1960's (allegedly, SMART is known as "Salton's Magical Automatic Retriever of Text"), and ideas in this work fundamentally changed fulltext processing methods on computers and provided the field of information retrieval with solid underpinnings. Key Articles 43 Chen, H.; Houston, A.L.; Sewell, R.R.; Schatz, B.R. (1998) “Internet browsing and searching: User evaluations of category map and concept space techniques,” Journal of the American Society for Information Science 49(7), pp.582-603. The development and refinement of algorithms to improve browsing and searching by addressing information overload and vocabulary differences are discussed. Whether 2 particular algorithms can help improve browsing and searching the Internet is studied. The results indicate that a Kohenen self-organizing map-based algorithm can successfully categorize a large and eclectic Internet information space into manageable sub-spaces that users can successfully navigate to locate a homepage of interest to them. A study of an automatically generated concept space algorithm for searching was especially encouraging. Subjects especially like the level of control they could exert over such a search. Salton G. Automatic Text Processing, Addison-Wesley Publishing Company, 1989. This book deals with the whole area of automatic text processing – that is, the handling of texts using automatic equipment. The aim is not to teach laymen or humanists how to program computers to manipulate text, nor to teach scientists language-processing skills. Instead, this book examines the area of text processing as a whole, describing various text-processing methodologies and identifying those tasks now undertaken routinely, while also discussing more experimental procedures not yet ready for operation. This book is divided into four parts: the first part covers the computer environment and automated office situation, in which text processing is of particular interest. The second part covers the main word processing areas, which treat texts on the level of individual words. The third part covers text-retrieval systems whose operations are normally based on text units larger than single, individual word forms. The fourth part covers the main language-analysis and language-processing topics in which text meaning and text understanding are of principle concern: syntactic and semantic language-analysis methods that determine language structure and text content, and knowledge-based text processing. O'Leary, D.E. “Knowledge-Management Systems: Converting and Connecting”, IEEE Intelligent Systems and their applications 13(3), May-June 1998, pp.30 –33. Organizations use knowledge management for a number of reasons, including environmental pressures, technological advancements, and the ability to create valuable information. Classic knowledge management thinking assumes that a firm gathers all its important knowledge in a single place, and employees use it to make good decisions that will benefit the organization. But this classical thinking is only partially right. The full range of knowledge management converting and connecting capabilities should include not only connecting knowledge and people, but also link knowledge to other knowledge or push knowledge to other knowledge or push knowledge out to employees. Croft, W.B. “Effective text retrieval based on combining evidence from the corpus and users,” IEEE Expert 10(6), Dec. 1995, pp.59 –63. The author surveys the representation, query processing and retrieval techniques used in the Inquiry system. By combining evidence about relevance from the corpus, individual 44 documents and users, Inquiry achieves effective overall recall and precision evaluation while avoiding occasional major failures. 45 Operation Research Introduction Operation Research (OR) looks at an organization’s operations - the functions it exists to perform. The objective of Operational Researchers is to work with clients to find practical and pragmatic solutions to operational or strategic problems, often working within tight timing constraints. Organizations may seek a very wide range of operational improvements - for example, greater efficiency, better customer service, higher quality or lower cost. Whatever the business engineering aim, OR can offer the flexibility and adaptability to provide objective help. Most of the problems OR tackles are messy and complex, often entailing considerable uncertainty. OR can use advanced quantitative methods, modelling, problem structuring, simulation and other analytical techniques to examine assumptions, facilitate an in -depth understanding and decide on practical action. The future issues will focus on decision analysis, vehicle routing, and effectiveness of mandatory minimum sentencing and information technology. MIS researcher can look at the opportunities of facilitating OR with information system, making the switch from academia to the "real world" Key People Hau L. Lee Stanford University Hau.Lee@stanford.edu Supply chain management; Global logistic system design and control; Multi-echelon inventory systems; Manufacturing and distribution strategy; Design for supply chain management Marshall Fisher The University of Pennsylvania Lanchester Prize, Management Science, 1977 Supply chain management, retailing 46 James B. Orlin MIT jorlin@mit.edu, http://web.mit.edu/jorlin/www/ Mathematical Programming, Combinatorial and Network Optimization, Design and Analysis of Algorithms and Heuristics, Logistics. George Nemhauser george.nemhauser@isye.gatech.edu School of Industrial and Systems Engineering Georgia Tech Lanchester prize (twice) Discrete optimization, solving large-scale mixed-integer programming problems, crew and fleet scheduling problems in the airline industry. Ellis Johnson School of Industrial and Systems Engineering, Georgia Tech ellis.johnson@isye.gatech.edu Lanchester Prize 1983 Mathematical programming and integer programming; theories on computational approaches; applications in manufacturing, distribution, and transportation. Paul H. Zipkin Fuqua School of Business, Duke University PaulZipkin@Duke.Edu Operations Management; Inventory Management; Supply-chain Management and Analysis; Product variety; design of logistics networks Moshe Dror The University of Arizona mdror@bpa.arizona.edu Combinatorial Optimization in Logistics and Manufacturing Systems; Cooperative Game Theory and Cost Allocation in Inventory and Combinatorial Problems; Agent Theory and Applications in Operations Management. Key Papers 47 Jack Edmonds, “Maximum matching and a polyhedron with 0,1-variation”, Journal of Research of national Bureau of Standards, 69 (1965), 123-130 Jack Edmonds, “Paths, Trees, and Flowers”, Canadian Jornal of Mathematics, 1965 Thomas L. Saaty, and Chen, Kun Yuan, Hoover's problem. Math. Mag. 51 (1978) 288292 05C20 Ellis Johnson, Manfred Padberg, and Harlan Crowder", Solving Large-Scale Zero-One Linear Programming Problems" Operations Research, 31:5 (1983), pp. 803-834. Hau L. Lee, Material Management in Decentralized Supply Chains, Operations Research, vol. 41 1993 Hau L. Lee, Hau. Information distortion in a Supply Chain: The Bullwhip Effect, Management Science, 43, 4 1997 James Orlin and Rina R. Schneur, A Scaling Algorithm for Multicommodity Flow Problems" Operations Research 46, (1998), 231-246. Dror, M. and Trudeau, P., (1989). "Savings by Split Delivery Routing", Transportation Science 23, 141-145 Dror, M., Stern, H.I., and Lenstra, J.K., (1987). "Parallel Machine Scheduling: Production Rates Dependent on Number of Jobs in Operation", Management Science 33, 1001-1009 Cachon, G. and M. Lariviere. 1999. An Equilibrium Analysis of Linear and Proportional Allocation of Scarce Capacity. IIE Transactions. 31 (9) 835-850. Cachon, G. and M. Lariviere. 1999. Capacity Choice and Allocation: Strategic Behavior and Supply Chain Performance. Management Science. 45 (8) 1091-1108. Glasserman P Introduction to the special issue on stochastic models and simulation MANAGE SCI 46: (9) III-IV SEP 2000 Glasserman P, Wang YS Leadtime-inventory trade-offs in assemble-to-order systems OPER RES 46: (6) 858-871 NOV-DEC 1998 Masuda Y, Whang S Dynamic pricing for network service: Equilibrium and stability MANAGE SCI 45: (6) 857-869 JUN 1999 Barnett A.l., Comment on a Market Share Theorem-comment, J Marketing Research, 13: (3) 312-312 1976 Zipkin P. H., Performance Analysis of a Multiitem Production-Inventory System Under Alternative Policies, Manage Sci. 41: (4) 690-703 APR 1995 48 Zipkin P.H. Computing Optimal Lot Sizes in the Economic Lot Scheduling Problem, Operation Research, 39: (1) 56-63 JAN-FEB 1991 Kelton W.D., Random Initialization methods in Simulation, IIE TRANS 21: (4) 355-367 DEC 1989 Chen, F. Optimal Policies for Multi-Echelon Inventory Problems with Batch Ordering. Operations Research 48, 376-389. 2000. 49 Social/Ethical/Psychological Issues Introduction Social, psychological, and ethical issues are important factors to consider in regards to information systems research because of the way they directly affect its users. Social issues address the impacts of the computer technologies that are currently available on organizations, individuals, and communities. Ethical issues involve privacy concerns, moral dilemmas, and sensitive information. The psychological issues within technology research deal with the cognitive and emotional states of people utilizing it. From these areas of research, self-regulation, laws governing computer technology, sociological and psychological well beings of people stems from these areas of research. Most Important Theories Some important theories, hypothesis, and models to come from this area of research are the Media Richness Theory, Social Presence Theory, SIDE theory, Computers as Social Actors, and Internet Addiction Theory. Key Issues, Conflicts, and Major Research Problems Amongst this body of literature, there are three major arguments that researchers uphold. The first is the ethical use of using subjects over the Internet. When looking at the social and psychological impacts of technology, a vast majority of research has been pertaining to areas involving the Internet (e.g., e-commerce, distance learning, privacy issues). Therefore, researchers raise the questions if it is considered ethical to monitor transactional behaviors of consumers and/or read through e-mail messages and postings found in chat rooms without the users consent. Another research problem is the ability to be able to study technology that is always in flux. 50 Key Researchers Mary J. Culnan Contact Information The McDonough School of Business, Georgetown University Washington D.C., 20057-1008 (202) 687-3802; e-mail: culnanm@msb.edu Research areas Dr. Culnan’s research focus is on how information technology is impacted by social and public policies and information privacy issues. She is currently working on the Georgetown Internet Privacy Policy Study (GIPPS) and also looks at trends in consumer attitudes and electronic marketing. Sara Kiesler Contact Information 3513 Newell-Simon Hall Carnegie Mellon University 5000 Forbes Ave. Pittsburgh, PA 15213-3891 (412) 268-2888; e-mail: kiesler@andrew.cmu.ecu Research Areas Dr. Kiesler has been currently working on the social, emotional, and behavioral impacts of computing on individuals, families, and teams. She is best noted for her NSF sponsored research regarding interdisciplinary collaborations and a system called HomeNet, designed to study Internet usage among families. Other significant contributions to the field by Dr. Kiesler include issues regarding e-mail flaming and standards, formation of electronic groups, and social equalization and is currently a Professor in the Human Computer Interaction Institute. Robert Kling Contact Information School of Library and Information Science Indiana University at Bloomington 107 S. Indiana Avenue Bloomington, IN 47405-7000 (812) 855-9763, e-mail: kling@indiana.edu Research areas Social consequences of computerization and how it affects the public, computer ethics, and personal privacy are major issues Dr. Kling focuses on. Currently he is working on areas pertaining to scholarly communication and the use of electronic media to support it. He has authored over 4 books pertaining to computerization, social impacts, and controversies. Donald Norman Contact information 51 Apple Computer, Inc. MS 301-4UE 1 Infinite Loop, Cupertino, CA 95014 USA (408) 862-5515; e-mail: dnorman@apple.com Research areas Dr. Norman is a leading researcher on human cognition and the interaction of technology and society. He has taken his findings from the field of academics, leaving the University of California, San Diego, and working for Apple Computer and being the President of UNext.com Learning Systems. He is interested in how people utilize technology and the impact that has on society. Gary Olson Contact Information 306A West Hall 550 E. University Ann Arbor, MI 48109-1092 (734) 647-3576; e-mail: gmo@umich.edu Research areas Topics of specialization for Dr. Olson include computer support for collaboration issues, policy formation, and decision-making. He is interested specifically in cognitive psychology and human-computer-interaction. His background is in psychology and he implements theories of psychology to social issues governing the use of computers. The NSF, NICH, Apple computers, Arthur Andersen and Co, and Ameritech have funded his research. Lee Sproull Contact Information Leonard N. Stern School of Business New York University New York, New York Research areas Dr. Sproull’s research focuses on social and organizational implications of technology. So far, she has published more then 50 books and articles on these topics. She is currently working on the dynamics and consequences of electronic groups and communities. Among her achievements are emphasizing connections between different academic disciples and was a founding member of the Interdisciplinary department of social and decision sciences at Carnegie Mellon University. Key Papers Birnbaum, M. H. (2000). Psychological experiments on the Internet. Academic Press: San Diego, CA. Gackenbach, J. (1998). Psychology and the Internet: Intrapersonal, interpersonal, and transpersonal implications. Academic Press: San Diego, CA. 52 Kling, R. (1980). Social analyses of computing: Theoretical perspectives in recent empirical research. Computing surveys, 12, 62-89. This article examined empirical studies of computing use in organizations and in public life. The roles of computer technologies for innovation, in the work life, in decision making, and in influencing power are examined. In addition, this article also reviews the privacy and social accountability issues. This articles groups analyses of the social character and development of computing into two major perspectives: system rationalism and segmented institutionalism. Kraut, Kiesler, Mukhopadhyay, Scherlis, and Patterson. (1998). Social impact of the Internet: What does it mean? Communications of the ACM (41), 12. According to prior research involving studies regarding the HomeNet project, results were found that people using the Internet incurred declines in social and psychological well-being. Depression increased, communication between friends and family decreased, and people overall felt lonelier even though the purpose for using the Internet was to increase their interpersonal communication. Other outcomes of the study showed that there is a difference between people who have positive versus negative attitudes about the Internet. People with positive attitudes are not as concerned with their privacy, perceive shopping by mail as beneficial, and have coping strategies for dealing with unwanted mail. The authors give future research suggestions including focusing on characteristics such as the sensitivity of the information, its source, its perceived relevance to the original transaction, and whether disclosure reflects informed consent or results in a potentially harmful outcome to the individual. This has implications for MIS research involving e-commerce. Due to findings, MIS e-commerce research needs to take into consideration people's attitudes about the Internet so that they can target ways in which to assure people of their privacy and also encourage on-line shopping. Norman, D. (1988). Psychology of the everyday things, Chapter 1, pp. 1-33. In Design of Everyday Things. Within the first chapter of his book, the concept of affordances, perceived and actual properties of things, is introduced. Dr. Norman suggests that it is important to make affordances visible, participate in natural mappings, taking advantage of physical analogies and cultural understandings, and integrating user feedback. His discussion revolves around taking a user-based center when designing anything from hardware to software to tools. At times, MIS researchers focus on task and problem solving with little regards to the user. The field of MIS research can benefit by reading this chapter as it allows for awareness of user importance in design. Turkle, S. (1995). Life on the screen: Identity in the age of the Internet. Simon and Schuster. Turkle's book is one of the first books to really describe ethnographically how people are currently using the Internet and the possibilities of future use. She observes different online cultures (e.g., MOOs, MUDs, Chatrooms) and how they compare to real life communities. This book can be beneficial for MIS researchers to read to use as a basic understanding of how people are using new technologies and the social norms that are already established on-line. They can in turn use this found knowledge by learning how 53 to redesign systems that are already in place to better serve its users. They can also research into how people are using the systems already and project and propose future research and better systems. 54 Supply Chain Management Most Important Theories To compete successfully in the global market, companies need to manage the effectiveness and efficiency of the operations that manufacture and distribute their products or services to their customers. Supply chain management deals with the management of materials, information and financial flows in a network consisting of suppliers, manufacturers, distributors, retailers, and customers. Many industries have found it challenging to manage these flows efficiently and effectively. There are three types of flows in a supply chain that require careful planning and coordination. Material flows involve both physical product flows from suppliers to customers through the chain as well as the reverse flows via product returns, servicing, recycling, and disposal. Information flows involve order transmission and delivery status. Financial flows involve credit terms, payment schedules, and consignment and title ownership arrangements. These flows cut across companies and sometimes ownership arrangements. These flows cut across companies and sometimes even industries [1]. Key Issues and Conflicts The research of Supply Chain Management processes focuses on the coordination and integration of the flows in a supply chain consisting of multiple sites and organizations with multiple independent decision makers. The types of research in Supply Chain Management can be: Theoretical work motivated by real life problems and situations Applications based on real cases Conceptual work that provides a framework to analyze problems in industry Empirical studies based on real data Surveys of existing literature and industrial practice [1] Key research issues and topics include: product and process designs for supply chain management; structuring supply chains for mass customization; third party logistics; outsourcing and contract manufacturing; supplier contracting; incentive and performance measures; global supply chain management; quick response and cycle time reduction; multi-product and multi-location production and inventory coordination; consolidation, warehousing, scheduling and coordination of transportation and production flows; and industry-wide supply chain integration. References: [1] “Editorial objectives for Supply Chain Management.” Management Science, http://www.informs.org/Pubs/Mansci/statements.html#SUP [2] Discussion with Dr. Danial Zeng, Department of MIS, University of Arizona, December 12, 2000. 55 Key researchers Gerard P. Cachon University of Pennsylvania (2000 – present), Duke University (previous) Email: gpc@mail.duke.edu Webpage: www.duke.edu/~gpc Research area: supply chain management; incentives in operations management, electronic commerce Fangruo Chen Columbia University Email: fc26@columbia.edu Webpage: http://www.columbia.edu/cu/business/divisions/mgmtsci/chen.html Research area: supply chain management Hau L. Lee Stanford University Email: Hau.Lee@forsythe.stanford.edu Webpage: www-ieem.stanford.edu/faculty/lee/lee.html Research area: production and operations management, with special interest in supply chain management, global logistics and distribution systems, inventory management, information systems and logistics restructuring, manufacturing and distribution interface, and manufacturing strategy. Paul H. Zipkin Duke University Email: PaulZipkin@Duke.Edu Webpage: http://faculty.fuqua.duke.edu/%7Ezipkin/bio/index.htm Research area: operations management, inventory management, supply-chain management and analysis Key papers Lee H.L., Padmanabhan V., and Whang S. “Information distortion in a supply chain: The bullwhip effect.” Management Science, April 1997, Vol. 43, Iss. 4; pg. 546, 13 pgs. A series of companies in a supply chain is considered, each of who orders from its immediate upstream member. In this setting, inbound orders from a downstream member serve as a valuable informational input to upstream production and inventory decisions. It is claimed that the information transferred in the form of orders tends to be distorted and can misguide upstream members in their inventory and production decisions. In particular, the variance of orders may be larger than that of sales, and the distortion tends to increase as one moves upstream - a phenomenon termed the bullwhip effect. Four sources of the bullwhip effect are analyzed: demand signal processing, rationing game, order batching, and price variations. Actions that can be taken to mitigate the detrimental impact of this distortion are also discussed. 56 Cachon G.P., Lariviere M.A. “Capacity choice and allocation: Strategic behavior and supply chain performance.” Management Science, August 1999, 45, 8, 1091-1109. A simple supply chain in which a single supplier sells to several downstream retailers is considered. The supplier has limited capacity, and retailers are privately informed of their optimal stocking levels. If retailer orders exceed available capacity, the supplier allocates capacity using a publicly known allocation mechanism, a mapping from retailer orders to capacity assignments. It is shown that a broad class of mechanisms is prone to manipulation; retailers will order more than they need to gain a more favorable allocation. Another class of mechanisms induces the retailers to order exactly their needs, thereby revealing their private information. However, there does not exist a truthinducing mechanism that maximizes total retailer profits. The supplier's capacity choice is also considered. It is shown that a manipulable mechanism may lead the supplier to choose a higher level of capacity than one would under a truth-inducing mechanism. Nevertheless, one's choice will appear excessively restrictive relative to the prevailing distribution of orders. Cachon, G.P. “Managing supply chain demand variability with scheduled ordering policies.” Management Science, June 1999, Vol. 45, 6, 843-857. Supply chain demand variability is studied in a model with one supplier and N retailers that face stochastic demand. Retailers implement scheduled ordering policies: Orders occur at fixed intervals and are equal to some multiple of a fixed batch size. A method is presented that exactly evaluates costs. Previous research demonstrates that the supplier's demand variance declines as the retailers' order intervals are balanced, i.e., the same number of retailers order each period. It is shown that the supplier's demand variance will (generally) decline as the retailers' order interval is lengthened or as their batch size is increased. Lower supplier demand variance can certainly lead to lower inventory at the supplier. It is found that reducing supplier demand variance with scheduled ordering policies can also lower total supply chain costs. Chen F. “Decentralized supply chains subject to information delays.” Management Science, August 1999, Vol. 45, Iss. 8, 1076-1091. A supply chain whose members are divisions of the same firm are considered. The divisions are managed by different individuals with only local inventory information. Both the material and information flows in the supply chain are subject to delays. Under the assumption that the division managers share a common goal to optimize the overall performance of the supply chain, the optimal decision rules for the divisions are characterized. The team solution reveals the role of information leadtimes in determining the optimal replenishment strategies. It is shown that the owner of the firm can manage the divisions as cost centers without compromising the systemwide performance. This is achieved by using an incentive-compatible measurement scheme based on accounting inventory levels. The impact of irrational behavior on supply chain performance is investigated. It is important for the upstream members of the supply chain to have access to accurate customer demand information. Gavirneni S., Kapuscinski R., and Tayur S. "Value of information of capacitated supply chains.” Management Science, January 1999, Vol. 45, Iss. 1; pg. 16, 9 pgs. 57 Information flow is incorporated between a supplier and a retailer in a two-echelon model that captures the capacitated setting of a typical supply chain. Three situations are considered: 1. A traditional model where there is no information to the supplier prior to a demand to him except for past data, 2. The supplier knows the (s, S) policy used by the retailer as well as the end-item demand distribution, and 3. The supplier has full information about the state of the retailer. Order up-to policies continue to be optimal for models with information flow for the finite horizon, the infinite horizon discounted and the infinite horizon average cost cases. Study of these three models enables one to understand the relationships between capacity, inventory, and information at the supplier level, as well as how they are affected by the retailer's (S - s) values and end-item demand distribution. The savings at the supplier due to information flow are estimated and when information is most beneficial is studied. 58 Systems Analysis and Design Key Issues 1.Software has become an integral part of world's economy. Software development and deployment remain labor-intensive and intellectually demanding, requiring the best from developers who must play a number of roles. There are still problems in the process of making complex software. 2. Shortening cycle time for software projects with more efficiency. 3.Techniques for reuse of software. 4.New techniques for analysis and design- like UML. Further growth into the object oriented approach. Key Researchers Tom DeMarco Tom DeMarco is a principal of the Atlantic Systems Guild, a computer systems think tank with offices in the US, Germany, and Great Britain. He was the winner of the 1986 Warnier Prize for "lifetime contribution to the field of computing. His work includes Peopleware: Productive Projects and Teams and Software State-of-the-Art (with coauthor Tim Lister); Structured Analysis and System Specification; Controlling Software Projects: Management, Measurement and Estimation; Why Does Software Cost So Much? and Other Puzzles of the Information Age; and a ground-breaking training video Productive Teams. He has written more than 100 articles and papers about management and the system development process. From his early seminal work on structured analysis, to his later contributions in the areas of software metrics and team building, Mr. DeMarco has established himself as a pioneer and leader in the software profession. He is a member of the IEEE Software Editorial Board, and was chosen to serve as guest editor for that journal's May, 1997 Special Issue on Risk Management. He is a faculty member of Cutter Consortium Grady Booch Grady Booch is one of the leading software development methodologists in the world. Along with Rational colleagues Ivar Jacobson and Jim Rumbaugh, Grady developed the Unified Modeling Language (UML), the industrystandard language for specifying, visualizing, constructing, and documenting the artifacts of software systems. The UML was officially adopted as a standard by the Object Management Group (OMG) in 1997. His work centers primarily around complex software systems. Booch is the author of four books, including "Object-Oriented Analysis and Design," and "Object Solutions: Managing the Object-Oriented Project." He is a member of AAAS, IEEE, and CPSR, and is both an ACM Fellow and Rational Fellow. Currently he is the chief scientist at Rational Software. 59 Michael Fagan During his development career, Michael created the inspection process for use on his own projects. He created the Fagan Defect-Free Process, incorporating Formal Process Definition, and reinforcing the Continuous Process Improvement aspect of the Inspection Process. Using the inspection method, he was also able to use its metrics to monitor projects and keep them on track. The methodology developed by Michael Fagan is credited with dramatically reducing the number of defects in software and hardware products, increasing the feature content per release, shortening cycle time, increasing customer satisfaction, improving development processes, accelerating SEI/CMM maturity in organizations, and significantly reducing costs! He was the first software senior technical staff member in IBM's T.J. Watson Research Laboratory; a member of the Corporate Technology Staff; and, one of the founder members of the IBM Quality Institute. After creating the Inspection Process in 1972, he continued refining the methodology, incorporating Formal Process Definition, and reinforcing the Continuous Process Improvement aspect of the Fagan Inspection Process. Since 1989, when he formed Michael Fagan Associates, he has continued to refine the methodology and has also found ways to help facilitate its very rapid implementation in more than 60 organizations. From 1983 to 1985, Michael Fagan was a Visiting Professor in the Department of Computer Science at the University of Maryland. Michael Fagan Associates in located in Palo Alto, California. Roger S. Pressman Roger S. Pressman is an internationally recognized consultant and author in software engineering. For over 25 years, he has worked as a software engineer, manager, professor, author, and consultant, focusing on software engineering issues. Dr. Pressman specializes in helping companies establish effective software engineering practices. He is the developer of Process Advisor, the industry's first self-directed software process improvement product, and Essential Software Engineering, a comprehensive video curriculum. Dr. Pressman is the president of R.S. Pressman and Associates. Dr. Pressman is the author of six books and many technical and management articles. His book Software Engineering: A Practitioner's Approach, is the world's most widely used software engineering textbook. He is also on the Editorial Board of IEEE Software and is Series Advisor for the McGraw-Hill Systems Design and Implementation Series. He is a member of the IEEE, ACM, and Tau Beta Pi. Watts S. Humphrey Watts S. Humphrey founded the Software Process Program of the Software Engineering Institute (SEI) at Carnegie Mellon University. He is a Fellow of the Institute and is a research scientist on its staff. His publications include many technical papers and seven books. His most recent books are "Managing the Software Process" (1989), "A Discipline for Software Engineering" (1995), "Managing Technical People" (1996), "Introduction to the Personal Software Process" (1997), and "Introduction to the Team Software Process" (2000). Humphrey was responsible for developing improved software engineering process methods. He has continued to work closely with software engineers in industry and government, helping them to implement these improved methods. Before joining the SEI, Humphrey was with IBM for 27 years 60 in various technical and management positions. He is a Fellow of the SEI and the IEEE, a member of the ACM, a past member of the Malcolm Baldridge national Quality Award Board of Examiners, and a holder of five issued U.S. patents. He lives in Sarasota Florida. Edward Yourdon Ed has worked in the computer industry for 36 years, beginning when Digital Equipment Corporation innocently risked the downfall of Western civilization by hiring him as a starry-eyed undergraduate student in 1964 to write the FORTRAN math library for the PDP-5 and the assembler for the popular PDP-8 minicomputer. During his career, he has worked on over 25 different mainframe computers, and was involved in a number of pioneering computer technologies such as time-sharing operating systems and virtual memory systems. He was a co-developer of the Yourdon/Whitehead method of object-oriented analysis/design and the popular Coad/Yourdon OO methodology. Ed is the author of over 250 technical articles; he has also authored or coauthored 26 computer books since 1967. Key Papers/Books DeMarco, T. (1979). Structured Analysis and System Specification. Prentice-Hall. This classic book of tools and methods for the analyst brings order and precision to the specification process as it provides guidance and development of a structured specification. Covers functional decomposition; data dictionary; process specification; system modeling; structured analysis for a future system. Pressman, R. S. (1997). Software Engineering: A Practitioner's Approach. McGraw-Hill. This book explains all the important topics in software engineering. It is the most widely used software engineering textbook in the world. Yourdon, E., and Constantine, L. (1979). Structured Design. Prentice-Hall. Grady Booch: Object-Oriented Development. TSE 12(2): 211-221 (1986) According to the author, functional development methods suffer from several fundamental limitations: they do not effectively address data abstraction and information hiding, they are generally inadequate for problem domains with natural concurrency and they are often not responsive to changes in the problem space. Rick DeNatale, Grady Booch, Peter Coad, Dave A. Thomas, John Tibbets: The Role of Methods and CASE in OO Development (Panel). OOPSLA 1992: 145 Barry W. Boehm, Tom DeMarco: Guest Editors' Introduction: Software Risk Management. IEEE Software 14(3): 17-19 (1997) Tom DeMarco: The Role of Software Development Methodologies: Past, Present, and Future. ICSE 1996: 2-4 61 Dennis J. Frailey, "Reducing Cycle Time," Software Development, August 2000 According to this article the "cycle time" delays are caused by three fundamental problems: variability; overly complex processes; and bottlenecks and constraints. The author goes on to say that "a more fundamental symptom of cycle-time problems is rework. The more you do things over, the more [work in process] you'll have, which means you add cost and introduce delays. Michael E. Fagan: Design and Code Inspections to Reduce Errors in Program Development. IBM Systems Journal 38(2/3): 258-287 (1999) Michael E. Fagan: Design and Code Inspections to Reduce Errors in Program Development. IBM Systems Journal 15(3): 182-211 (1976) Michael E. Fagan: Advances in Software Inspections. TSE 12(7): 744-751 (1986) 62 Telecommunication Key Theories and Issues Today's computer communication networks are based on a technology called packet switching. Data to be communicated is broken into small chunks that are labeled to show where they come from and where they are to go. Packets are forwarded from one computer to another until they arrive at their destination. If any are lost, they are re-sent by the originator. The recipient acknowledges receipt of packets to eliminate unnecessary re-transmissions. ARPANET, a pioneering work in the networking field, was initiated in 1969. Since then numerous networking research was progressed to solve the problem of linking different kinds of packet networks together without requiring the users or their computers to know much about how packets moved from one network to another. A new set of computer communication protocols, TCP/IP (Transmission Control Protocol and Internet Protocol), that would allow multiple packet networks to be interconnected in a flexible and dynamic way were developed to speed up the invention of what was later known as Internet. By the mid-1980s there was sufficient interest in the use of Internet for business implementation. An experimental electronic mail relay was built and put into operation in 1989 and its commercial use has exploded. The Internet has been experiencing exponential growth in the number of networks, number of hosts, and volume of traffic. One of the major forces behind the exponential growth of the Internet is a variety of new capabilities in the network -- particularly directory, indexing, and searching services that help users discover information in the vast sea of the Internet. Many of these services have started as university research efforts and evolved into businesses. The World Wide Web was first used in experimental form in 1989, and researchers developed a graphical browser for the Web which, combined with hypertext, started a new telecommunication era. Future Work It is risky to predict the future of something as dynamic as the Internet. It seems safe to state that there will be a continuing explosion of new services. There is every reason to believe that the Internet will transform education, business, government, and personal activities in ways we cannot fully fathom. The main challenge would come from how to predict the future networking trend and catch up with the rapid technical evolution while there is almost no clue to predict for the future. Key Researchers Robert E. Kahn (http://www.cnri.reston.va.us/bios/kahn.html) Robert E. Kahn is president of the Corporation for National Research Initiatives (CNRI). He worked at Bell Laboratories, and taught at MIT. He later joined Bolt Beranek and 63 Newman, DARPA. Dr. Kahn conceived the idea of open-architecture networking. He is a co-inventor of the TCP/IP protocols and was responsible for originating DARPA's Internet Program. Dr. Kahn also coined the term National Information Infrastructure (NII) in the mid 1980s, widely known as the Information Super highway. In his recent work, Dr. Kahn has been developing the concept of a digital object infrastructure as a key middleware component of the NII. This notion is providing a framework for interoperability of heterogeneous information systems and is being used in several applications. He is a co-inventor of Knowbot programs, mobile software agents in the network environment. Dr. Kahn is a member of the National Academy of Engineering, a Fellow of the IEEE, a Fellow of AAAI. He is also a member of the President's Information Technology Advisory Committee. He is a recipient of numerous awards by his outstanding work. Vinton G. Cerf ( http://www.stupi.se/Internauts/htmls/Vint-Cerf.html ) Vinton Cerf is senior Vice president of data architecture for MCI's Data and Information Services Division, a unit of MCI Business Markets. Cerf recently was vice president of the Corporation for National Research Initiatives (CNRI), where he conducted national research efforts on information infrastructure technologies. Cerf co-developed the computer networking protocol, TCP/IP, widely used in the industry and for communications, and known collectively as the Internet. From 1982 to 1986, Cerf was vice president of MCI Digital Information. He played a major role in sponsoring the development of Internet-related data packet technologies. Cerf is a fellow of the IEEE, ACM and AAAS, and the recipient of numerous awards and commendations in connection with his work on the Internet. He also has served as president of the Internet Society since 1992. Ted Nelson (http://www.sfc.keio.ac.jp/~ted) Ted Nelson is currently a Visiting Professor of Environmental Information, Keio University, Japan. He is best known for coining terms "hypertext" and "hypermedia," 1963 (first published 1965), and as founder and pursuer of Project Xanadu, the name for Ted Nelson's hypertext work since 1960. Ted Nelson foresaw long ago the use of hypertext on a world-wide network. The structures he and his group designed during the 1960s through 1980s were to make it possible to annotate and reuse electronic documents, as well as create a new zone of copyright. During the past four years in Japan, aided by colleagues, Nelson has been redefining a component Xanadu for the new Internet environment, unpacking the one unified idea of Xanadu into many separately achievable parts. David Clark (http://ana-www.lcs.mit.edu/anaweb/clark.html) David Clark is senior research scientist of MIT Laboratory for Computer Science. He had worked at Multics, and Arpanet managing the development of the ARPA network protocols. He was one of the developers of key token ring LAN concepts. He currently heads the Advanced Network Architecture research group. In the security area, Dr. Clark developed an information security model that stresses integrity of data. 64 His current research interests are protocols and architectures for very large and very highspeed networks. Specific activities include the development of methods to support realtime traffic in the Internet, and new models of network service to support distributed information systems. Dr. Clark is a member of the IEEE and the ACM. He received the ACM SigComm award and the IEEE Award for his work on the Internet. He chaired the Internet Activities Board as well as a study committee of the National Academy of Sciences. Deborah Estrin (http://lecs.cs.ucla.edu/~estrin/) Deborah Estrin is currently an Associate Professor of Computer Science Department of University of Southern California. Dr. Estrin’s work has focused on the design of network and routing protocols for very large, global, networks. Her current research interests are in scalable multicast routing protocols, multicast-oriented reservation setup protocols, inter-domain routing for global internets, adaptive routing to support multimedia applications, and design tools and techniques for developing scalable network protocols. Dr. Estrin is a member of the ACM and AAAS. She has served on several panels for the NSF, National Academy of Sciences/CSTB, ARPA, and Office of Technology Assessment. In 1987, she received the National Science Foundation Presidential Young Investigator Award for her research in network interconnection and security. Roch Guerin (http://www.seas.upenn.edu:8080/~guerin/) Roch Guerin is currently the Alfred Fitler Moore Professor of Telecommunications Networks in the University of Pennsylvania. After graduating from Caltech, he worked at the IBM T.J. Watson Research Center. His current research interests are in the areas of networking and Quality-of-Service, and in particular the intersection of the above two areas. The issues of his interest include randomization in QoS routing, advance reservations, and the impact of aggregation on service guarantees and verification capabilities. Key Articles “Compatibility or Chaos in Communications”, Sanders, Ray W.; Cerf, Vinton G.; Datamation, Barrington; Mar. 1976; Vol. 22, Issue 3. A conflict is developing in data-communications in transmitting data between the manufacture’s equipment and other brands. The users are pushing to erase as many major incompatibilities as possible. Network Standardization would benefit both sides by giving users more choice of equipment while opening new markets that would be economically feasible due to resource sharing. Users must have a greater comprehension of networks. An explanation of networks, access methods, layers of network access protocols, physical link, and packet-level protocol is presented. Also discussed are the protocols on top of protocols – link control header, packet header, information field, and control trailer, graph and diagram. 65 “Information Processing Technology for Emergency Management”, Kahn, Robert E. Information Society, New York; 1985. Several information-processing technologies are capable of augmenting human performance in handling a range of emergency situations. Technological areas that are particularly important to emergency management are: communications, computers, machine intelligence, and security. Both conventional and emerging technologies are important in the area of communication networks. Some of the systems that have proved useful in enhancing information collection, transmission, and selective processing are: packet radio networks, satellite network technology, expert planning systems, Interneting, and machine intelligence. Packet radio and multiple satellite technology, both based on packet-switching, can make a considerable difference, and computer-based Internetwork -systems will initially be most useful for communicating messages electronically. To be effective, information technology must be integrated into daily patterns to make its use comfortable and familiar. “The Heart of Connection: Hypermedia Unified by Transclusion”, Nelson, Ted; Association for Computing Machinery, New York; Aug 1995; Vol. 38, Issue 8. The development of a system for massive parallel creative work and study is discussed. The system is intended to be a technical, legal, and commercial basis for a worldwide populist and participatory electronic literature of freely weaving screen transmedia republishable and quotable without restrictions - to the betterment of human understanding and freedom of expression and access. The central idea is the concept of transclusion, or reuse with original context available, through embedded shared instancing (rather than duplicate bytes). Thus the user may intercompare contexts of what is re-used, both for personal work and publication. The elements of transclusion are discussed. “Intradomain Qos Routing In IP Networks, A Feasibility And Cost/Benefit Analysis”, Guerin, Roch, IEEE Network, 1999. Constraint-based routing gradually becomes an essential enabling mechanism for a variety of emerging network services. In this work the workers build on previous results on the cost of QoS routing and investigate the performance/cost trade-offs involved in the operation of a representative QoS routing architecture, elaborate on the constituents of this cost, and identify the main methods for containing the cost that QoS routing incurs on routers. The results show that the cost of QoS routing is not excessive and that there exist operational configurations, which can achieve reasonable performance gains with only a minimal increase in processing cost when compared to conventional best-effort routing. “An Analysis of TCP Processing Overhead”, David Clark; V. Jacobson, J. Romkey; H. Salwen, IEEE Communications Magazine, June 1989, Vol. 27, No. 6. The transport layer of the protocol suite, especially in connectionless protocols, has considerable functionality and is typically executed in software by the host processor at the end points of the network. It is thus considered a likely source of processing overhead. However, a preliminary examination has suggested to the authors that other aspects of networking may be a more serious source of overhead. To test this proposition, 66 a detailed study was made of the Transmission Control Protocol (TCP), the transport protocol from the Internet protocol suite. In this set of protocols, the functions of detecting and recovering lost or corrupted packets, flow control, and multiplexing are performed at the transport level. The results of that study are presented. It is concluded that TCP is in fact not the source of the overhead often observed in packet processing, and that it could support very high speeds if properly implemented. “Controls for Interorganization Networks”, Estrin, Deborah; IEEE Transactions On Software Engineering, New York; Feb 1987; Vol. SE13, Issue 2. Interorganization computer networks support person-to-person communication via various methods. Because of most firms' desire for limited access of resources to outsiders, interorganization networks (ION) have unique usage-control requirements. A conceptual model for implementing usage control in IONs is described. Usage control requirements in networks that cross organization boundaries are discussed. The analysis indicates that category sets and nondiscretionary control mechanisms can be employed to isolate strictly internal facilities from ION facilities and distinct IONs from one another. Attention is then focused on the problem of authentification in IONs -- an essential component of the proposed control mechanisms. 67 Workflow Introduction 1. Definition - Workflow The computerized facilitation or automation of a business process, in whole or part. Workflow is often associated with Business Process Re-engineering, which is concerned with the assessment, analysis, modeling, definition and subsequent operational implementation of the core business processes of an organization (or other business entity). 2. Definition - Workflow Management System A system that completely defines, manages and executes “workflows” through the execution of software whose order of execution is driven by a computer representation of the workflow logic. The Evolution of Workflow The evolution of workflow as a technology has thus encompassed a number of different product areas. Image Processing Document Management Electronic Mail and Directories Groupware Applications Transaction-based Applications Project Support Software BPR and Structured System Design Tools Separation of workflow functionality Trends Workflow Automation Workflow Analysis Workflow and E-Commerce Workflow and AI 68 Key People Christoph Bussler Oracle Corporation, USA Email: Christoph.Bussler@Informatik.Uni-Erlangen.DE Webpage: http://www6.informatik.unierlangen.de/history/people/bussler.html Research areas: Organizational policy management in workflow management systems, generic workflow models, architecture of highperformance workflow management systems, and mobility aspects of workflow management Clarence Ellis University of Colorado at Boulder Email: Skip@Colorado.EDU Webpage: http://rintintin.colorado.edu/~skip/ Research areas: Workflow technology, groupware, cognitive science (group cognition), computer supported cooperative work, object oriented systems, systems modeling, databases, group user interfaces, and distributed systems. Stefan Jablonski University of Erlangen-Nuernberg, Germany Email: Stefan.Jablonski@Informatik.Uni-Erlangen.DE Webpage: http://www6.informatik.uni-erlangen.de/Staff/jablonski.html Research areas: Workflow management, business process and enterprise modeling, systems integration, transaction management, and database management Amit P. Sheth University of Georgia Email: amit@cs.uga.edu Webpage: http://lsdis.cs.uga.edu/~amit/ Research areas: Interoperable information systems and enterprise application integration (esp. workflow management), global information systems (esp. management of heterogeneous digital media, information brokering, the logical/semantic view of the web through use of broad variety metadata and ontologies). J. Leon Zhao University of Arizona Email: lzhao@bpa.arizona.edu Webpage: http://shell.bpa.arizona.edu/~lzhao/ Research areas: Development of database and workflow technologies and their applications in electronic commerce, knowledge management, and organizational process automation. 69 Key Papers Dimitrios, Mark Hornick and Amith Sheith An Overview of Workflow Management: From Process Modeling to Workflow Automation Infrastructure, Distributed and Parallel Database, 3, 119-153 (1995) Today's business enterprises must deal with global competition, reduce the cost of doing business, and rapidly develop new services and products. To address these requirements enterprises must constantly reconsider and optimize the way they do business and change their information systems and applications to support evolving business processes. Workflow technology facilitates these by providing methodologies and software to support (i) business process modeling to capture business processes as workflow specifications, (ii) business process reengineering to optimize specified processes, and (iii) workflow automation to generate workflow implementations from workflow specifications. This paper provides a high-level overview of the current workflow management methodologies and software products. In addition, it discusses the infrastructure technologies that can address the limitations of current commercial workflow technology and extend the scope and mission of workflow management systems to support increased workflow automation in complex real-world environments involving heterogeneous, autonomous, and distributed information systems. In particular, it discusses how distributed object management and customized transaction management can support further advances in the commercial state of the art in this area. 2. Akhil Kumar; J Leon Zhao; Dynamic routing and operational controls in workflow management systems; Management Science, Providence; Feb 1999; 45, 2; 253-273. Businesses around the world are paying more attention to process management and process automation to improve organizational efficiency and effectiveness. A general framework for implementing dynamic routing and operational control mechanisms in workflow management systems (WMS) is described. The framework consists of three techniques: workflow control tables, sequence constraints, and event-based workflow management rules. This approach offers several unique features that are missing in commercial workflow management systems: 1. It provides more flexibility in process modeling and control. 2. It permits rework on an ad hoc basis. 3. It handles exceptions to routing and operational controls. 4. It exploits parallelism to increase system throughput and response time. Finally, the workflow management techniques are applied to the case of consumer loan management and compared with other approaches based on static routing. 3. W.M.P. van der Aalst, The Application of Petri Nets to Workflow Management , Department of Mathematics and Computer Science reports, Eindhoven University of Technology. Workflow management promises a new solution to an age-old problem: controlling, monitoring, optimizing and supporting business processes. What is new about workflow management is the explicit representation of the business process logic which allows for computerized support. This paper discusses the use of Petri nets in the context of workflow management. Petri nets are an established tool for modeling and analyzing processes. On the one hand, Petri nets can be used as a design language for the 70 specification of complex workflows. On the other hand, Petri net theory provides for powerful analysis techniques which can be used to verify the correctness of workflow procedures. This paper introduces workflow management as an application domain for Petri nets, presents state-of-the-art results with respect to the verification of workflows, and highlights some Petri-net-based workflow tools. 4. Christoph Bussler, Stefan Jablonski; Implementing Agent Coordination for Workflow Management Systems Using Active Database Systems. RIDE-ADS 1994: 53-59 One crucial function of a workflow management system (WFMS) is to assign tasks to users who are eligible to carry them out. Except in simple workflow scenarios, roles such as secretary and manager are not a sufficient basis for determining eligibility. Additionally, WFMSs are deployed not only in group settings by small companies but also worldwide by large enterprises. Since local laws and business policies have to be followed, task assignment policies for the same task generally differ from country to country and, therefore, must be specified locally. The Policy Resolution Architecture (PRA) model provides more generality and expressiveness than role models do and at the same time supports the independent specification of task assignment policies in different parts of an enterprise. PRA can be used to model arbitrary organization structures and to define realistic task assignment (eligibility) rules by means of precisely defined organizational policies. Thus, PRA provides real-world organizations with a precise, simple means of expressing their complex task assignment policies. 71 Appendix A Name Lynda M Applegate Yannis Bakos Frank Biocca Grady Booch Organization Harvard University New York University Michigan State University Gerard P Cachon Vinton G. Cerf University of California, Los Angeles Massachusetts Institute of Technology Oracle Corporation University of Pennslvnia MCI Fangruo Chen Columbia University Hsinchun Chen University of Arizona Massachusetts Institute of Technology University of Massachusetts, Amherst Georgetown University Christine L. Borgman Erik Brynjolfsson Christoph Bussler David Clark W. Bruce Croft Mary J. Culnan Thomas Davenport Tom DeMarco Peter J. Denning Jerry DeSanctis Vinton G. Cerf Moshe Dror Clarence Ellis Deborah Estrin Michael Fagan Edward A. Feigenbaum Marshall Fisher R. Brent Gallupe Seymour E. Goodman Roch Guerin Watts S. Humphrey Edward A. Fox Boston University George Mason University Duke University MCI University of Arizona University of Colorado at Boulder University of Southern California Stanford University University of Pennsylvania Queens University Georgia Institute of Technology University of Pennsylvania Virginia Polytechnic Institute and State University Research Field E-Commerce E-Commerce CMC/HCI/Communication/Visualiz ation Systems Analysis and Design Knowledge Management / Information Retrieval Information Economics Workflow Operations Research/Supply Chain Management Telecommunication Operations Research/Supply Chain Management Artificial Intelligence/Knowledge Management Knowledge Management / Information Retrieval Telecommunication Information Retrieval Social/Ethical/psychological issues Information Retrieval Systems Analysis and Design Computing Policy Group Support Systems Telecommunication Operations Research Workflow Telecommunication Systems Analysis and Design Artificial Intelligence/Knowledge Management Operations Research Group Support Systems Computing Policy Telecommunication Systems Analysis and Design Information Retrieval 72 Knowledge Management / Information Retrieval Knowledge Management / Information Retrieval Stefan Jablonski Sirkaa L. Jarvenpaa Ellis Johnson Karen Sparck Jones Robert E. Kahn Sara Kiesler Won Kim Robert Kling Robert Kraut Charles H. Kriebel Hau L. Lee Stuart E. Madnick Gary Marchionini John McCarthy Haim Mendelson Tridas Mukhopadhyay Ted Nelson Theodor Holm Nelson George Nemhauser Peter G. Neumann Jakob Nielsen Eli M. Noam Donald Norman Jay F. Nunamaker, Jr. University of ErlangenNuernberg, Germany University of Texas at Austin Georgia Institute of Technology University of Cambridge Corporation for National Research Initiatives Carnegie Mellon University Cyber Database Solutions, Inc. Indiana University at Bloomington Carnegie Mellon University Carnegie Mellon University University of Stanford Massachusetts Institute of Technology Stanford University Stanford University Carnegie Mellon University Keio University, Japan Keio University Georgia Institute of Technology Daniel E. O'Leary Columbia University Apple Computer, Inc. University of Arizona University of Southern California Gary M. Olson University of Michigan Judy Olson University of Michigan Massachusetts Institute of Technology Massachusetts Institute of Technology Wanda J. Orlikowski James B. Orlin Roger S. Pressman Sudha Ram University of Arizona Workflow Group Support Systems Operations Research Information Retrieval Telecommunication Group Support Systems Social/Ethical/psychological issues Database Social/Ethical/psychological issues CMC/HCI/Communication/Visualiz ation Computing Policy Information Economics Operations Research/Supply Chain Management Database Information Retrieval Artificial Intelligence/Knowledge Management E-Commerce E-Commerce Telecommunication Artificial Intelligence/Knowledge Management Operations Research Computing Policy CMC/HCI/Communication/Visualiz ation Computing Policy Social/Ethical/psychological issues Group Support Systems Knowledge Management / Information Retrieval Knowledge Management / Information Retrieval Group Support Systems Group Support Systems Operations Research Systems Analysis and Design Database 73 Information Economics Social/Ethical/psychological issues CMC/HCI/Communication/ Visualization Raj Reddy Gerard Salton (1927-1995) Jerome Howard Saltzer Omar El Sawy Roger c. Schank Amit P. Sheth Ben Shneiderman Barbara Simons Herbert A. Simon Lee Sproull Sherry Turkle Douglas R. Vogel Joseph Walther Suzie Weisband Andrew B. Whinston J. Leon Zhao Paul H. Zipkin Vladimir Zwass Carnegie Mellon University Artificial Intelligence/Knowledge Management Cornell University Massachusetts Institute of Technology University of Southern California Northwestern University University of Georgia Information Retrieval University of Maryland Carnegie Mellon University New York University Massachusetts Institute of Technology City University of Hong Kong Rensselaer Polytechnic Institute University of Arizona University of Texas at Austin University of Arizona Duke University Fairleigh Dickinson University Knowledge Management / Information Retrieval Computing Policy Knowledge Management / Information Retrieval Artificial Intelligence/Knowledge Management Workflow CMC/HCI/Communication/Visualiz ation Computing Policy Artificial Intelligence/Knowledge Management Social/Ethical/psychological issues CMC/HCI/Communication/Visualiz ation Group Support Systems CMC/HCI/Communication/Visualiz ation CMC/HCI/Communication/Visualiz ation E-Commerce Workflow Operations Research/Supply Chain Management E-Commerce 74 Information Economics