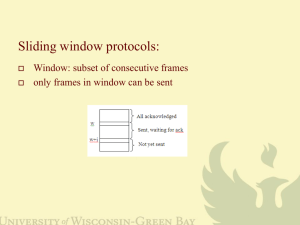
08-reliable-data-transfer - Rose
advertisement
08 - Transport Layer Transport Layer 3-1 Reliable data transfer: getting started rdt_send(): called from above, (e.g., by app.). send side udt_send(): called by rdt, to transfer packet over unreliable channel to receiver deliver_data(): called by rdt to deliver data to upper receive side rdt_rcv(): called when packet arrives on rcv-side of channel Transport Layer 3-2 Reliable data transfer: getting started We’ll: incrementally develop sender, receiver sides of reliable data transfer protocol (rdt) consider only unidirectional data transfer but control info will flow on both directions! use finite state machines (FSM) to specify sender, receiver state: when in this “state” next state uniquely determined by next event state 1 event causing state transition actions taken on state transition event actions state 2 Transport Layer 3-3 Reliable transfer over a reliable channel underlying channel perfectly reliable no bit errors no loss of packets separate FSMs for sender, receiver: sender sends data into underlying channel receiver read data from underlying channel Wait for call from above rdt_send(data) packet = make_pkt(data) udt_send(packet) sender Wait for call from below rdt_rcv(packet) extract (packet,data) deliver_data(data) receiver Transport Layer 3-4 Channel with bit errors underlying channel may flip bits in packet checksum to detect bit errors the question: how to recover from errors: acknowledgements (ACKs): receiver explicitly tells sender that pkt received OK Imagine a telephone conversation. negative acknowledgements (NAKs): receiver explicitly How do humans tells sender that pkt recover had errors from “errors” during sender retransmits pkt on receipt of NAK conversation? new mechanisms in rdt2.0 (beyond rdt1.0): error detection receiver feedback: control msgs (ACK,NAK) rcvr->sender Transport Layer 3-5 Channel with bit errors underlying channel may flip bits in packet checksum to detect bit errors the question: how to recover from errors: acknowledgements (ACKs): receiver explicitly tells sender negative acknowledgements (NAKs): receiver explicitly that pkt received OK tells sender that pkt had errors sender retransmits pkt on receipt of NAK Transport Layer 3-6 Group Assignment #1 Divide into groups of 4 and modify our original FSM to include ACKs and NACKs. Note that an ACK is sent when the packet arrives at the receiver with no errors and a NACK is sent when the packet is corrupted in transmission. Wait for call from above rdt_send(data) packet = make_pkt(data) udt_send(packet) sender Wait for call from below rdt_rcv(packet) extract (packet,data) deliver_data(data) receiver Transport Layer 3-7 On the Board Let’s discuss your solution (Please make any changes to your quiz notes if necessary). Transport Layer 3-8 Group Assignment #2 What happens if ACK/NAK corrupted? sender doesn’t know what happened at receiver! can’t just retransmit: possible duplicates Transport Layer 3-9 On the Board Let’s discuss your solution (Please make any changes to your quiz notes if necessary). Key: Introduce sequence numbers. Stop and Wait! Transport Layer 3-10 Group Assignment #3 How would you replace NACKs in your FSM? Transport Layer 3-11 On the Board Let’s discuss your solution (Please make any changes to your quiz notes if necessary). Key: instead of NAK, receiver sends ACK for last pkt received OK receiver must explicitly include seq # of pkt being ACKed duplicate ACK at sender results in same action as NAK: retransmit current pkt Transport Layer 3-12 Group Assignment #4 What if the underlying channels can also lose packets (data or ACKs)? Transport Layer 3-13 On the Board Let’s discuss your solution (Please make any changes to your quiz notes if necessary). Key: sender waits “reasonable” amount of time for ACK retransmits if no ACK received in this time if pkt (or ACK) just delayed (not lost): retransmission will be duplicate, but use of seq. #’s already handles this receiver must specify seq # of pkt being ACKed requires countdown timer Transport Layer 3-14 rdt3.0 in action Transport Layer 3-15 rdt3.0 in action Transport Layer 3-16 For Next Time… Pipelined Protocols Take a look at the Go-Back-N and Selective Repeat protocol applets on the textbook website. How do these two protocols work? Transport Layer 3-17