Finding_26
advertisement
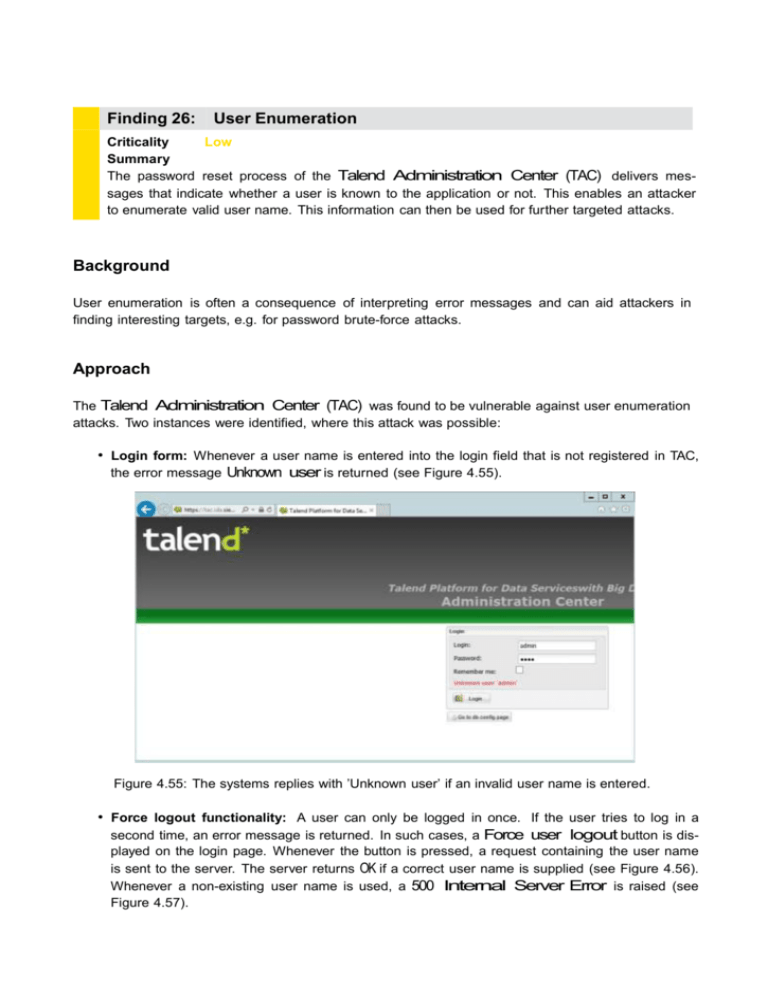
Finding 26: User Enumeration Criticality Low Summary The password reset process of the Talend Administration Center (TAC) delivers messages that indicate whether a user is known to the application or not. This enables an attacker to enumerate valid user name. This information can then be used for further targeted attacks. Background User enumeration is often a consequence of interpreting error messages and can aid attackers in finding interesting targets, e.g. for password brute-force attacks. Approach The Talend Administration Center (TAC) was found to be vulnerable against user enumeration attacks. Two instances were identified, where this attack was possible: • Login form: Whenever a user name is entered into the login field that is not registered in TAC, the error message Unknown user is returned (see Figure 4.55). Figure 4.55: The systems replies with ’Unknown user’ if an invalid user name is entered. • Force logout functionality: A user can only be logged in once. If the user tries to log in a second time, an error message is returned. In such cases, a Force user logout button is displayed on the login page. Whenever the button is pressed, a request containing the user name is sent to the server. The server returns OK if a correct user name is supplied (see Figure 4.56). Whenever a non-existing user name is used, a 500 Internal Server Error is raised (see Figure 4.57). Figure 4.56: Registered users can get logged out using this request. Figure 4.57: Entering invalid user names triggers an internal server error. Effort and Prerequisites The attacker needs access to the application login screen in the IDA network. Impact Because of error messages an attacker can enumerate valid user names. If the attacker knows a valid user name the next step could be a brute-force attack to the related password. Countermeasures The system should deliver a neutral error message e.g. wrong username or password. With such a message an attacker is not able to enumerate valid user names.