1 COEN 152 / 252 Spring 2011 Final Examination 1. Ethics
advertisement

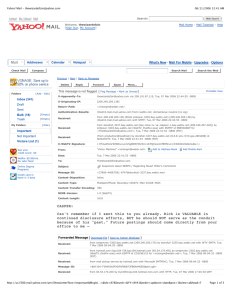
COEN 152 / 252 Spring 2011 Final Examination 1. Ethics Throughout the course we have discussed the multiple ethical challenges faced as a forensics practitioner. Being mindful of our discussions and the Markkula Center for Applied Ethics Framework, describe which of the approaches is most workable for you. Apply that perspective to the following ethical problem: A law enforcement community develops the Ruminant, a program that monitors all electronic communication through a given internet site. Ruminant generates a listing of email for human consumption according to rather narrow search criteria as spelled out in a search warrant. Is deploying Ruminant ethical? 2. Legal We have discussed the guidelines established by the Daubert case. Describe these guidelines in your own words. Why are they important? How do they impact the admissibility of digital evidence? 3. Network Sniffing In the following simulated scenario, we suspect a backdoor into a machine, bobadilla.engr.scu.edu. We captured traffic, available as a Wireshark capture file: (http://www.engr.scu.edu/~tscocca/COEN252_09/PracticalFinal/capture.pcap) and also used fport with this result: (http://www.engr.scu.edu/~tscocca/COEN252_09/PracticalFinal/cap112407html.html) Analyze the TCP connections open during the capture time and ascertain whether they are suspicious or not? 4. Evidence Processing Chain of custody; describe the concept. What is its importance in the analysis of digital evidence? Give an example of the proper chain of custody in the handling of an item of digital evidence. 5. Windows Artifacts In Lab 5, use ProDiscover or FTK Imager to locate the SID stings for each account that is present in the image. Identify the SID for each account and describe which “user” the account is associated with. In and analysis scenario, what is the importance of this SID? 1 6. File Headers In Lab 5, use ProDiscover or FTK Imager to locate the two files that Howie sent to Joe. What are the names of these files? For this file type, describe the unique file header that can be used to located files of this type by using a string search. 7. Email Investigation The following email was received at my Yahoo mail account. Apparently someone wishes to return an ATM card to me that I never lost. There are of course fees associated with this return. Examine the email and for all domains and IP addresses, provide available details about the domain owners. You may use and email header tracing site to gather this information. Ensure the information is accurate before you rely on it for your answer. Provide attribution for the tracing site used to get your answer. (Note: X-YMailISG: value has been truncated in the interest of saving space.) From Dr. Mathias Bello Sat Jun 4 16:39:41 2011 X-Apparently-To: tscocca@yahoo.com via 68.142.200.134; Sat, 04 Jun 2011 16:39:36 -0700 Return-Path: <emaill5585999@mail.com> X-YahooFilteredBulk: 195.4.92.98 Received-SPF: none (mta1475.mail.mud.yahoo.com: domain of emaill5585999@mail.com does not designate permitted sender hosts) X-YMailISG: G4I8AEccZArEBtNDy3wF.RssP61kl1kGTgQ2xqihAKft6h2V...................... X-Originating-IP: [195.4.92.98] Authentication-Results: mta1475.mail.mud.yahoo.com from=mail.com; domainkeys=neutral (no sig); from=mail.com; dkim=neutral (no sig) Received: from 127.0.0.1 (EHLO mout8.freenet.de) (195.4.92.98) by mta1475.mail.mud.yahoo.com with SMTP; Sat, 04 Jun 2011 16:39:31 -0700 Received: from [195.4.92.27] (helo=17.mx.freenet.de) by mout8.freenet.de with esmtpa (ID gordon.kleinau@team-atlas.de) (port 25) (Exim 4.76 #2) id 1QT0RD-0000DP-B9; Sun, 05 Jun 2011 01:39:27 +0200 Received: from [46.166.129.140] (port=3999 helo=User) by 17.mx.freenet.de with esmtpa (ID gordon.kleinau@team-atlas.de) (port 587) (Exim 4.72 #5) id 1QT0RC-0004Zo-W7; Sun, 05 Jun 2011 01:39:27 +0200 Reply-To: <off1cemail03@yahoo.co.jp> From: "Dr. Mathias Bello"<emaill5585999@mail.com> Subject: GET BACK TO US Date: Sun, 5 Jun 2011 00:39:41 +0100 MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="----=_NextPart_000_0120_01C2A9A6.52F4484E" X-Priority: 3 X-MSMail-Priority: Normal X-Mailer: Microsoft Outlook Express 6.00.2600.0000 X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000 Message-ID: <1QT0RC-0004Zo-W7@17.mx.freenet.de> Content-Length: 3638 2 8. Data Analysis When considering the analysis of a digital evidence item, why is the operational environment of that system or device a factor? 9. Data Attribution Given that an HTML file appears in a browser cache area, list 3 examples of how this could happen without the browser having written the content to the cache? How would you use other artifacts to identify the resource that deposited the HTML file? 10. Legal When considering the use of a digital evidence analysis tool, why is validation of the output of that tool important? When considered in the context of a legal proceeding, discuss the impact of tool validation on expert testimony that may be necessary during a proceeding. 11. Forensic Duplication You were introduced to the concept of a forensic duplicate of digital media. Describe in your own words why this concept developed and how it is employed in the examination of digital media? Be sure to include in your description the impact of the “Best Evidence” rule. 3