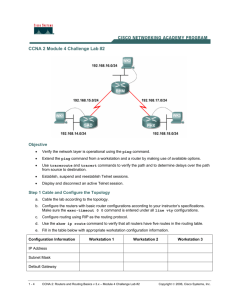
Lab Exercise – Configure the PIX Firewall and a Cisco Router
advertisement
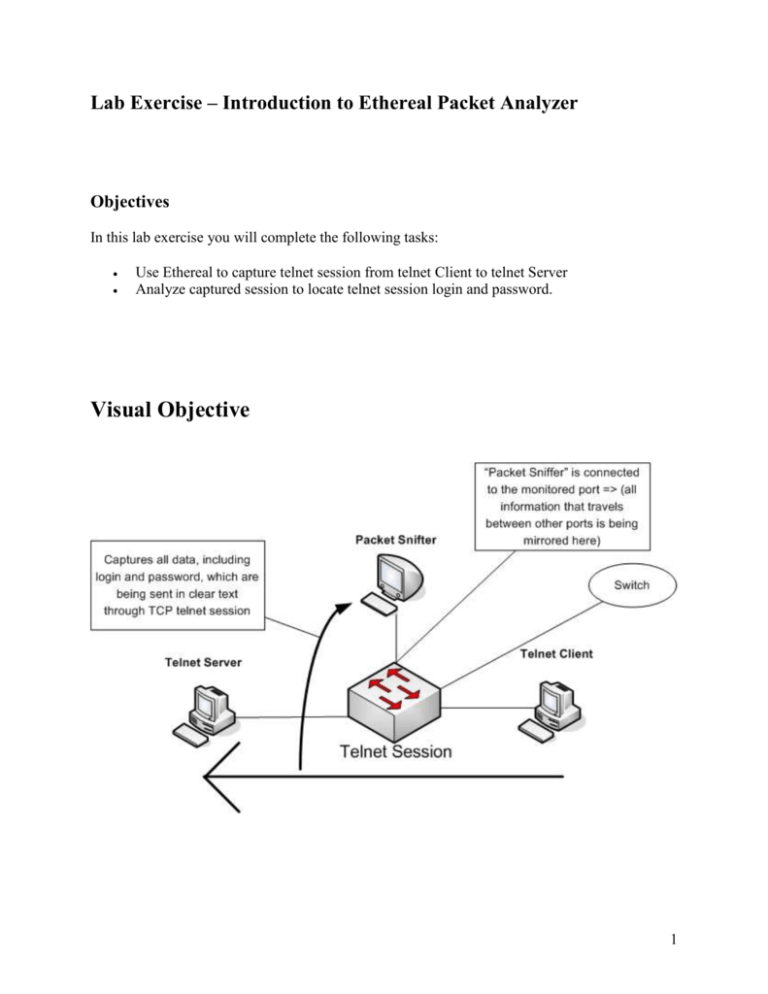
Lab Exercise – Introduction to Ethereal Packet Analyzer Objectives In this lab exercise you will complete the following tasks: Use Ethereal to capture telnet session from telnet Client to telnet Server Analyze captured session to locate telnet session login and password. Visual Objective 1 Ethereal tool/Lab overview Ethereal is a freely available network protocol analyzer tool, also known as “packet sniffer”, which captures packets from the network and decodes them into the format readable by user. Ethereal can operate in two modes – non-promiscuous and promiscuous. In nonpromiscuous mode network interface would check every arriving packet to see if its destination MAC address matches MAC address of network interface card. If it does not, the packet will be dropped. Non-promiscuous mode can be used for debugging network interface problem or such. The promiscuous mode allows you to capture all packets that your network interface receives. Here, we need to mention that there is two network environments – non-switched and switched. In non-switched environment, which is usually created by using a hub, all hosts that are connected to the hub would receive all data that is traveling through the hub medium, but only ones who are interested in it, would retain it. Thus, when one is using promiscuous mode and in non-switched environment, one would pass all information straight to the kernel, without checking whether this information is actually destined to ones interface. On opposite, in switched environment, which is usually created by using a switch, switch would decide where to sent data based on MAC address supplied with it. In switched environment promiscuous mode wouldn’t do much unless switch is configured or tricked to operate accordingly. A switch can be configured with monitor port, which would receive all data that is being transferred through the switch, or one can trick switch into sending specific or all data to interested party. In this lab we would use switch with monitor port, se we can emulate non-switch environment. Important note: All pictures that provided with this instruction are here to describe Ethereal interface and not to show any data associated with the lab! 2 Task 1 – Use Ethereal to capture telnet session from Telnet Client to Telnet Server In this task you will use Ethereal to capture packets from telnet session from telnet client PC to Telnet Server, which would be run by TA. Step 1: Go to PC with Ethereal on it (TA will show you) Run Ethereal by clicking shortcut on desktop. Step 2: Go to capture tab and choose options from drop menu. Capture Options window would open. Here you can setup which network interface you want to use to capture data, activate/deactivate promiscuous mode, direct captured output to specific file, etc. Make sure that you check in Capture packets in promiscuous mode option. Proceed by clicking Start button in the lower right corner of the Capture Options window. After you have clicked Start button, the capture window would show up, meaning that the capture of data has started. While capturing process is being active, the capture window would show the use of network protocols in percentage manner. 3 Step 3: Now, ask TA to proceed with Telnet part of the lab. After TA has finished telnet session click stop button. 4 Task 2 – Analyze captured session to locate telnet session login and password Step 4: As you press Stop button in the capture window, it would close, and other window behind it would display captured packets. Now, to get all data associated with telnet session, you would need to sort data first. To do so, click on the protocol tab, as many times as you need to get all telnet lines together. As you sort it, take screenshot and include it to your report. Then, highlight the top string of telnet protocol and click analyze (menu tab at the top of the window) and then choose follow TCP stream. (see the picture below) Step 5: The new “Follow TCP Stream” window would open and display results; you should be able to see telnet session login and password. Take Screenshot of the log or save it as txt file and add to your report. That’s it. You have reached the end of the lab. By now, you hopefully understand how easy it can be to acquire sensitive data, when it is transmitted in clear text. 5 Grading Rubric Please note that the report would weight only 36% of the grade for this LAB, and your group are only required to give a simple report, such as a serious of step by step snapshots (or screen shots) showing how your group conducts this lab exercise. 64% of your grade would come from the lab quiz, which you will be given individually at the end of the lab in room 202. The quiz questions may deal with not only practical but theoretical aspects of the lab as well. The quiz is intended to check how much attention you have paid to the practical part of the lab and whether you understand the idea behind the lab. Report Writing Requirements The report must include a cover page. Among other things, the name of each group member must be put on the cover page. The contribution of each group member must be summarized in the report. That is, the report should report “who did what” in a clear way. The report must include a series of screen shots showing how the group conducts the lab step by step. Two or more screen shots may need to be associated with one step of the lab. For each step, the screen shots should show both the status before the step and the status (or results) after the step. The screen shots should be properly ordered in the report. 6