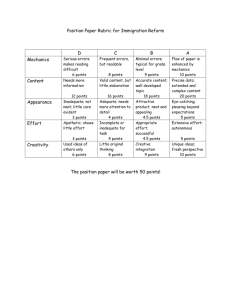
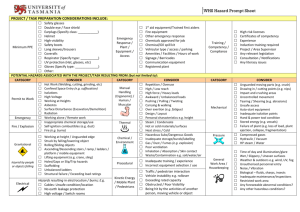
The Evolving Role of NHS SIRO and IAO

The Evolving Role of the NHS SIRO and IAO
Please read the information pack that has been placed on your chair before we start
Housekeeping
• Fire alarms
• Exit routes and assembly point
• Toilets
• Mobile phones
• Smoking areas
• Refreshments
• Questions
Agenda
• Welcome and session introduction
• Session 1 – The Roles and Responsibilities (45mins)
• Session 2 – Acute Case Study One (45mins)
• Break
• Session 3 – PCT Case Study Two (45mins)
• Close of session and opportunity for Q&A
Introductions
• Presentation team
• Attendees
• Aims of today’s event
Why is it important that you are here?
• Public, professional, organisational and political confidence in our ability to protect sensitive personal and business data is vital
• Information risk management is deceptively easy
• Improving information risk management at an enterprise level can involve changing cultures, processes and technologies across an organisation
• Benefits are hard to measure
Driving Business Benefits
Repeating disparate information risk management techniques across the organisation is inefficient and unlikely to succeed because:
• Securing one system often requires changes to others
• Investment in one system may undermine security in another
• Overall performance may be constrained by factors such as style of information governance, cultural attitudes, HR policies and compliance monitoring
– These factors need to be addressed across the organisation rather than at the system level
• Costly
– There are economies of scale
Mitigating Information Risk
Data breaches to incur up to £500,000 penalty
“New powers, designed to deter personal data security breaches, are expected to come into force on
6 April 2010. The Information Commissioner’s Office
(ICO) will be able to order organisations to pay up to
£500,000 as a penalty for serious breaches of the
Data Protection Act”.
ICO Press release 12/1/10
IA Delivery Model
Roles
Accounting Officer
Senior Information
Risk Owner
Information Asset
Owner(s)
Information Asset
Administrator(s)
NHS Trust
Chief Executive
Board Level SIRO
Department Heads
Operational
Managers
General
Practice
PCT Chief
Executive
PCT SIRO
Senior Partner
Practice Manager
The role of the SIRO
“ The NHS SIRO should be a member of the Trust Board, or equivalent level within NHS organisations without Boards, who is responsible to ensure organisational information risk is properly identified and managed and that appropriate assurance mechanisms exist.”
The role of the IAO
Information Asset Owners:
• are directly accountable to the
SIRO in this role
• must provide assurance information risk is managed effectively for the information assets that they ‘own’
• may ‘own’ several assets that include components used in assets of other IAOs e.g. shared hardware and software
The supporting role of IAAs
Information Asset Administrators
(IAA) are:
• Usually operational managers who are familiar with information risks in their area or department e.g. Security managers, Records
Managers, DP Officers, Internal
Audit, Department Heads, etc
Relationships
SIRO
Risk Policy
Risk
Management
IG Activities
Assurance
IAO IAA
Components of an Information
Asset
Personal Information Content
Databases and data files
Back-up and archive data
Audit data
Paper records (patient case notes and staff records)
Paper reports
Software
Applications and System Software
Data encryption utilities
Development and Maintenance tools
Other Information Content
Databases and data files
Back-up and archive data
Audit data
Paper records and reports
System/Process Documentation
System information and documentation
Operations and support procedures
Manuals and training materials
Contracts and agreements
Business continuity plans
Hardware
Computing hardware including PCs,
Laptops, PDA, communications devices eg. blackberry and removable media
Miscellaneous
Environmental services eg. power and air-conditioning
People skills and experience
Shared service including Networks and
Printers
Computer rooms and equipment
Records libraries
Positioning Information Risk
• Information Risk Assurance &
Management (IRA&M) must be considered in a structured way alongside other NHS business risk:
– All NHS organisations should have the means to effectively identify, assess and address their information risks
– Evidence of risk consideration will allow a proportionate response
Business Impact Analysis
Business Impact Analysis (BIA) is:
• A formal mechanism to help identify essential functions and assets
• A key stage of the IRA&M process
• Essential to understand the business values, dependencies and impacts that affect an information asset
Staff Training and Awareness
• Critical issue for the effective management of information risk
• All staff and contractors who have access to personal data must undergo annual training concerning information risk awareness
• The SIRO should verify a process exists to ensure staff and contractors receive this training on induction and annually thereafter
Audit
• The DH-ID IG Policy and Planning team have been working with the Audit Commission to develop an ‘Audit
Handbook’.
• The handbook will describe the audit requirements in detail and is due to be released in conjunction with the IG
Toolkit version 8, due end of June 2010.
Information Risk
Considerations for Boards
• “What have we done as a board to understand the information risks that we are accountable for managing?”
• “What were the outcomes of our most recent reviews of the risks to our key information assets and have all reasonable steps to mitigate against these risks been taken?”
• “Do we, as an organisation board, have the capacity and capability to ensure that information incidents are quickly identified and effectively managed with lessons learned appropriately?”
End of Session 1
Acute Scenario
NHS Information Governance
Background
• A small Acute Trust hospital trust, would have been a district general at one time
• Has less than 2000 staff, many long serving
• Mainly new executive directors with little corporate memory
• Some long serving clinicians are finding it difficult to adjust to the new competitive health economy and are resistant to change
• Robust Information Governance in IT, but keen to improve, aware of some weaknesses and in the process of recruiting additional resources
Incident
• The GUM clinic Office Administrator makes an initial call for assistance in the management of scanned records to the ICT Helpdesk
– This was prompted by her return from long-term sickness, the departure before her return of the temp, who destroyed/disposed of information before she left and provided no handover
• The ICT helpdesk engineer identifies this as a possible new data flow and in need of investigation
• A helpdesk alert is issued to the Information Security
Manager for further investigation
Investigation
Interview with the Office Manager identified key issues:
• Historically records for specific clinics have been subject to special treatment as a response to limited on storage space
– Records considered not sensitive as patients in GUM clinics are given the opportunity to give a false identity
• A supplier had been requested (there was no contract) to:
– Collected paper files
– Scanned them to a digital image
– Destroyed the paper files
– Returned scanned images
Report 1
Procurement
• There was no copy of a contract or any agreement between Trust and supplier
• There was no confirmation from the supplier of compliance with national requirements
– The supplier subsequently provided assurances that their system would comply with national guidelines
Records Management
• There was no protocol for the selection or logging of records given to the supplier. Approximately 70 records had been handled by the supplier for a trial run
• There was no record of the individual files sent
• There was no confirmation of file destruction
• There was no record or correlation of the files returned.
• There was no record of checking the quality of the images
Report 2
Training
• The Office Manager had completed the Trust’s own E-learning
Module on confidentiality
• The Office Manager had not completed the E-learning Module on the Information Security Policy
Immediate Actions
• The Office Manager has been advised to halt any further removal of records until the issue had been resolved
• The Office Manager has requested the return of the CDs held by the proposed new supplier of the test batch of records
• The Security Manager to engage with the proposed new supplier to establish whether or not the test batch of records had already been destroyed and, if so, what verification was available, and if not, get them back.
Next steps
• The Trust decided to initially declare this as a Level 2
Serious Untoward Incident, while they moved on to the next stage of investigation to establish the full scale of the incident
• The incident was recorded on the local (Datix) and external (STEIS) databases within 48 hours
• Terms of Reference for the SUI Panel were developed
Lessons Learnt 1
Fault/weakness in local system management controls:
• No evidence of involvement by other senior staff in the development of this process
• Inadequate third party support and maintenance contract in place.
• No evidence of Contract or Non-disclosure agreement in place
Lessons Learnt 2
Ineffective operational system management arrangements in place:
• No evidence of involvement by other senior staff in the development of the process for digitising GUM clinic records
• Service compromised by non-adherence to documented support procedures in central policies
• Lack of awareness of Information Security Policy, Code of Conduct for Confidentiality, Medical Records Policy and Standing Financial Orders.
• Service compromised by absence of documented support local procedures
• No guidelines or procedural documentation for the process undertaken
Lessons Learnt 3
Teamwork Shortcomings?
• Supervision was available but not sought
• No evidence provided that any advice was sought from
ICT, Finance or Medical Records in the creation of the process
Skills or Performance Deficit?
• Induction content should be reviewed with regards to the introduction of changes and the need to refer to policies and management
• The original process was develop by a previous member of staff who has since left without any handover documentation.
End of Session 2
PCT Scenario
NHS Information Governance
Background
• PCT created by merging three covering a large and rural area
• Severe financial restraints and resulting in poor relations with providers
• Mainly newly appointed executive directors with expanded and expanding portfolios.
• Inherited mixed governance / management structures and disparate legacy IT systems
• 8000+ staff; long serving, low morale, frequent management restructuring; staff co-located with local
Acutes
• Former PCTs scored between 33% to 64% in IGT; now less than 33%!
Situation
PCT A
•Registered copy
•Not in use
•Own IT Dept
PCT B
• Registered copy
• In use
• IT SLA from
Acute
• Database not covered
PCT C
• No copy
• ‘Unwritten’ IT SLA with Acute
Incident
Report categorised the incident as “Non-Patient”
• Specialist Nurse using database ‘XXX’
• Patient contact information
• Clinical assessment
• Letters to GPs
• Audit clinical performance
• Database increasingly unreliable: on the day, the database failed on 5 occasions and reported 'disc error‘
• Restarting database = rebooting computer = loss data
• Reported to Data Quality Manager in former PCT A
• Advised to report incident and send urgent email to him
Investigation
•
Database designed by GPwSI , recommended by a British
Society and used nationally, but unstable
• Clinical management tool and service auditing tool functions
• Records demographic and clinical information including admissions and nurse contacts
• Print outs are filed in Acute Health Records
•
Automated clinician letter of medications
• Patient data not stored locally, but transmitted securely to a server
• Supplier technical support very limited: updates and patches rarely available
• Local ‘workarounds’ add stability and anonymised extracts for research
Report
PCT A
•Registered copy
•Not in use
•Own IT Dept
PCT B
• Registered copy
• In use
• IT SLA from
Acute
• Database not covered
PCT C
• No copy
• ‘Unwritten’ IT SLA with Acute
In PCT A:
Data Quality Manager requests additional copy of software from IT
Dept in PCT B.
In PCT C:
•Database is set up and frequently fails.
•Failure reported by Nurse.
Requests For IT Support:
PCT B - local Acute IT will not support (not in SLA).
PCT C - local Acute IT will not support (not in SLA).
PCT A - IT Dept report unregistered database to IG Manager
Risks and Impacts
•
Risks:
•
Technical
•
Physical
•
Administrative
•
Impacts:
•
Service Provision
•
Financial
•
Reputation
•
Staff
Issues
•
Information Asset Owner and Administrators
•
SIRO
•
IAO
•
IAA
•
Information Asset
•
Identifying the Asset
•
Identifying the Owner
•
Setting the boundaries
Lessons Learnt
No. Management Conclusion
(a) (b)
1.
Information Asset
Register
SIRO/IAO
Inadequate
2.
Inadequate
Framework
3.
Operational
Management
Inadequate
4.
Governance
Inadequate
(Line management)
5.
Information Risk
Register
Inadequate
( Corporate Risk
Register)
No. Management Conclusion
(a) (b)
6.
Information Asset
Ownership
Inadequate
Inadequate
7.
IT SLA
(unwritten)
8.
Info Gov
Leadership /
Accountability
Inadequate (eg add to risk register)
9.
IG Assurance
10.
Software
Accreditation
Inadequate (eg report to
SIRO/IG SG
Inadequate
(unregistered )
Lessons Learnt
No.
System
(c)
1.
Database
2.
Data Quality
3.
4.
System
Accreditation
Introduction of new systems
Conclusion
(d)
Inadequate
(unfit for purpose)
Inadequate
(Loss of data)
Inadequate
Inadequate
No.
5.
System
(c)
Business
Continuity
Conclusion
(d)
Inadequate (No plan eg backups)
6.
Procurement
Control
Inadequate
7.
System Patching Inadequate
8.
Compatibility with Strategies
Inadequate
Lessons Learnt
No.
Process
1.
2.
(e)
Security
Procedures
Documented
Procedures
3.
Policies and
Procedures
4.
Incident
Reporting
Conclusion
(f)
Inadequate
Inadequate
Inadequate
(No PCT standard)
Adequate
No.
Process
5.
(e)
Investigation carried out
6.
7.
Findings considered
Incident
Feedback
8.
Learning from Incidents
Conclusion
(f)
Adequate
Inadequate
Inadequate
Inadequate
Lessons Learnt
No.
People
(g)
1.
IT expertise
Conclusion
(h)
Inadequate
2.
IG Awareness
(General)
Inadequate
3.
User Training Inadequate
4.
5.
Levels of
Authority
Organisational
Identity
Inadequate
Inadequate
Cultural Paradigm
STORIES
• Cures
• Villains
• Change agents are fools
• Abuse of managers
• ‘They’ say/do
RITUALS &
ROUTINES
• Consultation
• Ward Rounds
• Patient infantilising
• Pass the buck
SYMBOLS
• Terminology
• White Coats/Uniforms
• Big institutions
• Retinues
• Offices
PARADIGM
• NHS is ‘good’
• Public service
• Free at point of delivery
• Clinicians values
• Doctor knows best
POWER
• Professional bodies
• Clinicians
• Senior Executives
• Regional bodies
• Politicians
CONTROLS
• Performance reporting
• Financial reporting
• Professional responsibility
ORGANISATION
• Hierarchical
• Mechanistic
• Pecking order
• Sub-ordination
• Tribal/functional
Information Risk
Considerations for Boards
• “What have we done as a board to understand the information risks that we are accountable for managing?”
• “What were the outcomes of our most recent reviews of the risks to our key information assets and have all reasonable steps to mitigate against these risks been taken?”
• “Do we, as an organisation, have the capacity and capability to ensure that information incidents are quickly identified and effectively managed with lessons learned appropriately?”