Security+ Guide to Network Security Fundamentals, Third Edition Chapter 4
advertisement

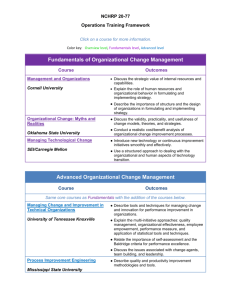
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 4 Network Vulnerabilities and Attacks Objectives • Explain the types of network vulnerabilities • List categories of network attacks • Define different methods of network attacks Security+ Guide to Network Security Fundamentals, Third Edition 2 Network Vulnerabilities • There are two broad categories of network vulnerabilities: – Those based on the network transport media – Those found in the network devices themselves Security+ Guide to Network Security Fundamentals, Third Edition 3 Media-Based Vulnerabilities • Monitoring network traffic – Helps to identify and troubleshoot network problems • Monitoring traffic can be done in two ways – Use a switch with port mirroring • To redirect traffic that occurs on some or all ports to a designated monitoring port on the switch – Install a network tap (test access point) • A separate device that can be installed between two network devices, such as a switch, router, or firewall, to monitor traffic Security+ Guide to Network Security Fundamentals, Third Edition 4 Security+ Guide to Network Security Fundamentals, Third Edition 5 Security+ Guide to Network Security Fundamentals, Third Edition 6 Media-Based Vulnerabilities (continued) Security+ Guide to Network Security Fundamentals, Third Edition 7 Media-Based Vulnerabilities (continued) • Just as network taps and protocol analyzers can be used for legitimate purposes – They also can be used by attackers to intercept and view network traffic • Attackers can access the wired network in the following ways: – False ceilings – Exposed wiring – Unprotected RJ-45 jacks Security+ Guide to Network Security Fundamentals, Third Edition 8 Media-Based Vulnerabilities (continued) Security+ Guide to Network Security Fundamentals, Third Edition 9 Network Device Vulnerabilities • Weak passwords – A password is a secret combination of letters and numbers that serves to authenticate (validate) a user by what he knows – Password paradox • Lengthy and complex passwords should be used and never written down • It is very difficult to memorize these types of passwords – Passwords can be set to expire after a set period of time, and a new one must be created Security+ Guide to Network Security Fundamentals, Third Edition 10 Network Device Vulnerabilities (continued) • Characteristics of weak passwords – – – – – – A common word used as a password Not changing passwords unless forced to do so Passwords that are short Personal information in a password Using the same password for all accounts Writing the password down Security+ Guide to Network Security Fundamentals, Third Edition 11 Network Device Vulnerabilities (continued) • Default account – A user account on a device that is created automatically by the device instead of by an administrator – Used to make the initial setup and installation of the device (often by outside personnel) easier • Although default accounts are intended to be deleted after the installation is completed, often they are not • Default accounts are often the first targets that attackers seek Security+ Guide to Network Security Fundamentals, Third Edition 12 Network Device Vulnerabilities (continued) Security+ Guide to Network Security Fundamentals, Third Edition 13 Network Device Vulnerabilities (continued) • Back door – An account that is secretly set up without the administrator’s knowledge or permission, that cannot be easily detected, and that allows for remote access to the device • Back doors can be created on a network device in two ways – The network device can be infected by an attacker using a virus, worm, or Trojan horse – A programmer of the software creates a back door on the device Security+ Guide to Network Security Fundamentals, Third Edition 14 Network Device Vulnerabilities (continued) • Privilege escalation – It is possible to exploit a vulnerability in the network device’s software to gain access to resources that the user would normally be restricted from obtaining Security+ Guide to Network Security Fundamentals, Third Edition 15 Categories of Attacks • Categories include denial of service, spoofing, manin-the-middle, and replay attacks Security+ Guide to Network Security Fundamentals, Third Edition 16 Denial of Service (DoS) • Denial of service (DoS) attack – Attempts to consume network resources so that the network or its devices cannot respond to legitimate requests • Example: SYN flood attack – See Figure 4-4 • Distributed denial of service (DDoS) attack – A variant of the DoS – May use hundreds or thousands of zombie computers in a botnet to flood a device with requests Security+ Guide to Network Security Fundamentals, Third Edition 17 Security+ Guide to Network Security Fundamentals, Third Edition 18 Denial of Service (DoS) (continued) Security+ Guide to Network Security Fundamentals, Third Edition 19 Security+ Guide to Network Security Fundamentals, Third Edition 20 Denial of Service (DoS) (continued) Security+ Guide to Network Security Fundamentals, Third Edition 21 Spoofing • Spoofing is impersonation – Pretends to be someone or something else by presenting false information • Variety of different attacks use spoofing – Attacker may spoof her address so that her malicious actions would be attributed to a valid user – Attacker may spoof his network address with an address of a known and trusted host – Attacker can set up his AP device and trick all wireless devices to communicate with the imposter device Security+ Guide to Network Security Fundamentals, Third Edition 22 Man-in-the-Middle • Man-in-the-middle attack – Intercepts legitimate communication and forges a fictitious response to the sender – See Figure 4-8 – Common on networks – Can be active or passive • Active attacks intercept and alter the contents before they are sent on to the recipient Security+ Guide to Network Security Fundamentals, Third Edition 23 Man-in-the-Middle (continued) Security+ Guide to Network Security Fundamentals, Third Edition 24 Replay • Replay attack – Similar to a passive man-in-the-middle attack – Captured data is used at a later time • A simple replay would involve the man-in-themiddle capturing login credentials between the computer and the server • A more sophisticated attack takes advantage of the communications between a device and a server – Administrative messages that contain specific network requests are frequently sent between a network device and a server Security+ Guide to Network Security Fundamentals 25 Methods of Network Attacks • Network attack methods can be protocol-based or wireless – As well as other methods Security+ Guide to Network Security Fundamentals, Third Edition 26 Protocol-Based Attacks • Antiquated protocols – TCP/IP protocols have been updated often to address security vulnerabilities – SNMP is another updated protocol • Used for exchanging management information between networked devices • The use of community strings in the first two versions of SNMP, SNMPv1 and SNMPv2, created several vulnerabilities • SNMPv3 was introduced in 1998 Security+ Guide to Network Security Fundamentals, Third Edition 27 Protocol-Based Attacks (continued) • DNS attacks – Domain Name System (DNS) is the basis for name resolution to IP addresses today • DNS poisoning – Substitute a fraudulent IP address so that when a user enters a symbolic name, she is directed to the fraudulent computer site Security+ Guide to Network Security Fundamentals, Third Edition 28 Protocol-Based Attacks (continued) Security+ Guide to Network Security Fundamentals, Third Edition 29 Protocol-Based Attacks (continued) • DNS poisoning (continued) – Substituting a fraudulent IP address can be done in one of two different locations • TCP/IP host table name system (See Figure 4-10) • External DNS server – Attack is called DNS poisoning (also called DNS spoofing) – See Figure 4-11 – DNS poisoning can be prevented by using the latest editions of the DNS software, BIND (Berkeley Internet Name Domain) Security+ Guide to Network Security Fundamentals, Third Edition 30 Security+ Guide to Network Security Fundamentals, Third Edition 31 Security+ Guide to Network Security Fundamentals, Third Edition 32 Protocol-Based Attacks (continued) • DNS transfers – Almost the reverse of DNS poisoning – Attacker asks the valid DNS server for a zone transfer, known as a DNS transfer – Possible for the attacker to map the entire internal network of the organization supporting the DNS server Security+ Guide to Network Security Fundamentals, Third Edition 33 Protocol-Based Attacks (continued) • ARP poisoning – Address Resolution Protocol (ARP) • Used by TCP/IP on an Ethernet network to find the MAC address of another device • The IP address and the corresponding MAC address are stored in an ARP cache for future reference – An attacker could alter the MAC address in the ARP cache so that the corresponding IP address would point to a different computer Security+ Guide to Network Security Fundamentals, Third Edition 34 Protocol-Based Attacks (continued) Security+ Guide to Network Security Fundamentals, Third Edition 35 Protocol-Based Attacks (continued) • TCP/IP hijacking – Takes advantage of a weakness in the TCP/IP protocol – The TCP header consists of two 32-bit fields that are used as packet counters • Updated as packets are sent and received between devices – Packets may arrive out of order • Receiving device will drop any packets with lower sequence numbers Security+ Guide to Network Security Fundamentals, Third Edition 36 Protocol-Based Attacks (continued) • TCP/IP hijacking (continued) – If both sender and receiver have incorrect sequence numbers, the connection will “hang” – In a TCP/IP hijacking attack, the attacker creates fictitious (“spoofed”) TCP packets to take advantage of the weaknesses Security+ Guide to Network Security Fundamentals, Third Edition 37 Security+ Guide to Network Security Fundamentals, Third Edition 38 Wireless Attacks • Rogue access points – Rogue means someone or something that is deceitful or unreliable – Bypass all of the network security and opens the entire network and all users to direct attacks – An attacker who can access the network through a rogue access point is behind the firewall • Can directly attack all devices on the network Security+ Guide to Network Security Fundamentals, Third Edition 39 Wireless Attacks (continued) Security+ Guide to Network Security Fundamentals, Third Edition 40 Wireless Attacks (continued) • War driving – Beaconing • At regular intervals, a wireless AP sends a beacon frame to announce its presence and to provide the necessary information for devices that want to join the network – Scanning • Each wireless device looks for those beacon frames – Unapproved wireless devices can likewise pick up the beaconing RF transmission – Formally known as wireless location mapping Security+ Guide to Network Security Fundamentals, Third Edition 41 Wireless Attacks (continued) • War driving (continued) – War driving technically involves using an automobile to search for wireless signals over a large area – Tools for conducting war driving: • • • • • Mobile computing device Wireless NIC adapters Antennas Global positioning system receiver Software Security+ Guide to Network Security Fundamentals, Third Edition 42 Wireless Attacks (continued) • Bluesnarfing – Bluetooth • A wireless technology that uses short-range RF transmissions • Provides for rapid “on the fly” and ad hoc connections between devices – The IEEE 802.15.1 standard was adapted and expanded from the existing Bluetooth standard – Two types of 802.15.1 network topologies • Piconet (See Figure 4-14) • Scatternet (See Figure 4-15) Security+ Guide to Network Security Fundamentals, Third Edition 43 Wireless Attacks (continued) Security+ Guide to Network Security Fundamentals, Third Edition 44 Wireless Attacks (continued) Security+ Guide to Network Security Fundamentals, Third Edition 45 Wireless Attacks (continued) • Bluesnarfing (continued) – The unauthorized access of information from a wireless device through a Bluetooth connection – Allows an attacker to access e-mails, calendars, contact lists, and cell phone pictures and videos • By simply connecting to that Bluetooth device without the owner’s knowledge or permission • Blue jacking – Sending unsolicited messages from Bluetooth to Bluetooth-enabled devices Security+ Guide to Network Security Fundamentals, Third Edition 46 Other Attacks and Frauds • Null sessions – Unauthenticated connections to a Microsoft Windows 2000 or Windows NT computer that do not require a username or a password – Could allow an attacker to connect to open a channel over which he could gather information about the device – Pose a serious security threat to vulnerable computers and cannot be fixed by patches to the operating systems Security+ Guide to Network Security Fundamentals, Third Edition 47 Other Attacks and Frauds (continued) • Check kiting – A type of fraud that involves the unlawful use of checking accounts to gain additional time before the fraud is detected • Domain Name Kiting – Registrars are organizations that are approved by ICANN to sell and register Internet domain names – A five-day Add Grade Period (AGP) permits registrars to delete any newly registered Internet domain names and receive a full refund of the registration fee Security+ Guide to Network Security Fundamentals, Third Edition 48 Other Attacks and Frauds (continued) • Domain Name Kiting (continued) – Unscrupulous registrars attempt to take advantage of the AGP by registering thousands of Internet domain names and then deleting them – Recently expired domain names are indexed by search engines – Visitors are directed to a re-registered site • Which is usually a single page Web with paid advertisement links – Visitors who click on these links generate money for the registrar Security+ Guide to Network Security Fundamentals, Third Edition 49 Summary • Network vulnerabilities include media-based vulnerabilities and vulnerabilities in network devices • The same tools that network administrators use to monitor network traffic and troubleshoot network problems can also be used by attackers • Network devices often contain weak passwords, default accounts, back doors, and vulnerabilities that permit privilege escalation • Network attacks can be grouped into four categories Security+ Guide to Network Security Fundamentals, Third Edition 50 Summary (continued) • Protocol-based attacks take advantage of vulnerabilities in network protocols • Attacks on wireless systems have increased along with the popularity of wireless networks • Other network attacks include null sessions, which are unauthenticated connections to a system using a legacy version of Microsoft windows • Domain Name Kiting is fraud that involves the use of a grace period to delete newly registered domain names Security+ Guide to Network Security Fundamentals, Third Edition 51