Section 2.4 Transposition Ciphers
advertisement

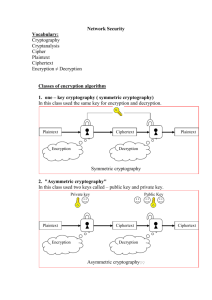
Section 2.4 Transposition Ciphers • Definition: A Transposition Cipher is a cipher in which the plaintext message is rearranged by some means agreed upon by the sender and receiver. – In transposition ciphers, no new alphabet is created. The letters of the plaintext are just rearranged in some fashion… Simple Types of Transposition Ciphers • Rail Fence Cipher – The plaintext is written in a zig-zag pattern in two rows and form the ciphertext by reading off the letters from the first row followed by the second row. • Example 1: Encipher “CHUCK NORRIS IS A TOUGH GUY” – Row 1: CUKORSSTUHU – Row 2: HCNRIIAOGGY – ciphertext: CUKORSSTUHUHCNRIIAOGGY • To decipher a rail fence cipher, we divide the ciphertext in half and reverse the order of the steps of encipherment, that is, write the ciphertext in two rows and read off the plaintext in zig-zag fashion. (Note: if there are an odd number of letters, the first row has one more letter then the second) • Example 2: Decipher the message “CITAT ODABT UHROE ELNES WOMYE OGEHW VR… Simple Types of Transposition Ciphers • Simple Columnar Transpositions – The Rail Fence Cipher is a special case of this. (The Rail Fence has n / 2 or n / 2 + 1 columns) You use two or more columns to do the same thing. You first agree on the number of columns. • Example 3: Encipher “THE JOKER SAID THAT IT WAS ALL PART OF THE PLAN” as a 5 column transposition cipher. • Example 4: Decipher TOTBA AUJAA KMHKO ANTAU FKEEE LTTYR SRLHJ RDMHO ETEII which was enciphered using a 4 column transposition: • In general, given a simple column transposition with n letters and c columns, then there are n / c rows if the remainder is 0, and n / c + 1 rows, with r columns have n / c + 1 entries, and c – r columns having n / c. – Example 5: Suppose n = 50, c = 9. Then there are 50 / 9 + 1 = 6 rows. The last row will have 5 letters in it. The first 5 columns will each have 6 letters, and the last 4 columns will have 5… Keyword Columnar Transposition • Suppose that we use the keyword TUCKER (student from 2011 class). – This keyword has six letters in it. That means that there are six columns, and each column must have the same number of letters. (See below about what to do if letters repeat) • • Let us suppose that we want to transmit the message: “THE STUDENT MENTIONED ABOVE IS A SENIOR AT PULASKI HIGH SCHOOL.” – – This message has 52 letters in it. To be divisible by six we must add 2 letter to the message as fill letters. We will use ZZ. Write the message in rows with 6 letters for each row. (The word document explains how to handle repeated letters). • • Therefore, we may need to add fill letters at the end of the message so that the length of the message is divisible by 6. The message sent is: “ENIBARAGOTMNVETKSZSTOOSASHLUEEENPICZTDNDIIUHHHETASOLIO”. To decipher, given that you know the keyword: – – – – Write out the keyword. Divide the ciphertext into columns of equal letters (use the keyword to get the length of each column). Put the first column of letters under the letter in the keyword that comes alphabetically first. Put the second column of letters under the letter in the keyword that comes second. Etc... ADFGX • During World War 1 most of the world was using either substitution or transposition ciphers to encrypt messages. – In March 1918 Germany began using ADFGX. • It was invented by Colonel Fritz Nebel a Signals Officer… • These particular letters were chosen because they were very different and could not be confused when using Morse Code. ADFGX • Two step process: – Step 1: • Create a 5x5 table with ADFGX along the top and similarly along the side. Example: (See below and to the right) • This table was created randomly. • The letters I and J are interchangeable. (There are 26 letters and only 25 slots.) – Step 2: Apply a substitution or transposition cipher. • Example… ADFGX • Historically – Germans thought the code was unbreakable. – It was broken by French Army Lieutenant Georges Painvin. – Probably contributed to Germany’s ill-fated 1918 Sring Offensive. – Painvin (who was already slender) spent many hours during a 3 month period breaking ADFGX and ADFGVX codes. He lost 33 pounds and had to go through rehabilitation… ADFGVX • Similar to ADFGX except now you use 6 x 6 table. This allows for all letters and the digits 0-9. • Assignments: • 3.1 #1,4,8, and one of 9-11. • 3.2 #1, 5 • 3.3 #1, 3 • 3.5 #3…!