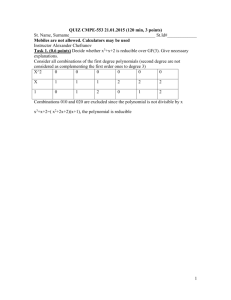
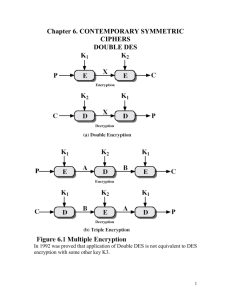
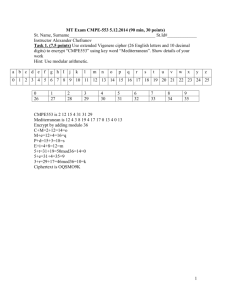
OT-0022
advertisement

A New Approach to Enhance the Security and Performance of Blowfish Algorithm 1,2 Ashwak Mahmood ALabaichi , 3 Ramlan Mahmood, 4 Faudziah Ahmad 5,6 Mohammed S. Mechee Information Technology Department- University Utara Malaysia-06010, Sintok, Malaysia 2 Department of computer science-Faculty of Sciences -University of Kerbala- Iraq 3 Faculty of Computer Science and Information Technology- University Putra Malaysia, Serdang, Selangor, Malaysia 4 Information Technology Department- University Utara Malaysia-06010, Sintok, Malaysia 5 and Information Technology Institute of Mathematical Sciences-university of Malaya-Kuala LumpurMalaysia 6 University Putra Malaysia Department of Mathematics-Faculty of Mathematics and Computer Sciencesuniversity of Kufa- Najaf- Iraq 1 Ashwakalabaichi2007@yahoo.com, 3ramlan@fsktm.upm.edu.my,4fudz@uum.edu.my, 5mohsabd@yahoo.com 1 Abstract Blowfish is a secret-key block cipher proposed by B. Shneier. It is a Feistel network which can iterate a simple encryption function 16 times. The block size is 8bytes and the key can be of any length up to 56-bytes. Blowfish algorithm must dynamically compute all sub-keys and S-boxes before the start of encryption; there is a slight overhead in the computation. This computational overhead of sub-keys and S-box creation results in roughly the equivalence of encrypting an additional four kilobytes of data per data file. Its large memory requirement makes it infeasible for smart card applications. Blowfish also suffers from the defect of the weak key problem. It means that there exists a collision of an S-box. That is, for the keydependant S-box of Blowfish (S1), there exists two different bytes of 'a' and 'a0' such that S1(a) = S1(a0 ). In this paper a 64- bit block cipher called blowfish dynamic S-box and a dynamic permutation table encryption algorithm using a variable key length up to 56 bytes are proposed. It is a Feistel network, iterating a simple encryption function 16 times and it is inspired from 64-bits Blowfish designed to satisfy many goals such as reducing requirements of memory as well as improving the security. The security of blowfish dynamic S-box and the dynamic permutation table encryption algorithm (BDSDP) increased by several techniques such as the relocation of bytes-based secret keys, transformation of the cylinder in three different cases, permutation table -based secret keys and the application of one of block cipher modes(CBC). In BDSDP, Algorithm avoids a symmetric from the output of S-box by a specified approach. The memory requirement is reduced by using the idea of cylinder as a single 3D S-box. The size of 3D S-box is 256 bytes instead of four S-boxes the size of each is 1024 bytes without compromising security. The Cryptographic strength in the context of this paper is related to the ability of the algorithm to produce a random output. The experimental results on five data categories show that BDSDP is better from blowfish algorithm and compatible for any files type without restrictions on files contents. Keywords: block cipher, Blowfish algorithm, dynamic S-box, cylinder, F-function; relocate byte, transformation, dynamic permutation table, randomness test 1 4 mo