Public Key Authentication between two Solaris Servers:
advertisement

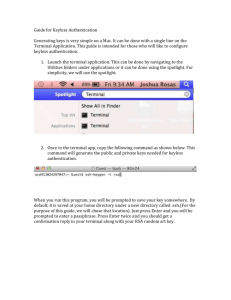
Public Key Authentication between two Solaris Servers: [a]. Generate a pair of SSH keys on the client. Take the default key name ~/.ssh/id_rsa root@fsctsp2# ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (//.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in //.ssh/id_rsa. Your public key has been saved in //.ssh/id_rsa.pub. The key fingerprint is: 05:26:98:a9:1f:c3:03:d1:b1:4e:35:e8:9b:f7:e3:89 root@fsctsp2 Note: Here passphrase is set as null. It is also possible to generate SSH keys using passphrase. When ssh-keygen asks for a passphrase, it is better to enter return twice (i.e.: don't set any passphrase). It's safer to protect a key with a passphrase, however, given the way it will not buy extra security, as the passphrase will have to circulate between your client and the server, and will be stored in clear text. The above said is optional, if the user feel safer; feel free to enter a passphrase. [b]. Copy the public key from the client to the server: root@fsctsp2# scp /.ssh/id_rsa.pub fsctsp1:/ root@fsctsp1's password: id_rsa.pub 100% 222 0.2KB/s 00:00 On the server, append the newly obtained key to the ~/.ssh/authorized_keys file,which stores SSH public keys in the OpenSSH implementation: root@fsctsp1# cat /id_rsa.pub >> /.ssh/authorized_keys [a]. Modify the permissions of the authorized_keys file. If this file is write-able by anybody other than the user, then server will deactivate PK authentication. root@fsctsp2# chmod 600 ~/.ssh/authorized_keys [b].At the client, decrypt and register your key with the ssh-agent: This is required only if passphrase is used. 1. At the client, try and login to the server: root@fsctsp2# ssh fsctsp1 Last login: Thu Sep 22 12:52:21 2005 from fsctsp2 Sun Microsystems Inc. SunOS 5.8 Generic Patch October 2001 Sun Microsystems Inc. SunOS 5.8 Generic Patch October 2001 You have mail. root@fsctsp1# Password-less login Note: This point is valid only when you are generating SSH keys with passphrase. At this point, you'll probably want to set up passwordless login, which is done with the following commands: Invoke ssh-agent and its outputted shell commands: root@fsctsp2# eval `ssh-agent` Agent pid 9626client Decrypt and add your newly generated private key to ssh-agent's database: root@fsctsp2# ssh-add id_rsa Identity added: id_rsa (id_rsa) Now you should be able to do a password-less login to the server: root@fsctsp2# ssh fsctsp1 Last login: Thu Sep 22 12:52:21 2005 from fsctsp2 Sun Microsystems Inc. SunOS 5.8 Generic Patch October 2001 Sun Microsystems Inc. SunOS 5.8 Generic Patch October 2001 You have mail. root@fsctsp1# As you will soon notice, this only gives you password-less login through this terminal. To achieve true one-time per system authentication, it is recommend to use the Keychain utility. This involves downloading the keychain program and adding two lines to your ~/.bashrc or ~/.bash_profile (or ~/.cshrc) files. The utility then keeps you from entering your passphrase more than once.