Syllabus
advertisement

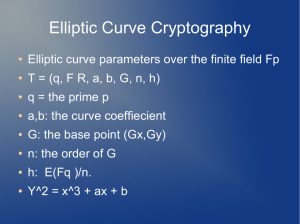
CS 517 – Advanced Cryptography & Data Security Spring 2015 This is a three-credit course on the advanced methods, algorithms, techniques, and tools of data security and cryptography. Catalogue Data: Information theoretic aspects of cryptography, number theory, elliptic curve cryptosystems, games, oblivious transfer, cryptographic protocol theory, secure multi-party computation, electronic voting applications, digital cash applications, efficient implementations of cryptographic algorithms, side-channel and fault attacks. Prerequisite: Course is open to graduate students. Undergraduate students can be registered with the permission of the instructor. Instructor: Erkay Savaş Schedule: References: FENS 1098, x9606, erkays@sabanciuniv.edu Tuesday 10:40 – 12:30, FENS L067 (Lecture) Wednesday 14:40 – 15:30, FENS L067 (Lecture) Wednesday 09:40 – 11:30, FENS 1098 (Office Hours) - W. Trappe and Lawrence C. Washington, Introduction to Cryptography with Coding Theory. Second Edition, Prentice Hall, 2005, ISBN 13- 978-0131862395 - Douglas R. Stinson, Cryptography Theory and Practice, Chapman & Hall/CRC, 2006. - A. J. Menezes P. C. van Oorschot, and S. A Vanstone. Handbook of Applied Cryptography, CRC Press, 1997. - W. Mao, Modern Cryptography: Theory and Practice. Prentice Hall, 2004. Tentative Outline Information theoretic aspects of cryptography: Probabilistic nature of cryptographic systems, entropy, unconditional security, computational security Mathematical foundations: Number theory, finite fields, primitive roots, square roots, Jacobi symbol, Lucas Symbol Elliptic curve cryptosystems: Elliptic curve group, Elliptic curve point operations, Elliptic curve key exchange, elliptic curve digital signature, pairing-based cryptography Homomorphic encryption schemes: Homomorphic property, Yao’s scheme, Paillier Cryptosystem, DamgardJurick Cryptosystem. Oblivious transfer: oblivious transfer application in data mining and e-commerce Cryptographic protocol theory: zero-knowledge, -protocol Secure multiparty computations: secure two-party computation, secure function evaluation Electronic elections: e-voting principles, algorithms and implementation E-cash: e-cash principles, algorithms and implementation Efficient implementations of cryptographic algorithms: Modular multiplication, multiplicative inverse, modular exponentiation, RSA implementations, elliptic curve implementations, pairing based cryptography implementations. Side-Channel and Fault Attacks: Side-channel attack principles, Cache-based side attacks, fault attacks, countermeasures Student Responsibilities (tentative) o Homework assignments: There will be a minimum number of three homework assignments. You will be required to write programs in Matlab and C/C++. You may have to use a library called NTL that stands for “number theory library”. o CS 517 class projects: Students are required to work on a term project. They may propose a project topic or may choose from a list provided by the instructor. It is essential for students to meet time schedule of the projects. Project groups must provide a demonstration of their work. During the demonstration, all the project members must be present. Students may work in groups of two. Grading Midterm exam Final exam Homework Project 25% 35% 15% 25% Class Website: http:// people.sabanciuniv.edu /~erkays/cs517