Introduction
The Implement a small switched network module provides you with the instructions and Cisco
hardware to develop your hands on skills in the basic setup of Cisco switches. This module includes
the following exercises:
1) The initial configuration dialog
2) Basic switch configuration using the CLI
3) Verifying the switch operation
4) Configuring port security
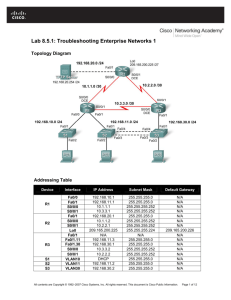
Lab Diagram
During your session you will have access to the following lab configuration. Depending on the
exercises you may or may not use all of the devices, but they are shown here in the layout to get an
overall understanding of the topology of the lab.
Internet
ISP1
172.14.0.3/24
Frame-Relay
WAN
NYEDGE1
Cisco
2911 Router
LDNWAN1
ISP2
172.14.0.4/24
Ser0/0/0
Ser0/0/0
Ser0/0/1
Ser0/0/0
Gi0/1
172.16.16.0/24
NWRKWAN1
NYWAN1
Cisco
2911 Router
Ser0/1/1
Ser0/1/0
Gi0/0
Ser0/0/1 Gi0/0
Gi0/0
Ser0/0/1
Fas1/0/1
Fas1/0/1
Fas1/0/2
Fas1/0/12
Fas1/0/23
Fas1/0/24
NYCORE1
Fas1/0/22
Fas1/0/22
Cisco 3750v2-24PS
Switch
Fas0/24
PLABCSCO01
Cisco Tools Server
NYEDGE2
Cisco
2911 Router
Gi0/1
Gi0/1
Lab Nic
192.168.16.10/24
Fas0/1
NYCORE2
Cisco 3750v2-24PS
Switch
Fas0/23
NYACCESS1
Cisco 2960-24
Switch
Cisco
IP Phone
Connecting to your lab
In this module you will be working on the following equipment to carry out the steps defined in each
exercise.
NYACCESS1
NYCORE1
NYCORE2
PLABCSCO01
Each exercise will detail which terminal you are required to work on to carry out the steps.
During the boot up process an activity indicator will be displayed in the device name tab:
Black - Powered Off
Orange - Working on your request
Green - Ready to access
If the remote terminal is not displayed automatically in the main window (or popup) click the
Connect icon located in the tools bar to start your session.
Copyright Notice
This document and its content is copyright of Practice-IT - © Practice-IT 2014. All rights reserved.
Any redistribution or reproduction of part or all of the contents in any form is prohibited other than
the following:
1) You may print or download to a local hard disk extracts for your personal and non-commercial use
only.
2) You may copy the content to individual third parties for their personal use, but only if you
acknowledge the website as the source of the material. You may not, except with our express
written permission, distribute or commercially exploit the content. Nor may you transmit it or store
it in any other website or other form of electronic retrieval system.
Exercise 1 - The initial configuration dialog
In this exercise you will navigate through the initial configuration dialog. The initial configuration
dialog is present when you boot up a Cisco device (be it router or switch) for the first time. There are
some variations on the settings you may see depending on the model or hardware type, but the
majority of the settings are the same.
You can also access this configuration dialog by either erasing the configuration of a device (which
you will learn later in this course), or by typing setup from the Command Line Interface (CLI) in what
is known as privileged mode.
Use your study material as further reference on how to carry out the tasks in this exercise.
You MUST set the ALL passwords to lower case cisco unless specified. This enables us to
successfully recover the devices once you have finished.
Switch / Router modes
Before starting, if you are not aware of the modes that a Cisco device can be in, these are the
common ones:
User Exec mode, signified by the > at the end of the device name, for example:
Switch1>
Privileged mode, signified by the # symbol at the end of the device name, for example:
Switch1#
Global configuration mode, signified by the (config)# at the end of the device name, for example:
Switch1(config)#
The Initial configuration dialog
Note: If you want to save time in this lab, you can power on NYACCESS1, NYCORE1, NYCORE2 and
PLABCSCO01 now. Please note that by doing so, some of the output (for example the interface
states) may be slightly different to what is shown, but should not impede your process through the
lab in any way.
Step 1
Click on the NYACCESS1 icon in the device list on the left of the window, click the power on button
in the toolbar at the bottom of the devices terminal, you will need to click the device before the
device controls are shown in the toolbar. Once NYACCESS1 is powered on the terminal will be shown
and the small icon in the top left of the device tab will go green.
You will notice that once the terminal is shown, the device will be booting up. The boot-up process is
useful to watch as you can view the switch going through its various boot and test stages,
remember, these are real Cisco devices so depending on the hardware and software of the device
this may take a few minutes.
The boot times and process for NYACCESS1 and NYCORE1 are very different because they are
different platforms and run different IOS versions.
Once the device has booted you will see a message stating:
Press RETURN to get started!
Press return and the initial configuration dialog will appear, note that the output below may differ
slightly depending on which IOS is installed, however the last line, the prompt to enter the initial
configuration dialog should be there.
--- System Configuration Dialog --Enable secret warning
---------------------------------In order to access the device manager, an enable secret is required
If you enter the initial configuration dialog, you will be prompted for the enable
secret
If you choose not to enter the intial configuration dialog, or if you exit setup
without setting the enable secret,
please set an enable secret using the following CLI in configuration modeenable secret 0
---------------------------------Would you like to enter the initial configuration dialog? [yes/no]:
Note: While you are configuring Cisco devices, you may see a number of messages appear on the
screen. If you are in the middle of typing a command and the command is now mixed in to the log
message, simply press the tab key to refresh the command on a new line.
Note: The terminal you are connected to is connected to the console port of the switch (as with all
the Cisco devices in the labs). This means regardless of the settings you make to the switch you will
always have access (there are some exceptions so please steer clear of configuring the console port
settings unless specifically asked to do so).
If at any time, or for some reason you get a switch> prompt instead of the initial configuration
wizard, simply type enable then type setup.
Step 2
Once the initial configuration dialog appears, use the following output to guide you through
configuring the switch. Type the values shown in the output in to the terminal as they appear in the
following snippet:
Would you like to enter the initial configuration dialog? [yes/no]: yes
At any point you may enter a question mark '?' for help.
Use ctrl-c to abort configuration dialog at any prompt.
Default settings are in square brackets '[]'.
Basic management setup configures only enough connectivity
for management of the system, extended setup will ask you
to configure each interface on the system
Would you like to enter basic management setup? [yes/no]: yes
Configuring global parameters:
Enter host name [Switch]: Switch1
The enable secret is a password used to protect access to
privileged EXEC and configuration modes. This password, after
entered, becomes encrypted in the configuration.
Enter enable secret: cisco
The enable password is used when you do not specify an
enable secret password, with some older software versions, and
some boot images.
Enter enable password: cisco1
The virtual terminal password is used to protect
access to the router over a network interface.
Enter virtual terminal password: cisco
Configure SNMP Network Management? [no]: no
The above settings simply changed the hostname of the switch from it’s default of Switch to
Switch1, we then set an enable secret and password, both of these protect privilged mode access
with a password (albeit the secret overrides the password when set, so in fact the password to gain
access to privileged mode in this example is cisco not cisco1).
You are then presented with the interface summary, if you want to view each interface line by line
you can press the return key, otherwise using the space bar will page through the interfaces.
Press either return or the space bar to get to scroll through the interface list and get to the next
prompt.
Current interface summary
Interface
Protocol
IP-Address
OK? Method Status
Vlan1
unassigned
YES unset
administratively down down
FastEthernet0/1
unassigned
YES unset
down
down
FastEthernet0/2
unassigned
YES unset
down
down
FastEthernet0/3
unassigned
YES unset
down
down
FastEthernet0/4
unassigned
YES unset
down
down
FastEthernet0/5
unassigned
YES unset
down
down
FastEthernet0/6
unassigned
YES unset
down
down
FastEthernet0/7
unassigned
YES unset
down
down
FastEthernet0/8
unassigned
YES unset
down
down
FastEthernet0/9
unassigned
YES unset
down
down
FastEthernet0/10
unassigned
YES unset
down
down
FastEthernet0/11
unassigned
YES unset
down
down
FastEthernet0/12
unassigned
YES unset
down
down
FastEthernet0/13
unassigned
YES unset
down
down
FastEthernet0/14
unassigned
YES unset
down
down
FastEthernet0/15
unassigned
YES unset
down
down
FastEthernet0/16
unassigned
YES unset
down
down
FastEthernet0/17
unassigned
YES unset
down
down
FastEthernet0/18
unassigned
YES unset
down
down
FastEthernet0/19
unassigned
YES unset
down
down
FastEthernet0/20
unassigned
YES unset
down
down
FastEthernet0/21
unassigned
YES unset
down
down
FastEthernet0/22
unassigned
YES unset
down
down
FastEthernet0/23
unassigned
YES unset
down
down
FastEthernet0/24
unassigned
YES unset
down
down
GigabitEthernet0/1
unassigned
YES unset
down
down
GigabitEthernet0/2
unassigned
YES unset
down
down
Once you have reached the end of the interface summary, continue on with the initial configuration
dialog using the following settings:
Enter interface name used to connect to the
management network from the above interface summary: Vlan1
Configuring interface Vlan1:
Configure IP on this interface? [no]: yes
IP address for this interface: 192.168.16.7
Subnet mask for this interface [255.255.255.0] : 255.255.255.0
Class C network is 192.168.16.0, 24 subnet bits; mask is /24
Would you like to enable as a cluster command switch? [yes/no]: no
Once you have reached the cluster command option and type no the summary configuration will
now appear, this is the configuration that has been generated using the configuration settings you
have applied during the initial configuration dialog and some default settings that get applied to
interfaces etc. Press return to go through the configuration line by line, or press the spacebar to
page through.
The following configuration command script was created:
hostname Switch1
enable secret 5 $1$2D0U$ZWu/q0pR/z9hsR4oc7W04/
enable password cisco1
line vty 0 15
password cisco
no snmp-server
!
!
interface Vlan1
no shutdown
ip address 192.168.16.7 255.255.255.0
!
interface FastEthernet0/1
!
interface FastEthernet0/2
!
interface FastEthernet0/3
!
interface FastEthernet0/4
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface FastEthernet0/9
!
interface FastEthernet0/10
!
interface FastEthernet0/11
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
interface FastEthernet0/14
!
interface FastEthernet0/15
!
interface FastEthernet0/16
!
interface FastEthernet0/17
!
interface FastEthernet0/18
!
interface FastEthernet0/19
!
interface FastEthernet0/20
!
interface FastEthernet0/21
!
interface FastEthernet0/22
!
interface FastEthernet0/23
!
interface FastEthernet0/24
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
end
Once you are at the end you will reach the save settings menu.
[0] Go to the IOS command prompt without saving this config.
[1] Return back to the setup without saving this config.
[2] Save this configuration to nvram and exit.
Enter your selection [2]: 0
In the next exercise you will configure a switch using the command line interface, CLI. To prepare for
this choose option 0 to go to the IOS prompt without saving.
[0] Go to the IOS command prompt without saving this config.
[1] Return back to the setup without saving this config.
[2] Save this configuration to nvram and exit.
Enter your selection [2]: 0
% You can enter the setup, by typing setup at IOS command prompt
Switch>
The initial configuration dialog wizard enables you to configure a number of essential settings that
should be set on any switch, including the hostname and passwords.
A point to note is that the switch has encrypted the enable secret which lets you enter privileged
mode, this is shown by the line in the output:
enable secret 5 $1$2D0U$ZWu/q0pR/z9hsR4oc7W04/
However the switch did not encrypt the password used when logging in to gain access to user exec
mode (non-privileged mode).
line vty 0 15
password cisco
Leave this device powered on in its current state and proceed to the next exercise where you will
configure these same options but this time you will use the command line interface (CLI).
Exercise 2 - Basic switch configuration using the CLI
In the previous exercise you configured a switch’s basic settings using the initial configuration dialog.
In this exercise you will configure the same settings that were made using the initial configuration
dialog but this time you will use the CLI to build the same configuration.
Please refer to your course material for reference on the commands used in this exercise, or use
your preferred search engine to gain an understanding of these tasks.
Configuring a Switch using the CLI, preparation
Step 1
Click on the NYCORE1 tab in the devices list. As in the previous exercise, you will need to ensure the
switch is powered on to start using it, do this by ensuring the correct tab is selected and then click
the power on button in the controls toolbar at the bottom of the terminal window.
Please note if the text in the terminal appears to stop, the switch has possibly booted. Simply click in
the terminal window and press return and you will see the initial configuration dialog prompt. For
example you may see something like this:
*Mar 1 00:01:45.822: %LINEPROTO-5-UPDOWN: Line protocol on Interface
FastEthernet1/0/24, changed state to up
*Mar 1 00:02:10.551: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1,
changed state to up
Then by pressing return, you will see:
--- System Configuration Dialog --Enable secret warning
---------------------------------In order to access the device manager, an enable secret is required
If you enter the initial configuration dialog, you will be prompted for the enable
secret
If you choose not to enter the intial configuration dialog, or if you exit setup
without setting the enable secret,
please set an enable secret using the following CLI in configuration modeenable secret 0
---------------------------------Would you like to enter the initial configuration dialog? [yes/no]:
Once the switch has booted, cancel out of the initial configuration dialog by typing no at the
prompt.
Would you like to enter the initial configuration dialog? [yes/no]: no
Switch>
Step 2
Using the commands outlined in the section below and the reference from your course material try
and configure the switch as you did before using the configuration dialog, but this time using the CLI.
The commands are hopefully self-explanatory and will map very closely to the wording that was
used during the initial configuration dialog.
Commands you will need to use
The following commands are required to achieve the tasks set out in this exercises:
Changing modes on the switch
Privileged mode, accessed from user exec mode using the command: enable
Global configuration mode, entered from privileged mode using the command: configure terminal
Interface configuration mode interface x a/b/c (where x is the interface type and a/b/c is the
interface number), this is accessed once you are in global configuration mode.
Configuration commands
The following commands are the commands required to configure the switch as you did previously.
Global configuration commands
hostname Switch1
enable secret cisco
enable password cisco1
VTY line commands
line vty 0 15
password cisco
login
Interface configuration commands
interface vlan 1
ip address 192.168.16.5 255.255.255.0
no shutdown
Transcript of commands
As this is your first configuration, here is a transcript of what you should have entered:
Switch>
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line.
End with CNTL/Z.
Switch(config)#hostname Switch1
Switch1(config)#enable secret cisco
Switch1(config)#enable password cisco1
Switch1(config)#interface Vlan1
Switch1(config-if)#ip address 192.168.16.5 255.255.255.0
Switch1(config-if)#no shutdown
Switch1(config-if)#exit
Switch1(config)#line vty 0 15
Switch1(config-line)#password cisco
Switch1(config-line)#login
Switch1(config-line)#exit
Switch1(config)#exit
Switch1#
Leave this device powered on in its current state and proceed to the next exercise where you will
use the command line interface to verify the switch operation.
Exercise 3 – Verifying the switch operation
In this exercise you will use some fundamental testing utilities to ensure that a Cisco switch is
functioning correctly and able to communicate to other devices on the network.
These utilities are tools that are used almost every single day to troubleshoot and test connectivity
so it is vital to understand how to use them and what the options and differences are between the
tools. The tools you will use in this exercise are:
Ping
Traceroute
Telnet
For more information on some of these utilities, use your preferred search engine to gain a greater
understanding, there will be lots of information on Wikipedia etc.
Network utilities, ping and traceroute
There are a number of tools available to you as a network engineer to help with troubleshooting and
verifying the operation of your network devices. Many of these are available on many other
operating systems, including Microsoft Windows, Linux/Unix variants etc.
Two of these commands are very commonly used which are ping and traceroute.
Ping (Packet Internet Groper) uses the ICMP protocol to see if a remote device is responding to
network traffic. Ping sends an ICMP echo request and expects to receive an ICMP echo reply from
the remote destination. Note that even though you may receive an ICMP reply, it does not mean
that the services on the remote device are available, it simply means it is responding to ICMP
requests. This is a useful tool for verifying that the remote device is at least alive.
Traceroute enables the engineer to view the path taken through a network to get from point A to
point B. This is very useful in determining where potential problems are on the network, for example
highly utilised links or paths that have failed etc will show up in the output of this command.
Commands you will need to use
The following commands are required to achieve the tasks set out in this exercises:
Both of the following commands are available in both privileged and user exec modes:
ping 192.168.16.10
traceroute 192.168.16.10
Using PING
Connect to NYCORE1 again in the lab (if you disconnected from previous exercise then you will need
to go back and ensure you have configured the settings in exercise 2 of this module).
As previously explained, Ping is a utility that sends out an echo request to another device which in
turn should send back an echo response. If the response successfully comes back to the source
device, the time taken between echo request and echo reply are measured and reported back.
Depending on the device type and options chosen when using the PING utility normally 4 or 5
consecutive echo requests are sent one after another, if a response is not heard within a timeout
limit the next request is sent. Normally the statistics are then shown to the end user at the end of
the set.
Checking network connectivity from the switch using PING
Before continuing this task, ensure that PLABCSCO01 is powered on by selecting the device in the
lab devices list, then click the Power On button. You will need to wait for the device to power on
before continuing.
This exercise assumes that you correctly configured an IP Address on VLAN1 on NYCORE1 in the
previous exercise. If this failed, then you will need to rectify this issue before continuing.
Step 1
Check that the switch is has connectivity to other devices using the ping utility on the switch. The
PLABCSCO01 server is on the same subnet as interface Vlan 1 on your switch, it has an IP address of
192.168.16.10.
Ping is available in either privileged or user mode, so from either the Switch1# or Switch1> prompt
type ping 192.168.16.10 and see if the device responds:
Switch1#ping 192.168.16.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.16.10, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/2/8 ms
Switch1#
A successful reply is signified by an exclamation mark. A failure is signified by a full stop.
Notice that in the output above the first ping request failed, this is almost always due to the ARP
process. You will find that the first request you make (or anything makes) to a device may fail
initially, but once the network is aware of the device things are normal. To prove this, retry the
command and see if it fails again (your may not have failed initially in which case there is no
requirement to re-test).
Switch1#ping 192.168.16.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.16.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/8 ms
Step 2
Next, use the ping command to test connectivity to 192.168.16.99
Does the device respond, what does the switch show when it does not receive an ICMP echo reply?
Switch1#ping 192.168.16.99
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.16.99, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Switch1#
Checking network connectivity from the switch using TRACEROUTE
Traceroute is another utility that is used to verify connectivity; normally you would use traceroute
when you are trying to find the path or route through the network to remote device, i.e. which (OSI)
layer 3 devices do packets take to get from the source device to the destination device.
Step 1
Traceroute is available in either privileged or user mode, so from either the Switch1# or Switch1>
prompt type traceroute 192.168.16.10 and see which route the packets take to get from Switch1 to
PLABCSCO01.
You will notice when you type the command it seems initially slow. This is because the device is
trying to resolve a name to the IP address of the server. As DNS is not configured the name lookup
will eventually timeout.
Switch1#traceroute 192.168.16.10
Type escape sequence to abort.
Tracing the route to 192.168.16.10
1 192.168.16.10 0 msec 0 msec *
Switch1#
As you can see the traceroute successfully completed and there was just one hop to the server, i.e. it
is directly connected and does not go through any layer 3 devices (routers) to get between the
switch and the server, however an important point here is that to get to the server, the packets DO
go through another switch, but at what layer does a switch operate at?
Verifying connectivity to the switch using Telnet
Telnet and SSH are protocols that are used to communicate to terminal based devices. If you can
telnet or SSH to a device then it’s a sure fire way of confirming that the device is on the network and
it is responsive to requests.
However, telnet and SSH do not give any information regarding how quickly the device responds to
network traffic (like Ping does) or the path taken to get to the device (like traceroute does). It also
does not confirm necessarily that the device is doing what it is supposed to be doing in all instances
(i.e. that it is forwarding traffic). You would normally use ping to do this, but not to the switch itself,
but to other devices attached to the switch.
To telnet to the device, you will need to connect to PLABCSCO01 in the lab. Click the icon in the lab
panel then click Connect.
Once connected, there is a program on the desktop called Putty which is an excellent free telnet and
SSH client. Use your favourite search engine to find the download link to be able to download Putty
outside of the labs. Open putty by double clicking the icon.
Using Telnet
Step 1
In the Host Name (or IP Address) field in the Putty main window type the IP address of the Switch
that you previously configured (192.168.16.5), and ensure that the Telnet protocol is selected, not
SSH (SSH is the default). Then click the open button to connect.
You should now be presented with a login prompt to the switch.
Step 2
Login to the switch using the VTY password you configured during this module, the password should
be cisco
Note: The characters do not appear when typing.
You should now be in user mode on the switch (signified by the Switch1> prompt)
Prove that your enable secret also works by typing enable on the device and again type in the
password that you previously configured as cisco
Assuming all has gone well you should see the output shown in the screenshot above.
You have successfully configured remote access to your switch, congratulations!
Leave the devices you have powered on in their current state and proceed to the next exercise.
Exercise 4 - Configuring port security
So far in this module you have configured two different switches and their basic settings for normal
operation. You should have successfully configured telnet access to NYCORE1 and confirmed that
you are able to communicate using the ping and traceroute utilities.
In this part of the exercise you will carry out some more advanced configuration on a switches
interfaces which are used to permit and deny access to the network itself using a technology called
port security.
This isn’t anything to do with firewalls or TCP/UDP ports that are used to permit and deny traffic,
this is to do with physical access to the network and whether the physical switch port that a device is
connected to will permit or deny access.
Setting up Port Security
Step 1
Click on the NYCORE2 tab in the device list and power the device on if you haven’t already. Please
note that this switch will power on at the same time as NYCORE1. Therefore it will show a black
screen waiting for key input. When the portal shows the switch is on (indicated by the green icon)
simply click in the black terminal window and press return.
Quit out of the initial configuration dialog on NYCORE2:
Enable secret warning
---------------------------------In order to access the device manager, an enable secret is required
If you enter the initial configuration dialog, you will be prompted for the enable
secret
If you choose not to enter the intial configuration dialog, or if you exit setup
without setting the enable secret,
please set an enable secret using the following CLI in configuration modeenable secret 0
---------------------------------Would you like to enter the initial configuration dialog? [yes/no]: no
Commands you will need to use
The following commands are used under interface configuration mode:
switchport mode access
switchport port-security mac-address sticky
switchport port-security maximum 1
switchport port-security violation shutdown
switchport port-security
Step 2
Once you have the switch prompt, configure NYCORE2’s interface fastethernet 1/0/12 to have port
security enabled, use the commands above to help you.
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line.
End with CNTL/Z.
Switch(config)#interface fastethernet 1/0/12
Switch(config-if)#switchport mode access
Switch(config-if)#switchport port-security mac-address sticky
Switch(config-if)#switchport port-security maximum 1
Switch(config-if)#switchport port-security violation shutdown
Switch(config-if)#switchport port-security
Switch(config-if)#
Step 3
To confirm the status of the interface with port security enabled you will need to use the show
commands which are accessed from privileged mode, some are available in exec mode too.
The command to view the current status of an interfaces port-security is:
show port-security interface fastethernet1/0/12
Use this command to see that the port is operating normally (i.e. the port status is Secure-Up).
Switch#show port-security interface fastethernet1/0/12
Port Security
: Enabled
Port Status
: Secure-up
Violation Mode
: Shutdown
Aging Time
: 0 mins
Aging Type
: Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses
: 1
Total MAC Addresses
: 1
Configured MAC Addresses
: 0
Sticky MAC Addresses
: 1
Last Source Address:Vlan
: 000b.5f92.61e3:1
Security Violation Count
: 0
Step 4
Next, change the allowed MAC address on fastethernet 1/0/12 on the switch so that it is not the
same as the device currently connected to this interface. To do this however we need to clear the
sticky MAC address. Follow this process to do this:
Shutdown the interface fastethernet 1/0/12
Remove the sticky MAC address the switch learnt
Permit a new MAC address
Bring up the interface
Switch(config-if)#shutdown
Switch(config-if)#exit
Switch(config)#exit
Switch#clear port-security sticky interface fastEthernet 1/0/12
Switch#configure terminal
Enter configuration commands, one per line.
End with CNTL/Z.
Switch(config)#interface fastethernet 1/0/12
Switch(config-if)#switchport port-security mac-address 0001.0001.0001
Switch(config-if)#no shutdown
In the above configuration, I have made up a fictitious MAC address of 0001.0001.0001, you can
chose anything you like providing it isn’t the actual device connected to the interface.
Once you enable the interface using the no shutdown command, the device connected to Fas1/0/12
will start to boot up. It is an IP phone so will get its power from the switch (the first few messages
will be the switch granting power to the phone), then once it is booted, after a minute or so you
should see the following log message appear in the console:
*Mar 1 00:06:25.162: %PM-4-ERR_DISABLE: psecure-violation error detected on
Fa1/0/12, putting Fa1/0/12 in err-disable state
*Mar 1 00:06:25.171: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation
occurred, caused by MAC address 0013.c460.50f6 on port
FastEthernet1/0/12.
*Mar 1 00:06:26.169: %LINEPROTO-5-UPDOWN: Line protocol on Interface
FastEthernet1/0/12, changed state to down
*Mar 1 00:06:27.167: %LINK-3-UPDOWN: Interface FastEthernet1/0/12, changed state
to down
Step 5
Finally, view the output of the show port-security command you previously used:
Switch#show port-security interface fastEthernet 1/0/12
Port Security
: Enabled
Port Status
: Secure-shutdown
Violation Mode
: Shutdown
Aging Time
: 0 mins
Aging Type
: Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses
: 1
Total MAC Addresses
: 1
Configured MAC Addresses
: 1
Sticky MAC Addresses
: 0
Last Source Address:Vlan
: 000b.5f92.61e3:1
Security Violation Count
: 1
You should see that the Port Status is now Secure-shutdown. Also notice what the interface status is
when you use the show interface fastethernet 1/0/12 command, you will see that the interface is
now in the err-disable state, this output is important to note!
Summary
In this module you achieved the following activities:
You went through the initial configuration dialog to configure the basic settings of a switch,
including setting the VTY passwords and an enable secret.
You used the CLI or command line interface, to configure the same settings as you did in the
initial configuration dialog.
You accessed various different modes on a switch, including user exec mode, privileged
mode, global configuration mode and interface configuration mode.
You user ping, traceroute and telnet to verify that the switch is carrying out its basic
operating functions.
You assigned an IP Address to VLAN1 to be able to remotely connect to the switch.
You configured remote access (telnet) access to the switch by simply putting a password on
the VTY lines (and enabling login).
You configured port-security on a switch interface, only allowing a single MAC address.
Also Try
Using your lab infrastructure you can attempt the following topics at your own pace, these are
additional tasks that can be done building on what you have learnt in this module:
Assign an IP Address to NYACCESS1 VLAN1 interface, make it the same subnet as NYCORE1 and
ensure you can ping between the two devices.
How do you re-enable the interface once the switchport security has shutdown the interface?
What other violation types can you have, why not configure a different violation type?
Final Configuration
Your final configuration on NYCORE1, should look similar to the following output. Note that this does
not include any of the additional tasks you may have configured:
NYCORE1:
Switch1#show running-configuration
Building configuration...
Current configuration : 1441 bytes
!
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch1
!
boot-start-marker
boot-end-marker
!
no aaa new-model
switch 1 provision ws-c3750-24p
system mtu routing 1500
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
interface FastEthernet1/0/1
!
interface FastEthernet1/0/2
!
interface FastEthernet1/0/3
!
interface FastEthernet1/0/4
!
interface FastEthernet1/0/5
!
interface FastEthernet1/0/6
!
interface FastEthernet1/0/7
!
interface FastEthernet1/0/8
!
interface FastEthernet1/0/9
!
interface FastEthernet1/0/10
!
interface FastEthernet1/0/11
!
interface FastEthernet1/0/12
!
interface FastEthernet1/0/13
!
interface FastEthernet1/0/14
!
interface FastEthernet1/0/15
!
interface FastEthernet1/0/16
!
interface FastEthernet1/0/17
!
interface FastEthernet1/0/18
!
interface FastEthernet1/0/19
!
interface FastEthernet1/0/20
!
interface FastEthernet1/0/21
!
interface FastEthernet1/0/22
!
interface FastEthernet1/0/23
!
interface FastEthernet1/0/24
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
interface Vlan1
ip address 192.168.16.5 255.255.255.0
!
ip classless
ip http server
ip http secure-server
!
line con 0
line vty 5 15
!
end
NYCORE2:
Switch#show running-config
Building configuration...
Current configuration : 1478 bytes
!
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
!
!
no aaa new-model
switch 1 provision ws-c3750v2-24ps
system mtu routing 1500
!
!
!
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
interface FastEthernet1/0/1
!
interface FastEthernet1/0/2
!
interface FastEthernet1/0/3
!
interface FastEthernet1/0/4
!
interface FastEthernet1/0/5
!
interface FastEthernet1/0/6
!
interface FastEthernet1/0/7
!
interface FastEthernet1/0/8
!
interface FastEthernet1/0/9
!
interface FastEthernet1/0/10
!
interface FastEthernet1/0/11
!
interface FastEthernet1/0/12
switchport mode access
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address 0001.0001.0001 vlan access
!
interface FastEthernet1/0/13
!
interface FastEthernet1/0/14
!
interface FastEthernet1/0/15
!
interface FastEthernet1/0/16
!
interface FastEthernet1/0/17
!
interface FastEthernet1/0/18
!
interface FastEthernet1/0/19
!
interface FastEthernet1/0/20
!
interface FastEthernet1/0/21
!
interface FastEthernet1/0/22
!
interface FastEthernet1/0/23
!
interface FastEthernet1/0/24
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
interface Vlan1
no ip address
!
ip classless
ip http server
ip http secure-server
!
!
!
line con 0
line vty 5 15
!
end
This completes the final configuration.