Sigma Six_Improve Phase_Mike
advertisement

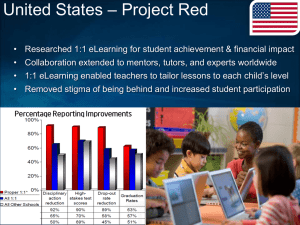
Mike Turner Improvements Phase Healthcare in the Cloud Cloud Security Concerns Fear of the lack of valid security and compliance has caused the healthcare industry to slow down cloud implementation. Cloud providers must ensure that their infrastructure is secure and that their clients’ data and applications are protected while the customer must ensure that the provider has taken the proper security measures to protect their information. Most concerns lie within these areas… 1. Identity and Access Management: Identity management helps to maintain security, visibility and control, and centralizing IT control of identities and access is useful. 2. Data Protection: Encryption of traffic and isolation mechanisms that serve to separate memory, storage, and routing between tenants must be put in place in multi-tenant cloud environments. 3. Compliance: Different countries and regions have different privacy laws, some more strict than others. To be sure that cloud vendors are compliant with policy, it is important that the cloud infrastructure is auditable. 4. Trust: When migrating to the cloud, most of the control is now in the hands of the cloud vendor which requires trust. To build trust vendors need to deliver incident response, such as; attack analysis, containment, data preservation, remediation and service continuity. Data management tools are required so that the client can see over their data on the cloud and make sure agreed upon policies are being enforced. 5. Secured Architecture: Large cloud infrastructures obviously present a bigger and more vulnerable target for cybercriminals. To protect a healthcare cloud from trojans, rootkits and malware requires management of identities and APIs at the network edge to ensure that only authorized users can gain access. Also Hardware and software components that are inherently trusted (Roots of Trust) must be established to secure server and client machines by measuring or verifying software, protecting cryptographic keys and performing device authentication. These concerns can be mitigated by using Intel technology. Intel has done a lot to improve the security of the cloud and make it safe enough for any industry including the Health Care Industry. Cloud Security Solutions To help address the issue of securing sensitive patient data and medical records it is necessary that both client and vendor are using AES encryption. 1. AES (Advanced Encryption Standard) – This type of encryption uses complex algorithms to secure data. a. Due to the complexity of AES algorithms, in an environment where there is endless data being passed to and from the cloud, there will be too much overhead. a) Solution: Intel’s Advanced Encryption Standard New Instructions (AES NI) 1) This solution speeds up the execution of encryption algorithms by anywhere up to 10 times other solutions. 2) Intel has built this technology right into many of their Xeon, Core vPro and Core processors. b) Video on Intel AES NI - http://www.youtube.com/watch?v=Bvmy5BKMG1g b. Using the machine specs in the chart below, Intel measured the performance benefit offered by Intel AES-NI on a Linux/Java software stack to prove that use of their advanced encryption technology would be beneficial for the healthcare sector and allow more organizations to address the increasing security concerns within the industry and by consumers. a) Specs b) Test Results - The test was run 100 times for each encryption method and the results were averaged. c) Key Findings 1) Application file encryption improved 39% (average) and file decryption 37% (average) with Intel® AES-NI enabled over AES128 key. 2) Application file encryption improved 37% (average) and file decryption 38% (average) with Intel® AES-NI enabled over AES256 key. 2. Secure communication connections – Browser protocols must be used to secure browser access and encrypt content as it is transferred over the network and throughout the cloud. a. Secure Socket Layer (SSL) b. Transport Layer Security (TLS) a) The session initiation phase and the bulk-data transfer phase of traditional SSL and TLS are very compute-intesive. 1) Solution: Intel has helped to enhance the speeds and performance by creating 2 library functions to OpenSSL a. The first function accelerates session initiation b. The second function enables simultaneous execution of data encryption and authentication for bulk data. 2) Any software that incorporates OpenSSL can automatically take advantage of these Intel advancements 3. Intel® AES-NI Boosts Data Security for Swedish Healthcare - Sweden is recognized worldwide for its advanced healthcare systems and effective adaption of healthcare IT, but also faces the same problems of healthcare facilities elsewhere. Due to the Swedish Patient Data Act and its demand for stringent security and data protection, even tougher security is required for them to migrate to the cloud. a. Along with basic security measures, the following security measures must be met according to the requirements of the Swedish Patient Data Act to access sensitive health information: 1) Authorized health workers must have a patient relationship (“need to know”) 2) Receive patient consent 3) Employ strong authentication using the Secure IT in Health Services (SITHS) smart card and digital certificates. 4) The Swedish Patient Data Act also governs the maintenance of security logs and requires routine audits of healthcare information disclosure, as well as patient consent, patient access, provisions for breach, and patient requests for modifications to health records b. Siemens Melior – As a solution, Intel collaborated with Siemens to create an innovative healthcare application suite, called Siemens Melior. a) This suite is built on a foundation of Intel Xeon processor-based servers b) Supports SITHS c) Applies role-based access control in support of the security principles of “need to know” and “least privilege.” d) Protects communications of health information in transit through transportlevel SSL encryption and message-level encryption using SAML tokens and digital certificates. e) To address data protection at rest it deploys hardware-assisted encryption in the data center using AES-NI. f) Siemens’ customers are advised to encrypt sensitive information in client, desktop, and mobile devices using full-disk encryption accelerated with Intel AES-NI and solidstate drives (Intel® SSDs). 4. Authenticating Identity and Access a. Intel Identity Protection Technology (IPT) – This is built into Intel Core vPRo processors. a) Provides a simple way to authenticate legitimate users are logging in. b) It validates transactions and defends against malware b. Intel’s Expressway Service Gateway (Intel® ESG) – for API Security a) ESG is a software appliance that provides enforcement points at the network’s edge to authenticate API requests against an organization’s existing identity and access-management systems. 5. Ensuring Trust – Putting data in the cloud is risky business and because you can’t see into the cloud infrastructure, you can’t tell if the data is actually secure and if the vendor is meeting compliance. a) Intel’s Trusted Execution Technology (Intel® TXT) establishes a more secure platform centered on a hardware root of trust at the level of the chipset and CPU to ensure system integrity. b) TXT improves the ability to audit the cloud environment by permitting hardware-based reporting of platform trust both locally and remotely. c) Intel TXT is found in Intel Xeon processors Conclusion Intel has built a foundation secure enough to allow the Health Care Industry to migrate to the cloud without as much concern with security. Although you can never truly be 100% secure, Intel has done a lot to calm the concerns. With using this technology, the healthcare industry will significantly improve on the safety of their data in the cloud. Sources Intel Industry Brief: Healthcare Cloud Security http://www.intel.com/content/dam/www/public/us/en/documents/solution-briefs/cloud-computingsecurity-healthcare-brief.pdf AES NI Charts http://www.intel.com/content/dam/www/public/us/en/documents/white-papers/healthcare-and-inteladvanced-encryption-standards-new-instructions.pdf Securing the Cloud for Government Entities http://www.intel.com/content/dam/www/public/us/en/documents/solution-briefs/cloud-computingsecurity-government-brief.pdf Securing the Cloud for Financial Institutions http://www.intel.com/content/dam/www/public/us/en/documents/solution-briefs/cloud-computingsecuring-cloud-financial-brief.pdf Siemens and Intel Deliver Enhanced Scalability and Robust Security for Healthcare http://www.intel.com/content/dam/www/public/us/en/documents/white-papers/siemens-inteldeliver-enhanced-scalability-robust-security-for-healthcare-paper.pdf Securing the Enterprise with Intel AES NI http://www.intel.com/content/dam/doc/white-paper/enterprise-security-aes-ni-white-paper.pdf Wikipedia http://en.wikipedia.org/wiki/Six_Sigma http://en.wikipedia.org/wiki/Cloud_computing_security http://en.wikipedia.org/wiki/Health_Insurance_Portability_and_Accountability_Act http://en.wikipedia.org/wiki/Audit_trail http://en.wikipedia.org/wiki/Intellectual_property Other Sources Healthcare 'most breached industry in 2011' http://blogs.csoonline.com/1806/healthcare_most_breached_industry_in_2011 Security First: A Network Prescription for the Healthcare Industry http://blog.level3.com/bcdr/security-first-a-network-prescription-for-the-healthcare-industry/ Assessing IT Risks in the Health-care Industry http://www.theiia.org/intAuditor/itaudit/archives/2008/january/assessing-it-risks-in-the-health-careindustry/ Healthcare Cloud Computing (Clinical, EMR, SaaS, Private, Public, Hybrid) Market - Global Trends, Challenges, Opportunities & Forecasts (2012 – 2017) http://www.marketsandmarkets.com/Market-Reports/cloud-computing-healthcare-market-347.html Health care and the cloud are finally coming together http://www.infoworld.com/d/cloud-computing/health-care-and-the-cloud-are-finally-coming-together212581 Roots of Trust http://healthitsecurity.com/2012/12/27/nist-roots-of-trust-for-healthcare-mobile-devices/