EC312 Lesson 21: Spread Spectrum
advertisement

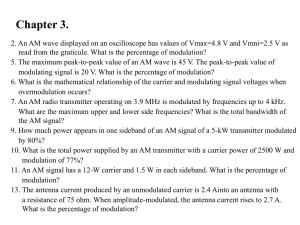
EC312 Lesson 21: Spread Spectrum: Electronic Protection Techniques
(3/20/14)
Objectives:
(a) Understand the purpose of spread spectrum, the challenges it overcomes, and the advantages it provides for
EW and commercial applications of digital communication..
(b) Describe the difference between Frequency Hopping Spread Spectrum (FHSS) and Direct Sequence Spread
Spectrum (DSSS) in terms of data and frequencies.
(c) Analyze the engineering factors associated with an FHSS signal (e.g., dwell time, bandwidth, data rate,
etc.).
(d) Analyze the engineering factors associated with a DSSS signal (e.g., processing gain, chipping rate, data
rate, etc.).
All of our previous discussions of modulation, both analog and digital, we have always been concerned about
the conservation of bandwidth and how much more bandwidth we need to get more data and more speed. The
goal has been to achieve maximum data transmission using minimum bandwidth. (We are reminded of our
lesson in digital modulation, where we encoded our multiple phase shifts and amplitudes to represent more bits
per symbol, 256-QAM, to keep the same bandwidth while increasing our information.)
In this lesson we will concentrate on a new technique of modulation, wideband modulation, and the goal is to
increase the bandwidth of the transmitted signal. So why would we want to do that?
One of the main reasons to spread our spectrum, or modulate over many frequencies for one transmission is to
avoid a jamming attack.
Your main worry may be protecting your RC car from interfering signals, but the
rest of the world is also interested in keeping their information secure and keeping
their infrastructures intact!
Wideband modulation
The most common forms of wideband modulation are:
Spread spectrum(SS)
o Frequency-hopping spread spectrum(FHSS)
o Direct sequence spread spectrum (DSSS) or code-division multiple access (CDMA)
Spread spectrum has its roots in the military’s need for communication systems that are secure and immune to
jamming. Consider how the spectrum is typically divided among multiple users. Below is our FM Band:
Frequency
(MHz)
1
This system of frequency division allows multiple stations (transmitters) to share a portion of the RF spectrum
(88–108 MHz) without interference from each other. The main advantage is simplicity. But what are the
implications of fixed frequencies for military applications?
High-power, fixed-frequency transmitters make easy targets… targets that are easy to jam and easy to destroy.
In our last lesson on EW, we used many of the principles from our wireless lessons to show that the enemy has
the capability to find our transmitter and affect its transmission.
Recapping, we remember that initially:
1) The adversary may need only a simple dipole antenna whose radiation pattern is an omni – directional,
donut shaped, pattern to try to pick up any of our transmissions.
2) He could extend the length (/2) of the dipole to try to pick up different frequencies in its range to hone
in on a specific carrier frequency that looks interesting.
3) Once received, he can use its signal strength (dBm) to give an idea of its area of location (like our
Bad_Egg Access Point) and then,
4) He can use 3 different positions to triangulate and really locate the transmitter.
5) At this point he could use a better focused antenna like the Yagi to get better reception of the signal and
6) Then, he can work to try to figure out the specific modulation and encryption that was used so that he
can demodulate and then decode the transmission to get the data and now that channel would be
insecure.
7) Also, once he figures out the distance to the receiver target using TDOA and his distance from the
target, he can figure out the strength of the jamming signal he needs to provide to interfere with any
operation the transmitter and target are controlling
8) All of this depends on him locating the transmission of a fixed carrier frequency.
So, to the rescue! Along comes:
Frequency hopping – just like it sounds, our data will hop from one carrier to the next.
This dilemma of fixed frequency location was recognized prior to WWII. In 1942, a scheme was proposed for
a remote control torpedo guidance system that would employ frequency hopping. By changing the transmitter
frequencies in a “random” pattern, the torpedo control signal could not be jammed.
In a frequency hopping spread spectrum system, the carrier frequency is switched in a pseudorandom fashion.
The transmitter and receiver know the pattern and are synchronized. So each user of the frequency band that is
being used shares the band, but has his own pseudorandom sequence for transmitter and receiver.
time t1 t2 t3 t4 t5 t6 t7 t8 t9 …………….t14
User 1: {f2, f1, f2, f7, f5, f3, f6, f3, 0, f4, f1, f7, f1, f5} Hz
User 2: {f6, 0, f7, f4, f7, f1, f4, f7, f2, f4, f2, f5, f3, f6} Hz
User 3: {f4, f3, f2, f3, f2, f5, 0, f7, f3, f6, f1, f3, f5, f1} Hz
.
.
User 6: {f6, f7, f4, f3, f1, f7, f6, 0, f2, f4, f1, f5, f6, f3} Hz
.
.
User 10:{f1, f1, f2, f3, f3, f4, f4,0, f5, f6, f6, f6, f7, f7} Hz
2
Dwell time
f1
f2
f3
f4
f5
f6
f7
Notice for this particular example of a frequency hopping system that time is on the vertical axis above. After
each increment of time, a single user changes (hops) between different frequencies to send his data. So his
message is spread out over many random frequencies within a band.
Example
If the frequency band of the FHSS system above, 222.5-257.5MHz ,was divided into 7 sub-bands which 10
users share. Which user’s pattern is shown above?
FCC authorized use of spread spectrum in specific bands at 1W for civilian applications: 902- 928MHz,
2.4-2.438GHz, and 5.725 - 5.85GHz. Many commercial communication systems use SS techniques on these
frequencies, ie wireless networks, cell phones, etc.
Frequency hopping transmitter ( Figure next page)
The binary data binary data to be transmitted is first applied to a conventional
two-tone
FSK modulator.
In this FHSS system, a frequency synthesizer produces a sine wave (the carrier) at a random frequency
determined by a pseudorandom code generator. These two signals are mixed together, filtered and then
transmitted.
3
Typically the rate of frequency change determined by the pseudorandom (PSN) code generator is much higher
than the serial binary data rate. The illustration above shows that the frequency synthesizer changes 4 times for
each data bit. The time period spent on each frequency is called the dwell time (typically < 10 ms).
The resulting signal, whose frequency rapidly jumps around, effectively scatters pieces of the signal all over the
band. Someone else monitoring the spectrum looking would not recognize a transmission is being made. In
other words, instead of seeing two strong frequencies in use (and thus presuming someone is using BFSK),
someone monitoring the spectrum would see a blur of very faint frequencies in use, and presume it is just noise.
Example
If the bit rate of the FHSS system above is 1kbps, and the dwell time is 0.1ms on the frequency range of
222.5MHz- 257.5MHz range, how many frequency shifts occur during the transmission of each bit?
Frequency hopping receiver The received signal is mixed using a local oscillator driven by the same
pseudorandom sequence.
The output produces the original FSK signal from which the binary data can be extracted.
Timing is extremely critical in frequency hopping systems in order to provide for synchronization.
Military spread spectrum examples
HAVEQUICK
4
HAVEQUICK is a frequency-hopping system used in virtually all aircraft radios to provide antijamming. Every radio is synchronized by a timing signal (usually GPS) and steps through a predetermined set of frequencies which is loaded into the radio daily.
SINCGARS is a VHF-FM frequency-hopping system used by the Army, Navy and USMC. SINCGARS
operates on any or all of the 2,320 frequencies between 30 and 87.975 MHz in 25 kHz increments.
SINCGARS
Direct Sequence Spread Spectrum
Another method of realizing spread spectrum is called direct sequence spread spectrum (DSSS). In DSSS,
the serial binary data is XORed (bitwise logic function) with a pseudo-random binary code which has a bit rate
faster than the binary data rate, and the result is used to phase-modulate a carrier. The bit rate of the
pseudorandom code is called the chipping rate.
Sudden phase changes to a carrier signal (like those occurring in simple BPSK,0o and 180o phase shifts,) cause
the bandwidth of the resulting modulated signal to increase. Beyond that, if we increase the rate of the phase
changes of the carrier the bandwidth also increases. If we can get the phase change rate up high enough (thanks
to a high chipping rate), the resulting modulated signal will look more like noise than an actual signal. It would
look like noise just from the rapid phase changes. However, it becomes even more noise-like due to the fact
that the phase changes are generated in a pseudorandom fashion.
Figure 4. A high-level description of a DSSS system.
5
1
data
1
0
1
time of one data bit
carrier modulated by the data
Pseudo Random
Sequence
“chip”
data PRS
XOR
carrier modulated by the data PRS
Instead of using the original data to phase
modulate a carrier, we would now use the
output of the XOR process. This will change
the phase of the carrier much more frequently
than the original data would, so the signal
power would be spread over a wider
bandwidth.
power
UNMODULATED
CARRIER
SLOW SPEED PSK
HIGH SPEED PSK
frequency
Figure 5. An illustration of the spread spectrum and noise properties of DSSS.
In DSSS, a signal that would normally occupy a few kHz of bandwidth (say like your regular FM broadcast) is
spread out 10 to 10,000 times its normal bandwidth. The energy that would normally be concentrated in that
narrow bandwidth is still there in DSSS, but has been spread out, too. In fact the energy is so spread out, that
it’s often indistinguishable from the normal atmospheric background noise as shown in Fig. 6 below. It’s so
diluted that it appears as noise in a conventional receiver where rapid frequency changes cause noise like effects
and spreading of a signal’s bandwidth.
Figure 6. The energy of a DSSS signal is spread over such a large bandwidth that the energy is
indistinguishable from naturally occurring background noise.
As was the case with frequency-hopping spread spectrum, a DSSS receiver must know the pseudorandom
sequence of the transmitter and have a synchronizing circuit to get in step with this pseudorandom digital signal.
6
The receiver using an identically programmed PN sequence can then “see” incoming matched signal clearly
from the noise. Even cooler, multiple DSSS broadcasts can overlap each other spectrum-wise. Other signals
using different PN sequences appear as noise to the receiver and is ignored.
DSSS is also called Code Division Multiple Access (CDMA). CDMA is used in satellites and digital cell
phones.
List some reasons CDMA is attractive for cell phones and satellites.
The measure of the spreading is called the processing gain, G, which is the ratio of the DSSS bandwidth, BW,
divided by the data rate, fb.
G
BW
fb
The higher the processing gain, the greater the DSSS signal’s ability to fight interference.
Example
A 13kbps binary signal is spread over a bandwidth of 1.25 MHz using BPSK. What is the processing gain of
the resulting DSSS signal? Express the answer as a ratio and in decibels.
Benefits of Spread Spectrum and how they relate to Cyber
Spread spectrum is being used in more and more applications in data communications.
Security – need a wide BW receiver and precise knowledge and timing of the pseudorandom sequence,
and this relates to the confidentiality and authenication of our data
Resistance to jamming and interference – jamming signals are usually restricted to one frequency
Band sharing – many signals can use the same frequency band; and many spread spectrum signals
raise the overall background noise level, but don’t prevent reliable communication. This relates to the
availability of our data
Resistance to fading – fading is a frequency-selective phenomenon; a spread spectrum signal doesn’t
reside at only one frequency
Precise timing – signals jump so quickly that even the most determined snooper will only “see” a
fraction of a bit’s worth of data
This lesson finishes the section of material in the wireless section of Cyber2 that is covered by Exam II. You
have learned the vulnerabilities that are specific to this section and you hopefully understand that to defend and
attack against threats in cyber communications; you were provided with the conventional and theoretical
development to get a baseband signal (voice, video, and data) from a transmitter to a receiver through the
channel of free space.
The lessons have brought you from learning the electromagnetic spectrum, and the time signals and their
frequencies and wavelengths to the modulation techniques for these analog and digital signals (AM,ASK, FM,
FSK, PM, PSK). The bandwidths of the different techniques and the antennas and filters were very important to
defining the limitations of the communication systems ( 1/2 power, -3dB, helped define the upper to lower
cutoffs). The gain and attenuation involved in the transmission of the signal and the propagation idiosyncrasies
of the different modulation frequencies guided us to be wary of the noise associated every step of the way.
7
In the previous lesson you’ve had a discussion and demonstration of the wireless aspect of military
communications and the ideas of how electronic warfare has become ever present in today’s age. The take away
for you especially in this lesson on jamming mitigation is that you find that a principle that you had been
preserving, bandwidth, as it was finite and regulated became your best friend to ignore and spread out when
trying to defend, and the ugly noise that is everywhere and causes frustration when trying to get your signal,
became your friend, as you could hide behind it. So always think outside the box, EW is not fought fairly, so
playing with strategy and tactics to use constraints differently can be your best invention.
Asst. Prof. Currie Wooten, CDR Hewitt Hymas
Help us improve these notes! Send comments, corrections and clarifications to cwooten@usna.edu
8