1952: Istituzione del "Comitato Nazionale per le - Cresco
advertisement

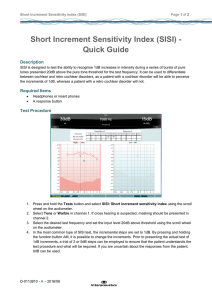
SISI - Information System for Protection of Infrastructures and Population DEVELOPMENT OF GIS-BASED TOOLS FOR VULNERABLE SITES LOCATION ON TERRITORY A.B. Della Rocca, G. Abbate, G. Fattoruso, S. Lo Curzio, F. Pasanisi, A. Peloso, R. Pica, M. Pollino, C. Tebano, A. Trocciola – ENEA ACS Dept. CRESCO - S.P.III.6 OVERVIEW The main aim of SISI Project is to develop a GIS capable of locating vulnerable sites on territory, considering human or natural factors. Location and extension of vulnerable sites are based on the presence of one or more dangerous/vulnerable geographical features inside a specific research area (Fig. 1). According to SISI purposes, geographical features can belong to two different categories: natural (river, basins, land use, etc…) or anthropic (roads, railways, urban areas, etc…) A geographical feature is regarded as “dangerous” if, due to human or natural causes, it can induce the partial or total loss of functionality of other geographical features in its neighbourhood. Examples of dangerous features are: portions of land subject to landslides, chemical plants, oil tanks, dumps, etc. On the other hand, a geographical feature is regarded as “vulnerable” if, due to presence of dangerous features located in its neighbourhood, it can be subjected to partial or total loss of functionality. Typical examples of vulnerable features are civil infrastructures and human settlements. Fig. 1. Location of a vulnerable site based on the co-presence of vulnerable/dangerous geographical features It is noteworthy that the same geographical feature can be regarded either as dangerous or vulnerable feature. For example, a water body is dangerous due to risk of flooding, and, at the same time, vulnerable to pollution due to domestic sewage or industrial discharge. Depending on the nature of considered geographical features, dangerousness or vulnerability can be defined considering also morphological criteria or topological relation among features. The project has been implemented using GIS technology, capable of fusing disparate data, analyzing trends and patterns, and providing actionable information that are easily shared and understood. GIS is essential for critical infrastructure and population protection and provides support by mapping critical assets, analyzing vulnerabilities, identifying protection and mitigation strategies. SISI ARCHITECTURE As for the functionality, SISI system consists of three integrated modules (Fig. 2): 1. Geospatial database, containing data for the entire Italian territory; 2. Geoprocessing tools for territorial “diagnostics”, specifically designed and implemented to identify vulnerable sites based on above described criteria; 3. Web-GIS for accessing, viewing and sharing the vulnerable sites maps on the web. Fig. 2. Overall architecture of SISI system SISI’s diagnostic tools are based on advanced and customized geospatial functions that allow to accurately pinpoint the physical areas where exist defined morphological and topological relationships among the geographical elements (e.g. a given land use, a given distance between features, etc.) and where user defined vulnerability criteria are verified. The analysys can be performed onto the entire national territory or onto defined and delimited areas. These functionalities are accessible via easy-to-use interfaces. The SISI’s user might be an expert with knowledge of territory (e.g. local authorities or administrators), but not necessarily an expert GIS analyst or user. The diagnostic tools allow the following functions, at national or local scale extension: - Selecting investigated geographical features; - Defining extension of research elementary area, called “Focus Area” (e.g. circle with radius 1 km); - Defining possible relations among features which influence dangerousness and/or vulnerability: coexistence, morphological (e.g. curvature) and/or topological conditions (e.g. “within a given distance”, “intersect”, etc.), relative and absolute altimetry, feature dimensions (length or area), etc… Once data have been properly filtered, buffer and intersect operations can be applied to layers. Then, by combining filters, buffer and intersection operations, the whole step is optimized mainly in terms of computation time. Another task of the SISI project has regarded the implementation of a solution capable to optimize the matching of both topological and morphological properties, on the basis of the results obtained in the previous step. RESULTS In Fig. 3 is shown the SISI tool interface, accessible by ESRI ArcGIS environment and whose main steps are the following: 1. Selecting geographical features to be used for analysis; 2. Defining extension of research area (focus) in which all selected geographical features must be present (e.g. circle with radius 1 km); 3. Possibly including morphological and/or topological and/or 3D conditions; 4. Perform analysis. Fig. 4. SISI Tool interface Two different examples are shown in Fig. 4 e Fig. 5. In those cases, the difference is related to the specific vulnerability criterion applied and used to perform the analysis by means of SISI Tool. Fig. 4. Example of result: vulnerable sites location using co-presence criteria Fig. 5. Example of result: vulnerable sites location using co-presence and topological criteria CONCLUSIONS In the framework of SISI Project have been developed innovative processing methods, tools and systems, never up to now realized, that can help to define and adopt suitable actions in order to contrast dangerous or critical events on the territory, and particularly focused to improve population safeguard. In other terms, SISI results can represent an important and meaningful input to those GIS and DSS (Decision Support Systems) that are devoted to the planning and the management of the territory, by mapping critical assets, analyzing vulnerabilities, identifying protection and mitigation strategies In order to reach efficiently SISI objectives, it becomes necessary the access to a high performance computing infrastructure, like CRESCO HPC Platform, especially considering the large amount of data managed and the complexity of analysis involved.