networking - Tripod.com
advertisement

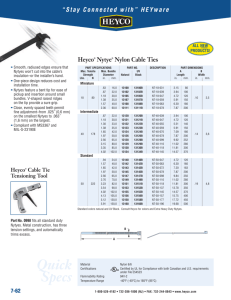
NETWORKING PHYSICAL CABLING LOGICAL NETWORK NETWORK TOPOLOGIES Classification TOPOLOGIES PROTOCOLS HARDWARE TYPES Linear Coaxial Ethernet OSI model Hubs, LAN Star Twisted Pair Token Ring TCP/IP Switches MAN Ring Fiber Optic FDDI IPX Repeaters, WAN Tree ATM NetBIOS/NetBEUI Bridges CAN Mesh Routers, TAN Brouters Gateway DEFINITIONS: A NETWORK consists of two or more computers that are linked in order to share resources (such as printers and CD-ROMs), exchange files, or allow electronic communications. The computers on a network may be linked through cables, telephone lines, radio waves, satellites, or infrared light beams. When any one of these computers are connected to a LAN they are referred to as a WORKSTATION. All computing devices on a network; workstations, printers, etc., are referred to as NODES. When connecting a workstation, the interface hardware is referred to as an ADAPTER. Networking adapters are also commonly referred to as NETWORK INTERFACE CARDS or NICS. Most NIC's break the information into FRAMES or PACKETS of information. The LAN connection for a printer, however, is referred to as a PRINT SERVER and not a NIC. The SERVER is the computer whose resources are shared with other computers. SEGMENTS are trunks of cabling connecting devices to a routing device. A BACKBONE is the foundation of the LAN/WAN where the servers are linked together in a common series of concentration devices. A network where a server acts as a dedicated server and supplies information to workstations is called a CLIENT/SERVER network. A PEER-TO-PEER network is a network where all computers act as both servers and clients and data files can be shared. This network has no one dedicated server. A basic network is made up of primary components. 1. A hub (which acts as the traffic cop on your small information highway. The hub acts as a switch to route information from one terminal to another through the use of cables. 2. an interface card (hardware in each computer that connects to the hub) 3. a server (the central storage computer for information). 4. special cabling 5. computers, printers, scanners, etc. TYPES OF NETWORKS: The three basic types of networks include: Local Area Network (LAN): A Local Area Network (LAN) is a network that is confined to a relatively small area. It is generally limited to a geographic area such as a writing lab, school, or building. Rarely are LAN computers more than a mile apart. Metropolitan Area Network (MAN): A Metropolitan Area Network (MAN) covers larger geographic areas, such as cities or school districts. By interconnecting smaller networks within a large geographic area, information is easily disseminated throughout the network. Local libraries and government agencies often use a MAN to connect to citizens and private industries. Wide Area Network (WAN): Wide Area Networks (WANs) connect larger geographic areas, such as Florida, the United States, or the world. Dedicated transoceanic cabling or satellite uplinks may be used to connect this type of network. CAN: Campus Network TAN: Tine Area Networks are 2 - 3 computers networked at home or in a small business. NETWORK TOPOLOGIES There are two types of topology: physical and logical. The physical topology of a network refers to the configuration of cables, computers, and other peripherals. Logical topology is the method used to pass the information between workstations as can be seen in protocols. PHYSICAL TOPOLOGIES 1. LINEAR BUS A linear bus topology or 10BASE2 bus topology consists of a main run of cable with a terminator at each end. All nodes (file server, workstations, and peripherals) are connected to the linear cable. ETHERNET AND LOCALTALK networks use a linear bus topology. Networking is simple. The network may have or hub or not. DISADVANTAGES Entire network shuts down if there is a break in the main cable. Terminators are required at both ends of the backbone cable. Difficult to identify the problem if the entire network shuts down. Not meant to be used as a stand-alone solution in a large building. 2. STAR TOPOLOGY A star topology is designed with each node (file server, workstations, and peripherals) connected directly to a central network hub or concentrator. A concentrator is a device that provides a central connection point for cables from workstations, servers, and peripherals. Most concentrators contain the ability to amplify the electrical signal they receive. DISADANTAGES Requires more cable length than a linear topology. If the hub or concentrator fails, nodes attached are disabled. More expensive than linear bus topologies because of the cost of the concentrators. This configuration is common with twisted pair cable; however, it can also be used with coaxial cable or fiber optic cable. A simple star topology is also used for 10BASE-T ETHERNET networks. 3. STAR-WIRED RING (TOKEN RING) A STAR-WIRED RING topology may appear (externally) to be the same as a star topology. Instead of having a concentrator at the center of the ring network, there is a device called a MAU (MULTISTATION ACCESS UNIT). Internally, the MAU of a star-wired ring contains wiring that allows information to pass from one device to another in a circle or ring. The MAU does the same thing a hub does, but it works with TOKEN RING networks instead of Ethernet. A Token ring using Unshielded twisted pair in star or modified star transfers at 4 Mbps. A Token Ring configuration using shielded twisted pair in star or modified star configuration transfers at 4 or 16 Mbps. A local Ring Hub allows four-node connections on one MAU port cable. 64 - 72 (max.) nodes are recommended per ring for optimal performance. A double ring may have a maximum of 12 MAU's, each which can support 8 nodes. THe maximum distance between MAU and workstation is 45 m.; MAU to MAU is 120 m. In difference, FDDI (FIBER DISTRIBUTED DATA INTERFACE), pronounced fidee, also uses A COMPLEX token ring topology. FDII networks run on optical fiber cables instead of copper cabling. It's similar to Token Ring but can be connected to 2 MAUS so if one fails, the other can work. The FDDI has an added alternate ring. If a break occurs in either ring, it automatically reroutes the data transmission to the alternate ring. This ring supports speeds up to 100 Mbps. Has become the defacto high speed backbone. Maximum stations are 1000. THe distance limitation is 2 miles. 4. TREE TOPOLOGY A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable. Tree topologies allow for the expansion of an existing network, and enable schools to configure a network to meet their needs. DISADVANTAGES Overall length of each segment is limited by the type of cabling used. If the backbone line breaks, the entire segment goes down. More difficult to configure and wire than other topologies. 5-4-3 RULE: A consideration in setting up a tree topology using Ethernet protocol is the 5-4-3 RULE. One aspect of the Ethernet protocol requires that a signal sent out on the network cable reach every part of the network within a specified length of time. Each concentrator or repeater that a signal goes through adds a small amount of time. This leads to the rule that between any two nodes on the network there can only be a maximum of 5 segments connected through 4 repeaters/concentrators. In addition, only 3 of the segments may be populated (trunk) segments if they are made of coaxial cable. A populated segment is one which has one or more nodes attached to it. This rule does not apply to other network protocols or Ethernet networks where all fiber optic cabling is used. 2. MESH TOPOLOGY In a mesh topology, each device on the network is networked (cabled) to eachother. ADVANTAGES: Mesh topologies are installed where FAULT TOLERANCE is important. A single cable failure would not stop network communications between any two computers. The mesh topology is highly fault tolerant. DISADVANTAGES: More expensive and difficult to install. Requires more cabling since each device is cabled to eachother. CABLING XBaseX classification: 10BaseT, 100BaseT and 10Base2 are networking standards and there are others. The first number is an indication of the transmission speeds involved. It is listed in Mbps (Mega Bits Per Second). The second portion designates Baseband or Broadband, how the data is sent across the cabling. In Baseband one signal takes up the entire bandwith of the cable. This data is digital. With Broadband, the total bandwith of the cabling is divided and there will be many signals traveling through the cabling at a time. Broadband is analog. Broadband signals can travel father then Baseband. The last portion is an indication of wire type and the approximate distances involved or the type of cabling. TYPES OF CABLE There are three types of network wiring. Coaxial Twisted-Pair Fiber Each type of cabling has different requirements if it is to meet network standards. IEEE 802.X SPECIFICATIONS THE INSTITUTE OF ELECTRICAL AND ELECTRONIC ENGINEERING (IEEE) published the 802 specifications. This designed standards for the physical components of a network. 802.1 Internetworking 802.2 Logical Link Control (LLC) 802.3 CSMA/CD LANs (Ethernet) 802.4 Token Bus LAN 802.5 Token Ring LAN 802.6 MAN 802.7 Broadband Technical Advisory Groups 802.8 Fiber Optic Technical Advisory Group 802.9 Integrated Voice and Data Networks 802.10 Network Security 802.11 Wireless Network, etc. The 802 standards break the Data Link Layer further: LOGICAL LINK CONTROL (LLC) - For error correction and control. MEDIA ACCESS CONTROL (MAC) - gives physical addresses to device. Like the TO: and FRO: of an envelope. 1. COAXIAL CABLE Following the IEEE 802.3 Standard, coaxial cable is used for 10BASE2 (thin-net, CheaperNet) and 10BASE5 (thick-net) networking. No concentrator is needed. 10BASE2 is not the most reliable cabling. 10BASE2 and 10BASE5 are used in a LINEAR BUS topology. With Ethernet 10Base2 255 devices cab be connected maximum length of a segment is 185 meters is usually standard industry RG-58 cable o has a solid copper center conductor o braided outer conductor o 50 ohm cable o requires termination at both ends of segment using 50 ohm terminator. Each computer connects to the computer with a T-Connector (BNC - British Naval Connector). With Ethernet 10Base5 is usually standard industry RG-8 or RG-11 cable maximum length of a segment is 500 meters 50 ohm cable requires termination at both ends of segment using 50 ohm terminator. 10Base5 wire is connected not by BNC connectors but by AUI connectors. AUI connectors are a DB15 connector, that is, a D-shaped plug with 15 pins. These look just like RS-232 modem connectors, only about half as broad. These are common on equipment such as routers. 10Base5 cable may also be connected by a vampire connector with clamps holding the cable in place. A vampire tap is a connection to a coaxial cable in which a hole is drilled through the outer shield of the cable so that a clamp can be connected to the inner conductor of the cable. This cable connection is made with a unit that clamps onto and "bites" into the cable, hence the vampire name. 2. TWISTED PAIR CABLING (STP and UTP) Coaxial and SHIELDED TWISTED PAIR (STP) have a copper braid of foil that offers good resistance to electrical noise, but the extra foil creates a larger, thicker cable, making it difficult to pull the cable through conduit and walls during installation. UNSHIELDED TWISTED PAIR (UTP) does not contain this aluminum shielding and is thinner and therefore easier to install. It offers less resistance to electrical noise. STP is used in Token Ring, ARCnet and Appletalk networks. UTP is used in Star Topologies. Unshielded Twisted Pair(UTP) is the next step up from Coaxial. TP cabling is a cable made up of four pairs of insulated copper wires. UTP are 8 copper conductor, four pair wires. RJ45 connectors are fitted on each end of the cable. They resemble a normal telephone plug (RJ11) with the exception of eight pins rather than four. The RJ45 cable connects to a NETWORK PATCH PANEL which is connected to the hub. The RJ45 is an 8 wire (4 pair) media connector. EAI/TIA 568 COMMERCIAL BUILDING WIRING STANDARD for Unshielded TP(UTP): UTP comes in levels of Category 1 - 5. The Electronics Industries Association and the Telecommunication Industries Association (EIA/TIA) created this standard for Unshield Twisted Pair cabling. The higher category cables contain more wire paths and higher number of twists to prevent EMI. Category 1: not rated for performance Category 2: used for telephone wiring sasta rate of 1 magabit per second. Category 3: lowest level that can be used for networking. Used for ETHERNET 10BASE-T. Data rate of 16 megabits per second.Used for data up to 10 Mps Category 4: used for Token Ring and 10BASE-T. Maximum dat rate is 20 megabits per second. Category 5: used for Ethernet 10BASET. Maximum date rate of 155 megabits per second. Used for voice/or data. UTP (Unshieded Twisted Pair) is most commonly used in Category Three (CAT3) or Category Five (CAT5). The difference between the ratings is the number of twists per inch. Higher is better. CAT5 is probably the most commonly seen and used. It is inexpensive, reliable, easy to maintain and expand. COATING ON CABLES: Cable through the ceilings must be plenum-rated and riser-rated and capable of withstanding environmental and fire conditions(riser) without giving off toxic gases(plenum) when it burns. PVC rated is the least expensive but highly flammable. Stripping and Terminating a Cat5 Cable: Illustrated Tutorial. 3. FIBER OPTIC CABLE Standard IEEE 802.8. Rather than using electrical impulses over wire, optical fiber transmits data using pulses of light. It is expensive to install and maintain. The average network administrator lacks the expertise to terminate each end. Fiber can carry data as high as 622 megabits per second. Fiber is not affected by EMI like copper cable and does build up a magnetic field to allow crosstalk. It is very lightweight compared to copper-based cable. LOGICAL TOPOLOGIES A protocol is a set of rules that governs the communications between computers on a network. These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transfer. Logical topologies instruct the hardware how to packet and transmit data across a physical topology. 1. ETHERNET The Ethernet protocol is by far the most widely used. The Ethernet protocol allows for linear bus, star, or tree topologies. Data can be transmitted over twisted pair, coaxial, or fiber optic cable at speeds of 10 Mbps. The foundations of Ethernet is CSMA/CD (Carrier Sense Multiple Access/Collision Detection). In an Ethernet network, all computers share a single network segment, called a collision domain. When 2 computers transmit data along the segment simutaneoulsy, collision occurs. Each computer then can transmit data only when no other computer is transmitting. Ethernet uses CSMA/CD described in the IEEE standard 802.3. Cabling MAX Distance/ Segment Devices/ Segment Topology Max IRLs Max Length of Cable Devices Attached To: Termination Grounded 2.5km (1.5 miles) Standard Thick Ethernet (10Base5) COAXIAL 1640 ft. (500 m) 10 Mbps Speed 100 Workstations per trunk maximum lngth of trunk 500 m. Bus 2 entire network trunk maximum 2500 m. Backbone by use of transceivers 50-ohm resistor (both ends) To earth NICs with built-in BNC transceivers 50-ohm resistor (both ends) To earth 5-4-3 RULE 925m (3035 ft.) Thin Ethernet (10Base2) COAXIAL Shielded (STP) 10Base-T TWISTED PAIR Unshielded (UTP) 10Base-T TWISTED PAIR 607 ft. (185 m) 10 Mbps 30 Workstations per trunk 328 ft. (100 m) 16 - 155 Mbps 328 ft. (100 m) 10 Mbps Speed Bus 2 1024 workstations per network minimum cable length between workstations 20" Token Ring 3 500m Central hub managed or unmanaged None needed Star 3 500m Central hub managed or unmanaged None needed 1023 workstations without bridging 5-4-3 RULE Workstations only 328 ft. from concentrator minimum cable legnth between stations 8 ft. 1023 workstations without bridging 5-4-3 RULE Unshielded 328 ft. (UTP) (100 m) Workstations 100Base-T 100 Mbps only 328 ft. TWISTED Speed from PAIR concentrator Star 3 500m Central hub managed or unmanaged None needed Star 2 4km Fiberoptic hub or repeater None needed minimum cable legnth between stations 8 ft. 10Base-FL FIBER OPTIC 1.2 miles (2 km)(w/5 segments max. is 500m) 100 Mbps - 2 Gbps 2 The Ethernet standard has grown to include faster networks. Cable Type Data Transfer 100BASE-T (fast Ethernet) Speed 100 megabits per second Maximum Distance 20 m. 100BASE-FX (Fast Ethernet on optical fibers) none 100BASE-T4 20 m. 2. TOKEN RING Uses IEEE Standard 802.5, Token Ring is very different from Ethernet. In token ring a single packet is passed around the network. Every computer waits its turn. There are no collisons. Token Ring has the same bandwidth as Ethernet. Too many computers result in network slowness. FDDI is a faster Token Ring configuration (as described above). 3. ATM (Asynchronous Transfer Mode Following IEEE Standard 802.9, ATM is one of the newer topologies. It can carry voice and data over network wire or fiber. ATM transmits packets as 53-byte cells that have a variety of identifiers to detmine such things as Quality of Service or wich packet is to be routed first. Packets are sent their need for bandwidth. For example, email would have a low priority and voice and video a higher priority and be sent first. ATM runs 25 - 622 megabits per second. It is also expensive. NETWORK PROTOCOLS On top of the Logical Topologies are protocols. Protocols handle the translation of data from applications to the logical topology. THe OSI model explain how a network should work. The lower the level the less abstract and more concrete the layer is. Each layer communicates only with the layer above or below it while moving data. OSI MODEL (Open Systems Interconnect) The seven-layer OSI (Open systems Interconnection) model, created by the ISO (International Standards Organization), defines internetworking environments. It provides a description of how software and hardware interact to permit communication between computers. An interface separates each layer from those above and below it; each layer provides services to the layer directly above it. This handy mnemonic will help you keep the layers in proper order: LAYER Application Layer (Rx. the 7. All Application 6. People Presentation 5. Seem Session 4. To Transport 3. Need Network 2. Data Data Link 1. Processing Physical FUNCTION Allows application processes to access network services. PROTOCOLS FTP, SNMP, SMPT NCP HARDWARE Gateway dashboard of your car. The different gauges make you aware of the information that you need to know in order to maintain speed limits and optimal performance for your vehicle. Manages communication between applications. Flow control and error recovery is handled here. Presentation Layer (RX. the universal signs both on the highway and inside your vehicle.) FORMAT Functions as the network’s translator – handles protocol conversion, data translation and encryption, and data compression. The redirector operates here. NCP Gateway Session Layer (Rx. the designated traffic lanes TRAFFIC COP. Provides synchronization between computers; allows applications on two computers to establish a session. None Gateway Transport Layer (Rx Speed recognition devices on a highway) RESPONSIBLE FOR THE ACCURACY OF THE DATA TRANSMISSION. Ensures reliable delivery of packets. Repackages messages, dividing them into smaller packets. Uses protocols TCP, SPX(Sequenced Packet Exchange) from IPX/SPX stack, and NWLink (Microsoft's implementation of IPX/SPX), NetBEUI SPX and TCP packets are connection Gateway protocols. Network Layer (Rx highway exit numbering scheme) Establishes THE UNIQUE NETWORK ADDRESS AND MANAGES THE TRANSPORT OF INFORMATION PACKETS BETWEEN DIFFERENT NETWORKS. Routes the packets and determines the best route for sending them. Manages network traffic problems, packet switching, routing, and reassembling data. IP, IPX, NetBEUI, DLC Router, Brouter Data Link Layer (Rx. Entry ramp/toll booth that allows access onto the highway) DETERMINES HOW DEVICES CONNECTED WILL GAIN ACCESS. Determines how 1's nd 0's are asssembled into frames or packets of data. Sends data frames from the Network Layer to the Physical Layer. Contains the physical address of a device. Like the FROM: and TO: of a envelope. None Bridge, Remote Bridge, Brouter, Switch Physical Layer (Rx. determining if the road infrastructure will be built of concrete or asphalt.) Transmits data bits between computers. Defines how 1's and 0's are interpreted from the medium. DEFINES CABLES, NETWORK INTERFACE CARDS, AND OTHER PHYSICAL None IEEE 802.X Standards Ethernet, Token Ring, FDDI The NIC CARDS, REPEATERS, CONCENTRATORS/HUBS, MAU's, SWITCHING HUBS etc. CABLES - IEEE 802.X ASPECTS. 1. TCP/IP Network Protocol 1. DEFINITION: Stands for Transmission Control Protocol/Internet Protocol. This is the protocol that carries data over the Internet. It is actually a set of protocols o PPP - Point to Point Protocol o SMPT - Simple Mail Transport o TCP - Transmission Control Protocol o IP - Internet Protocol that handles addresses, etc. o FTP - File Transfer Protocol o MIME - Multipurpose Internet Mail Extensions, is more of a standard than a protocol. Used by e-mail applications, it is a method for sending files back and forth between computers through electronic mail. This allows formatted documents created through word processors or spreadsheet programs to be attached to an electronic mail message and arrive on the other end exactly as they were sent. TCP/IP uses 5 layers of the OSI model(1,2,3,4, and 7) 2. IP ADDRESSES: To communicate on the Internet, computers must have unique identifiers in order to differentiate one computer from another. This is accomplished through IP addresses. IP is made up of a 32-bit address or 4 "octet" address. An IP address consists of 4 parts separated by decimal points. 199.250.132.1 128.30.7.10 Every host has at least one unique IP address. In addition, every router has a unique IP address for every network adapter it possesses. However, all hosts on the same physical network must have the same network prefix. (For example, Take a look at the IP addresses on the side of each machine in the lab) 3. DYNAMIC and STATIC NAMING: IP addresses can be assigned uniquely by the administrator or assigned dynamically by a DHCP (DOMAIN HOST CONFIGURATION PROTOCOL) server. DHCP is a dynamic router in that it builds and updates its own routing tables. It automates what the administrator has to do manually. Instead of dynamically naming a unique number for a network address, the server assigns a network address to whoever goes on the network next. Thus the network address of a computer or workstation will be different each time. It can also assign other things too, as a default gateway, DNS server, WINS server, and SUBNET MASK. 4. There are really 2 addresses in the TCP/IP packet o IP Addresses (starting address and ultimate ending address) o MAC addresses (Stopping point along the way) 5. IP ADDRESS CLASSES: IP addresses are grouped in different classes. Classes are allocated to organizations that request them in address blocks. The INTERNIC assigns the addresses. Three classes are used for HOSTS. A network is divided into subnets. A SUBNET is a network on where you are currently located. That network can be made longer by adding more subnets. When a network packet is not addresed to its own network or subnets, it is forwarded to a DEFAULT GATEWAY (like a post office). THE NUMBER OF HOSTS THAT MAY BE ALLOWED IN A NETWORK IS DETERMINED BY CLASS: Each class uses special numbering scheme for Domain Names. o Class A Addresses (very few left). Example: X.0.0.0 X = from 1 - 126. That is, 1.X.X.X - 126.X.X.X. First octet identifies the network, i.e. 1-126; and the last three identify the node. CLASS A DEFAULT SUBNET MASK = 255.0.0.0 11111111. 00000000 00000000 00000000 Network o node node node Class B Addresses 128.0.0.X - 191.255.X.X. The first two octets identify the network and the last two the node. CLASS B DEFAULT SUBNET MASK = 255.255.0.0 11111111. 11111111 00000000 00000000 Network o Network node node Class C Addresses: 192.0.0.X - 223.255.255.X The first three octets identify the network, and the last octet is the node. CLASS C DEFAULT SUBNET MASK = 255.255.255.0 11111111. 111111111 11111111 00000000 Network Network Network Network 6. PORT NUMBERS: TCP/IP has its own protocols. Different TCP/IP Internet protocols use different port numbers to connect to web servers. o HTTP uses default port 80 or 8080 o FTP (File Transfer Protocol) uses default port 21 o TELNET (text communication) uses default port 23 o SMNP uses default port 161 o SMTP (Simple Mail Transfer protocol) uses default port 25 7. DOMAIN NAME: Your IP address not only comes in numbers but has a Domain Name. It is easier to remember a name than a number. The DNS breaks addresses into groups and gives each level the responsibility for the levels under them. Each level is called a domain. A period separates each domain name from the next one. The right most portion of the address identifies the top level domain name which references the organization type. The following table lists commonly used domain names: .com = Commercial organizations .edu = Educational organizations .gov = Government (non-military) .mil = Military organizations .org = Non-profit association .net = Network resources Two services that the TCP/IP protocol uses to resolve domain name to IP adresses are HOST FILE : a test file that is kept on the local machine and contains a list of other hosts and IP numbers. The domain name resolver goes to this text field first. DNS Server: Every company has a DNS server that workstations may consult for a name to IP address resolution. THE DNS server contains FQDN (Fully Qualified Domain Names) to IP address matches. This database contains entries for every host within the organization. Only one DNS server will keep the master database. LMHosts - WINS: A LMHost file resolves a NetBIOS name to an IP address. The file must be installed and kept up to date on each machine. The WINS server is a database that keeps track of IP addresses and NetBIOS names. The WINS server is dynamic in its configuration and updates. TROUBLESHOOTING TCP/IP UTILITIES: PING: The ping command is used to test connectivity to a host. It is a loop-back address. You can also Ping an address on the other side of your router to test the default gateway. o To check if you have a path to an Internet host, enter the Ping command and the host's IP address at the command line, as in the following example: PING 204.32.23.67 NOTE: You can also use Ping with the DNS name of the host, such as www.wavetech.com. TRACERT:This utility allows you to find the route used between you and the remote computer host. For example, say that you are having trouble reaching a host named www.yahoo.com. Type the following command at the command prompt: TRACERT WWW.yahoo.com and press enter. WINIPCFG/IPCONFIG: A good utility to use to check the TCP/IP configuration on a Windows 95 workstation is WINIPCFG. You can quickly determine a computer's IP address, subnet mask, and default gateway using this utility. Windows NT has a command line utility, IPCONFIG that presents similar data about the IP configuration on an NT platform. 2. IPX Network Protocol IPX stands for Internet Packet Exchange. It is a Novell NetWare designed transport protocol. Novell Netware is an operating system made of FAT and DET(Directory Entry Table). Performs addressing and routing functions. Resides in the NETWORK layer. Requires some configuration. Requires the administrator to uniquely assign a network or cable segment address. 3. NetBIOS/NetBEUI Network Protocol Stands for Network Bios Input Output Sustem and Network Advanced User Interface. Microsoft designed this protocol for fast packet delivery in a small network without much configuration. It is not routable, but operates on the NETWORK and TRANSPORT layers of the OSI model. NETWORK HARDWARE More than any feature, network hardware may determine the speed, quality and performance of a network. Hubs A hub is a central connecting device that joins computers in a star configuration. Hubs may be passive or active. A passive hub merely connects computers to the network and does not process data in any way. Active hubs, sometimes called repeaters, regenerate the data in order to maintain signal strength. Some hubs have intelligence and can perform additional duties such as bridging, routing and switching. SWITCHES Fast Ethernet switches allow dedicated, high-speed connections at either 10BASE-T or 100BASE-TX. They are ideal for connecting servers or multiple hubs in small businesses that want the highest network performance possible to exchange large data files and images, and access real-time information. A switch does this by providing dedicated bandwidth to every device—server, PC, or hub—connected to one of its ports. They are intelligent in that they give priority to large bandwidth data. Repeater A repeater is the simplest and least expensive of the three. Repeaters are usually small enough to fit in your hand and are used to connect two segments of network cable. Extends the signal and distance of the LAN. The repeater retimes and regenerates signals but does not change the data frame or packet in any way. Transceiver A tranceiver connct different Ethernet nodes together in an organized fashion, and allows multiple Ethernet segment nodes to connect to eachother to create a segment. Bridge A bridge is like a smart repeater. Bridges, like repeaters, can connect two network segments, but bridges are a little smarter about the data they transport. Most bridges have the capacity to listen to the network and figure out the address of each computer on both sides of the bridge. The bridge can then inspect each message that comes from one side and broadcast it to the other side of the bridge, if the message is intended for a computer that is on the other side. If the paket's destination is on the same side of the bridge, it is is discarded. This creates a more efficient scheme for data transport. The bridge can connect segments that use different cable media types, like 10BaseT(Twister Pair) and 10Base5(Coaxial). cannot connect different transport protocols - like Ethernet and Token Ring networks. Routers A router is like super-intelligent bridge. They can link multiple LANs and look deeper into the data packet to determine its destination. Routers not only know the addresses of the computers on the network but are aware of all the other bridges and routers on the network and can decide the most efficient path in which to send data. The router uses a routing table of network addresses to determine where to forward the packet.When a router receives data, it discards the outer packet or frame or MAC address, repackages the data with network address, and retransmits the signal. By stripping off the outer layers of data before sending a packet, the total number of bits moving across the network is reduced. The router at the receiving end then repackages the data into a packet of frame that is appropriate for its network. There are ROUTABLE and NON-ROUTABLE protocols. TCP/IP and IPX/SPX are routable NetBEUI is non-routable because it cannot work out of its own subnet. Brouters A brouter is like a bridge that have advanced intelligence that allows them to take on duties that would normally require a router. These bridges are called brouters. Gateways A gateway is like a super-intelligent router. Gateways are designed to connect radically different networks. Although slower than a bridge or router, a gateway has its own processor and memory to perform complex functions such as interpreting between computers that speak different languages through both protocol and bandwidth conversion. A gateway can convert a TCP/IP packet to a NetWare IPX packet and vice versa. An example of a gateway is a messaging gateway, which converts messages between different protocols. Keys To Remember: Repeaters, bridges, routers and gateways all extend and segment networks. Because of this, they’re often confused, as they may take on similar duties. The difference between these devices lies in the different degrees of data discrimination and handling capability. Repeater: Regenerates signals to span longer segments of network. Does not alter data. Bridge: Links two subnets (networks) that use the same media and protocol. May control data traffic and speed. Router: Allows the interconnection of two or more physically distinct networks and have advanced intelligence enabling it to determine the most efficient method of delivering data. Gateways: Designed to connect radically different networks. FAULT TOLERANCE Fault tolerance involves storing data on multiple hard drives to insure against the failure of any individual drive. There are several levels of fault tolerance, referred to as RAID (Random Array of Inexpensive Disks) levels. RAID Levels FAULT TOLERANCE RAID Levels