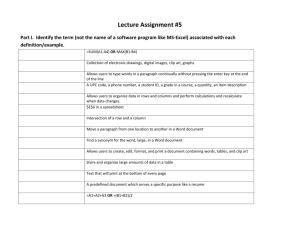
Name
Title
Group
Microsoft Corporation
Evolving Security Threat Landscape
Methods to Addressing Security Threats
Microsoft Trustworthy Computing
Addressing Security Threats with Microsoft
Next Steps
Local Area
Networks
First PC virus
Boot sector
viruses
Create notoriety
or cause havoc
Slow propagation
16-bit DOS
Internet Era
Macro viruses
Script viruses
Create
notoriety
or cause havoc
Faster
propagation
32-bit Windows
Broadband
prevalent
Spyware, Spam
Phishing
Botnets
Rootkits
Financial
motivation
Internet
wide impact
32-bit Windows
Hyper jacking
Peer to Peer
Social engineering
Application
attacks
Financial
motivation
Targeted attacks
64-bit Windows
Largest segment by
$ spent on defense
National Interest
Spy
Largest area by $ lost
Personal Gain
Largest area
by volume
Personal Fame
Curiosity
Fastest
growing
segment
Thief
Trespasser
•Vandal
Author
Script-Kiddy Undergraduate Expert
Specialist
Technology
Helps turn IT into a business asset not a cost center
Supports your day to day security processes
Is the Enabler to running your business successfully
Process
Data privacy processes to manage data effectively
IT security processes to implement, manage, and govern security
Financial reporting processes that include security of the business
People
Company understands the importance of security in the workplace
Individuals know their role with security governance and compliance
IT staff has the security skills and knowledge to support your business
Law
Enforcement
Public Policy
Consumer
Awareness
Industry
Partnerships
VIA
GIAIS
Security
Tools
Security
Readiness
Education
and Training
www.microsoft.com/technet/security
Product
Inception
Design
Threat
Modeling
Standards,
Security Push
best practices,
and tools
Final Security
Review
RTM and
Deployment
Signoff
Security
Response
Engineering Excellence
Excellence
Engineering
Security
Development Lifecycle
Lifecycle
Security Development
Trusted
Unhealthy PC
New Customer
Remediation Server
Isolated
Web
Server
Infrastructure Servers
Remote Access
Gateway
Trusted Home
Unmanaged Devices
Malicious
Users
Secure Anywhere Access
End-to-end security with IPv6 and IPsec
Access driven by policy not topology
Certificate based multi-factor authentication
Health checks and remediation prior to access
Policy-driven network access solutions
Windows Firewall with advanced filtering
Server and Domain Isolation
Network Access Protection (NAP)
ISA Server 2006
Intelligent Application Gateway (2007)
Windows Filtering Platform
Secure collaboration
Easily managing multiple identities
Government sponsored identities (eID)
Hardware supported trust platform
Disparate directories synchronization
Domain/Directory Certificate
Services
Services
ADFS
Centralized ID controls and mgmt.
Embedded identity into applications
Policy Governance / Compliance
Role Based Permissions
Identity and Data Privacy
MIIS
Authorization
Manager
RMS
Edge, server and client protection
“Point to Point” Solutions
Security of data at rest and in transit
Mobile workforce
Manageability
Corporate
Edge Protection
Server Protection
Client Protection
Consumer/ Small Business
Simple PC maintenance
Anti-Virus
Anti-Spyware
Anti-Phishing
Firewall
Performance Tuning
Backup and Restore
Industry Standards
Web Services (WS-*)
Open document format (XPS)
OpenID
Partner Products
Network Access Protection
EV Certificate support in IE7
Windows CardSpace
Windows Security Center
Industry Partnerships
SecureIT Alliance
Microsoft Security Response Alliance
Interop Vendor Alliance
Engineering Excellence
Security Development
Lifecycle
Microsoft Security Home Page: www.microsoft.com/security
Microsoft Forefront: http://www.microsoft.com/forefront/default.mspx
General Information:
Microsoft Live Safety Center: http://safety.live.com
Microsoft Security Response Center: www.microsoft.com/security/msrc
Security Development Lifecycle: http://msdn.microsoft.com/security/sdl
Get the Facts on Windows and Linux: www.microsoft.com/getthefacts
Anti-Malware:
Microsoft OneCare Live: https://beta.windowsonecare.com
Microsoft Defender (beta 2):
www.microsoft.com/athome/security/spyware/software
Spyware Criteria: www.microsoft.com/athome/security/spyware/software/isv
Guidance Centers:
Security Guidance Centers: www.microsoft.com/security/guidance
Security Guidance for IT Professionals: www.microsoft.com/technet/security
The Microsoft Security Developer Center: msdn.microsoft.com/security
The Security at Home Consumer Site: www.microsoft.com/athome/security
© 2007 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries.
The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market
conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation.
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.