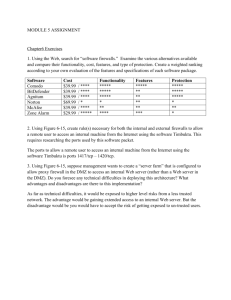
Network Security Fundamentals
Chapter 2:
Network and Server
Security
Understanding Protocols
• Protocol: Formal set of rules that describe how
computers transmit data and communicate across
network
• Layered architecture
– Protocols arranged in stack of layers (network stack)
– Data passed from highest to lowest layer when sending
transmission
– Data passed from lowest to highest layer when receiving
transmission
• Data encapsulation: Protocols and standards at
each layer attach information to data as it passes
through layer
Network Stack and Data Encapsulation
OSI Model
• Open Systems Interconnect (OSI)
reference model
– Provides basis for communication among
computers over networks
• Seven layers: Application, Presentation,
Session, Transport, Network, Data Link,
Physical
• Mnemonic: All People Seem To Need
Data Processing
OSI Model
• Application layer
– Provides services such as email, file
transfers, and file servers
– Protocols include: FTP,DNS, SMTP
• Presentation layer
– Provides encryption, code conversion,
data formatting
– Standards include: MPEG, HTTP, JPEG
OSI Model
• Session layer
– Negotiates and establishes connection
with another computer
– Protocols include: ASP, NFS, RPC
• Transport layer
– Supports reliable end-to-end delivery of
data
– Protocols include: TCP, SCTP, UDP,
SPX
OSI Model
• Network layer
– Performs packet routing across networks
– Protocols include: IP, ICMP, RIP, ARP
• Data Link layer
– Provides error checking and transfer of
message frames
– Two sublayers:
• Media Access layer
• Logical Link layer
– Protocols include: SLIP, PPP
OSI Model
• Physical layer
– Defines standards for:
• Transmission media
• Physical connection to media
• How data should be sent over network
– Addressed in IEEE 802 LAN/WAN standards,
e.g.:
• 802.2 Logical Link Control
• 802.3 Ethernet (CSMA/CD)
• 802.5 Token Ring
TCP/IP Model
• Uses packets that can be routed around broken
connections and reassembled at receiving end
• TCP: Verifies correct delivery, provides error
correction
• IP: Responsible for sending packets from node to
node to destination
• IP addresses
– Used for routing
– Two standards
• IPv4
• IPv6
TCP/IP Model
• IPv4 address: 4-byte destination IP
address, e.g.: 160.192.226.135
– Two portions
• Network portion: Network class (A – E) determines
portion of IP address used for network address
• Host (node) portion
• IPv6 address: 128-bit addressing
– 8 sets of 4 hexadecimal numbers
– Provides additional security features
TCP/IP Model Layers
• Layer 4: Application
– Equivalent to OSI Application,
Presentation, and Session layers
• Layer 3: Host-to-Host (Transport)
– Similar to OSI Transport
– Performs packet sequencing, supports
reliable end-to-end communications,
ensures data integrity, provides for
error-free delivery
TCP/IP Model Layers
• Layer 2: Internet
– Same function as OSI Network layer
– Manages connections across network
– Provides for logical transmission of packets over
network, assigns IP addresses to host
• Layer 1: Network Access
– Combines OSI Data Link and Physical layers
– Functions include mapping IP addresses to MAC
addresses, encapsulation of IP datagrams into frames
– Concerned with hardware, software, physical
transmission of data
TCP/IP Encapsulation
TCP/IP Ports
• Ports: Number included in packet header
– Used by TCP/IP protocols when transmitting
data
– Recipient computer uses port number to
identify service that should process packet
• Well-known ports
– Ports 0 – 1024
– Assigned to specific service, i.e. HTTP uses
port 80
• Ports 1025-65000 can be assigned to
custom applications
Viewing Ports with netstat -a
Best Practices for Network Security
• Basic guidelines for securing servers
on network
– Designing applications with security in
mind
– Maintaining security mindset
– Defense-in-depth
Security by Design
• Much more costly, time-consuming to build
in security after application deployment
• Difficulties in incorporating security in
design phase
– Community differences between software
designers and security professionals
– Lack of publicity of security threats
– Each application is essentially new coding
– Lack of justification for costs, time from
managerial perspective
– Rush-to-market approach
Maintaining a Security Mindset
• Base security decisions on risk
• Use defense-in-depth, using many
security controls
• Keep things simple
• Respect (do not underestimate)
adversary
• Work on security awareness
• Be paranoid
Defense-in-Depth
• Multiple lines of defense
– Series of protective measures that,
taken as whole, secure the environment
• All security resources should not be
concentrated on single protection
• Protective measure (security control)
is worth implementing even if
seemingly redundant
Securing Servers
• To operate server securely,
organization must establish plan that
addresses key security aspects
– Controlling server configuration
– Controlling users and access
– Monitoring, auditing, and logging
Controlling Server Configuration
• Most important considerations in
securing host system
– Physically secure system in locked
room and limit access
– Limit attack surface: Minimize risk by
removing unneeded services, ports,
input/output devices
– Back up host system to mitigate risk
Controlling Server Configuration
• Physical security of system
–
–
–
–
–
–
Uninterruptible power supply (UPS)
Fire protection
Cooling, ventilation
Adequate lighting, workspace in server space
Restrict physical access
Includes protection of other critical devices
(cabling, routers)
Controlling Server Configuration
• Minimizing services
– Attackers look to break in through services
– Separation of services: Each major service
should run on own protected host when
possible
– Many operating systems enable services by
default
– Typical services to disable include: Telnet,
SMTP, TFTP, Finger, Netstat, Systat, Chargen,
Echo, DNS, RPC
Controlling Server Configuration
• Managing Windows services
– Services utility: Configures enabling or
disabling services on startup
– Service dependencies: Some services depend
on others to operate
– Attackers may replace legitimate service, so
use account with most restrictive permissions
to permit service to operate
• Three built-in accounts
– Local System, Local Service, Network Service
Managing Windows Services
Dependencies of World Wide Web
Publishing Service
Setting a Service’s Log On Account
Controlling Server Configuration
• System backups
– Regularly scheduled as part of normal
operation of server
– Frequency determined by how critical
data or service is
• Determined by risk and business impact
analysis
– Failover system: Identical copy of server
and data
Border Security
• Border security: Implementing security for
different network segments
• Devices used for regulation and control
–
–
–
–
Routers
Switches
Bridges
Multi-homed gateways
Segmenting a Network
• Key network segments
– Public networks
• Allow access to everyone, e.g. Internet
– Semi-private networks
• Sit between public and private networks
• Typically exclusive subnets of large public networks
– Private networks
• Organizational networks handling confidential and
proprietary data
• May have exclusive addressing and protocols
Perimeter Defense
• Typical defenses
– Firewalls: Placed at terminal ends of every network
segment
– Specialized application proxies
• Demilitarized zones (DMZ)
– Perimeter or screened network
– Noncritical yet secure region generally designed at
periphery of internal and external networks
– Typical location for resources that must be accessed
from both Internet and internal network, i.e. Web servers
and FTP servers
Perimeter Defense Between
Private Network and Internet
Web Server in a DMZ
Firewalls
• Firewalls
– Used to secure connections to
unsecured network such as Internet
– Provide defense against:
•
•
•
•
Poor authentication
Weak software
Spoofing
Scanners and crackers
Firewalls
Firewalls
• Packet-filtering firewalls
– Use filters (rules) to determine which packets should be
allowed, based on metrics such as: IP addresses,
contained protocols
• Stateful packet-filtering (inspection) firewalls
– Connection information maintained in state tables
– Validated packets forwarded based on rule set defined
for particular connection
• Application proxy firewalls
– Shielding and filtering mechanism between public and
private networks, allowing complete shielding of
applications
Comparison of Firewall Technologies
Network Address Translation
• Network Address Translation (NAT)
– Service that translates internal, private
addresses into routable addresses on
public network
– Translation table: Allows single public IP
address to be mapped to multiple
private IP address
• Outside packets require public address and
port number to reach particular host on
private network
NAT Methodology
Summary
• Protocol: Formal set of rules describing how
computers transmit data and communicate across
network.
• Network stack: Stack of layers that divide network
functions; with protocols and standards
performing specific functions at each layer.
• As data passed through each layer, data
encapsulation process attaches information to
data packets.
• OSI reference model: Framework for network
communication with seven layers: Application,
Presentation, Session, Transport, Network, Data
Link, and Physical.
Summary
• TCP/IP Network Model has four layers:
Application, Host-to-Host (Transport),
Internet, and Network Access.
• TCP verifies correct delivery of data and
provides error detection capabilities. IP is
responsible for routing packets, using IP
addresses.
• General guidelines for implementing best
security practices include: Designing
applications with security in mind,
maintaining security mindset, and
implementing defense-in-depth.
Summary
• Key aspects of securing network servers include
controlling server configuration, controlling users
and access, and monitoring, auditing, and
logging.
• Three important considerations in controlling
server configuration include (1) physically
securing and protecting server, (2) minimizing risk
by removing unneeded services, ports, and
input/output devices, and (3) performing regular
backups of host system.
• Border security: Implementing security for
different network segments by erecting borders
that can only be crossed by certain types of traffic.
Summary
• Types of network segments include public, semiprivate, and private networks.
• Firewalls: Devices used to prevent unwanted
traffic and secure network perimeter; placed at
connection point of insecure network and internal
network.
• Types of firewalls: Packet-filtering firewalls,
stateful packet filtering (stateful inspection)
firewalls, and application proxy firewalls.
• Network Address Translation (NAT): Translates
private addresses into routable addresses on
public networks.
Key Terms
• Address Resolution Protocol
(ARP)
• American Standard Code
for Information Interchange
(ASCII)
• AppleTalk Session Protocol
(ASP)
• Application layer (OSI
model)
• Application layer (TCP/IP
model)
• Application proxy firewall
• Berkeley Internet Name
Domain (BIND)
• BootP
• Border security
• Broadcast packet
• Chargen
• Connectionless protocol
• Connection-oriented
protocol
• Crackers
• Data encapsulation
Key Terms
•
•
•
•
•
•
•
•
Data Link layer
Defense-in-depth
Demilitarized zone (DMZ)
Digital Network Architecture
Session
Control Protocol (DNA-SCP)
Domain Name System
(DNS)
Echo
Extended Binary-Coded
Decimal Interchange Code
(EBCDIC)
• Failover system
• File Transfer Protocol
(FTP)
• Filter
• Finger
• Headless server
• Host-to-Host layer
• Hypertext Transfer
Protocol (HTTP)
• Internet Control Message
Protocol (ICMP)
• Internet layer
Key Terms
• Internet Protocol (IP)
• Internet Protocol Security
(IPsec)
• Internetwork Packet
Exchange (IPX)
• IP address
• Joint Photographic Experts
Group (JPEG)
• Layered architecture
• Limiting the attack surface
• Local Service account
• Local System account
• Logical Link layer
• Media Access Control
(MAC) address
• Media Access layer
• Motion Picture Experts
Group (MPEG)
• Multicasting
• Multicast packet
• Multipurpose Internet Mail
Extensions (MIME)
• Need-to-access
environment
Key Terms
• Need-to-know environment
Netstat
• Network Access layer
• Network Address
Translation (NAT)
• Network File System (NFS)
• Network layer
• Network Service account
• Network stack
• Open Shortest Path First
(OSPF)
• Open Systems
Interconnect (OSI) model
• Packet filtering
• Packet sniffer
• Perimeter network
• Personal firewall
• Physical entry point
• Physical layer
• Ping
• Ping of death
Key Terms
• Point-to-Point Protocol
(PPP)
• POP3
• Port
• Port scanner
• Post Office Protocol (POP)
• Presentation layer
• Private network
• Promiscuous mode
• Protocol
• Protocol analyzer
• Proxy agents
•
•
•
•
•
•
•
•
Public network
Remote access server
Remote login
Remote Procedure Call
(RPC)
Reverse Address
Resolution Protocol
(RARP)
Rlogin
Routing Information
Protocol (RIP)
Rule base
Key Terms
• Ruleset
• Screened subnet
• Secure File Transfer
Protocol (SFTP)
• Secure Shell (SSH)
• Semi-private network
• Separation of services
• Sequenced Packet
Exchange (SPX)
• Serial Line Internet Protocol
(SLIP)
• Session Control Protocol
(SCP) Session layer
• Simple Mail Transfer
Protocol (SMTP)
• Simple Network
Management Protocol
(SNMP)
• Slogin
• Sockets
• SSH-2
• Stateful inspection
Key Terms
•
•
•
•
•
•
•
•
Stateful packet filtering
State table
Systat
Tagged Information
File Format (TIFF)
TCP/IP model
Telnet
Translation table
Transmission Control
Protocol (TCP)
• Transport layer (OSI
model)
• Transport layer
(TCP/IP model)
• Trivial File Transfer
Protocol (TFTP)
• Unicast packet
• User Datagram
Protocol (UDP)
• Well-known ports
Copyright Notice
Copyright 2008 John Wiley & Sons, Inc.
All rights reserved. Reproduction or translation of this
work beyond that permitted in section 117 of the 1976
United States Copyright Act without express
permission of the copyright owner is unlawful.
Requests for further information should be addressed
to the Permissions Department, John Wiley & Sons,
Inc. The purchaser may make back-up copies for
his/her own use only and not for distribution or resale.
The Publisher assumes no responsibility for errors,
omissions, or damages caused by the use of these
programs or from the use of the information herein.