Tutorial 3 - Prince Sultan University
advertisement

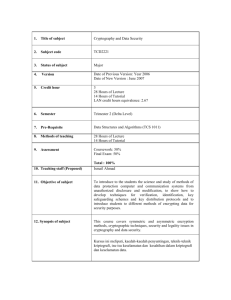
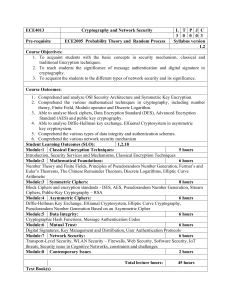
Prince Sultan University College of Computer & Information Sciences Department of Computer Science CS391: Computer Security Tutorial 3 2010 1- Using a block diagram, show the major components of a typical crypto system and the parameters involved. 2- What are the major security problems solved by cryptography? 3- What is the major difference between symmetric and asymmetric cryptography? 4- What are the major characteristics of asymmetric keys? 5- Explain how confidentiality is maintained in asymmetric key systems. 6- Explain how a client may authenticate a server using public key cryptography (prove the identity of the server, assuming that the public key of the server is known). 7- Explain how digital signatures may be implemented using public key cryptography. 8- What are the major types of cryptographic ciphers (algorithms)? Briefly describe each of them. 9- Using a simple plaintext phrase and key, explain how transposition ciphers work. 10- Using transposition ciphers and the key “wisdom”, transform the sentence “public key cryptography” into cipher text. 11- Explain how exponentiation ciphers work. 12- What is the major problem with symmetric key algorithms? 13- Explain how two users may establish a common symmetric key using the DiffieHellman algorithm. 14- Describe in detail the RSA public key cryptographic algorithm and state its main properties. 15- What is the major problem with RSA and public key cryptography in general?