Computer Lab Rules: Daily Lesson Log for Grade 10 ICT
advertisement
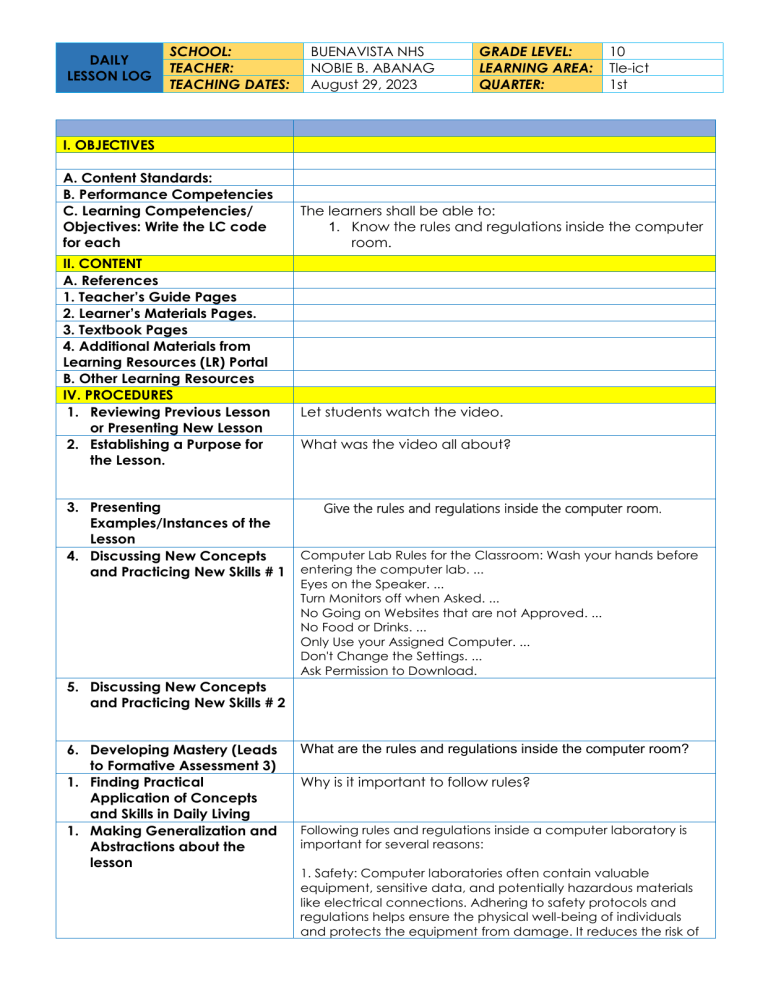
DAILY LESSON LOG SCHOOL: TEACHER: TEACHING DATES: BUENAVISTA NHS NOBIE B. ABANAG August 29, 2023 GRADE LEVEL: LEARNING AREA: QUARTER: 10 Tle-ict 1st I. OBJECTIVES A. Content Standards: B. Performance Competencies C. Learning Competencies/ Objectives: Write the LC code for each II. CONTENT A. References 1. Teacher’s Guide Pages 2. Learner’s Materials Pages. 3. Textbook Pages 4. Additional Materials from Learning Resources (LR) Portal B. Other Learning Resources IV. PROCEDURES 1. Reviewing Previous Lesson or Presenting New Lesson 2. Establishing a Purpose for the Lesson. 3. Presenting Examples/Instances of the Lesson 4. Discussing New Concepts and Practicing New Skills # 1 The learners shall be able to: 1. Know the rules and regulations inside the computer room. Let students watch the video. What was the video all about? Give the rules and regulations inside the computer room. Computer Lab Rules for the Classroom: Wash your hands before entering the computer lab. ... Eyes on the Speaker. ... Turn Monitors off when Asked. ... No Going on Websites that are not Approved. ... No Food or Drinks. ... Only Use your Assigned Computer. ... Don't Change the Settings. ... Ask Permission to Download. 5. Discussing New Concepts and Practicing New Skills # 2 6. Developing Mastery (Leads to Formative Assessment 3) 1. Finding Practical Application of Concepts and Skills in Daily Living 1. Making Generalization and Abstractions about the lesson What are the rules and regulations inside the computer room? Why is it important to follow rules? Following rules and regulations inside a computer laboratory is important for several reasons: 1. Safety: Computer laboratories often contain valuable equipment, sensitive data, and potentially hazardous materials like electrical connections. Adhering to safety protocols and regulations helps ensure the physical well-being of individuals and protects the equipment from damage. It reduces the risk of accidents, such as electrical shocks, fires, or data breaches, that could harm individuals or compromise the integrity of the lab. 2. Security: Computer labs often store and handle sensitive information, including personal data, research findings, or proprietary software. Following rules helps maintain the security and confidentiality of this information. It reduces the risk of unauthorized access, data breaches, theft, or the introduction of malicious software that could compromise the integrity of systems or jeopardize the privacy of individuals. 2. Evaluating Learning 1. Additional Activities for Application or Remediation VI – REMARKS Enumerate the rules and regulation inside the classroom. VII- REFLECTION A. No. of learners who earned 80% in the evaluation. B. No. of learners who required additional activities for remediation C. Did the remedial lessons work? D. No. of learners who continue to require remediation E. Which of my teaching strategies work well? Why did this work? F. What difficulties did I encounter which my principal or supervisor can help me solve? G. What innovation or localized materials did I used/ discover which I wish to share with other teachers? Prepared by: NOBIE B. ABANAG SST – II Checked by: DANILO H. SARMIENTO Master Teacher II Noted by: ADELA V. BAGAS School Principal II