A Framework for Dynamic Routing and Operational Integrity
advertisement

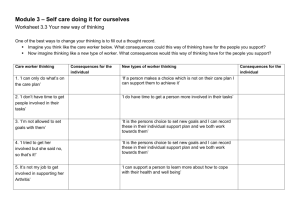
WMS systems manage and coordinate several independent subtasks. The coordination problems get even more serious when the subtasks are performed on separate systems. SYSTEM ARCHITECTURE FOR WMS : . 1) The flow of information in an organization occurs by means of documents (e.g., purchase order request, travel authorization request, etc.), which are passed through various individuals. Each individual performs operations on the document such as: fill in some fields, modify fields, etc. 2) This form then goes to a secretary who reviews it, and enters information on previous business travel by the employee. 3) Next, the form is sent to the manager who approves or disapproves the requested amount. Alternatively, the manager may approve a smaller amount than requested. 4) Finally, the form is returned to the individual concerned and the secretary to notify them of the decision. PROBLEMS : CONTROL AUTHORIZATION Three techniques for handling workflow control & authorization: 1) workflow control matrices : defines the relationship between two operations that can be performed in a temporal sense. 2) sequence constraints : consists of techniques for imposing and enforcing constraints on the routing sequence of the workflow, i.e., the sequence in which a document is sent to various employees 3) event-based constraints : event-based constraints which can be used to specify unusual routing needs and other special actions. These techniques can : can exploit parallelism, lead to more efficient processes Do better workflow systems can handle various kinds of exception situations that arise in workflow applications. The objective of our framework is to complete a list of tasks with respect to each document subject to a set of sequence constraints while providing support for dynamic routing and operational integrity control. Dynamic routing : routing a document in a dynamic manner subject to certain constraints. There is no predefined order as in static routing. Operational integrity control : refers to imposing restrictions on the permissibility of various operations that may be performed on various fields of a document by different individuals as the document travels through the organization. The WMS routes the documents to work baskets while workers interact with the documents through the work baskets assigned them. Three types of work baskets: document-based : each basket contains a particular type of document, and every worker accesses the same document in the same basket & are hard to use for routing documents. worker-based : contain all documents assigned to the same worker. Routing of documents can be done after a document is processed by moving documents from the basket of one worker to the basket of another. inflexible as modification to the routing mechanism is needed when a worker is absent or leaves the company. rolebased : contains similar documents that must be worked upon by workers performing a specific role. Any worker belonging to that role can process the documents in the basket. When a worker starts processing a document, the document is locked so that no one else can access it. Role-based baskets are most suitable for supporting dynamic routing because no change to the routing mechanism is needed when a worker leaves the system or is reassigned. The following terms to describe the workflow process and to develop the control and authorization mechanisms. 1) document (d): A statement or form that is needed for a business transaction, e.g., a billing statement or a travel authorization form. 2) field (f): Any data element contained in a document that has a numerical or symbolic value. 3) worker (w): Any person who performs operations on documents using the workflow management system. 4) roLe (r): A generic identifier for a group of workers, any one of whom may perform a task assigned to the “role”. 5) work basket (b): A unique, logical box associated with a role. Each work basket contains a stack (or queue) of documents waiting to be processed by a worker in the corresponding role. 6) operation (0): The smallest unit of work, e.g.,enter a data value into the amount field on a form. 7) Tusk (t): A collection of operations that corresponds to a step in a common business process, e.g., fill in the customer request form. 8) sequence dependency (s): Two tasks that must be performed by different roles in a given sequence create a sequence dependency. Proper routing of documents to various workers is by far the most important function of the workflow management system & is achieved by means of sequence constraints that impose dependencies between tasks on a document. The proper routing of a document is achieved by controlling the sequence in which a document is accessed by various roles. The operational integrity is maintained by placing restrictions on the kinds of operations (e.g., read, enter, modify, etc.) that a worker in a given role is allowed to perform on fields of a document. This is done by keeping a workflow control matrix that specifies the permissible operations that can be performed by a given role. Once a document is accessed by a worker, he or she will be notified of the permissible operations by the system. Eventbased constraints can be used to trigger special actions to take place especially when an unusual event Occurs. The workflow manager moves the documents among the baskets after each task is completed by consulting the control matrices, the sequence constraints, and the event-based constraints. This is how the system does automatic authorization and control of access and operations. The workflow control matrix restricts the operations that a worker in a certain role may perform on a document. This matrix is sequence independent but it is possible to enforce a sequence of operations between a pair of employees. An alternative, and possibly more concise, way of specifying the permissions is by means of explicit statements such as: Permission([ROLE].DOC[.FIELD].[OP] )=y /n. The default value of all permissions would be “n”, unless explicitly overridden by a permission statement. If the role entry (in the above syntax) is missing, then the statement would apply to all roles. Similarly, if the field or operation entry is missing, the statement would apply to all fields or operations. When a document moves within the organization, the sequence in which changes (or updates) are made to it is recorded, and is called the document history. If the exact sequence that a document must take each time is known before hand, it can be specified as a complete ordering; however, in general, the sequence can change because alternative paths might be acceptable, certain steps might not be essential, or an employee might be absent, etc. Therefore, the goal of sequence maintenance is to provide a mechanism whereby a set of constraints can be used to define a partial ordering on the document history and the workflow management system would enforce those constraints. A document history is considered legitimute or admisszble if none of the constraints is violated. Classified as : (1) time-based condition based on elapsed time eg : IF AGE(doc1D) > 10 THEN SEND(doclD,*,blO) (2) access pattern of a document eg : IF REWORK(w5,docID) = 5 THEN NOTIFY(docID, “rework 5 times” ,w5, bll) (3) combination of access pattern and elapsed time eg : IF AGE(doc1D) > 10 AND SEND( docID ,*,b10). REWORK(w5,docID) >2 THEN (4) special conditions that depend upon field values eg : IF VALUE(docID.fl) > 10000 THEN ROUTE( docID ,b 10) (5) special conditions that depend upon changes made to field values eg IF INC(docID.fl) > 5000 THEN ROUT E (do CID, b 10). THANK YOU !!