DANGER** FPGA Vulnerabilities
advertisement
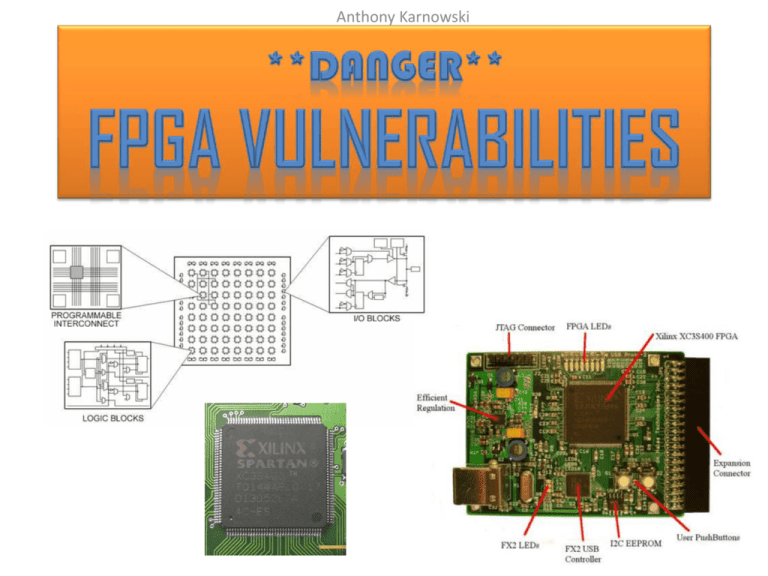
Anthony Karnowski • A field-programmable gate array (FPGA) is an integrated circuit designed to be configured by a customer or a designer after manufacturing—hence "field-programmable". The FPGA configuration is generally specified using a hardware description language (HDL), similar to that used for an application-specific integrated circuit. • The ability to update the functionality after shipping, partial re-configuration of a portion of the design and the low nonrecurring engineering costs relative to an Application specific integrated circuit design offer advantages for many applications. Basically the time in production for using this type of controller is much shorter. • • • • FPGA’s are widely used in all of the following industries and applications Aerospace and Defense • • Avionics/DO-254 • MILCOM • Missles & Munitions • Secure Solutions • Space Audio • Connectivity • Solutions • Portable Electronics • Radio Automotive • High Resultion Video • Image Processing • Vehicle Networking • and Connectivity • Automotive Infotainment Broadcast • • Real-Time Video Engine • EdgeQAM • Encoders • Displays • Switches and Routers Consumer Electronics • Digital Displays • • Digital Cameras • Multi-function Printers • Portable Electronics • • Set-top Boxes Data Center • Servers • Security • Routers • Switches • Gateways • Load Balancing High Performance Computing • • Servers • Super Computers • SIGINT Systems • High-end RADARS • • High-end Beam Forming Systems • Data Mining Systems Industrial • Industrial Imaging • • Industrial Networking • Motor Control Medical • Ultrasound • CT Scanner • • MRI • X-ray • PET • Surgical Systems Security • Industrial Imaging • Secure Solutions • Image Processing Video & Image Processing • High Resolution Video • Video Over IP Gateway • Digital Displays • Industrial Imaging Wired Communications • Optical Transport Networks • Network Processing • Connectivity Interfaces Wireless Communications • Baseband • Connectivity Interfaces • Mobile Backhaul • Radio • The FPGA industry is a 2.75 billion dollar a year industry. – Considering the low cost of FPGA’s, and the fact that there are in so many devices, we will just say ALOT!! • We will be looking at a specific FGPA later. – 50,000 of these units are produced a year and have been for the last 5 years. – These FPGA’s are specifically used in large format LED signage. • FPGA’s are physically vulnerable. –FPGA’s can be easily flashed by Jtag connection. –Flash protocols are some time vendor specific, we are not going to in depth. • FPGA’s often have vulnerable services. –FPGA’s operating systems often offer backdoor services for re-flashing. Company Product Processor ENEA Embedded Technology OSE PowerPC® 405 eSOL Co., Ltd PrKernel (µITRON4.0) PowerPC 405 / MicroBlaze™ Express Logic ThreadX® PowerPC 405, 440 / MicroBlaze Green Hills Software Integrity® PowerPC 405, 440 LynuxWorks BlueCat Linux PowerPC 405, 440 LynuxWorks LynuxOS PowerPC 405 Mentor Graphics ESD Nucleus Plus PowerPC 405, 440 / Microblaze Micriµm µC/OS-II PowerPC 405 / MicroBlaze MiSPO NORTi/ulTRON PowerPC 405 / MicroBlaze MontaVista Software MontaVista Linux PowerPC 405, 440 PetaLogix uClinux and Petalinux 2.6 MicroBlaze QNX Neutrino® PowerPC 405 Wind River Systems VxWorks® PowerPC 405, 440 Wind River Systems Wind River GPP Linux PowerPC 405, 440 Timesys LinuxLink PowerPC 405, 440 • • FPGA’s are made by the manufacturer to be “field programmable.” – This means that usually the device can be flashed by physically connecting to the device. – Some third party operating systems allow for a flash to be reset to defaults by way of a system service. A great example would be of both would be a wireless router. – Most wireless routers have a reset button to reset the router to defaults. – Most routers also have a web-based management system that allows the same. – Most routers even have a configuration page to load firmware. – And most routers are using some sort of FPGA controller • Consider that most of these third party operating systems are based on open source technologies or are freely available to users. It is pretty easy to get an understanding of vulnerabilities in a device. I would suspect that some of the students in this course have loaded third party firmware on a router at some point. When dealing with another FPGA, the ideas are no different. External Storage in form of USB. RJ-45 and JTAG Connection External Storage in form of Compact Flash. External Storage in form of SD Card. FPGA Controller • We don’t have access to the device to Flash via the JTAG. – The controller is under lock and Key. • After a couple of scans we found that our device has many services running. – FTP – HTTP for configuration – Telnet – SSH As this kernel is Linux based, we may be able to install and run a full installation of Metasploit. As this is a full Linux kernel, a worm or virus could also be ran via root privileges. • We have guessed the root username and password for this device. • We connected via telnet and can run any of the following commands from the existing Linux kernel. • We have at least one storage device available to us. • If this device is on a network with other computers, we will be able to mount an attack from the device. • We will use wget to download the necessary packages. • We will store them to external storage. • We will use make and install to build source packages. • We will attack the network. • We will use FTP to send data collected off network. • The first thing we do is create a separate user for the software package to use. • We edit the software to only have access to needed services. • The next thing we do is add a stronger password for the root user. • We always try to present the end customer with a closed network separate from their network. • If we install on the network we deny the controller access to the Internet. • Yes. • Other devices have some of the same services installed and running for diagnostics and communications. • FPGA’s are used in a wide variety of networking equipment. • We must maintain the security of FPGA’s to maintain our networks. • Please be weary. • ECEs spot FPGA security weakness; Finding may lead to new chip ID – http://www.ece.vt.edu/news/ar08/weakfpga.html • US Military Chips "Compromised” – http://www.technologyreview.com/view/428029/us-military-chipscompromised/ • Study looks into Xilinx FPGAs' vulnerability – http://forum.eetindia.co.in/view_comments.jspa?entry_id=8836&from=RS S • Backdoor Found (Maybe) in Chinese-Made Military Silicon Chips – http://www.schneier.com/blog/archives/2012/05/backdoor_found.html