Adaptive Network Management SBIR Proposal (DOC)
advertisement

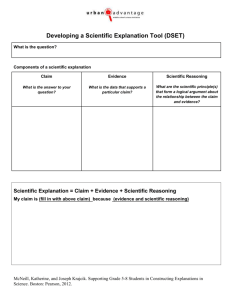
SBIR Phase I Technical Proposal MULTI-ABSTRACTIONS SYSTEM REASONING INFRASTRUCTURE TOWARD ACHIEVING ADAPTIVE COMPUTING SYSTEMS “ADAPTIVE NETWORK MANAGEMENT” 1. IDENTIFICATION AND SIGNIFICANCE OF THE PROBLEM The objective of this proposal is to design and develop a dynamic reasoning environment for a scalable virtualization platform. Simplification of the management of complex and dynamic environments provide control for an adaptive and resilient computing infrastructure. In our approach we propose using an advanced object model to provide an abstracted interface for establishing a reasoning methodology that allows various behaviors to be associated using multiple inheritance techniques. The approach targets security management and resource and availability controls to create a scalable and adaptive computing infrastructure with graphical work space tools to simplify policy management. Adaptability is achieved by establishing policies that take into consideration new and changing elements combined with a rich testing structure to assess and categorize the behavior of new elements. Combined with policies that describe allowed behavioral structures, an environment can be provided where new systems and applications can be added to existing virtualized environments without disruption or security issues being introduced into the system. Policies can define ranges and thresholds for maintaining integrity of their mandates and can trigger events when policy violations have occurred. Supervisory policies can then be applied to take correct action of the environment to accommodate the policy’s mandates. The initial phase of this project will complete the design approach to achieving these objectives. Subsequent phases will test the design within the infrastructure of what will become a product designed to provide a rich and adaptive virtualized computing environment. 1.1 Background As computing environments consolidate hardware resources utilizing virtualization, the issue of managing these resources becomes complex. In order to provide a reliable, secure and flexible scalable architecture, a method of establishing the policies and interactions between the various operations must be devised. Advanced methods of managing these complex environments with simplified graphical representation and policy management is the focus of the target product. Existing approaches have been devised that are based upon various rule systems. Such systems are difficult to control as new applications and virtual machines are introduced. Rigidity of rule based systems almost always require additional engineering to allow new applications and virtual machines to enter into the resource pool without disruption to the integrity of the environment. Chasing these complex environments can demand heavy human intervention and retesting of the newly adapted environment to ensure integrity to existing applications. Cyvergence Corporation 1 September 2012 2. PHASE I: TECHNICAL OBJECTIVES Managing the Environment with Adaptive Algorithms Adaptive elements provide continuity of these complex cloud environments as new elements are added, hardware elements fail, or there is a serious compromise in security. Adaptability ensures that the processing and security goals are met at all times. This project provides an overall structure and multi-abstraction approach to provide a flexible mechanism for the development of various reasoning algorithms. Rules are applied in the form of flowcharts that are attached to abstracted models of the elements that provide control. Managing the complexity is achieved by allowing simple policies to be devised but when combined, they work together in a reasoning engine to facilitate the goals of the policies. Policies are applied to the instance of the various abstracted objects using inheritance. Multiple policies can be attached to provide added functionality. Arbitration of conflicting methods are resolved by employing a technique of determining which policy will take priority or handing it off to a higher level reasoning algorithm. New virtualized machines and applications that enter into the environment must be tested to determine processing requirements and security allowances within the cloud. Existing methods of checking integrity of virtual machines can be employed and the results of the scans and checks entered into a policy. The results of the checks can trigger various responses within the reasoning mechanism resulting in the goals and objectives of the security policies being enforced. Upon detection of a failure or breach of established protocols the offending resource can be instructed what should be done to contain the issue according to the goals of the policies. Everything from a backup checkpoint for survivability, shutdown to migration, or containment within a quarantined environment can be specified. Elevation policies can be employed to contain and jail the offending applications as they progress. 2.1 Scalable Virtualization Platform The employment of the Linux kernel with a middleware framework known as CyverGIX performs the abstractions required to implement the objectives. KVM provides the components to implement an effective virtualization platform. CyverGIX currently provides a basic virtual machine hypervisor offering basic migration and other services on a fully meshed network. Scalability is provided by linking multiple hardware computer devices together and using the mesh capabilities of the network to manage resource routing within the cloud. The mesh is managed by the policy engines to assist in managing routing and containment within the cloud. Much has been written on the security and merits of the virtualization of the entire machine state as it relates to security. The focus of this project is to design and implement a prototype of the reasoning engine into the CyverGIX software layer. Accessibility of the security assessment elements can provide inputs to the reasoning structure to ensure security of the network is maintained. Cyvergence Corporation 2 September 2012 2.2 Using Multiple Abstractions in an Object Model to Perform Reasoning Object oriented architectures provide an abstraction of various entities and their related functions. Using multiple inheritance techniques, we can create a complex association of various policy objects to create an interaction of reasoning algorithms designed to provide system operating goals. Object abstractions include the development of: 1) Resource utilization policies – establishing usage parameters and limitations of various resources including network bandwidth, memory and processor guidelines. 2) Security and integrity policies – establishing methods of verifying the purity of various environments and subsystems including virus control, root kits, access control verification, etc. 3) Reliability and criticality policies – establishing mechanisms to ensure backup strategy, availability methods and redundancy management. 2.3 Policy Based Dynamic State Management Objects incorporate methods. Methods provide the procedural elements of interaction within an object system. The approach outlined here is a variation from standard object oriented paradigms but retains many of the features of multiple inheritance and the benefits of abstraction at the object layer. Implementing these object abstractions and incorporating them for use in an adaptive system involves attaching state procedures or workflow methods (WFM) to the various policy objects. The WFM procedures are constructed from basic functional elements that help to maintain a method of sending event messages to the various system objects abstracted by the object model herein described. Computing resources, policies and VMs are abstracted as objects within this environment. The object model provides events into the supervisory and policy objects and the policy objects respond with events to the resources requiring action. In this manner, a behavioral system can be devised to administer the complexity of the environment and ensure integrity of all the components. The object model also allows these abstractions to contain methods for facilitating the particular actions required in activating the required responses to these message paths. The use of inheritance and polymorphism afford the actual implementations to be borrowed from policies and then implemented by actual instances by the instances themselves. Using the object oriented methodology of inheritance, policy objects are attached to various resource objects by inheriting the policy objects methods. The policy objects methods evoke response handlers on the resource objects directly using polymorphism. This affords policies to be minimally concerned with actual implementations of the required actions and leaves this to the abstracted objects employing the policy. The employment of multiple inheritance concepts provides complex interactions and capabilities from several simpler inherited policy objects. Rules for arbitrating ambiguities in inherited methods is accomplished within the structure of the policy objects themselves. Policies can control the employment of other policy objects creating an extremely responsive and dynamic environment where just about every sort of response and adaptive capability can be devised. Cyvergence Corporation 3 September 2012 2.4 The Object Model The mechanism establishes abstractions for all of the important elements of the virtualized computing platform. In the CyverGIX product definition, we aim to provide abstractions of all the hardware elements as well as several configurative elements over multiple hardware machines that are used to control scalability. The initial abstractions are defined as follows: 1) Hardware Pools 2) Network Interfaces 3) Mesh Networks 4) Domains 5) Hypervisors 6) Virtual Machines 7) Mobile Devices 8) Policies 9) Other decision support abstractions, hardware or software monitors, etc. All of these abstractions have attached to them various methods that are utilized under the direction of a policy abstraction. They can inherit multiple policies to create a combined and complex behavior from simpler policy definitions. Cyvergence Corporation 4 September 2012 The object structure is a unique variant of object oriented programming principals found in today’s popular languages. In effect, the event propagation model is simplified and automatic 2.5 Object Methods Traditional object oriented design evokes event handlers or methods for various events triggered within the system being employed. The approach used in this system is highly modified and different from traditional systems. Traditional approaches involve the use of inline event handlers in response to messages. While our approach still has these types of methods in response to events, we have also devised state managed workflow components to attach complex procedures to the method structure. Each method is actually employed as a complex workflow that contains elements of interaction with other workflows. The mechanism is comprised of several types of elements that when combined produces a flow of logic. Temporal logics, that is logic that reviews information received over time, can be used to establish decisions. Cyvergence Corporation 5 September 2012 The types of functional elements that can occur as a part of workflow are as follows: 1) Processes – processes are called from within the policies and evoke handlers on the abstracted system classes using polymorphism. This allows the policy to direct the behavior of the object from a simplified perspective while the implementation on the abstracted class method actually performs the detailed system process to carry out the activity on the appropriate object. For examplee, the policy may request a suspension of a virtual machine but it is left to the abstraction of the virtual machine to actually carry out the task. In this manner, policies can remain functionally simple and unconcerned with the detail of the implementation. Process can set environment variables that can be used in subsequent decision making processes. 2) Decisions – logic flow of the method can branch around based upon conditions presented by the environment. Decisions can be placed at any point. The environment variables tested are scoped to the entire class of the instance of an abstracted class. Decisions can incorporate the result of a previously executed reasoning process. 3) Waits – A method can be suspended and will wait for another event to take place. A list of events that can respond are placed onto the waiting class as well. In essence this is a wait and branch on event function. A timeout value can also be expressed to indicate that no other event had occurred within the timeout period and execution of the method is to continue based upon the fact that no other events have occurred for the instance of an abstracted class. 4) Events – the workflow methods produce events that are processed by other waiting workflow methods attached to a particular abstracted class. This allows a complex interaction of procedures to interact based upon events that are occurring within the system. The employment of these complex workflow structures as methods to the abstracted system resources creates an advanced system for developing reasoning algorithms used in maintaining the system integrity. Graphical Representation of Reasoning and State Graphical representation of the overall system and the reasoning being applied is conducted using a customized graphical environment. The policy abstractions are Cyvergence Corporation 6 September 2012 represented as various ‘tools’ that can be dragged and dropped into the environment causing the affected objects to inherit the properties of these policies. 2.6 Network Layer 2 Meshing Employing a meshing capability in layer 2 of the network stack provides several advantages to the architecture: 1) Ability to find and locate virtual network interfaces within the hypervisor without identifying and managing complex router rules. 2) Eliminating layer 3 addresses from hypervisor reduces the hackers ‘landing’ resulting in a more secure system. Justification of layer 2 meshing in this project is based the success Cyvergence’s has experienced with incorporating it into its CyverGIX product offering. It is a valuable asset to managing the cloud networking environment and can be utilized to quarantine and manage VPN services. The layer 2 networking provides valuable information regarding the location of various resources inside of the cloud environment. Multiple physical machines can be networked to facilitate a scalable cloud solution. This layer is abstracted within the decision support system to allow an adaptive approach to scalability and security with a major reduction in the complexity of managing such a network. 3. PHASE I: WORK PLAN Phase I will provide a design and prototype environment for the construction of adaptive components and fit them into the CyverGIX middleware architecture. 1) Perform initial design for the following items: a. Current State Evaluation b. Software Integrity Evaluation c. Software Systems Security 2) Modify existing CyverGIX frameworks and map abstractions for the identified system components. 3) Develop policy algorithms to provide system parameters and goals for the processing environment. 4) Develop the main policy enforcement engine and support the event propagation models for the abstracted object classes. 5) Design the Workflow GUI components for build policy methods. 6) Design the graphical representation of the abstracted classes and their relationships to policy management. 7) Construct an approach to visualizing class instances and trace policy enforcements and policy testing methodologies. 8) Define how the overall reasoning structure facilitates new application testing and resource categorization to ensure adaptive constructs are meeting the projects objectives. Cyvergence Corporation 7 September 2012 4. RELATED WORK (By Brad Arant and Matt Link) a) Extensive experience with systems performance evaluation and tuning in an automated “lights out” environment. b) Created several “Operation Automation” products for the commercial market to monitor and handle alerts and events on IBM legacy systems in an automated environment. c) Wrote “dynamic workload balance” for IBM legacy systems that utilized an internal rule based expert system for decision capabilities. d) At Cyvergence, our team created a proprietary “Automated Workflow Management” system leveraging a custom written rule based expert system. e) Created a proprietary version of Linux called CyverGIX with extremely small footprint to run in high volume high performance applications. f) Utilizing a proprietary version of Linux, created a Virtual Machine Environment for commercial use. g) Implemented a proprietary VMM overseer application to leverage the Mets control and observation capabilities inherent in the proprietary VMM platform. h) As a team we created a policy based Data Archival Storage and Retrieval system for use in the forensics industry. i) Development of an elegant Graphical User Interface for representation and management of the Call Flow on the Virtual CyverPBX, and management of the Network Configuration. 5. RELATIONSHIP WITH FUTURE R&D The intent of our work effort is to produce a roadmap for the inclusion into our existing framework of an approach to the utilization of our Virtual Overseer to monitor, evaluate, and facilitate process execution in our Virtual Machine environment. This roadmap must define our approach to providing an ongoing runtime evaluation of critical processes being executed within the virtual machine instances and, where possible, provide the most appropriate resources available to the requestor in order to assure as high a probability of mission success as possible while minimizing the potential impact of attacks. System resources must be selected and provided to the requesting processes in such a manner as to be as transparent as possible. Selection criteria should be made based on the issues of system backup and retention, error and/or attack identification, vulnerability minimization, and event survivability. The culmination of a successful design phase will be that of providing design specifications and the necessary criteria to test and evaluate the efficacy of the proposed solution upon inclusion into the existing Virtual Machine environment. The need for clearances will rest entirely on those applications chosen to be utilized in the testing and evaluation phases of the project as it proceeds. If, in working with governmental agencies, the decision is made that the testing should be done with specific governmental applications, then clearances will need to be procured that will allow staff to evaluate those applications in order to develop acceptable criteria for the testing and evaluation of the product. If testing with Cyvergence Corporation 8 September 2012 commercially available software is deemed to be sufficient then specific clearances may not be needed. 6. COMMERCIALIZATION STRATEGIES Cyvergence is currently in the initial phases of developing a marketing approach for its Virtual Machine Environment. While it is clear that the initial thrust of governmental interest is that of protecting assets critical to the security of the nation, we do not feel that this is necessarily the only marketable use for this product. The concepts, approaches, and techniques developed under the auspices of this program can just as easily be applied to the goals of system administration, performance management, new system installation, and overall system security to allow commercial organizations to manage their software resource more effectively and efficiently in today’s competitive market. We contend that we can utilize these same techniques to implement commercial software constructs that will allow the industry to implement our systems across their enterprise. To that end, we intend to take those lessons and best practices learned within the scope of this project and apply them to our commercial offering as yet another differentiator that will enhance our product offerings. Cyvergence Corporation 9 September 2012