Ch. 6. Modern Symmetric Ciphers
advertisement

Chapter 6. CONTEMPORARY SYMMETRIC
CIPHERS
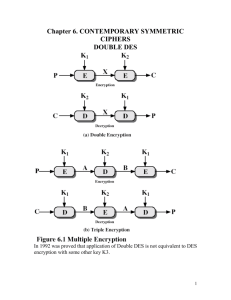
DOUBLE DES
In 1992 was proved that application of Double DES is not equivalent to DES
encryption with some other key K3.
1
Meet-In-the-Middle Attack on Double DES
It is based on the observation that, if we have
C=E K2 [EK1[P]]
Then (see Fig 6.1a)
X= EK1[P]= D K2 [C]
Given a known pair, (P,C), the attack proceeds as follows. First, encrypt P
for all possible 256 values of K1. Store these results in the table and then sort
the table by the values of X. Next, decrypt C using all 256 possible values of
K2. As each decryption is produced, check the result against the table for
match. If a match occurs, then test two resulting keys against a new known
plaintext-ciphertext pair. If the two keys produce the correct ciphertext,
accept them as the correct keys.
Triple DES with Two Keys
The function follows an encrypt-decrypt-encrypt (EDE) sequence (Figure
6.1b):
C=E K1 [DK2[E K1 [P]]]
A known plaintext attack is based on the observation that if we know A and
C (Figure 6.1b), then the problem reduces to that of an attack on Double
DES. Of course, the attacker does not know A, even if P and C are known,
as long as two keys are unknown. However, the attacker can choose a
potential value of A and then try to find a known (P,C) pair that produces A.
The attack proceeds as follows:
1. Obtain n (P,C) pairs. This is the known plaintext. Place these in a table
(Table 1) sorted on the values of P (Figure 6.2b).
2. Pick an arbitrary value a for A, and create a second table (Figure 6.2c)
with entries defined in the following fashion. For each of 256 possible keys
K1=i, calculate the plaintext value Pi that produces a:
Pi=Di[a]
For each Pi that matches an entry in the Table 1, create an entry in the Table
2 consisting of the K1 value and the value of B that is produced for the (P,C)
pair from the Table1, assuming that value of K1:
B=Di[C]
At the end of this step, sort Table 2 on the values of B.
3. We now have a number of candidate values of K1 in Table 2 and are in a
position to search for a value of K2. For each of the 256 possible keys K2=j,
calculate the second intermediate value for our chosen value of a:
Bj=Dj[a]
At each step, look up Bj in Table 2. If there is a match, then corresponding
key i from Table 2 plus this value of j are candidate values for the unknown
2
Triple DES with Two Keys (Cont 1)
keys (K1,K2). Why? Because we have found a pair of keys (i,j) that produce
a known (P,C) pair (Figure 6.2a)
4. Test each candidate pair of keys (i,j) on a few other plaintext-cipher-text
pairs. If a pair of keys produces the desired cipher-text, the task is complete.
If no pair succeeds, repeat from step 1 with a new value of a.
For a given known (P,C), the probability of selecting the unique value of a
that leads to success is 1/264. Thus, given n (P,C) pairs, the probability of
success for a single selected value of a is n/264. A basic result from the
probability theory is that the expected number of draws required to draw one
red ball out of a bin containing n red balls and N-n green balls is
(N+1)/(n+1) if the balls are not replaced. For example, if N=3, n=1, we
have
ExpectedDraws# =
1*(1/3)+2*(2/3)*(1/2)+3*(2/3)*(1/2)*1=1/3+2/3+1=2=(3+1)/(1+1)
So the expected number of values of a that must be tried is, for large n,
2 64 1 2 64
n 1
n
Thus, the expected running time of the attack is on the order of
2 64
2
2120log2 n
n
56
3
Triple DES with Two Keys (Cont 2)
Triple DES with Three Keys
Although the attack just described appears impractical, anyone using twokey 3DES may feel some concern. Thus, many researchers now feel that
three-key 3DES is the preferred alternative. Three-key 3DES has an
effective key length of 168 bits and is defined as follows:
C=E K3 [DK2[E K1 [P]]]
4
Backward compatibility with DES is provided by putting K3=K2 or K2=K1.
A number of Internet-based applications have adopted three-key 3DES,
including PGP and S/MIME for secure electronic mails.
Blowfish
It is a symmetric block cipher developed by Bruce Schneier in 1993
(http://www.schneier.com/blowfish.html ).
Features :
Fast – encrypts data on 32 bit microprocessors at a rate of 18 clock cycles
per byte
Compact – can run in less than 5K of memory
Simple
Variably secure – the key length is variable and can be as long as 448 bits.
It encrypts 64-bit blocks of plaintext into 64-bit blocks of cipher-text.
Sub-key and S-Box Generation
Blowfish makes use of a key that ranges from 32 to 448 bits (1 to 14 32-bit
words). That key is used to generate 18 32-bit sub-keys and four 8x32 Sboxes containing a total of 1024 32-bit entries. The total for sub-keys and Sboxes is 1042 32-bit values, 4168 bytes.
The keys are stored in a K-array:
K1, K2, .., Kj, j=1,2,..,14
The sub-keys are stored in the P-array:
P1, P2,.., P18
There are four S-boxes, each with 256 32-bit entries:
S1,0, S1,1, .., S1,255
S2,0, S2,1, .., S2,255
S3,0, S3,1, .., S3,255
S4,0, S4,1, .., S4,255
The steps in generating the P-array and S-boxes are as follows:
1. Initialize first the P-array and then the four S-boxes in order using the
bits of the fractional part of constant . Thus, the leftmost 32 bits of
the fractional part of become P1, and so on. For example, in
hexadecimal,
P1= 243F6a88
P2=85a308d3
..
S4,254=578fdfe3
S4,255=3ac372e6
2. Perform a bitwise XOR of the P-array and the K-array, reusing words
from the K-array as needed. For example, for the maximum length
5
Subkey and S-Box Generation (Cont 1)
key (14 32-bit words), P1=P1+K1, P2=P2+K2, .., P14=P14+K14,
P15=P15+K1, .., P18=P18+K4
3. Encrypt the 64-bit block of all zeros using the current P- and S-arrays;
replace P1 and P2 with the output of the encryption.
4. Encrypt the output of step 3 using the current P- and S-arrays and
replace P3 and P4 with the resulting ciphertext
5. Continue this process to update all elements of P and then, in order,
all elements of S, using at each step the output of the continuously
changing Blowfish algorithm
The update process can be summarized as follows:
P1,P2=EP,S[0]
P3,P4=EP,S[P1||P2]
..
P17,P18=EP,S[P15||P16]
S1,0S1,1= EP,S[P17||P18]
..
S4,254S4,255= EP,S[S4,252||S4,253]
where EP,S[Y] is the cipher-text produced by encrypting Y using
Blowfish with the arrays P and S
A total of 521 executions of the Blowfish encryption algorithm are
required to produce the final S- and P-arrays. Accordingly, Blowfish is
not suitable for applications in which secret key changes frequently.
Encryption and Decryption
Blowfish uses two primitive operations:
Addition of words, performed modulo 232, is denoted by +
Bitwise exclusive OR, this operation is denoted by
These two operations do not commute. This makes cryptanalysis more
difficult.
Figure 6.3a depicts the encryption operation.
6
Encryption and Decryption (Cont 1)
Note: sign in Fig. 6.3 and 6.4 stands for XOR ( )
The plaintext is divided into 2 32-bit halves LE0 and RE0. We use the
variables Lei and REi to refer to the left and right half of the data after
round i is completed. The algorithm can be defined by the following
pseudo-code:
For i=1 to 16{
REi=LE(i-1) Pi;
LEi=F[REi] RE(i-1);
}
LE17=RE16 P18;
RE17=LE16 P17;
The resulting cipher-text is contained in the two variables LE17 and
RE17. The function F is shown in Figure 6.4:
7
Encryption and Decryption (Cont 2)
The 32-bit input to F is divided into 4 bytes. If we label those bytes as a,
b, c, d, then the function can be defined as follows:
F [a, b, c, d ] (( S1,a S 2,b ) S 3,c ) S 4,d
Thus, each round includes the complex use of addition modulo 232 and
XOR, plus substitution using S-boxes.
Decryption, shown in Figure 6.3b, is easily derived from the encryption
algorithm. In this case, the 64 bits of cipher-text are initially assigned to
the two one-word variables LD0 and RD0. We use the variables LDi and
RDi to refer to the left and right half of the data after round i. As with
most block ciphers, Blowfish decryption involves using the sub-keys in
reverse order. The algorithm can be defined as follows:
8
Encryption and Decryption (Cont 3)
For i=1 to 16{
RDi=LD(i-1) P(19-i);
LDi=F[RDi] RD(i-1);
}
LD17=RD16 P1;
RD17=LD16 P2;
Discussion
Blowfish is a formidable symmetric cipher. Unlike DES, the S-boxes in
Blowfish are key dependent. Both the sub-keys and S-boxes are produced
by a process of repeated applications of Blowfish. This thoroughly
mangles the bits and makes cryptanalysis very difficult. Another
interesting aspect of the Blowfish design is that operations are performed
on both halves of the data in each round, compared to performing
operation on just half of the data in each round in the classic Feistel
cipher. Blowfish is very fast:
RC5
It is a symmetric encryption algorithm developed by Ron Rivest in 1994
(http://www.rsasecurity.com/rsalabs/node.asp?id=2251 )
It has following characteristics:
Suitable for hardware or software
Fast
Adaptable to processors of different word lengths
Variable number of rounds
9
RC5 (Cont 1)
Variable-length key
Simple
Low memory requirement
High security
Data-dependent rotations
RC5 has been incorporated into RSA Data Security, Inc’s major products
including BSAFE, JSAFE, and S/MAIL.
RC5 is actually a family of encryption algorithms determined by three
parameters, as follows:
Parameter
Definition
Allowable values
W
Word size in bits. RC5 16,32,64
encrypts 2-word blocks
R
Number of rounds
0,1,..,255
B
Number of 8-bit bytes 0,1,.., 255
(octets) in the secret
key K
Thus, RC5 encrypts blocks of plaintext of length 32, 64, or 128 bits into
blocks of cipher-text of the same length. The key length ranges from 0 to
2040 bits. A specific version of RC5 is designated as RC5-w/r/b. For
example, RC5-32/12/16 has 32-bit words (64-bit plaintext and cipher-text
blocks), 12 rounds in the encryption and decryption algorithms, and a key
length of 16 bytes (128 bits). Rivest suggests RC5-32/12/16 as the
“normal” version.
Key Expansion
RC5 performs a complex set of operations on the secret key to produce a
total of t sub-keys. Two sub-keys are used in each round, and two subkeys are used on an additional operation that is not part of any round, so
t=2r+2. Each sub-key is one word (w bits) in length.
Figure 6.5 illustrates the technique used to generate sub-keys:
10
Key Expansion (Cont 1)
The sub-keys are stored in a t-word array labeled S[0], S[1], .., S[t-1].
Using the parameters r and w as inputs, this array is initialized to a
particular fixed pseudorandom bit pattern. Then the b-byte key, K[0..b-1],
is converted into a c-word array L[0..c-1]. On a little-endian machine,
this is accomplished by zeroing out the array L and copying the string K
directly into the memory positions represented by L. If b is not an integer
multiple of w, then a portion of L at the right end remains zero. Finally, a
mixing operation is performed that applies the contents of L to the
initialized values of S to produce a final value for the array S.
Let us look at these operations in more detail.
The initialize operation makes use of two word-length constants defined
as follows:
Pw=Odd[(e-2)2w]
Qw=Odd[( -1)2w]
Where
e=2.718281828459.. (base of natural logarithms)
=1.618033988749.. (golden ratio=
1 5
)
2
11
Key Expansion (Cont 2)
and Odd[x] is the odd integer nearest to x (rounded to x+1 if x is an even
integer, although this won’t happen here). For example, Odd[3]=3, and
Odd[ ]=1. Using the allowable values of w, the constants are (in
hexadecimal):
W
16
32
64
Pw
B7e1
B7e15163
B7e151638aed2a6b
Qw
9e37
9e3779b9
9e3779b97f4a7c15
Using these two constants, the array S is initialized in the following
manner:
S[0]=Pw;
For i=1 to t-1
S[i]=S[i-1]+Qw,
where addition is performed modulo 2w. The initialized array S is then
mixed with the key array L to produce a final array S of sub-keys. For
this purpose, three passes are made through the larger of the two arrays;
the smaller array may be handled more times using left circular shift and
addition modulo 2w:
i=j=X=Y=0;
do 3*max(t,c) times:{
S[i]=(S[i]+X+Y)<<<3; X=S[i]; i=(i+1)mod (t);
L[j]=(L[j]+X+Y)<<<(X+Y); Y=L[j]; j=(j+1) mod (c);
}
Rivest comments that the key expansion function has a certain amount of
one-wayness: it is not easy to determine K from S.
12