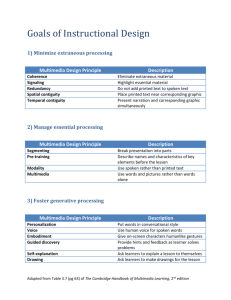
Computer Fundamentals: Intro, Features & Applications
advertisement

Computer Fundamentals & Programming Computer Fundamentals 1. Introduction To Computer System 1.1. Introduction Computer is most important device for this era. The computer technology has almost changed the world in short times. It becomes very essential tool in every walk of human life. The word computer is developed from the Latin word ‘coputare’ which means “To calculate or to compute”. Roughly we can say the machine which calculates is called a computer; but it is incomplete, In fact a computer is a programmable electronic calculating machine. It received data through it input devices, process it and produce output as our requirement with in a second. With help of computer technology a person can communicate to other people from one place to another place of the world through telephone, telex, fax, e-mail etc within a minute. A computer accepts data from an input device and processes it into useful information which it displays on its output device. It operates under the control of a set of instructions that is stored in its memory unit. Definition of computer A computer is an electronic device that accepts data; process it according to a set command and then gives results. In other words a computer is an electronic machine that is used for data processing to produce information. With viewpoints of this definition computer is said to be Electronic calculating machine, Programmable machine, Data processing device, Networking device, Automatic system etc... The computer has following basic system and components devices to process data and gets the output. It has optional components too. A) System device i) Input device ii) Processing device - keyboard, mouse – Central Processing Unit (CPU) iii) Output device – Monitor and Printer CPU Consists motherboard, hard disk, floppy disk drive, sound card, power supply, modem, etc. B) Basic and optional component device (i) 1 2. 3 Basic Components Processor Hard Disk RAM Capacity & functions - 600 MHz, 1200 MHz, 1700 MHz - 40 GB, 100 GB, 160 GB, 200 GB, 2000 GB - 128 MB, 256 MB, 512 MB, 1GB, 2GB 1 4 5 6. 7 8 9 10 Display /Video Card Keyboard Hard disk drive Floppy disk drive CD-ROM/DVD drive Mouse Monitor - 64 MB, 128MB, 512 MB, 1 GB - 84 keys , 104 Keys, 124 Keys - reads, writes on HD - reads, writes on floppy - reads, writes on CD-ROM, DVD-ROM - pointing & clicking device - Displaying device A complete basic components set of these devices is called a computer. Computer may have optional devices too. ii) 1 2 3 4. 5 6 7. 1.2. Optional Components Printer Scanner DVD drive Zip drive Pen drive Modem Speakers Capacity & functions 450ch/sec, 1-18 Pg/min, 4-24 Pg/min Flat bed type & Handheld type Reads/writes on DVD Reads/writes on Zip disk Reads/writes on Pen drive Internal & External type Throws sounds Features (Characteristics of computer) Computer is very important and useful device for everywhere of a human being of this century. This is due to its major capacity or features. There are some important features. i) Automatic Computer is an automatic calculating machine; any given a job it performs independently without assistance of human being. ii) High processing speed A computer is a very fast processing device .It can perform in a few seconds, the amount of work that a human being can do in an entire year. It can perform data processing job very fast usually measure in micro second (10-6), nano second (10-9) and Pico second (10-12). iii) Accuracy (100%) Computer is working its job very accurate. A computer performs every calculation with the same accuracy. However the mistake may occur; if any mistake found in it is not due to the mistake of computer but the mistake of programmer. It works consistently and accurately throughout the time. iv) Reliability Individual components of computer have a very high life and degree of reliability. Computer is only a machine and it does not make errors on its own. So computer is reliable device. v) Diligence (Stay constant) 2 Computer is a machine .It is free from monotony, tiredness and lack of concentration. It can continuously work for hours without creating any error and without grumbling vi) Versatility (Simple to complicated jobs) Versatile is one of the most wonderful things for a computer. It is capable to performing almost any task if the task is reduced to the finite series of logical steps .Once moment it is preparing result of an examination next it is busy to prepare electricity bills and in between it help to type a business letter. vii) Huge storing device Computer has huge storing capacity. It can store a large number of data in it. The secondary storage device is used for it. Thousands of books can be store in a small chip. For instant 1 Kilobyte = 1024 characters/symbol = 103 bytes around 1 Megabyte = 1024x1024 ʺ = 106 ʺ 9 1 Gigabyte = 1024x1024x1024 ʺ = 10 ʺ 12 1 Terabyte = 1024x1024x1024x1024 ʺ = 10 ʺ In accordance the computer has huge storage capacity. viii) World Wide Networking Computers are connected to word wide. Through internet a person from any place to the other person in any place of the world can talk, share picture etc .in a moment, a person get any kind of information through computer .This is all with the help of computer and its word wide network. ix) No I.Q. and Feeling Computer is a machine. It is free from any kind of emotion and feeling. It is not a magical device also. Though it perform the task as human being does but it has no brain as like a human brain. 1.3. Impact of the Computer Technology in the Society 1.3.1. Background: In the world today, computer awareness, use and its impact is increasing in a very high speed day by day. Compared to other technologies, it is developing and changing very frequently. It is a multi-dimensional technology, which can create a multidimensional effect in the all round development of the person, the society and the country. It can help the society providing quality service cost effectively. That is why people are adapting this technology very fast. At present, we have seen that people from different sectors like doctors, engineers, managers, teachers, researchers, businessmen, industrialists and students etc. are using the computers. Using this technology, they are increasing their living standards, economic status, and personal working capacity and so on. It can bring rapid progress and prosperity in the country. Singapore, Japan, South Korea, Taiwan and others are good examples. To develop the country and society, the revolution of agriculture had taken more than thousand years and the industrial revolution had taken about a century. But the revolution of technology has taken only about 25 years to change the society and country. It is a very fast changing technology, which can accelerate the developing speed of the nation. It can bring fast economical revolution to the country. It can quickly change the life style to bring prosperity. Therefore, it can impact the society in multiple ways. Advantage and disadvantage of the technology are as follows. 3 1.3.2. i. ii. iii. iv. v. vi. vii. viii. ix. x. xi. Employment benefit Greater efficiency Higher Quality Product Better Service Recreational and educational benefit Aid to handicapped Improved Safety Better Information retrieval Educational benefits Personal finance benefits Benefit of greater personal efficiency. 1.3.3. i. ii. iii. iv. v. vi. vii. Positive Impact: Negative Impact: Employment problem System Security problem The privacy issue Freedom restrictions Privacy control The threat to access by the hackers The threat to the system security, etc. 1.4. Application of Computer in the society Realizing the above social impact, the people of the world are endeavoring to provide computer education to their children from an early age. Most of the developed countries have made Computer Education compulsory from grade one to Ph.D. level. They had prepared the curriculums to use it according to the level and requirements. Most of the countries are investing lots of money on the computer education for better quality of life and speedy development. Due to the development of computer technology, India, South Korea, Taiwan, Singapore and Malaysia have upgraded the living standards of their people within the last two decades. But Nepal could not develop much compared to what they had done. In fact, Nepal had also started using this technology since 1970 AD but, because we did not care about the quality Computer Education in the right time. We have not yet been able to frame proper national policy of IT (Information Technology) development and human resource development on IT. Anyway, in Nepal also people had started computer Education from class 3 to the Ph. D. level at present. They are using computers in different sectors. There are good impacts of this technology. At present, people in Nepal are using this technology in the following fields for the personal and social benefits. 1.4.1. i. ii. iii. iv. v. vi. vii. Education Sector: Result Processing in Schools, 10+2, Colleges and Universities. School Information System Processing in Ministry of Education. Students & Teacher's Record Keeping. As a teaching tool for Science, Health, Geography, etc. As a learning tool in the practical class of Schools, Colleges and Universities. Account keeping, Payroll System and others. Statistical record keeping, etc. 4 1.4.2. i. ii. iii. iv. v. vi. vii. Health and Sector: CT scanning Ultra Sound Patient Record Keeping Account Keeping Statistical Report Medical Store Inventory Control Research and Development. 1.4.3. Banking Sector: (i) Bank Account Keeping (ii) Electronic Money Transfer (iii) General ledger (iv) Note conciliation (v) Monthly/Yearly Income & Expenditure Record Keeping (vi) Monthly/Yearly Money Transaction (vii) Research and Development (viii) Reconciliation. 1.4.4. Hotel Management: (i) Front Desk Management System (ii) Manpower Management (iii) Account keeping (iv) Store and kitchen Inventory Control System (v) Hotel Management System (vi) Hotel Booking (vii) Record Keeping. 1.4.5. Airlines Management: (i) Ticket Booking (ii) Ticket Reconciliation (iii) Billing & Ticketing (iv) Spare parts Inventory Control System (v) Account Keeping (vi) Commission Agents’ record keeping (vii) Personnel Management System. 1.4.6. (i) (ii) (iii) (iv) Agriculture Sector: National Agriculture Census Research and Development Personnel Management Production Control Management System 5 (v) Manpower Training (vi) Store and Inventory Control System. 1.4.7. Industrial Sector: (i) National Industrial census (ii) Research and Development (iii) Production Control (iv) Quality Control (v) Inventory Control System (vi) Demand and Supply System (vii) Manpower Management System (viii) Property Management System (ix) Spare parts Inventory Control System. 1.4.8. (i) (ii) (iii) (iv) (v) (vi) Communication Sector: International News Collection, Dissemination & Control National News Collection, Dissemination & control Dissemination of news, in terms of text, voice and views Research and Development Store Inventory Control System Record Keeping System, etc. There are other sector also where the application of computer is very important these are E-Governance, Office, Intelligence Machine, Weather Forecasting, Decision Making, Distance Education, Film recording, Traffic Control, Playing games, Publication etc. 1.5. History And Development Of Computers A computer is an invention of human beings to enhance their capabilities to accomplish tasks. Modern computers are developed after a gradual change over a long period of time. In another word, it was not developed in one day. Hence it has its own history. Tribal life in ancient time required man to remember a lot of information, so an early man felt the need to count the things. Then he started counting using his own fingers. However, the limited number of fingers had made it difficult for him to remember more facts. Thus, he started different methods to count using stones, sticks, scratches on a rock or wall or knots in a string. As a result, during fifth century Hindu philosophers were able to develop a new method of counting using the numbers (digits) 0 to 9. Since there are ten digits, the Arabic Number System method was called Decimal Number System of counting. Hence, the history of computer implies the gradual change in the concept over a long period of time. In the following section, we will explain the history of computing machines from their early forms to the most modern high-speed electronic computers. (a) BC 5000 to 2000 Abacus In early days, people used pebbles or beads on a counting board to carry out simple calculations. This tool is called the Abacus. Its exact origin is unknown. It may have originated in China, Egypt and Greece during 5000 B.C. to 2000 B.C. An abacus can be used to add, subtract, multiply and divide. Even today the abacus is used in many parts of the world (e.g. China). (b) A.D. 1614: Napier’s Bone 6 In 1614 John Napier, a Scottish Mathematician, first published the first table of logarithms. It was very helpful in simplifying multiplication of large numbers. In 1614, Napier also developed a numbered rod in order to multiply, divide and extract roots, known as Napier’s bone. It was called so because it was made up of strips of bones on which numbers were painted. By the combination of these bones, direct multiplication could be done. (c) A.D. 1620: Slide Rule In 1620, Slide Rule was developed by William Oughtred, UK which is an analog device. It used the principle of logarithms. It has two graduated scales. One scale slides or slips upon the other. With the proper alignment of the two scales, it is easy to find the product, quotient or any other function simply by viewing on the scales. (d) A.D. 1642: Pascal’s adding machine The first real calculating machine that could add and subtract was a mechanical calculator called Pascal’s Adding Machine or Pascaline, invented by a French scientist Blaise Pascal in 1642. Pascal’s Adding machine consisted of ten toothed wheels. The addition or subtraction was performed by turning these wheels. (e) A.D. 1694: Leibnitz’s Calculator The first calculator that could perform automatic addition, subtraction as well as multiplication and division was developed by a German philosopher Gottfried Wilhelm Von Leibniz. In 1671, Leibnitz modified his calculator. It was also known as. Stepped Recknor. (f) A.D. 1801: Jacquard’s Loom and Punched Card At the beginning of the nineteenth century (i.e. A. D. 1801), Joseph Marie Jacquard of France invented a punched card as an accessory to the loom. The punched card could automate the loom for the weaving of intricate patterns. Thus, he could control the weaving loom through the set of holes in a card, which could store the instruction for the loom. (g) A.D. 1822 and 1833: Babbage’s Differential Engine In 1822, another interesting development took place in the history of computers. Charles Babbage, an English Mathematician, invented a calculating device called Differential Engine . Babbage wanted to calculate Polynomial functions using the method of differences. Babbage, also wanted to design a bigger machine, called an Analytical Engine. The idea of an Analytical Engine developed in 1833 AD was considered as a most significant step in the history of computers, because of his idea only, the dream of modern computer has come true. That is why he is famous as “Father of Computer”. Babbage intended to have his machine to have a mechanism to input data and output the results. He wanted to input data with the help of punched cards and the output to be printed on copper plates. Babbage’s analytical engine and modern day computers are similar in their structure. This engine had four major units. 1. Store: A memory or store which could store data and intermediate results. 2. Mill: An arithmetic unit which was called a ‘Mill’. It could perform calculations. 3. His machine had mechanism having gears and shafts by which data and results were transferred between the store and the mill which is similar to the control unit of today’s computer. 4. Input and Output devices (h) A.D. 1848 Lady Ada Agusta In 1848 AD, a British mathematician Lady Agusta wrote a first program to run an analytical engine made by Prof. Charles Babbage. Hence she is called a first programmer. 7 (i) A.D. 1850 George Boole George Boole, a British mathematician, introduced mathematics of logic known as Boolean algebra. It laid the foundation of digital computers. Boolean considered two-valued binary notation (i.e. 0 and 1) to represent any form of data. (j) A.D. 1890: Dr. Herman Hollerith The first card machine which was electrically activated was used by Dr. Herman Hollerith to compute the statistics of the 1890 AD United States population census. Hollerith was an American mechanical engineer and statistician, working for the Census Bureau. He used the punched cards to store data, with the holes representing data values. He developed an electromechanical tabulating machine for punched cards. Because of his sincere efforts, the population census of 1890 could be processed in one-third of the time allotted. (k) A.D 1937: Electromechanical Computers (Mark I) In the early part of the twentieth century, tabulating machines were growing rapidly. In 1937, next important event occurred in history. The first electromechanical computer with the development of MARK I was invented by Howard Aiken and other was constructed MARK I at Harvard University under the sponsorship of IBM (International Business Machine).The MARK I also known as the Automatic Sequence Controlled Calculator. It was 50ft. long and 8 ft. high. It used electronic tubes and electrical relays. MARK I took 4½ seconds to multiply two 23-digit numbers. It was able to produce ballistics tables that were used in connection with Second World War. The input device used was the punched paper tape. (l) A.D. 1939: Electronic Computers (ABC computer). The age of electronic computer began when vacuum tubes were introduced. Such tubes were thousands of times faster than the earlier electromechanical devices. The first electronic digital computer was developed in 1939 AD by John V. Atanasoft and his student Clifford Berry It was called Atanasoft-Berry Computer (ABC computer). (m) A.D 1940: ENIAC (Electronic Numerical Integrator And Computer) In the true sense, the first electronic computer was developed by John W. Mauchly and John Presper Eckert. It was developed at the university of Pennsylvania and called ENIAC (Electronic Numerical Integrator And Computer), based Decimal Number System. ENIAC used high-speed vacuum tubes (switching devices). The high speed operation of the computer in the world was first experienced with ENIAC. It could add two numbers in 200 microseconds and multiply two numbers in 2800 microseconds. Number of vacuum tubes used was 19,000. It occupied an area of 150 square meters and was 1,000 times faster than Mark-1. (n) A.D. 1949: EDSAC (Electronic Delay Storage Automated Computer) In 1945, a noticeable improvement in the development of the computer took place when John Von Neumann, the Hungarian mathematician genius developed the idea of Stored Program Concept, which was a very important technique to design today's Computer. According Neumann, it would use Binary Number system instead of Decimal Number System used in ENIAC. Then Prof. Maurie Wilkes used the I.V Neumann’s stored program concept to design the computer called EDSAC (Electronic Delay Storage Automatic Computer). EDSAC was called the first stored program electronic computer developed completely in 1949. (o) A.D. 1951: UNIVAC (Universal Automatic Computer) After developing ENIAC, Mauchly and Eckert formed their own company in 1946. This company built a new computer called UNIVAC-I (Universal Automatic Computer-I) in 1951. UNIVAC was delivered to the 8 Census Bureau. Business organizations too started using UNIVAC. Hence, it was called the first commercially used electronic computer in the world. (p) A.D. 1970: Microprocessor The first Microprocessor was built at Intel Co-operation, USA in 1970. It was used to build minicomputer and micro computer at the beginning. (q) A.D 1972: Minicomputer The first minicomputer was developed by Digital Equipment Corporation (DEC) in 1972 A.D. Within 1977 AD different computers started developing varieties of Minicomputers. (r) A.D. 1974: Microcomputer The first microcomputer called ALT AIR 8800 was manufactured in 1974. It used an 8-bit Intel microprocessor. The Apple personal computer and IBM pc was first introduced in 1976 and 1981 AD respectively. (s) A.D. 1994: Pentium Series IBM Company launched PCXT (Extended Technology) and PCAT (Advanced Technology) microcomputers were developed first time in 1983 and 1984 AD respectively. Then in 1994 AD Pentium series of Microprocessor Chips were launched. In the same year, US vice President Mr. Algor announced about “Internet for all”. Then most of the developed and developing countries tried to use Information Technology (IT), where people could use Internet, Intranet, extranet and email. With the help of this technology they also started using Website, Digital Library, E-commerce, E-shopping, E-Banking and Telemedicine, etc. (t) AD 1995: Multimedia Technology (MMX) Pentium I with Multimedia Technology (MMX) computer was built and released. In the same year, Windows 95 and Graphical User Interface (GUI) were launched by Microsoft. (u) A.D.1996: Linux Operating system This year different individual software developers developed Linux Operating System. (v) A.D. 1997: MS-Office 97 Microsoft Company Launched MS-Office 97 (Office Application) for Windows 95. Similarly in the same year private individuals also designed and sold a special type of Operating System named LINUX in the world market. (w) A.D. 1998: Windows 98 Microsoft Company released advanced Windows 98 Operating System, which was the corrected and advanced version of Windows 95 and windows 97. (x) AD: 2000: Windows 2000 Microsoft Company again developed and released advanced version of windows 2000 Operating System, which are being used worldwide even today. 1.6. History and Development of Computer in Nepal: 9 Although the first electronic digital computer was built in mid 1940’s, computer was introduced in Nepal in the year 1972 only. It was introduced by Government for the population census of 1972 (2028 B.S). This was the second generation computer of IBM Company called IBM 1401. The Government had paid Rs One lakh twenty five thousand per month as rent for this computer. The Census Department at Thapathali Kathmandu had used IBM 1401 computer for the first time to process 1 corer 12.5 lakhs population census taking 1 year, 7 months and 15 days. Later, it became essential to operate the computer for day and night, for this reason a separate branch office called Yantric Sarinikaran Kendra (Electronic Data Processing Centre), was established in 1974 (15th Paush 2031 B.S.), which, after six years, was converted to National Computer Centre (NCC). For the population census of 1981 (B.S. 2038), a British computer ICL 2950/10 (International Computer Limited 2900 Series) which had 64 terminals was added from the aid of UNDP and UNFPA at two million American dollar from the British ICL Company. By the help of this fourth generation computer, the 1981 population census was completed within one year and 3 months. Microcomputer such as Apple, Vector and Sirus were introduced in Kathmandu for the first time in 1982 (B.S. 2039). New companies such as Computer consultancy (CC), Management Information Processing System (MIPS) and Data System International (DSI) were established. Since 1983 (BS. 2040) National Computer Center, on the other hand, also started giving training on programming, data entry, data processing, and development of software packages. As a result, many people from various sectors started showing their interest in the field of computers. Since 1977 (B.S. 2034) His Majesty’s Government employed IBM 1401 computer in tourist statistical data processing, industrial data processing, statistical and loan account keeping of Agricultural Development Bank, Provident fund, SLC result processing and TU result processing, etc. After a few years, new computer ICL 2950/10 was brought in use, which was more efficient for data processing in some other corporations such as Telecommunication, Electricity Authority, Janakpur Cigarette factory, Hetauda Cement Factory, Tribhuwan University, etc. Many others like travel agencies, hotels, factories, printing presses also started using computer for better & faster work. At present, not only Kathmandu is using microcomputers but also Lalitpur, Bhaktapur, Pokhara, Nepalgunj, Bhairhawa, Butwal, Hetauda, Birgunj, Biratnagar, Janakpur, Jhapa etc. are using computer for different purposes. Nowadays, computers have been used in different areas like, travel agencies, hotels, Airlines, Government offices, Banks, Colleges, Schools, Hospitals, etc. in Nepal. People are using computer even at home for day-to-day use for their personal convenience. Now there are more than 1000 private computer-training centers all over Nepal. About 50 software development centers are working in the Nepali market. At present, in Nepal more than 1250 schools, 107 higher secondary schools, 50 general colleges, 42 IT related colleges and 4 Universities are teaching and using computer technology. More than one hundred thousand computers are busy in Nepal. More than 28 private Internet Service Provider (ISP) are providing services in the Nepali market. Nepal had started using email, Internet, e-Banking and Websites since 1996 AD. The purpose of using the computers is for word processing, keeping accounts, keeping the records and details of employees, inventory control, etc. A few software houses are involved in software development and in exporting the software to the international market (i.e. in Japan, Germany, USA, UK etc) also. Some of the private institutes and companies are involved in computer assembling, selling and distributing like in other developed countries. The scope of computer in our country is increasing rapidly day by day. In May 2000 AD, Ministry of Science and Technology, HMG had announced the national policy on IT. Similarly, HMG had announced the Cyber Law and copyright Law in Sept 2004 etc. 1.7. Generations The "Generations of computer" refers to the development step of technology of computer. It provides a framework for growth of computer industry. Initially it was classified according to the use various hardware 10 technologies but it has now been extended to include both hardware and software. Up to now there are five computer generations. They are classified with their hardware and software technologies, characteristics and working speed which are shown by the following table. Generation (period)& working speed 1st Generation 1942 1954 Second to 2ndGeneratio n 1955 to 1964 Mile Second 3rd Generation 1965 to 1974 Micro Second 4th Generation 1975 to 1789 Nano Second Key hardware Key software technologies technologies Key characteristics Some representative System Vacuum tubes; electromagnetic relay memory; punched cards secondary storage Bulky in size Highly unreliable Limited commercial use and costly Difficult commercial production Difficult to use Faster, smaller, more reliable and easier to program than previous generation system commercial production was still difficult and costly Faster, smaller, more reliable, easier and cheaper to produce Commercially, easier to use, and easier to upgrade than previous generation systems Scientific, commercial and interactive on-line applications Small, affordable, reliable, and easy to use PCs; More powerful and reliable mainframe systems and super computers Totally general purpose machines; Easier to produce commercially Easier to upgrade ENIAC EDVAC EDSAC UNIVAC I IBM 701 Machine and assembly languages; Stored program concept; mostly scientific applications Transistors; Batch operating magnetic core system; memory; High-level magnetic tapes programming Disks for languages; secondary storage Scientific and commercial applications ICs with SSI and Timesharing MSI technologies; operating larger magnetic system; core memory; standardization larger capacity of high-level magnetic disks and programming tapes secondary languages; storage; Unbundling of Minicomputers software from upward compatible hardware family of computer ICs with VLSI Operating technology; systems for PCs; microprocessors; GUI; multiple semiconductor windows on a memory; single terminal larger capacity screen; hard disks as in- UNIX operating built secondary system; C storage; programming magnetic tapes and language; floppy disks as Object oriented portable storage design and Honeywell 400 IBM 7030 CDC 1604 UNIVACLA RC IBM 360/370 PDP-8 PDP-11 CDC 6600 IBM notebook Pentium PC SUN Workstation IBMSP/2 SGI Origin 2000 Apple II, TRS-80, VAX 9000, CRAY-I, 11 5th Generation 1990 to now Pico Second 1.8. media; Supercomputer based on parallel vector processing and symmetric multiprocessing personal computers; spread of highspeed computer networks ICs with ULSI technology; larger capacity main memory hard disk with RAID support larger Ooptical disks as portable read-only storage media; Notebook computers; powerful desktop PCs and workstations; Powerful servers, supercomputers The Internet Cluster computing programming PC, networkbased, and supercomputing applications; Rapid software development possible CRAY-2, CRAYX/MP Micro-kernel based, multithreading, distributed OS Parallel programming libraries like MPI and PVM JAVA World Wide Web multimedia, Internet applications Portable computers Powerful, cheaper, reliable, and easier to use desktop machines; Powerful supercomputers mainframes High uptime due to hot-pluggable components Totally general purpose machines Easier to produce commercially easier to upgrade Rapid software development possible IB notebooks, Pentium PCs, SUN Workstations, IBM SP/2, SGI Origin 2000, PARAM 10000 Types of computer There are various Types of computer they are classified as follows i) Volume wise -Super, Mainframe, Mini, Micro computer, Laptop, Palmtop ii) Job wise -Digital, Analog, Hydride iii) Brand wise - IBM,IBM Compatible, Apple/Macintosh iv) Assemble wise - Branded and Assembled 1.9. Computer Architecture (CPU, ALU,CU, Memory) The computer architecture means the physical and functional design of computer. This means the design of any part of the computer system or of an entire system including hardware and software. There are five basic operation of computer system .These are 12 i. ii. iii. iv. v. Inputting:-The process of entering data and instruction to the computer system is inputting. Storing: - Saving data and instruction to the computer to make them readily available for initial or additional processing whenever required is storing Processing: - performing arithmetic operation (add, subtract, multiply, divide, etc.) or logical operation (comparison like equal to, less than, greater then, etc.)on data to convert them into useful information is processing. Out putting:- The process of producing useful information or result user such a printed report or visual display is outputting Controlling:-Directing the manner and sequence in which all of the above operation are perform is controlling. CPU UUU UUU Logic Arithmetic UnitUU (ALU) Input Control Unit Output Memory To perform above function there are corresponding functional unit. i) Input Unit: The computer hardware that accept or receive data and instruction from the user. It performs following function. 1. Accepts (or reads) instruction and data from the user outside world. 2. Converts these instruction data in computer acceptable form. 3. Supplies the converted instruction and data to the computer system for further processing. Keyboard and mouse are the examples of input device ii) Output Unit: The hardware of the computer system which display or give result which is generated by processing of data. It performs following function. 1. Accept the results produce by the internal devices and software, which are in coded form and hence, cannot be easily understood. 2. Convert these coded results to human acceptable (readable) form. 3. Supplies the converted results to the user. Monitor and printer are the examples of output device. iii) Storage Unit: The hardware of the computer system which holds(or stores) the following: 13 1. 2. 3. Data and instructions required for processing time which are received from input device. Intermediate results of processing. Final result processing, before they are released to an output device. There are primary and secondary storage(memory) units. Primary memory is also known as main memory. Primary storage i. ii. iii. iv. v. vi. Use to hold running program instructions. Used to hold data ,intermediate results ,and result of ongoing processing of job(s) Fast in operation Small capacity Expensive Volatile (looses data on power dissipation) Secondary storage i. ii. iii. iv. v. vi. Use to hold stored program instructions. Used to hold data and information of stored jobs Slower than primary storage Large capacity Lot cheaper than primary storage Non Volatile (retains data even without) Registers- They are additional storage locations to store data during processing time. They appear in between ALU and CU of CPU Address- Character storage locations numbers in the main memory like a mail box numbers. Location numbers remains the same but the contents changes continuously. iv) ALU: The device inside CPU Box which performs Arithmetical & logical calculations. It is the place where the actual execution of instruction takes place during processing/operation. v) Control Unit (CU): The control unit of a computer system manages and coordinates the operation of all other component of the computer system. It is like a nerves system of the body; the whole system sending signal of data program and tells to process data and to store in the right place. vi) Central Processing Unit (CPU): The CU and ALU together constitute a processing unit; It is like brain of a computer system. It is responsible for controlling the operation of all other units of a computer system. It is also called micro processor. Note: I. II. ALU+CU=CPU It is a brain of the computer system It is responsible for controlling the operation of all other units of a computer system A system has following three characteristics It has more than one element All element of a system are logically related All elements of a system are controlled in a manner to achieve the system goal 14 A computer is a system as it comprises of integrated components (input unit, output unit, storage unit, and CPU) that work together to perform the steps called for in the executing program. 1.10. RISC, CISC, EPIC The architecture of CPUs with the small instruction set, fixed length instruction and reduce references to memory to retrieve operands is known as RISC. It is called reduce instruction set computer. The architecture of CPUs with the large instruction set, variable length instruction and a variety of addressing mode is known as CISC. It is called complex instruction set computer. The architecture of CPUs with the emerging technology which includes three key features, explicit parallelism, prediction and speculation is known as EPIC. It is called Explicitly Parallel Instruction Computing. 1.11. Working Speed Units Of The Computer: The working speed of a computer means the speed of its processors. The CU and ALU perform operation at incredible speed. These operations are usually synchronized by the built-in electronic clock (known as system clock) that emits millions of regularly spaced electric pulse per second (known as clock cycles). It is measured in hertz .Hertz means one cycle per second. Normally, several clock cycles required to obtain, decode and execute single program instruction. Hence, the speed at which an instruction is executed is related directly to a computers built-in clock speed which is the number of pulse produce per second. This cock speed is measured in mega hertz, gigahertz. Some examples are Class CPU Speed INTEL 4004 INTEL 8080 INTEL 8086/87 INTEL 8088 INTEL 20286/87 INTEL 20386 DX 108 KHz 2 MHz 5 MHz, 8 MHz and 10 MHz 4.77 MHz and 8MHz 8 MHz, 10 MHz and 12 MHz 16 MHz, 20MHz and 25 MHz, 33 MHz 16 MHz, 20MHz and 25 MHz, 33MHz 25 MHz, 33 MHz and 50 MHz INTEL 20386 SX/SL INTEL 20486 DX/SX INTEL 20486 DX2 INTEL PENTIUM INTEL PENTIUM MMX INTEL PENTIUM PRO Approx starting) 1970 1974 1976 1979 1982 1985 year (1970 1989 1991 33 MHz and 66 MHz 60 MHz to 200 MHz 166 200,233 MHz and 266 MHz 1992 1993 1997 166 and higher 1997 15 INTEL PENTIUM II INTEL PENTIUM III INTEL PENTIUM IV INTEL Dual Core INTEL Core 2 Duo 233 MHz to 450 MHz 500 MHz, 750 MHz More than 1.1 GHz up to GHz 2.0 GHz 3.4 GHz 2.0 1997 1999 2000-2007 2008 2008 2. Memory Units A device or a media that can accept data holds them and deliver as per demand at a later time is called memory. Every computer has a temporary storage built into the computer hardware. It stores instruction and data of a program mainly when the program is being executed by the CPU.The temporary storage memory is known as main memory or primary memory or simply memory. Physically, it consists of some chips either on the motherboard or on the small circuit board attached to the mother board of a computer. It is volatile and random access property. Types of main memory: i) Random Access Memory (RAM): The memory in which time to retrieve stored information is independent of the address where it is stored. It is volatile and random access memory. Types of RAM a. Dynamic RAM: Very commonly used RAM. They are refreshed thousand times per sec. They are used everywhere like in printer. b. Static RAM- Special RAM. They are less often refreshed. They are costly than dynamic RAM. (Computer writes on COMPASS offer reading ROM) ii) Read Only Memory (ROM): It is non volatile memories chips in which data are stored permanently, and cannot be alerted by programmers .It holds small amount data and displays it during to start computer. iii) PROM: A program strong empty memory chip. Once stored a program, it is permanent. Therefore PROM is non-volatile memory. iv) EPROM (Erasable PROM) - A chip, where the program can be erased by exposing it to ultraviolet light. v) EEPROM (Electrically Erasable PROM): It is special type of EPROM that is Electrically Erasable PROM. It is a chip in which stored information erased by using high voltage of electrical pulse .it is also known as flash memory. 3. Storage Devices:(Auxiliary or Secondary Storage Device) The devices that store data supplements main memory of a computer are called auxiliary or secondary memory. It is generally non volatile memory and used in computer to overcome the limitations of primary storage memory. The operating speed in it is very slow and cost of per bit of storage very low than that of the primary memory. There are two types of secondary storage device. 16 Types of Auxiliary Storage Device: i) Sequential Access Device (Tape): It is a device where the data con only be retrieved in the same sequence in which it is stored. The access time varies accorting to the storage location of the information being accessed. The example of this type of device is Tape Tape (Sequential Type) 60 MB-24 GB ii) Random Access Device: The storage device in which access to any stored information is direct, and approximately equal access time is required for accessing any information irrespective of its location. Magnetic, Optical and Magneto Optical disks are the the typical examples of such a storage device. A. Magnetic Disk a. Floppy Disk Floppy (Random Access Type) b.Hard Disk( Zip Disk, Super Disk ) i. Zip Disk ii. Jaz Disk (A cartridge) iii. Super Disk (A cartridge) 720 KB-1.44 MB 100 MB- 250 MB 2GB 120 MB B. Optical Disk (CD-ROM, CD-R , CD-RW, DVD Drive) i. CD-ROM (A cartridge) (630 MB-1GB) (About 700 floppy;3,000,000 page texts) ii. CD-R(Recordable)(A cartridge) It creates CD-ROM or Audio CDs to publish. It needs a CD-R software package. It can read CD-R and play Audio CDs. iii. CD-RW (A cartridge) It is a Re-Writable CD. (Many times rewrite) It is like a floppy disk of high storage capacity iv. Digital Video/Versatile It looks same as CD-ROM but has capacity of 4.7 or 8.5 GB It is also two types DVD-R and DVD-RW C. Magneto-Optical Drive Magneto-Optical Drive (A cartridge) It is a special type of disk drive. It can read and write MO-Disk. It stores 200 MB faster than CD-ROM. D. Pen drive 17 It is a compact device of the size of a pen. It plugs into a USB(Universal Serial Bus) Port of the computer 8 MB to 8 GB Memory Prime Memory Storage Memory Secondary Storage RAM Backup Storage ROM Semi-random Access Erasable Memory Serial Access Permanent Memory Disks SRAM Zero Power Non-volatile RAM Zero Power Non-volatile RAM DRAM EPROM EE-PROM Flash Memory Masked ROM PROM Floppy Hard CD-ROM Zip Disk Pen Drive Magnetic Tapes CCD 18 4. Input Devices: 4.1. Key Board, Mouse a. Keyboard b.Mouse - 101 keys, Alphanumeric key, Punctuation keys, Special keys, Arrow keys, etc. - Curser or Pointer controller, developed in 1963 USA. 4.2. Track Balls, Joystick a. Track Ball - Pointer mover by your palm, or thumb press. b. Joystick - Pointer mover leaver with two buttons (Triggers). 4.3. Scanner - It can read text and pictures to convert it into digitals form and store to print them. It can print 600 dots per inch quality text or Images. There is single color or multiple colored scanners. There are half or full page scanner. 4.4.Digital Camera - It can manipulate, save, delete, and rotate the images. It sends as digitals input files to the computer. 4.5. OMR, MICR, OCR, Bar Code Reader a. Optical Mark Reader (OMR): OMR is also called mark sensing, which is a technology. It can sense the presence or absence of the pencil mark. OMR is used in the aptitude texts. b. Optical character Reader (OCR): It reads the page of text and converts images into ASC II codes to store into the computer. In the future it can print ditto for the user. All OCR system includes an optical scanner. It enables to take a book and save into a computer file. c. Bar code Reader: Bar code reader is a photoelectric scanner that reads the bar code (Vertical Zebra Striped marks,) printed on the product. In the supermarket, you can find bar codes in ever items. d.Magnetic ink character Reader (MICR): MICR is direct entry method used in the banks. It is a special type of input device used in ATM. 4.6. Speech Input Devices: It is a type of device that allow a person to input data to a computer system by speaking to it. 4.7. Touch Screen, Touch Pad a. Touch Screen: - It is a type of display screen that has the touch sensitive transparent panel covering the screen. As a mouse pointer, you can use your finger on screen. b. Touch Pad: - On a portable PC you can find a small touch pad where you can use your finger along the pad. 19 4.8. Light Pen, Digitizing tablet a. Light Pen: - It is special pen, which uses light sensitive defector too select object on the screen display. This pen is also similar to mouse. b. Digitizing tablet It is an electronic tablet. A stylus pen is used here to draw pictures and to operate computer. They are called touch tablet 5. Output Devices: There are two types of output device Soft- copy Output and Hard-copy Output device. Monitor and printer are the major soft-copy and hard-copy output device. A) Monitor and Its Types The classification of monitor is as follows: (a) Color wise (b) Signal wise (c) Design wise (i) colored monitor (ii) Monochrome monitor (i) Digital monitor (ii) Analog monitor (i) Box type monitor (CRT): Cathode -ray-tube (ii) Flat type monitors (LCD): Liquid Crystal Display a. Characteristics, Size, Bandwidth of a Monitor:i) Size = 14", 15", 17", 24" ii) Resolution= how densely pixels are packed? For example:VGA monitor = 640x480 pixels = 300,000 pixels SVA monitor = 1024x 768 pixels = 800,000 pixels Colored monitor = 24 bits per pixels = 16 million color High and monitor = 1600x1200 pixels = 2,000,000 pixels B) Printer and its Types: The most common output device for producing hard-copy output is a printer. They can also classified as a. Impact printer: uses letter headed hammer, ink ribbon, paper : Dot matrix & Line printer, Drum, Chain /Band printer b. Non- impact printer- Ink-jet, Laser, LCD printer, Thermal printer i) Ink jet printer- Ionized ink spray, qualify print, diff. fonts. ii) Laser printer - Utilizes a laser beam to produce image on the drum. 1200-2400 dpi quality. iii) LCD & Led printer - Uses liquid crystal to produce image. Uses light emitting diodes produce image. iv) Line printers - It is a high speed printer 3000 lines/min. It can print only font. No pictures. v) Thermal printer - Produces images by trashing electrically heated pins against special paper. vi) Plotters - It draws only pictures using pen with continuous lines. Multi color plotters use different colored pens. They are used in the engineering applications. vii) Sound cards & speakers - Sound card is compulsory in the modem computers where speakers are used. Sound card enables the computer to output sound, to record input from a microphone connected to the computer and manipulate sound stored on a disk. Sound card translate digital data into analog sounds. 20 6. Computer Software: 6.1 Introduction, Software is the computer program. A program is the set of logical instructions given to a computer to perform a certain task. All the logical components and the programs are called the software. So software is an instruction that given to the computer. Computer software means instructions or data, which are electronically stored on the storage device. Software is mainly classified into two types. A) System software: The software required executing users program is known as system software. It helps to improve the interface between the user and the computer. It includes operating system and utilities software that enables computer to functions. Computer cannot be operated without system software. The system software includes; - Operating system - Language processors (assemblers, compilers, debugged) and - Utility programs B) Application software: The software, which is used to perform specific job, is called application software. This software is available for applications, which are common to many users and organizations. It includes programs, which do real job for the user. An application program is a computer program which installed on computers to give users ability to do specific task. For examples word processing, spreadsheet, DBMS and other end user made programs. There various types of application software/program. i) Operating System (OS):- It is a must to run a computer. OS performs basic tasks like recognizing impact from keyboard, sending output to display screen, keeping tracks o files and directories on 21 the disk. Most commonly used OS are MS-Windows, DOS, XENIX, Mac OS, OS/2, UNIX, MVS etc. There are single user and multi-user operating systems. ii) Language processors: the program translated by the language processor is understood by the hardware of the computer. It translates the program written in a programming language into an executable program. These are Compilers: Compiler is a program which converts source code into object code after looking whole part of the source code all at a time. Interpreters: Interpreter is a program which converts source code into object code line by line. The advantage of the interpreters is that they can execute a program immediately. Some time compiler and interpreters are called language translator programs. Debugged: Debugged is a program which helps to find the error/mistake to the program when the source code or program is compiling or execute by the compiler. iii) Utilities: - the software that provides additional facilities to the user is called utility program. It performs very specific tasks, usually related to managing disk drives, printers and other devices, sorting or margin is done. A call up programs by OS. Transferring data from one I/O devices to another. Disk repair, data copy, data move, virus scan etc are utility program Some examples of application software/ package: i) Word processing: - Creating, editing, formatting, previewing coloring line text, designing, tabulating saving, deleting and coping line text. Users do disk top publishing using it. ii) Spreadsheet: - Creating, editing, formatting line mathematical tables in rows and columns. Using arithmetical, algebraically, statistical, logical and graphical text documents. Users are the facilities here. iii) Database Management System (DBMS):- It is a collection of record programs. Inserting, deleting, copying, updating and saving the records are the facilities here. iv) Image processing: - It is a set of programs, which performs graphical pictures and animations. It has different facilities like enlarging rotating, coloring, zooming and many more. v) Engineering Designing Software: - CAL, CAI, CAD, etc. Computer Aided Designing (CAD) is a set o programs, which performs engineering calculations, picture designs, simulations and others. vi) Accounting software: - It helps to solve the problems of the accountant. It is use to account keeping properly having many facilities. Accounting package, Repackage and Tally are the examples of the accounting software. vii) Statistical software: - It is a collection of programs which performs the statistical activities. It is a kind of powerful statistical tool. SPSS and microstate are the good examples. viii) Any other tailor made software: - Locally made any type of software for any type of local institutes. C) Human ware:22 i. ii. iii. iv. v. vi. vii. viii. ix. x. xi. xii. xiii. xiv. To run above computer hardware and software and the whole computer system in the big organization, the different types of the technical personals are needed. Their types and post names are as given below. It is called human ware. Data Entry Operator - Non officer Data Coder - Non officer Data Supervisor - Non officer Data Administrator - Officer Programmer - Officer System Analyst - Officer System Designer - Officer Computer System Engineer - Officer Hardware Engineer - Officer Maintenance Engineer - Officer Networking Engineer - Officer Computer Operator - Non officer Computer Instructor - Officer Computer Consultants - Officer 6. Operating System(OS): 7.1. Introduction OS Operating System is the base program on a computer. It tells the computer how to work or operate. The operating system also allows us to load other programs that do specialized tasks on to our computer. It is an organized set of programs that control the overall operation of the computer system. It can interact between the computer hardware and software, and the user. The operating system is the core software component of our computer. It performs many functions and is, in very basic term, and interface between computer and the outside world. In the section about hardware, a computer is described as consisting of several component parts including monitor, keyboard, mouse, and other parts. The operating system provides an interface to these parts using what is referred to as “drivers”. This is why sometimes when you install a new printer or other piece of hardware, your system will ask you to install more software called a driver. 7.2. What does a driver do? A driver is a specially written program which understands the operation of the device it interfaces to, such as printer, video card sound card or CD ROM drive. It translates commands from the operating system or user into commands understood by the component computer part it interfaces with. It also translates responses from the component computer part back to responses that can be understood by the operating system, application program, or user. The below diagram gives a graphical depiction of the interfaces between the operating system and the computer component; 23 7.3. Functions Of The OS i) Job Management– To keep processing jobs in sequence, determining main memory, secondary storage capability and their timing. ii) Batch Processing -Any big jobs are classified and grouped in some order, Batch wise they can be processed. For example number wise or alphabetical wise or VDC wise or district wise, etc. iii) Data Management – Data can be edited, updated and saved in any storage device. It can be retrieved and stored at any time any data. iv) Virtual Storage – Some OS have a feature called virtual storage. Such OS can increase the capacity of the main memory without increasing its size, during processing time, when it is necessary. v) I/O Management – For the smooth input data flow to the CPU and output data flow from the CPU, it can manage. In the big computer system also OS can handle very carefully and accurately. It can stop to handle the data to the unauthorized persons, so it can save data from the less. 7.4. Classification of the OS: Classifications of the OS are as follows i) Multi user: - Any OS, at the same time if more than user can use the OS that is called multi user OS. Some OS permits hundreds or thousands o your to use concurrently. The OS called MVS for the main frame and UNIX for the minicomputer are the multi user OS. ii) Multi processing: - Multi processing OS permits many users to use different programs at the same time. MVS and UNIX are two examples used as multi processing OS. Multi processing OS is more complicated than single process systems. Multi processing also refers to the utilizing of multiple CPU in a single computer system called parallel processing. iii) Multi tasking:- Multi tasking permits more than one program to run currently. In multi tasking, only one CPU is involved, but it switches from one program to another so that it gives the appearance. Executing all the programs concurrently. There are two types of multi tasking i) Preemptive - CPU time slices to each program. 24 ii) Co-operative - Each program controls CPU as needed. If the program is not using CPU, however, it can allow another program to us it temporally. OS/2, Windows 95, Windows NT, Amiga and UNIX use preemptive multi tasking. But MS-Windows 3.x and the Multi Finder use co-operative multitasking. iv) Multi threading:- Multi threading allows different parts of a single program to run currently. If is a ability of an operating system to execute different parts of a program called threads simultaneously, without interfering with each other. v) Real time:- Real time system is an interactive processing system with severe time limitation. Several stations (PC's) can operate a database at the same time. The central input file are updated each time and inquires are answered correctly. Hotel reservation, Air lines ticket reservation and Car rental are the examples of real time system. But DOS and UNIX is not the examples real time system. 7. Programming Languages: 7.1. Introduction The language which is used to expressed algorithm in computer understandable form or to make a program in computer is called programming language. In brief Programming language means a computer language. The broad classifications of programming languages are Machine Language, Assembly Language, and High-Level Language. 7.2. Machine Language: The language which is written as strings of binary 1s and 0s.It understood by the computer without using a translator. This is basically based at binary system like (On/OF), (Yes/No), (True/False), (Right/ wrong) and (1,0) etc. About 50/60 years back, the computers like ENIAC had used the language only by many switches ON/OFF. There were about 6000 switches for a single program. For the next program the switches had to reset. A process that might take weeks. Thus the programming were like 11110101, 11010011 00011010 etc. This was very tedious such language is called machine language. Note: Machine language is also kwon as 1st generation language. 7.3. Assembly Language: The language that using alphanumeric mnemonic codes instead of numeric codes for the instructions in the instruction set e.g using ADD instead of 1110(binary) or 14(decimal) for instruction to add. To reduce programming complexity and provide some standardization, assembly languages were developed in 1950. It is known as assembly or symbolic language use abbreviation or mnemonic code like. PACK 210(8, 13), O2B (4, 7) When we provide such assembly language command to the compute, it converts into machine language then it performs the job. Note: 1. Assembly language is also kwon as 2nd generation language. 2. The Machine language and assembly language are known as low-level language. 7.4. High-Level Language: 25 The language which is similar to broken English language and independent to the machine language is called High-Level language. In this language the programmer need not know anything about the internal structure of computer on which high-level language program will be execute. It is written in high-level coding or writing instructions by using English words and familiar mathematical symbol and expression. COBOL, C, C++, C#, Pascal, FORTRAN are some examples of high level language. Note: High level language are classified as third, fourth and fifth generation language. 7.4.1. Types of High-Level Language: a) Procedural – oriented - 3rd generation computer language th b) Problem- oriented - 4 generation computer language c) Nature - 5th generation computer language a) Procedural-oriented language: - General-purpose programming language like BASIC, PASCAL, COBOL and FOTRAN are called procedural-oriented language. They are designed to express the logic and procedure of the problem. All of them are called high level programming language or third generation language. Advantages of the procedural oriented language i) ii) iii) iv) v) Program statements are very similarly to English language Very easy to write program. Less time consuming to write program. Easier to understand and edit. The programming languages are machine independents. Disadvantages i) Program takes long time to execute. ii) The programming language does not look active. a) Problem oriented language:- The fourth generation languages are called problem oriented language. They are high level language, which are used designed to solve specific problems like word processing, spreadsheet, database management system package program, etc. The fourth generation languages also are used to develop application tools as follows. i. Personal computer application software ii. Query language and report generator iii. Design support systems and financial planning language iv. Application generators. i) Personal computer application software: It means word processor, spreadsheet, DBMS, graphics, integrated packages, PowerPoint and other tailor-made ii) Query language and report generator: It means query language allows people who are non programmer to search database using certain selection commands. For example, Airlines ticket reservation, Room booking in hostel, MIS, School information system etc. 26 Report generators are designed for people needing to prepare their reports easily, e.g.-QBE, SQL, HAL, Answer/Database, Data retrieve etc. iii) Design support systems and financial planning language: Decision support system (DSS) is made for managers or chief Execution officers to take decisions. Financial planning languages are also a kind of decision support system, that are employed or mathematical statistical and forecasting procedures. Example: - Macro Stat, SPSS, Accounting packages, Metaphor, STRATAGEM, etc. iii) Application generators: Application generators are a collection of set of program modules, preprogrammed for different jobs. A non programmer uses this required report. Example the user inters his pass word and unique account code numbers, presenters as in ATM machine to get money. There are other examples of application generators as: FOCUS, FUSION, SAS, SYSTEM, LINE II, RADID/3000 etc. Different between 3GLs and 4GLs. S.N o 1. 2. 3. 4. 5. 6. 7. 8. 9. Third-generation language Fourth generation language Use by programmer. Requires specification of how to perform task. All alternatives must be specified Requires large number of procedural instructions. Code is difficult to read, understand and maintain. Language for batch operation. Difficult to learn. Difficult to debug. Typically file oriented. Use by non-programmer. Requires specification of what task is to be performs. Default alternatives are built in. Requires few instructions. Code is easy to understand because of English-like commands. Language developed for on-line use. Easy to learn. Easy to debug. Typically database oriented. v) Natural Languages: There are still in developing stage. They will be using in AI and expert systems. They have two characteristics. i) More human like speaking ii) More smarter with remembering capacity. There popular natural languages are LISP and PROLOG. 7.4.2.Assembler, Translators, Complier, Interpreters, Linker : A. Assembler A computer program that translates an assembly language program to its machine language equivalent is called assembler. B. Translator 27 i. High level programming language to work on the computer it must be translated into machine language. There are two types of translators like. Compiler: A translator program (software package) that translates a high-level language program into its equivalent machine language program is called compiler. In brief it reads whole program and converts it into machine language. Complier translates the whole program into machine language all at a time. The translation processor is called compilation. The programmer’s program is called source code but its machine language code is called object code. ii. Interpreters: A language processor that translates a statement of high-level language, and immediately executes it before translating the next source language statement is called interpreter. In brief it reads a line and converts into machine language; one statement at a time. Interpreters translate each program statement into machine code just before the program statement is to be executed. This process continues till whole process completes. But compiler language is better than interpreted language as they can be executed later. Complier is used in COBOL, C, C++ and FORTRAN. On the other hand interpreter language in BASIC programming. Interpreter do not need object code and so usually easier to develop. (i.e. to code &test). Thus, there are code complier, C compiler and BASIC Interpreter. C. Linker: A program that is used to properly combine all objects program files (modules) of a software, and to convert them into software’s final executable form is called linker. The Compilation Process: Source files are complied into object files, then through linkers object files using routine libraries it produces executable programs. Thus object codes pass through linkers. The linker combines modules and gives real values to all symbolic address. Hence, the linker translates object files into executables program files. 8. General Software Features &Trends: 9.1 Introduction We know the series of instructions that performs a particular task in the computer is called a program. There are two categories of programs like system software and application software. 28 A system software means combination of operating system, control program, database management and communication software. An application, software means any program that processes the data for the user. In short, the software tells hardware how to process the data. At present, in the world software projects are becoming more and more complex in size, sophistication, and technologies used. Now most software products manage to millions of users in different shape and size. For example word processors, ERP packages and SCM tools, which run mainframes and client server systems; different versions of web browsers for the PC and MAC; we have DBMS that run on MVS, UNIX, Windows NT, Linux and so on. The competition and the advancements in technology are driving software. Now computer and communication are becoming integral part of our lives. The driving force behind all these advancement is the computer software. They are becoming more and more complex. For example, the software is being used in controlling satellites, operating. Intercontinental, Ballistic Missiles, running banks, hospitals, airlines, hostels, etc, including door locking system and robotics. Software may communicate via internet, using e-mail or videoconferencing technologies. Thus its development is in advance and changing very fast. Now the general software features are given below. i) Easy to Use: Presently, most of the software companies are producing more and more user’s friendly, software's. The software developers are developing the software’s including facilities like user's interface, displaying error message, self leaning type etc. Thus software are becoming easier to use, ii) Graphical User Interface (GUI): Now-a-days interface, most of the software applications are graphical user interface (GUI) brand. That is software's are self learning type, which are very easier to use. In the software, there will be self guided dialog box. Most of the tasks could be performed by mouse click. This almost software guided uses using icons, dialog boxes and other graphical elements. iii) More Features: In order to service the software companies they have to be constantly innovative and be always ahead of the competition. So they are producing better producers for the end-users. That means new software will be coded by more features at affordable price. Micro-soft companies products could be the good examples for the more features in the new products every year. iv) Requirement Of The Powerful Hardware: As you know, as the facilities are increasing in the software, it wants more and more advanced computers. About 10 years back there were 386 types of machines which can run only Windows95. Now-a-days users are running Windows XP on Pentium IV computers. Hence the new software wants more and more powerful computers. Otherwise the new software will not be able to run. v) Multi-Platform Capability: 29 Now-a-days, most of the application software supports multiplatform both hardware and software platforms. There are software applications that support hardware platforms from PCs to mainframe and different software platforms like windows to UNIX, AIX, Solaris and MVS. Similarly other important feature of today's application software is that they support in many languages like Japanese, Arabic, Chinese and English. Likewise they support different national currencies too. vi) Network Capabilities: As the popularity of computers network increase, the demand of software that can run on the computers connected on the network are increasing. The idea behind network computers is that many users who are connected to a network do not need all the computer power they get from a typical personal computer. Instead they can rely on the power of network server. vii) Compatibility With Other Software: There are many software companies in the world market. Software vendors are battling for the market share. It means that the users will get better products. To make salable software, vendors are making their software compatible with other competitors. For example, you can import WordPerfect documents, text documents, and HTML documents and so on into a MS-word document. Almost all vendors practice this technique to stay and service in the business. Similarly, most of the vendors maintain compatibility with easier version, as they release the new version. For example Ms-word 2000 supports all previous versions words, word97, and word95. viii) Object Linking And Embedding: While you are working in MS-word, you can open and link MS-Excel. If you want you can import a table and a graphical picture from MS-Excel to your word document. To call a table and a picture from external software to the running software is called linked and embedded object. Thus Micro soft company has developed a method to integrate external tool into an application using the Object Linking and Embedding (OLE) architecture. Now OLE is a compound document. If enables you to create objects with one application and then link or embed them in a second application changes made to the embedded object effort only the document that contents it. Support for OLE is built into the Windows and Macintosh Operating System. This embedding and linking of components enables applications to share components. ix) Group Work Capabilities: To work in a group using computer terminals sharing files, software tools and facilities of the common file server are called group-ware and work flow automation. In another word groupware is an umbrella term describing the electronic technologies that support person-to-person collaboration. Groupware includes Email, Electronic Meeting System (EMS), Desktop Video Conferencing (DVC) as well as systems for work flow and Business Process Reengineering (BPR). To-day software vendors are integrating collaboration technologies into their products. Groupware maximizes human interaction while minimizing technologies interference. The term 'Groupware' and ‘Collaborative Computing' are often used interchangeably when in fact they are different. Groupware is basically a subset of 30 collaborative computing. Collaborative computing refers to the technology that is hardware, software and structures that support group working. x) Mail Enabling: As you know windows program has a "Send" command and windows 2000 has a "Send to" command in its "File Menu". If you choose and click on "Send to" command of File Menu you will find mail recipient menu, Fax recipient, etc. When you click on mail recipient, then the document will be sent as an attachment using your default e-mail client to the address you specify. This is the new facilities added to the application software. This is an example of the advanced and more sophisticated mail enabled applications software. Mail enabled applications are designed to capitalize on e-mail. xi) Web Enabling: As you know to-day most of the information are available in the internet. Therefore software vendors are adding the facilities into their product to link the internet and down load the required information. Most software applications are now web-enabled. During installation, most of the applications will automatically connect to the internet and to the vender's web site and will register their products. For example, Word 2000 can now connect to the Microsoft's website and get clipart new images if the user wants to put in his computer, thus the options available to the user are more now. In the future also they will have more and more web enabling facilities in the new software. . 9. 9.1. Data Processing: Introduction, The Data is a collection of facts or observations in unorganized form but able to be organized into useful information. It may be any words, numerical numbers, codes or any mixture of numerical numbers and alphabets. It could be voice, text, images or any numeric data too. Data means a file of records of raw facts. Record means a set of fields. Data processing means the processing of data to make it more usable and meaningful information. It means to collect, manipulate and organize the data in a logical order. It analyzed, evaluated and placed it into a proper order for the end user. Thus the raw data is manipulated by calculating, sorting, comparing, classifying and summarizing to convert into the required information. Data processing is a series of actions or operations that convert data into useful information .It include resource such as people, procedures, and devices used to process input data for producing desirable output. 9.2. Data Versus Information, Data is a collection of facts or instruction received from input device of the in raw form and the information means the refinement of data after proper processing and organization .In fact anything which is received/accept from input device of the computer is called data and after suitable processing and organization it becomes information. These are relative terms also any information will become data for another purpose or another task. Information in one purpose becomes data for another purpose. For example the result of +2 level is a information for those student who appear in the board examination but this will 31 become data for those person/researcher who want to analyze this result for the improvement of examination system in this level 9.3. Standard Method of Organizing Data There are two standard methods of organizing data: a) File –Oriented Method /File Management Method b) Database–Oriented Method /Database Management Method a. File –Oriented Method /File Management Method: - After collection data, it is kept in separate files. Collected data is organized into one or more files and application program processes them to generate the desired output. This process is called file management or file oriented method. A file management system supports following file types i. Transaction file: Store input data until it can be processed. ii. Master file: Contains all current data relevant to an application. iii. Output file:Stores output produced by one program that is used as input to another program. iv. Report file:Holds a copy of a report generated by an application. v. Backup file:Copy of a file, created as a safety precaution against lost of data. The method of keeping file also divided into two categories like sequential and direct access. i) Sequential Method: The collected data are stored one after another in ascending or descending order determined by the value of the key field of the records. The tape is in a sequence order. If such data is managed in this method that is called sequential data management or sequential file method. Some time there will be group wise data collection (batch wise e.g. district wise or date wise or others) in the different files. Those data files will be merged into a file. Then the master file will be sorted in some sequence and lastly processed it. This type of processing is called sequential file processing. ii) Direct- Access Method: - The data can have direct access in a file stored in a tape. But except tape it has direct access into the data stored floppy disk, hard disk or compact disk (CD).For the direct access file management, the data file must be organized for the direct access that means the data file must be created in the floppy or hard disk or CD with some unique codes or index numbers. b. Database–Oriented Method /Database Management Method: A database means a self describing collection of integrated records. Most of the databases contain a directory of its contents. It can contain multiple related files. A file means a collection of records. A record consists of different fields. User defines data fields and makes entry of fields into records. Then they combine records to a file. Now users can manipulate and retrieve stored data in database in various ways to prepare reports and collect certain desired information arranged in some order. The database-oriented method facilitates data from multiple related files are integrated together to form a database: It provides greater query flexibility It reduce data redundancy It solve data integrity (inconsistency) problem It makes data independent of the application programs It includes data security features at database level, record level, and field level. The data of one file is related to the data of another file through the use of common field. The database management packages have also data manipulating and data analyzing capability. It can also produce graphs from data in the database. All these activities are called database management. 32 A number of database management packages are available such as dBASE, ORACLE, UNIFY, FOXBASE, SAYBASE and INFORMIX, etc. In database processing the database management system (DBMS) acts as an intermediary between user and the database. 10. Database Management System: 10.1. Introduction Information is the most important resource of the organization or knowledge. It helps managers to make right decision for the future planning of the organization. Data, images, texts, documents and voice can be an input data to convert into information. The user receives the information and then makes a decision and takes an action. Information is power. 10.2. Quality Of Information: In any aspect the quality of information must be maintained. That means, the information must be accurate, timely and relevant. I. Accuracy: Accuracy of information means error free information. II. Time Lines: Timelines means that the user can get the information when they need it. In fact it is prompt. III. Relevancy: Relevancy means the use of a piece of information for a particular person. It is very subjective and personal matter. Information relevant for a one person may not be relevant or useful for another. 10.3. Database An organization of data in usable form to the user is called database. In other word a database is an organized collection of related information about particular subject or purpose. For example, to create a database of a library it is designed in such a fashion that the user can find out the price wise, edition wise, author wise or publication wise etc. at any time. In computer a database is also like a box containing index cards. The only difference is that instead of index cards, a computer database is filled with records. While each index cards in a box contains information’s written in many lines, a record in a database contains all the information related to an item in just one line. Information in a database is stored in rows (records) and columns (fields) in a sequence of unique number. 10.4. Database Management System In database–oriented approach of organizing data, a set of programs is provided to facilitate users in organizing, creating, deleting updating, and manipulating data in a database all these programs together form a Database Management System (DBMS).In another words DBMS is a set of programs or software which provides services for accessing a database, while maintaining all the required features of the data. Hence DBMS is software that creates, manages, protects, and provides access to a database. Some of the major services of a DBMS are as given below. (i) Transaction Management A transaction of data means creating, updating, deleting one record or modifying a set of records in sequence. Similarly transaction processing means daily processing of records in sequence. For example any accountant officer users computer for entering new records steps by steps and processor it accordingly (ii) Security Management DBMS can make sure that only authorized users are given access to the data in the database. This is called the security management or a protection of a database from the unauthorized persons. (iii) Recovery Management 33 Recovery management is a facility used in the DBMS. Recovery mechanisms in a DBMS make sure that the database is returned to a consistent state after a transaction fails or aborts. For example a DBMS, if a record is incomplete or damaged the program skips it and does process again during processing time. (iv) Programming Interface The DBMS provides support programming languages used for the definition and manipulation of the data in the database. The data structures are created using the data definition language commands. The data manipulation is done using the data manipulation command. This is the example of language interface management of the DBMS. (v) Concurrency Control/management Concurrency management means co-coordinating the actions of database manipulations concurrently in the shared data during data processing. For example if one user manipulates a record, the effect is distributed in the other shared records too. (vi) Storage Manager The DBMS provides a facility of permanently storing of the data. The storage manager interfaces with the operating system to access the physical storage. The internal schema defines how the data should be stored by the storage management mechanism. (vii) Data Catalogs In any type of DBMS there is a data catalog system. Data catalog or Data Dictionary is a system database that contains the descriptions of data in the database. It contains information about data, relationship, constrains and the entire schema that organize these features into a unified database. (viii) Application Services provided by a DBMS 10.5. Why DBMS? A DBMS provides a secure and survivable medium for the permanent storage and retrieval of data. It can provide many facilities like transaction processing, programming interface, security management, recovery management, concurrency management and storage management, etc. DBMS is very easy to use, access and manipulate the data in the database. As we know, database is an organized collection of related data. It is an integrated collection of records which contains different fields like name, address and telephone number. The telephone directory could be a simple 34 example to answer this question. The user Mr. A can use this database for finding telephone number of a particular person or Mr. B can use it for finding a person’s name of a particular telephone number and third user Mr. C can use the same diary to find a list of similar names and their telephone numbers within the same city code. Thus a telephone diary (a database) could be used in three ways or more. Therefore the database is created to fulfill user’s need for different purpose. Similarly from a database of a library file, the user can find the list of books like edition wise, publisher wise, subject wise, or writer wise etc. But to find these four lists, the user must needs to process the database four times. Therefore, to run a database there must be software and a system to arrange the records within the database. Such system software is called database management system (DBMS). Without this software, if somebody creates the database, there will be many problems during the database preparation. The problems may be as follows until a final database is prepared. Types of problems in creating a database: (i) (ii) (iii) (iv) (v) (vi) (vi) Data repetition Data inconsistency Data security to maintain Wrong coding within the range Wrongly entered data Data sharing may not be possible Data lost etc. At last, the user prepares a final error free and clean database after facing all the above mentioned problems. Then the characters of the data in a database should be as follows. I. Shared - Among different users, the data in a database can be shared. II. Security - The data of the database is totally secured from the unauthorized persons. III. Consistency - The data of the database is maintained the consistency. IV. Validity/ Correctness - The data of the database is error free. Using all the methods all the errors is already deleted. 10.6. Type Of Database Management System: There are five types of the database management system like (i) Hierarchical (ii) Network (iii) Relational (iv) Object oriented and (v) Deductive. These are the five DBMS models, which are running in the world markets at present. i) Hierarchical Hierarchical Model is running since 1950 AD. It is an oldest DBMS Model. It assumes that a tree structure is the most frequently occurring relationship. This assumption is recognized today a misleading. For example, hierarchical model is similar to company’s organizational structure. At the top we have GM. Under him there are 2, 3 deputy general managers (DGM). Just below DGM there are 6,7 department heads and so-on. Here the row position implies the relationship to each other from top to bottom. It looks like a tree structure. ii) Network To-day, the hierarchical model is replaced by Network model. The Network model can be used in a book distributor as an example. A book can have many attributes like Title, Author, Publisher, Year of publication, distributor, cost etc. Similarly on the other hand, a distributor can have attributes like Name, Contact address, Discount and others. We can use these both examples in the network model. iii) Relational Model A relational database organizes data in a table format consisting or related rows and columns. Each location in a table contains a single piece of data, known as data item. Each column of a table represents a field, which consists of data items. A full set of data in any given row is called a record. The whole related records makeup a 35 file. In a relational database a file is also called a relation. The relational model uses the rows and columns of tables to organize the data elements. The relational model is currently the most popular database mode. iv) Object oriented v) Deductive 11. Introduction To Telecommunication 11.1. Introduction The transmission of data to the long range through different media (web, cable, satellite, etc) is known as telecommunication. It refers to all types of data transmission. It may be sound, video, text; etc whatever may be that is acceptable to sender (transmitter) and receiver. 11.2. Analog & Digital Signals The data are transmitted either in analog or digital form .An analog form means the electrical signals that propagate (transmit ) in the form of continuous wave or graph is called analog signal. The data which transmit by means of discrete representation or numerical representation is called digital signals. Most of the analog signal can be simulated digitally and digital signal are in analog signal. 11.3. Modulation To carry the audio signals, a high frequency carrier wave is used .The process of changing some characteristics (amplitude, frequency or phase) of carrier wave in accordance with the intensity of the signal is known as modulation. In brief modulation means to change; In modulation some characteristics of the carrier wave are changed in accordance with the intensity (amplitude) of the signals. The resultant wave is called the modulation wave or radio wave and contains the audio signals. Therefore, modulation permits the transmission to occur at high frequencies where it simultaneously allows the carrier of the audio signals. 11.4. Types of Modulation The modulation is process of changing of amplifier or frequency. There are three types of modulation. A. Amplitude modulation (AM) When the amplitude of the high frequency carries wave is changed in accordance with intensifies of the signal, it is called amplitude modulation (AM). In the case of amplitude modulation A. The amplitude of the carrier wave changes according to the intensify of the signal B. The amplitude variation of the carrier wave is at the single frequency. C. The frequency of the amplitude modulated wave remains the same carrier frequency. B. Frequency Modulation(FM) When the frequency of the carrier wave is changed in accordance with the intensity of the signal, it is called Frequency Modulation .In frequency modulation, only the frequency of the carrier wave is changed. However the amplitude of the modulation wave remains the same. The frequency modulation has following properties: 36 A. It produces noiseless reception. Noise is a form of amplitude vibrations and FM receivers reject such signals. B. Opening range is quite large. C. It gives high fidelity reception. D. The efficiency of transmission is very high. C. Phase Modulation (PM) Phase modulation is changed in the carrier phase angle .The Phase cannot change without effecting the change in frequency. Therefore phase modulation is in reality a second form of frequency modulation. 12. Computer Network 12.1. Introduction A chain of interconnecting two or more the two computer for transmission of data and is known as computer network. A network is a way to connect computers for communication, data exchange and resource sharing. We can see in the computer networking in business organization like bank, shopping center, corporate office, academic institution, etc. The main purpose of computer networking is to share data to each other. If there is main or master computer which share the data to other computers then this computer known as server and client or node to the rest computer. 12.2. Overview Of Network In general a communication network means any arrangement, where a sender transmits a message to a reviver over a channel consisting of some types of medium. It maybe in office room, one building, local area or wide range. For communication network we need five basic components as follows. i. Computer ii. Communication channel or media iii. Communication processor iv. Communication software v. Terminals 12.3. Communication Media The media over which, data are transmitted and received are called communication channels. In other words the media or channels that are used to transmit data is said to be communication media. For telecommunication there are different types of channels or media such as copper wire, co-axial cables, fiber optical cable, micro wave system and communication satellite system to inter connect to other devices of a network. 12.4. Communication Processor The device which helps to transmit and received data between terminals is called communication processor. In other words it is a processing unit that coordinates network and data communication. Within a computer network, it ensures that data flows to and from different computer systems correctly and efficiently. 37 It is also a kind of simple CPU processor. It includes modem, message switchers, multiplexers, front-end processor. 12.5. Communication Software, The software that enables transfer of data and programs from one computer system to another in a network of computers. It is main part communication network .Communication software’s are store in the host computer in the front end computer s and other communication processor. In a large computer networks communication software package is called teleprocessing (TP). 12.6. Terminals Terminals means a set of computer including video display terminals and other end user work stations .Any Input/ Output device that uses a network to transmit or receive data is a terminals this includes micro computers, telephone fax machine ,etc. No matter how large and complex the real world networks may appear to be, the above five basic categories of component must be at work to support a network. 12.7. Types of Network There are mainly two types of networks. I. Local –Area Network (LAN) A computer network interconnecting computers and other peripheral devices within a limited geographical area is called local area network (LAN).They are in same room or floor or a same building etc. II. Wide –Area Network (WAN) A computer network interconnecting computers spread over a large geographical area is called wide area network (WAN).They are connected by telephone lines or radio waves; they are geographically apart, like in the different buildings, cities or countries. 12.8. Network Protocol A set of rules and procedure established to interconnect and communicate between computers is called network protocol. It provides the method for orderly and efficient exchange of data by establishing rules for proper interpretation of controls and data transmitted as raw bits and bytes. In other words a network protocols is a set of rules for the exchange of data between two or more than two computers. Protocols are handled by software related to the network. The international standards organization (ISO) based in Geneva Switzerland, has define a set of protocols called Open System Interconnection (OSI)model.OSI model has been endorsed by the United Nations. The protocols determine the following points. The type of error checking to be used. Data compression method ,if any How the sending device will indicate that it has finished sending a message. How the receiving device will indicate that it has received message. 38 The protocol can be implemented either in hardware or software. Some of the popular protocols are TCP/IP, HTTP, FTP, SMTP, POP, Token Ring, Ethernet, Modem, Kermit, MNP etc. These are the examples of the standard protocols. 12.9. Network Architecture. A method or system of communicating data to the computers in a networking system is called Network Architecture; that is how the data are sent and received in networking system .It is either peer to peer or client/ server architecture . I. Peer to peer Architecture The architecture in which all computers are in peer-to peer arrangement, they are in equal status, no one is in control is known as Peer to Peer Architecture. In this architecture each computer will distributes all files and peripheral devices facilities across several computers working in LAN. They share each other’s data and devices as and when needed. The main disadvantage is lack of speed in the most peer to peer networks system. This system slow down under heavy use of terminals. II. Client/server Architecture The architecture in which one computer serve as a master computer called server; it controls the networks and rest of the computer received and sent data to this computer called client or node is known as client/server architecture .in particular, a server has the hard disk holding shared files and often has the highest quality printers, which can be used by all the nodes. Under this architecture processing is usually done by the server and only the results are sent to the client or node .sometimes the server is called file server and the client is called workstation. Server is stronger the node/client. 12.10. Network Topology The structure of interconnecting of nodes of a computer networking is called network topology. It is the interconnection pattern of the network or geographical arrangements of a computer system .There are various types of networks. Some of them are a. Star Topology The networking topology in which one or more computers or peripheral devices are connected to the host computer or CPU is called star topology. In fact the each client /node is connected to the server in center it looks as a star so it is called star topology. This system is frequently used everywhere, in this system several users are able to share a control processor and time sharing system. b. Ring Topology The networking topology in which two or more than two computers are connected one to one in a simple and closed ring is called ring topology. In other words all the computers or nodes are connected in a closed loop. Message travel around a ring, with each node reading those messages addressed in it. Access and control of ring networks are typically maintained by a “token passing” system. c. Bus Topology The networking topology in which all client/nodes are connected in a single communication cable. In other words the data are passing through server to client is highway and each nodes are station of this topology. Access and control of bus networks are typically maintained by a method called CONTIENTION 13. Communication System: 39 13.1. INTRODUCTION Communication is the transmission of data from one computer to another, one place to another or from one device to another. A communication device, is any machine that assists data transmission. For example, Radio, TV, Satellites, etc are all communication device. 13.2. Radio and TV Radio A radio is a receiver, which contains an input circuit for tuning into the frequencies of different transmitters to be received, a demodulation circuits for separating audio frequencies from the high-frequency carrier waves, a low frequency amplifier stage, and a loud speaker. A radio contains a device to receive long waves 9150-285KHz), Medium waves (up to 1605 KHz), short waves (6-21.4MHz), and ultra-short waves (up to 100 MHz). Long, medium and short wave reception function with a channel spacing of 9 KHz and with amplitude modulation (AM). The channel spacing in the ultra-short wave range is 300 KHz, and in this range frequency modulation (FM) is employed. All the four waves are elector magnetite waves. The propagation conditions of the four radio wave ranges determine their possibilities of application and the purposes for which they are used. Television Television is a system of sending and receiving pictures and sound by means of electronic signals transmitted through wires and optical fibers or by electromagnetic radiation. These signals are usually broadcast from a central television station to reception devices in television sets in homes. The most common use of television is as a source of information and entertainment. Security personal use television to monitor buildings and facilities as also a cc TV. Doctors can check the interior of the human body with a microscopic television camera. Thus television is the world's most power form of communication. (i) How TV Works? The TV receives electrical signals, either through air, from broadcast stations or over cable or from CR. These signals are pulses of electrical energy that arrive in the wave. These waves can have many different shapes, and each shape can tell the TV something about what it is suppose to do A TV uses two kinds of waves AM (for Amplitude modulation i.e. for AM picture information) and FM (for frequency modulation i.e. for FM radio signals). FM signals can carry multiple audio channels- in this case two for stereo sound. AM waves, which are the same kind as the one use to carry radio signals, carry two picture information. AM can carry 30 pictures per second. The TV draws pictures by synchronizing the electron guns (which shoot the beams that light the screen) with the yoke, a circle of magnets that deflects the electron beam left and right, and up and down, across the screen. Together guns and yoke can draw pictures, by knowing what to draw and where to draw it. Another AM signal carries the color information. It tells the TV where to put the color. This signal actually consists of two signals on the same wave, separated by time. (ii) Transmission of Television Signals Cable television was first developed in the late 1940s to serve people. Viewers in most areas can now subscribe to cable television services. Network television stations use microwave relay stations to broad case to affiant's communication satellites also receive television signals from a ground station and relay them back to specific area. Satellite transmissions are used to efficiently distribute television and radio programs from one geographic location to another. In addition, direct-broadcast satellites deliver television programming directly to individual receivers through small home dishes. 13.3. Microwave System 40 Microwave transmission uses what is called line of sight transmission of data signals through the atmosphere rather than through wire. Microwave transmission consists of high frequency waves (10003000MHz) that travel in a straight line. Since these signals cannot bend around the curvature of the earth, 30KM 30KM relay stations-often antennas in high places such as tops of the mountains and buildings are position at points approximately 30 km apart to continue the transmission. Microwave transmission offers speed, cost effectiveness, and ease of implementation when one tower receives the signals, it amplifies the signal and sends it to the next tower. Unfortunately, in major metropolitan area tall buildings may interfere with microwave transmission. Fig Microwave Transmission Communication satellites in space, orbiting in the Clarke orbit are also used as microwave relay stations because they rotate at the preside point and speed above the equator, that makes them appear stationary to the microwave transmitters on the ground. Microwave systems have the capacity to carry large quantities of data, both digital and analog at high rates of speed. They are used for the transmission of television and telephones signals. 13.4. Communication Satellites Satellites have now become an integral part of the world communications systems. (For example, Radio, TV, Fax, Telephone, e-Mail, Internet, Intranet, Extranet, etc.). The basic components of satellite communication are earth stations, which sends and receive signals and a satellite components called a transponder. The transponder receives the transmission from an earth station, amplifies the signal, changes the frequency, and re-transmits the data to receiving earth stations. The satellite is nothing more than a radiorelay station. One of the most important events in the history of satellite communication took place when COMSAT or communications satellite corporation, lunched four satellites within 6 years that is between 1965 to 1970. The first of these series was the "Early Bird", which was launched in 1965. This was the first communications station to handle worldwide commercial telephone traffic from a fixed position in space. The next series, INTELSAT was a group of satellites that served 150 stations on 80 countries. (i)The satellite Orbit: The communication satellites are placed in orbits called EQVATORIAL GEOSYNCHRONOUS orbit. The satellite place in this orbit will appear stationary over a selected location on the earth's surface. So communication satellites are placed in an orbit that is directly over the equator, moving in a west-to-east 41 direction at an altitude of 22,282 mile above sea level and with a forward velocity of 6874 mph to couplet one orbit in 24 hours. This orbit is called the CLARKE ORBIT. (ii) Up-link and down-link: Up-link system includes all the ground equipments along with the transmission path and receiving antenna are the satellite. The down-link is described in terms of satellite transmitter output power, down-link antenna gain and beam width and ground area that the transmitted signal will cover the FOOT PRINT. (iii) Cross-link: At the altitude if the CLARKE ORBIT, one satellite could command a footprint area of 42.2% of the earth's surface. The beam width from the satellite for such coverage is 17.2 degree. Since such a satellite is not sufficient for global coverage, we need more than one (to be specific, 3) satellite. These 3 satellites are placed 120 degrees apart in CLARKE ORBIT and would cover the earth's entire surface except for the polar caps. Due to such arrangement of the 3 satellites, one can communicate form one part of the glob to the opposite side of it. As described below in the figure, the distance between two satellites is 45,458 miles. From this picture, it is clear that to travel one information from one part of the earth to its opposite part, it travels 90,014 miles (i.e earth-satellites A- satellite B- opposite of the earth). Fig: Cross-link connections for global coverage. INTELSAT was the first to set up such a communication link. With satellites spaced over the Indian, Atlantic and Pacific oceans above the equator. (iv) Component of a satellite: There are five major components in the satellite. They are as follows: a. The transponder. b. The antenna system. c. The power package. d. The control and information system. e. The rocket thruster system. The transponder is a high-frequency radio receiver, a frequency down-converter and a power amplifier, which is used to transmit the down-link signal. The antenna system contains and the mechanisms to position them correctly. Once properly in place, they will generally function trouble-free for the life of the satellite. The power package is the power supply to the satellite. The power is supplied to the satellites by the combination of battery power and solar energy. 42 The control and information system and the rocket thruster system are called the station keeping system. The function of the station keeping system is to keep the satellite in the correct orbit with the antennas pointed in the exact direction desired. 13.5. Radar and Fiber Optical RADAR The “RADAR” means the Radio Detecting and Ranging device. It devotes the method of scanning the surrounding space by means of high frequency radio waves, which are sent out from a powerful transmitter and are reflected by any object, which they encounter. The reflected beam is picked up by a receiver and its strength and direction gives information on the size, distance, altitude, etc of the object. For example, an observer in an aircraft wishes to survey by radar the terrain over, which he is flying. The observer is strikes out the radar beam from the aircraft on the ground. The radar beam scans a circular area in the form of a sector, which sweeps round and round. Depending on the nature of the reflecting objects the intensity of the reflected beam will very as shown in the following picture. The transmission and reception of the high frequency of radio waves are effected in the radar apparatus. The radar waves are generated in the transmitter, which is equipped with radio tube of special design. The transmitting antenna usually also functions as the receiving antenna. This process is called “periodic changeover”. The receiver picks up the beam in a cathode Ray Tube (CRT). The beam is so deflected that it scans the luminescent screen from the center to the edge. Fiber Optic Cable Fiber optic cable and laser technology allows huge amounts of data to be routinely transmitted at the speed of light through tiny threads of glass or plastic. Fiber optic cable, the size of a human hair can transmit 2 billion bits per sec. This is about ten times greater than co-axial cables and 200 times better than twisted-pair wired. It is a tiny glass pipe. The 'core' of a fiber optic cable is a very thin strand of highly refined cylindrical glass. The glass core of the cable may have a diameter as small as 4.5µm (2/10,000in) or as large as 400 µm. A second layer of glass called the 'clad' surrounds the core. Glass Protective covering Optical fiber Outer sheath 15. Fig: Fiber optical cable The clad has a different optical density form the core material. Fiber optics founded on the theory of reflection that results at the interface between two materials of different densities. They can conduct light pulses generated by laser at transmission of information with high speed as 2 billion bits per sec. Fiber optical cable can be used to transmit voice, data and video. (a) Advantages of a fiber optic system are: (i) The main ingredient in glass is sand, which is very cheap and available everywhere compare to copper and aluminum. (ii) Photon of light, rather than an electrical current move through the optic fiber. Therefore, there is no chance of spark flash. Hence the system is safer. (iii) Since the fiber optical system carries no electrical current; the energy transmitted through the fiber cannot radiate radio frequency interference, nor can it be contaminated by any external noise or radio frequency fields. 43 (iv)Because of absence of current flow through fiber, intrusion, into the system is also prevented. Confidential information cannot be routed to unwanted receivers, nor can false information be fed into the data stream. (v) The transmission losses of fiber optic cables are much lower than that of the twisted-pair wires and co-axial cables. (vi)Fiber optic cables provide substantial size and weight reduction as well as increased speed and grater carrying capacity. A half inch diameter fiber optic cable can carry up to 50,000 channels, compared to about 5,500 channels for a standard co-axial cable. (vii) Glass is immune to corrosive and oxide degradation and will stand up well in hostile environment. (viii) The size of the core and clad of a single fiber conductor is much smaller than the diameter of the common copper wire. Since fiber optic cables are not affected by and do not generate electromagnetic radiation. Therefore, multiple fibers can be placed in the same cable. (b) Disadvantages of the fiber optic systems are: (i) Use of fiber optical cable is limited. That is, they can be used only on point-to-point on the ground level. (ii) It cannot be used to the very low powered devices. (iii)The ways in which the light source can be modulated are limited. 15.8 Integrated Services Digital Network (ISDN): ISDN is a high speed, fully digital telephone service. ISDN upgrades to day’s analog telephone network to a digital system. ISDN can operate at speed up to 128 kilo bits/sec, which is 5 or more times faster than today’s analog modem. ISDN can dramatically speed up transfer of information over the Internet or over a remote LAN connection, especially rich media like graphics, audio or video or applications that normally run at LAN speeds. There are several types of ISDN service, but the most appropriate type for individual computer users, and the type that this site focuses on is the ISDN Basic Rate Interface (BRI). Most of the world’s existing telephone networks are already digital. The only part that typically is not digital is the section that runs from the local exchange to your house or office. ISDN makes that final by of the network digital. The original version of ISDN employs base band transmission. Another version, called B-ISDN, uses broad band transmission and is able to support transmission rates of 1.5 Mbps. B-ISDN requires fiber optic cables and is not widely available. (a) Why is ISDN so Important? More than just a means for fast, accurate, data transmission, ISDN truly represents the next generation of the world’s telephone service for all forms of telecommunication including voice. ISDN brings the digital network to the individual users. Thus, the same twisted-pair wire telephone line that could traditionally carry only voice or one computer or one fax “conversation” can now carry as many as three separate “conversation” at the same time through the same line. ISDN the “magic” that makes this happen. Thus at the same line and through same cable three separate “Conversions” like (i) a voice call (ii) a computer transmission, (iii) an e-mail massage or a credit card authorization for example, could also takes place through the same connection. 14. Internet and World Wide Web (Www). 14.1. Introduction Now you have the general idea about Tele-Communication and Networks. Based on these ideas, you can explain about the data transmission through LAN, MAN and WAN. Using telecommunication media now anybody can send and receive any type of data around the world within a minute. That is why many people 44 are talking and using about e-mail, e-banking, e-business, tele-teaching, telemedicine and chatting, etc. All these activities fall under Internet. At the beginning, Internet was called information super Highway in the mid 1990s. In fact, the network of networks globally connected to send and receive any type of information is called "Internet". In the world, US department of defense is the first user of the Internet. As the cold war ended at the beginning of the decade 1990s when the Soviet Union fell then the US vice president Mr. Algor announced Internet facilities can be used by any country as they wish. Any single individual, company or country does not own this global network. 14.2. History of Internet In 1969 AD, the US department of defense created a network called ARPA net, which stands for advanced research Project Agency networks. In those days, there were no microcomputers. The model of centralized mainframe computers and terminals ruled the computer world. Under the model, the big mainframe computer sat at the center of a starfish like system with a dumb terminal at the tip of each tentacle. Later, a concept of network had been developed in which many devices were connected so they had shared resources. But here nothing was centralized, that is why it was quite a new concept. To fulfill this concept, a project called ARPA net was started in the USA. Later ARPA net changed into Defense Advanced Research Project Agency net (DARPA net) during 1970 to 1980 AD. Later other networks like BITNET, NSFNET, USENET and UUCP were connected with DARPANET. Then US government had facilitated its development by providing funding and some guidance. Then the name of this group of this Network was given as Information Super Highway. Then after 1996 the name of information super Highway also changed into Internet. Again at the beginning of 2000 AD, Intranet and Extranet also came into the world market as a special part of the Internet. What is Special about Internet? There are three obvious reasons. Internet is the cheapest and fastest means to: i) Get information: At present people are using Internet (i.e. world wide web- www) to get information about people, products text, organization, research data, electronic version of the printed media, etc. ii) Provide information People can use Internet to provide information about their Institutes, organizations, companies, products, facilities, rule and regulations, graphical pictures, photo’s, etc. They can advertise globally for a long time in a cheap price and providing more spaces, using website (Internet). People are using Internet for the distance learning and assistance for students. iii) Compile information You can conduct a survey collecting opinion of the people within or outside your country for example using SMS in TV or radio etc. The web provides you ideal platform and opportunity. 14.3. Internet Access You can connect internet is two ways, that is: i) Dialing into an internet service ii) With a direct connection to difference is mainly in the speed and your ISP using a telephone line and called dial up connection. Some connection. Provider (ISP) and internet service provider. The cost, in most cases you connect to modem. This type of connection is times you go in for a direct 45 Fig: Computer of a dial up connection In the dial up connection you use modem, but in the direct connection to ISP you do not use modem. In the direct connection you will use Integrated Services Digital Network (ISDN). ISDN can handle more than 56,600 bps. ISDN provides you voice mail, e-mail, chatting and computer processing facilities, 14.4. Internet Basic, To run the Internet, you need windows 95 or 98 or 2000 or Windows NT Operating system as software. Similarly, in the side of the hardware you need a set of microcomputer, a set of telephone and a printer. On the top of that a modem including a service of Internet Service Provider (ISP), which helps you to connect WWW, US Net, News group or e-mail, chat etc is also necessary. At present there are 21 ISP services in Nepal. The requirements in short are: i) A set of computer ii) A modem iii) Access to the Internet host iv) A communication software (Internet Explorer & Netscape Navigator, etc.) v) A dedicate telephone line. vi) Registration to one of the local Internet Service Providers 5.4.1. Internet Protocol Internet Protocols means the set of data transmission rules, that govern the way data travels from one machine to another across networks. There are various Internet Protocols that we use. The most commonly used protocols are: i) Transmission control protocol/ Internet protocol (TCP/IP) ii) File transfer protocol (FTP) iii) Hyper text transfer protocol (HTTP) iv) Telnet. v) Gopher vi) Wide area information service (WAIS) 14.5. Internet Addressing Internet addressing is a systematic way to identify related people computers and internet resources. If you want to connect to other computers, transfer files to or from another computer, or send e-mail message, you first need to know where the other computer is you need the computer’s “address”. 46 An IP (Internet Protocol) address is an Identifier for a particular machine on a particular network. It is a part of a scheme to identify computers on the Internet. IP addresses are also referred to as IP numbers and Internet addresses. An IP address consists of four sections separated by periods. Each section contains a number ranging 0 to 255. Example 202.54.1.6. These four sections represent both the machine itself or host and network that the host is on. The network portion of the IP address allocated to internet services providers (ISPs) by the Inter NIC, under authority of the Internet Assigned Numbers Authority (IANA). ISPs then assign the host portion of the IP address to the machines on the networks that they operate. The IP addresses have the following characteristics in common: i) IP addresses are unique. ii) No two machines can have the same IP number. iii) IP addresses are also global and standardized. iv) All machines connected to the internet agree to use the same scheme for establishing an address. 14.6. DOMAIN NAME: A domain name is a way to identify and locate computers connected to the Internet. No two organizations can have the same domain name. A domain name always contains two parts, or more separated by dots. Examples:. Microsoft.com, Tel.net, Nide.org, Min.edu etc. www. Microsoft.com. etc. 14.7. Activities Available In the Internet Form the web site you can down load files, play games, send and receive mails and even chat with others. In other word, the modern day web browsers are very versatile and they allow you to almost all the activities that are possible on the internet. Using web browser, you can do many activities as follows. The list of activities 1) Visit web sites. 2) Send and receive electronic mail. 3) Read and post articles in news groups. 4) Down load files on your PC. 5) Chat with other user on line. 6) Play games with others on line. 7) Access on- line multimedia including radio and video broadcasts. 8) Search the internet for information. 9) Subscribe to electronic newspaper, newsletters, e-mail, etc. 10) Join contests. 11) Contribute articles and other materials. 12) Do on line shopping. 13) Post your resumes on the internet. 14) Create your own web sites. 15) Create an e-mail ID and account for you. 16) Use the e-mail remainder service. 17) Find a person’s details. 18) Send flowers or gifts to other. The above list is by no means a computer and comprehensive one. There are a lot of other things that you can do on the Internet. 14.8. WebPages, Html, Web Browsers, Searching the Web, Internet Chat. 47 Between two computer users, they communicate the message using computer and telephone lines it is called "chatting". Chat is a word, which means to talk. Now a days, sitting in the cyber café many people use chatting. They search friends, make friends, send pictures and messages. Using these facilities, some of them turn into couple and some user entertainment. Now it has become a common business in the market. 15. WORLD WIDE WEB (WWW): In 1992, Mr. Tim Berners Lee of Zeneva, Switzerland had designed a concept of World Wide Web (www) in his laboratory. Using about 200 computer systems, they were linked and tested this technology experimentally in Oct 1993 AD. It was a successful test. It was the first experiment, where Mr. Lee had used the sound, video images and graphical pictures as data. He had used a scripting language called Hyper Text Markup Language (HTML) to create a Webpage. To communicate these data, Mr. Lee had used Hyper Text Transfer Protocol (HTTP), which is called "web" or www. At present, any user can use Internet explorer, or Netscape Navigator to view the websites or web page. In general, these programs are called web browser. It is a kind of interactive application program. Using this, you can search, find, copy, print the information found in the websites. Similarly, you also can send the information and create the websites for the global users at any time. 16. Electronic Mail: 16.1. INTRODUCTION: An electronic mail is called e-mail. Now a day this word is very common. Between two users, using this service they can pass on their messages within a minute through telephone line using computers. It is an electronically mailing service around the world. This service was started first time by the USA in 1976. This is the first stage of using Internet globally. Using e-mail anybody can send and receive the text and pictures as information from one corner to another of the world. Due to e-mail service, the surface mail has gone down around the world. Because e-mail service is very useful, quick, cheap and easy. Now this service is available at your personal computer, too. 16.2. E-MAIL ADDRESS: To send e-mail, the receiver's e-mail address must be correct. Similarly, the user must have the general idea about the e-mail address. From the following examples, you also will have the clear idea of e-mail address, which contains five parts as follows. Here we can take following two examples as: i) hari@wlink.com.np ii) ncollege@ccsl.edu.np Hari and ncollege = Individual or user's name. A sign @ = a separator symbol wlink and ccsl = a Internet service provider (ISP), which is called a domain name. .com and .edu = a commercial or educational group which is called a top domain name. .np = country code (np= Nepal) 16.3. MAILING BASIC: To compose an E-mail message, click on "compose new message" button on the tool bar. You will see an empty mail form, which will have the following parts as shown below: 48 To-Enter the E-mail address to where you are sending message. CC- Enter the E-mail address to where the copy of messages is sent. Subject-Enter the brief description as to what the message is about. Body-Enter the actual message here. Almost all E-mail programs have the following features: address look, signature feature and attachment facility. 16.4. EAIL ETHICS:- Like any form of communication, there are certain manner and general decplain that you should follow where using the E-mail. There are some guide lines, which will help you in getting the most out of your electronic mailing i. Let your message have a personal touch and politeness. ii. Be friendly on writing. iii. Be short and sweet. iv. Know your recipient. v. Be brief. vi. Make the subject line precise. vii. Use your technology like spell checker & thesaurus. viii. Read the message carefully and answer properly. ix. Don't send copies of E-mail to people unless they need it. x. You should check your mail regularly. 16.5. NTERNET CODE OF CONDUCT:- i. Don't encode the personal privacy of other users. ii. Do not forward E-mail without permissions. iii. Do not deliberately break into computer system. iv. Getting passwords or other access information fraudulently is unacceptable. v. Copy or making available copies of protected works without the author's precession is illegal. 16.6. ADVANTAGES & DISADVANTAGES OF E-MAIL a) Advantages: - (Bright side) i. E-mail is accessible 24 hours a day and 365 days a year. ii. Endless amount data you can send any part of the world. iii. Global communication is easier. iv. At your home also you can access E-mail. v. Work can be now done anywhere a computer can be plugged in. b) Disadvantages: - (Dark side) i. Import of virus into your computer. ii. Over load information is created. iii. Swamped by link mails. 17. Intranets: 49 18. INRODUCTION TO INTRANET Internet is a communication network, which bridges the entire small computer networks worldwide as a whole. Intranet is based upon internet technology, in particular World Wide Web (www), technology to build information system within organization or enterprise to accomplish standardization and automation. Ultimately it allows a certain organization to build a group ware within web environment at low cost on top of existing network in fracture. If a corporate web connects two or more trading partners, it is often referred to as a business to business web or an extranet. Extranet is a sub-group of internet. For example of web server and a professional organization with the thousand web server can each the considered an Intranet. 18.2) CHARCTERIETICS OF INTRANET: i. Openness ii. Easy to use iii. Low cost iv. flexibility v. Scalability vi. Innovative. 18.3 ADVANTAGES OF INTRANET:- i. It costs much less to build initial system, which results in maximum efficiency and flexibility. ii. It is based an internet protected, which expands accessibility worldwide. iii. It helps on decision making system and it automates lauding a MIS. iv. It handles multimedia data effortlessly. v. Ready to access the information worldwide. vi. Low administration and maintenance costs. vii. Platform –independent system configuration features. 18.4) WHY DOES AN ORGANIZATION NEED INTRANET? :A good business houses wants to reach more customer more effectively and efficiently, and to provide them with letter service. Daily, more consumer look to the Web for new sources, and more business look to their internet Web or Internet, to process their client's needs in more cost effective and efficient manner. To remain competitive, all organization needs to keep pace with technological advances. Large organizations, which use internets to electronically transmit documents internally, pay back their investment in the technology within six to twelve weeks according to a study commissioned by Netscape. BENEFITS OF INTRANET OF EMPLOYEES AND ORGANIZATION:i. ii. iii. iv. v. vi. vii. Employees can access information they need, when they need it. One determines as to who can have access to what data and to what extent? Transactions can be followed electronically. Database can be updated automatically as the transaction occurs. Communication can take place instantaneously anywhere in the world. Employee can work remotely, and remote employee can be shared for their expert ices. You can access other business for ordering, sourcing, contracting and so on. 19. EXTRANET:50 An extranet is a business to business intranet that allows limited, controlled, secure access between a company's internets and designed authenticated users from remote location. It is an intranet that allows controlled access by authenticated parties. A brief list of examples could include: i. Allowing suppliers access to relevant inventory levels. ii. Allowing clients to review their account recorders. iii. Allowing students to update address information in real time. As with intranet access is granted only where you establish that it is required. User access is controlled lay the latest in security technologies, protecting sensitive material from intrusion. 20. THE MULTIMEDIA 20.1 INTRODUCTION TO MULTIMEDIA: Multimedia is a technology that is made by combining hypertext, still pictures and video images, sound, animation and video using the computing power of pc. All these have been made possible recently by the latest developments in computer software and hardware. Many of us think that multimedia and CD-ROM are synonymous. But it is not true, CD-ROM is a storage device. Multimedia is a technology. For example if you want to use multimedia capabilities, your pc alone is not enough. You need additional set of hardware and software to support multimedia elements. 20.1 MULTIMEDIA SYSTEM: As you know, people can run some special classes using the multimedia system. To run such advanced class, they need a set of multimedia elements like a) Computer set b) Compatible software c) CD-ROM Reading drive d) Sound card e) Sound blast f) Microphone g) CD-ROM h) Head phone i) Digital camera, etc. With the help of these sets of multimedia system, any body can store, digitize, compress retrieve and decompress the information. To do this type of the job, the collection of the above sets of hardware set is called multimedia system. Using this system, anybody can do nice and advanced presentation. 20.1 19.3 MULTIMEDIA TECHNOLOGY: Multimedia Technology is a special computerized technique, which helps the user by providing techniques to combine texts, pictures, sound and video films including interactive facilities. It also provides facilities to the user to create, store, edit, delete and copy those data in the computer media. To store those types of data, CDROM can be a very useful storing media. Such multimedia data stored CD is called multimedia CD. Now a day, instead of heavy book a light multimedia CD is sufficient. Such CD is very cheap, light, simple, portable and easy to carry. It also helps to provide colorful presentations. Therefore multimedia technology has created more and move marketing in the world. Hence now in most of the books, video paper, film reels floppy disks, super disks and zip disks are replaced by CD-ROM. Every where you can see multimedia CD. 19.4 USING THE MULTIMEDIA ANYWHERE: Due to invention of multimedia hardware and software, computer users are taking more advantages at present. By combining the multimedia technology and multimedia system, users are gaining entertainment, knowledge, education and profits. Due to invention of multimedia technology, they are using it in the video game, film making, software training, education, seminars, website, office work and even in the video conferencing, etc. 51 19.5 SOFTWARE USED IN THE MULTIMEDIA: To design and write multimedia software, the programmer has to use different utilities and programming languages, which are as follows. (i) Java (Programming Language). (ii) Windows media player (Utilities). (iii) Real Judie or Shock wave (Utilities). (iv) Active-x of open Dock. 19.6 ADVANTAGES AND DISADVANTAGES OF THE MULTIMEDIA: Advantages: (i) It helps to use in the nice video presentation for all subjects. (ii) At anytime, anywhere and anybody can use it. (iii) Very easy to use, handle, carry, copy and store. (iv) Usable in interactive web page, Internet, video conferencing Open University and distance education and seminars (v) Powerful presenting tool with colored pictures, motion pictures and graphical pictures with multiple facilities. Disadvantages: (i) (ii) (iii) (iv) Very costly at the beginning during multimedia production Requires very skilled manpower to use it. Requires very costly hardware set to use it. Poor people cannot use it due to high cost. Exercise 1. 2. 3. 4. 5. 6. What is multimedia? Explain it with examples. What is the difference between multimedia and CD-ROM? What is a multimedia system? What is a multimedia technology? What is the difference between multimedia system and multimedia technology? Why and where are users using the multimedia? 18. COMPUTER SECURITIES The computer security is concerned with the protection of the software and hardware, etc. There are different problems you face while working in a computer system environment. Power or supply to a computer may fail especially in bad weather; program or packages may contain bugs. Computer Media such as disk or hard disk or tapes may become corrupted, data may be lost. Even the working staff may be careless or do some criminal type of activities. The computer can be given security under the following headings: 1. Hardware Security (i) Natural disaster (ii) (iii) Air conditioning (iv) (v) Building Construction and Design (vi) (vii) Insurance 2. Hardware Security Electric Power supply Access Control Fire Protection 52 3. Software Security 4. Security of Data. 5. Safety from Virus 20.1 Hardware Security: The environment and natural disaster has enormous influence on the security of the hardware. To protect the hardware from the natural disaster, necessary actions must be taken in proper time. (i) Natural disaster: The likely risks due to the computer location need to be assessed. The other factors or conditions affecting the hardware are Earthquake, Wind, Rain, Snow, Ice, Floods, Lightening, Land slip, Fire, etc. (ii) Uninterruptible power supply (UPS): No computer can operate without power supply. Computer needs 220 Volts (AC) 240 Volts (A.C) supply as the input voltage to its Power Supply Unit. The frequency of AC (Alternating Current) supply should be 49.5 Hz to 50 Hz. An uninterrupted power supply (UPS) is one, which provides uninterrupted supply of power in case of failure of regular supply to the computer system. Whenever there is power cut or supply problem, automatic switching takes place between regular supply line and the UPS and without interruption, a continuous or constant supply to the computer is maintained. Hence, data or program loss or any electric damages to any unit or circuit will not take place. A standby generator with battery supported UPS can maintain supply. Such a generator need very high capital cost. You can use volt guard or spike guard to protect your computer from the high or low voltage. As a cheap device, it can be used. A stand by emergency lighting is always necessary to escape in case of supply line failure. Large electric torches or lanterns should be kept near the reception desk. (iii) Air Conditioning: Large computers dissipate too much heat, so ventilation is needed to maintain the temperature. For the computer, certain environment is needed. Humidity and temperature must be controlled, and a dust-free atmosphere is to be maintained which is possible with air conditioning plants. A typical air conducting plant re-circulates some of the air and introduces a continuous supply of clean filtered air at the correct temperature and humidity. Some air is exhausted to the outside. The temperature of 21° C ± 2° C (70 °F± 3 ° F) and the relative humidity of 50% ± 5% are necessary. Rise in temperature inside the computer room leads to overheating of components (i.e. IC chip, transistor etc.), moisture precipitation. (iv) Access Control: Unnecessary persons should not be allowed inside the computer room. The entry and exit point of the computer room should be controlled and monitored properly using ID card system. The commonly used access control methods are: - By using people (e.g. Security guard) - By using mechanical locks (e.g. Door Lock) - By using electronic system (e.g. Card Locks) (v) Insurance Protection: Incase of the computer system is in danger due to natural disaster or malfunctioning or theft or rubbery, the insurance protection is a must. 53 20.2 SOFTWARE SECURITY: The security of software includes security of both application programs and system software. From the security viewpoint, Operating System (OS) is the most important which controls and monitors the entire system. To provide security to the software the use can apply the following methods. i) Password: To prevent using the computer, the user can put the password system in the computer. If somebody wants to run the computer, he or she must entry the password, when the computer wants the password, if not it won't allow it to run lock key. ii) Backup: Sometimes, the software or database stored in the hard disk could be damaged due to crash of the hard disk or due to virus. If the user finds this type of problem, he can solve the problem using his backup program or the database file, provided he has the backup files. Hence to prevent such problems of the software, the user must create the backup files from time to time. iii) Hard lock key: Hard lock key is a kind of checking point available within the software during its running time. The user needs to type a kind of password when the software asks the hard lock key to be typed. If it matches the software runs, otherwise it does not work. Thus the hard lock key protects from the software piracy. iv) Virus scanning: Computer virus is a man made small program, which creates software problems to the users. For example, it damages the program or database files or the outputs. Hence the user must protect his application program, operating system or database files from the virus by any means. The details about the virus you can find in the following chapter. Exercise 1. What is the hardware security? Explain any two methods. 2. Give any two points to protect software. Explain how do you do. 3. Write short notes on: a. Power Protection b. Password c. De - fragmentation d. Backup e. Computer security 4. What do you mean by computer security? 5. What is a UPS? What is the range of voltage and its frequency that can be applied to the computer system? 6. Why do you need Air-Conditioner? 7. Explain how building construction affect the computer security 8. Do the people in an organization affect the security of computer? Explain why? 9. How are hardware and software security maintained? 10. What should be the abilities of software having proper security system? 11. Write two examples of security package. 12. Why do we need security of data? 19. IT Policies And Cyber Laws: 54 21.1 BACKGROUND: Actually Nepal had started using computer technology in 1971 for the national population census 2028BS. Since then till now, Nepal has crossed many obstacles and gained different types of experiences in using IT. As everybody knows that the country like Nepal had tapped many opportunities using IT to speed up the allround development of the country. With the help of using IT, the developing areas are education sector, health sector, agriculture sector tourism sector, banking sector and publishing sector, etc. With the help of using IT, there will be increment in opportunities, developing activities, democratic process, financial status and all round awareness, etc. There will be big change in the people's thinking capability. In a short period of time, people will be able to achieve all round development and improve their quality of life. From the development of IT in the country, it will be able to avoid poverty and bring quick change in life. It will create job opportunities and will establish the intellectual basic infrastructures. 21.2 OBJECTIVE: The development of IT will be done for the following three basic objectives in the country. i) To create knowledge based society ii) To create job opportunities for the people. iii) To establish knowledge based industries. 21.3 INFORMATION TECHNOLOGY (IT) POLICY: To fulfill the above mentioned three basic objectives, Nepal government will establish IT centers in most of the VDC's. Each and every department and ministry of the government will create their websites, develop ecommerce, e-education, e-health and e-banking. With the help of using the above tools, they try to create job opportunities and provide quick services to the people of different communities. The Nepal government will try to establish basic informative infrastructure and basic working culture with the help of internet, intranet and extranet. 21.4 WORKING POLICY: To implement the national IT policy of Nepal and to fulfill the following objectives, the government of Nepal will follow the following points. i) With the help of people's participation to develop the IT based infrastructures. ii) With the help of people's participation to develop the skilled manpower. iii) To disseminate the information technology within the country. iv) To provide different facilities to develop the information technology. 21.5 INSTITUTIONAL MANAGEMENT: i) Under the chairmanship of the honorable pri-minister and deputy chairmanship of the science and technology minister with other 16 members an organization called National Information Technology Development committee (NITDC) has been established in 2003 AD. It is the head of National Information Technology center, under which National Technology Committee will work. NITDC is the main body, under which Nepal works to develop information technology within whole Nepal. ii) Similarly, to develop and expand the area of the information technology, to revise and update, to supervise and monitor the yearly progress and to solve the problems regarding IT, an organization called National Information Technology Centre (NITC) has been established in 2003 AD. This organization is running under the chairmanship of the honorable science and technology minister including deputy chairmanship of the deputy chairman of National Planning Commission and 10 other members. NITC is working under NITDC. iii) Regarding information technology, to develop the curriculum to develop manpower, to fix the standard and levels, to organize the research works and to co-ordinate between private institutes and governmental organizations and the organization called National Information Technology Co-ordination Committee (NITCC) has been formed in 2003 AD. iv) Similarly, as per necessary district level and regional level information technology centers will be opened, where the local people will be involved and will take advantages sharing information, using internet, 55 intranet, extranet and e-mail. According to their knowledge, capacity and requirements, the local people will gain knowledge and experiences. 21.6 LEGISLATION: Nepal government will design, update and implement the cyber laws from time to time as per national and international situation. The law will be related to e-banking, digital signature, software piracy, data protection by encryption, copyright protection and privacy protection act, etc. 21.7 UPDATING THE IT POLICY: Nepal government will supervise the running of cyber law from time to time and rewrite them to update. In every two alternate years continuously, it will be updated. International Cyber Laws: Fair Credit Reporting Act-1970 = Privacy act. Freedom of Information Act-1970 = To access data file & to collect information from the government agencies. Federal Privacy Act-1974 = To allow individuals to know what is stored in the file about them. Video Privacy Protected Act.-1988 = To stop disclosing a person's video, in the bank, hospital without authority. Computer Matching and Privacy Protection Act-1988 = To prevent the government from comparing records to find match. Copy Right Act-1992 = To protect copy right , PenaltyUS $260,000 & 5 Years of jail. 20. Data Representations 5.8.1. Integer, 5.8.2. Real Numbers, Strings .Bits ,Bytes ,Nibble ,Positional And Non Positional Number 5.8.3. Binary, Decimal, Octal, Hexadecimal System and Their Conversions. 24. E-TECHNOLOGIES:E-Technologies means the use of Information Communication Technologies (ICT) in the banking sector , management sector, education sector, mailing sector, business sector, tourism sector and others. Detail discussion on the above subjects matter is called discussion on E-technologies. 1.12. History and Development of Computer in Nepal: Although the first electronic digital computer was built in mid 1940’s, computer was introduced in Nepal in the year 1972 only. It was introduced by Government for the population census of 1972 (2028 B.S). This was the second generation computer of IBM Company called IBM 1401. The Government had paid Rs One lakh twenty five thousand per month as rent for this computer. The Census Department at Thapathali Kathmandu had used IBM 1401 computer for the first time to process 1 corer 12.5 lakhs population census taking 1 year, 7 months and 15 days. Later, it became essential to operate the computer for day and night, for this reason a separate branch office called Yantric Sarinikaran Kendra (Electronic Data Processing Centre), was established in 1974 (15th Paush 2031 B.S.), which, after six years, was converted to National Computer Centre (NCC). 56 For the population census of 1981 (B.S. 2038), a British computer ICL 2950/10 (International Computer Limited 2900 Series) which had 64 terminals was added from the aid of UNDP and UNFPA at two million American dollar from the British ICL Company. By the help of this fourth generation computer, the 1981 population census was completed within one year and 3 months. Microcomputer such as Apple, Vector and Sirus were introduced in Kathmandu for the first time in 1982 (B.S. 2039). New companies such as Computer consultancy (CC), Management Information Processing System (MIPS) and Data System International (DSI) were established. Since 1983 (BS. 2040) National Computer Center, on the other hand, also started giving training on programming, data entry, data processing, and development of software packages. As a result, many people from various sectors started showing their interest in the field of computers. Since 1977 (B.S. 2034) His Majesty’s Government employed IBM 1401 computer in tourist statistical data processing, industrial data processing, statistical and loan account keeping of Agricultural Development Bank, Provident fund, SLC result processing and TU result processing, etc. After a few years, new computer ICL 2950/10 was brought in use, which was more efficient for data processing in some other corporations such as Telecommunication, Electricity Authority, Janakpur Cigarette factory, Hetauda Cement Factory, Tribhuwan University, etc. Many others like travel agencies, hotels, factories, printing presses also started using computer for better & faster work. At present, not only Kathmandu is using microcomputers but also Lalitpur, Bhaktapur, Pokhara, Nepalgunj, Bhairhawa, Butwal, Hetauda, Birgunj, Biratnagar, Janakpur, Jhapa etc. are using computer for different purposes. Nowadays, computers have been used in different areas like, travel agencies, hotels, Airlines, Government offices, Banks, Colleges, Schools, Hospitals, etc. in Nepal. People are using computer even at home for day-to-day use for their personal convenience. Now there are more than 1000 private computer-training centers all over Nepal. About 50 software development centers are working in the Nepali market. At present, in Nepal more than 1250 schools, 107 higher secondary schools, 50 general colleges, 42 IT related colleges and 4 Universities are teaching and using computer technology. More than one hundred thousand computers are busy in Nepal. More than 28 private Internet Service Provider (ISP) are providing services in the Nepali market. Nepal had started using email, Internet, e-Banking and Websites since 1996 AD. The purpose of using the computers is for word processing, keeping accounts, keeping the records and details of employees, inventory control, etc. A few software houses are involved in software development and in exporting the software to the international market (i.e. in Japan, Germany, USA, UK etc) also. Some of the private institutes and companies are involved in computer assembling, selling and distributing like in other developed countries. The scope of computer in our country is increasing rapidly day by day. In May 2000 AD, Ministry of Science and Technology, HMG had announced the national policy on IT. Similarly, HMG had announced the Cyber Law and copyright Law in Sept 2004 etc. 57