Systems Software 2 [pps]
advertisement
![Systems Software 2 [pps]](http://s2.studylib.net/store/data/005446651_1-28fd8fabbd88a37f2534ff5d4707c83a-768x994.png)
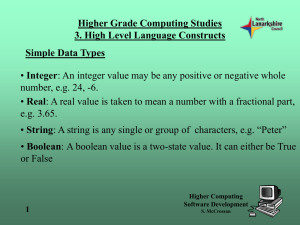
Higher Grade Computing Studies 8. Supporting Software Software Compatibility • Whether you are doing a fresh installation of or upgrading from a previous piece of software, checking your hardware and software for compatibility is a must. • The main factors to consider are: • Memory requirements – How much RAM do I need? • Storage requirements – Do my application programs generate large files? • Operating System – Will an application run on an older OS? 1 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Viruses • A virus is a programming code that causes some undesirable and unexpected event to happen in a computer. • Viruses can be quite harmful and erase data or close down a system. 2 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Viruses • A virus is a programming code that causes some undesirable and unexpected event to happen in a computer. • Viruses can be quite harmful and erase data or close down a system. 3 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software File Viruses • File viruses attach themselves to program files such as .exe or .com files. When the program is loaded, the virus is also loaded. • A file viruses can also take the form of a complete program, or script, attached to something else, e.g. an e-mail. 4 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Boot Sector Viruses • These viruses infect executable code found in certain system areas on a disk. • They attach to the boot sector on disks or the master boot record on hard disks. • To infiltrate the boot sector, the virus is read while the system is running and then activated the next time the operating system is loaded. 5 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Macro Viruses • Macro viruses infect applications and typically cause a sequence of actions within the application e.g. inserting unwanted words or phrases in a document. 6 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Virus Code Actions - Replication • A computer virus has the unique ability to replicate. Like a biological virus they can spread quickly and can be difficult to control. • They can attach themselves to almost any type of file and spread as files are copied and sent between computer users. A virus can take a long time to replicate itself before activation. This gives it time to be spread over many computers before being discovered. 7 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Virus Code Actions - Camouflage • It is possible for a virus to avoid detection by taking on the characteristics that detection software is programmed to look for and ignore. 8 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Virus Code Actions - Watching • A virus can lie in wait and ambush a computer when something routine is carried out e.g. opening a particular application. • The damage routines will activate when certain conditions are met, e.g. on a certain date, or when the infected user performs a particular action may trigger the virus. 9 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Virus Code Actions - Delivery • Infected disks brought in from the outside used to be the main source of viruses until e-mail provided the ideal delivery vehicle. 10 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software WORMs • A worm is a self-replicating virus that does not alter any files but takes up residence in the computer's active memory and duplicates itself. • They only become noticeable once their replication consumes the memory to the extent that the system slows down or is unable to carry out particular tasks. Worms tend to use the parts of the computer's operating system that is not seen by the user until it is too late. 11 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Trojan Horse • A Trojan horse is a program where harmful code is contained inside another code which can appear to be harmless. Once the apparently harmless code is in the computer, it releases the malicious code to do its damage. Trojan horses may even claim to be anti-virus in order to get the user to install it. 12 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Anti-virus Techniques • Anti-virus software can screen e-mail attachments, Web downloads, and checks all of your files from timeto time removing any viruses that are found. Techniques used by anti-virus software to detect a virus include: 13 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Anti-virus Techniques - Checksum • This technique involves adding together the numeric values contained in the file. A calculation (checksum) is carried out on this total and it is placed as a 16-bit number at the end of the block. The receiver of the data performs the same calculation on the data and compares its checksum with the transmitted checksum. If they match, data transfer successful. If not, there is a possibility that the file is infected. 14 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Anti-virus Techniques – Virus Signatures • A virus signature is a unique pattern of bits within a virus. It can be used to detect and identify specific viruses. • Once known, the anti-virus software uses the virus signature to scan for the presence of malicious code and removes it. 15 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Anti-virus Techniques – Heuristic Detection • Heuristic techniques work on the probabilities of a file being infected i.e. it will give a percentage likelihood of a file being infected by weighing up the file behaviour. • For example, if a file attempts to access your address book then that might be suspicious. If the same file includes code that checks a date, then the suspicion rises. There will come a point when a warning is issued on the possibility of a virus. 16 Higher Computing Computer Systems S. McCrossan Higher Grade Computing Studies 8. Supporting Software Anti-virus Techniques – Memory Resident Monitoring • Some anti-virus software is memory resident and is loaded on start up. It actively monitors the system for viruses whilst the computer is switched on and checks programs for infection every time they run. • The price to be paid with memory resident programs is that they can cause delays in program loading and execution whilst the checks are being carried out. 17 Higher Computing Computer Systems S. McCrossan
![Systems Software 1 [pps]](http://s2.studylib.net/store/data/005419302_1-897cf02cd0c88c582e0cc1a66dfe3efe-300x300.png)