Network Security Assignment: Firewalls & DMZ Configuration
advertisement
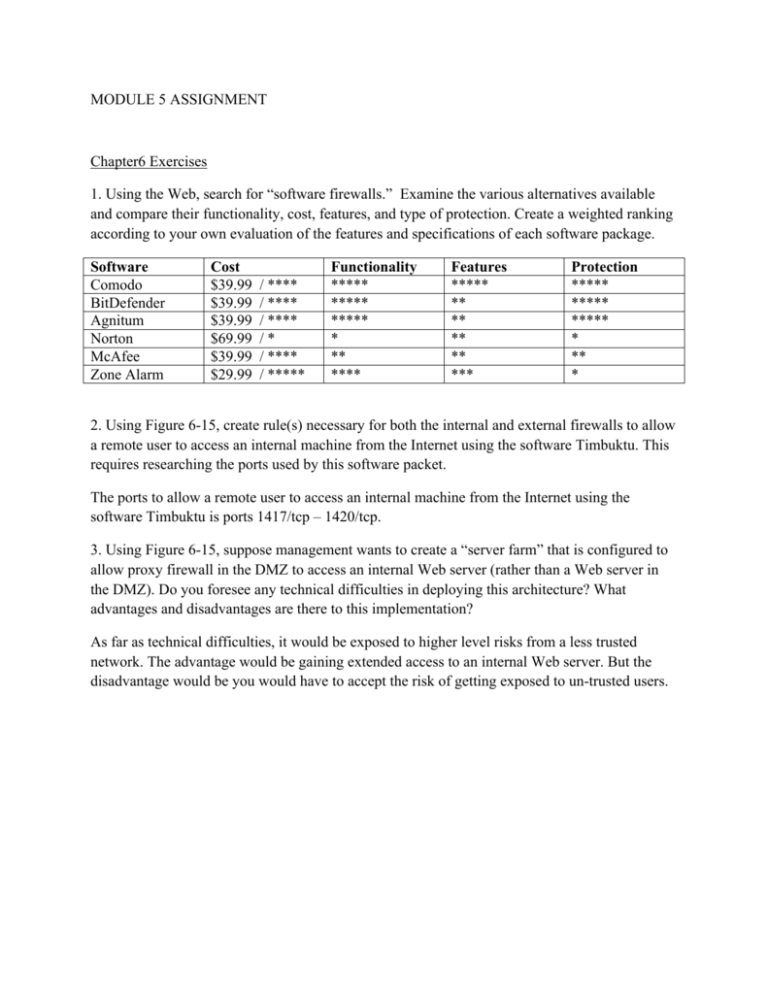
MODULE 5 ASSIGNMENT Chapter6 Exercises 1. Using the Web, search for “software firewalls.” Examine the various alternatives available and compare their functionality, cost, features, and type of protection. Create a weighted ranking according to your own evaluation of the features and specifications of each software package. Software Comodo BitDefender Agnitum Norton McAfee Zone Alarm Cost $39.99 $39.99 $39.99 $69.99 $39.99 $29.99 / **** / **** / **** /* / **** / ***** Functionality ***** ***** ***** * ** **** Features ***** ** ** ** ** *** Protection ***** ***** ***** * ** * 2. Using Figure 6-15, create rule(s) necessary for both the internal and external firewalls to allow a remote user to access an internal machine from the Internet using the software Timbuktu. This requires researching the ports used by this software packet. The ports to allow a remote user to access an internal machine from the Internet using the software Timbuktu is ports 1417/tcp – 1420/tcp. 3. Using Figure 6-15, suppose management wants to create a “server farm” that is configured to allow proxy firewall in the DMZ to access an internal Web server (rather than a Web server in the DMZ). Do you foresee any technical difficulties in deploying this architecture? What advantages and disadvantages are there to this implementation? As far as technical difficulties, it would be exposed to higher level risks from a less trusted network. The advantage would be gaining extended access to an internal Web server. But the disadvantage would be you would have to accept the risk of getting exposed to un-trusted users.