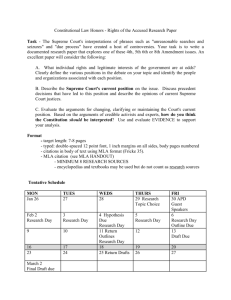
Courts Neg -- MAGS Lab - University of Michigan Debate Camp Wiki
advertisement

Page 1 Courts Fail Page 2 Circumvention --- 1st Amendment First Amendment cases fail --- even if the aff fiats First Amendment for the chilling effect, future courts will default to the original pretrial jungle of restrictions for plaintiffs Lynch 7 --- J.D. (Matthew, “CLOSING THE ORWELLIAN LOOPHOLE: THE PRESENT CONSTITUTIONALITY OF BIG BROTHER AND THE POTENTIAL FOR A FIRST AMENDMENT CURE”, 5 First Amend. L. Rev. 234, Lexis)//trepka IV. Claim No. 3: Old Reliable, Sometimes - The First Amendment If the Fourth Amendment and the due-process right to privacy cannot slay the Orwell Act, its opponents may look to a more creative approach utilizing the most sacred of constitutional rights: the rights to free speech and association under the First Amendment. Such an approach may seem counterintuitive considering that opponents to privacy-enhancing statutes, such as news reporters, often challenge them on First Amendment right-of-access or right-to-publish-information grounds. n77 Indeed, in The Death of Privacy?, Michael Froomkin details a frightening array of government and private surveillance technologies and efforts before asking whether a statute to restrict such efforts would [*258] pass First Amendment scrutiny. n78 But he does not discuss whether the First Amendment might actually require protection from surveillance, or at least from surveillance by the government. This omission is not unwarranted. Cases challenging government surveillance on First Amendment grounds are relatively rare , and such cases rarely reach the merits of the First Amendment claim. Considering the extensive and widely condemned history of federal government surveillance throughout the Twentieth and early Twenty-First Centuries, this fact is nothing less than remarkable. n79 Nevertheless, like the right to privacy, dicta in some cases suggest that a First Amendment objection to the Orwell Act may find some success if it can reach the merits. Perhaps the most optimistic dictum comes from Keith, a Fourth Amendment case: The price of lawful public dissent must not be a dread of subjection to an unchecked surveillance power. Nor must the fear of unauthorized official eavesdropping deter vigorous citizen dissent and discussion of Government action in private conversation. For private dissent, no less than open public discourse, is essential to our free society. n80 Unfortunately for the Anti-Orwellians, the case did not go as far as this statement suggests; the Court merely ruled that the government must follow the warrant requirement to conduct surveillance under its powers over domestic security. n81 As discussed above, the Fourth Amendment's warrant requirement has eroded since Katz. n82 Despite this subsequent shift in the Fourth Amendment, the language above suggests a spirit of judicial suspicion of government surveillance as to the First Amendment - a spirit that points to the unconstitutionality of the Orwell Act. But first, the Anti-Orwellians must traverse the uncertain pretrial jungle of standing. standing issue presents unique problems for Anti-Orwellians because the Orwell Act does not fit the mold of most laws that fall victim to the First Amendment. By its terms, the Act does not criminalize any speech, nor does it compel any citizen to profess beliefs that he does not believe. [*259] The In fact, it better serves the Act's purpose of protecting national security if all people freely profess their true beliefs, because the Orwell Act cannot protect the public from a silent terrorist. Nor does it discriminate against any particular speech on the basis of content or viewpoint, at least on its face; it captures all communications regardless of subject matter. In short, the Act is not directed at speech, at least under the Court's current understanding of the doctrine, nor does it regulate conduct. The Act does not truly require speakers to open their speech to government surveillance; it simply gives the government the power to listen. As the Court stated in Bowens v. Roy, n83 a case that threw out a free-exercise challenge brought by Stephen Roy to enjoin the government from using the Social Security number of his daughter, Little Bird of the Snow: Never to our knowledge has the Court interpreted the First Amendment to require the Government itself to behave in ways that the individual believes will further his or her spiritual development or that of his or her family ... . The Free Exercise Clause affords an individual protection from certain forms of governmental compulsion ; it does not afford an individual a right to dictate the conduct of the Government's internal procedures ... . The Federal Government's use of a Social Security number for Little Bird of the Snow does not itself in any degree impair Roy's "freedom to believe, express, and exercise" his religion. Consequently, [Roy's] objection ... is without merit. n84 The same reasoning applies to the Speech Clause, which is phrased in negative terms almost identical to those of the Free Exercise [*260] Clause. n85 The Court has not suggested that the government has an affirmative duty to foster speech among its citizens, but only a Page 3 duty not to impair it absent sufficient justification. n86 But the Orwell Act does not impair the freedom to believe, express, and exercise one's freedom of speech, at least in the Court's conventional understanding of impairment as involving some kind of law or regulation outlawing or requiring some action. The Act, quite simply, requires nothing of citizens and prohibits nothing pertaining to speech. This is not to say that it cannot have First Amendment consequences, however. Two (somewhat overlapping) lines of cases offer some hope for the Anti-Orwellians: cases involving a "chilling effect" on the freedom of association, and cases involving a "chilling effect" on speech generally. A. Associations on the Rocks The term "freedom of association" does not appear in the First Amendment, but it now stands as a "clearly established" constitutional right. n87 Perhaps fortuitously for Anti-Orwellians, the first case to "establish" the right to free association, NAACP v. Alabama, n88 rested upon the danger of a chilling effect upon protected freedoms: It is hardly a novel perception that compelled disclosure of affiliation with groups engaged in advocacy may constitute as effective a restraint on freedom of association as the forms of governmental action in the cases above [involving regulations having a chill upon speech] were thought likely to produce upon the particular [*261] constitutional rights there involved. This Court has recognized the vital relationship between freedom to associate and privacy in one's associations ... . Inviolability of privacy in group association may in many circumstances be indispensable to preservation of freedom of association, particularly where a group espouses dissident beliefs. n89 Since that time, the Court has recognized that freedom of association exists "in two distinct senses": the freedom "to enter into and maintain certain intimate human relationships" (intimate association), and the freedom "to associate for the purpose of engaging in those activities protected by the First Amendment - speech, assembly, petition for redress of grievances, and the exercise of religion" (expressive association). n90 For the purposes of the Orwell Act, the first category overlaps in relevant respects with the due-process right to privacy and warrants no further discussion here. n91 The second category, however, may hold some hope for the Anti-Orwellians. The second category has evolved to include protection for expressive groups against forced inclusion of unwanted members and restrictions upon their ability to disseminate their views, two strands that hold little weight in challenging the Orwell Act. But, according to one scholar, "the privacy of the group and its members remains the core of the right." n92 Unfortunately, if privacy remains the core of associational rights, the Supreme Court has certainly not treated it as such; it has heard only one case concerning the surveillance of expressive groups and dismissed it for lack of standing. n93 Indeed, there is a legitimate question as to whether privacy remains at the heart of freedom of association. The Supreme Court has not cited NAACP for the proposition that freedom of association encompasses privacy of association since 1986, n94 and it has not issued a ruling on the basis of a right to private association since [*262] 1984. n95 As for the lower courts, some "have held political surveillance claims justiciable where the surveillance targeted a particular group or individual." n96 The Orwell Act does not target particular groups or individuals on its face, nor does it "exclude a person from a profession or punish[] him solely because he is a member of a particular political organization or because he holds certain beliefs," n97 which the First Amendment freedom of association prohibits. On the other hand, the Supreme Court has not allowed the government to "inquire about an individual's beliefs and associations" n98 for the purpose of giving or withholding a benefit unless it can show "a substantial relation between the information sought and a subject of overriding and compelling state interest." n99 In addition, an organization may assert an interest in keeping the confidentiality of its membership list if the confidentiality is "so related to the right of the members to pursue their lawful private interests privately and to associate freely with others in so doing as to come within the protection" of the Constitution n100 - that is, if compelled disclosure "is likely to affect adversely the ability of [the organization] and its members to pursue their collective effort to foster beliefs which they admittedly have the right to advocate." n101 The Orwell Act would inevitably reveal information regarding citizens' expressive associations. With cameras, microphones, and email, computer, and phone monitoring, it is unlikely that citizens could hide their associations from the government while still remaining active members of those groups. The reality of this inevitable disclosure could provide Anti-Orwellians (or, more specifically, Anti-Orweillian expressive organizations) with two arguments: first, that the surveillance amounts to compelled disclosure for the purpose of giving or [*263] withholding benefits, and second, that it "chills" their "collective effort to foster" beliefs through lawful advocacy. The first claim is the more dubious of the two. While the government "inquires into" associations in the sense that they inquire into all communication through general surveillance, it does not make this inquiry of associations directly. The government asks no questions; it merely observes. Under such an expansive reading of NAACP, the government in that case would have been prohibited from discovering the identities of the NAACP's members by indirect methods; for example, if a citizen came to the attorney general's office and said, "My neighbor told me he is a member of the NAACP," the attorney general would have to close his ears. Furthermore, NAACP relied at least in part upon evidence that the disclosed members were subject to private reprisals, n102 whereas the Orwell Act does not authorize disclosure to private individuals and our hypothetical does not envision abuse of this information by public officials. In addition, the government neither confers nor withholds benefits on the basis of the Orwell Act, at least in the traditional sense of economic or employment opportunities. The surveillance may lead to consequences the federal government may increase local surveillance of suspicious people or use data against suspects in criminal trials - but it is a stretch to consider the freedom from increased government suspicion a "benefit" that the government "withholds" as a result of citizens' associational ties. The second claim holds more promise for Anti-Orwellians in that constant government surveillance would likely discourage membership in anti-government organizations. n103 Putting aside the question of whether the government surveillance actually chills expressive association, the Anti-Orwellians face other difficulties in establishing a claim under NAACP - namely, that a court could easily distinguish the NAACP case on its facts. NAACP was a case involving compelled disclosure of an organization's member list. While citizens [*264] are "compelled" to reveal their associations under the Orwell Act in the sense that the realities of government surveillance make it impossible to hide them, the Act requires no affirmative disclosure to the government. It adds no direct relationship between organizations and the government. In sum, a claim that the Orwell Act violates citizens' rights to engage in expressive association carries hope in principle, but the claim may fall short in the details. Case law also suggests that surveillance in itself does not abridge the right to expressive association unless it involves targeted surveillance of certain groups. n104 The government's efforts regarding general surveillance blend into the Anti-Orwellians' second claim under the First Amendment: that the Orwell Act chills free speech generally. B. Speech on the Rocks 1. A Brief Historical Perspective The history of domestic surveillance in response to citizens' exercise of their First Amendment rights is not a proud one. It is divisible into two categories with different degrees of Page 4 government mens rea: surveillance of individuals because of their messages themselves, n105 and surveillance of individuals because their messages suggest that they may pose a threat to national security given external events. n106 The first category treats speech as harmful in itself, at least to the government in power, and surveillance in such circumstances constitutes political espionage. The second category treats speech as a symptom, a convenient means for criminal profiling based on ideology. [*265] The government's early efforts at widespread domestic surveillance fell into the profiling category. Following an outbreak of terrorist bombings in 1919, the FBI created "dossiers detailing the political beliefs of [communists] and other radicals" and arrested thousands of them in the 1920 "Palmer Raids." n107 These efforts continued to concentrate on suspected communists (as well as fascists and other extremists) immediately prior to World War II, and communists remained a point of focus through the first thirty years of the Cold War. n108 Surveillance of those of Middle Eastern descent in the days following the terrorist attacks of 9/11 certainly belongs in this category. After World War II, the government also began surveillance in the political espionage category: "FBI investigations covered "the entire spectrum of the social and labor movement in the country,'" all for "pure intelligence" purposes. n109 The FBI's investigation of Martin Luther King, Jr. offers the most infamous example of this type of surveillance. n110 In these cases, the FBI did more than just keep a watchful eye on dissidents: it infiltrated dissident groups, sent "poison-pen letters intended to break up marriages," "encouraged gang warfare," and operated "on the theory that preventing the growth of dangerous groups and the propagation of dangerous ideas would protect the national security and deter violence." n111 Amid this history of nationwide efforts at surveillance, Anti-Orwellians cannot help but feel dismay at the relatively small number of free-speech cases addressing the issue of government surveillance. The Supreme Court has heard only one First Amendment challenge to a systematic government surveillance program, and it dismissed the case for lack of standing. n112 Justice Thurgood Marshall, sitting as Circuit Justice, heard one case addressing surveillance at one specific event, and [*266] he ruled for the government on the merits. n113 Lower courts have rarely dealt with the issue since those two Supreme Court rulings in the early 1970s, and few cases reached the merits. n114 This could, of course, be attributed to a reduction in government domestic surveillance following the Watergate scandal. But domestic surveillance increased following the terrorist attacks of 9/11; since that time, federal courts have heard only a handful of cases alleging that federal government surveillance created a "chilling effect" on speech. n115 This discouraging history may result from the nature of surveillance itself, in that subjects may not know they are under surveillance and thus have no motivation to seek an injunction to stop it. But it may also result from the tallest pretrial hurdle for "chilling effect" cases: standing. Even if the Anti-Orwellians can meet these standing requirements, the question of the appropriate level of scrutiny remains. 2. Standing, and Falling Under traditional standing requirements, the Court requires that plaintiffs show (1) "injury in fact" - that is, a "concrete and particularized" legal harm that is "actual or imminent, not "conjectural' or "hypothetical'" - that (2) arises from "the challenged action of the defendant" and (3) is "likely" to be "redressed by a favorable decision." n116 In chilling-effect cases, the first two requirements are the sticking points: chilling-effect harms are difficult to prove , and even if they exist, a court may decide that they arise not from actions of the defendant, but from " speculative apprehensiveness " that amounts to a "subjective "chill.'" n117 [*267] In addition, claims carry an inherent contradiction that works against standing. When plaintiffs claim that government action "chills" their speech, they essentially claim that they lack the courage to speak out against the government because they fear negative repercussions. Yet the "chilling-effect" very act of bringing a public lawsuit against the government is an act of courage in defiance of those repercussions; if a harm truly existed, if these plaintiffs were truly "chilled," then they would not have brought suit in the first place. Further, the Supreme Court has refused to give plaintiffs in chilling-effect cases the ability to assert standing on behalf of less-courageous non-parties to a lawsuit: "if [the plaintiffs] themselves are not chilled, but seek only to represent those "millions' whom they believe are so chilled, [they] clearly lack that "personal stake in the outcome of the controversy' essential to standing." n118 Even if the Anti-Orwellians could overcome this inherent difficulty, the challenge of showing a concrete and particularized chill remains. The likelihood of success in this element may depend upon the nature of repercussions for certain speech. Obviously, the more concrete the deterrent against lawful speech, the more concrete the chill in the eyes of the Court. Page 5 Circumvention --- 4th Amendment Even ruling on the 4th amendment is insufficient --- the government can just get data from associates Lynch 7 --- J.D. (Matthew, “CLOSING THE ORWELLIAN LOOPHOLE: THE PRESENT CONSTITUTIONALITY OF BIG BROTHER AND THE POTENTIAL FOR A FIRST AMENDMENT CURE”, 5 First Amend. L. Rev. 234, Lexis)//trepka Finally, even if the Court finds that the government interest pales in comparison to any privacy interests, and it rules against the Orwell Act, Anti-Orwellians face another practical difficulty: the limitations of the exclusionary rule . While a ruling that strikes down Orwell-Act searches on Fourth Amendment grounds might bar the admission of a defendant's own recorded conversations in a court proceeding, it would not bar the admission of the evidence gained by listening to the conversations of others , because defendants have no standing to object to violations of the privacy of others. n46 For example, in the prosecution of a drug dealer, the government could collect recorded communications of all of the drug dealer's associates. Suppose an associate calls another associate and tells him that the dealer expects a new shipment to arrive at a certain time and location. The government could send officers to that location to arrest the dealer as he makes the purchase; it could convince the associates to testify against the dealer; and it could even introduce the associates' conversations against the dealer at trial (subject, of course, to the limitations of the Confrontation Clause and rules of evidence). Other exceptions to the exclusionary rule, such as attenuation n47 and the independent source doctrine, n48 give the government opportunities to use [*250] the fruits of unlawful searches of the defendant himself. In short, the holes in the exclusionary rule give the government little incentive to abandon such a powerful means of uncovering evidence of criminal activity. Page 6 Cirvumention --- 5th/14th Amendment Applying the Fifth/Fourteenth amendment’s protection to privacy is insufficient --- it won’t be consistently applied afterwards and status quo surveillance isn’t even unconstitutional Lynch 7 --- J.D. (Matthew, “CLOSING THE ORWELLIAN LOOPHOLE: THE PRESENT CONSTITUTIONALITY OF BIG BROTHER AND THE POTENTIAL FOR A FIRST AMENDMENT CURE”, 5 First Amend. L. Rev. 234, Lexis)//trepka **Orwell Act = hypothetical government program that’s a conglomeration of all status quo government surveillance programs III. Claim No. 2: New (Un)Reliable - The Right to Privacy Rather than tying their constitutional hopes to a right with a shrinking scope of protection, perhaps it would be wiser for Anti-Orwellians to employ a right that has undergone a recent expansion: n50 the right to privacy. This "right," which falls under the "substantive force of the liberty protected by the Due Process Clause" n51 of the Fifth and Fourteenth Amendments, n52 does not explicitly appear within the [*251] Constitution. But the Court has used it to strike down some laws - primarily morals legislation, at least in the post-Lochner era with broad, sweeping language that could give hope to Anti-Orwellians: Our precedents "have respected the private realm of family life which the state cannot enter." These matters, involving the most intimate and personal choices a person may make in a lifetime, choices central to personal dignity and autonomy, are central to the liberty protected by the Fourteenth Amendment. At the heart of liberty is the right to define one's own concept of existence, of meaning, of the universe, and of the mystery of human life. Beliefs about these matters could not define the attributes of personhood were they formed under compulsion of the State. n53 Based upon this paragraph alone, the Orwell Act seems like a government venture into unconstitutional waters. While constant surveillance may not dictate the "choices central to personal dignity and autonomy" in the same sense that the criminalization of one of those choices would, one could argue that individuals should be free to "define one's own concept of existence" without the government looking over their shoulders. They may argue that true dignity, autonomy, and liberty require some breathing room, some private space where people can rest assured that their are limits to the application of these broad-stroke principles. The Court does not apply such liberty-promoting statements lawful words and actions will not fall within the government spotlight. But there consistently , and the task of convincing the Court to overrule some government action on substantive due-process grounds is not as simple as fitting it under the wide umbrella of generous dicta. n54 The Court [*252] instead relies upon a two-step approach to substantive due process claims: first, the asserted right must be one of "those fundamental rights and liberties which are, objectively, "deeply rooted in this Nation's history and tradition,'" and second, the Court must be able to make a "" careful description' of the asserted fundamental liberty interest." n55 Of course, not all abstract claims of rights require constitutional protection and recognition from the Court; these purported rights must, in some way, find some basis in the text of the Constitution n56 or American history and practice, n57 or perhaps some kind of reasoned consensus that the right warrants protection in an "organized society." n58 [*253] A. A Right in Search of a Definition In this case, the Anti-Orwellians could take two approaches. First, they could define their claim within an already-established right, such as the right to marital privacy n59 or the right of an adult to engage in consensual sexual relations with another adult n60 (they may also claim that it violates their fundamental free-speech rights under the First Amendment, and this Article will deal with that issue in the next section). They would simply argue that the Orwell Act violates these rights because it infringes upon "the liberty relating to intimate relationships, the family, and decisions about whether or not to beget or bear a child." n61 The problem with this approach is that the Orwell Act prohibits nothing. Citizens remain free to make reproductive decisions, engage in intimate relations, and raise their families as they see fit, so long as their conduct does not involve abuse , neglect , or other well-established criminal violations. The Orwell Act does not regulate these matters such that the government removes choice from the hands of the citizens; if reproductive decision-making is a constitutional right, the Orwell Act on its face does nothing to ban the exercise of that right. This is not to say that the Orwell Act could not violate these rights with regard to specific unconstitutional applications in specific, limited contexts. n62 But such misuse of the gathered information would not render the entire Act unconstitutional; a favorable ruling would merely prohibit the government from using the information in that way. The key question then becomes whether the government, acting only as a silent observer and listening in on family life, telephone calls, and [*254] important conversations, effectively deprives Americans of the free exercise of their Page 7 fundamental rights. It is certainly a plausible argument, considering that the Court often uses spatial metaphors to describe the breadth of the right ("realm of personal liberty" n63 and "zone of privacy" n64 are two of the most oft-cited examples). But it may also conclude that the mere presence of hidden surveillance equipment transmitting data to faceless computer banks miles away, with no penalty for the lawful exercise of these rights, does not amount to any meaningful deprivation of these rights at all. Women will still have the freedom to obtain abortions and couples may still engage in intimate relations. If the worst-case scenario for citizens is that some nameless, unknown strangers working for the government miles away might see transcripts or listen to recordings of the citizens practicing their lawful rights, without any authorization to disclose the information, then any purported deprivation of these rights could be too speculative to hold up in the Supreme Court. Page 8 Circumvention --- FISA FISA restrictions fail --- executive can label anyone an agent of a foreign power Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka Although FISA defined "foreign intelligence information" with relative clarity, within that definition, the "national defense or the security of the United States" was not defined with certain specificity. n69 The failure of Congress to articulate which activities fall under this national security classification allows surveillance of a foreign power or an agent of a foreign power where the executive deems the target of surveillance as a threat to national security. Further lowering the burden on the executive to secure a FISA order, the law allowed a FISA court judge to approve of the requested surveillance where the judge determines that the evidence presented by the executive official is "not clearly erroneous." n70 In so concluding, the judge is not required to conduct an in-depth probe into the validity of the information presented in the application, and instead makes his determination based on the executive official's certification. n71 Due to the great deference given to [*200] the executive branch to certify that the target of surveillance is a national security threat with a connection to a foreign power and the minimal inquiry required by the FISA judge into the validity of the facts, FISA fails to effectively safeguard from abuse possible targets of surveillance by the executive and authorizes surveillance of United States persons engaged in alleged criminal activities which have garnered Fourth Amendment protection in the past. Page 9 Circumvention --- Generic Courts fail – can’t set a precedent Correia 15 (Evan, J.D. Candidate, May 2015, Temple University Beasley School of Law, “NOTE & COMMENT: PULLING BACK THE VEIL OF SECRECY: STANDING TO CHALLENGE THE GOVERNMENT'S ELECTRONIC SURVEILLANCE ACTIVITIES” // AKONG) Courts routinely show considerable deference to claims of national security interests, which are bound to arise in these types of suits. n297 For example, in In re City of New York, n298 which involved police surveillance of protestors at the 2004 Republican National Convention, the Second Circuit refused to allow discovery of officers' field reports, even in redacted form. n299 The court explained that discovery of the field reports would reveal information about undercover operations and potentially hinder operations in the future. n300 Moreover, "lawsuits designed to uncover surveillance of intellectual activities may be unable to identify the "intellectual records' gathered by the government due to the way certain surveillance systems operate." n301 Fusion centers access and analyze private and public databases as well as real-time video feeds without ever creating or storing records. n302 "Although fusion center surveillance of all individuals' on and offline activities is continuous and totalizing, it does not necessarily produce records that could be packaged and produced as part of a discovery process." n303 The expansiveness of contemporary governmental total information awareness renders the judiciary incapable of reviewing the majority of situations on an individual basis. n304 Furthermore, any individual cases that make it to judgment would do little to effectuate any meaningful change because they would be focused on the intellectual privacy interests of specific litigants. n305 In other words, any one individual case could not challenge the systems of totalizing surveillance as a whole. The Klayman and ACLU v. Clapper decisions demonstrate the potential for the judiciary to subject government surveillance to meaningful scrutiny. n306 Specifically, there must be a review process that is open and adversarial, as opposed to the one-sided, closed hearings before the FISC in which judges consider only arguments from the government and operate in secret. n307 However, even if both suits ultimately succeed on appeal, the impact would likely affect only the government's collection of metadata. Measures must be adopted to facilitate meaningful judicial review of other government surveillance programs rather than [*214] the present reliance on the disclosure of classified material. In the field of electronic surveillance, the role of the judiciary is essential to ensuring a proper separation of powers and protecting individuals from "unreasonable searches and seizures" by the government as provided by the Fourth Amendment. n308 Page 10 Confusion --- Americans Overseas Can’t solve --- legal ambiguity Forgang 9 --- J.D. Candidate at Fordham (Jonathan, "THE RIGHT OF THE PEOPLE": THE NSA, THE FISA AMENDMENTS ACT OF 2008, AND FOREIGN INTELLIGENCE SURVEILLANCE OF AMERICANS OVERSEAS, Fordham Law Review, Lexis)//trepka Answering these allegations, the Director of the NSA, Lieutenant General Keith B. Alexander, said the agency acted with "respect for the law." n18 The Fourth Amendment, n19 the Foreign Intelligence Surveillance Act (FISA), n20 Executive Order 12,333, n21 and U.S. Signals Intelligence Directive 18 (USSID 18) n22 govern the NSA's electronic surveillance [*222] activities. The Highlander surveillance draws attention to an unresolved Fourth Amendment legal question about the surveillance of American citizens living outside the United States. Specifically, there is a controversy over whether the warrant requirement to the Fourth Amendment applies to surveillance of American citizens overseas . n23 It is estimated that over six million American citizens, including members of the military, live overseas. n24 While many of the United States' greatest threats come from abroad, government surveillance outside the country still affects the privacy rights of a substantial number of Americans. Page 11 Confusion --- Warrants Ruling on warrants is controversial --- decks solvency Forgang 9 --- J.D. Candidate at Fordham (Jonathan, "THE RIGHT OF THE PEOPLE": THE NSA, THE FISA AMENDMENTS ACT OF 2008, AND FOREIGN INTELLIGENCE SURVEILLANCE OF AMERICANS OVERSEAS, Fordham Law Review, Lexis)//trepka One point of contention is whether there is a relationship between the clause prohibiting unreasonable searches and the clause establishing the conditions under which the government may issue warrants. n45 The U.S. Supreme Court has held that a search without a warrant is generally unreasonable , with some well-established exceptions such as when police have probable cause or when there are exigent circumstances. n46 Other Supreme Court decisions have implied, however, that a warrant is not required at all and the Fourth Amendment only requires that a search be reasonable. n47 The controversy continues because the Fourth Amendment [*226] does not explicitly state that the fruits of warrantless or unreasonable searches and seizures must be barred as evidence in courts of law. n48 Professor Akhil Reed Amar has written that both the exclusionary rule and the warrant requirement are not valid because the Fourth Amendment at the time of its adoption did not explicitly require warrants, probable cause, or the exclusion of justification for this view is that the actual text of the Fourth Amendment does not require a warrant, stating only that "no Warrants shall issue, but upon probable cause." n50 Instead of a warrant requirement, Amar believes that the Fourth Amendment's text only requires that a search is reasonable . n51 According to Amar, the warrant requirement to the Fourth Amendment is a illegally obtained evidence. n49 The purely modern invention . n52 Page 12 Constitutional --- FISA Doesn’t violate 4th amendment Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka Addressing Fourth Amendment concerns regarding FISA surveillance, the Senate Select Committee on Intelligence undertook a balancing test, as conducted in the Keith case, where the government's interest in national security is weighed against the intrusiveness of the surveillance to the targeted individual. n85 The Committee concluded that the additional procedural safeguards imposed by FISA upon the executive branch allow the less stringent standards implemented by FISA to be constitutional under the standards set forth in the Keith [*203] decision. n86 The Committee further stated that although FISA surveillance diverges from the traditional Fourth Amendment warrant requirements, it was reasonable and therefore constitutional as FISA created new safeguards for personal privacy while allowing surveillance "in circumstances where, because of uncertainty about the legal requirements, the Government may otherwise be reluctant to use this technique for detecting dangerous foreign intelligence and terrorist activities by foreign powers in this country." n87 Both the text and the history of FISA, while clear that the purpose of a FISA order must be foreign intelligence gathering, precluded neither the use of foreign surveillance information in criminal proceedings, nor the communication between criminal prosecutors and foreign intelligence agents conducting FISA surveillance, as long as the primary purpose of the surveillance remained foreign intelligence gathering. FISA was intended to authorize domestic surveillance Plummer 6 --- J.D., Mississippi College School of Law, law clerk for Barnes of the Mississippi Court of Appeals (Brooke, “Domestic Spying: A Necessity in a Post-9/11 America or an Abuse of Presidential Power?”, Mississippi College Law Review, Lexis)//trepka FISA authorizes electronic surveillance only upon certain specified showings, and only if approved by a court. The statute specifically allows for warrantless wartime domestic electronic surveillance - but only for the first fifteen days of a war. n10 It makes criminal any electronic surveillance not [*306] authorized by statute (emphasis added); n11 and it expressly establishes FISA and specified provisions of the federal criminal code (which govern wiretaps for criminal investigation) as the '[exclusive] means by which electronic surveillance ... may be conducted.' n12 Importantly, FISA was not intended to apply to electronic surveillance conducted solely outside of the United States; rather, the statute "protects U.S. persons who are located in the United States from being targeted in their domestic or international communications without a court order no matter where the surveillance is being carried out." n13 Page 13 No Court Modeling The Constitution and political system aren’t modeled anymore Moravcsik, Professor of Politics & International Affairs at Princeton University, 6-31-5 (Andrew, “Dream On, America,” Newsweek) Americans are living in a dream world. Not only do others not share America's self-regard, they no longer aspire to emulate the country's social and economic achievements. The loss of faith in the American Dream goes beyond this swaggering administration The truth is that and its war in Iraq. A President Kerry would have had to confront a similar disaffection, for it grows from the success of something America holds dear: the spread of democracy, free Countries today have dozens of political, economic and social models to choose from. Anti-Americanism is especially virulent in Europe and Latin America, where countries have established their own distinctive ways--none made in America. markets and international institutions--globalization, in a word. Futurologist Jeremy Rifkin, in his recent book "The European Dream," hails an emerging European Union based on generous social welfare, cultural diversity and respect for international law--a model that's caught on quickly across the former nations of Eastern Europe and the Baltics. In Asia, the rise of autocratic capitalism in China or Singapore is as much a "model" for development as America's scandal-ridden corporate culture. "First we emulate," one Chinese businessman recently told the board of one U.S. multinational, "then we overtake." Many are tempted to write off the new anti-Americanism as a temporary perturbation, or mere resentment. Blinded by its own myth, America has grown incapable of recognizing its flaws. For there is much about the American Dream to fault. If the rest of the world has lost faith in the American model--political, economic, diplomatic--it's partly for the very good reason that it doesn't work as well anymore. AMERICAN DEMOCRACY: Once upon a time, the U.S. Constitution was a revolutionary document, full of epochal innovations--free elections, judicial review, checks and balances, federalism and, perhaps most important, a Bill of Rights. In the 19th and 20th centuries, countries around the world copied the document, not least in Latin America. So did Germany and Japan after World War II. Today? When nations write a new constitution, as dozens have in the past two decades, they seldom look to the American model . When the soviets withdrew from Central Europe, U.S. constitutional experts rushed in. They got a polite hearing, and were sent home. Jiri Pehe, adviser to former president Vaclav Havel, recalls the Czechs' firm decision to adopt a European-style parliamentary system with strict limits on campaigning. "For Europeans, money talks too much in American democracy. It's very prone to certain kinds of corruption, or at least influence from powerful lobbies," he says. "Europeans would not want to follow that route." They also sought to limit the dominance of television, unlike in American campaigns where, Pehe says, "TV debates and photogenic looks govern election Kosovo opted for a European constitution. Drafting a postSouth Africa rejected American-style federalism in favor of a German model, which leaders deemed appropriate for the social-welfare state they hoped to construct. Now fledgling African democracies look to South Africa as their inspiration, says John Stremlau, a former U.S. State Department official who currently heads the international relations department at the University of Witwatersrand in Johannesburg: "We can't rely on the Americans." The new democracies are looking for a constitution written in modern times and reflecting their progressive concerns about racial and social equality, he explains. "To borrow Lincoln's phrase, South Africa is now Africa's 'last great hope'." Much in American law and society troubles the world these days. Nearly all countries reject the United States' right to bear arms as a quirky and dangerous anachronism. They abhor the death penalty and demand broader privacy victories." So it is elsewhere. After American planes and bombs freed the country, apartheid constitution, protections. Above all, once most foreign systems reach a reasonable level of affluence, they follow the Europeans in treating the provision of adequate social welfare is a basic right. All this, says Bruce Ackerman at Yale University Law School, contributes to the growing sense that American law, once the world standard, has become "provincial." The United States' refusal to apply the Geneva Conventions to certain terrorist suspects, to ratify global human-rights treaties such as the innocuous Convention on the Rights of the Child or to endorse the International Criminal Court (coupled with the abuses at Abu Ghraib and Guantanamo) only reinforces the conviction that America's Constitution and legal system are out of step with the rest of the world. The Supreme Court isn’t modeled anymore New York Times 9-18-8 (“U.S. Court, a Longtime Beacon, Is Now Guiding Fewer Nations”) American legal influence is waning. Even as a debate continues in the court over whether its decisions should ever cite foreign law, a diminishing number of foreign courts seem to pay attention to the writings of American justices . ''One But now of our great exports used to be constitutional law,'' said Anne-Marie Slaughter, the dean of the Woodrow Wilson School of Public and International Affairs at Princeton. ''We are losing one of the greatest bully pulpits we have ever had.'' From 1990 through 2002, for instance, the Canadian Supreme Court cited decisions of the United States Supreme Court about a dozen times a year, an analysis by The New York Times found. In the six years since, the annual citation rate has fallen by half, to about six. Australian state supreme courts cited American decisions 208 times in 1995, according to a recent study by Russell Smyth, an Australian economist. By 2005, the number had fallen to 72. The story is similar around These days, foreign courts in developed democracies often cite the rulings of the European Court of Human Rights in cases concerning equality, liberty and prohibitions against cruel treatment, said Harold Hongju Koh, the dean of the Yale Law School. In those areas, Dean Koh said, '' they tend not to look to the rulings of the U.S. Supreme Court.'' The rise of new and sophisticated constitutional courts elsewhere is one reason for the globe, legal experts say, particularly in cases involving human rights. Page 14 the Supreme Court's fading influence, legal experts said. The new courts are, moreover, generally more liberal than the Rehnquist and Roberts courts and for that reason more inclined to cite one another. Specific decisions aren’t modeled – Just the foundations of our system Klug, Law Professor at the University of Wisconsin, 2K (Heinz, “MODEL AND ANTI-MODEL: THE UNITED STATES CONSTITUTION AND THE ‘RISE OF WORLD CONSTITUTIONALISM,’” Wisconsin Law Review, 2000 Wis. L. Rev. 597) Before discussing the various ways in which the American experience has served as a constitutional model, it is important to specify what serves as the model. The model is not merely the constitutional document and its amendments; it is also, more importantly, the ideas and institutions of American constitutionalism - popular sovereignty, federalism, the separation of powers, and judicial review - as well as the over two hundred years of constitutional jurisprudence that has flowed from the Constitution. It is this vision of the United States Constitution, as an elaborated text with a history of structural, institutional, and jurisprudential changes, that allows us to understand the place of the United States Constitution as the backdrop or wallpaper before which subsequent constitutional stories, from constitution-making to constitutional adjudication, have evolved. I must also clarify my use of the idea of a model. By model I mean a general source of ideas, concepts, examples, and even specific constitutional arguments rather than a mere reproduction or copy of what has occurred or is contained in the United States Constitution or constitutional jurisprudence. Caution at the notion of a constitutional model is also important. The pure adoption of any particular model or example does not guarantee any particular outcome. This problem is clearly evident in the experience of the United States in the Philippines, despite the aim of the United States to establish a different form of colonial relationship. After obtaining formal control from Spain through the Treaty of Paris in 1898 and after over fifty years of "tutelage" designed to establish an American form of government, the efforts of the United States seem to have achieved little more than a system of institutional charades, cast aside as soon as they no longer served those in power. From the passage of the 1934 Philippine Commonwealth and Independence Act, which provided that the Constitution should "include a [*600] bill of rights and establish a "republican form of government'"; to the subsequent adoption of the 1935 Constitution by a Philippine constitutional convention and the wholesale adoption of American case law, which seems to have been used as binding precedent; the experience produced no more than a symbolic manifestation of United States constitutionalism. As Andrzej Rapaczynski argues, "politically speaking, the cloning of America did not effectively protect the Philippines from a dictatorship, and even the best commentators could not see why the result was not what the Americans had intended." n5 Despite this failure to clone, the United States constitutional experience has served as a model, in my more general sense of the concept. As a general model it has served a number of distinct functions. On the one hand, the American constitutional experience offers examples of a range of structural features, whose evolution and impact may be observed over two centuries. These structural features include the transformation of the political idea of the separation of powers into a working constitutional principle; the creation of a federal system providing for the division of powers between a central government and its constituent regions; and finally, the creation of a range of institutional mechanisms for checking and balancing the exercise of governmental power, which provided political adversaries multiple sites for raising and contesting issues. On the other hand, the American experiment has raised the banner of individual rights and through a long and wavering jurisprudence demonstrated how vast areas of political conflict may become judicialized. Although often criticized as a legalization of politics, the creation of a popular rights consciousness among citizens of the United States has indeed inspired advocates of human rights and is reflected most clearly in the adoption of international human rights instruments and the post1945 emergence of an international human rights culture. Although less common, the specific doctrines of United States rights jurisprudence have at times served as a direct model abroad. A significant example of this is the influence of free speech doctrines flowing from the First Amendment of the United States Constitution on the common law based freedom of speech jurisprudence in Israel n6 and Australia. n7 However, instead of specific constitutional doctrines, particular institutional forms, or even specific constitutional rights, it has been the ideas and broad structural innovations of American constitutionalism that have found the greatest resonance among constitution-makers and interpreters. [*601] From the development of a single fundamental law, incorporated within one written document, to the distribution of public power among different geographic and institutional levels of government, the experience of American constitutionalism has provided a vast experiment to which constitution-builders abroad could turn. With subsequent waves of constitution-making these constitutional forms have evolved - both in the United States and abroad - to provide further elucidations of the original American model that could be relied upon by subsequent waves of constitution-makers. Other countries aren’t modeling the U.S. anymore – They’re looking to other countries Klug, Law Professor at the University of Wisconsin, 2K (Heinz, “MODEL AND ANTI-MODEL: THE UNITED STATES CONSTITUTION AND THE ‘RISE OF WORLD CONSTITUTIONALISM,’” Wisconsin Law Review, 2000 Wis. L. Rev. 597) With the widespread adoption of institutions and constitutional forms genetically tied to the innovations of the American revolution, it is not surprising that both advocates and detractors of the American experience assume that the United States is, at the beginning of the twenty-first century, the hegemonic model. Despite this assumption, American Page 15 scholars participating in what was, in the 1990s, more than a billion dollar program to promote the rule of law around the world, found themselves in competition with alternative constitutional models. Although the bulk of activity in the post-cold war "rule of law" movement was and lawyers and remains focused on judicial and legislative reform designed to promote market economies, it is important to recognize that a central product of this dual [*598] process of political transformation and rule of law advocacy was fundamental constitutional reform in over half the world - approximately 104 of the 188 members of the United Nations Organization. Of these, a staggering seventy-eight percent, or approximately eighty-one countries, adopted completely new constitutions. Given our common understanding of the historic influence of the United States Constitution, described by Louis Henkin as a "source of inspiration and ideas, [which] was studied and appraised by scholars, invoked by publicists, adopted or many of those who joined the multitude of legal expeditions to the coal-face of constitution-making in Eastern Europe, Africa, and many other parts of the world, found themselves confronted with alternative constitutional models. As exporters, advocates of the American model found that instead of enjoying an unassailable, dominant status, they faced open competition from advocates of the German, Canadian, Indian, or other constitutional experiences. Given that these alternative constitutional experiences are to a large extent themselves based on the adapted by revolutionaries, nation builders and statesmen," n4 it is indeed surprising that American model of constitutionalism, it seems counterintuitive that instead of serving as the dominant model the American experience serves as one of a number of alternative models, if not as an anti-model. If this impression is correct, then the assumption that the United States Constitution is the model to which the world turned, as States around the globe engaged in one of the most widespread and profound processes of constitutional and political reconstruction ever, is wrong. What then is the role of the United States Constitution outside the United States? This Article briefly discusses and evaluates the place of the United States Constitution in the context of a globalizing constitutionalism. It will emphasize both the enduring contribution to constitutionalism and as the ways in which American constitutionalism and constitutional jurisprudence are being used as the antimodel in many more recent constitution-making processes and in the dramatic expansion of constitutional jurisprudence around the world. I will also discuss the ways in which United States constitutional jurisprudence and scholarship is both a source of ideas and an outsider to a growing transnational constitutional conversation that is going on most evidently in the opinions of different constitutional courts and human rights fora. I will argue that although historically the United States Constitution provided an inspiration to the recent direction of United States constitutional jurisprudence has led most constitution-makers to seek alternative models. Although these alternatives are, I argue, premised on the fundamental elements of the American constitutional system - on the many, development of judicial review, federalism, and the separation of powers in [*599] United States jurisprudence - they have evolved into distinctly different alternatives. Even in those cases where the United States exercised a great deal of influence in the constitution-making process, the turn to alternative forms means that in many ways the United States Constitution and the jurisprudence that has flowed from it has, more recently, been providing the anti-model. This trend is even more evident in the constitutional jurisprudence of different constitutional courts, where United States Supreme Court opinions are discussed and either distinguished or the dissenting opinions of various United States Supreme Court Justices are quoted as sources of argument for decisions that are diametrically opposite to those reached by United States courts. Finally, I will briefly discuss the implications this view of a globalizing constitutional discourse may have for the debate in the United States Supreme Court over the use of foreign jurisprudence in interpreting the United States Constitution. Even if they win that other countries look at specific decisions, they will change them to meet the needs of their country. There is no reason they can’t figure it out on their own. Klug, Law Professor at the University of Wisconsin, 2K (Heinz, “MODEL AND ANTI-MODEL: THE UNITED STATES CONSTITUTION AND THE ‘RISE OF WORLD CONSTITUTIONALISM,’” Wisconsin Law Review, 2000 Wis. L. Rev. 597) it is in the jurisprudence of Supreme Courts and Constitutional Courts around the world that the true use of the antimodel may be witnessed. The highest courts of constitutional review in Canada, India, South Africa, Zimbabwe, and even the Privy Council of the House of Lords in reviewing cases from the Commonwealth all engage in extensive discussion of comparative constitutional jurisprudence and the case law of the United States Supreme Court in particular - quite unlike the rather parochial focus of courts in the United States. However, despite extensive citation of United States cases and reliance on some of the arguments employed by the United States Supreme Court, by and large United States jurisprudence has been increasingly used as a counterBut example , as a source of distinction, or merely distinguished as inapposite. Other countries don’t model us wholesale – Even if we have some bad decisions on the books, it doesn’t mean that our overall model is damaged Klug, Law Professor at the University of Wisconsin, 2K (Heinz, “MODEL AND ANTI-MODEL: THE UNITED STATES CONSTITUTION AND THE ‘RISE OF WORLD CONSTITUTIONALISM,’” Wisconsin Law Review, 2000 Wis. L. Rev. 597) While many features of the American model have been adopted elsewhere, it has been only in very rare circumstances, such as the Philippines in 1935, where the adopters have not fundamentally transformed the model to suit their own particular circumstances or to reflect their perceptions of the inadequacy of the original form. In order to reflect this reality and to [*605] demonstrate the emergence of the role of anti-model, I will separate my discussion of this particular impact of the United States constitutional model into two distinct phases: first, as an inspiration to or influence on constitution-makers; and second, as a constitutional text or source of constitutional argument for courts empowered to interpret newly adopted constitutions and/or bills of rights around the globe. For constitution-makers, the United States Constitution was for almost a century-and-a-half, the essential prototype of a written, single-document constitution. The United States' experience was part of the debates surrounding the creation of new constitutional orders in France and Germany from the early nineteenth century. Significantly, however, both limited knowledge of the actual United States constitutional experience and even incorrect translation of the Constitution itself served to limit its impact. Most importantly, the failure or limited success of democratic revolutions in Europe in the middle of the nineteenth century made the model wholly unsuitable to the forces that restored the position of the monarchy in these nineteenth-century European constitutions. Thus it was only in the twentieth century that Page 16 constitution-makers were very reluctant to incorporate some of the most basic American structural and institutional forms. For example, although notions of federalism and bills of rights were readily taken up, the content was often quite different. Very few constitution-making bodies accepted the notion of a national government of limited powers; instead, the sub-units - regions and provinces were given limited powers. Likewise, bills of rights were often included but the mechanisms of enforcement remained weak. In the case of judicial review, for example, many constitutions explicitly adopted the idea of judicial or constitutional review; yet, there was a marked the American Constitution began to emerge as a popular source of constitutional structures and institutions for constitution-makers. Even then, reluctance to accept the corresponding American idea of lifetime judicial appointments. Instead, constitution-makers tended to favor limiting judicial appointments to a particular term of years, thus keeping the membership of the highest constitutional court more closely tied, through the appointment process, to the broad contours of changing political circumstances. With non-renewable terms of seven to twelve years, constitution-makers in some cases tried to both ensure judicial independence and make the court as a whole subject to the democratic shifts that produce the changing political forces who control the appointment process. Page 17 No Norms No impact to norm setting --- friendly democracies will selectively ignore bad US norms, and authoritarian nations don’t care either way John O. McGinnis 7, Professor of Law, Northwestern University School of Law. ** Ilya Somin ** Assistant Professor of Law, George Mason University School of Law. GLOBAL CONSTITUTIONALISM: GLOBAL INFLUENCE ON U.S. JURISPRUDENCE: Should International Law Be Part of Our Law? 59 Stan. L. Rev. 1175 The second benefit to foreigners of distinctive U.S. legal norms is information. The costs and benefits of our norms will be visible for all to see. n268 Particularly in an era of increased empirical social science testing, over time we will be able to analyze and identify the effects of differences in norms between the United States and other nations. n269 Such diversity benefits foreigners as foreign nations can decide to adopt our good norms and avoid our bad ones .¶ The only noteworthy counterargument is the claim that U.S. norms will have more harmful effects than those of raw international law, yet other nations will still copy them. But both parts of this proposition seem doubtful. First, U.S. law emerges from a democratic process that creates a likelihood that it will cause less harm than rules that emerge from the nondemocratic processes [*1235] that create international law. Second, other democratic nations can use their own political processes to screen out American norms that might cause harm if copied.¶ Of course, many nations remain authoritarian. n270 But our norms are not likely to have much influence on their choice of norms. Authoritarian states are likely to select norms that serve the interests of those in power, regardless of the norms we adopt . It is true that sometimes they might cite our norms as cover for their decisions. But the crucial word here is "cover." They would have adopted the same rules, anyway. The cover may bamboozle some and thus be counted a cost. But this would seem marginal compared to the harm of allowing raw international law to trump domestic law. Page 18 No I-Law --- Fails International law doesn’t prevent conflict or constrain nations Hiken, Associate Director Institute for Public Accuracy, 7-17-’12 (Luke, “The Impotence of International Law” http://www.fpif.org/blog/the_impotence_of_international_law) Whenever a lawyer or historian describes how a particular action “violates international law” many people stop listening or reading further. It is a bit alienating to hear the words “this action constitutes a violation of international law” time and time again – and especially at the end of a debate when a speaker has no other arguments available. The statement is inevitably followed by: “…and it is a war crime and it denies people their human rights.” A plethora of international law violations are perpetrated by every major power in the world each day, and thus, the empty invocation of international law does nothing but reinforce our own sense of impotence and helplessness in the face of international lawlessness. The United States, alone, and on a daily basis violates every principle of international law ever envisioned: unprovoked wars of aggression; unmanned drone attacks; tortures and renditions; assassinations of our alleged “enemies”; sales of nuclear weapons; destabilization of unfriendly governments; creating the largest prison population in the world – the list is virtually endless. Obviously one would wish that there existed a body of international law that could put an end to these abuses, but such laws exist in theory, not in practice. Each time a legal scholar points out the particular treaties being ignored by the superpowers (and everyone else) the only appropriate response is “so what!” or “they always say that.” If there is no enforcement mechanism to prevent the violations, and no military force with the power to intervene on behalf of those victimized by the violations, what possible good does it do to invoke principles of “truth and justice” that border on fantasy? The assumption is that by invoking human rights principles, legal scholars hope to reinforce the importance of and need for such a body of law. Yet, in reality, the invocation means nothing at the present time, and goes nowhere. In the real world, it would be nice to focus on suggestions that are enforceable, and have some potential to prevent the atrocities taking place around the globe. Scholars who invoke international law principles would do well to add to their analysis, some form of action or conduct at the present time that might prevent such violations from happening. Alternatively, praying for rain sounds as effective and rational as citing international legal principles to a lawless president, and his ruthless military. International law isn’t key to global cooperation to solve transnational problems Estreicher, Law Professor at NYU, 3 (Samuel, “Rethinking the Binding Effect of Customary International Law,” Virginia Journal of International Law Association, Fall, 44 Va. J. Int'l L. 5) As for the subsidiary law that an increasingly interdependent world needs in advance of treaties, traditional CIL could not easily play this role as it was essentially backwards looking. The new, instantaneous customary law tries to play this role, but in a way that hardly comports with legitimacy. Without relying on CIL, states, international organizations, and other actors have ample means of identifying problems requiring interstate cooperation, drafting instruments that might command state support, and marshaling the forces of moral suasion. It is hard to see that the "law" aspiration of CIL offers the prospect of a significant incremental gain. In any event, the ultimate question is whether any such benefit warrants the accompanying costs - to which I now turn. International law has ZERO impact on state behavior Goldsmith, Law Professor at the University of Chicago, 2K (Jack, “Understanding the Resemblance Between Modern and Traditional Customary International Law,” Virginia Journal of International Law Association, Winter, 40 Va. J. Int'l L. 639) The significance of this "new" CIL is controversial. Many believe it is incoherent and illegitimate. n6 Others view it as a happy development for international law generally and - because the new CIL primarily concerns Page 19 human rights - for world justice. n7 In this essay we suggest that both critics and proponents of the new CIL proceed from a faulty premise. The faulty premise is that CIL - either the traditional or the new influences national behavior. In [*641] our view, the new CIL is no less coherent or legitimate than the old. But this is not because the new CIL is particularly coherent or legitimate, whatever those terms may mean in this context. It is because the commentators misunderstand how CIL, new or old, operates. CIL, new and old, reflects patterns of international behavior that result from states pursuing their national interests. These interests, along with the relative power of each state and other exogenous features of the international environment, determine which rules of CIL emerge in equilibrium. In both the traditional and new varieties, CIL as an independent normative force has little if any effect on national behavior. The plan does nothing to improve world order Berkowitz, of the Hoover Institution, 5 (Peter, “BOOKS: Laws of Nations,” April & May, http://www.hoover.org/publications/policyreview/2939681.html) Although their book is written with scholarly detachment, it represents a frontal assault on the liberal internationalist view that international law emerges from reflection on moral principles and that states comply with it in significant measure because of its moral and legal claim upon them. The authors argue that states comply with international law for almost exclusively instrumental reasons. This is not to say that international law is not law. It is to say that the study of it does not provide the key to state conduct and that the elaboration of it will not decisively improve world order. Nor is it to contend that states lack good reasons to comply with international law. They often do reasonably comply with their international obligations — because of a coincidence of interest, or because states gain by coordinating their behavior; or because cooperation in the short term will result in long term gains, or because of coercion by a stronger state or states of a weaker state or states. The heart of Goldsmith’s and Posner’s book is their rational-choice analysis of how customary international law originates and changes, and why states comply with it, and their examination of why states makes treaties and honor them. It will raise plenty of hackles. The lucidity and accessibility of their theorizing and the incisiveness of their doctrinal analysis will only heighten the effect. Yet it is their conclusions about the relation between morals and international law that provides the greatest challenge to the liberal internationalism Slaughter champions. First, Goldsmith and Posner reject the view that the increasing propensity of states to adopt the language of international law — particularly the language of human rights law — is evidence of the power of international human rights norms to shape state conduct. As with individuals, they argue, so too with states: Talk is cheap. Still, international-law talk serves strategic purposes. While talking tough about foreign affairs at home, a leader may make concessions or abdicate responsibilities abroad in ways that are invisible to an uninformed domestic audience. Alternatively, a leader may attempt to deceive foreign audiences by insisting on his country’s benign intentions and sincere respect for international norms. Still, liberal internationalists would insist that the increasing use by foreign leaders of the language of international human rights can’t help but exert a pull on their own thinking and the formation of state policy. Goldsmith and Posner doubt it. They think there is a perfectly good explanation, rooted in self-interest, for the fact that the language of international human rights law has come to supply the moral and legal content for the rhetoric of today’s world leaders: In an increasingly interconnected world order, a state may develop relations with almost any other state and must make its case in the most universal language available. Second, and more boldly, the authors contend that a moral obligation to obey international law does not even exist. They point out that states change regimes; it would not make sense to hold a state that has made the transition to democracy, for example, to treaties it signed while under communist dictatorship. They also observe that in the absence of a world government, there is no clear international authority that promulgates, enforces, and is responsible for the benefits of international law and to which states therefore might owe allegiance. And they note that the liberal internationalist practice of treating violations of international law as a step in the emergence of a new legal Page 20 order — when the violation corresponds with the moral judgments of liberal internationalists, at any rate — is inconsistent with the usual understanding of legal obligation. As they argue throughout their book, Goldsmith and Posner maintain that the absence of a moral obligation to obey international law does not much affect the conduct of states, which have a variety of self-interested reasons for compliance. In fact, they worry that the view that states possess such obligations may actually promote greater lawlessness in the international arena. One could wonder, for example, how the rule of law was served by the liberal internationalist consensus opposing the use of force to remove Saddam Hussein in March 2003 despite his flouting of 17 resolutions passed by the United Nations Security Council over a period of 12 years. Page 21 No I-Law --- Resilient Liberal international order resilient Ikenberry, Professor Politics at Princeton, ’10 (G John, “The Liberal International Order and its Discontents” Millennium: Journal of International Studies,Vol 38 No 3, p 509-521, SagePub) The Durability of Liberal International Order There are also reasons to think that this liberal order will persist , even if it continues to evolve. the violent forces that have overthrown international orders in the past do not seem to operate today. We live in the longest period of ‘great power peace’ in modern history. The great powers have not found themselves at war with each other since the guns fell silent in 1945. This non-war outcome is certainly influenced by two realities: nuclear deterrence, which raises the costs of war, and the dominance of democracies, who have found their own pathway to peace. In the past, the great Firstly, moments of order-building came in the aftermath of war when the old order was destroyed. War itself was a ratification of the view that the old order was no longer sustainable. War In the absence of great power war it is harder to clear the ground for new ‘constitutional’ arrangements. Secondly, this order is also distinctive in its integrative and expansive character. In essence, it is ‘easy to join and hard to overturn’. This follows most fundamentally from the fact that it is a liberal international order – in effect, it is an order that is relatively open and loosely rulebased. The order generates participants and stakeholders. Beyond this, there are three reasons why the architectural features of this post-war liberal order reinforce downward and outward integration. One is that the multilateral character of the rules and institutions create opportunities for access and participation. Countries that want to join in can do so; Japan found itself integrating broke the old order apart, propelled shifts in world power and opened up the international landscape for new negotiations over the rules and principles of world politics. through participation in the trade system and alliance partnership. More recently, China has taken steps to join, at least through the world trading system. Joining is not costless. Membership in institutional bodies such as the WTO must be voted upon by existing members and states must meet specific requirements. But these bodies are not exclusive or the liberal order is organised around shared leadership and not just the United States . The G-7/8 is an example of a governance organisation that is based on a collective leadership, and the new G-20 grouping has emerged to provide expanded leadership. Finally, the order also provides opportunities for a wide array of states to gain access to the ‘spoils of modernity’. Again, this is not an imperial system in which the riches accrue disproportionately to the centre. States across the system have found ways to integrate into this order and experience economic gains and rapid growth along the way. Thirdly, rising states do not constitute a bloc that seeks to overturn or reorganise the existing international order. China, India, Russia, Brazil, South Africa and others all are seeking new roles and more influence within the global system. But they do not constitute a new coalition of states seeking global transformation. All of these states are capitalist and as such are deeply embedded in the world economy. Most of them are democratic and embrace the imperial. Secondly, political principles of the older Western liberal democracies. At the same time, they all have different geopolitical interests. They are as diverse in their orientations as the rest of the They are not united by a common principled belief in a postliberal world order. They are all very much inside the existing order and integrated in various ways into existing governance institutions. Fourthly, the major states in the system – the old great powers and rising states – all have complex alignments of interests. They all are secure in the sense that they are not threatened by other major states. All worry about radicalism and failed states. Even in the case of the most fraught relationships – such as the emerging one between the United States and China – there are shared or common interests in global issues related to energy and the environment. These interests are complex. There are lots of ways in which these countries will world in regard to energy, religion and ideologies of development. compete with each other and seek to push ‘adjustment’ to problems onto the other states. But it is precisely the complexity of these shared interests that creates opportunities and incentives to negotiate and cooperate – and, ultimately, to support the open and rule-based frameworks that allow for bargains and agreements to be reached. Overall, these the leading states of the world system are travelling along a common pathway to modernity. They are not divided by great ideological clashes or emboldened by the potential gains from great power war. These logics of earlier orders are not salient today. Fascism, communism and theocratic dictatorships cannot propel you along the considerations suggest that modernising pathway. In effect, if you want to be a modern great power you need to join the WTO. The capitalist world economy and the liberal rules and institutions that it supports the liberal character of that system still provides attractions and benefits to most states within it and on its edges. – and that support it – are foundational to modernisation and progress. The United States and other Western states may rise or fall within the existing global system but It doesn’t depend on US leadership Ikenberry, Professor Politics at Princeton, ’10 (G John, “The Liberal International Order and its Discontents” Millennium: Journal of International Studies,Vol 38 No 3, p 509-521, SagePub) Page 22 the American liberal hegemonic order is in crisis. But it is a crisis of authority within the liberal international order and not a crisis of its underlying principles and organisational logic. That is, it is a crisis of the American governance of liberal order and not of liberal order itself. The crisis of liberalism today will ultimately bring forth ‘more liberalism’ . This is true if by liberal order we mean an open, rule-based relations system organised around expanding forms of institutionalised cooperation. In this sense, liberal international order can be contrasted with alternative logics of order – blocs, exclusive spheres and closed geopolitical systems. The future still belongs to the liberal international order. I argue that the post-Cold War liberal international order is more durable than many think. Russia and China are not its inevitable enemies. A grand alternative does not exist. To put it sharply: the pathway to the future still runs through I want to be sceptical of these views. Yes, institutions and relationships created over the last 60 years. American unipolarity will no doubt eventually give way to something new. Power and authority will shift in the global the United States and Europe and rising states – many of which are in Asia – will have more reasons and not fewer reasons to cooperate in open and rule-based ways. The rest of the article is divided into three parts. Firstly, I will examine the ‘old order’ and highlight its logic and durability. Secondly, I will assess the sources of crisis. And finally, I will discuss the dilemmas and pathways forward for liberal international order. American-led Liberal International Order Remarkably, we still live in the international order built by the United States and its allies over a half-century ago. It is system as they have over the centuries. But rival orders will not emerge – even if new leaders will. In the decades ahead, a distinctive type of order, organised around open markets, multilateral institutions, cooperative security, alliance partnership, democratic solidarity and United States hegemonic It is an order anchored in large-scale institutions leadership. , which include the United Nations, NATO, the Bretton Woods institutions, the World Trade Organization, alliance partnerships between the United States and Asian partners, and informal governance groupings such as the G-7/8. In the background, the United States played a hegemonic role, providing public goods by supporting open markets and the provisioning of security.5 The aff is the 31st case in the decade to deal with international law- can’t send strong signal Sloss, Ramsey, and Dodge- Law Profs- August 24, 2010, David L. Sloss (Santa Clara University - School of Law), Michael D. Ramsey (University of San Diego School of Law), William S. Dodge (University of California - Hastings College of the Law), The U.S. Supreme Court and International Law: Continuity and Change, http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1664773 The twenty-first century’s first decade was an extraordinarily active one for international law in the Supreme Court, with the Court issuing more than 30 decisions implicating international law. Many of these decisions came in high-profile cases, and many made important contributions to the Court’s jurisprudence. In Sanchez-Llamas v. Oregon and Medellin v. Texas, the Court considered the domestic legal status of treaties and the domestic effects of decisions by the International Court of Justice. It considered the federal judiciary’s role in applying customary international law under the Alien Tort Statute in Sosa v. AlvarezMachain. In a series of cases including Lawrence v. Texas, Roper v. Simmons, and Graham v. Florida it turned in part to international law and foreign practice to decide the scope of domestic constitutional rights. In F. Hoffman-La Roche Ltd. v. Empagran S.A., Morrison v. Australia National Bank and other cases, it used international law and related principles to constrain the global reach of federal statutes. And in prominent cases arising in the aftermath of the September 11, 2001 terrorist attacks, the Court grappled with questions of individual rights and separation of powers in a new kind of international warfare. Many of these decisions were deeply controversial, provoking strong dissents from Justices not in the majority and strong criticism from academic and political commentators. Critics and supporters often differed sharply as to whether the Court’s decisions were faithful to, or a radical departure from, prior precedents . Indeed, the rhetoric of the criticisms can hardly be overstated: to some, the Court was abandoning a longstanding commitment to international law; to others, the Court was allowing international law to invade domestic law at the expense of traditional notions of national sovereignty. To assess the modern Court’s relationship with its international law past, it is first necessary to understand what has come before. To that end, this volume seeks to provide a complete account of international law in the Supreme Court’s decisions from the Founding to the present. To assist in this project, we are fortunate to have assembled a distinguished group of contributors with expertise in international law, foreign affairs law, and legal Page 23 history. This book will not resolve debates about modern decisions, but we hope that it will inform those debates by providing a better understanding of the Court’s international law past. Court is already applying CIL Sloss, Ramsey, and Dodge- Law Profs- August 24, 2010, Customary international law’s rebirth in the Supreme Court began with Banco Nacional de Cuba v. Sabbatino,95 ironically a case that used the act of state doctrine to reject a claim brought under the international law of expropriation. Sabbatino also expressly disconnected the act of state doctrine from international law, describing it instead in separation of powers terms. But Sabbatino’s treatment of the act of state doctrine as federal common law, and its apparent endorsement of the argument that Erie did not apply to international law, suggested that customary international law might also be understood as federal common law.96 This question became more pressing towards the end of the twentieth century with the advent of human rights litigation under the Alien Tort Statute (ATS). Beginning with Filartiga v. Pena-Irala in 1980,97 lower federal courts used this previously-obscure, statute as a foundation for suits against foreign officials, and later private corporations, for human rights abuses. 98 The law these lower courts applied was new, having arisen from the ashes of the Holocaust. It was also more domestically intrusive than older species of customary international law because it governed relationships between nations and their own people. In Sosa v. AlvarezMachain,99 the Supreme Court cautiously endorsed the direct application of widely accepted and specifically defined rules of human rights law under the ATS.100 In answer to the question raised by Erie, Sosa appeared to treat customary international law as federal common law,101 at least for suits under the ATS. The extent to which customary international law is federal common law for other purposes has yet to be worked out,102 but at least to a limited extent Sosa marked customary international law’s return to the Supreme Court after a long absence. Sosa is remarkable for the attention its opinions pay to questions of continuity and change. Arguing against the direct application of human rights law, Justice Scalia pointed to the “avulsive change” wrought by Erie.103 “Post-Erie federal common lawmaking,” he asserted, “is so far removed from that general-common-law adjudication which applied the ‘law of nations’ that it would be anachronistic to find authorization to do the former in a statutory grant of jurisdiction that was thought to enable the latter.”104 In reply, the Court’s majority invoked the theme of continuity: “[w]e think it would be unreasonable to assume that the First Congress would have expected federal courts to lose all capacity to recognize enforceable international norms simply because the common law might lose some metaphysical cachet on the road to modern realism.”105 Page 24 No I-Law --- AT: HR States are rational actors – Human rights laws have ZERO impact on their behavior Goldsmith, Law Professor at the University of Chicago, 2K (Jack, “Understanding the Resemblance Between Modern and Traditional Customary International Law,” Virginia Journal of International Law Association, Winter, 40 Va. J. Int'l L. 639) We do not deny that human rights are more salient today than fifty years ago, or that nations take actions today to redress human rights violations (such as the arrest of Pinochet, or the invasion of Kosovo) that they probably would not have taken fifty years ago. But these facts do not by themselves demonstrate the efficacy of the CIL (or other international law) of human rights, n126 as there are many other plausible explanations for this phenomenon. Contrary to conventional wisdom, international law has long reflected protections for individuals against the state. n127 These laws had instrumentalist justifications, sometimes reflecting cooperation, but more reflecting the coercion of powerful nations seeking to promote security or stability. n128 These latter concerns were made particularly salient by the world wars, and resulted in an expansion of human rights concerns beyond minority rights to individuals generally. In addition, changes in technology have affected the enforcement of human rights. Nations have always been willing to pay, but not willing to pay much, to relieve visible suffering in other countries. n129 Developments since World War II have increased the benefits and lowered the costs of such enforcement. [*671] The rise of television means that suffering in other countries has become more visible; ordinary altruists thus gain more by seeing such suffering relieved than in the past, when relief as well as suffering could be described only in print. Advances in military technology have reduced the cost of intervening when human rights abuses occur in poor nations. So too have international institutions that were created to facilitate coordination of security issues, which are also available to coordinate responses to human rights abuse. This analysis does not deny that citizens of a particular state may feel altruism toward citizens in other states, particularly those that they see suffering on television. Nor does it deny that these feelings of altruism count as part of the national interest and may be reflected in a state's policy. But the state that pursues its interest, so defined, is not motivated by a desire to comply with international human rights law. As we have stressed, the evidence is precisely the opposite . If states sought to comply with international norms, which are inherently universalizing, then they would not enforce human rights selectively. But they do. They incur costs to enforce human rights only when doing so serves their interests, whether that means an interest in promoting stability in strategically important states, or an interest in appeasing the selective altruism of domestic interest groups. V. Conclusion This article has made a methodological point and a substantive point. The methodological point is that rational choice models provide a fruitful approach to understanding CIL. While we acknowledge that these models have shortcomings, these shortcomings should not blind one to the greater inadequacies of traditional international law approaches. As evidence for our view, we offer the example of the fishing vessel exemption, which should be added to our earlier work on diplomatic immunity, maritime jurisdiction, and the treatment of neutral trade. n130 The substantive point is not that international cooperation is impossible, but that it occurs only in limited conditions. We have argued elsewhere that many of the behavioral regularities called CIL do not reflect meaningful international cooperation, but rather reflect coincidence of interest or coercion, both of which [*672] lack normative import. n131 Some behavioral regularities associated with CIL (such as diplomatic immunity) do appear to reflect genuine cooperation, although this cooperation has a bilateral structure rather than the multilateral structure assumed by the traditional account. n132 This paper has extended that discussion to the coastal fishing vessel exemption in the law of prize. There is little evidence that the exemption, whether one wants to call it CIL or not, is the result of international cooperation. n133 The bulk of the evidence suggests that nations refrain from seizing fishing vessels when there is no military or economic value in doing so. The Paquete Habana, an important casebook symbol of the power of CIL, is a hollow shell. This brings us to the modern CIL of human rights. We deny that modern CIL differs from old CIL in an important way. The Page 25 essential difference is content: old CIL focused on commercial and military relationships between states; modern CIL focuses on human rights. But similarities overwhelm this difference. Modern CIL does not constrain nations any more than old CIL did. When nations decline to violate CIL, this is usually because they have no reason to violate it. Nations would act no differently if CIL were not a formally recognized source of law. n134 Modern CIL is mostly aspirational, just as old CIL was. With old and new CIL alike, nations mouth their agreement to popular ideals as long as there is no cost in doing so, but abandon their commitments as soon as there is a pressing military or economic or domestic reason to do so. Their evidence is just trumped up political rhetoric – U.S. non-adherence to international human rights treaties and norms has NO impact on other countries Moravcsik, Government Professor & Director of the European Center at Harvard, 2 (Andrew, Multilateralism & U.S. Foreign Policy: Ambivelent Engagement, edited by: Stewart Patrick and Shepard Forman) It is often argued that U.S. nonparticipation undermines international human rights institutions, as well as the global human rights movement. As Patricia Derian asserted before the Senate in 1979: "Ratification by the United States significantly will enhance the legitimacy and acceptance of these standards. It will encourage other countries to join those that have already accepted the treaties. And, in countries where human rights generally are not respected, it will aid citizens in raising human rights issues." Deputy Secretary of State Warren Christopher went even further, arguing that human rights policy is "a way of taking the ideological initiative, instead of merely reacting." President Carter himself added that it "might possibly reverse the tide that has been going against democracies in the past." Many similar quotations could be cited, since drawing a direct link between U.S. behavior and the effectiveness of international norms has, of course, a powerful rhetorical appeal. Yet little evidence suggests a close link between U.S. behavior and international norms, let alone domestic democratization. Everywhere in the world, human rights norms have spread without much attention to U.S. domestic policy. Under the European Convention on Human Rights, the Europeans have established the most effective formal system for supranational judicial review of human rights claims, based in Strasbourg, without U.S. participation. In the wake of the "third wave" of democratization in Eastern Europe, East Asia, and Latin America, government after government moved ahead toward more active domestic and international human rights policies without paying much attention to U.S. domestic practice. Indeed, emerging democracies in the Western Hemisphere are following Europe's lead in ratifying and accepting compulsory jurisdiction of a regional human rights court, while ignoring U.S. unwillingness to ratify the American Convention on Human Rights, let alone accept jurisdiction of a supranational court. One might argue with equal plausibility that the pride of Latin American democracies in full adherence to the American Convention on Human Rights is strengthened by the unwillingness of the United States, Canada, Mexico, and the stable democracies in the anglophone Caribbean to adhere. Likewise, 191 countries have ratified the CRC in record time without waiting to see what the United States would do. There is little evidence that Rwandan, Serbian, or Iraqi leaders would have been more humane if the United States had submitted to more multilateral human rights commitments. The human rights movement has firmly embedded itself in public opinion and NGO networks, in the United States as well as elsewhere, despite the dubious legal status of international norms in the United States. In sum, the consequences of U.S. nonadherence to global norms, while signaling a weakening in theory, is probably of little import in practice.365 Page 26 Even if their hypocrisy arguments are true, there is no impact – The U.S. can still be a global human rights leader even if we only selectively ratify human rights norms Ignatieff, Carr Professor of Human Rights at the Kennedy School of Government at Harvard, 2 (Michael, “No Exceptions?,” Legal Affairs, May / June, http://www.legalaffairs.org/issues/May-June2002/review_ignatieff_mayjun2002.msp) This defense of the United States does not, however, address the charge of hypocrisy. If America wants to be a human rights leader, the argument goes, it must obey the rules it seeks to champion. Leadership depends on legitimacy, and legitimacy requires consistency. But it's not clear that the effective use of American power in fact depends on being consistent, or on being seen by others as legitimate. Perceived legitimacy eases but it isn't essential to the exercise of power. Being seen as hypocritical or doubledealing may impose some costs on a superpower, but these costs are rarely prohibitive. America has faced a storm of protest about its treatment of the Guantanamo Bay prisoners—a storm that has led the Bush Administration to concede that the Geneva Convention should determine which protections Taliban prisoners (though not Al Qaeda ones) receive. At the same time, the prisoners remain, and are likely to remain, in American custody and subject to American justice. In another example, Slobodan Milosevic is in detention in The Hague, thanks in large measure to the pressure of the United States on the Serbian government. America could exert that pressure despite resisting the creation of a permanent criminal court with the power to try American citizens. (Milosevic will make much of this resistance to demonstrate that he is the casualty of victor's justice.) And again, as a matter of equity and ethics, it may be undesirable for the United States to support international tribunals for others but not for its own citizens. It is less clear, however, that this prevents American support for these tribunals from being effective. If the hypocrisy of exceptionalism doesn't prevent the U.S. from promoting human rights abroad, then what's really at stake is American identity. Those who wish that America didn't except itself, or excepted itself less often, want the United States to be a certain kind of good international citizen. They want it to be bound, despite its unique power, by international definitions of a state's responsibility to its own people. This identity is supposed to make the U.S. more effective by winning over more friends. But it's really about making America more attractive to itself, a benevolent empire that voluntarily restricts its own sovereignty for the sake of the greater global good. The problem here is that this benevolent ideal has limited appeal to the American electorate. To most voters, it makes little sense to say, "Why can't you be more like the Europeans?" or less plausibly, "Why can't you be more like the Canadians?" In addition, the identity that internationalists envision is decidedly more liberal than most Americans are comfortable with: against the death penalty, in favor of a woman's right to choose, in favor of allowing American citizens to be tried in international courts. Page 27 AT: FISA Bad --- Needs Warrants Their privacy arg is hype --- there’s a nuanced compromise between liberty and terror now Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka The need to reconcile domestic intelligence requirements with the protection of civil liberties is a recurring and prominent theme in the war on terror. While this tension between domestic intelligence gathering and civil liberties can be seen in many contexts since 9/11, this Article focuses on the Bush administration's Terrorist Surveillance Program (TSP), where the National Security Agency (NSA) secretly wiretapped Americans without traditional Foreign Intelligence Surveillance Act (FISA) warrants and the resulting FISA reform legislation culminating in the FISA Amendments Act of 2008 (FAA). In July 2008, the American Civil Liberties Union (ACLU) filed suit against the FAA arguing that it is unconstitutional; this Article, however, argues that the FAA is most likely lawful and appears to be a nuanced compromise between the legitimate need to expeditiously gather intelligence against terrorists and the protect ion of Americans' civil liberties . In order to draw this conclusion, it is necessary to understand what traditional FISA requires, how the TSP program departed from that rubric, and how advances in technology and the nature of terrorism have impacted intelligence gathering. Part I of this Article analyzes the legal framework of domestic spying and discusses the Fourth Amendment, Title III of the Omnibus Crime Control and Safe Streets Act of 1968, FISA, and changes made to FISA with the USA Patriot Act. Part II analyzes the Bush administration's warrantless surveillance program and whether, and to what extent, it violated the law. Part III discusses the challenges posed by terrorism to intelligence gathering and the need for modifications to FISA. Part IV analyzes the FAA of July 2008 and ponders whether it is just the perception that civil liberties could be eroded, or whether Americans' civil liberties truly are at risk. Finally, in Part V, this Article argues that in some ways the FAA has not gone far enough in addressing the underlying problems with conducting surveillance of terrorists and suggests areas for future reform. Warrants aren’t 4th amendment rights Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka I. The Evolution of the Warrant and Probable Cause Requirements The text of the Fourth Amendment does not by its terms require the government to obtain a warrant before conducting a search n20: [*349] The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized. n21 If the Framers intended to require warrants - even if only presumptively they could have drafted the Amendment to make that command clear . Instead, they opted for language that limits the availability of warrants n22: "No Warrants shall issue ... ." This reading suggests that the Fourth Amendment as understood at the time of its drafting disfavors the use of warrants. n23 Without the warrant requirement, the touchstone of the Fourth Amendment becomes a search or seizure's " reasonableness ," which can be assessed by balancing the intrusiveness of the search against the societal interest in investigating or preventing the particular crime or threat at issue. n24 The historical understanding of warrants at the time of the Framing supports the view that the Fourth Amendment was designed to limit the use [*350] of warrants, not to require them for all searches . In the pre-revolutionary colonies, a warrant primarily served to insulate a government official from civil liability from a lawsuit alleging trespass, which was the main method used to punish and deter such a search. n26 Thus, it was not the warrant that determined the legality of the search, which could have been perfectly acceptable without one. The warrant merely provided a defense at a later civil action. "Warrants then, were friends of the searcher, not the searched." n27 n25 Page 28 Requiring warrants is unnecessary --- there’s already a ton of exceptions Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka I. Legal Background of Domestic Spying A. Fourth Amendment The Fourth Amendment of the Constitution provides the foundation for limiting the government's role in collecting domestic surveillance. It protects against "unreasonable searches and seizures" and requires that warrants be issued only upon "probable cause." n7 At a fundamental level, it is important to understand that the warrant and reasonableness requirements are distinct. The Supreme Court has recognized situations where warrants are not required to conduct a search and seizure because the circumstances are otherwise reasonable , and it would be impractical to obtain a warrant. Examples of warrantless searches include the plain view doctrine , n8 the motor vehicle exception, n9 consensual searches, n10 searches incident to arrest, n11 and searches in exigent circumstances. n12 [*272] The Supreme Court has further held that a warrantless search can be constitutional "when special needs, beyond the normal need for law enforcement, make the warrant and probable cause requirement impracticable ." n13 In determining whether the "special needs" doctrine applies, the Supreme Court distinguishes searches designed to uncover evidence of "ordinary criminal wrongdoing" (generally requiring a warrant), and those motivated at a "programmatic level" by other governmental objectives, n14 such as stops of motorists at roadblocks for the purpose of securing the border or conducting sobriety checkpoints, n15 administrative searches in regulated industries, n16 searches of government employees to test for drugs, n17 and searches of public school students. n18 In other words, not every search and seizure requires a warrant. In New Jersey v. T.L.O the Supreme Court held that the "underlying command of the Fourth Amendment is always that searches and seizures be reasonable ," and "what is reasonable depends on the context within which a search takes place." n19 Significantly, for purposes of this article, the Foreign Intelligence Surveillance Court of Review (FISCR) has specifically held that the government's "programmatic purpose" in obtaining foreign intelligence information is "to protect the nation against terrorist and espionage threats directed by foreign powers." n20 The "programmatic purpose" fulfills "a special need" that fundamentally differs from "ordinary crime control." n21 [*273] Another significant fact about Fourth Amendment jurisprudence is that a governmental intrusion is only a "search" if it invades a "reasonable expectation of privacy ." n22 In areas where the Supreme Court has found there to be reasonable expectations of privacy (such as private conversations), Congress has enacted two significant statutes for purposes of surveillance: Title III of the Omnibus Crime Control and Safe Streets Act of 1968, n23 dealing with domestic wiretapping, and the Foreign Intelligence Surveillance Act (FISA), n24 which deals with the collection of foreign intelligence. An understanding of both of these statutes is fundamental background to analyze and understand what is really at stake with the FAA of July 2008. Warrant exceptions disprove their argument Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka However, the sheer impracticality of requiring warrants in certain situations led the Court to create a slew of exceptions to this requirement. n31 As the Katz Court put it: "Searches conducted outside the judicial process, without prior approval by judge or magistrate, are per se unreasonable under the Fourth Amendment - subject only to a few specifically established and well-delineated exceptions." n32 Perhaps the most well known of these [*351] exceptions Page 29 is for " exigent circumstances ." n33 Under this exception, a warrantless search is constitutional when obtaining a warrant would be impractical due to an emergency of some sort, such as the need to enter a dwelling to render aid , n34 to arrest a murderer and search for other accomplices or victims, n35 or to preserve evidence of a crime . n36 The Court has created so many exceptions to the warrant requirement n37 that one commentator has asked whether in practice warrants are now the exception rather than the rule . n38 Page 30 AT: FISA Bad --- Tyranny FISA averts the worst abuses and can’t be used to try or convict Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka C. Foreign Intelligence Surveillance Act of 1978 In 1978, Congress enacted FISA to deal with the unresolved issue of gathering foreign intelligence (solely domestic intelligence is still governed by Title III). For decades, presidents had conducted electronic surveillance for national security purposes without a warrant. Indeed, wiretaps for such purposes were authorized by presidents at least since the administration of Franklin Roosevelt in 1940. n39 In the 1960s, Presidents Johnson and Nixon used the agency to listen in on hundreds of Americans , including Vietnam War protesters and the Rev. Martin Luther King Jr. n40 During the Watergate scandal in the 1970s, President Nixon relied on national security concerns to hide his wiretapping of domestic political opponents . n41 Between 1975-1976, the Church Committee did an exhaustive inquiry into domestic spying and discovered (1) that the FBI had conducted 500,000 investigations into alleged subversives from 1960-1974; (2) that the CIA had engaged in widespread mail-openings in the United States; (3) that Army intelligence operatives had conducted secret inquiries against 100,000 U.S. citizens opposed to the Vietnam War; (4) that the NSA monitored every cable sent overseas or received by Americans from 1947 to 1975; and (5) that the NSA conducted surveillance of telephone conversations of an additional 1680 citizens. n42 All these aforementioned acts were taken with no judicial oversight. As a result of these governmental abuses of civil liberties, and as a result of the Keith decision that suggested that the rules for gathering intelligence may be different than the rules for law enforcement, in 1978 Congress enacted FISA to replace presidentially ordered surveillance of national security threats and to reign in politically motivated surveillance. n43 FISA provides a statutory framework for the U.S. government to engage in electronic surveillance and physical searches n44 to obtain "foreign intelligence information ," which generally encompasses [*276] evidence of terror ism, espionage , and sabotage . n45 Like Title III, FISA surveillance can target U.S. citizens as well as foreign nationals inside this country, but provides simplified procedures for obtaining and executing warrants for both electronic surveillance and physical searches. FISA allows wiretapping of aliens and citizens in the U.S. based on a finding of probable cause to believe that the target is a member of a foreign terrorist group or an agent of a foreign power. n46 Significantly, unlike Title III which requires a finding of probable cause that the search will reveal evidence of a crime, under FISA the government only needs to establish probable cause that the target is a member of a foreign terrorist group or an agent of a foreign power. This lower threshold for conducting surveillance under FISA reflects the inherent differences between obtaining surveillance for intelligence (e.g. prevention) purposes, as opposed to obtaining evidence to be used to convict an individual in a court of law. Although the Supreme Court has not ruled on the constitutionality of FISA, several lower courts have upheld its constitutionality even without traditional probable cause, because "governmental interests in gathering foreign intelligence are of paramount importance to national security, and may differ substantially from those presented in the normal criminal investigation." n47 Page 31 AT: Rule on Katz Doesn’t apply --- national security Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka Pursuant to the 1967 Supreme Court case Katz v. United States, in order to conduct electronic surveillance of one's private conversations, a government agent must obtain a warrant from a judicial officer based on probable cause that criminal activity will be revealed, and the warrant must adhere to the Fourth Amendment's particularity requirements specifying the place to be searched. The Court in Katz, however, explicitly declined to extend its holding to cases "involving the national security." In 1968, Congress passed Title III of the Omnibus Crime Control and Safe n25 n26 n27 Streets Act of 1968 (Title III) to regulate domestic electronic surveillance to meet the Fourth Amendment's particularity requirements. n28 Congress enacted Title III to ensure that if the government obtained evidence pursuant to this statutory rubric, it would be admissible in court. Title III only allows wiretapping for certain enumerated crimes, limits the time period for the surveillance, requires minimization procedures to limit eavesdropping on innocent parties, and requires reporting to the court on the results of the surveillance. n29 In order to obtain a Title III warrant, the government official must also explain whether other investigative methods would produce the same results and specify the facilities and communications sought to be intercepted. n30 Title III specified that none of its provisions would "limit the constitutional power of the President to take such measures as he deems necessary [*274] to protect the Nation against actual or potential attack or other hostile acts of a foreign power, to obtain foreign intelligence information deemed essential to the security of the United States," or "limit the constitutional power of the President to take such measures as he deems necessary to protect the United States against any clear and present danger to the structure or existence of the Government." These caveats seemed to suggest that "national security" wiretaps in both domestic and international investigations could continue outside the parameters of Title III. In 1972, however, Significantly, n31 during the Vietnam War, the Supreme Court held in United States v. United States District Court (Keith) that the president had no constitutional power to conduct warrantless surveillance of domestic individuals and organizations that have "no significant connection" to a foreign power. n32 In Keith, the defendants were accused of trying to bomb a CIA office in Ann Arbor, Michigan, but there was no connection to a foreign power or entity. The Supreme Court held that surveillance of domestic targets - even under circumstances of "clear and present" danger - is unconstitutional without a judicial warrant the Supreme Court left open the possibility that the president may have authority to conduct warrantless surveillance of foreign powers and their agents . (This understanding was the primary basis for President Bush's ordering NSA to conduct warrantless wiretapping post 9/11. ) Significantly, after Keith, every federal appeals court to address the issue, including the FISCR, has concluded that the president has the inherent authority to conduct warrantless surveillance to gather foreign intelligence. based on probable cause, and meeting the particularity requirements of the Fourth Amendment. n33 Nonetheless, n34 n35 n36 Page 32 AT: Rule on Keith Keith doesn’t ban domestic searches without warrants Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Despite its sweeping rhetoric attesting to the need for full Fourth Amendment protections in the domestic security context, the Keith Court opened the door to a relaxed constitutional requirement. Court found that because the "exact targets ... may be more difficult to identify " n75 in domestic surveillance than in ordinary crime control, Congress could enact legislation that placed different controls on the In particular, the domestic intelligence-gathering machinery than on normal criminal investigations, subject only to the Fourth Amendment's reasonableness requirement. Congress, however, has not taken the Court up on its offer. Page 33 AT: Warrants Good --- Dissent They’ve got it backwards Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka One of the principle reasons the Keith Court declined to extend the warrant exception to the domestic intelligence context is the perceived deleterious impact surveillance can have on political dissent. Put simply, the government's search power could be used to squelch legitimate political opposition. n149 However, this argument ignores the historical abuse of warrants to further political oppression. It also fails to account for the fact that criminal law in many cases allows the government to obtain a warrant to search political groups on the pretext of seeking evidence related to a minor offense , thus actually enabling searches designed to squelch political dissent. The idea that warrants protect against political suppression is strange given the historical abuse of warrants by the government and the resulting distrust of them by the public: The British Crown employed general warrants to quash political dissent in England as early as the sixteenth century. The warrant was used against the [*369] press, and authorized both the government and private persons to "seize, take hold and burn ... books and things ... offensive to the state." n150 Even warrants issued by the judicial branch were viewed as a mere extension of the Executive's authority , both before and after the adoption of the Fourth Amendment. As such, the idea that warrants will prevent, rather than further , political oppression is peculiar in light of the history surrounding the Fourth Amendment. Despite the lack of historical pedigree for this argument, n151 warrants could theoretically prevent political oppression. By interposing a neutral judge prior to a search that might implicate free speech concerns, the likelihood that the executive branch will impermissibly suppress such protected speech will be decreased. n152 Much like the argument that warrants prevent racial discrimination, however, this contention is flawed. First, a warrant requirement only protects the speech of political dissenters if the official conducting the search knows she will answer for any failure to obtain a warrant. In the intelligence context, however, it is likely that a significant portion of intelligence activity will never be used in a criminal prosecution . As a result of this, and of the unlikelihood that a subject who is not criminally prosecuted will ever learn about clandestine intelligence activity directed against her, an intelligence officer is not deterred from engaging in illegal intelligence gathering without a warrant. n153 The warrant requirement is as powerless here as it is in the racial discrimination context. n154 Moreover, in those instances where an officer believes that the information she uncovers will be used in a criminal proceeding, she also knows that she will have to justify the search before a court. If the courts are concerned with the stifling of political dissent - as they should be - they can require a higher showing during after-the-fact review of the justification for the search in these situations. The reasonableness paradigm of the Fourth Amendment should take into account the legitimate political activities of the subject of a search as weighing against the government's need for information. n155 In this instance, then, it is the reasonableness requirement - [*370] not warrants - that stands between the citizen and illegal or abusive surveillance . Page 34 AT: Warrants Good --- Race Nope --- structural disincentives check Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka This is not to say that racial, ethnic, and religious discrimination are not possible concerns in the intelligence-gathering arena. Evidence of racial discrimination, however, likely would lead an intelligence search to be deemed unreasonable under the Fourth Amendment. n132 This is true not only because of the tremendous costs borne by victims of discrimination but also because the search furthers no legitimate government objective : discrimination merely wastes resources that could be put to more productive use. n133 Because discrimination is wasteful , properly managed and accountable intelligence agencies have an incentive to avoid harassing minorities via illegitimate intelligence activities. The costs of racial discrimination when searches are conducted by well run intelligence-gathering agencies, therefore, are likely to be muted . Data mining is evenly distributed Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka The political process can also protect against discriminatory abuses. First, any search regime that is spread out over the whole of the population - such as data-mining operations to search all electronic communications for certain words that would indicate a connection to terrorism - ensures that its costs are borne by the majority of people . n143 As a result, the majority will pressure elected officials in the legislative and executive branches to narrowly tailor or eliminate the program. n144 The public outcry over the disclosure of the existence of an NSA database containing millions of Americans' phone records proves this point too well . n145 Because the political process works in this context, courts do not need to conduct searching review of executive action. Page 35 Courts Mini-DAs Page 36 Court Clog DA Page 37 1NC Link Court clog Citron and Gray 13 (Danielle, Lois K. Macht Research Professor of Law, University of Maryland School of Law; Affiliate Scholar, Stanford Center on Internet and Society; Affiliate Fellow, Yale Information Society Project, David, Associate Professor of Law, University of Maryland School of Law, “Addressing the Harm of Total Surveillance: a Reply to Professor Neil Richards” // AKONG) Richards proposes to grant individuals standing to challenge governmental surveillance.81 Putting concerns about the constitutionality of such a challenge aside, his proposal may raise practical problems. Granting individuals standing to challenge governmental surveillance of them would overwhelm the courts. There are not enough judicial resources to adjudicate three hundred million such suits, each of which could be renewed — almost as soon as it is resolved — on nothing more than suspicion of continued surveillance because the focus, under Richards’s approach, is on what information is being gathered. The possibility of a class action would not help matters because individual issues of harm attached to what particular information is gathered would predominate.82 Suits are also bound to be met with claims of national security interest, to which courts routinely show considerable deference.83 For example, in litigation involving police surveillance of protestors at the 2004 Republican National Convention, the Second Circuit refused to allow discovery of officers’ field reports, even in re- dacted form, because they would reveal information about undercover operations and thus potentially hinder future ones.84 Page 38 2NC AT: Class Action The aff sends a signal that suits regarding government surveillance will succeed Correia 15 (Evan, J.D. Candidate, May 2015, Temple University Beasley School of Law, “NOTE & COMMENT: PULLING BACK THE VEIL OF SECRECY: STANDING TO CHALLENGE THE GOVERNMENT'S ELECTRONIC SURVEILLANCE ACTIVITIES” // AKONG) Granting individuals standing to challenge governmental surveillance would overwhelm the courts. n293 There are simply not enough judicial resources to adjudicate the approximately three hundred million suits this proposal could potentially generate. n294 Moreover, each of these suits would have the potential to be renewed almost as soon as it is resolved based on nothing more than suspicion of continued surveillance because their focus is on the information being gathered. n295 [*213] The possibility of a class action suit would not stem the flow if individual lawsuits either because individual issues of harm concerning what particular information is gathered would predominate. n296 Page 39 Court Legitimacy DA Page 40 1NC Court Legitimacy DA Turn – Legitimacy: The plan shreds the legitimacy and independence of the courts. Yoo, Law at Berkeley, 97 (John, Law Professor at Berkeley School of Law, “Federal Courts as Weapons of Foreign Policy: The Case of the Helms-Burton Act,” Hastings International & Comparative Law Review, V. 20:747) certain types of cases can place demands on the integrity of the federal courts as well as on their capabilities. My colleague Paul Mishkin has argued that structural injunctions call upon the courts to employ procedures that undermine the impartiality of the federal judiciary.71 In setting spending priorities for state governments, allocating state resources, and deciding on policies, federal courts can lose their objectivity and become actors in the political process and in the case itself.72 As cases move into the remedial stage, federal courts may lose their sense of detachment and become more interested in effective management of the defendant's conduct and of the overall remedy. An intrusive judiciary, and the failure or shortcomings of its remedies, may breed a lack of confidence in, or even a lack of respect for, the legitimacy of the federal courts. To be sure, there are a great many differences between structural injunction and foreign relations cases. Nonetheless, suits under Structural remedies also indicate that certain roles and Title III of Helms-Burton could invite similar problems. To adjudicate a Title III suit, a federal court will have to determine facts and causation that occurred more than 30 years ago in another country. Information on the events producing an expropriation may be hard to discover and may be of doubtful reliability, due to the termination of diplomatic and economic relations between the United States and Cuba. Courts may have to reconstruct complex financial transactions and chains of ownership among many different companies from many different nations that stretch back to the early 1960s. Courts may need to make sensitive judgments about the political relationships and decisions not just of the present The Supreme Court long has recognized that adjudicating claims arising from events and policies abroad present unique problems for the federal courts. In its political question cases, the Court has described its day, but of the 1960s, 1970s and 1980s. unwillingness to hear foreign relations cases both because the foreign affairs power is vested in the other branches, and because the judiciary is functionally ill-equipped for the task. [s]uch decisions are wholly confided by our Constitution to the political departments of the They are delicate, complex and involve large amounts of prophecy... They are decisions of a kind for which the Judiciary has neither aptitude, facilities nor responsibility ... "n While the As Justice Jackson wrote, " government, Executive and Legislative. political question doctrine does not apply to Helms-Burton, these concerns about judicial competence ought to be taken into account in evaluating how Title III will operate and whether it will succeed. Further, as with structural injunctions, Title III remedies may create significant institutional problems for the judiciary. Defendants are likely to have most of their assets abroad, which would leave the court with little property to attach in order to enforce its judgments. Enforcing judgments abroad is not easy; as the Supreme Court recognized long ago in Hilton v. Guyot, "[ajs an act of government, [a judgment's] effects are limited to the territory of the sovereign whose court rendered the judgment, unless some other state is bound by treaty to give the judgment effect in its territory, or unless some other state is willing, for reasons of its own, to give the judgment effect."74 As the United States has not entered into any international agreements on the enforceability of its judgments abroad, no other nations have a binding obligation to enforce a Title III judgment against their own nationals.75 These difficulties are only compounded when the foreign nations disagree with the policy of the law that gave rise to the liability, to the extent that they even enact "clawback" legislation that allows their corporations to sue in their domestic courts to recover awards rendered under American laws.76 Current disagreement with Such ineffectiveness serves to dilute public respect for the federal courts, which, as Alexander Hamilton noted in Federalist No. 7S, "have neither Force nor Will, but merely judgment."77 If Title III leaves the judiciary in the position of issuing judgments that none expect to be enforced, it enhances an image of powerlessness on the part of the courts. It may dilute the institutional capital of the courts in more important areas (such as constitutional rights), in which judges must depend on public respect to enforce counter-majoritarian decrees.73 Although considerations of political capital should not prevent the courts from exercising jurisdiction when the Constitution or federal law require it," they should inform policy decisions on whether to expand federal jurisdiction in the first place. Powerlessness is not the only Helms-Burton abroad may mean that few judgments rendered under Title III will be capable of enforcement. threat to judicial authority. My colleague Martin Shapiro has written that courts in several different cultures possess certain shared characteristics that enhance their social legitimacy, and hence the willingness of parties and the public to accept their judgments.85 Although courts deviate in different ways from this ideal model, courts essentially find their As the adjudicators become less neutral and more a part of the machinery of the state and of the political system, they lose their legitimacy. "When we move from courts as conflict resolvers to courts as social controllers, their social logic and their independence is even further undercut. For in this realm, while proceeding in the guise of triadic conflict resolver, courts clearly operate to impose outside interests on the parties."31 Ironically, granting the courts too much of a certain type of power—that of enforcer of public policy-also has the effect of threatening judicial integrity. Title III of Helms-Burton may prove to be a good example of this tension between a court's duty to resolve conflicts on the one hand, and to pursue public policy on the other. In the foreign relations area, a cause of action is more likely to be seen as a tool for the advancement of a specific public goal, rather than as the correction of an injustice or inequity. In other words, courts will be acting as instruments of the national government, even of the State Department, rather than as neutral decisionmakers engaged in conflict resolution. The legitimacy in the "logic of the triad," as Professor Shapiro describes it—the idea that two parties in conflict refer their dispute to a third, neutral party for resolution. U.S. House Committee on International Relations made this clear with regard to Title III when it declared that the "purpose of this new civil remedy is, in part, to discourage persons and companies from engaging in commercial transactions involving confiscated property, and in so doing to deny the Cuban regime the capital generated by such ventures and deter the exploitation of property confiscated from U.S. nationals."82 Usually, these international relations goals would be achieved by the imposition of economic sanctions by the executive and legislative branches, rather than through a cause of action in federal court. Enlisting the judiciary to achieve these purposes encourages a Page 41 perception of the federal courts as interested implementers of American foreign policy, which will undermine the legitimacy of the federal courts and of their judgment in the eyes of the public and of our allies. Judicialization of Cuba policy raises yet another threat to judicial independence. We have discussed the problems that arise both from the frustration of judicial remedies and from the perception of courts as merely arms of the state. Again as with structural injunctions, a third difficulty may arise when a class of cases calls for a change in the role of the individual judge. In structural injunctions situations, it will be remembered, judges can lose their objectivity and impartiality as they become interested players in the political give-and-take that occurs in remedial proceedings. Helms-Burton might produce a similar problem by placing judges in the difficult position either of executing American foreign policy or of flouting national security concerns. In ruling on the merits of a Title III case, judges may not find it easy cither to put aside their patriotism or to ignore popular support for Cuba sanctions. The price, however, of giving in to these temptations may be the further loss of neutrality and of legitimacy on the part of the courts. Judicialization of Cuba policy also will transfer the political bargaining and confrontation that occurs over foreign policy from the Congress and the White House to the courtroom. In the structural the expansion of the courts' remedial power over injunction context, some of the basic decisions of state government, such as budget, tax, and educational policy resulted in the transformation of the judicial process into a forum for the allocation of resources and the development of public programs.'*3 A similar prospect foreign policy may lie in store for the federal courts if the enforcement of —in this case Cuba policy-becomes the goal of litigation. For example, in Barclays Bank PLC v. Franchise Tax Board of California?4 a case which challenged the constitutionality of California's tax on multinational corporations, amicus briefs were entered by the United Kingdom, the European Community, Banque Nationale de Paris, the Confederation of British Industry, the Council of Netherlands Industrial Federations, the Federal of German Industries, the Japan Federation of Economic Organizations, the Japan Tax Association, Reuters, the U.S. Chamber of Commerce, and dozens of American states." Instead of fighting in Congress and the executive branch for a different international economic policy, these parties transferred their disputes to a judicial forum because of the Court's jurisdiction over may breed politicization, which in the long run would do great harm to the institution of the judiciary. dormant commerce clause cases. A similar result may occur when Cuba policy becomes a regular subject for federal lawsuits. Judicialization That undermines judicial independence and the legitimacy of the court O’scannlian, Federal Judge on the 9th Circuit Court of Appeals, 6 (Diarmuid, “On Judicial Activism: Judges and the Constitution Today,” Open Spaces Quarterly, volume 3, Number 1, http://www.openspaces.com/article-v3n1-oscannlain.php) A judge, however, is not expected to act on any person's behalf or pursuant to anyone's direction. Indeed, he must do precisely the opposite in his official role, spurning not only personal affinities but all communication outside of the courtroom. Even if we were to conceive of a judge as a peculiar kind of agent, one that is charged with acting without concern for his master, the judge-as-agent could be brought to heel by his master when he is derelict in his duties, however they are framed. That is, the it is exactly the lack of oversight that makes the judicial office remarkable. If judges fit easily into the framework of the democratic republic, it is not because they are indirectly representative of the popular will. In my view, judges fit into our democratic framework not because they choose to exercise their power in popular ways but because they do not actually exercise personal power at all. Alexander Hamilton captured this idea succinctly with his observation that federal judges have neither force nor will, only judge would be subject to effective oversight. Nevertheless, judgment. Unlike executing the law, which is the President's role, or making the law, which is the Congress's, judging is a passive process. A judge confronts the law as it is written and the facts as they have been placed in evidence. His power may be great over the parties before him, but almost none of it-if exercised properly-can be exerted to advance a judge's own objectives. It is to guarantee this neutrality that he is given independence. Consider a criminal case. Congress enacts a statute that makes certain conduct a crime and provides a punishment. Someone violates that law. The Attorney General, who is the President's appointee, then prosecutes. Only upon the confluence of these events does the judge become involved. With the government and the defendant before him, the judge evaluates whether the specific acts committed by the defendant fall within the ambit of the statute. Whereas the Congress had broad latitude in formulating the substance of the statute and the President and his officers had significant discretion in their selection of targets and enforcement strategies, the judge has almost no discretion over the course and outcome of the prosecution. If the law has been correctly enforced against the defendant, the judge must announce the defendant's conviction; conversely, if the law has not been correctly enforced against the defendant, the judge must acquit. The role of the judge is thus limited to determining whether the law has been enforced "correctly." This determination is traditionally conceptualized as having two elements. First, the relevant facts must be wholly and accurately established; second, the law must be faithfully applied to the relevant facts. The skeptic will wonder how it is that the judge can be thought to be any more intrinsically "accurate" or "faithful" than the prosecutor who comes before him. That is a fair question, and it gets to the heart of the role of the judge. Those terms are meant to depict the consequences of the decision-making process rather than any metaphysical qualities of the decisions themselves. That is, judicial determinations are presumed to be accurate and faithful exactly because they are made by someone acting solely as a judge: a person who is new to the dispute (and thus without any vested interest in the outcome), is drawing conclusions through due process of law in the context of an open and adversarial presentation (in contrast to a one-sided investigation), and is independent (not answerable to the President or Congress). This presumption, it should be emphasized, does not rest on some unsubstantiated premise that judicial decisions are by their nature good decisions. That is to say, the argument is not that a decision is "good" because it is made by someone who acts like a judge; rather, a decision is "good" because it is made within an accuracy-enhancing procedure, and judicial decisions also tend to be "good" because that same procedure is the one that judges use. The Supreme Court has expressly acknowledged that the marginal improvement secured by this procedure can have constitutional significance even in the context of decisions that are not traditionally reserved to judges. In the 1970 case of Goldberg v. Kelley, the Court concluded that a state could not constitutionally terminate benefits to a welfare recipient without an adversarial hearing. In prescribing the indispensable elements of the constitutionally mandated pre-termination proceeding, the Court stated: "The fundamental requisite of due process of law is the opportunity to be heard." The hearing must be "at a meaningful time and in a meaningful manner." In the present context these principles require that a recipient have timely and adequate notice detailing the reasons for a proposed termination, and an effective opportunity to defend by confronting any adverse witnesses and by presenting his own arguments and evidence orally. These rights are important in cases such as those before us, where recipients have challenged proposed terminations as resting on incorrect or misleading factual premises or on misapplication of rules or policies to the facts of particular cases. The Court's observations underscore the importance of several attributes that are intrinsic to judicial decision-making but typically absent from executive and legislative decision-making: a neutral arbiter, written notice to the concerned parties, confrontation of adverse witnesses, and opportunity for oral argument. Unsurprisingly, the Court found these attributes to be critical when rules are applied to "the facts of particular cases." The constitutional underpinnings of the Supreme Court's decision in Goldberg v. Kelly remind us of an essential element of the judicial inquiry into whether the law has been faithfully applied. Judges must consider not just the relevant statute whose vindication the executive specifically seeks, but also the procedural and substantive provisions of law that protect individuals from governmental misconduct and overreaching. In short, judges must ensure that the statute at issue does not, in either its enactment or its enforcement, invade that sphere of constitutional liberty preserved for the individual. Law and liberty will inevitably conflict. Every individual at his liberty may do anything he is physically capable of doing. An individual under law, however, may do only what the law has not proscribed, and this will certainly be less than what the individual might otherwise do. Thus, an individual cannot enjoy absolute liberty under the rule of law. In this light, the rule of law seems distinctly unattractive. Even in that most salubrious of states, the democratic republic, absolute liberty is lost-subsumed to the will of one's community. The loss of some liberty, however, can improve the value of the remainder. As Thomas Hobbes persuasively observed some three hundred and fifty years ago, too much liberty results not in happiness but despair: [D]uring the time men live without a common power to keep them all in awe, they are in that condition which is called war, and such a war as is of every man against every man. . . . In such condition there is no place for industry, because the fruit thereof is uncertain: and consequently no culture of the earth; no navigation nor use of the commodities that may be imported by sea; no commodious building; no instruments of moving and removing such things as require much force; no knowledge of the face of the earth; no account of time; no arts; no letters; no society; and, which is worst of all, continual fear and danger of violent death; and the life of man solitary, poor, nasty, brutish, and short. In the face of such a prospect, we are only too happy to surrender some of our liberty to law. We continue to wonder, however, just how much liberty we should be surrendering. Too much liberty results in life that is "nasty, brutish, and short," but, as the lives of people in the totalitarian states of the twentieth century made painfully clear, too much law is no better. One can view the guarantees of individual rights in the Constitution as our nation's documented consensus on where to draw the limits of law. At the Founding, we viewed the Constitution and the Bill of Rights as constraining the scope of the national government almost exclusively. That government, imperious and remote, seemed more likely to capitalize upon our collective abdication of individual liberty in a way that would degrade our lives rather than enhance them. We were understandably Page 42 loath to abdicate too much. At the same time, however, we left to the states relatively unfettered authority to intrude into spheres that we now consider inviolably personal. Most states lacked provisions analogous to the federal Bill of Rights. Our consensus on the appropriate limits of the law changed, however, by the end of the Civil War. During Reconstruction, congressional Republicans sought to prevent the reemergence of the sort of oppressive state law that had been increasingly relied upon to prop up slavery in the antebellum South. The Republicans thus proposed and spearheaded the ratification of the Fourteenth Amendment, whose terms imposed upon the states most of the provisions of the Bill of Rights. As a result, the line between law and liberty encroached further on the power of the state and gave individual liberty a wider scope. The constitutional compromise between law and liberty has always been subject to dispute. Many people believe that the government is much more substantially limited in what it may do than is apparent on the face of the Constitution. Others contend the opposite. Occasionally, the dispute has resulted in the revision of the Constitution, as with the Fourteenth Amendment; most of the time, however, the judge in any given case must prevent a partisan in the dispute from getting the upper hand. In short, the judge must defend the constitutional compromise between law and liberty as memorialized in the text of the Constitution itself. To alter the compromise (or to allow it to be altered) is not no such revision has occurred. In discharging his duty to determine whether the law has been faithfully applied, faithfully to apply the Constitution but to amend it-to usurp a power reposed exclusively in the people of the United States. Preserving the constitutional compromise between law and liberty requires federal judges to defer to the legislative and executive branches on all issues properly within the realm of the law. If the text of the Constitution does not preclude the government's action, the judge must uphold it. He must do so even if the government's action is patently unfair or plainly inappropriate, for determining that something is the power to direct government action pursuant to one's own will is precisely the power that a judge lacks. The judge's duty to apply the law faithfully demands that he do more than merely defer to the political branches of government when they permissibly exercise governmental power. The very concept of law requires the judge to apply it in a manner that is both predictable and uniform. "unfair" or "inappropriate" without an independent standard for fairness or appropriateness requires an exercise of sheer will. And Predictability ensures that everyone knows what the law is at any given point in time. Uniformity ensures that the law is applied in the same way by any judge to any party anywhere When a judge is swayed by his own sentiment rather than considerations of deference, predictability, and uniformity, he fails by definition to apply the law faithfully. This is the essence of judicial activism. It is impossible to say with certainty in any given case that the in the country. judge's sentiments will lead him to a "bad" decision, but no one could say that they never would. Any of us would appreciate a judge's merciful departure from a draconian law. How many of us, though, would appreciate a judge's draconian departure from a merciful law? The remedy for a bad law is to change the law through legislative action, not to depart from it one way or the other in the courts. The solution, in short, is democracy-the political process-and not judicial activism. Judicial activism is not always easily detected, because the critical elements of judicial activism either are subjective or defy clear and concrete definition. For instance, a critical consideration is the state of mind of the allegedly activist judge. Judicial activism means not the mere failure to defer to political branches or to vindicate norms of predictability and uniformity; it means only the failure to do so in order to advance another, unofficial objective. Occasionally, the fact that a judge has an ulterior motive is evident, but oftentimes it is not. We are left to infer the existence of an ulterior motive from the relative distances that separate the judge's actual decision from the decision that would have been correct and the one that would have most perfectly accorded with the judge's personal sentiments. This gives rise to another difficulty in detecting judicial activism, which is that we must establish a non-controversial benchmark by which to evaluate how far from the "correct" decision the supposedly activist judge has strayed. Occasionally this, too, is easy-but not always. Because of the inherent difficulty in detecting judicial activism with any certainty, many activist decisions may pass without significant criticism and many others may be labeled by particularly sensitive commentators as "activist" when they are not. Perhaps the most notorious instance of judicial activism is captured in the century-old Supreme Court case, Rector of the Holy Trinity Church v. United States. Congress had enacted a statute declaring that it shall be unlawful . . . in any manner whatsoever, to prepay the transportation, or in any way assist or encourage the importation or migration, of any alien . . . into the United States . . . to perform labor or service of any kind. Because the defendant church had contracted with an English clergyman to come to New York City to serve as rector, the government brought suit under this statute. Both the trial and appellate courts ruled that the Church had violated the law. The Supreme Court disagreed. After observing that "this is a Christian nation," Justice Brewer reached the remarkable conclusion for the Court that religious ministry could not have been the "labor or service of any kind" that Congress had intended to proscribe. Justice Brewer plainly thought, and all of his brethren agreed, that his departure from the statute did nothing but benefit the American people. Even if it was well received at the time, the Court's characterization of the country might not be so benignly received today, particularly as the basis for departing from a statute duly enacted by our democratically elected representatives. The problem with the Court's decision was that it undermined the predictability and uniformity of the law. Before the Supreme Court ruled, the statute was clear; afterwards, no one could predict its true scope. Moreover, lower courts would now be free to apply whatever exemptions they, too, thought Congress Judicial activism might have intended, regardless of the language Congress actually enacted. can have consequences that are far more profound than the unregulated immigration of nineteenth-century English rectors. When applied not simply to arcane statutes but to the United States Constitution-the foundational document of our Republic- works a seismic shift in the balance between government and individual judicial activism inevitably and has often done so on divisive questions. Take, for example, the question of whether an individual's decision to end his own life is beyond the power of the government to regulate. After the people of the State of Washington rejected the ballot measure at the polls, several Washington residents brought suit and invited judges to give them what the legislative process would not: a governmentally enforceable right to assisted suicide. The United States Court of Appeals for the Ninth Circuit, which includes Washington and eight other Western states, eventually ruled for the plaintiffs, declaring that the Constitution guaranteed each of them a "right to die." This decision, though purportedly compelled by the federal Constitution, rested upon nothing written in that document. Eight judges of the eleven-judge panel hearing the case simply promulgated a new constitutional right, one unheard of in over two hundred years of American history. The Supreme Court, in Washington v. Glucksberg, recognized the Ninth Circuit's decision for the rejection of democracy that it was and unanimously reversed, but not before rivers of ink had flowed in celebration or condemnation of a judgment that seemed intrinsically more political than judicial. Perhaps the outcome reached by the Ninth Circuit was the better policy, arguably someone who is terminally ill and wants to end his life really should not have to act alone. It is certain that many people other than the plaintiffs in the Glucksberg case thought so. Even if it were true, which seems rather difficult to ascertain in any objective sense, this belief does not establish that the court made the right decision, because the court was wrong to make the decision at all. Readers who resist this conclusion need only look at the experience of the people of Oregon. Unlike their northern neighbors, a majority of Oregonians went to the polls only a couple of years later and enacted a law giving a terminally ill individual the right to physician-assisted suicide. Nevertheless, just like their northern neighbors, the people of Oregon were rebuked by a federal court declaring that they had overstepped the scope of governmental authority. In that case, entitled Lee v. Oregon, a federal judge held that in his view there was "no set of facts" in which Oregon's newly enacted assisted suicide law could be considered "rational." That conclusion must have come as quite a surprise to the thousands upon thousands of Oregonians who voted for the law. Surely, the conclusion must have unsettled the view of the eight Ninth Circuit judges who had previously joined together in declaring that the Constitution guaranteed the very right to assisted suicide that the same Constitution was now being read to preclude the people of Oregon from enacting. This uncomfortable tension was resolved when the Ninth Circuit reversed the Lee decision and returned the issue of assisted suicide once again to the realm of political discourse, where it belongs. Even for someone who cares not a whit about whether an individual has the right to assistance in committing suicide, these cases underscore the problems that arise when judges purport to apply the law but fail to apply it faithfully-the problems, that is, of judicial activism. The first of these our democratic republic descends into what Thomas Jefferson famously reviled as "oligarchy." The will of one judge or a handful is substituted for the will of the popular majority-or, at the very least, the political representatives elected problems is, of course, that by and accountable to that majority. Moreover, because judges exert their will, when they do, by pronouncements applied retroactively in individual cases rather than by codified statutes or rules, the resulting "law" not only lacks democratic validity but predictability and uniformity as well. Decisions that manifest judicial activism do not, in short, amount to A judicially active interpretation of the Constitution shifts the dividing line between government power and individual liberty. what we think of as "law" at all. When it involves constitutional interpretation, judicial activism presents a unique additional problem. That judge-made shift, unless subsequently repudiated by the Supreme Court, can be remedied only by a constitutional amendment. Ratification of such an amendment, which The consequence of all of this is that judicial decisions redefining individual liberties distort the delicate balance of power between the branches of government. What Congress could once do by the relatively straightforward process of statutory enactment, it can thereafter do only by discharging the Herculean task of constitutional amendment. Not only does judicial activism in whatever form hobble the political branches of government, it also undermines the requires supermajorities at both federal and state levels, is arduous by design and, when undertaken, is rarely successful. Page 43 judiciary itself. Courts, lacking the power to enforce their own judgments, rely on popular confidence in those judgments for their implementation. Judicial activism erodes this confidence and thereby erodes the efficacy of the judiciary as a whole. One need not look far to find the breakdown of confidence in, and resulting threat to the independence of, judicial decision-making. By far the most famous such incident occurred with the advent of the New Deal in the 1930s. Franklin Delano Roosevelt had been elected President after campaigning on the promise of federal relief from the widespread economic dislocation accompanying the Great Depression. Upon his inauguration, President Roosevelt proposed and, with the assent of the Congress, enacted into law an unprecedented program of economic reform. After the Supreme Court invalidated several popular statutes at the core of the President's program, the President pursued a plan to "pack" the Supreme Court. He proposed to increase its membership so that he could appoint enough new Justices to win a majority in future cases. The plan was never executed because, faced with this threat, the Supreme Court relented and upheld subsequent legislation. It thus appeared that the Supreme Court very nearly became the casualty of its own political assaults on judicial decisions judicial activism. Far from being merely a product of the exigencies of the Great Depression, specific still occur. In the last presidential election, both parties' nominees openly criticized a federal trial judge in New York for his refusal to admit as evidence in a drug prosecution large amounts of cocaine seized by law enforcement officers. After President Clinton suggested on the campaign trail that the judge might resign his office, the judge reconsidered his ruling and raises the disturbing specter of judicial decisionmaking by popular will, and the fear that our judges might have become little more than politicians in robes. What lesson can we learn from these experiences? Judicial activism generates a vicious cycle: it triggers a lack of confidence in judicial decisions which triggers political meddling which reinforces a lack of confidence in judicial reversed it. This incident, like the Supreme Court's about-face sixty years earlier, decisions. A politician in robes is no judge at all. Once a judge imposes his will as legislator, he loses his democratic legitimacy. No one person in a democratic society of 270 million A judge who wields power like a politician enters the political process. Having forsaken neutrality, he will soon lose his independence. The people will allow a judge to be independent only for as long as they perceive him as truly neutral-forsaking decisions based upon his own interests and biases. Thus, judicial activism encourages political interference both in the process of judging and selection of judges. One need look no further than the current battle between the White House and the Senate over judicial nominees for a glimpse of the extent to which the judicial citizens should wield legislative power if only fifty-two people have approved of him. appointments process has become politicized. Nor does the threat of political interference end after the judge is selected. A multitude of proposals have been offered in Congress to weaken the independence of the judiciary. Some take the form of constitutional amendments to impose term limits on judges; others have been nothing more sophisticated than calls Fortunately, judges retainat least for now-their independence to apply the law neutrally and faithfully. But so long as one judge indulges his own for the impeachment of particular judges who have rendered unpopular decisions. These may be only harbingers of what is to come. sympathies rather than following the text of the law before him, he will only make it harder for his colleagues to retain the courage to decide cases in faithful, predictable, and uniform ways. That collapses our global democratic model Sobel, President of the American Judicature Society, 5 (Allan, “Executive Director's Report: POLITICAL ASSAULT ON THE JUSTICE SYSTEM,” Judicature, March – April, 88 Judicature 197) This unprecedented effort of Congress, with assistance from the Executive Branch, to reenergize a private dispute that had already been considered, reconsidered, and resolved by the courts, sets a dangerous precedent and has degenerated into an alarming affront against the delicate balance of power that sustains our democracy. The American Judicature Society Political ambition and political rancor are once again driving our justice systems to a crossroads of either (1) stability through independence, accountability, and respect, or (2) timidity and submissiveness through unfair and intemperate criticism, irresponsible threats, and direct assault on their jurisdiction and powers. Our courts are constitutionally charged with the interpretation of the laws of the land and the protection of our constitutional rights. The judicial branch is uniquely dependent on what the late Judge Richard Arnold called “the continuing consent of the governed” to fulfill its mission of interpreting the law and resolving peacefully seemingly irreconcilable differences. If the courts do not have the support of, and are not shown due is most concerned about the toll this is taking on our courts. deference by, elected officials, how can we expect citizens, our friends and neighbors, to uphold the sanctity of the law of the land? To meet their common responsibility of protecting and empowering the citizens of this country, the navigators of each branch of government must remain above the fray of increasing moral and political polarization, resist resorting to Our democratic government has been challenged often during its history. It has been wounded over the years by destructive forces from both outside and inside its borders. Through each such ordeal, however, America has survived and grown stronger to become the leader of the free world, with the opportunity to serve as an example for emerging democracies around the globe. We could not do so without a strong, independent, and genuinely respected justice system, at local, state, and federal levels. The United States at present is the object of unusually intense scrutiny and virulent criticism from all parts of the world. At a time when we are asking, and in some cases directing, governments across the globe to follow the lead of the United States to achieve freedom and democracy, it is paramount that the United States, as an example to others, embody and practice the ideals of the Constitution. It is the sworn duty of our elected officials to respect and protect the judicial branch. It is the mutual respect of every branch of government that has enabled the country to survive and thrive in spite of significant hardship and challenges to its existence. incendiary rhetoric for selfish gain, and above all embrace due respect for and deference to one another. It is not difficult to understand the powerful emotions welling up in Terri Schiavo's family members and other caring and thoughtful people as they watched from the sidelines the 13day dénouement of her life. And in this day when moral outrage, religious zeal, and media sensationalism are the norm in America, one might forgive reckless and emotionally*231 charged, irrational statements directed at those judges, both elected and appointed, who some may deem to be responsible for her death . . . unless those reckless and irrational Congress and the Executive must be statements emanate from our elected members of government. For it is the members of those in power in Branch who held to a higher standard, who more than anyone must bear responsibility for safeguarding the strength and stability of our courts. The American Judicature Society calls on all Page 44 respect and support for an independent judiciary as guardian and arbiter of the rule of law. For history demonstrates that a judiciary independent of special interests and partisan politics may be necessary to mend the torn seams of this vast and diverse country. The alternative, vividly suggested in some of the actions and words of recent weeks, is anarchy. participants in our government, citizens and holders of elected office alike, to step back and recommit to Page 45 2NC Court Legitimacy DA Our argument straight turns their internal links – If the court loses it’s legitimacy, it won’t be effectively modeled by other countries AND even if it is modeled, the model is a bad one where the court has TOO MUCH POWER. Limitless judicial review UNDERMINES stable democracies. Zakaria, Editor of Newsweek & Managing Editor at Foreign Affairs, 97 (Fareed, “The Rise of Illiberal Democracy,” Foreign Affairs, November / December) The distinction between liberal and illiberal democracies sheds light on another striking statistical correlation. Political scientists Jack Snyder and Edward Mansfield contend, using In countries not grounded in constitutional liberalism, the rise of democracy often brings with it hyper-nationalism and war-mongering. When the political system is opened up, diverse groups with incompatible interests gain access to power and an impressive data set, that over the last 200 years democratizing states went to war significantly more often than either stable autocracies or liberal democracies. press their demands. Political and military leaders, who are often embattled remnants of the old authoritarian order, realize that to succeed that they must rally the masses behind a national cause. The result is invariably aggressive rhetoric and policies, which often drag countries into confrontation and war. Noteworthy examples range from Napoleon III's France, Wilhelmine Germany, and Taisho Japan to those in today's newspapers, like Armenia and Azerbaijan and Milosevic's Serbia. The democratic peace, it turns out, has little to do with democracy. THE AMERICAN PATH AN AMERICAN SCHOLAR recently traveled to Kazakstan on a U.S. government-sponsored mission to help the new parliament draft its electoral laws. His counterpart, a senior member of the Kazak parliament, brushed aside the many options the American expert was outlining, saying emphatically, "We want our parliament to be just like your Congress." The American was horrified, recalling, "I tried to say something other than the three words that had immediately come screaming into my mind: 'No you don't!'" This view is not unusual. Americans in the democracy business tend to see their own system as an unwieldy contraption that no other country should put up the adoption of some aspects of the American constitutional framework could ameliorate many of the problems associated with illiberal democracy. The philosophy behind the U.S. Constitution, a fear of accumulated power, is as relevant with. In fact, today as it was in 1789. Kazakstan, as it happens, would be particularly well-served by a strong parliament -- like the American Congress -- to check the insatiable appetite of its president. It is odd that the United States is so often the advocate of elections and plebiscitary democracy abroad. What is distinctive about the American system is not how democratic it is but rather how undemocratic it is, placing as it does multiple constraints on electoral majorities. Of its three branches of government, one -- arguably paramount -- is headed by nine unelected men and women with life tenure. Its Senate is the most unrepresentative upper house in the world, with the lone exception of the House of Lords, which is powerless. (Every state sends two senators to Washington regardless of its population -- California's 30 million people have as many votes in the Senate as Arizona's 3.7 million -which means that senators representing about 16 percent of the country can block any proposed law.) Similarly, in legislatures all over the United States, what is striking is not the power of majorities but that of minorities. To further check national power, state and local governments are strong and fiercely battle every federal intrusion onto their turf. Private businesses and other nongovernmental groups, what Tocqueville called intermediate associations, make up another stratum within society. The American system is based on an avowedly pessimistic conception of human nature, assuming that people cannot be trusted with power. "If men were angels," Madison famously wrote, "no government would be necessary." The other model for democratic governance in Western history is based on the French Revolution. The French model places its faith in the goodness of human beings. Once the people are the source of power, it should be unlimited so that they can create a just society. (The French revolution, as Lord Acton observed, is not about the limitation of sovereign power but the abrogation of all intermediate powers that get in its way.) Most non-Western countries have embraced the French model -- not least because political elites like the prospect of empowering the state, since that means empowering themselves -- and most have descended into bouts of chaos, tyranny, or both. This should have come as no surprise. After all, since its revolution France itself has run through two monarchies, two empires, one proto-fascist dictatorship, and five republics. n9 Of course cultures vary, and different societies will require different frameworks of government. This is not a plea for the wholesale adoption of the American way but rather for a more variegated conception of Before new policies can be adopted, there lies an intellectual task of recovering the constitutional liberal tradition, central to the Western experience and to the development of good government throughout the world. Political progress in Western history has been the result of a growing liberal democracy, one that emphasizes both parts of that phrase. recognition over the centuries that, as the Declaration of Independence puts it, human beings have "certain inalienable rights" and that "it is to secure these rights that governments are instituted." If a democracy does not preserve liberty and law, that it is a democracy is a small consolation. LIBERALIZING FOREIGN POLICY A PROPER appreciation of constitutional liberalism has a variety of implications for American foreign policy. First, it suggests a certain humility. While it is easy to impose elections on a country, it is more difficult to push constitutional liberalism on a society. The process of genuine liberalization and democratization is gradual and long-term, in which an election is only one step. Without appropriate preparation, it might even be a false step. Recognizing this, governments and nongovernmental organizations are increasingly promoting a wide array of measures designed to bolster constitutional liberalism in developing countries. The National Endowment for Democracy promotes free markets, independent labor movements, and political parties. The U.S. Agency for International Development funds independent judiciaries. In the end, however, elections trump everything. If a country holds elections, Washington and the world will tolerate a great deal from the resulting government, as they have with Yeltsin, Akayev, and Menem. In an age of images and symbols, elections are easy to capture on film. (How do you televise the rule of law?) But there is life after elections, especially for the people who live there. Conversely, the absence of free and fair elections should be viewed as one flaw, not the definition of tyranny. Elections are an important virtue of governance, but they are not the only virtue. Governments should be judged by yardsticks related to constitutional liberalism as well. Economic, civil, and religious liberties are at the core of human autonomy and dignity. If a government with limited democracy steadily expands these freedoms, it should not be branded a dictatorship. Despite the limited political choice they offer, countries like Singapore, Malaysia, and Thailand provide a better environment for the life, liberty, and happiness of their citizens than do either dictatorships like Iraq and Libya or illiberal democracies like Slovakia or Ghana. And the pressures of global capitalism can push the process of liberalization forward. Markets and morals can work together. Even China, which remains a deeply repressive regime, has given its citizens more autonomy and economic liberty than they have had in generations. Much more needs to change before China can even be called a liberalizing autocracy, but that we need to revive constitutionalism should not mask the fact that much has changed. Finally, . One effect of the overemphasis on pure democracy is that little effort is given to creating imaginative constitutions for transitional countries. Constitutionalism, as it was understood by its greatest eighteenth century exponents, such as Montesquieu and Madison, is a complicated system of checks and balances designed to prevent the accumulation of power and the abuse of office. This is done not by simply writing up a list of rights but by constructing a system in which government will not violate those rights. Various groups must be included and empowered because, as Madison explained, "ambition must be made to counteract ambition." Constitutions were also meant to tame the passions of the public, creating not simply democratic but also deliberative government. Unfortunately, the rich variety of unelected bodies, indirect voting, federal arrangements, and checks and balances that characterized so many of the formal and informal constitutions of Europe are now regarded with suspicion. What could be called the Weimar syndrome -- named after interwar Germany's beautifully constructed constitution, which failed to avert fascism -- has made people regard constitutions as simply paperwork that cannot make much difference. (As if any political system in Germany would have easily weathered military defeat, social revolution, the Great Depression, and hyperinflation.) Procedures that inhibit direct democracy are seen as inauthentic, muzzling the voice of the people. Today around the world we see variations on the same majoritarian theme. But the trouble with these winner-take-all systems is that, in most democratizing countries, the winner really does take all. DEMOCRACY'S DISCONTENTS WE LIVE IN a democratic age. Through much of human history the danger to an individual's life, liberty and happiness came from the absolutism of monarchies, the dogma of churches, the terror of dictatorships, and the iron grip of totalitarianism. Dictators and a few straggling totalitarian regimes still persist, but increasingly they are anachronisms in a world of global markets, information, and media. There are no longer respectable alternatives to democracy; it is part of the fashionable attire of modernity. Thus the problems of governance in the 21st century will likely be problems within democracy. This makes them more difficult to handle, wrapped as they are in the mantle of legitimacy. Illiberal democracies gain legitimacy, and thus strength, from the fact that they are reasonably democratic. Conversely, the greatest danger that illiberal democracy poses -- other than to its own people -- is that it will discredit liberal democracy itself, casting a shadow on democratic governance. This would not be unprecedented. Every wave of democracy has been followed by setbacks in which the system was seen as inadequate and new alternatives were sought by ambitious leaders and Page 46 restless masses. The last such period of disenchantment, in Europe during the interwar years, was seized upon by demagogues, many of whom were initially popular and even elected. the most useful role that the international community, and most importantly the United States, can play is -- instead of searching for new lands to democratize and new places to hold elections -- to consolidate democracy where it has taken root and to encourage the gradual development of constitutional liberalism across the globe. Democracy without constitutional liberalism is not simply inadequate, but dangerous, bringing with it the erosion of liberty, the abuse of power, ethnic divisions, and even war. Eighty years ago, Woodrow Wilson took America into the twentieth Today, in the face of a spreading virus of illiberalism, century with a challenge, to make the world safe for democracy. As we approach the next century, our task is to make democracy safe for the world. The real basis of democracy and for our democratic model is allowing the people themselves to determine what the Constitution means. The plan sucks out the vitality of popular constitutionalism and our democratic model. Kramer, Law Professor at NYU, 1 (Larry, “THE SUPREME COURT 2000 TERM: FOREWORD: WE THE COURT,” Harvard Law Review, November, 115 Harv. L. Rev. 4) the current Supreme Court has, by slow degrees, begun systematically to extend the reach of judicial review. The Rehnquist Court has, quite simply and literally, abandoned the New Deal settlement, reoccupying ground taken for the people in the 1930s without yielding so much as an inch of territory already held. Change, in itself, is Which brings us, finally, to the Rehnquist Court. In a manner not unlike the Court of the Gilded Age, not necessarily wrong. The New Deal system for reconciling judicial supremacy with popular constitutionalism was not the only one possible, and there could be a better one. But the Rehnquist Court has not offered an alternative accommodation. It has, rather, disowned the notion of popular constitutionalism altogether, staking its claim to be the only body empowered to interpret fundamental law with authority. Congress gets to have its say, of course, because the Court reviews actions the legislature has already [*128] taken. But what Congress thinks about the Constitution carries no formal legal weight in the eyes of the Rehnquist Court, and has only so much practical weight as the Justices think it deserves (which typically turns out to be not much). A majority of the Court may decide that something is constitutionally permitted, but the notion that the decision whether the thing is permitted might be somebody else's to make is fast disappearing. More remarkably still, the Justices have not even tried to explain or justify this grab for power - apparently taking it as obvious, as their right, because the Constitution is "law" and because, if the Constitution is "law," this must mean the whole Constitution. Naturally, assumptions such as these run into difficulty when faced the Rehnquist Court has simply repudiated cardinal principles of twentieth-century jurisprudence (including rational basis scrutiny with judicial doctrines developed under different assumptions. But rather than question the rightness of what it is doing, of ends-means relationships and deferential review of facts), casting aside a century and a half of hard-earned experience in a spasm of "law is law" formalism. Worse, the Court's felt The Rehnquist Court has thus devised rules that artificially limit the authority of lawmakers because it finds such rules necessary to ensure its ability to dominate constitutional interpretation. The result is a Constitution that is less and does less, and for no better reasons than the Court's low opinion of Congress and desire to protect its position as king of the hill. Identifying the origins of this drift toward judicial exclusivity is not easy. I suspect that it began need to maintain its interpretive supremacy - to ensure that it alone controls the meaning of the Constitution - has itself become a doctrine-shaping imperative. before the Rehnquist Court, sometime in the years after Cooper v. Aaron. Controversy over judicial supremacy (though not over the Court's decisions) subsided just as the Justices became increasingly active and ambitious in their interpretations of individual rights. Apart from enforcing these rights, the Warren and Burger Courts made no serious effort to limit the powers of Congress. This may have been because their members had no interest, and not because they were self-consciously committed to a New Deal vision of popular constitutionalism, but unarticulated and incipient understandings were irrelevant so long as the actual terms of the settlement were observed. Yet in this environment, the meaning of the struggle that had been waged to preserve the people's role in defining fundamental law was gradually forgotten, and a notion of the Constitution as nothing more than ordinary positive law, subject to Supreme Court supervision, came to be pervasively held - by liberals as well as by conservatives, by lawyers as well as by nonlawyers. Based on this understanding, conservative critics began to present the Court's failure to secure a judicial vision of Article I as a sellout, a failure by the Justices to live up to their constitutional responsibilities in an important domain. This had no consequences outside the academy so long as the [*129] Court remained in liberal hands. It is only since the consolidation of a solid conservative majority on the Court, able and willing to be as activist in the domains it cares about as the liberal Court had been in protecting individual rights, that this changed background understanding has started to bear fruit. While this may make the shift explicable, it does not make it any the less a matter of concern. We are witnessing a constitutional revolution, but not the one depicted in the press. The difference between the Rehnquist Court and the Warren Court is not just It is not just the reinvigoration of judicially enforced federalism. Triumphant conservative taunts that what is sauce for the goose is sauce for the gander miss the point. The Rehnquist Court's activism explicitly denies the people any role in determining the ongoing meaning of their Constitution, other than by the grace of the Justices the beginnings of a matter of activism in different domains. themselves (or by the cumbersome process of formal amendment). The practical consequences of this denial are clear in the Court's decisions, which have stripped the federal A Constitution that truly is nothing more than ordinary law, that has ceased to be the people's law in any meaningful sense, is as unwarranted as it is unprecedented. Popular constitutionalism has been an indispensable element of American government from the beginning, the most profound reflection of what the American Revolution was all about. To squeeze "the people" out of the Constitution is to squeeze the life out of it. government of important powers. But its philosophical and, yes, its symbolic importance should not be missed either. Page 47 The plan is too far in the opposite direction – It creates too much judicial review which undermines the foundation of our democracy Kramer, Law Professor at NYU, 5-23-2K (Larry, “The Arrogance of the Court,” Washington Post) The justices did much more in than sweep the act off the books. Under a pretense of interpreting the Constitution, they declared that they have the final say about the expediency of an important, and potentially very large, class of federal laws: not just laws under the This is an astonishing ruling from a court that professes to care about democratic majorities and respect the political process. this decision Commerce Power, which constitute the bulk of modern federal legislation, but many other laws as well. For the limits of all Congress's powers turn eventually on judgments about the Previous courts have exercised aggressive judicial review, but never like this. Nothing in the Constitution's language or history supports letting the Supreme Court strike down laws just because it disagrees with Congress's assessment of how much they are needed. Except for a brief period in the 1930s when an earlier court tried to stop FDR's New Deal and was decisively repudiated, the court's role has always ended once it was clear that legislation was rationally related to the exercise of a constitutional power. As Alexander need for federal action. This is radical stuff. Hamilton observed back in 1792, rejecting the very same argument as that made by the court today, "the degree in which a measure is necessary can never be a test of the legal right to judicial review must be contained or we lose the essence of self-government. They saw that, while courts have a vital role to play in protecting individuals and minorities from laws that trample their rights, Congress's decisions respecting the need to exercise its legislative power must otherwise be left to voters and elections. They foresaw that questions would arise over adopt it." The Founding generation understood, in a way our generation seems to have forgotten, that the limits of federal authority vis-a-vis the states. But, they said (over and over again), those battles must be waged in the political arena. And so they have been, until now. What kind of government is it when five justices of the Supreme Court, appointed for life by presidents whose mandates expired long ago, can cavalierly override the decision of a democratically elected legislature not on the ground that it acted irrationally but because they do not like its reasoning? By what right do these judges claim the authority to second-guess what Justice Souter in dissent accurately described as a "mountain of data" based on nothing more than their contrary intuitions? This is important. We have become way too complacent about letting the Supreme Court run our lives, and the current court has exploited this apathy to extend its authority to unheard of lengths. Everyone in the country should be incensed by this decision: not because the Violence Against Women Act was so wonderful or so necessary, but because deciding that it is not--and make no mistake, that is all the majority did--is none of the Supreme Court's business. Yet liberals will sit awkwardly by because they liked the judicial activism we got from the Warren court, though that court could not touch this one for activism. And, of course, conservatives will gleefully hold their tongues because they never much liked this law in the first place, and because they adore the court's new federalism (not to mention the chance to see liberals hoist by their own petard). In the meantime, only democratic government suffers. Ironies this thick would be comical were the stakes not so high. Page 48 Disease DA Page 49 1NC Disease Public health surveillance solves pandemics Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka Public Health Surveillance A. Modern Public Health Surveillance The history of public health surveillance and public health interventions is both fascinating and complicated: A full account is far beyond the scope of this paper. n11 However, two observations based on that history frame my argument. First, the basic features of modern public health surveillance are not new; they were developed as responses to serious contagious disease. Second, public health surveillance in the United States has, in general, enabled interventions which - criticisms aside - have effectively addressed the public health crises they targeted. n12 To give just one example, the surveillance and interventions conducted using New York City's nineteenth-century tuberculosis registry prevented the spread of tuberculosis. n13 The program was accompanied by an impressive array of free services that helped to prevent and treat the disease. City and charitable organizations disinfected homes after a tubercular patient had moved or died, treated patients in facilities established across the City, created open-air programs for children and adults, and provided financial and logistical aid to tubercular patients. n14 Other municipalities offered similar services to patients. n15 [*1955] While public health surveillance has undergone radical changes n16 - with technological developments, epidemiologic shifts, and the rapid expansion and coordination of public health surveillance activities transforming a disparate collection of municipalities, each battling contagion, into a sophisticated, coordinated, and pervasive public health apparatus - the purpose remains the same: to collect and compile information about sick people over time, and then use that information to protect the public health . A cursory review of government public health activities since the late medieval period demonstrates that " throughout history , governments have performed their public health role by ... taking steps to prevent the spread of epidemics ." n17 Mandatory quarantine programs - "features of most port towns" in colonial America - provide a dramatic example of surveillance-based public health interventions. n18 The relevant point is that surveiling individuals to protect the public health is anything but new. Indeed, the New York City Department of Health and Mental Hygiene intentionally modeled the A1C Registry - the paradigm of emergent public health surveillance - upon nineteenth-century surveillance and intervention programs that targeted tuberculosis. n19 The innovations - and the problems - at the heart of emergent programs are that they target individuals who pose no health risk to others, and they employ technology that enables surveillance that is virtually unlimited in scope. That’s the only way to prevent extinction Casadevall 12 March 21st, 2012, Arturo Casaveall is a professor of Microbiology and Immunology at the Albert Einstein College of Medicine, Arturo, “The future of biological warfare,”http://onlinelibrary.wiley.com/doi/10.1111/j.1751-7915.2012.00340.x/full In considering the importance of biological warfare as a subject for concern it is worthwhile to review the known existential threats. At this time this writer can identify at three major existential threats to humanity: (i) large-scale thermonuclear war followed by a nuclear winter, (ii) a planet killing asteroid impact and (iii) infectious disease. To this trio might be added climate change making the planet uninhabitable. Of the three existential threats the first is deduced from the inferred cataclysmic effects of nuclear war. For the second there is geological evidence for the association of asteroid impacts with massive extinction (Alvarez, 1987). As to an existential threat decades have provided unequivocal evidence for the ability of certain pathogens to cause the extinction of entire species. Although infectious disease has traditionally not been associated with extinction this view has changed by the finding that a single chytrid fungus was responsible for the extinction from microbes recent of numerous amphibian species (Daszak et al., 1999; Mendelson et al., 2006). Previously, the view that infectious diseases were not a cause of extinction was predicated on the notion that many pathogens required their hosts and that some proportion of the host population was naturally resistant. However, that calculation does not apply to microbes that are acquired directly from the environment and have no need for a host, such as the majority of fungal pathogens. For those Page 50 types of host–microbe interactions it is possible for the pathogen to kill off every last member of a species without harm to itself, since it would return to its natural habitat upon killing its last host. Hence, from the viewpoint of existential threats environmental microbes could potentially pose a much greater threat to humanity than the known pathogenic microbes, which number somewhere near 1500 species (Cleaveland et al., 2001; Tayloret al., 2001), especially if some of these species acquired the capacity for pathogenicity as a consequence of natural evolution or bioengineering. Page 51 Spillover Ruling on the Fourteenth amendment reverses the precedent and spills over to all disease surveillance Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka The emergent model brings to the fore questions about the constitutional permissibility of the privacy invasion at the core of public health surveillance programs. In Part II, I describe existing constitutional privacy protections for medical and other personal information. I argue that emergent public health surveillance programs - unlike their predecessors and unlike alternative surveillance models - invade a fundamental privacy interest and should accordingly receive strict scrutiny under the Fourteenth Amendment . My argument is limited to the privacy invasion effected by the government's ongoing and nonconsensual collection of individually-identified health information, like A1C results. I do not address the privacy implications of individually-targeted health interventions. n63 [*1963] II Emergent Public Health Surveillance Intrudes upon a Fundamental Interest Emergent public health surveillance programs intrude upon a privacy interest that courts should recognize as fundamental for purposes of the Fourteenth Amendment . Accordingly, emergent programs should be reviewed under a strict scrutiny standard. n64 The Supreme Court has recognized that the Fourteenth Amendment protects an interest in not disclosing private health information to the government. n65 However, the Supreme Court has never explained the contours of that right. n66 Moreover, lower court opinions that address the constitutionality of government public health surveillance programs are sparse, outdated, and inconsistent. In general, they have upheld public health surveillance programs against privacy challenges, after applying rational basis review or a deferential balancing test. n67 Courts need not and should not apply a deferential standard to emergent programs. In Subpart A, I argue that existing jurisprudence does not require deferential review; in fact, it implicitly and explicitly [*1964] invites more stringent review of emergent programs like the A1C Registry. In Subpart B, I suggest that, to the extent that the constitutionality of the privacy invasion effected by emergent public health surveillance programs remains an open question, recent assessments of security surveillance programs help to provide an answer. I describe three features of security surveillance that have provoked privacy concerns, and that either do or may increase the constitutional protections for privacy afforded under the Fourth Amendment. Because emergent health surveillance programs share those features , courts should similarly enhance the constitutional scrutiny that applies to those programs under the Fourteenth Amendment . In Subpart C, I summarize the argument for applying strict scrutiny to emergent programs. A. Health Information Privacy Precedents This Subpart describes existing Fourteenth Amendment privacy protections that apply to government public health surveillance programs. Those protections are widely understood to be limited , and - to the extent the question has been addressed - scholars assume similarly limited protection would apply to emergent programs. n68 Yes spillover --- the core controversy is the privacy interest and specific targeting which applies equally to infectious disease and the plan Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka Recognizing that the privacy interest at stake is fundamental would trigger strict scrutiny, under which a reviewing court would inquire whether the challenged surveillance program was narrowly tailored to further a compelling government interest. n182 In one sense, the proposed analysis would not depart from past practice. Arguably, the public health surveillance programs reviewed by courts to date have not involved a fundamental privacy interest , due to Page 52 technological limits on the breadth and depth of surveillance, the type of information collected, or program design. In particular, most public health surveillance programs, such as those that involve anonymized or consensual data collection , do not intrude upon a fundamental privacy right at all. In addition, the strict scrutiny analysis may be satisfied when the surveillance model at the heart of emergent programs - ongoing, intimate, and individualized surveillance - targets people with a highly infectious disease in order to prevent the disease from spreading. The critical question is whether emergent surveillance programs satisfy the narrow tailoring requirement of a strict scrutiny analysis . Part III describes one approach to finding an answer. Page 53 Solves Disease Legislative protections solve health --- there’s a precedent Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka Fortunately, a precise definition of the interest invaded by emergent programs is not required: A personal fundamental right to privacy is deeply rooted in this country's history and tradition. A complete account of legal [*1985] and cultural protections for personal privacy is far beyond the scope of this paper, but two examples are particularly worth noting. First, the history of Fourth Amendment jurisprudence demonstrates that the "most sacred of all areas ... is the home," not because "it is a physical structure in which someone chooses to live," but because there is a societal consensus that people have "virtually unlimited expectations of privacy from intrusions" into their homes. n177 A cursory review of Supreme Court cases suggests that we protect the "home" at least in part because it serves as a proxy for personal privacy. n178 Scholars have made the same observation. n179 Moreover, robust Fourth Amendment protection of the home is a product of a deep national commitment to preventing government incursions upon personal privacy that dates to the founding era. n180 Second - and also relevant in the context of emergent public health surveillance programs - there is a clear history of judicial and legislative protections against nonconsensual disclosures of medical information. n181 Page 54 Federalism DA Page 55 1NC Federalism The aff’s ruling on the Fourteenth Amendment devastates federalism Mendenhall 15 --- staff attorney to Chief Justice Roy S. Moore of the Supreme Court of Alabama, adjunct professor at Faulkner University (Allen, “Is The Fourteenth Amendment Good?”, https://mises.org/library/fourteenthamendment-good)//trepka Few issues divide libertarians the way the Fourteenth Amendment to the United States Constitution does. Gene Healy has observed that "[c]lassical liberals of good faith have found themselves on either side of the issue." On the one side are those who praise the amendment for circumventing the power of the states to prejudice, police, regulate, or otherwise use force to impose discriminatory laws on their citizens. On the other side are those who, while acknowledging the problematic nature of state misconduct and wrongdoing, are not willing to condone and in the transfer of power from states to the federal government , particular to the federal judiciary. The divide comes down to one's views on federalism , i.e., on the balance or separation of the state and national governments. The first and fifth sections of the Fourteenth Amendment are the most controversial . Section One consists of the Citizenship Clause, the Privileges or Due Process Clause , and the Equal Protection Clause, and Section Five bestows on the US Congress the authority to enforce the amendment legislatively . These provisions have vested increased powers in the national government, allowing federal courts to bring states into compliance with federal laws regarding certain individual rights — or alleged rights . Immunities Clause, the Extinction Calabresi 95 (Steven G. Calabresi, Associate Professor, Northwestern University School of Law, “A Government of Limited and Enumerated Powers,” Michigan Law Review December, 1995) First, the rules of constitutional federalism should be enforced because federalism is a good thing , and it is the best and most important structural feature of the U.S. Constitution. Second, the political branches cannot be relied upon to enforce constitutional federalism, notwithstanding the contrary writings of Professor Jesse Choper. Third, the Supreme Court is institutionally competent to enforce constitutional federalism. Fourth, the Court is at least as qualified to act in this area as it is in the Fourteenth Amendment area. And, fifth, the doctrine of stare [*831] decisis does not pose a barrier to the creation of any new, prospectively applicable Commerce Clause case law. The conventional wisdom is that Lopez is nothing more than a flash in the pan. 232 Elite opinion holds that the future of American constitutional law will involve the continuing elaboration of the Court's national codes on matters like abortion regulation, pornography, rules on holiday displays, and rules on how the states should conduct their own criminal investigations and trials. Public choice theory suggests many reasons why it is likely that the Court will continue to pick on the states and give Congress a free ride. But, it would be a very good thing for this country if the Court decided to surprise us and continued on its way down the Lopez path. Those of us who comment on the Court's work, whether in the law reviews or in the newspapers, should encourage the Court to follow the path on which it has now embarked. The country and the world would be a better place if it did. We have seen that a desire for both international and devolutionary federalism has swept across the world in recent years. To a significant extent, this is due to global fascination with and emulation of our own American federalism success story. The global trend toward federalism is an enormously positive development that greatly increases the likelihood of future peace, free trade, economic growth, respect for social and cultural diversity, and protection of individual human rights. It depends for its success on the willingness of sovereign nations to strike federalism deals in the belief that those deals will be kept . 233 The U.S. Supreme Court can do its part to encourage the future striking of such deals by enforcing vigorously our own American federalism deal. Lopez could be a first step in that process, if only the Justices and the legal academy would wake up to the importance of what is at stake. Page 56 Uniqueness The tipping point for federalism is coming Ryan 13 [Erin Ryan, Associate Professor, Lewis & Clark Law School, Portland, Oregon, U.S.A; Fulbright Professor of Law, Zhongguo Haiyang Daxue (Ocean University), Qingdao, CHINA [. "The Once and Future Challenges of American Federalism: The Tug of War Within" The Ways of Federalism in Western Countries and the Horizons of Territorial Autonomy In Spain. Ed. Alberto López Basaguren & Leire San-Epifanio. Springer] The dilemmas of American federalism have become especially palpable in recent years, reflecting the progressing demands on all levels of government to meet the inexorably more complicated challenges of governance in an increasingly interconnected world.2 Some reflect similar dilemmas in other federalist societies, while others are unique to our own particular constellation of national, state, and municipal governance.3 Some federalism dilemmas are of genuine constitutional import, others more sound and fury—signifying little beyond the substantive political agenda of one interest group or another.4 Each heralds the potential for real consequences in the political arena—and indeed, these political consequences of federalism dilemmas are apparent throughout the policy spectrum. They are visible in the litigation over health care reform efforts that has now reached the United States Supreme Court5 and in similar battles over environmental governance and climate policy,6 banking and financial services regulation,7 immigration policy,8 and gay marriage.9 Consequences are also visible in the emergence of popular constitutional political consequences are what receive the most sustained public attention. The movements, such as the “Tea Party” 10 and even the “Tenthers.”11 The latter are named for the Tenth Amendment to the U.S. Constitution that affirms our system of dual sovereignty, which divides sovereign authority between local and national government at the state and federal levels.12 After decades of playing a merely supporting role in U.S. federalism theory,13 the Tenth Amendment has emerged as a passionate site of political contest, rallying advocates for state right-to-die legislation,14 home schooling,15 and sectarian education,16 and among opponents of Medicaid and Medicare,17 federal gun laws,18 tax collection,19 drivers’ license requirements,20 and the deployment of National Guard troops abroad.21 Page 57 --AT: Gay Marriage The ruling was inevitable, constitutional, and doesn’t affect federalism Sasson 6/26/15 --- Reporter for WSJ (Eric, “The LGBT Movement's Supreme Court Hero: Anthony Kennedy”, http://www.newrepublic.com/article/122182/lgbt-movements-supreme-court-hero-anthony-kennedy)//trepka There was little mystery about who would be writing today's SCOTUS decision on marriage: As he's done for almost all decisions involving LGBT rights during his tenure, Justice Anthony Kennedy once again took up his pen to write the majority opinion in a 5-4 ruling that went as far as the court possibly could in defending the rights of same-sex couples. “No union is more profound than marriage, for it embodies the highest ideals of love, fidelity, devotion, sacrifice, and family,” Kennedy writes in the closing paragraph of the court's opinion. “As some of the petitioners in these cases demonstrate, marriage embodies a love that may endure even past death. It would misunderstand these men and women to say they disrespect the idea of marriage. Their plea is that they do respect it, respect it so deeply that they seek to find its fulfillment for themselves. Their hope is not to be condemned to live in loneliness, excluded from one of civilization’s oldest institutions. They ask for equal dignity in the eyes of the law. The Constitution grants them that right.” Make no mistake, this is Kennedy's decision. While he chose, in 2013's United States v. Windsor, to argue against DOMA on federalism grounds , it was his language regarding the dignity of same-sex couples and the potential harm inflicted on the children of these couples that led judges across the country to strike down gay-marriage bans, arguing that the Windsor ruling effectively made these bans unconstitutional. The domino effect continued until only 14 states remained without equal marriage rights. Public opinion shifted swiftly from a minority position to 60 percent or more now in favor in most polls. The court rarely wants to get ahead of public opinion. Still, it's hard not to interpret Kennedy's language in the earlier Windsor ruling as deliberate, designed to influence lower courts toward rulings which would create the environment where SCOTUS could comfortably rule in favor of marriage without seeming to be ahead of the curve. Following Thursday's rulings on Obamacare and housing discrimination, this decision seems to confirm a leftward tilt in the Roberts Court that is leaving conservatives fuming and full of conspiracy theories. But if those decisions came as somewhat of a surprise, this one seems to have been foreshadowed since October, when the Court refused to hear appeals arguments by five states where same-sex marriage was allowed. It was unlikely that the court would effectively allow marriage in those states (and by default several others), only to later strike down marriage on the federal level. The Court consolidated four separate cases to consider its ruling, but most of the attention has focused on the title case, Obergefell v. Hodges, in which Jim Obergefell wanted the death certificate of his husband, John Arthur, to reflect that Obergefell was the surviving spouse, something which was still not legally required under Ohio law. Partners for more than twenty years, Obergefell and Arthur had flown to Maryland to get married once they found out that Arthur, long suffering from ALS, had only a few months left to live. Family members and friends donated the $13,000 to pay for the medical flight to have the ceremony performed in a state where marriage is legal. These kinds of burdensome trips will soon no longer be necessary—which doesn't mean conservatives have necessarily given up on the issue completely. On Thursday, Texas AG Ken Paxton told county clerks in his state to wait for “direction and clarity” from his office before issuing any same-sex marriage licenses. We have seen this before, notably in Alabama a few months ago, and will likely see it in Louisiana soon as well, as Governor Bobby Jindal, a presidential candidate, tries to bolster his conservative cred among Evangelicals. Still, reaction among mainstream Republicans has been mostly muted so far. Most presidential hopefuls and governors have issued standard-issue remarks about how they support "traditional marriage." Scott Walker and Mike Huckabee will try, and fail, to goad the others into calls for a constitutional amendment and promises to protect religious liberty, i.e., the right of “dissenting” people of faith to deny services to same-sex couples. But all in all, I'm sure the Republicans will be glad that SCOTUS has taken them off the hook on this issue, much as the court has done in its health care ruling. Outside of select Republican primaries , rallying against same-sex marriage doesn't win you votes any more. But the seeming inevitability of this ruling doesn't make it any less historic. Next weekend in Philadelphia, the LGBT rights movement will celebrate the 50th anniversary of the “Annual Reminder” marches for equality that began in that city in 1965, at the time the largest demonstrations for gay and lesbian equality in the world, preceding the Stonewall Riots by four years. Fifty years doesn't seem like a long time, cosmically speaking, but it's an important reminder, whenever people speak about the “lightning speed” at which gays and lesbians have been securing rights in the U.S., that the movement didn't begin a few years ago. That the 1980s and '90s brought an AIDS epidemic that ravaged the community and was largely ignored by the federal government. That in 2004, dozens of states passed same-sex marriage bans. Since then, the LGBT Page 58 community gathered and regrouped, after tragedy and setback, and continued to push for its rights and dignity. The eloquence of Kennedy's final paragraph shows that these struggles were not in vain. Their ev is just media hype CSM 7/8/15 --- Christian Science Monitor (“Same-sex marriage and federalism: Miles's Law wins, again”, http://www.csmonitor.com/USA/Politics/Politics-Voices/2015/0708/Same-sex-marriage-and-federalism-Miles-s-Law-winsagain)//trepka been much in the news lately. Critics of the Supreme Court’s decision on same-sex marriage say that the justices should have left the matter to the states. A decade ago, however, many of them favored an amendment to the United States Constitution that would have taken the matter away from the states and defined marriage only as the union of a man and a woman. Another example is federalism, which has Page 59 Link It’s the core of federalism Kinsella 9 --- Practicing Patent Attorney, Director of C4SIF (Stephan, “The Libertarian Case Against the Fourteenth Amendment”, http://www.stephankinsella.com/2009/11/the-libertarian-case-against-the-fourteenth-amendment/)//trepka The “libertarian” case against it … well that’s a different issue than the legal case. The best legal case is in my view in Raoul Berger’s works, and in the Slaughterhouse decision itself [for Berger, see his work scanned in here; see also here]. My view on the legalities is that if nothing else, the 14th amendment is not clear about what privileges or immunities means. And, given that the broader you construe P-I the more power you grant to the central state, basically eating away at the core federalist structure of the Constitution itself [a great writer on this is law prof Tom McAffee; some of his stuff is here; see also my post The Unique American Federal Government], eroding the “ vertical separation of power ” and the “limited and enumerated scheme” of powers delegated to the feds, then you have to give the P-I clause a narrow reading and you have to construe any ambiguity against a grant of power to the feds. This is because if you find a right in there, that is a grant of power to the federal government to have jurisdiction over the states on this matter. Small decisions are the greatest threat to federalism Lebow ‘97 (Cynthia, associate Director @ Rand, Univ Tennessee Law Review, 1997, spring, pg lexis) See Southland, 465 U.S. at 21 (O'Connor, J., dissenting) (noting Rehnquist, C.J., joining opinion of O'Connor, J.); FERC, 456 U.S. at 775 (O'Connor, J., concurring in part and dissenting in part) (noting Rehnquist, C.J., joining in opinion of O'Connor, J.). Justice Powell filed his own partial dissent in FERC that also deserves mention. FERC, 456 U.S. at 771 (Powell, J., concurring in part and dissenting in part). Lauding the "appeal" and "wisdom" of Justice O'Connor's dissent, Powell stated that PURPA "intrusively requires [states] to make a place on their administrative agenda for consideration and potential adoption of federally proposed standards.'" Id. at 771, 775 (Powell, J., concurring in part and dissenting in part). While finding that precedents of the Court supported the constitutionality of the substantive provisions of PURPA "on this facial attack," Powell also evoked principles of federalism to warn against the encroachment of federal authority into state affairs: But I know of no other attempt by the Federal Government to supplant state-prescribed procedures that in part define the nature of their administrative agencies. If Congress may do this, presumably it has the power to pre-empt statecourt rules of civil procedure and judicial review in classes of cases found to affect commerce. This would be the type of gradual encroachment hypothesized by Professor Tribe: "Of course, no one expects Congress to obliterate the states, at least in one fell swoop. If there is any danger, it lies in the tyranny of small decisions in the prospect that Congress will nibble away at state sovereignty, bit by bit, until someday essentially nothing is left but a gutted shell ." Id. at 774-75 (Powell, J., concurring in part and dissenting in part) (quoting Laurence H. Tribe, American Constitutional Law 302 (1978)). Despite his warning, Justice Powell could probably never have envisioned the degree to which Congress would attempt to preempt state court procedures with respect to tort and product liability actions, areas so traditionally anchored in state common law. Page 60 Turns Discrimination Absent the judiciary, decentralized solutions solve Mendenhall 15 --- staff attorney to Chief Justice Roy S. Moore of the Supreme Court of Alabama, adjunct professor at Faulkner University (Allen, “Is The Fourteenth Amendment Good?”, https://mises.org/library/fourteenthamendment-good)//trepka If the federal government were the only or the best mechanism for reducing the type of discrimination and rights violations prohibited by the Fourteenth Amendment, the Fourteenth Amendment would be welcome and warranted. But it is not the only conceivable corrective, and besides, isn't it counterintuitive for libertarians to applaud and champion an increase in both the scope and degree of federal power, even if that power has, on some occasions, brought about admirable results? In contexts unrelated to the Fourteenth Amendment, it is almost never controversial for libertarians to promote nongovernmental, local, or decentralized cures for unfair, discriminatory laws and practices. It is often alleged that industry and trade and plain economics are better mechanisms for reducing discriminatory behavior, whether it is based on race, class, sex, gender, and so forth, than is government force. Yet frequently those libertarians who raise alarm about the Fourteenth Amendment's governmental, federal, and centralized approaches to discriminatory laws and practices are disingenuously treated, in the place of argument, as supporters of those laws and practices rather than as principled opponents of federal, centralized reparations for social harms. Page 61 Turns Privacy Spills over to overall federalism Mendenhall 15 --- staff attorney to Chief Justice Roy S. Moore of the Supreme Court of Alabama, adjunct professor at Faulkner University (Allen, “Is The Fourteenth Amendment Good?”, https://mises.org/library/fourteenthamendment-good)//trepka Having established the limited reach of the privileges or immunities clause in the Slaughterhouse Cases, the Supreme Court would later turn to the Equal Protection Clause and the Due Process Clause to strike down state laws under the Fourteenth Amendment. But the Supreme Court has not stopped at state laws: gradually it has used the Equal Protection Clause and the Due Process Clause as a pretext for regulating private citizens and businesses. The Fourteenth Amendment, which was intended to reduce discrimination, has even been used, ironically, to uphold affirmative-action programs that discriminate against certain classes of people. Turns privacy Mendenhall 15 --- staff attorney to Chief Justice Roy S. Moore of the Supreme Court of Alabama, adjunct professor at Faulkner University (Allen, “Is The Fourteenth Amendment Good?”, https://mises.org/library/fourteenthamendment-good)//trepka The Fourteenth Amendment is not itself a positive good but a dangerous animal to be handled with care. Libertarians as a class have manifest undue devotion to its operation. We need instead an open, honest, and collegial debate about the merits and function of this amendment, lest other creatures of its likeness rear their head in the future, and at the expense of our cherished liberties. Page 62 Impact --- Democracy Commitment to federalism is critical to global democratic success Broder 01 (David Broder, Washington Post, June 24, 2001, “Lessons On Freedom”) Even more persistent were the questions about the role the United States would play, under this new administration, in supporting democratic movements around the world. It is sobering to be reminded how often, during the long decades of the Cold War, this country backed (and in some cases, created) undemocratic regimes, simply because we thought military rulers and other autocrats were more reliable allies against communism. The week of the Salzburg Seminar coincided with President Bush's first tour of Europe. He was a target of jokes and ridicule for many of the fellows as the week began. But the coverage of his meetings and, especially, his major address in Poland on his vision of Europe's future and America's role in it, earned him grudging respect, even though it remains uncertain how high a priority human rights and promotion of democracy will have in the Bush foreign policy. Another great lesson for an American reporter is that the struggle to maintain the legitimacy of representative government in the eyes of the public is a worldwide battle. Election turnouts are dropping in almost all the established democracies, so much so that seminar participants seriously discussed the advisability of compulsory voting, before most of them rejected it as smacking too much of authoritarian regimes. Political parties -- which most of us have regarded as essential agents of democracy -- are in decline everywhere. They are viewed by more and more of the national publics as being tied to special interests or locked in increasingly irrelevant or petty rivalries -- anything but effective instruments for tackling current challenges. One large but unresolved question throughout the week: Can you organize and sustain representative government without strong parties? The single most impressive visitor to the seminar was Vaira Vike-Freiberga, the president of Latvia, a woman of Thatcherite determination when it comes to pressing for her country's admission to NATO, but a democrat who has gone through exile four times in her quest for freedom. She is a member of no party, chosen unanimously by a parliament of eight parties, and bolstered by her popular support. But how many such leaders are there? Meantime, even as democracy is tested everywhere from Venezuela to Romania to the Philippines, a new and perhaps tougher accountability examination awaits in the supranational organizations. The European Union has operated so far with a strong council, where each nation has a veto, and a weak parliament, with majority rule. But with its membership seemingly certain to expand, the age-old dilemma of democracy – majority rule vs. minority and individual rights – is bound to come to the fore. The principle of federalism will be vital to its success. And, once again, the United States has important lessons to teach. But only if we can keep democracy strong and vital in our own country. Extinction Diamond 95 — Senior Fellow at the Hoover Institution (Larry, “Promoting Democracy in the 1990s”, December 1995, http://wwics.si.edu/subsites/ccpdc/pubs/di/1.htm) OTHER THREATS This hardly exhausts the lists of threats to our security and well-being in the coming years and decades. In the former Yugoslavia nationalist aggression tears at the stability of Europe and could easily spread. The flow of illegal drugs intensifies through increasingly powerful international crime syndicates that have made common cause with authoritarian regimes and have utterly corrupted the institutions of tenuous, democratic ones. Nuclear, chemical, and biological weapons continue to proliferate. The of life on Earth, the global ecosystem, appears increasingly endangered. Most of these new and unconventional threats to security are associated with or aggravated by the weakness or absence of democracy, with its provisions for legality, accountability , popular sovereignty, and openness . LESSONS OF THE TWENTIETH CENTURY The experience of this century offers important lessons. Countries that govern themselves in a truly democratic fashion do not go to war with one another. They do not aggress against their neighbors to aggrandize very source themselves or glorify their leaders. Democratic governments do not ethnically "cleanse" their own populations, and they are much less likely to face ethnic insurgency. Democracies do not sponsor terrorism against one another. They do not build w eapons of m ass d estruction to use on or to threaten one another. Democratic countries form more reliable, open, and enduring trading partnerships. In the long run they offer better and more stable climates for investment. They are more environmentally responsible because they must answer to their own citizens, who organize to protest the destruction of their environments. They are better bets to honor international treaties since they value legal obligations and because their openness makes it much more difficult to breach agreements in secret. Precisely because, within their own borders, they respect competition, civil liberties, property rights, and the rule of law, democracies are the only reliable foundation on which a new world order of international security and prosperity can be built. Page 63 Impact --- Econ Federalism is critical to economies of scale – it’s key to production success and cost division Calebresi 95 (Stephen Calebresi, Associate Professor, Northwestern University School of Law. B.A. 1980, J.D. 1983, Yale, “Reflections on United States v. Lopez: “A Government of Limited and Enumerated Powers: In Defense of United States v. Lopez,” 94 Mich. L. Rev. 752, Michigan Law Review, December 1995) A third related advantage is that international federations can undertake a host of governmental activities in which there are significant economies of scale. This is one reason why federations can provide better for the common defense than can their constituent parts. Intercontinental ballistic missiles, nuclear-powered aircraft [*772] carriers and submarines, and B-2 stealth bombers tend to be expensive. Economies of scale make it cheaper for fifty states to produce one set of these items than it would be for fifty states to try to produce fifty sets. This is true even without factoring in the North American regional tensions that would be created if this continent had to endure the presence of fifty nuclear minipowers, assuming that each small state could afford to own at least one Hiroshima-sized nuclear bomb. Important governmental economies of scale obtain in other areas, as well, however, going well beyond national defense. For example, there are important economies of scale to the governmental provision of space programs, scientific and biomedical research programs, the creation of transportation infrastructure, and even the running of some kinds of income and wealth redistribution programs. Page 64 Impact --- India Ethnic tensions – federalism prevents them from spilling over Pye 08 (Political Science, MIT, “The State of India’s Democracy,” June, 2008, http://www.foreignaffairs.org/20080501fashortreview87356/sumit-ganguly-larry-diamond-marc-fplattner/the-state-of-india-s-democracy.html) This symposium volume brings together more than a dozen American and Indian scholars to evaluate the state of India's democracy. It is standard practice to honor India by declaring it, without further analysis, to be the world's largest democracy. The authors of this volume, in contrast, take it as a given that there are many different versions of democracy and that India is a special case. They begin by analyzing India's party system and election results and how the relationship of politics to society leads to the management of ethnic conflicts. A key factor in the strength of Indian democracy is the country's successful federalism, the balance achieved between the central government and state and local authorities. Another key factor in India's democracy is its judiciary. Overall, however, the success of Indian democracy is very much determined by the country's civil society and the pride Indians take in their democratic institutions. At the same time, Indians are bothered by corruption in public affairs. The emergence of marginalized elements has further opened the door to graft. Extinction Fai in ’01 (Ghulam Nabi, Executive Director of the Kashmiri American Council, The Washington Times, “The Most Dangerous Place”, July 8, Proquest) The most dangerous place on the planet is Kashmir, a disputed territory convulsed and illegally occupied for more than 53 years and sandwiched between nuclear-capable India and Pakistan. It has ignited two wars between the estranged South Asian rivals in 1948 and 1965, and a third could trigger nuclear volleys and a nuclear winter threatening the entire globe. The United States would enjoy no sanctuary. This apocalyptic vision is no idiosyncratic view. The Director of Central Intelligence, the Department of Defense, and world experts generally place Kashmir at the peak of their nuclear worries. Both India and Pakistan are racing like thoroughbreds to bolster their nuclear arsenals and advanced delivery vehicles. Their defense budgets are climbing despite widespread misery amongst their populations. Neither country has initialed the Nuclear Non-Proliferation Treaty, the Comprehensive Test Ban Treaty, or indicated an inclination to ratify an impending Fissile Material/Cut-off Convention. Page 65 Impact --- Iraq Iraq models American federalism Hulsman 03 (John Hulsman, Ph.D., Research Fellow in European Affairs, The Heritage Foundation, “Forging a Durable Post-War Political Settlement in Iraq,” http://www.heritage.org/Research/MiddleEast/bg1632.cfm) A good political model for such a successful post-war Iraqi federation already exists--the so-called Great Compromise of 1787 that enabled the creation of America's constitutional arrangement among the states. In Iraq's case, this type of system would give each of the country's three major sub-groups equal representation in an upper house of the legislature in order to protect each group's interests at the national level. These political outcomes--an Iraq that can control its own political destiny and that does not threaten that of its neighbors--are critical if an Iraqi settlement is to be judged a success. That solves ethnic conflict and secessionism – leads to internal conflict Brancati 04 – visiting scholar at the Center for the Study of Democratic Politics at Princeton University, 2004 (Can Federalism Stabilize Iraq?, http://www.twq.com/04spring/docs/04spring_brancati.pdf) The United States devoted nine months to planning the war in Iraq and a mere 28 days to planning the peace, according to senior U.S. military officials. Much more time has to be invested in the peace, however, if the military achievements of the war are to be preserved and a stable democracy is to be created in Iraq. Establishing a governmental system that can accommodate Iraq’s different ethnic and religious groups, previously kept in check by the political and military repression of the Saddam Hussein regime, is paramount to securing that peace. In the absence of a system uniquely designed toward this end, violent conflicts and demands for independence are likely to engulf the country. If not planned precisely to meet the specific ethnic and religious divisions at play, any democratic government to emerge in Iraq is bound to prove less capable of maintaining order than the brutal dictatorship that preceded it. By dividing power between two levels of government—giving groups greater control over their own political, social, and economic affairs while making them feel less exploited as well as more secure—federalism offers the only viable possibility for preventing ethnic conflict and secessionism as well as establishing a stable democracy in Iraq. Yet, not just any kind of federal system can accomplish this. Rather, a federal system granting regional governments extensive political and financial powers with borders drawn along ethnic and religious lines that utilize institutionalized measures to prevent identity-based and regional parties from dominating the government is required. Equally critical to ensuring stability and sustainable democracy in Iraq, the new federal system of government must secure the city of Kirkuk, coveted for its vast oil reserves and pipelines, in the Kurdish-controlled northern region to assure that the Kurds do not secede from Iraq altogether. For its part, the United States must take a more active role in advising Iraqi leaders to adopt a federal system of government along these lines. Such a system will help the United States not only to build democracy in Iraq but also to prevent the emergence of a Shi‘a-dominated government in the country. Without this form of federalism, an Iraq rife with internal conflict and dominated by one ethnic or religious group is more likely to emerge, undermining U.S. efforts toward establishing democracy in Iraq as well as the greater Middle East. Global nuclear war Corsi 07 (Jerome, Ph.D. in Political Science – Harvard University, “War with Iran is Imminent”, World Net Daily, 1-8, http://www.worldnetdaily.com/news/article.asp?ARTICLE_ID=53669) If a broader war breaks out in Iraq, Olmert will certainly face pressure to send the Israel military into the Gaza after Hamas and into Lebanon after Hezbollah. If that happens, it will only be a matter of time before Israel and the U.S. have no choice but to invade Syria . The Iraq war could quickly spin into a regional war, with Israel waiting on the sidelines ready to launch an air and missile strike on Iran that could include tactical nuclear weapons . With Russia ready to deliver the $1 billion TOR M-1 surface-to-air missile defense system to Iran, military leaders are unwilling to wait too long to attack Iran. Now that Russia and China have invited Iran to join their Shanghai Cooperation Pact, will Russia and China sit by idly should the U.S. look like we are winning a wider regional war in the Middle East? If we get more deeply involved in Iraq, China may have their war could easily lead into a third world war , moment to go after Taiwan once and for all. A broader regional much as World Wars I and II began. Page 66 Impact --- Multilat Federalism is critical to international unity and alliance Calabresi 95 (Steven G. Calabresi, Associate Professor, Northwestern University School of Law, “A Government of Limited and Enumerated Powers,” Michigan Law Review December, 1995) These old geostrategic arguments for federalist consolidation obviously hold true today and played a role in the forming of the European Union, the United Nations, and almost every other multinational federation or alliance that has been created since 1945. Sometimes the geostrategic argument is expanded to become an argument for a multinational defensive alliance, like NATO, against a destabilizing power, like the former Soviet Union. In this variation, international federalism is partly a means of providing for the common defense and partly a means of reducing the likelihood of intra-alliance warfare in order to produce a united front against the prime military threat. Providing for the common defense, though, is itself a second and independent reason for forming international federations. It was a motivation for the formation of the U.S. federation in 1787 and, more recently, the European Union. Page 67 Impact --- Russia Federalism is critical to prevent state disintegration and political instability – causes Russian loose nukes Hahn 03 (Gordon M. Hahn, Visiting Research Scholar – Stanford U, Demokratizatsiya, Vol. 11, Issue 3, Summer) Where did Russia's federal state come from, where has it been, where is it going, and why does it matter beyond a small circle of Russia specialists? Taking the last question first, the success or failure of Russia's transformation into a stable market democracy will determine the degree of stability throughout Eurasia. For such a large multinational state, successful political and economic development depends on building an efficient democratic federal system. Indeed, one of the main institutional factors leading to the demise of the Soviet partocratic regime and state was the considerably noninstitutionalized status of the RSFSR (Russian Republic) in the Soviet Union's pseudofederal, national-territorial administrative structure. Only a system can hold together and effectively manage Russia's vast territory, the awkward administrative structure inherited from the failed USSR, and hundreds of divergent ethnic, linguistic, and religious interests. Dissolution or even any further weakening of Russia's federal democratic federal state could have dire consequences for Russian national and international security by weakening control over its means of mass destruction. Russia Federalism is key to prevent Genocide Dugin 06 (Alexander Dugin, political scientist, “Russia’s Future: A Unitary State or an Ethno-Federation?” Translated by Denis Shcherbakov Rossiia, No. 4, February 2006) Experts and political scientists were prompted to consider such questions by reforms to the hierarchy of governance in the course of 2005 - especially the abolition of elections for regional leaders. For example, Alexander Voloshin, former head of the presidential administration, spoke about a possible scenario for transforming federative Russia into unitary Russia, noting that the ethnic republics, as self-sufficient regions of the Federation, are hotbeds of tension. Therefore, the process of expanding regions might end in erasing the borders of the ethnic republics. Meanwhile, Boris Nemtsov agreed with other Russian liberals in naming "the curtailment of federative principles and local government, leading to a unitary state," among the negative trends of the past year. I'd agree with the liberal opposition here, but from a completely different standpoint - a Eurasian standpoint. Russia as a unitary state would be the worst of all possible options, precisely because it would happen at the expense of genocide for the native ethnic groups comprising it. This genocide doesn't just threaten ethnic minorities that are assimilated into the majority people; it also threatens the majority people, which loses its unique ethnic qualities, its native characteristics, originality, traditions; its members become mere citizens of the nation-state. Consequently, Russia ought to take the federalist path, but with one substantial proviso: federalism should change from the territorial federalism of today to ethno-federalism - that is, a federation of ethnic groups, or Eurasian federalism. Page 68 Impact --- Trade Federalism is critical to free trade Calabresi 95 (Steven G. Calabresi, Associate Professor, Northwestern University School of Law. “A Government of Limited and Enumerated Powers,” Michigan Law Review December, 1995) A fourth and vital advantage to international federations is that they can promote the free movement of goods and labor both among the components of the federation by reducing internal transaction costs and internationally by providing a unified front that reduces the costs of collective action when bargaining with other federations and nations. This reduces the barriers to an enormous range of utility-maximizing transactions thereby producing an enormous increase in social wealth. Many federations have been formed in part for this reason, including the United States, the European Union, and the British Commonwealth, as well as all the trade-specific "federations" like the GATT and NAFTA. Page 69 Impact --- Tyranny Majority tyranny – federalism provides a check on majoritarianism Calabresi 95 (Steven G. Calabresi, Associate Professor, Northwestern University School of Law. “A Government of Limited and Enumerated Powers,” Michigan Law Review December, 1995) Small state federalism is a big part of what keeps the peace in countries like the United States and Switzerland. It is a big part of the reason why we do not have a Bosnia or a Northern Ireland or a Basque country or a Chechnya or a Corsica or a Quebec problem. 51 American federalism in the end is not a trivial matter or a quaint historical anachronism. Americanstyle federalism is a thriving and vital institutional arrangement - partly planned by the Framers, partly the accident of history - and it prevents violence and war. It prevents religious warfare, it prevents secessionist warfare, and it prevents racial warfare. It is part of the reason why democratic majoritarianism in the United States has not produced violence or secession for 130 years, unlike the situation for example, in England, France, Germany, Russia, Czechoslovakia, Yugoslavia, Cyprus, or Spain. There is nothing in the U.S. Constitution that is more important or that has done more to promote peace, prosperity, and freedom than the federal structure of that great document. There is nothing in the U.S. Constitution that should absorb more completely the attention of the U.S. Supreme Court. Page 70 Impact --- Water Federalism is critical to effective water management – nationalization fails Craig 11 (Robin Kundis Craig, Associate Dean for Environmental Programs, Professor of Law, Florida State University College of Law, “Adapating Water Federalism to Climate Change Impacts: Energy Policy, Food Security, and the Allocation of Water Resources,” Environmental and Energy Law and Policy Journal, Vol. 5, No. 2, January 30, 2011, http://www.law.uh.edu/eelpj/publications/5-2/02Craig.pdf) That said, however, the prospect of whole scale nationalization and federalization of water resources should give pause. Water serves local ecological and economic needs that could easily be sacrificed to national interests, particularly if Congress pursues a few specific national priorities—national energy security, national food security—with tunnel vision. 304 Moreover, at the extreme, large-scale water transportation on a national scale will be incredibly expensive, creating a cost-benefit issue that suggests that more efficient means of addressing national water priorities, such as national investment in upgraded water infrastructure and water conservation, probably exist and should be looked for. The overriding danger that climate change poses for water law and policy is that governments at all levels will avoid making the hard decisions that climate change demands until they are regulating in a panicked and reactive emergency mode, eliminating the opportunity to make those decisions in a proactive and reasoned disaster-avoidance planning mode. The former, panicked, mode is far more likely to result in last-minute nationalization and federalization of water to ensure the viability of a few priorities. The latter emergency planning mode, in contrast, would allow for longer-term identification and balancing of multiple priorities at multiple scales. Thus, where exactly the balance of authority in water management and allocation actually ends up in the climate change era will, I suspect, depend far more on how soon all levels of government choose to start planning for climate change‘s impacts on water resources than any theoretical notions roles —and we are all more likely to end up with a more optimal balance of water federalism if they all start sooner rather than later. of ― proper governmental That decimates the US agriculture sector WEF 11 (Water Environment Federation, “Water Sector Interdependencies: Summary Report 2011,” 2011, http://www.wef.org/uploadedFiles/Access_Water_Knowledge/Water_Security_and_Emergency_Response /Final_WEF_Summary_WSI.pdf) The water sector and the the sector is agriculture and food sector are heavily interdependent. According to the agriculture and food SSP, dependent upon the water sector, “for clean irrigation and processed water.” This is certainly true, although understated. In fact, according to the U.S. Geological Survey (USGS), almost 60% of all the world’s freshwater withdrawals go toward irrigation uses. Agriculture is a major user of ground and surface water in the United States and, according to the USDA, accounts for 80% of the nation’s consumptive water use and over 90% in many western states. However, the agriculture and food sector’s dependencies on water go well beyond irrigation. Throughout the production, process, and distribution of the nation’s food supply, water use and recovery is essential. The agriculture and food sector refers to this cycle as the “farm-to-table continuum” and includes the supply chains for feed, animals, and animal products; crop production; and the supply chains of seed, fertilizer, and other necessary related materials. It also includes the post-harvesting components of the food supply chain, from processing, production, and packaging through storage and distribution to retail sales, institutional food services, and restaurant or home consumption. In addition to irrigation, a major user of water is livestock watering. USGS defines livestock water use as water associated with “livestock watering, feedlots, dairy operations, and other on-farm needs. This includes water for raising cows, chickens, horses, rabbits, fish, and pets, and also water used in the production of meats, poultry, eggs, and milk.” Extinction Klare, 12 — professor of peace and world security studies at Hampshire College (Michael T., “Michael T. Klare: The Hunger Wars in Our Future”, 8/8/12, http://www.guernicamag.com/daily/michael-t-klare-thehunger-wars-in-our-future/) This, however, is just the beginning of the likely consequences: if history is any guide, rising food prices of this sort will also lead to widespread social unrest and violent conflict . Because so many nations depend on grain imports from the U.S. to supplement their own harvests, and because intense drought and floods are damaging crops elsewhere as well, food supplies Page 71 are expected to shrink and prices to rise across the planet. Food–affordable food–is essential to human survival and well-being. Take that away, and people become anxious, desperate, and angry. In the United States, food represents only about 13 percent of the average household budget, a relatively small share, so a boost in food prices in 2013 will probably not prove overly taxing for most middle- and upper-income families. It could, however, produce considerable hardship for poor and unemployed Americans with limited resources. “You are talking about a real bite out of family budgets,”commented Ernie Gross, an agricultural economist at Omaha’s Creighton University. This could add to the discontent already evident in depressed and highunemployment areas, perhaps prompting an intensified backlash against incumbent politicians and other forms of dissent and unrest. It is in the international arena, however, that the Great Drought is likely to have its most devastating effects. Because so many nations depend on grain imports from the U.S. to supplement their own harvests, and because intense drought and floods are damaging crops elsewhere as well, food supplies are expected to shrink and prices to rise across the planet. “What happens to the U.S. supply has immense impact around the world,” says Robert Thompson, a food expert at the Chicago Council on Global Affairs. As the crops most affected by the drought, corn and soybeans, disappear from world markets, he noted, the price of all grains, including wheat, is likely to soar, causing immense hardship to those who already have trouble affording enough food to feed their families. The Hunger Games, 2007-2011 What happens next is, of course, impossible to predict, but if the recent past is any guide, it could turn ugly. In 2007-2008, when rice, corn, and wheat experienced prices hikes of 100 percent or more, sharply higher prices–especially for bread–sparked “food riots” in more than two dozen countries, including Bangladesh, Cameroon, Egypt, Haiti, Indonesia, Senegal, and Yemen. In Haiti, the rioting became so violent and public confidence in the government’s ability to address the problem dropped so precipitously that the Haitian Senate voted to oust the country’s prime minister, Jacques-Édouard Alexis. In other countries, angry protestors clashed with army and police forces, leaving scores dead. Those price increases of 2007-2008 were largely attributed to the soaring cost of oil, which made food production more expensive. (Oil’s use is widespread in farming operations, irrigation, food delivery, and pesticide manufacture.) At the same time, increasing amounts of cropland worldwide were being diverted from food crops to the cultivation of plants used in making biofuels. The next price spike in 2010-11 was, however, closely associated with climate change. An intense drought gripped much of eastern Russia during the summer of 2010, reducing the wheat harvest in that breadbasket region by one-fifth and prompting Moscow to ban all wheat exports. Drought also hurt China’s grain harvest, while intense flooding destroyed much of Australia’s wheat crop. Together with other extreme-weather-related effects, these disasters sent wheat prices soaring by more than 50 percent and the price of most food staples by 32 percent. Once again, a surge in food prices resulted in widespread social unrest , this time concentrated in North Africa and the Middle East. The earliest protests arose over the cost of staples in Algeria and then Tunisia, where–no coincidence–the precipitating event was a young food vendor,Mohamed Bouazizi, setting himself on fire to protest government harassment. Anger over rising food and fuel prices combined with long-simmering resentments about government repression and corruption sparked what became known as the Arab Spring. The rising cost of basic staples, especially a loaf of bread, was also a cause of unrest in Egypt, Jordan, and Sudan. Other factors, notably anger at entrenched autocratic regimes, may have proved more powerful in those places, but as the author of Tropic of Chaos, Christian Parenti, wrote, “The initial trouble was traceable, at least in part, to the price of that loaf of bread.” Until recently, most scientists were reluctant to blame particular storms or droughts on global warming. Now, however, a growing number of scientists believe that such links can be demonstrated in certain cases. As for the current drought, analysts are already warning of instability in Africa , where corn is a major staple, and of increased popular unrest in China, where food prices are expected to rise at a time of growing hardship for that country’s vast pool of low-income, migratory workers and poor peasants. Higher food prices in the U.S. and China could also lead to reduced consumer spending on other goods, further contributing to the slowdown in the global economy and producing yet more worldwide misery, with unpredictable social consequences. The Hunger Games, 2012-?? If this was just one bad harvest, occurring in only one country, the world would undoubtedly absorb the ensuing hardship and expect to bounce back in the years to come. Unfortunately, it’s becoming evident that the Great Drought of 2012 is not a one-off event in a single heartland nation, but rather an inevitable consequence of global warming which is only going to intensify. As a result, we can expect not just more bad years of extreme heat, but worse years, hotter and more often, and not just in the United States, but globally for the indefinite future. Until recently, most scientists were reluctant to blame particular storms or droughts on global warming. Now, however, a growing number of scientists believe that such links can be demonstrated in certain cases. In one recent study focused on extreme weather events in 2011, for instance, climate specialists at the National Oceanic and Atmospheric Administration (NOAA) and Great Britain’s National Weather Service concluded that human-induced climate change has made intense heat waves of the kind experienced in Texas in 2011 more likely than ever before. Published in the Bulletin of the American Meteorological Society, it reported that global warming had ensured that the incidence of that Texas heat wave was 20 times more likely than it would have been in 1960; similarly, abnormally warm temperatures like those experienced in Britain last November were said to be 62 times as likely because of global warming. It is still too early to apply the methodology used by these scientists to calculating the effect of global warming on the heat waves of 2012, which are proving to be far more severe, but we can assume the level of correlation will be high. And what can we expect in the future, as the warming gains momentum? When we think about climate change (if we think about it at all), we envision rising temperatures, prolonged droughts, freakish storms, hellish wildfires, and rising sea levels. Among other things, this will result in damaged infrastructure and diminished food supplies. These are, of course, manifestations of warming in the physical world, not the social world we all inhabit and rely on for so many aspects of our daily well-being and survival. The purely physical effects of climate Page 72 change will, no doubt, prove catastrophic. But the social effects including, somewhere down the line, food riots, mass starvation, state collapse, mass migrations, and conflicts of every sort, up to and including full-scale war, could prove even more disruptive and deadly. In her immensely successful young-adult novel The Hunger Games (and the movie that followed), Suzanne Collins riveted millions with a portrait of a dystopian, resource-scarce, post-apocalyptic future where once-rebellious “districts” in an impoverished North America must supply two teenagers each year for a series of televised gladiatorial games that end in death for all but one of the youthful contestants. These “hunger games” are intended as recompense for the damage inflicted on the victorious capitol of Panem by the rebellious districts during an insurrection. Without specifically mentioning global warming, Collins makes it clear that climate change was significantly responsible for the hunger that shadows the North American continent in this future era. Hence, as the gladiatorial contestants are about to be selected, the mayor of District 12’s principal city describes “the disasters, the droughts, the storms, the fires, the encroaching seas that swallowed up so much of the land [and] the brutal war for what little sustenance remained.” The focus is understandably on the immediate consequences of the still ongoing Great Drought: dying crops, shrunken harvests, and rising food prices. But keep an eye out for the social and political effects … In this, Collins was prescient, even if her specific vision of the violence on which such a world might be organized is fantasy. While we may never see her version of those hunger games, do not doubt that some version of them will come into existence–that, in fact, hunger wars of many sorts will fill our future. These could include any combination or permutation of the deadly riots that led to the 2008 collapse of Haiti’s government, the pitched battles between massed protesters and security forces that engulfed parts of Cairo as the Arab Spring developed, the ethnic struggles over disputed croplands and water sources that have made Darfur a recurring headline of horror in our world, or the inequitable distribution of agricultural land that continues to fuel the insurgency of the Maoist-inspired Naxalites of India. Page 73 FISA DAs Page 74 Deference Now --- FISA Executive deference now on FISA Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka Those courts affirming the holding of the Truong court, that the primary purpose of warrantless surveillance must be foreign intelligence gathering and extending its application to FISA authorized surveillance, have not excluded information collected pursuant to a FISA order in criminal prosecutions where, at the time the information was collected, it could be reasonably anticipated that a criminal investigation would [*204] result. n88 In United States v. Duggan, the Second Circuit Court of Appeals held that the requirement that foreign intelligence surveillance "be the primary objective of the surveillance is plain not only from the language of § 1802(b) but also from the requirements in § 1804 as to what the application must contain." n89 The court concluded that the application process, in requiring certification of the presented facts by an executive branch official, ensures that the information sought will be for the purpose of gathering foreign intelligence information. n90 FISA requires that the FISA court "not ... second-guess the executive branch official's certification that the objective of the surveillance is foreign intelligence information," effectively requiring the FISA court to presume the executive branch has the purpose of foreign intelligence gathering in applying for a FISA application. n91 However, recognizing that such a presumption may lead to future abuse of FISA surveillance, the court clarified that such a presumption does not "give the government carte blanche to obtain a surveillance order in violation of a target's right to due process" and may be overcome by a substantial showing that ""a false statement knowingly and intentionally, or with reckless disregard for the truth was included' in the application and that the allegedly false statement was "necessary' to the FISA Judge's approval of the application." n92 In addition to giving deference to the executive in declaring that the primary purpose of the surveillance was for foreign intelligence gathering, the Duggan court held that a FISA order is not invalid simply [*205] because the executive could anticipate that the fruits of the surveillance would be later used in a criminal trial. n93 The court emphasized that in passing FISA, Congress anticipated that the concerns of the government with respect to foreign intelligence will overlap those with respect to law enforcement. n94 The court ultimately concluded that the mere presence of a domestic law enforcement purpose will not invalidate FISA surveillance where the primary purpose of the surveillance was to gather foreign intelligence information, as certified to by an executive branch official, where the defendant was engaged in international terrorist acts or the plotting of those acts. n95 While Duggan and numerous other circuit court decisions have agreed that the proper constitutional requirement for acquiring a FISA order is that the surveillance be conducted for the primary purpose of gathering foreign intelligence information, numerous courts have simply applied the plain language of FISA. n96 In assessing the validity of a FISA search, these courts have required a showing that the purpose of the surveillance, rather than the primary purpose, was to obtain foreign intelligence information and that such information could not have been acquired through normal investigative techniques. n97 Coincidentally, these courts held, in accordance with those courts applying the primary purpose test, that where evidence of criminal activity was discovered through a FISA order, such evidence is admissible in a criminal prosecution of the target of the surveillance. n98 However, the court in United States v. Belfield, while applying the statutory language of FISA, asserted that the inquiry required under FISA to determine the legality of the surveillance is easier to satisfy than [*206] the pre-FISA requirement. n99 The court noted that before FISA, "courts had to determine whether the surveillance fell within the President's inherent power to conduct electronic surveillance for foreign intelligence purposes." n100 After FISA, courts merely had "to determine whether the application and order comply with the statutory requirements." n101 Through this statement, the Belfield court recognized that FISA essentially codified a new standard for assessing the validity of warrantless foreign intelligence surveillance, whereby the court no longer must inquire into the nature of the surveillance by the executive, but, assuming that FISA is constitutional, must determine if the requirements of the statute have been followed. By making this assertion, the court left unresolved the question of whether the purpose standard used in FISA was the equivalent of the primary purpose standard iterated in Truong. Page 75 Deference Now --- CT Maintaining FISA overreach is key to prosecute terrorists --- it’s upheld by all lower courts now Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka After 9/11, the Department of Justice worked to expand the surveillance tools needed to gather intelligence on terrorist activity. Approximately five weeks after 9/11, Congress passed the U.S.A. Patriot Act, n68 which, inter alia, increased emergency surveillance before obtaining a FISA warrant from twenty-four hours to seventy-two hours, n69 expanded the number of FISA judges from seven to eleven, n70 expanded the availability of physical searches, pen registers, and trap and trace devices, n71 and allowed roving wiretaps. n72 It also extended the time periods for the surveillance from 90 days to 120 days. n73 While a thorough analysis of the Patriot Act is beyond it is useful to discuss (arguably) the most consequential change to FISA: the requirement that a "significant purpose" as opposed to "the purpose" of the surveillance be to conduct foreign intelligence. Before 9/11, to the scope of this Article, for purposes of the later discussion in Part IV (analyzing the FAA), obtain a FISA warrant, the government had to assert that the "purpose of the surveillance is to obtain foreign intelligence information." Over the years, based on several court decisions, the government interpreted "purpose" to be "primary purpose " to gain foreign intelligence information. n75 [*281] Furthermore, a 1995 Office of Legal Counsel (OLC) opinion concluded that "courts are more likely to adopt the 'primary purpose' test than any less stringent n74 formulation," and that "the greater the involvement of prosecutors in the planning and execution of FISA searches, the greater is the chance that the government could not assert in good faith that the 'primary purpose' was the collection of foreign intelligence." n76 If evidence of criminal wrongdoing was discovered pursuant to a properly executed FISA warrant (where the primary purpose was to collect intelligence), this evidence could still be used at trial. n77 Nonetheless, because of fears that zealous prosecutors would manipulate FISA warrants to bypass the need to obtain traditional law enforcement warrants under Title III (with the more rigorous probable cause standard), a "wall" was created that impeded prosecutors from discussing their cases with intelligence officers or controlling, initiating, or expanding FISA investigations. In fact, "in 1995, the Reno Justice Department issued guidelines that FISA information could almost never be shared with criminal investigators." n78 It is this artificial wall - one created by custom, bureaucracy, and practice but not by law - that the 9/11 commissioners criticized in the 9/11 Commission Report. n79 As law professor William Banks attests, the "FISA wall procedures were designed to protect against using the secretive foreign intelligence collection process in order to build a criminal case," but "never stood in the way of the sharing of criminal information with intelligence investigators," nor "the sharing of intelligence information with criminal investigators, so long as the sharing met the foreign intelligence purpose rule." n80 The Patriot Act changed the legal standard for a FISA warrant from one whose "primary purpose" was to gather foreign intelligence to one that only needed a "significant purpose ." Some individuals, like law professor Stephen Schulhofer at New York University, argue that adding the word "significant" [*282] produces a "large change in law enforcement power." n81 According to Schulhofer, the change to the phrase "significant purpose" from "purpose" means that U.S. citizens and foreign nationals may be exposed to "broad FISA surveillance" when the government's primary purpose is not to gather foreign intelligence but instead to gather evidence for use at a criminal trial. n82 Similarly, Banks argues in The Death of FISA that the change to "significant purpose" essentially "gutted the central premise of FISA" because it allows "the primary objective of the planned surveillance [to be] evidence to support a prosecution." n83 Banks observes that, since 9/11, there has been a "growing criminalization of terrorismrelated activities [that] has made the prosecutorial agenda a larger part of the sphere of electronic surveillance and has accordingly further complicated the task of managing FISA implementation." n84 Nonetheless, in 2002, the FISCR specifically upheld the change to "significant purpose" as lawful, despite the overlap between intelligence and criminalization of terrorist activities. As the FISCR explained: [The primary purpose] analysis, in our view, rested on a false premise and the line the court sought to draw was inherently unstable, unrealistic, and confusing. The false premise was the assertion that once the government moves to criminal prosecution, its 'foreign policy concerns' recede... . That is simply not true as it relates to counterintelligence. In that field the government's primary purpose is to halt the espionage or terrorism efforts, and criminal prosecutions can be, and usually are, interrelated with other techniques used to frustrate a foreign power's efforts. n85 In other words, criminal prosecution and the gathering of foreign intelligence are often intertwined , and one way to prevent threats to national security is to prosecute terrorists . Furthermore, the FISCR aptly noted that the definition of an agent of a foreign power for U.S. persons is rooted in criminal conduct (i.e. knowingly engaging in activity that may be a crime). n86 The FISCR concluded that Page 76 unless the government's "sole objective" was to obtain evidence of a past crime, a FISA warrant should be granted. n87 The FISCR stressed, however, that the "FISA process may not be used to investigate wholly unrelated ordinary crimes." n88 While the Supreme Court has yet to rule on the constitutionality of FISA or the specific change to all other courts to consider the issue, except one district court, have agreed with the FISCR's holding that the change to "significant purpose" is reasonable under the Fourth Amendment. n89 "significant purpose," Page 77 Deference Now --- Warrants Courts are moving away from warrant requirements now Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka While full argumentation for the proposition that the Fourth Amendment embodies such an exception is beyond the scope of this Note, n110 the case law is clear that the true " touchstone of the Fourth Amendment is reasonableness ," n111 such that the Fourth Amendment only "sometimes ... requires warrants." n112 Especially in light of the increasing number of exceptions to the warrant requirement, n113 it seems likely that an exception is appropriate in the context of foreign intelligence surveillance for purposes of national security, not only in terms of meeting a more formalist reading of the Fourth Amendment, but even more forcefully meeting a functionalist reading , under which [*2221] the improved protections of civil liberties could render the decreased reliance on ex ante judicial review preferable under the Fourth Amendment. Page 78 Disease DA --- Privacy The aff’s 4th amendment precedent spills over from security to health --- that wrecks disease surveillance that depend on privacy invasions Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka Similarities in Security Surveillance and Public Health Surveillance Courts and commentators have addressed similar questions in the context of security surveillance programs. In particular, they have identified three features of government security surveillance that make the privacy invasions especially troubling: the surveillance is increasingly comprehensive and intimate, it involves registries of unprecedented size and data mining potential, and it targets politically underrepresented domestic communities . In the context of security surveillance programs, all three features have provoked significant privacy concerns. B. However, there is variation in the extent to which courts have incorporated each concern into Fourth Amendment analysis: The intimate and comprehensive nature of government surveillance is changing the analysis under the Fourth Amendment and its state counterparts, the targeting of politically underrepresented communities has not explicitly done so, and the use of registries and data mining falls in the middle. My goal in this Part is to borrow from recent judicial opinions and public commentary about each feature of security surveillance, and to suggest that emergent public health surveillance programs raise similar concerns. n105 I do not intend to equate Fourth Amendment doctrine with Fourteenth Amendment doctrine. I claim only that the Fourth Amendment cases demonstrate a growing judicial recognition that a relationship exists between government surveillance technologies and methods on the one hand, and the nature of the individual [*1971] privacy interest at stake on the other. Similarly, I do not claim that the government interventions that may result from surveillance are the same in the security and public health surveillance contexts. n106 My claim is that emerging conclusions about the relationship between the nature of government surveillance and the privacy interest at stake in the security context can inform a conversation about emergent health programs . The security surveillance cases and commentary delineate an area of privacy - or alternatively, a type of government intrusion into personal privacy - that may warrant heightened constitutional protection. The analysis in this Part has two implications. First, emergent programs may effect a privacy invasion that violates social and constitutional values. n107 Second, altering constitutional jurisprudence in response to the changing nature of government surveillance activities is viable and appropriate. To oversimplify, if developments in security surveillance tactics and technologies can transform a permissible government activity into a "search" under the Fourth Amendment, which in turn requires ex ante judicial review before the activity can constitutionally occur, then similar developments in emergent public health surveillance programs may warrant more robust analysis under the Fourteenth Amendment. Public health surveillance solves pandemics Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka Public Health Surveillance A. Modern Public Health Surveillance The history of public health surveillance and public health interventions is both fascinating and complicated: A full account is far beyond the scope of this paper. n11 However, two observations based on that history frame my argument. First, the basic features of modern public health surveillance are not new; they were developed as responses to serious contagious disease. Second, public health surveillance in the United States has, in general, enabled interventions which - criticisms aside - have effectively addressed the public health crises they targeted. n12 To give just one example, the surveillance and interventions conducted using New York City's nineteenth-century tuberculosis registry prevented the spread of tuberculosis. n13 The program was accompanied by an impressive array of free services that helped to prevent and treat the disease. City and charitable organizations disinfected homes after a tubercular patient had moved or died, treated patients in facilities established across the City, created open-air programs for children and adults, and provided financial and logistical aid to tubercular patients. n14 Other municipalities offered similar services to patients. n15 [*1955] While public health surveillance has undergone radical changes n16 - with technological developments, epidemiologic shifts, and the Page 79 rapid expansion and coordination of public health surveillance activities transforming a disparate collection of municipalities, each battling contagion, into a sophisticated, coordinated, and pervasive public health apparatus - the purpose remains the same: to collect and compile information about sick people over time, and then use that information to protect the public health . A cursory review of government public health activities since the late medieval period demonstrates that " throughout history , governments have performed their public health role by ... taking steps to prevent the spread of epidemics ." n17 Mandatory quarantine programs - "features of most port towns" in colonial America - provide a dramatic example of surveillance-based public health interventions. n18 The relevant point is that surveiling individuals to protect the public health is anything but new. Indeed, the New York City Department of Health and Mental Hygiene intentionally modeled the A1C Registry - the paradigm of emergent public health surveillance - upon nineteenth-century surveillance and intervention programs that targeted tuberculosis. n19 The innovations - and the problems - at the heart of emergent programs are that they target individuals who pose no health risk to others, and they employ technology that enables surveillance that is virtually unlimited in scope. Extinction --- no burnout Casadevall 12 March 21st, 2012, Arturo Casaveall is a professor of Microbiology and Immunology at the Albert Einstein College of Medicine, Arturo, “The future of biological warfare,”http://onlinelibrary.wiley.com/doi/10.1111/j.1751-7915.2012.00340.x/full In considering the importance of biological warfare as a subject for concern it is worthwhile to review the known existential threats. At this time this writer can identify at three major existential threats to humanity: (i) large-scale thermonuclear war followed by a nuclear winter, (ii) a planet killing asteroid impact and (iii) infectious disease. To this trio might be added climate change making the planet uninhabitable. Of the three existential threats the first is deduced from the inferred cataclysmic effects of nuclear war. For the second there is geological evidence for the association of asteroid impacts with massive extinction (Alvarez, 1987). As to an existential threat decades have provided unequivocal evidence for the ability of certain pathogens to cause the extinction of entire species. Although infectious disease has traditionally not been associated with extinction this view has changed by the finding that a single chytrid fungus was responsible for the extinction from microbes recent of numerous amphibian species (Daszak et al., 1999; Mendelson et al., 2006). Previously, the view that infectious diseases were not a cause of extinction was predicated on the notion that many pathogens required their hosts and that some proportion of the host population was naturally resistant. However, that calculation does not apply to microbes that are acquired directly from the environment and have no need for a host, such as the majority of fungal pathogens. For those types of host–microbe interactions it is possible for the pathogen to kill off every last member of a species without harm to itself, since it would return to its natural habitat upon killing its last host. Hence, from the viewpoint of existential threats environmental microbes could potentially pose a much greater threat to humanity than the known pathogenic microbes, which number somewhere near 1500 species (Cleaveland et al., 2001; Tayloret al., 2001), especially if some of these species acquired the capacity for pathogenicity as a consequence of natural evolution or bioengineering. Page 80 Military DA --- Warrants Exigent circumstances are key to military effectiveness --- warrants devastate flexibility Forgang 9 --- J.D. Candidate at Fordham (Jonathan, "THE RIGHT OF THE PEOPLE": THE NSA, THE FISA AMENDMENTS ACT OF 2008, AND FOREIGN INTELLIGENCE SURVEILLANCE OF AMERICANS OVERSEAS, Fordham Law Review, Lexis)//trepka A warrant requirement is always subject to exceptions. n411 It is logical that the warrant requirement for surveillance of Americans overseas should also be subject to many of the same exceptions . The most important warrant exception for foreign intelligence surveillance is the exigent circumstances exception . n412 The United States' intelligence agencies, military , and law enforcement personnel must be able to respond to national security threats with speed and efficiency . Therefore, any FISA warrant requirement should include an exigent circumstances exception. n413 Beginning surveillance under this exception should not end the judicial scrutiny of foreign intelligence surveillance. There should still be accountability when the government uses the exigent circumstances exception. Though the threat may be imminent enough that it necessarily means that the delay of seeking prior judicial approval is unreasonable, once the necessary surveillance begins it should be easy to have the FISC quickly review the surveillance's necessity and minimization precautions. The original FISA rules required approval of surveillance initiated under the exigent circumstances exception within seventy-two hours. n414 However, the most recent FISA amendments have extended the period for approval of surveillance begun under exigent circumstances to seven days. n415 A period of warrantless surveillance should be minimized because there is a significant risk that warrantless surveillance unnecessarily invades Americans' privacy. This risk is necessary where there is a dire threat to national security. But it is important that an impartial party assesses whether this threat actually exists and if the surveillance is beneficial. Another necessary exception to the warrant requirement should be surveillance conducted as part of an American war effort . The rules of surveillance of civilians should not apply when the government is acting to obtain surveillance for the war efforts of the United States military. In this scenario there should be few situations where Americans are surveillance targets of the U.S. military. To the extent that the Highlander surveillance was necessary military surveillance confined to Iraq and Afghanistan and conducted to protect American troops, the surveillance was justifiable. NSA surveillance targeting Americans in other parts of the Middle East, when not responding to an immediate threat, however, is unreasonable unless the NSA submits to prior judicial review of the surveillance. Decline causes lashout --- specifically China, North Korea, and Russia --- that escalates Olsen 14 – (Wyatt; Military’s reduced readiness seen as emboldening China, Russia; May 20; www.stripes.com/news/military-sreduced-readiness-seen-as-emboldening-china-russia-1.283925; kdf)//trepka Just to the west, China recently began preparations for what the Philippines described as a possible military airstrip on a reef in the Spratly Islands , which both countries claim. Meanwhile, Russia has ratcheted up its presence in the Pacific — including long-range air patrols off the coast of California and near the U.S. territory of Guam — to gather intelligence and display its military might. The Japan Air Self Defense Force almost doubled its number of scrambles against Russian aircraft in the 12 months leading up to March compared with the previous year. And North Korea has intensified its rhetoric amid what appear to be preparations for its fourth underground nuclear weapons test. The U.S. still maintains the most formidable force in the Pacific. The Pacific Fleet consists of about 180 ships, which include five aircraft carrier strike groups and almost 2,000 aircraft, according to U.S. Pacific Command. One aircraft carrier and about 65 ships are permanently forward deployed in Japan. By comparison, as of last year China’s navy had only 52 frigates and 23 destroyers, many of them antiquated, according to the Pentagon’s most recent assessment of China’s military. Russia’s Pacific Fleet consists of a missile cruiser, five destroyers and a few dozen submarines, according to recent news reports. “The U.S. certainly retains an ability to project an awful lot of air and sea power for more Page 81 limited contingencies — and do so very quickly,” said Anthony Cordesman, a defense expert at the bipartisan Center for Strategic and International Studies in Washington, D.C. And even if U.S. forces did become embroiled in Pacific confrontations such as those unfolding in Vietnam and the Philippines, they aren’t the kind of interventions that demand huge follow-up forces, he said. Cordesman cautioned against equating these kinds of skirmishes with a potential outbreak of hostilities on the Korean peninsula because the U.S. is prepared and willing to match escalation there, he said. “You’re not going to go to general war over an [exclusive economic zone] or a reef somewhere in the Pacific,” he said. Still, Cordesman admitted, irrational behavior and miscalculations by adversaries can quickly lead to escalation and “the need for putting many more follow-on forces in the field over time.” Some experts say that flagging readiness — real or perceived — actually invites escalation by weakening America’s “deterrent effect ” as China and Russia continue beefing up their Pacific forces. Page 82 State Secrets DA --- Warrants Probable cause requirements undermines state secrets privilege and separation of powers Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka The law should also be amended to give standing to any persons who have been overheard by FISA surveillance, or have a reasonable suspicion that they were overheard, to challenge the surveillance techniques and the evidence submitted to the FISA court in the persons should be given an implied right of action to sue the government for infringing their right to privacy where the evidence submitted to the government was not sufficient to establish probable cause that the target of the surveillance had a connection with a foreign power. The burden of proof would be on the individual to disprove application for FISA surveillance. n204 Such the government's evidentiary support for the FISA surveillance. Complicating this proposed remedy, in addition to the fact that targets will not know that they are under investigation, is the state secrets privilege which allows the government to refuse disclosure of military and state secrets which, if exposed, pose a reasonable danger of [*229] threaten ing the safety of the nation. n205 The state secrets doctrine is an evidentiary privilege which may be invoked by the executive branch to protect military and state secrets from disclosure in a judicial proceeding. n206 The privilege is only available to the executive and may be invoked only where the court is satisfied that disclosure of evidence or a response to a question will have a negative effect on national security. n207 In accordance with the Classified Information Procedures Act of 1980 ("CIPA"), a court reviewing information determined by an executive order to "require protection against unauthorized disclosure for reasons of national security" may authorize the government to "delete specified items of classified information from documents to be made available to the defendant through discovery." n208 Since CIPA was enacted by Congress, it can certainly be amended to allow defendants challenging FISA surveillance to review the evidence against them. However, it is unclear if Congress has the authority to revoke the state secrets privilege of the executive branch. If this privilege is an inherent power of the executive branch, Congress will not be able to amend the practice and defendants contesting FISA will not be able to review the evidence against them where the state secrets doctrine is invoked. Congress could, however, enact legislation which mandates that in a challenge to FISA surveillance the executive branch may invoke the state secrets privilege only if the government pays damages to the defendant, regardless of the outcome of the case. If the government does not wish to pay damages, the evidence against the defendant must be disclosed. While this policy would provide defendants with a remedy, it is unclear if such a coercive measure against the executive branch in the field of foreign affairs and national security would withstand judicial scrutiny as it may violate the separation of powers doctrine. If the state secrets privilege is determined by a court to be an inherent power of the President and the executive branch, there is little Congress could do to force the President's hand regarding matters strictly delegated to the executive branch by the Constitution. Violation of the State Secrets privilege risks nuclear war Masco 10 --- associate professor of anthropology at the University of Chicago (Joseph, “Sensitive but Unclassified”: Secrecy and the Counterterrorist State, http://publicculture.org/articles/view/22/3/sensitive-but-unclassified-secrecy-and-thecounterterrorist-state)//trepka The power of the secret in contemporary American society is difficult to overestimate. Under the U.S. war on terror (inaugurated during George W. Bush’s administration in 2001), the logics and policy goals of the national security state — including the rationale for preemptive war, the terms of “extraordinary rendition” and the “detainee,” and the surveillance of U.S. Page 83 citizens — have all been formally designated as “secrets” under a discourse of imminent threat. However, the “newness” of the war on terror masks the deep structure of this security logic and the profound mutation in the nature of the state produced by the advent of the atomic bomb and the accompanying expansion of state secrecy devoted to protecting it. Indeed, the invention of the national security state after World War II transformed America into a new kind of secret society, one in which state power rests to an unprecedented degree precisely on the ability of officials to manage the public/secret divide through the mobilization of threat. This “secrecy/threat matrix” marks all state secrets as equivalents of the atomic secret, making revelation a matter not just of politics but of the life or death of the nation-state. The Cold War arms race — founded on the minute-to- minute possibility of nuclear war — installed the secrecy/threat matrix as the grounds for a new species of politics in the United States. Page 84 Terror DA --- Warrants Maintaining status quo case law is sufficient to uphold privacy considerations --- the alternative is warrant requirements that hamstring counterterror operations Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Commentators advance many rationales to justify the warrant requirement in general, several of which this Comment addresses in Part II. However, it should be noted at the outset that the warrant application process conceivably could be counterterrorism officers must search widely to gather information on latent threats, a significant amount of the information gathered will ultimately be unrelated to any terrorist activity. n11 Thus, much of the information gathered through clandestine intelligence operations will not be used in criminal prosecutions , and these the only review of intelligence activities by courts. Because intelligence activities will never come to light. One could therefore assert that the warrant requirement is necessary to provide a judicial check on the executive's intelligence-gathering prerogative. n12 This Comment rejects this argument for two reasons. First, where intelligence officers' main concern is not preserving evidence for a future criminal prosecution but instead uncovering latent plans for a terrorist attack so that it can be prevented, the incentive to obtain a warrant - even where one is required - is greatly diminished because those officers know they are unlikely to ever need to justify the search before a court. Thus, the warrant requirement itself may be inadequate to ensure that a court reviews the domestic intelligence activities of the executive branch. President Bush's authorization of domestic wiretapping in violation of FISA n13 underscores this point. Second, insofar as a search is likely to come to light courts will then be available to review the intelligence-gathering operations in question. An intelligence officer will [*347] likely not know for sure whether she will need to justify a search before a court at some point in the future. Even if a warrant is not required, therefore, a wise officer will take steps to ensure that the search is reasonable , so as to - whether through leaks to the news media, congressional oversight, or a criminal prosecution - the ensure favorable judicial review at a later point. Thus, where a search is almost certain never to come to light (say, because the government has no intention of using the information in a criminal prosecution, but instead to further ongoing military operations), an officer has little incentive to seek a warrant, making the warrant requirement impotent. But because there is some likelihood that the search will be subject to judicial review, an officer likely will take steps to ensure the reasonableness of that search. Thus, this Comment argues that the debate over whether or not warrants should be required actually devolves into a debate over whether before-the-fact review is inherently better than after-the-fact review in the intelligence-gathering context. As noted more fully in Part II, warrants offer little benefit vis-a-vis after-the-fact review. Furthermore, warrants impose real costs on intelligence gathering . The warrant's probable cause requirement stifles many legitimate intelligence-gathering activities that are vital to uncovering the plans of covert terrorist agents, n14 and the warrant application process itself can deter legitimate searches. n15 While commentators advance legitimate policy concerns to justify the warrant requirement, n16 this Comment argues that other measures can adequately address these concerns without imposing the costs of the warrant process on intelligence gathering. n17 Given the warrant requirement's burden on counterterrorism and the availability of adequate alternatives to the warrant, the Court should break with its precedent in the domestic intelligence context - where the stakes are high and adopt a rule that when the government gathers domestic intelligence to thwart a future attack, its conduct is governed solely by the reasonableness standard and only reviewed by courts after-the-fact. Although such an approach would require repudiating Keith, it can fit comfortably within the Court's current Fourth Amendment jurisprudence as an Page 85 extension of either the " special needs " or foreign intelligence exceptions to the warrant requirement. n18 This Comment thus does not argue for a radical shift in the Court's Fourth Amendment case law. Strict interpretations of the Fourth Amendment don’t solve privacy, but they make it impossible to prevent a bioweapons attack Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Imagine two scenarios. In the first, an American citizen with a connection to al Qaeda conspires with his cohorts, also American citizens, to attack the United States using biological warfare agents. He surveils potential sites for the attack - a high-rise tower, an athletic stadium, a government facility - and acquires some of the materials needed to carry out the attack. Meanwhile, his coconspirators are busy in their makeshift lab concocting the biological agent to be used in the attack. The members of the group communicate with each other and with their financial and ideological backers overseas via cell phone, email, and in person. They live in an American city, biding their time as they wait for their superiors to give them the final go-ahead. The second scenario is identical to the first, except that no overseas superiors direct and finance the operation. Instead, our terrorist cell is out on its own, unconnected to - though ideologically compatible with - al Qaeda. Even without its master in a foreign land, the group has the resources necessary to carry out the attack. In effect, the threat posed in both scenarios is identical. n1 Despite the indistinguishable threats posed by these two groups, the United States government is substantially more likely to thwart an attack by the group in the first scenario. The President has greater authority to conduct counterterrorism surveillance and intelligence gathering against groups with foreign connections than against groups with no foreign connections. This dichotomy derives from the Supreme Court's decision in the Keith case, which held that a warrant is required for a domestic intelligence search to comport with the Fourth Amendment. n2 Thus, unlike investigations into groups with foreign connections, domestic terrorist investigations are subject to far more stringent requirements under the Fourth Amendment . n3 Over the last few years, much of the scholarship on the Fourth Amendment and intelligence gathering has focused on foreign intelligence gathering within the United States. n4 President Bush's January 2005 authorization [*345] of warrantless electronic surveillance of al Qaeda-related communications with overseas connections has generated a wealth of commentary, most of it analyzing whether such conduct violates the Foreign Intelligence Surveillance Act (FISA), n5 or whether Congress can constitutionally limit the President's power to conduct foreign intelligence surveillance within the United States. n6 This Comment eschews the separation of powers questions that dominate these analyses. Instead, it attempts to fill a gap in the scholarship by focusing on purely domestic intelligence gathering that implicates the Fourth Amendment. This Comment challenges the assertion made by many commentators that warrants, whether for domestic or foreign intelligence gathering in the United States, should be required because they provide a check on executive discretion. This Comment argues that warrants provide only marginal privacy-protection benefits while imposing real costs on domestic intelligence gathering - defined as intelligence gathering designed to thwart threats with no foreign connections. The Fourth Amendment's reasonableness touchstone should supplant the focus the Supreme Court has placed on warrants and probable cause in determining compliance with the Fourth Amendment in the domestic intelligence-gathering context. Reasonableness inherently involves the weighing of various interests on both sides of an issue and can therefore take into account the waxing and waning of threats posed against the United States. n7 Thus, an intrusive search designed to prevent a terrorist attack might be reasonable, but the same search using the same means solely to investigate a crime that has already been committed might be unreasonable . By straight-jacketing itself into a Page 86 warrant and probable cause analytical framework, the Court forces itself to find exception after exception when such a framework proves unworkable, n8 due to either the needs of the government [*346] or the nature of the particular search. n9 Such exceptions to the warrant requirement are understandable because a warrant presumption can, in many instances, be an effective way to enforce the Fourth Amendment's commands. However, given that in the domestic intelligence context, warrants are insufficient to protect Fourth Amendment interests and that the probable cause requirement for all searches makes effective intelligence gathering difficult , n10 the Court should extend an exception to the warrant requirement for domestic intelligence gathering . It’s uniquely key to prevent terrorism now --- ruling to protect 4th amendment rights undermines a necessary degree of surveillance with the ever-present threat of terrorism Plummer 6 --- J.D., Mississippi College School of Law, law clerk for Barnes of the Mississippi Court of Appeals (Brooke, “Domestic Spying: A Necessity in a Post-9/11 America or an Abuse of Presidential Power?”, Mississippi College Law Review, Lexis)//trepka Benjamin Franklin once famously remarked that "they that can give up essential liberty to obtain a little temporary safety deserve neither safety nor liberty." n124 In the midst of the current national debate over the NSA's [*319] domestic spying program, these words have become a mantra for those who claim that the program cannot withstand scrutiny under the current law of the United States. However, while Franklin's notion that liberty cannot be sacrificed for safety is great in theory, it cannot withstand the reality of a post-9/11 America, at least not in its absolute form. Franklin could not possibly have envisioned a series of events such as those that transpired on 9/11 and how those events would change this nation. The American citizenry simply cannot expect the same degree of privacy that it enjoyed prior to 9/11 while at the same time demanding that its government protect it from an enemy that thrives on such privacy. However, this is certainly not to say that civil liberties must always be forsaken for the pursuit of national security, for to allow that to happen would destroy the values upon which this country was founded. Therefore, perhaps the greatest challenge faced by the United States as it prosecutes the war on terror is striking the appropriate balance between the protection of civil liberties and the pursuit of national security. Whether the NSA domestic spying program strikes this balance remains to be seen. As laudable a goal as national security is, this is still a nation of laws and, as the foregoing discussion illustrates, there is substantial evidence to support the argument that the NSA program violates these laws. Nonetheless, one must always remember that the war on terror is not a conventional war, and it is for this reason may not be desirable to require that the means used to prosecute this war strictly comply with laws whose creators could not possibly have conceive d of the realities of a post-9/11 America. Again, this is not to say that such laws can be disregarded in the pursuit of the safety of the nation, but only to that it suggest the laws' requirements be interpreted in light of the nation's current state of affairs, for the failure of those entrusted with the responsibility of interpreting the law to adapt the law to changing circumstances can lead to more harm than good, especially when something as serious as national security is at stake. That being said, the NSA domestic spying program authorized by President Bush may not withstand scrutiny under any interpretation of the relevant laws and, because of its national significance, the final arbiters of this debate will almost surely be the nine justices of the United States Supreme Court. Given that the ACLU case is currently making its way through the appeals process, the Court is likely to be faced with this most important of cases sooner rather than later. Furthermore, due to the recent changes in the Court's make-up, there is no way to accurately predict how the Court might rule. Regardless, in the meantime, the debate over domestic spying will surely rage on. Page 87 The plan’s precedent spills over to overall national security Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka The legal issues surrounding the NSA wiretapping program are complex, implicating constitutional law, statutory law, canons of constitutional interpretation, [*285] and national security law. The purpose of this section is to highlight the main legal issues. This section in no way, however, exhausts all the relevant legal issues. Critics argue that FISA provides the exclusive manner to conduct foreign surveillance; therefore it was unlawful for President Bush to bypass its provisions by executive order. These critics also emphasize that FISA already contains provisions for warrantless surveillance such as allowing emergency wiretaps without a warrant for seventy-two hours as long as a warrant is obtained within that time frame; or allowing warrantless surveillance fifteen days following a declaration of war by the Congress; or allowing the Attorney General to conduct warrantless surveillance for up to one year if U.S. persons are not the targets. n99 Hence, critics contend that, given the exceptions for warrantless surveillance, there was no need for the President to bypass the statutory scheme created by Congress. n100 Furthermore, critics maintain that Congress had been willing to amend FISA as it did with the Patriot Act, so there was no justification for the executive to unilaterally bypass FISA without Congressional authorization. n101 The Bush administration countered that FISA was not exhaustive and allowed for subsequent statutes concerning foreign surveillance. Specifically, FISA prohibits any person from intentionally "engaging ... in electronic surveillance under color of law except as authorized by statute." n102 Therefore, the Bush administration maintained that in enacting FISA, Congress contemplated the possibility that the president might be permitted to conduct electronic surveillance pursuant to a later-enacted statute that did not incorporate all of the procedural requirements set forth in FISA, or that did not expressly amend FISA itself. n103 Furthermore, the Bush administration claimed that the AUMF passed by Congress on September 14, 2001 (which authorizes the president "to use all necessary and appropriate force against those nations, organizations, or persons he determines planned, authorized, committed, or aided the terrorist attacks that occurred on September 11, 2001") qualified as such a statute, authorizing electronic surveillance within the meaning of FISA. n104 According to the Bush administration, the broad language of the AUMF afforded the president, [*286] at a minimum, discretion to employ the traditional incidents of the use of military force, which included surveillance. n105 The Bush administration pondered how it could use "force" if it could not first locate the targets, which obviously required surveillance. The Bush administration further supported a broad reading of the AUMF by citing to the Supreme Court's decision in the case of Hamdi v. Rumsfeld, n106 where the Court held that the AUMF implicitly authorized the president to detain enemy combatants, even though the AUMF contained no explicit mention of that power. n107 Ruling on the Fourth Amendment makes it impossible to combat terrorism Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka Bush administration felt it needed to bypass FISA because it did not have probable cause that the targets it sought were agents of foreign powers, or believed it did have probable cause but felt it did not have adequate time to comply with seeking a FISA warrant. n135 In other words, the rationale for the TSP may have been based on a belief that the substantive probable cause standard was too demanding , or the TSP was preferred in order to simply bypass the procedural requirements of FISA in seeking a warrant . The Perhaps the reality may be a little of both. Although Gonzales stated in 2005 that the TSP required the Bush administration have a "reasonable basis" for believing that one party to the call was a terrorist, n136 it is unresolved whether "reasonable basis" was closer to the predicate "probable cause" required by FISA or the lesser standard of "reasonable suspicion." n137 The administration has argued both positions. [*291] While Gonzales stated that "reasonable basis" was Fourth Amendment , reports indicate that General Hayden stated that the Bush administration had adopted a "reasonable suspicion" standard in applying the TSP because the probable cause standard in FISA was "too onerous." essentially the same as "probable cause" under the n138 n139 Complicating matters more, in 2002, a senator tried to change the "probable cause" standard to "reasonable suspicion" for non-US persons under FISA, but the Justice Department did not support the change, arguing that the probable cause standard was not an obstacle to effective use of FISA and that the change to reasonable suspicion would probably be unconstitutional. n140 Such a revelation is especially troubling given General Hayden's statement regarding adopting "reasonable suspicion" as the TSP standard. In essence, it appears that the Bush administration purposefully opted for the lower reasonable suspicion standard with no FISA oversight at all. Hence, there appear to be two primary rationales for the TSP: (1) that the probable cause Page 88 standard is too high and (2) that the procedural requirements seeking a FISA warrant are too burdensome. Each potential explanation is addressed in turn. A. Substantive Probable Cause Standard To what extent is the probable cause standard under FISA sufficient to counter the terrorist threat? As explained previously, unlike Title III, FISA does not require probable cause that a crime is being, has been, or is about to occur before the issuance of a warrant, but rather probable cause that the target is an agent of a foreign power or terrorist group (and for U.S. persons, the additional requirement that the U.S. person may be engaging in activities that knowingly could be a crime). n141 Despite the lower burden under FISA, several policy makers and lawyers argue that requiring probable cause that the target is an agent of a foreign power is too onerous and does not appreciate the complexities in detecting terrorist activity. According to former Deputy Attorney General John Yoo, because FISA "assumes that the government already has [probable cause] to believe that a target is the agent of the foreign power before it even asks for a warrant," FISA works well when the foreign agents are easy [*292] to detect like "foreign embassy, officials working for a hostile nation," or "a Soviet KGB agent operating undercover as a diplomat." n142 Al Qaeda poses a different challenge, however; its members do not work for embassies and are not part of any one nation. Yoo's claims are also supported by former federal prosecutor Andrew McCarthy, n143 and Seventh Circuit appellate judge Richard Posner. n144 As McCarthy explains, "To have probable-cause on a target is to know already that he is dangerous. That's too late. Today's challenge is to discover the unknown Mohamed Atta in our midst, something that can't be done unless surveillance begins whenever it is reasonable to suspect a foreign operative." n145 As Yoo describes, "counterterrorism agencies must search for clues among millions of potentially innocent connections, communications, and links." n146 Judge Posner observes that innocent people may not even be aware that they know or are abetting a terrorist: "the intelligence services must cast a wide net with a fine mesh to catch the clues that may enable the next attack to be prevented." n147 Hence, according to Yoo, McCarthy, and Posner, U.S. intelligence agents need to be able to follow leads quickly and must act fast on educated guesses. Consider the following example, which is informed by Yoo's description of intelligence gathering in War By Other Means: an al Qaeda leader is captured in Europe and his laptop or cell phone has ten U.S. phone numbers on it. It is questionable whether a FISA judge would find probable cause that the users of the ten phone numbers are terrorists. Perhaps, the captured terrorist had called a hotel in the United States to merely make a reservation. Nonetheless, intelligence officials would want to conduct surveillance on the ten individuals - many who may be innocent and not even aware that their communications may have intelligence value - to n148 n149 determine if any are terrorists. n150 As Cato Senior Fellow Robert Levy explains, there may be a need to conduct surveillance [*293] on individuals who have had "contact" (even innocent contact) with al-Qaeda members, even though these people are not "agents" of a foreign power as FISA currently The government can't get a FISA warrant just to find out whether someone is a terrorist; it has to already have a reason to believe [s]he's one." According to requires. n151 Yet, as Posner notes: " n152 Yoo, even if the phone numbers on the cell phone established probable cause, obtaining a FISA warrant is a cumbersome process in which "FBI and DOJ lawyers prepare an extensive package of facts and law to present to the FISA court." n153 The attorney general must also sign off on the application and another national security officer "must certify that the information sought is for foreign intelligence." n154 Yoo maintains that "leads could go stale" during Yoo concludes that FISA does "not meet today's challenge - a sophisticated, covert, foreign enemy that does not operate out of embassies like the spies of the Cold War , but instead conceals its communications within the billions of innocent phone calls and e-mails sent every day." General Hayden has expressed the same concern about leads going stale under a rationale of "hot pursuit," where it is felt there is not enough time to obtain a FISA warrant without jeopardizing the surveillance. For instance, if NSA were spying on a terrorist in Yemen and the terrorist called a person in the United States, then NSA this time period. n155 n156 n157 could legally listen to the call without a warrant because the target was the Yemeni terrorist. But as soon as the call was complete, NSA could not continue listening to this American's conversations without a FISA warrant. Yet, according to Hayden, time would be of the essence and there would not be time to obtain a FISA warrant. n158 While FISA allows a seventy-two hour window to begin surveillance, a warrant application would still need to be prepared within seventy-two hours, and, more importantly, there must still be probable cause to begin the surveillance. n159 According to Hayden and Yoo, however, under conditions of hot pursuit, there may not be probable cause that the American is an agent of a terrorist group. He could just be an innocent contact of al-Qaeda or an agent of a terrorist group; surveillance is necessary to make that determination. As law professor Sims describes, "the warrantless surveillance program is based on the fear that some relevant communications may slip through the cracks, in a situation in which the government either Other hypothetical examples also highlight deficiencies with the probable cause standard. For instance, Senator Malcolm Wallop proposed the following scenario: Consider the case of someone with knowledge of a band of nuclear terrorists , hiding in one of a thousand apartments in a huge complex. It would be both reasonable and easy to tap every telephone in the complex, discard all intercepts but the correct one, and gain the vital information. But that would involve 999 violations of [FISA]. Assistant Attorney General David Kris described a similar fact pattern during Congressional testimony: If the government had probable cause that a terrorist possessed a nuclear bomb somewhere in Georgetown, and was awaiting telephone instructions on how to arm it for detonation, and if FISA were interpreted not to allow surveillance of every telephone in Georgetown in those circumstances, the President's assertion of Article II power to do so would be quite persuasive and attractive to most judges and probably most citizens. While these "ticking bomb" scenarios may be rare, and arguably farfetched, they do illustrate a potential problem with the cannot get a FISA warrant or is unwilling to do so." n160 [*294] n161 n162 Page 89 probable cause standard that could justify rethinking the needed predicate for surveillance. Part V provides some thoughts about potential reforms. Procedural amendments bad --- undermine counterterror Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka Along with the required substantive changes to FISA, procedural amendments are also required to ensure that FISA will not be used to escape the Fourth Amendment. As discussed in Part III, the FISA court currently defers to the executive official's assertion that the significant purpose of surveillance is for foreign intelligence purposes, absent a determination that such certification is "clearly erroneous." To properly ensure that the government's purpose is foreign intelligence surveillance, rather than defer to the executive official, the determination of whether the proper purpose of the surveillance is foreign intelligence gathering should be made through a factual inquiry and review by a FISA court judge of the evidence and sworn affidavit submitted by the executive attesting to the existence of probable cause to believe that the target of surveillance has a connection with a foreign power. such review by the court may delay the granting of a FISA order for surveillance, this policy would do more to ensure the validity of the executive's assertions than the current procedures. This procedural safeguard is especially necessary in light of the recent disclosure that "the FBI has repeatedly submitted inaccurate information to the Foreign [*226] Intelligence Surveillance Court ("FISC") in its efforts to obtain secret warrants in terrorism and espionage cases - severely undermining the Government's credibility in the eye of the Chief Judge of that Court." n195 However, the problem with such a procedural change, in addition to dramatically slowing down the government's ability to respond to and effectively counter threats to national security, lies in the fact that the information before the FISA court was submitted by the executive branch, and the court, as it is not in the business of collecting facts, has no way to verify that the submitted facts are true. Though this procedural amendment would delay counterintelligence efforts and place the court in an unfamiliar role , such a policy would conclusively ensure that the government has a Although proper purpose for surveillance. Another link Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka To require a court order for every instance in which a foreign target communicates with someone inside the United States is to require a court order for every foreign target, and requiring this would reverse 30 years of established intelligence gathering. The intelligence community cannot possibly know ahead of time who these terrorists will talk to. It needs to have the flexibility to monitor calls that may occur between a foreign terrorist and a person inside the United States. n222 Undermines administrative flexibility Plummer 6 --- J.D., Mississippi College School of Law, law clerk for Barnes of the Mississippi Court of Appeals (Brooke, “Domestic Spying: A Necessity in a Post-9/11 America or an Abuse of Presidential Power?”, Mississippi College Law Review, Lexis)//trepka In addition to citing the aforementioned cases recognizing a foreign intelligence exception, the Administration relies on the special needs exception to the Fourth Amendment's warrant requirement in arguing that the program is constitutional. n116 The Administration Page 90 contends that the special needs exception is particularly applicable "in circumstances in which the Government faces an increased need to be able to react swiftly and [*318] flexibly, or when there are at stake interests in public safety beyond the interests in ordinary enforcement;" furthermore, the Administration asserts and that "one important factor in establishing 'special needs' is whether the Government is responding to an emergency that goes beyond the need for general crime control." n117 Therefore, according to the Administration, in light of the continuing threat of terrorism and the clandestine nature of terrorist activities, domestic electronic surveillance for the purposes of foreign intelligence fits within the special needs exception and, therefore, may be carried out without a warrant. n118 Furthermore, because the Fourth Amendment requires that any search by the government be reasonable, irrespective of whether a warrant is required, the Administration argues that the invasion of privacy presented by domestic electronic surveillance of individuals suspected with terrorist ties is reasonable in light of the "Government's overwhelming interest in detecting and thwarting further al Qaeda attacks." n119 According to the Administration, this interest renders its electronic surveillance of communications in which one party is a suspected terrorist reasonable. n120 Supreme Court upholds the “special needs” exception now --- that’s critical to intelligence gathering Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka The Court has also frequently cast aside the traditional warrant requirement for searches or seizures that are conducted for reasons other than criminal law enforcement - the " special needs " exception. n39 That is, the Court has allowed warrantless searches on less than probable cause when they "are designed to serve the government's "special needs, beyond the normal need for law enforcement.'" n40 Under this exception, the Court has approved a checkpoint to query motorists about a hit-and-run accident n41 and [*352] allowed a public school to test its student-athletes for drugs at random. n42 Upon a showing of a special government need, the Court evaluates the constitutionality of a search merely "by balancing its intrusion on the individual's Fourth Amendment interests against its promotion of legitimate governmental interests ," n43 i.e., by determining the search's reasonableness. The special needs exception has also been used to justify warrantless intelligence gathering in the United States. In 2002, the Foreign Intelligence Surveillance Court of Review (FISCR) n44 heard an appeal by the government from the FISA court's imposition of certain restrictions on the government's foreign intelligence surveillance operation. n45 Amici, arguing in opposition to the government, n46 claimed that FISA warrants are not warrants within the meaning of the Fourth Amendment and thus any search conducted under such court authorization for the primary purpose of criminal prosecution is per se unreasonable. n47 The FISCR sided with the government, concluding that "the question [is] whether FISA ... is a reasonable response based on a balance of the legitimate need of the government for foreign intelligence information to protect against national security threats with the protected rights of citizens." n48 Under this framework, the court addressed the restrictions imposed by the FISA court, which were designed to further the proverbial "wall" between intelligence and law enforcement operations and personnel. n49 Amici argued that the wall was necessary to effectuate the Fourth Amendment's traditional warrant requirement for foreign intelligence searches conducted within the United States where the government's primary purpose is pursuing criminal prosecution. n50 The FISCR disagreed, holding that the Fourth Amendment does not require warrants for searches where a significant purpose of the search is foreign intelligence gathering . n51 The FISCR's holding relied in part on the special needs exception . While noting that the special needs exception would only apply where the government has a purpose beyond criminal law enforcement, the FISCR [*353] held that the proper method of Page 91 applying the exception is to analyze the programmatic purpose of FISA-related activities, not the purpose for which each individual search is undertaken. n52 Under this view, the goal of building a case for criminal prosecution can be the purpose of an individual surveillance activity, so long as such surveillance is part of the broader net under which FISA activities fall, namely the gathering of foreign intelligence. Thus, it is "the nature of the "emergency,' which is simply another word for threat, [that] takes the matter out of the realm of ordinary crime control," n53 even though in almost all instances the threat itself may constitute a crime. n54 Ultimately, the court applied a balancing test and concluded that "FISA as amended is constitutional because the surveillances it authorizes are reasonable." n55 Imposing warrant requirements overdeters --- decks the entirety of counterterror operations Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka themselves overdeter. Put simply, obtaining a warrant is costly . As William Stuntz argues: Warrants may be costly to the police - not in terms of money or lost convictions, but in time and energy ... . One of the primary reasons searches conducted with warrants tend so strongly to uncover evidence of crime is that Finally, warrants may getting warrants is such a hassle for police officers. In many cases, getting a warrant means a day's worth of paperwork plus sitting around the courthouse, all for the five-minute meeting with the magistrate... . Such queuing costs may tend to discourage officers from using warrants [unless the warrant is likely to bear significant fruit ]. n115 To lower the costs associated with obtaining a warrant, many jurisdictions have adopted streamlined warrant application procedures. For instance, magistrates in some places hear applications and issue warrants over the phone. n116 However, if ex parte review of in-person warrant applications is too biased in the government's favor, n117 then surely rushed over-the-phone applications - where the magistrate cannot even see the officer to judge his credibility or personally review any supporting documents or evidence the officer may have - only make the problem worse. Under these lax procedures, one begins to wonder if the warrant has any utility at all. A warrant application process that affords any real protection - however slight - would necessarily impose significant costs on the officers seeking the warrant. This is cause for concern, especially in the domestic intelligence context. As one scholar notes, the police generally do not seek warrants in marginal cases (where the chance of uncovering evidence is significant but far from certain), suggesting that one of the reasons warrants are issued almost without exception is because they are only sought when it is obvious they will be granted. n118 However, proactive intelligence gathering should necessarily involve "false positives" - searches that, though reasonable, turn up no evidence of terrorist activity. n119 But because a warrant is required for a domestic intelligence search, and because the warrant process is costly , intelligence officers are deterred from seeking a warrant, and [*363] therefore from searching at all. Many have argued that the FBI did not seek a warrant to search Zacarias Moussaoui's computer out of fear that a judge would not grant the warrant. n120 The fear of having a warrant application denied, then, leads to overly cautious intelligence gatherin g that necessarily decreases the amount of information counterterrorism agencies possess to combat threats from within. Although intelligence agencies, even absent a warrant requirement, could fail to conduct a search for fear that a judge will disapprove of the search in after-the-fact review, this scenario is unlikely because a judge in ex post review would apply the reasonableness standard , n121 which is less exacting the government and more favorable towards than probable cause. n122 As such, ex post review, consistent with the text of the Fourth Amendment (which only prohibits "unreasonable" searches), lowers the burden on the government to justify the search, which in turn would weaken an intelligence agent's fear that he would not be able to justify a search before a judge after the fact. Even if an agency becomes less sensitive to the possibility of Page 92 judicial disapproval of warrant applications, there is generally less evidence available to justify a warrant for a prospective terrorist attack than there would be for other crimes. n123 Thus, both the substantive requirements needed to obtain a warrant and the costs incurred in the process of obtaining it might prove so high that the warrant requirement actually stifles innovative national security measures. If the FBI is acting only when it strongly believes there is a specific threat - i.e., when it has probable cause of such a threat - it may well be too late, and it is certainly too timid. Thus, warrants deter or outright prevent counterterrorism intelligence gathering against all but the most obvious, known threats. This creates an unacceptable risk that the government will be denied information necessary to prevent the deaths of scores of its citizens . Page 93 SOP DA Page 94 1NC SOP Surveillance would be ruled unconstitutional on a separation of powers standing – that sets a precedent for judicial protection of separation of powers Slobogin 15 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, “Standing and Covert Surveillance” // AKONG) One response to standing arguments based on the insights of scholars like Milligan and Richards is that they ignore the close relationship between standing and the scope of the right in question. n131 Indeed, when the Fourth Amendment is the basis for the claim, the Supreme Court has explicitly conflated standing with the Amendment's substance. In Rakas v. Illinois, n132 [*542] the Court stated that the decision as to whether a defendant can make a Fourth Amendment claim "forthrightly focuses on the extent of a particular defendant's rights under the Fourth Amendment, rather than on any theoretically separate, but invariably intertwined con-cept of standing." n133 If a government action is not a Fourth Amendment "search" vis-à-vis the litigant, Rakas held, then the litigant lacks standing to challenge it. If that reasoning is the correct approach to standing, then in cases challenging covert surveillance on Fourth or First Amendment grounds everything rides on whether the surveillance, as it operates in the way the plaintiff describes it, infringes the plaintiff's reasonable expectations of privacy or speech and association interests. n134 While such a finding would presumably be made in the Clapper case, which involved the alleged interception of the content of overseas phone calls, n135 it is less certain in connection with collection and querying of metadata. The Fourth Amendment is only meant to protect reasonable expectations of privacy. n136 Supreme Court case law to date strongly suggests that any privacy one might expect in one's metadata or Internet activity is unreasonable, because we assume the risk that third parties to which we knowingly impart information(here phone companies and Internet service providers) will in turn divulge it to the government. n137 The same type of analysis might limit standing in cases brought under the First Amendment. As the Court intimated in Clapper, n138 one could conclude that even if speech and association are inhibited by surveillance, that inhibition proximately results from the individual's choices, not from [*243] anything the government has done to the individual. n139 On this view, even if an individual can show that he or she was targeted, standing to contest surveillance does not exist unless and until the government uses the seized information against the individual, because otherwise a colorable claim that a constitutionally cognizable interest was infringed cannot be made. If, despite its impact on political participation, covert surveillance like the metadata program remains immune from Fourth and First Amendment challenges, there remains another avenue of attack, derived directly from separation of powers doctrine. In other work, I have argued that, even if the Fourth (or First) Amendment does not govern a particular type of surveillance, Ely's political process theory provides a basis for challenging panvasive actions that are the result of a seriously flawed political process. n140 More specifically, panvasive surveillance might be challengeable on one of three grounds: (1) the surveillance is not authorized by the appropriate legislative body; (2) the authorizing legislative body does not meaningfully represent the group affected by the surveillance; or (3) the resulting legislation or law enforcement's implementation of it violates notions underlying the non-delegation doctrine. n141 The first and third of these grounds are based explicitly on separation of powers concerns. As I pointed out, some panvasive surveillance has not been legislatively authorized or has been authorized by legislation that does not announce an "intelligible principle" governing the implementing agency. n142 Panvasive surveillance is also defective under non-delegation principles if, as I have argued is true of the NSA's metadata program, it is implemented by rules or practices that are not explained, were produced through flawed or nontransparent procedures, or are applied unevenly. n143 Based on several Supreme Court cases, particularly in the administrative law area, n144 I [*544] concluded that any one of these deficiencies could be the basis for the claim that the legislature, the relevant law enforcement agency, or both are failing to carry out their constitutional obligations as law-making and law-implementing bodies. n145 Although this type of claim, like the Fourth and First Amendment claims, aims at "generalized relief," the Court itself has often granted standing to individuals making separation of powers claims. n146 The rationale of these cases is not difficult to grasp, because it again reflects the political process rationale. Many years ago Justice Brandeis stated, "[T]he doctrine of the separation of powers was adopted by the convention of 1787 not to promote efficiency but to preclude the exercise of arbitrary power." n147 More recently, Chief Justice Burger asserted that "checks and balances were the foundation of a structure of government that would protect liberty." n148 More recently still, in Bond v. United States n149 the Court stated "[t]he structural principles secured by the separation of powers protect the Page 95 individual as well." n150 If one accepts the possibility that a separation of powers argument can be made in covert surveillance cases, then parties who can demonstrate the type of injury described above--that is, a significant stifling of political participation that, to borrow the Second Circuit's language in its Clapper decision, n151 is a reasonable, non-fanciful, and nonparanoid reaction to covert surveillance--should have standing to challenge panvasive surveillance even if it is not a search under the Fourth Amendment or does not abridge First [*545] Amendment freedom. The merits claim would not be that the surveillance is an unreasonable search or infringement of speech or association rights, but rather that the legislature has failed in its delegation task or that the relevant law enforcement or intelligence agency has acted in an ultra vires fashion. These are the types of separation of powers claims that courts ought to hear because they assure the proper functioning of the political process that the Court is so eager to protect (with, inter alia, its standing doctrine). To requote Chief Justice Roberts, "[T]he obligation of the Judiciary [is] not only to confine itself to its proper role, but to ensure that the other branches do so as well." n152 Congressional war powers hinge on the degree of separation of powers – judicial precedent allows Congress to pursue further restrictions on executive warfighting capabilities Heder 10 (Adam, J.D., magna cum laude, J. Reuben Clark Law School, Brigham Young University, “THE POWER TO END WAR: THE EXTENT AND LIMITS OF CONGRESSIONAL POWER,” St. Mary’s Law Journal Vol. 41 No. 3 // AKONG) Given the textual and historical silence on the issue of whether Congress may claim statutory authority to terminate a war, this Article considers structural arguments to determine whether such a power is implied. Two basic structural principles of the Constitution are the system of checks and balances and the separation of powers.5 5 These principles ensure a balanced system in which no branch has overwhelming authority. Any develop- ment that would tilt the scales too heavily in favor of one branch, therefore, would violate these fundamental structural principles. As noted, Congress and the Executive share the war powers.56 While Congress has the power to raise an army,57 delegate funds,58 and declare war,59 the President has the authority to conduct the war effort.60 Accordingly, the Constitution creates a power-sharing regime in which Congress and the Executive cooperate, at least to some degree, in the prosecution of war. Likewise, Congress’s appropriation power and the President’s power to command the armies as he sees fit ensure that neither branch has final authority in all matters related to the prosecution of war. Thus, whether Congress has the more robust power to legally terminate a war, apart from its appropriation power, hinges in large part upon whether the exercise of such a power would be consistent with the principles of the system of checks and balances and the separation of powers. consistent with the principles of the system of checks and balances and the separation of powers. This Article first considers the Treaty Clause.61 As with other provisions of the Constitution, the Treaty Clause erects a power- sharing scheme between the elected branches. Endowing one branch with unilateral power to terminate war would contradict such a structural scheme. As noted above, the Constitution gives the President the right to make treaties, which includes the power to make peace treaties.62 Thus, the President’s power to make treaties presumably includes the power to formally end a war. However, the Clause does not give all treaty power to the President. It stipulates the President may make a treaty, “provided two thirds of the Senators present concur.”63 The process of formally declaring peace or formally ending a war, therefore, is a political process in which the President negotiates with the Senate to come up with a satisfactory solution.6 4 The point is that neither branch has ultimate authority. Rather, the political branches must cooperate in ratifying peace treaties. Such a scheme is consistent with a system in which the two political branches share war powers. Indeed, the two branches are expected to cooperate in order to draft a peace treaty. Instead of Congress having authority to unilaterally order the President to cease military operations, one would expect the two branches to engage each other politically to work toward a solution. Notwithstanding the Page 96 other structural considerations could militate in favor of a robust implied congressional power to statutorily terminate a war. In accordance with the separation of powers principle, Congress has the legislative power65 and the President has the executive power.66 Congress, having the legislative power either to declare war or pass a resolution authorizing war,67 has the implied legislative power, some might argue, of repealing such authorization. Under this argument, Congress would have the more robust power to end a war through means other than its appropriation power. Congress’s enumerated powers carry with them “subordinate and auxiliary” powers.68 The power to “declare war,” therefore, assumes the lesser power to legislatively “undeclare” war. Congress did this during the Vietnam War, when it repealed the Gulf of Tonkin Resolution,69 and considered similar action in 2007 regarding the Iraq War.70 Whether Congress’s attempts were or would have been constitutionally appropriate and legally binding upon the President remains largely unanswered because courts generally refused to adjudicate challenges to the constitutionality of the Vietnam War.71 Nevertheless, Congress has tried this avenue and likely will attempt it again. power-sharing scheme reflected in the Treaty Clause and the war-power-sharing structure of the Con- stitution, Executive war powers are key to averting extinction Li 9 (Zheyao, J.D. candidate, Georgetown University Law Center, 2009, B.A., political science and history, Yale University, 2006, “War Powers for the Fourth Generation: Constitutional Interpretation in the Age of Asymmetric Warfare,” // AKONG) A. The Emergence of Non-State Actors Even as the quantity of nation-states in the world has increased dramatically since the end of World War II, the institution of the nation-state has been in decline over the past few decades. Much of this decline is the direct result of the waning of major interstate war, which primarily resulted from the introduction of nuclear weapons.122 The proliferation of nuclear weapons, and their immense capacity for absolute destruction, has ensured that conventional wars remain limited in scope and duration. Hence, "both the size of the armed forces and the quantity of weapons at their disposal has declined quite sharply" since 1945.123 At the same time, concurrent with the decline of the nation-state in the second half of the twentieth century, non-state actors have increasingly been willing and able to use force to advance their causes. In contrast to nation-states, who adhere to the Clausewitzian distinction between the ends of policy and the means of war to achieve those ends, non-state actors do not necessarily fight as a mere means of advancing any coherent policy. Rather, they see their fight as a life-and-death struggle , wherein the ordinary terminology of war as an instrument of policy breaks down because of this blending of means and ends.124 It is the existential nature of this struggle and the disappearance of the Clausewitzian distinction between war and policy that has given rise to a new generation of warfare. The concept of fourth-generational warfare was first articulated in an influential article in the Marine Corps Gazette in 1989, which has proven highly prescient. In describing what they saw as the modem trend toward a new phase of warfighting, the authors argued that: In broad terms, fourth generation warfare seems likely to be widely dispersed and largely undefined; the distinction between war and peace will be blurred to the vanishing point. It will be nonlinear, possibly to the point of having no definable battlefields or fronts. The distinction between "civilian" and "military" may disappear. Actions will occur concurrently throughout all participants' depth, including their society as a cultural, not just a physical, entity. Major military facilities, such as airfields, fixed communications sites, and large headquarters will become rarities because of their vulnerability; the same may be true of civilian equivalents, such as seats of government, power plants, and industrial sites (including knowledge as well as manufacturing industries). 125 It is precisely this blurring of peace and war and the demise of traditionally definable battlefields that provides the impetus for the formulation of a new theory of war powers . As evidenced by Part M, supra, the constitutional allocation of war powers, and the Framers' commitment of the war power to two co-equal branches, was not designed to cope with the current international system, one that is characterized by the persistent Page 97 machinations of international terrorist organizations, the rise of multilateral alliances, the emergence of rogue states , and the potentially wide proliferation of easily deployable w eapons of m ass d estruction, nuclear and otherwise. B. The Framers' World vs. Today's World The Framers crafted the Constitution, and the people ratified it, in a time when everyone understood that the state controlled both the raising of armies and their use. Today, however, the threat of terrorism is bringing an end to the era of the nation-state's legal monopoly on violence, and the kind of war that existed before-based on a clear division between government, armed forces, and the people-is on the decline. 126 As states are caught between their decreasing ability to fight each other due to the existence of nuclear weapons and the increasing threat from non-state actors, it is clear that the Westphalian system of nation-states that informed the Framers' allocation of war powers is no longer the order of the day. 127 As seen in Part III, supra, the rise of the modem nation-state occurred as a result of its military effectiveness and ability to defend its citizens. If nation-states such as the United States are unable to adapt to the changing circumstances of fourth-generational warfare-that is, if they are unable to adequately defend against lowintensity conflict conducted by non-state actors-" then clearly [the modem state] does not have a future in front of it .' 128 The challenge in formulating a new theory of war powers for fourthgenerational warfare that remains legally justifiable lies in the difficulty of adapting to changed circumstances while remaining faithful to the constitutional text and the original meaning. 29 To that end, it is crucial to remember that the Framers crafted the Constitution in the context of the Westphalian system of nation-states. The three centuries following the Peace of Westphalia of 1648 witnessed an international system characterized by wars, which, "through the efforts of governments, assumed a more regular, interconnected character."' 130 That period saw the rise of an independent military class and the stabilization of military institutions. Consequently, "warfare became more regular, better organized, and more attuned to the purpose of war-that is, to its political objective."' 1 3' That era is now over . Today, the stability of the long-existing Westphalian international order has been greatly eroded in recent years with the advent of international terrorist organizations, which care nothing for the traditional norms of the laws of war. This new global environment exposes the limitations inherent in the interpretational methods of originalism and textualism and necessitates the adoption of a new method of constitutional interpretation. While one must always be aware of the text of the Constitution and the original understanding of that text, that very awareness identifies the extent to which fourth-generational warfare epitomizes a phenomenon unforeseen by the Framers, a problem the constitutional resolution of which must rely on the good judgment of the present generation. 13 Now, to adapt the constitutional warmarking scheme to the new international order characterized by fourth-generational warfare, one must understand the threat it is being adapted to confront. C. The Jihadist Threat The erosion of the Westphalian and Clausewitzian model of warfare and the blurring of the distinction between the means of warfare and the ends of policy, which is one characteristic of fourthgenerational warfare, apply to al-Qaeda and other adherents of jihadist ideology who view the United States as an enemy. An excellent analysis of jihadist ideology and its implications for the rest of the world are presented by Professor Mary Habeck. 133 Professor Habeck identifies the centrality of the Qur'an, specifically a particular reading of the Qur'an and hadith (traditions about the life of Muhammad), to the jihadist terrorists. 134 The jihadis believe that the scope of the Qur'an is universal, and "that their interpretation of Islam is also intended for the entire world, which must be brought to recognize this fact peacefully if possible and through violence if not."' 135 Along these lines, the jihadis view the United States and her allies as among the greatest enemies of Islam: they believe "that every element of modern Western liberalism is flawed, wrong, and evil" because the basis of liberalism is secularism. 136 The jihadis emphasize the superiority of Islam to all other religions, and they believe that "God does not want differing belief systems to coexist."' 37 For this reason, jihadist groups such as al-Qaeda "recognize that the West will not submit without a fight and believe in fact that the Christians, Jews, and liberals have united against Islam in a war that will end in the complete destruction of the unbelievers.' 138 Thus, the adherents of this jihadist ideology, be it al-Qaeda or other groups, will continue to target the United States until she is destroyed. Their ideology demands it. 139 To effectively combat terrorist groups such as al-Qaeda, it is necessary to understand not only how they think, but also how they operate. Al-Qaeda is a transnational organization capable of simultaneously managing multiple operations all over the world."14 It is both centralized and decentralized: al-Qaeda is centralized in the sense that Osama bin Laden is the unquestioned leader, but it is decentralized in that its operations are carried out locally, by distinct cells."4 AI-Qaeda benefits immensely from this arrangement because it can exercise direct control over high-probability operations, while maintaining a distance from low-probability attacks, only taking the credit for those that succeed. The local terrorist cells benefit by gaining access to al-Qaeda's "worldwide network of assets, people, and expertise."' 42 Post-September 11 events have highlighted al-Qaeda's resilience. Even as the United States and her allies fought back, inflicting heavy casualties on al-Qaeda in Afghanistan and destroying dozens of cells worldwide, "al-Qaeda's networked nature allowed it to absorb the damage and remain a threat." 14 3 This is a far cry from earlier generations of warfare, where the decimation of the enemy's military forces would generally bring an end to the conflict. D. The Need for Rapid Reaction and Expanded Presidential War Power By now it should be clear just how different this conflict against the extremist terrorists is from the type of warfare that occupied the minds of the Framers at the time of the Founding. Rather than maintaining the geographical and political isolation desired by the Framers for the new country, today's United States is an international power targeted by individuals and groups that will not rest until seeing her demise. The Global Page 98 War on Terrorism is not truly a war within the Framers' eighteenth-century conception of the term, and the normal constitutional provisions regulating the division of war powers between Congress and the President do not apply. Instead, this "war" is a struggle for survival and dominance against forces that threaten to destroy the United States and her allies, and the fourth-generational nature of the conflict, highlighted by an indiscernible distinction between wartime and peacetime, necessitates an evolution of America's traditional constitutional warmaking scheme. As first illustrated by the military strategist Colonel John Boyd, constitutional decision-making in the realm of war powers in the fourth generation should consider the implications of the warfare, quick reactions , disrupting the enemy's OODA loop are the keys to victory. "In order to OODA Loop: Observe, Orient, Decide, and Act. 44 In the era of fourth-generational proceeding through the OODA Loop rapidly, and win," Colonel Boyd suggested, "we should operate at a faster tempo or rhythm than our adversaries." 145 In the words of Professor Creveld, "[b]oth organizationally and in terms of the equipment at their disposal, the armed forces of the world will have to adjust themselves to this situation by changing their doctrine, doing away with much of their heavy equipment and becoming more like police."1 46 Unfortunately, the existing constitutional understanding, which diffuses war power between two branches of government, necessarily (by the Framers' design) slows down decision- making. In circumstances where war is undesirable (which is, admittedly, most of the time, especially against other nation-states), the deliberativeness of the existing decision-making process is a positive attribute. In America's current situation, however, in the midst of the conflict with al-Qaeda and other international fatal hindrance to achieving the initiative necessary for victory. As a slow-acting , deliberative body , Congress does not have the ability to adequately deal with fast-emerging situations in fourth-generational warfare. Thus, in order to combat transnational threats such as al-Qaeda, the executive branch must have the ability to operate by taking offensive military action even without congressional authorization, because only the executive branch is capable of the swift decision-making and action necessary to prevail in terrorist organizations, the existing process of constitutional decision-making in warfare may prove a fourth-generational conflicts against fourthgenerational opponents. Page 99 2NC Link Restraints spillover to restrict all presidential war powers Heder 10 (Adam, J.D., magna cum laude, J. Reuben Clark Law School, Brigham Young University, “THE POWER TO END WAR: THE EXTENT AND LIMITS OF CONGRESSIONAL POWER,” St. Mary’s Law Journal Vol. 41 No. 3 // AKONG) This constitutional silence invokes Justice Rehnquist’s oftquoted language from the landmark “political question” case, Goldwater v. Carter . 121 In Goldwater , a group of senators challenged President Carter’s termination, without Senate approval, of the United States ’ Mutual Defense Treaty with Taiwan . 122 A plurality of the Court held, 123 in an opinion authored by Justice Rehnquist, that this was a nonjusticiable political question. 124 He wrote: “In light of the absence of any constitutional provision governing the termination of a treaty, . . . the instant case in my view also ‘must surely be controlled by political standards.’” 125 Notably, Justice Rehnquist relied on the fact that there was no constitutional provision on point. Likewise, there is no constitutional provision on whether Congress has the legislative power to limit, end, or otherwise redefine the scope of a war . Though Justice Powell argues in Goldwater that the Treaty Clause and Article VI of the Constitution “add support to the view that the text of the Constitution does not unquestionably commit the power to terminate treaties to the President alone ,” 126 the same cannot be said about Congress’s legislative authority to terminate or limit a war in a way that goes beyond its explicitly enumerated powers. There are no such similar provisions that would suggest Congress may decline to exercise its appropriation power but nonetheless legally order the President to cease all military operations. Thus, the case for deference to the political branches on this issue is even greater than it was in the Goldwater context. Finally, the Constitution does not imply any additional powers for Congress to end, limit, or redefine a war. The textual and historical evidence suggests the Framers purposefully declined to grant Congress such powers. And as this Article argues, granting Congress this power would be inconsistent with the general war powers structure of the Constitution. Such a reading of the Constitution would unnecessarily empower Congress and tilt the scales heavily in its favor . More over, it would strip the President of his Commander in Chief authority to direct the movement of troops at a time when the Executive’s expertise is needed. 127 And fears that the President will grow too powerful are unfounded, given the reasons noted above. 128 In short, the Constitution does not impliedly afford Congress any authority to prematurely terminate a war above what it explicitly grants. 129 Declaring these issues nonjusticiable political questions would be the most practical means of balancing the textual and historical demands, the structural demands, and the practical demands that complex modern warfare brings . Adjudicating these matters would only lead the courts to engage in impermissible line drawing — lines that would both confus e the issue and add layers to the text of the Constitution in an area where the Framers themselves declined to give such guidance. The perception of legislative restrictions on executive war powers signal weakness and trigger conflict – empirically proven by the War Powers Resolution Turner 5 (Robert, Professor, University of Virginia School of Law, “The War Powers Resolution: An Unnecessary, Unconstitutional Source of "Friendly Fire" in the War Against International Terrorism?” // AKONG) partisan bickering was not lost on radical states in the Middle East, and the Syrian Foreign Minister announced that the United States was "short of breath." [62] The message had also not escaped radical Muslim militia members in Beirut, and in October U.S. intelligence intercepted a message between two terrorist units saying: "If we kill 15 Marines, the rest will leave." Inadvertently, by its partisan debate and repeated pronouncements that further Marine All of this casualties could provoke another debate and a withdrawal of funds for the deployment (such legislation had already been reported out of a key House subcommittee), in their partisan effort to invoke the War Powers Resolution, Congress had essentially placed a bounty on the lives of American forces. The rest is history. Early on the morning of Sunday, October 23, 1983, a Mercedes truck loaded with highly-sophisticated explosives drove into the Marine Corps compound at the Beirut International Airport and exploded. America's terrorist enemies had capitalized on the congressional signals of weakness by murdering 241 sleeping marines, sailors, and soldiers-more Marines than had been lost on any single day since the height of the Vietnam War in 1968 and more American military Page 100 personnel than had been killed in the Gulf War, Grenada, Haiti, Somalia, the Former Yugoslavia, and all other military operations since Vietnam until the September 11, 2001 attack on the Pentagon. Just as Congress had passed the War Powers Resolution in 1973 to misdirect the American people into believing that it bore no responsibility for the tragic defeat in Indochina-when, in reality, by cutting off funds it had snatched defeat from the jaws of victory-after the Beirut bombing Congress demanded that Commandant Kelley bring them the head of a Marine they could blame the latest catastrophe upon. General Kelley, an officer of legendary ability, principle, and courage, who was widely expected to soon be named the first Marine to chair the Joint Chiefs of Staff, refused to sacrifice his subordinates to appease Congress or the press. In taking a principled stand, he understood that he would never become Chairman. Congress deserves the appreciation of all Americans for its bipartisan unity immediately following the September 11 terrorist attacks. But the multiple references to the War Powers Resolution in the statutory authorization approved three days later suggests either that things really have not changed or that the tragedy of October 23, 1983 had been forgotten. The thousands of people murdered in the World Trade Center and the Pentagon on September 11, 2001, would not have died had the terrorists been deterred. Deterrence is a function of perceptions of strength and will. Nothing in the past three decades has done more to undermine perceptions of U.S. will than the behavior of Congress, outlawing efforts to prevent international aggression in places like Angola and Central America and threatening to do so if there were casualties time and again in crisis spots around the globe. Both Democrats and Republicans have ignored the fundamental principle that partisan politics should stop at the water's edge. And nothing has facilitated this process than the War Powers Resolution. Page 101 Mosaic Theory DA Page 102 Notes Here’s the easy explanation of the disad “Mosaic theory” is an idea first implemented in the judicial branch in a D.C. Circuit Court case United States v Maynard Basically it’s that information collected from someone in a public space is not a search as per the 4 th amendment which defines a search as having an expectation of privacy / not being in a public space However, when the government collects a lot of information from you in a public space, which is out of the ordinary / an ordinary person is not expected to assemble that much info from you from public movements, that violates the expectation of privacy because the government can then assemble that information and garner details about that life that cannot be understood from merely occasionally learning things about someone from their public behavior—you can know a lot about someone from GPS tracked movements This court case only ruled in the context of police putting a GPS device on someones car, and the court ruled that this violated 4th amendment because of “mosaic theory” Mosaic theory was implicitly upheld in the supreme court in United States v Jones, but the language was never used, and mosaic theory has not yet been broadly applied to surveillance policy nor to constitutional doctrine as a whole—it has not been widely implemented yet because both United States v Jones and United States v Maynard were solely in the context of GPS tracking of vehicles There has been a debate in law literature about the efficacy of mosaic theory in constitutional doctrine and whether and how it can be implemented so as to be narrowly tailored and not hamstring intelligence, which is proof that it has yet to be so broadly applied The ambiguity of mosaic theory as it currently exists in Supreme Court opinions in the previous cases means there are disadvantages to applying it broadly in that fashion One good part of the debate for the aff and neg might be whether it would be applied narrowly in the context of the aff or whether it would have far reaching implications on constitutional doctrine and investigative agencies The aff can also argue that its key to privacy or that the case would be ruled on exclusively using other bases The Hafetz card is the best impact card, although that leaves the neg vulnerable to link turns like info overload and the other components of the terror debate that the neg may want to stay away from (like the impact perhaps), but it is by far the impact with the best internal links The neg may go for Congress CP solves the info overload turn but avoids invoking mosaic theory which further inhibits counterterrorism (a link differential type argument) Additionally, the drone impact might be paired with some cards from the Drones core that was recently turned out The law enforcement internal link can analytically be used as an internal link to a narcoterror impact when paired with some of the cards in the drug cartels section, but those cards are less stellar Page 103 Lastly, the privacy impact card functions as a link turns case argument against any courts privacy aff because if you win the aff is ruled on the basis of mosaic theory, it says that in the absence of a judicial ruling, congress will establish statutory privacy laws on the use of the technology—the court ruling then deters those statutory restrictions which would otherwise solve the aff while avoiding the terrorism or whatever other external impact you read --Ammar Plumber Page 104 1NC Mosaic theory is undeveloped and not yet broadly applied but has basis in the Supreme Court Walsh, 12 (Courtney, Special Counsel at Parker Poe Adams & Bernstein LLP, LL.M. Master of Laws from Harvard Law School, JD law UFlorida, Spring 2012, St. Thomas Law Review, 24 St. Thomas L. Rev. 169, “CRIMINAL LAW ISSUE: FEATURED CONTRIBUTOR: SURVEILLANCE TECHNOLOGY AND THE LOSS OF SOMETHING A LOT LIKE PRIVACY: AN EXAMINATION OF THE "MOSAIC THEORY" AND THE LIMITS OF THE FOURTH AMENDMENT”, lexis, amp) Litigation in the appellate courts, manifesting itself in a debate over the particular technology of real-time Global Positioning System ("GPS") surveillance, has once again forced the issue as a problem for adjudication. Most federal appellate courts, in the context of recent GPS surveillance cases, have taken a conventional view that privacy, as a matter of Fourth Amendment doctrine, cannot logically expand into the public sphere. n23 The United States Court of Appeals for the District of Columbia, however, struck out in a substantially different direction, attempting to reevaluate settled law in light of new surveillance technologies. In United States v. Maynard, the court, sensing a similar problem as the one posed by Chief Justice Rehnquist, introduced the "mosaic theory," a conceptually novel approach to Fourth Amendment law intended to cultivate a constitutionally anchored sphere of privacy that would attach under conditions of long-term technology-driven surveillance operations. n24 According to the D.C. Circuit, persistent collection of publicly viewable conduct triggers Fourth Amendment scrutiny when such information can be aggregated into a "mosaic" that reveals essentially private insights about a person. n25 In the re-styled case of United States v. Jones, the Supreme Court had the opportunity to address directly the viability of the lower court's "mosaic theory" approach. Despite [*174] the Court's avoidance of the "mosaic theory" in its controlling rationale , a review of the Jones concurring opinions yields one remarkable and irreducible conclusion. The "mosaic theory," regardless of label, is conceptually alive and well as a source of future privacy litigation and policymaking. n26 With a majority of the Court having endorsed the normative assumptions and the analytical framework of the "mosaic theory," n27 the complete canon of this litigation, from Maynard to its subsequent treatment in Jones, merits close discussion in order to gain a sense of how this doctrine might shape future constitutional doctrine and the governance of privacy policy in the context of surveillance technology. Critics of the Maynard "mosaic" have questioned whether Fourth Amendment privacy can, with any doctrinal coherence, expand so as to regulate government surveillance in plainly public areas. n28 Alternatively, even if such a rule can be ascribed to the Fourth Amendment, a question remains as to whether the Fourth Amendment should have to bear this weight or whether other policy responses would be more appropriate. n29 Answering these questions requires a review of the jurisprudential history of privacy and its doctrinal relationship with the Fourth Amendmen INSERT LINK Broader court rulings on mosaic theory hamstring counterterrorism --new public hearings in courts about mosaic theory in different contexts divulge information about the inner workings of intelligence agencies and informs covert terrorism strategies Page 105 --mosaic theory forms the basis of intelligence gathering, and thus broader applications of mosaic theory to restrict its use in the courts makes counterterrorism impossible Hafetz, 14 (Jonathan, Associate Professor of Law at Seton Hall University School of Law, author of Habeas Corpus after 9/11: Confronting America’s New Global Detention System, co-editor of The Guantanamo Lawyers: Inside a Prison Outside the Law, senior attorney at the ACLU and a litigation director at NYU’s Brennan Center for Justice, 1-17-14, Just Security, “Bulk Data Collection and the Mosaic Theory: A More Balanced Approach to Information”, http://justsecurity.org/5758/guest-post-bulk-data-collection-mosaic-theory/, amp) The mosaic theory is a fundamental principle of intelligence gathering. As David Pozen has explained, “[d]isparate pieces of information, though individually of limited or no utility to their possessor, can take on added significance where combined with other items of information.” The theory’s most familiar use has been in the classification of documents and withholding of documents sought under the Freedom of Information Act (FOIA). The government has invoked the theory with increasing frequency since 9/11 in resisting FOIA requests perceived to implicate national security, leading to what Jameel Jaffer has described as “a concentration of information in government hands.” In Center for National Security Studies v. U.S. Department of Justice, for example, the D.C. Circuit applied the mosaic theory to justify the Justice Department’s refusal to provide information about hundreds of individuals swept up and detained following the 9/11 attacks. The Third Circuit similarly relied on the theory in North Jersey Media Group v. Ashcroft in upholding the government’s decision to close to the press and public immigration court hearings involving post-9/11 detainees. The information provided at public hearings, the Third Circuit reasoned, “could allow terrorist organizations to alter their patterns of activity to find the most effective means of evading detection,” while information that was not presented at the hearings could “provide important clues to terrorists, because it could reveal what the investigation has not yet discovered.” Absent prevention, nuclear terror risks extinction Schwartz 15 (Benjamin [Worked at the Departments of State, Defense and Energy]; Right of Boom: The Aftermath of Nuclear Terrorism; The Overlook Press; p. 1-2; kdf) IN AN OTHERWISE CALM AND UNEVENTFUL MORNING, A small nuclear weapon explodes in downtown Washington, DC. The device generates a yield of fifteen kilotons, roughly the same force unleashed by the bomb Little Boy over Hiroshima. The casualty count rises to over a hundred thousand, and the destruction is measured in hundreds of billions of dollars. The blast's electromagnetic pulse burns out electrical components across the metropolitan area. Radiation leaves the center of the city uninhabitable for the first time since it was declared America's capital in 1790, and the scientific community predicts that it will remain so for a decade. The stock market plunges as investors anticipate draconian customs regimes that will choke global trade. Fear of further attacks paralyzes America and much of the Western world. Hours after the explosion, a little unkown terrorist group claims responsibility. It is the first time the president, who was not in Washington at the time of the blast, and his surviving cabinet members, including the director of national intelligence, have heard of the group. After searching intelligence databases, analysts report that the group is linked to three hostile governments, all of which have issued statements condemning the attack and denying involvement. It will take weeks for the remnants of the US intelligence community to assess that one of these three governments is probably lying, but even then the US government won't have irrefutable evidence of complicity. Unlike a ballistic missile or bomb delivered by enemy land-, air-, or seacraft, the origin of Page 106 what analysts will call a "container-based improvised nuclear device" is difficult to determine and impossible to prove. Nuclear forensics will ultimately provide strong evidence that the fissile material used in the device originated from the country under suspicion. Signals intelligence will record celebrations and praise of the attack by midlevel officials in that country's military and intelligence establishment. However, the intelligence reporting taken as a whole will suggest that negligence within that country's weapons industry and at its nuclear complexes is at least as plausible a scenario as a deliberate transfer by government officials to the terrorist group. Yet there is no conclusive reporting that points to either willful negligence or human error. Either way, there is no way to know if the transfer occurred through official policy, the machinations of a venal or ideologically motivated individual, or simple incompetence. There is almost nothing about the origins of the attack that the president of the United States knows for certain. Page 107 Uniqueness Page 108 AT Non-Unique The Jones ruling was narrow, and mosaic theory wasn’t explicitly invoked Pascal, 14 (Brian, research fellow with the University of California Hastings Law School Institute for Innovation Law and a fellow with Stanford Law School’s Center for Internet and Society, American Bar Association, Litigation: The Journal of the Section of Litigation, Vol. 40 No. 3, “How Technology Broke Privacy”, http://www.americanbar.org/publications/litigation_journal/201314/spring/how_technology_broke_privacy.html, amp) Though the mosaic theory is an attractive argument, it was not the basis for the majority opinion (though Justice Sotomayor’s concurrence relied on an effectively identical justification). By declining to explicitly accept the mosaic theory (or a similarly flexible approach), the Court ensured that its holding in Jones would be so narrow as to be nearly obsolete the day it was handed down . Staunch opposition and criticism of mosaic theory remains Gatewood, 14 (Jace, Georgetown University, A.B., 1983; Georgetown University Law Center, J.D., 1990, Associate Professor of Law at Atlanta's John Marshall Law School, Nebraska Law Review, 2014, 92 Neb. L. Rev. 504, “ARTICLE: District of Columbia Jones and the Mosaic Theory - In Search of a Public Right of Privacy: The Equilibrium Effect of the Mosaic Theory”, lexis, amp) C. Issues Regarding the Implementation of the Mosaic Theory The introduction of the mosaic theory into Fourth Amendment jurisprudence has met with mixed reaction. n180 Those that support the newly formulated theory are staunch supporters, n181 while those that oppose the new theory are adamant in their opposition. n182 Whatever side one happens to fall on, the criticism of the mosaic theory is generally the same . n183 The first issue raised by the adoption of the mosaic theory into Fourth Amendment jurisprudence is how to determine the scope of the mosaic necessary to create a Fourth Amendment violation. n184 In other words, how much is too much? The Maynard decision did not express a bright-line rule regarding how much surveillance is required to create a mosaic sufficient to violate the Fourth Amendment. n185 In addition, it has been proffered that the pro-mosaic opinions authored in Maynard (Judge Ginsburg) and Jones (Justices Alito and [*529] Sotomayor) each suggest a different answer. n186 This ambiguity makes it difficult to apply the mosaic theory. n187 Mosaic theory judicial use isn’t yet established Gatewood, 14 (Jace, Georgetown University, A.B., 1983; Georgetown University Law Center, J.D., 1990, Associate Professor of Law at Atlanta's John Marshall Law School, Nebraska Law Review, 2014, 92 Neb. L. Rev. 504, “ARTICLE: Page 109 District of Columbia Jones and the Mosaic Theory - In Search of a Public Right of Privacy: The Equilibrium Effect of the Mosaic Theory”, lexis, amp) The Maynard decision marked a dramatic shift in Fourth Amendment jurisprudence and, at the time of its decision in 2010, was contrary to holdings of several other circuit courts. n19 When the Supreme Court reviewed the Maynard decision in 2012 in the retitled action United States v. Jones, n20 even though the Supreme Court did not resolve the case using the mosaic theory, Justice Sotomayor's concurring opinion and Justice Alito's concurring opinion, which was signed or joined by three other justices, endorsed some form of the mosaic theory. n21 In the aftermath of Maynard, many articles were written on the mosaic theory and its viability for Fourth Amendment application. n22 Some of the articles argued against the wisdom of the mosaic theory and its use in Fourth Amendment jurisprudence because of its impracticability. n23 According to those commentators, implementing the mosaic theory [*508] would be difficult if not impossible to administer. n24 Without a doubt, the mosaic theory raises several challenging issues for the future of Fourth Amendment jurisprudence. Notwithstanding, however, and despite the wide-ranging criticism, the application of the mosaic theory may help establish and restore a balance between our public and private lives. Mosaic theory faces opposition and is only narrowly applied now Arcila, 12 (Fabio Jr, Professor of Law, Touro Law Center, participated pro bono in United States v. Jones by consulting with Jones's Supreme Court counsel and authoring a historical amicus brief supporting Jones, North Carolina Law Review, December 2012, 91 N.C.L. Rev. 1, “ARTICLE: GPS TRACKING OUT OF FOURTH AMENDMENT DEAD ENDS: UNITED STATES V. JONES AND THE KATZ CONUNDRUM*”, lexis, amp) The D.C. Circuit held that law enforcement engaged in an unconstitutional search under the Fourth Amendment when it [*12] conducted warrantless GPS tracking of Jones's vehicle for twenty-eight days. n25 Controversially, the D.C. Circuit latched onto the prolonged nature of the surveillance to invoke the "mosaic theory." n26 In a search and seizure context, mosaic theory posits that privacy interests, such as those protected under the Fourth Amendment, should be protected in a manner that guards against collections of small bits of information that individually may not be particularly revealing but when aggregated may reveal a great deal. n27 By doing so, the court avoided the precedent of United States v. Knotts, n28 a beeper surveillance case that strongly suggested that Jones enjoyed no privacy protections in his public movements because "[a] person traveling in an automobile on public thoroughfares has no reasonable expectation of privacy in his movements from one place to another." n29 The D.C. Circuit explained: Here the police used the GPS device not to track Jones's "movements from one place to another," but rather to track Jones's movements 24 hours a day for 28 days as he moved among scores of places, thereby discovering the totality and pattern of his movements from place to place to place. ... . ... We hold the whole of a person's movements over the course of a month is not actually exposed to the public because the likelihood a stranger would observe all those movements is not just remote, it is essentially nil... . [*13] ... . Page 110 The whole of one's movements over the course of a month is not constructively exposed to the public because, like a rap sheet, that whole reveals far more than the individual movements it comprises. The difference is not one of degree but of kind, for no single journey reveals the habits and patterns that mark the distinction between a day in the life and a way of life, nor the departure from a routine that, like the dog that did not bark in the Sherlock Holmes story, may reveal even more. n30 This mosaic approach is controversial because it suggests that some limited degree of warrantless GPS tracking would be constitutional under the Fourth Amendment, but too much is not. Where the dividing line is located, and how it is identified, remains a mystery. The United States sought en banc review, which the D.C. Circuit denied over a vigorous dissent that gamely challenged the mosaic theory. The panel opinion seems to recognize that Jones had no reasonable expectation of privacy in any particular datum revealed by the GPS-augmented surveillance, but somehow acquired one through "the totality of Jones's movements over the course of a month." In the view of the panel, this is true "because that whole reveals more ... than does the sum of its parts." While this may be true, it is not evident how it affects the reasonable expectation of privacy by Jones. The reasonable expectation of privacy as to a person's movements on the highway is ... zero. The sum of an infinite number of zero-value parts is also zero. n31 Unsurprisingly, the United States targeted the mosaic theory in seeking a reversal from the Supreme Court, arguing that it leaves law enforcement officers with too much uncertainty regarding allowable warrantless GPS tracking. n32 Page 111 AT Uniqueness overwhelms Mosaic theory isn’t well defined or developed now, but the Court is ready to latch on—magnifies the link Talai, 14 (Andrew, J.D., University of California, Berkeley, School of Law, 2014; B.A., Anthropology, University of California, Los Angeles, California Law Review, June 2014, 102 Calif. L. Rev. 729, “COMMENT: Drones and Jones: The Fourth Amendment and Police Discretion in the Digital Age”, lexis, amp) While Justice Sotomayor's concurrence also treated the mosaic theory as a special application of the Katz test - assessing society's expectations in the digital age - it was different in two respects. First, Justice Sotomayor embraced a democratic rationale (that is, abuse of discretion and chilling effects) for the Fourth Amendment. n215 Second, she recognized that democratic concerns arise "in cases involving even short-term monitoring." n216 Ultimately, her solution was to grapple with the public thoroughfare doctrine and third-party doctrines, n217 finding that in their present state, these the exact contours of the mosaic theory are far from clear , the Jones plurality "suggests that a majority of the Court is ready to embrace some form of the D.C. Circuit's mosaic theory ." n219 are "ill suited to the digital age." n218 While Momentum is building in support of mosaic theory, but some opposition and controversy remains—proves the link Arcila, 12 (Fabio Jr, Professor of Law, Touro Law Center, participated pro bono in United States v. Jones by consulting with Jones's Supreme Court counsel and authoring a historical amicus brief supporting Jones, North Carolina Law Review, December 2012, 91 N.C.L. Rev. 1, “ARTICLE: GPS TRACKING OUT OF FOURTH AMENDMENT DEAD ENDS: UNITED STATES V. JONES AND THE KATZ CONUNDRUM*”, lexis, amp) The positions that Justices Alito and Sotomayor took are also important for what they imply about the Supreme Court's views on mosaic theory. Neither of them use the term, but they implicitly indicate varying degrees of willingness to accept mosaic theory as at least part of Fourth Amendment surveillance law. Justice Alito's thoughts on mosaic theory are implicit in the new temporal distinction he applies when determining if an objective expectation of privacy exists. It appears that, in his view, what makes brief GPS monitoring not a "search" under the Fourth Amendment is that it reveals a smaller and thus acceptable amount of information, such that no objective expectation of privacy is infringed. n293 By contrast, Justice Alito suggests that what makes prolonged GPS monitoring a Fourth Amendment "search" is that it will reveal more information, such that an objective expectation of privacy is infringed. n294 If this is correct, Justice Alito is, even if unconsciously, [*63] endorsing a version of mosaic theory, as he is drawing Fourth Amendment distinctions based upon the amount of information collected, rather than through some other measure such as the type of search activity at issue. Importantly, at least three other Justices (Justices Ginsberg, Breyer, and Kagan, who joined Justice Alito's concurrence) presumably agree with this implicit embrace of mosaic theory and its incorporation into Fourth Amendment law, as none of them wrote separately to indicate any qualms about or disagreements with it. Page 112 In her separate concurrence, Justice Sotomayor even more clearly endorsed the use of mosaic theory in the Fourth Amendment. Citing to and even parenthetically quoting from that portion of the New York Court of Appeals's Weaver decision that relied upon mosaic theory, n295 she pointed to the GPS-enabled capability of developing a "precise, comprehensive record of a person's public movements that reflects a wealth of detail about her familial, political, professional, religious, and sexual associations." n296 She went on to specify that she would ask "whether people reasonably expect that their movements will be recorded and aggregated in a manner that enables the Government to ascertain, more or less at will, their political and religious beliefs, sexual habits, and so on." n297 These statements demonstrate that, more than any other Justice, she would consider the amount and extent of information obtained through surveillance, and thus looks favorably upon mosaic theory in the context of Fourth Amendment surveillance law. Justice Scalia is no fan of the mosaic theory, and by extension it appears that the three Justices who joined him (Chief Justice Roberts and Justices Kennedy and Thomas) are not either. Justice Scalia derided the mosaic theory implications of Justice Alito's temporal distinction, pointing to the difficulty of the line-drawing that inevitably follows. n298 Nonetheless, the support evident in Justice Alito's and Justice Sotomayor's concurring opinions for some iteration of the mosaic theory may have significant implications. They have added their voices to Weaver's embrace of mosaic theory in a Fourth Amendment [*64] context. n299 After Jones, momentum may be building on this point, as the South Dakota Supreme Court has added its support as well. n300 Mosaic theory judicial applications are not yet completely solidified Walsh, 12 (Courtney, Special Counsel at Parker Poe Adams & Bernstein LLP, LL.M. Master of Laws from Harvard Law School, JD law UFlorida, Spring 2012, St. Thomas Law Review, 24 St. Thomas L. Rev. 169, “CRIMINAL LAW ISSUE: FEATURED CONTRIBUTOR: SURVEILLANCE TECHNOLOGY AND THE LOSS OF SOMETHING A LOT LIKE PRIVACY: AN EXAMINATION OF THE "MOSAIC THEORY" AND THE LIMITS OF THE FOURTH AMENDMENT”, lexis, amp) [*215] Having isolated the issue reserved in Knotts, Judge Ginsburg determined that Knotts merely stood for the proposition that individuals traveling in an automobile on a public thoroughfare have no reasonable expectation of privacy in their "movements from one place to another, not that such a person has no reasonable expectation of privacy in his movements whatsoever, world without end ... ." n286 Establishing this narrowed view of Knotts, the court contrasted the facts in Maynard, concluding that the issue of persistent surveillance raised in this case is the precise problem contemplated and reserved by the Supreme Court in Knotts. n287 The importance of this conclusion cannot be underestimated, because having shed the controlling burden of Knotts, the Maynard court could permit itself to engage in the fuller normative discussion of the Fourth Amendment's boundaries that leads to the formulation of the "mosaic theory." Mosaic theory judicial use isn’t yet established Gatewood, 14 (Jace, Georgetown University, A.B., 1983; Georgetown University Law Center, J.D., 1990, Associate Professor of Law at Atlanta's John Marshall Law School, Nebraska Law Review, 2014, 92 Neb. L. Rev. 504, “ARTICLE: Page 113 District of Columbia Jones and the Mosaic Theory - In Search of a Public Right of Privacy: The Equilibrium Effect of the Mosaic Theory”, lexis, amp) The Maynard decision marked a dramatic shift in Fourth Amendment jurisprudence and, at the time of its decision in 2010, was contrary to holdings of several other circuit courts. n19 When the Supreme Court reviewed the Maynard decision in 2012 in the retitled action United States v. Jones, n20 even though the Supreme Court did not resolve the case using the mosaic theory, Justice Sotomayor's concurring opinion and Justice Alito's concurring opinion, which was signed or joined by three other justices, endorsed some form of the mosaic theory. n21 In the aftermath of Maynard, many articles were written on the mosaic theory and its viability for Fourth Amendment application. n22 Some of the articles argued against the wisdom of the mosaic theory and its use in Fourth Amendment jurisprudence because of its impracticability. n23 According to those commentators, implementing the mosaic theory [*508] would be difficult if not impossible to administer. n24 Without a doubt, the mosaic theory raises several challenging issues for the future of Fourth Amendment jurisprudence. Notwithstanding, however, and despite the wide-ranging criticism, the application of the mosaic theory may help establish and restore a balance between our public and private lives. Mosaic theory faces opposition and is only narrowly applied now Arcila, 12 (Fabio Jr, Professor of Law, Touro Law Center, participated pro bono in United States v. Jones by consulting with Jones's Supreme Court counsel and authoring a historical amicus brief supporting Jones, North Carolina Law Review, December 2012, 91 N.C.L. Rev. 1, “ARTICLE: GPS TRACKING OUT OF FOURTH AMENDMENT DEAD ENDS: UNITED STATES V. JONES AND THE KATZ CONUNDRUM*”, lexis, amp) The D.C. Circuit held that law enforcement engaged in an unconstitutional search under the Fourth Amendment when it [*12] conducted warrantless GPS tracking of Jones's vehicle for twenty-eight days. n25 Controversially, the D.C. Circuit latched onto the prolonged nature of the surveillance to invoke the "mosaic theory." n26 In a search and seizure context, mosaic theory posits that privacy interests, such as those protected under the Fourth Amendment, should be protected in a manner that guards against collections of small bits of information that individually may not be particularly revealing but when aggregated may reveal a great deal. n27 By doing so, the court avoided the precedent of United States v. Knotts, n28 a beeper surveillance case that strongly suggested that Jones enjoyed no privacy protections in his public movements because "[a] person traveling in an automobile on public thoroughfares has no reasonable expectation of privacy in his movements from one place to another." n29 The D.C. Circuit explained: Here the police used the GPS device not to track Jones's "movements from one place to another," but rather to track Jones's movements 24 hours a day for 28 days as he moved among scores of places, thereby discovering the totality and pattern of his movements from place to place to place. ... . ... We hold the whole of a person's movements over the course of a month is not actually exposed to the public because the likelihood a stranger would observe all those movements is not just remote, it is essentially nil... . [*13] ... . Page 114 The whole of one's movements over the course of a month is not constructively exposed to the public because, like a rap sheet, that whole reveals far more than the individual movements it comprises. The difference is not one of degree but of kind, for no single journey reveals the habits and patterns that mark the distinction between a day in the life and a way of life, nor the departure from a routine that, like the dog that did not bark in the Sherlock Holmes story, may reveal even more. n30 This mosaic approach is controversial because it suggests that some limited degree of warrantless GPS tracking would be constitutional under the Fourth Amendment, but too much is not. Where the dividing line is located, and how it is identified, remains a mystery. The United States sought en banc review, which the D.C. Circuit denied over a vigorous dissent that gamely challenged the mosaic theory. The panel opinion seems to recognize that Jones had no reasonable expectation of privacy in any particular datum revealed by the GPS-augmented surveillance, but somehow acquired one through "the totality of Jones's movements over the course of a month." In the view of the panel, this is true "because that whole reveals more ... than does the sum of its parts." While this may be true, it is not evident how it affects the reasonable expectation of privacy by Jones. The reasonable expectation of privacy as to a person's movements on the highway is ... zero. The sum of an infinite number of zero-value parts is also zero. n31 Unsurprisingly, the United States targeted the mosaic theory in seeking a reversal from the Supreme Court, arguing that it leaves law enforcement officers with too much uncertainty regarding allowable warrantless GPS tracking. n32 Page 115 Links Page 116 Drones --- 1NC Drone surveillance strengthens the currently narrow mosaic doctrine Talai, 14 (Andrew, J.D., University of California, Berkeley, School of Law, 2014; B.A., Anthropology, University of California, Los Angeles, California Law Review, June 2014, 102 Calif. L. Rev. 729, “COMMENT: Drones and Jones: The Fourth Amendment and Police Discretion in the Digital Age”, lexis, amp) 3. Mosaic Theory and Drones Under the mosaic theory, only long-term surveillance in public would be considered a search. In fact, the mosaic theory has only been applied successfully in two cases : People v. Weaver and United States v. Maynard. n242 Both cases involved affixing a physical GPS device to a vehicle. The mosaic theory has only been applied to GPS surveillance cases because it relies on a [*766] substantial period of continuous surveillance or data aggregation in public movements. How would the mosaic theory apply to drone surveillance? n243 This analysis uses the D.C. Circuit's approach to the mosaic theory, as it is the clearest exposition so far. In Maynard, the court held that twenty-eight days of continuous GPS surveillance of an individual on public thoroughfares aggregated to a search, but a single "frame" of surveillance would not. n244 The rationale was that the whole is something different than the sum of its parts - long-term surveillance contravenes society's expectation of privacy in the whole of our movements. n245 However, the court did not provide a framework for drawing the line between short-term and long-term surveillance. In a Justice Stewart-like move, n246 the court left that question for another day. n247 Applying these rules to the drone problem depends on the duration of the surveillance: "snapshots" would not amount to a search, while "pervasive" surveillance would. In Brossart, the Predator drone was only aloft for a short period of time, nowhere near twenty-eight days. Under the D.C. Circuit's logic, there would be no problem with this mosaic theory would find drone surveillance a search where a system like ARGUS - designed to capture a 24/7 persistent feed aggregated the sum of an individual's movements . kind of surveillance. Rather, the Page 117 Drones --- 2NC Mosaic theory will be applied --- it’s the only way to solve the aff Talai, 14 (Andrew, J.D., University of California, Berkeley, School of Law, 2014; B.A., Anthropology, University of California, Los Angeles, California Law Review, June 2014, 102 Calif. L. Rev. 729, “COMMENT: Drones and Jones: The Fourth Amendment and Police Discretion in the Digital Age”, lexis, amp) When applying the Jones majority's rationale to the facts of Brossart, this result makes sense. The trespass test is narrowly tailored to a physical trespass on private property - this monist inquiry does not grapple with the complexities of drone surveillance. However pervasive, the extent of surveillance does not matter. The public thoroughfare distinction is also irrelevant. In fact, it does not even matter if a drone or a manned aircraft gathered the surveillance. Practically speaking, there is no claim for trespass against aircrafts flying tens of thousands of feet above private property. n221 Further, those same aircraft [*762] make no actual physical occupation of private property: as such, there would be no search under the Jones majority's rule. n222 grapple with drone surveillance . Thus, only the Katz test and mosaic theory can Page 118 Police Surveillance --- 1NC Restricting police surveillance ensures application of mosaic theory Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) 2. Rejection of the Public Disclosure and Third Party Doctrines The most troubling part of adopting the mosaic theory is that it requires the abandonment of, or dramatic alterations to, the Doctrines. The basic problem is the inherent conflict between the first and second models of reasonable expectation. While the Doctrines embrace a per se rule focusing solely on disclosure and why this vitiates privacy, the mosaic theory rests on society's opinion and what it deems reasonable. n223 Consider the Public Disclosure Doctrine. The fact that public movements are not protected under the Fourth Amendment is critical to law enforcement investigations. n224 Visual warrantless surveillance remains a central part of police surveillance. n225 It is not clear to what extent these practices will remain constitutional with the introduction of the mosaic theory. For instance, it is common for officers to track vehicles and aggregate information from various sources over a period of time. n226 As Gray and Citron point out, the "mosaic theory puts these practices and the line of doctrine endorsing them in obvious jeopardy, particularly when officers are too successful and their investigations produce too much information." n227 This danger is compounded by the fact that law enforcement may use a combination of visual and technology-based surveillance (a la Knotts) when investigating a suspect. "How, after all," ask Gray and Citron, "are we to distinguish "between the supposed invasion of aggregation of data between GPS-augmented surveillance and a purely visual surveillance of substantial length'?" n228 It won't do here to simply say that a specific duration of technology-dependent surveillance violates the expectation of privacy. The problem is that the Public Disclosure Doctrine treats all public movements the same, regardless of how much information is disclosed or how long it is observed. n229 To carve out exceptions based on what society thinks is unreasonable leaves vulnerable investigative techniques that are essential to effective law enforcement. The Third Party Doctrine would also be on shaky ground. Here, too, the [*1843] mosaic theory would upset the voluntary disclosure principle that stands at the heart of this doctrine. n230 Shifting the focus to what society or an individual deems reasonable (the first model of reasonable expectation of privacy) would surely frustrate the use of undercover informants or other surreptitious data collection techniques that do not require a warrant. Imagine a scenario where an informant is deep undercover for a significant period of time gaining the trust of a suspect. Or imagine an informant who dupes a suspect into allowing her into her home and disclosing private and incriminating information. Or perhaps the government simply acquires a wealth of financial records from a suspect's bank. Currently, all of these types of law enforcement tools do not trigger Fourth Amendment protection because the individual voluntarily discloses the information to another person or entity. n231 However, under the mosaic theory, none of these tactics are secure . n232 Societal expectations may find that these methods, too, impinge on Fourth Amendment rights as they involve unreasonable duplicity and Page 119 reveal private information. Police would thus find themselves in the new position of having to secure a warrant based on probable cause before engaging in these practices. For some, this conclusion may be welcomed, particularly in today's technological world where disclosures to various entities and individuals have become ubiquitous. n233 Justice Sotomayor, in fact, raises this possibility in her concurrence. n234 This Article does not take such a drastic approach, nor would such a course be desirable. Any such rejection would come at the cost of jettisoning or severely curtailing essential law enforcement investigative [*1844] techniques that have historically not been subject to warrant and probable cause requirements. n235 Page 120 Private Communications --- 1NC Private communications surveillance would implicate and support the use of mosaic theory Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) Enter the mosaic theory with a focus on intimate associations . n51 While individual social networking communications would not be protected because of the Third Party Doctrine, in the aggregate, these communications are more than just a bundle of transmissions - together they are constitutive of an intimate relationship. If courts care about the government not interfering in these relationships in the face-to-face context, via direct application of intimate associational rights, they should similarly care about these relationships on the Internet when assessing Fourth Amendment protection. n52 This means finding that the underlying social networking communication passes the Fourth Amendment reasonable expectation of privacy test, because it is part-and-parcel of an intimate relationship. n53 Page 121 Social Networking --- 1NC Social networking surveillance would implicate and support the use of mosaic theory Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) Enter the mosaic theory with a focus on intimate associations . n51 While individual social networking communications would not be protected because of the Third Party Doctrine, in the aggregate, these communications are more than just a bundle of transmissions - together they are constitutive of an intimate relationship. If courts care about the government not interfering in these relationships in the face-to-face context, via direct application of intimate associational rights, they should similarly care about these relationships on the Internet when assessing Fourth Amendment protection. n52 This means finding that the underlying social networking communication passes the Fourth Amendment reasonable expectation of privacy test, because it is part-and-parcel of an intimate relationship. n53 Page 122 Social Networking --- 2NC It has to be applied Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) The Fourth Amendment and technology have always had a volatile relationship. As technology advances, courts and scholars have struggled to update privacy protection. n1 The Supreme Court introduced the mosaic theory as one way to combat extended electronic surveillance of a suspect's movements, though the consensus appears to be that it is not sustainable in the larger Fourth Amendment framework. n2 This Article deploys the mosaic theory in the Internet context - particularly social networking sites - where it provides an effective way to protect communications that would otherwise not pass the reasonable expectation of privacy test under the Fourth Amendment. Page 123 TPD --- 1NC Third Party Doctrine surveillance would implicate and support the use of mosaic theory Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) 2. Rejection of the Public Disclosure and Third Party Doctrines The most troubling part of adopting the mosaic theory is that it requires the abandonment of, or dramatic alterations to, the Doctrines. The basic problem is the inherent conflict between the first and second models of reasonable expectation. While the Doctrines embrace a per se rule focusing solely on disclosure and why this vitiates privacy, the mosaic theory rests on society's opinion and what it deems reasonable. n223 Consider the Public Disclosure Doctrine. The fact that public movements are not protected under the Fourth Amendment is critical to law enforcement investigations. n224 Visual warrantless surveillance remains a central part of police surveillance. n225 It is not clear to what extent these practices will remain constitutional with the introduction of the mosaic theory. For instance, it is common for officers to track vehicles and aggregate information from various sources over a period of time. n226 As Gray and Citron point out, the "mosaic theory puts these practices and the line of doctrine endorsing them in obvious jeopardy, particularly when officers are too successful and their investigations produce too much information." n227 This danger is compounded by the fact that law enforcement may use a combination of visual and technology-based surveillance (a la Knotts) when investigating a suspect. "How, after all," ask Gray and Citron, "are we to distinguish "between the supposed invasion of aggregation of data between GPS-augmented surveillance and a purely visual surveillance of substantial length'?" n228 It won't do here to simply say that a specific duration of technology-dependent surveillance violates the expectation of privacy. The problem is that the Public Disclosure Doctrine treats all public movements the same, regardless of how much information is disclosed or how long it is observed. n229 To carve out exceptions based on what society thinks is unreasonable leaves vulnerable investigative techniques that are essential to effective law enforcement. The Third Party Doctrine would also be on shaky ground. Here, too, the [*1843] mosaic theory would upset the voluntary disclosure principle that stands at the heart of this doctrine. n230 Shifting the focus to what society or an individual deems reasonable (the first model of reasonable expectation of privacy) would surely frustrate the use of undercover informants or other surreptitious data collection techniques that do not require a warrant. Imagine a scenario where an informant is deep undercover for a significant period of time gaining the trust of a suspect. Or imagine an informant who dupes a suspect into allowing her into her home and disclosing private and incriminating information. Or perhaps the government simply acquires a wealth of financial records from a suspect's bank. Currently, all of these types of law enforcement tools do not trigger Fourth Amendment protection because the individual voluntarily discloses the information to another person or entity. n231 However, under the mosaic Page 124 theory, none of these tactics are secure . n232 Societal expectations may find that these methods, too, impinge on Fourth Amendment rights as they involve unreasonable duplicity and reveal private information. Police would thus find themselves in the new position of having to secure a warrant based on probable cause before engaging in these practices. For some, this conclusion may be welcomed, particularly in today's technological world where disclosures to various entities and individuals have become ubiquitous. n233 Justice Sotomayor, in fact, raises this possibility in her concurrence. n234 This Article does not take such a drastic approach, nor would such a course be desirable. Any such rejection would come at the cost of jettisoning or severely curtailing essential law enforcement investigative [*1844] techniques that have historically not been subject to warrant and probable cause requirements. n235 Page 125 TPD --- 2NC Social networking use of mosaic theory is implicated by analysis of the third party doctrine Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) Enter the mosaic theory with a focus on intimate associations . n51 While individual social networking communications would not be protected because of the Third Party Doctrine, in the aggregate, these communications are more than just a bundle of transmissions - together they are constitutive of an intimate relationship. If courts care about the government not interfering in these relationships in the face-to-face context, via direct application of intimate associational rights, they should similarly care about these relationships on the Internet when assessing Fourth Amendment protection. n52 This means finding that the underlying social networking communication passes the Fourth Amendment reasonable expectation of privacy test, because it is part-and-parcel of an intimate relationship. n53 Page 126 Internal links Page 127 AT No Spillover Stare decisis means endorsing mosaic theory has broad implications Gray and Citron, 13 (David--Associate Professor, University of Maryland Francis King Carey School of Law, Danielle Keats--Lois K. Macht Research Professor of Law, University of Maryland Francis King Carey School of Law, Affiliate Scholar, Stanford Center on Internet and Society, Affiliate Fellow, Yale Information Society Project, North Carolina Journal of Law & Technology, Spring 2013, 14 N.C. J.L. & Tech. 381, “ARTICLE: A Shattered Looking Glass: The Pitfalls and Potential of the Mosaic Theory of Fourth Amendment Privacy”, lexis, amp) The mosaic theory endorsed by the U.S. Court of Appeals for the District of Columbia and a majority of concurring Justices in United States v. Jones proposes nothing short of a revolution in Fourth Amendment law. Never before has the Court suggested that we can have reasonable expectations of privacy in certain quantities or ag-gregations of information even if we have no such expectations in the constituent parts. n111 As with any doctrinal revolution, the mosaic theory appears to require some blood on the floor. Specifically, adopting a mosaic approach to the Fourth Amendment may require abandoning or dramatically altering two important lines of Fourth Amendment law: the public observation doctrine n112 and the third party doctrine. n113 To the extent that this is so, commitments to these doctrines, or simply to stare decisis, counsel caution before adopting a mosaic theory of Fourth Amendment privacy. Page 128 Impacts Page 129 Court Failure Broadening mosaic theory rulings causes court failure and delegitimation Kerr, 12 (Orin, Fred C. Stevenson Research Professor, George Washington University Law School, December 2012, Michigan Law Review, 111 Mich. L. Rev. 311, “ARTICLE: THE MOSAIC THEORY OF THE FOURTH AMENDMENT”, lexis, amp) The first difficulty with the mosaic theory is the most obvious: its implementation raises so many difficult questions that it will prove exceedingly hard to administer effectively. Because the mosaic theory departs dramatically from existing doctrine, implementing it would require the creation of a new set of Fourth Amendment rules-in effect, a mosaic parallel to the sequential precedents that exist today. The problem is not only the number of questions but also their difficulty. Many of the questions raised in Part III of this Article are genuine puzzles that Fourth Amendment text, principles, and history cannot readily answer. Judges should be reluctant to open the legal equivalent of Pandora's Box. Murky standards are not unknown in Fourth Amendment law, of course. But the murkiness of the mosaic theory is unprecedented . I find it particularly telling that not even the proponents of the mosaic theory have proposed answers for how the theory should apply . For example, in one recent article, a group of scholars who endorsed the mosaic approach dismissed the conceptual difficulties of its implementation on the ground that answering such puzzles "is why we have judges."199 A pro-mosaic amicus brief in Jones signed by several prominent legal academics was similarly nonresponsive. 200 The brief brushed off the difficulties with implementing the mosaic theory by stating that judges encounter vague standards elsewhere in Fourth Amendment law and they can implement the mosaic theory by "consider[ing] the same criteria applied to other surveillance situations.120 ' I appreciate such confidence in judicial abilities. But surely there is a stark difference between applying vague standards and implementing a theory so mysterious that Fourth Amendment experts decline to express an opinion on how to apply it. Judges are smart people, but they are not like Moses bringing the tablets down from Mount Sinai. If the questions raised by the mosaic theory can be answered, proponents of the theory should answer them. Expressions of confidence that answers can be found do not substitute for the answers themselves. 20 2 The challenge of answering the questions raised by the mosaic theory has particular force because the theory attempts to regulate use of changing technologies. Law enforcement implementation of new technologies can occur very quickly, while judicial resolution of difficult constitutional questions typically occurs at a more snail-like pace. As a result, the constantly evolving nature of surveillance practices can lead new questions to arise faster than courts might settle them. Old practices would likely be obsolete by the time the courts resolved how to address them, and the newest surveillance practices would arrive and their legality would be unknown. Like Lucy and Ethel trying to package candy on the ever-faster conveyor belt,203 the mosaic theory could place judges in the uncomfortable position of trying to settle a wide range of novel questions for technologies that are changing faster than the courts can resolve how to regulate them. Consider the changes in location-identifying technologies in the last three decades. Thirty years ago, the latest in police location-tracking technologies was the primitive radio beeper seen in Knotts. But radio beepers are obsolete. Today the police have new tools at their disposal that were unknown in the Knotts era, ranging from GPS devices to cell-site records to license plate cameras. The rapid pace of technological change creates major difficulties for Page 130 courts trying to apply the mosaic theory: if the technological facts of the mosaic change quickly over time, any effort to answer the many difficult questions raised by the mosaic theory will become quickly outdated. Courts eventually may devise answers to the many questions discussed in Part III. But by the time they do, the technology is likely to be obsolete. Court broadened rejection of mosaic theory delegitimizes the court Kerr, 12 (Orin, Fred C. Stevenson Research Professor, George Washington University Law School, December 2012, Michigan Law Review, 111 Mich. L. Rev. 311, “ARTICLE: THE MOSAIC THEORY OF THE FOURTH AMENDMENT”, lexis, amp) Third, as a normative matter, courts should reject the mosaic theory. The mosaic approach is animated by legitimate concerns: it aims to maintain the balance of Fourth Amendment protection as technology changes, a method I have elsewhere called "equilibrium-adjustment." n16 But it aims to achieve this reason-able goal in a peculiar way. By rejecting the building block of the sequential approach, the mosaic theory would be very difficult to administer coherently. Even if courts could develop answers to the many questions the theory raises, doing so would take many years - by which time the technologies regulated by the theory would become obsolete. The mosaic theory would also deter enactment of statutory privacy regulations and force judges to consider questions that they are poorly equipped to answer. If courts must broaden Fourth Amendment rules in response to new technologies, the better approach is to rule that certain steps are always searches. The model should be the Supreme Court's famous decision in Katz v. United States, n17 not the concurring opinions in Jones. Page 131 Drones Mosaic theory inhibits drone use Talai, 14 (Andrew, J.D., University of California, Berkeley, School of Law, 2014; B.A., Anthropology, University of California, Los Angeles, California Law Review, June 2014, 102 Calif. L. Rev. 729, “COMMENT: Drones and Jones: The Fourth Amendment and Police Discretion in the Digital Age”, lexis, amp) How would the mosaic theory apply to drone surveillance? n243 This analysis uses the D.C. Circuit's approach to the mosaic theory, as it is the clearest exposition so far. In Maynard, the court held that twenty-eight days of continuous GPS surveillance of an individual on public thoroughfares aggregated to a search, but a single "frame" of surveillance would not. n244 The rationale was that the whole is something different than the sum of its parts - long-term surveillance contravenes society's expectation of privacy in the whole of our movements. n245 However, the court did not provide a framework for drawing the line between short-term and long-term surveillance. In a Justice Stewart-like move, n246 the court left that question for another day. n247 Applying these rules to the drone problem depends on the duration of the surveillance: "snapshots" would not amount to a search, while "pervasive" surveillance would. In Brossart, the Predator drone was only aloft for a short period of time, nowhere near twenty-eight days. Under the D.C. Circuit's logic, there would be no problem with this mosaic theory would find drone surveillance a search where a system like ARGUS - designed to capture a 24/7 persistent feed aggregated the sum of an individual's movements . kind of surveillance. Rather, the Page 132 Health data Mosaic theory inhibits governmental collection of health data Gray, et al, 13 (David--Associate Professor, University of Maryland Francis King Carey School of Law, Danielle Keats Citron--Lois K. Macht Research Professor of Law, University of Maryland Francis King Carey School of Law, Affiliate Scholar, Stanford Center on Internet and Society, Affiliate Fellow, Yale Information Society Project, Liz Clark Rinehart—Professor University of Maryland Francis King Carey School of Law, Summer 2013, Journal of Criminal Law and Criminology, 103 J. Crim. L. & Criminology 745, “SYMPOSIUM ON CYBERCRIME: FIGHTING CYBERCRIME AFTER UNITED STATES V. JONES”, lexis, amp) The amount of personal information, including health information, aggregated by government agencies, is referred to as "Big Data," and for good reason. Federal agencies, state authorities, and their private con-tractors store mind-boggling amounts of information. Given the quantity and scope of this information, there can be no doubt that Big Data implicates privacy interests recognized by the mosaic theory of Fourth Amendment privacy endorsed to varying degrees by the concurring opinions in Jones. n135 As the mosaic theory suggests, aggregations of rather [*768] innocuous information may "reveal[] more - sometimes a great deal more - than does the sum of its parts." n136 This is a particularly likely prospect given Big Data's use of increasingly sophisticated analytics, which promise to reveal far more about us than is disclosed by the raw bits and bytes, no matter how "big" or small the data. n137 The dangers are yet more pronounced if health-related data is part of the mix because of what this information can reveal about the most intimate of our affairs . n138 Page 133 Law Enforcement Mosaic theory deters law enforcement agent investigation Ostrander, 11 (Benjamin, JD Law Notre Dame Law School, Volume 86 Issue 4 Notre Dame Law Review, 7-1-11, “THE "MOSAIC THEORY" AND FOURTH AMENDMENT LAW”, http://scholarship.law.nd.edu/cgi/viewcontent.cgi?article=1088&context=ndlr, amp) The application of the "mosaic theory" to the Fourth Amendment would not only be wrong in principle, it would be impractical in application. Maynard is steeped in uncertainty as to the effects of the Fourth Amendment's recognition of an aggregation theory of searches. In articulating a novel theory of Fourth Amendment law, Maynard lacks an accompanying elucidation of the manner in which the theory functions in the Fourth Amendment. Maynard left little guidance as to the determination of the proper scope of the mosaic, whether the theory would implicate other pattern-detecting investigatory techniques, and the appropriate standard of judicial review. A. The Creation and Scope of the Mosaic Maynard left little guidance as to what durational threshold must to be crossed in order for the use of pattern-detecting technology to be sufficiently prolonged as to render it a search.93 Without a clearly demarcated line, law enforcement agents, judges, and individuals cannot know when an aggregate of information will receive Fourth Amendment protection. Law enforcement agents are left to speculate as to how much is too much. 9 4 This lack of clarity will deter law enforcement agents from utilizing the full extent of their investigatory power. This is even more problematic with respect to the "mosaic theory's" creation of retroactive unconstitutionality. 95 As soon as a pat- tern is created, previously permissible individual law enforcement steps become unconstitutional. Because the "mosaic theory" retroactively renders the entire mosaic unconstitutional and subject to suppression, law enforcement agents will be even more hesitant in exercising the full extent of their investigatory power. Broad adoption of mosaic theory chills law enforcement investigatory power Gatewood, 14 (Jace, Georgetown University, A.B., 1983; Georgetown University Law Center, J.D., 1990, Associate Professor of Law at Atlanta's John Marshall Law School, Nebraska Law Review, 2014, 92 Neb. L. Rev. 504, “ARTICLE: District of Columbia Jones and the Mosaic Theory - In Search of a Public Right of Privacy: The Equilibrium Effect of the Mosaic Theory”, lexis, amp) C. Issues Regarding the Implementation of the Mosaic Theory The introduction of the mosaic theory into Fourth Amendment jurisprudence has met with mixed reaction. n180 Those that support the newly formulated theory are staunch supporters, n181 while those that oppose the new theory are adamant in their opposition. n182 Whatever side one happens to fall on, the criticism of the mosaic theory is generally the same. n183 Page 134 The first issue raised by the adoption of the mosaic theory into Fourth Amendment jurisprudence is how to determine the scope of the mosaic necessary to create a Fourth Amendment violation. n184 In other words, how much is too much? The Maynard decision did not express a bright-line rule regarding how much surveillance is required to create a mosaic sufficient to violate the Fourth Amendment. n185 In addition, it has been proffered that the pro-mosaic opinions authored in Maynard (Judge Ginsburg) and Jones (Justices Alito and [*529] Sotomayor) each suggest a different answer. n186 This ambiguity makes it difficult to apply the mosaic theory. n187 The second major criticism, and perhaps just as problematic as the first, is determining what search methods trigger the mosaic theory. n188 What if the government used cell phone location data, pen registry data, wiretaps, GPS surveillance, and visual surveillance? n189 Which, if any of these modes of surveillance, would be acceptable for the purpose of a mosaic? What if one mode of surveillance only reveals limited information? Does that mode of surveillance get aggregated with all other modes of surveillance or just with similar or the same modes? n190 According to opponents of the mosaic theory, these questions would need to be addressed if the mosaic theory were adopted. n191 Perhaps the most critical issue raised with respect to adoption of the mosaic theory is the retroactive unconstitutionality that the mosaic theory may create. n192 It is conceivable that individual components of a search would not, in and of themselves, constitute a search under any theory of the Fourth Amendment. But when all the pieces are aggregated together, the mosaic may reveal far more than the individual pieces, making the individual pieces retroactively unconstitutional. n193 The above, while not exhaustive, could have a chilling effect on law enforcement's exercise of the full extent of their investigatory power if the mosaic theory is adopted . n194 But that is exactly the point. Adoption [*530] of the mosaic theory will force law enforcement officials to adopt guidelines and procedures and make critical decisions regarding the use of certain investigatory techniques so as to avoid having valuable evidence excluded, err ing on the side of caution by obtaining a warrant or utilizing their investigatory methods in a less intrusive or abusive manner. In the wake of advanced technology, the mosaic theory will provide a balancing effect - equilibrium if you will - between Fourth Amendment privacy rights and the need for effective and efficient law enforcement by restoring the practical considerations that once limited the extent to which law enforcement could intrude on one's privacy without violating the Fourth Amendment. Broad mosaic theory application would prevent informants and police investigations through the Doctrines Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) 2. Rejection of the Public Disclosure and Third Party Doctrines The most troubling part of adopting the mosaic theory is that it requires the abandonment of, or dramatic alterations to, the Doctrines. The basic problem is the inherent conflict between the first and second models of reasonable expectation. While the Doctrines embrace a per se rule focusing solely on disclosure and why this vitiates privacy, the mosaic theory rests on society's opinion and what it deems reasonable. n223 Page 135 Consider the Public Disclosure Doctrine. The fact that public movements are not protected under the Fourth Amendment is critical to law enforcement investigations. n224 Visual warrantless surveillance remains a central part of police surveillance. n225 It is not clear to what extent these practices will remain constitutional with the introduction of the mosaic theory. For instance, it is common for officers to track vehicles and aggregate information from various sources over a period of time. n226 As Gray and Citron point out, the "mosaic theory puts these practices and the line of doctrine endorsing them in obvious jeopardy, particularly when officers are too successful and their investigations produce too much information." n227 This danger is compounded by the fact that law enforcement may use a combination of visual and technology-based surveillance (a la Knotts) when investigating a suspect. "How, after all," ask Gray and Citron, "are we to distinguish "between the supposed invasion of aggregation of data between GPS-augmented surveillance and a purely visual surveillance of substantial length'?" n228 It won't do here to simply say that a specific duration of technology-dependent surveillance violates the expectation of privacy. The problem is that the Public Disclosure Doctrine treats all public movements the same, regardless of how much information is disclosed or how long it is observed. n229 To carve out exceptions based on what society thinks is unreasonable leaves vulnerable investigative techniques that are essential to effective law enforcement . The Third Party Doctrine would also be on shaky ground. Here, too, the [*1843] mosaic theory would upset the voluntary disclosure principle that stands at the heart of this doctrine. n230 Shifting the focus to what society or an individual deems reasonable (the first model of reasonable expectation of privacy) would surely frustrate the use of undercover informants or other surreptitious data collection techniques that do not require a warrant. Imagine a scenario where an informant is deep undercover for a significant period of time gaining the trust of a suspect. Or imagine an informant who dupes a suspect into allowing her into her home and disclosing private and incriminating information. Or perhaps the government simply acquires a wealth of financial records from a suspect's bank. Currently, all of these types of law enforcement tools do not trigger Fourth Amendment protection because the individual voluntarily discloses the information to another person or entity. n231 However, under the mosaic theory, none of these tactics are secure . n232 Societal expectations may find that these methods, too, impinge on Fourth Amendment rights as they involve unreasonable duplicity and reveal private information. Police would thus find themselves in the new position of having to secure a warrant based on probable cause before engaging in these practices. For some, this conclusion may be welcomed, particularly in today's technological world where disclosures to various entities and individuals have become ubiquitous. n233 Justice Sotomayor, in fact, raises this possibility in her concurrence. n234 This Article does not take such a drastic approach, nor would such a course be desirable. Any such rejection would come at the cost of jettisoning or severely curtailing essential law enforcement investigative [*1844] techniques that have historically not been subject to warrant and probable cause requirements. n235 Page 136 Mosaic theory hamstrings law enforcement generically Walsh, 12 (Courtney, Special Counsel at Parker Poe Adams & Bernstein LLP, LL.M. Master of Laws from Harvard Law School, JD law UFlorida, Spring 2012, St. Thomas Law Review, 24 St. Thomas L. Rev. 169, “CRIMINAL LAW ISSUE: FEATURED CONTRIBUTOR: SURVEILLANCE TECHNOLOGY AND THE LOSS OF SOMETHING A LOT LIKE PRIVACY: AN EXAMINATION OF THE "MOSAIC THEORY" AND THE LIMITS OF THE FOURTH AMENDMENT”, lexis, amp) However, a stronger and more specific form of the "unworkability" critique comes in two forms. The first is that the "mosaic theory" would have the effect of making constitutional surveillance practices, when applied over time, unconstitutional. In other words, it would make constitutional practices "retroactively unconstitutional." n430 This criticism is not unfair, given that neither the Maynard decision nor the Jones concurrences offer much guidance on the presumed number of days - or weeks - that warrantless surveillance could persist before it turned into an offending "mosaic" and, therefore, a "search." n431 Howev-er, this situation is not as untenable as it would first seem. Albeit a slightly different context, this mirrors the problem faced by the Court as a result of its decision in Gerstein v. Pugh. In Gerstein, the Court held that persons arrested without a warrant had a right to a "prompt" hearing in front of a neutral and detached magistrate. n432 While there was substantial debate after Gerstein about what "prompt" meant in practical terms, the Court subsequently remedied this in County of Riverside v. McLaughlin, when it held that a hearing that takes [*236] place within forty-eight hours of arrest was presumably reasonable. n433 Turn-ing again to the specific facts in Maynard and Jones, these cases offer little practical guidance, aside from the fourweek bright-line standard, that would assist law enforcement in translating the rule into operation. However, just as in County of Riverside, the Court can announce more specifically tailored rules and guidelines in the course of future litigation. Alternatively, in the absence of judicial action, the legislative branch could set policy, regulating the number of days government agents could use GPS technology to collect location data without a warrant. As one example, Congress, via the Foreign Intelligence Surveil-lance Act ("FISA"), restricts the Attorney General's authority to conduct warrantless electronic surveil-lance for an unlimited duration following a declaration of war. n434 A final criticism of the "mosaic theory" is that it does not provide any formulation for determining the size and scope of a mosaic that would trigger Fourth Amendment scrutiny. n435 Defense attorneys, attempt-ing to bring entire investigations within the scope of a "mosaic," could argue that the totality of an inves-tigatory file reveals intimate insights and facts about a person that would otherwise be unavailable to members of the general public. n436 Consistent with the "mosaic" formulation, this argument has doctrinal purchase now, as no person would reasonably expect to be investigated and tracked by a member of the general public; therefore, any information collected as a part of a law enforcement investigation could be viewed as a product of a Fourth Amendment "search" and subject to warrant requirements. This argument foresees that if Maynard were extended to its logical extreme entire investigations could be subjected to more intense Fourth Amendment scrutiny with few guiding principles to assist law enforcement in avoid-ing pitfalls. n437 This is a serious critique; nevertheless, the Maynard court appears to anticipate this concern in attempting to limit [*237] its holding to the specific context of extended GPS surveillance, reserving questions of prolonged visual or other surveillance. n438 Turning to Jones, even though Justice Alito's con-currence similarly attempts to limit the Justice Sotomayor's opinion illustrates how the "mosaic theory" and its logic, if applied broadly, application of its rationale to lengthy, technology-driven surveil-lance, Page 137 can begin to extend well-beyond the specific facts of the present case . Regardless of any attempt to limit the application of "mosaic theory" rationale, the opinions from Maynard and Jones offer future criminal liti-gants a credible doctrinal foothold to argue for far greater court regulation over entire criminal investigations . Hurts investigative practices Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) The mosaic theory - first articulated by the Supreme Court in United States v. Jones two years ago - has turned out to be an empty promise of Fourth Amendment protection. However, this may have less to do with the theory itself and more to do with the context in which it has been applied. Introduced as a mechanism to combat long-term GPS police surveillance, scholars have widely criticized the theory as untenable and too costly. Its application jeopardizes longstanding police investigative tactics, including the use of undercover informants and even short-term human surveillance. This Article provides the first application of the mosaic theory to social networking communications over the Internet. The refrain of "the sum is greater than the parts" remains. Only this time it is a group of communications, not a person's movements, that informs the relevant analysis. This Article employs the principle of associational rights - referenced by Justice Sotomayor in Jones - as a key ingredient to explaining why these social networking communications, in the aggregate, merit privacy protection. This is not simply an academic exercise. In light of the news that the NSA has been collecting messages over sites such as Facebook, courts need a Fourth Amendment framework to protect these communications where one currently does not exist. This narrow use of the theory also has the benefit of preserving the current Fourth Amendment landscape and the police's ability to use a wide range of investigative tactics. Page 138 Drug Cartels Mosaic theory would prevent investigative techniques for narcotics arrests Gray and Citron, 13 (David--Associate Professor, University of Maryland Francis King Carey School of Law, Danielle Keats--Lois K. Macht Research Professor of Law, University of Maryland Francis King Carey School of Law, Affiliate Scholar, Stanford Center on Internet and Society, Affiliate Fellow, Yale Information Society Project, North Carolina Journal of Law & Technology, Spring 2013, 14 N.C. J.L. & Tech. 381, “ARTICLE: A Shattered Looking Glass: The Pitfalls and Potential of the Mosaic Theory of Fourth Amendment Privacy”, lexis, amp) In King, police officers followed a suspect, who had just purchased crack cocaine from an undercover agent, into an apartment building.93 As they entered the building’s breezeway, they heard a door close, but could not discern which of two apartments the suspect had entered.94 The officers had no reason to think that the suspect knew he was being followed, so they had no claim of hot pursuit or any other emergency at that point.95 They did, however, detect the smell of burning marijuana emanating from behind one door, so they decided to knock, announce themselves, and request entry. 96 The predictable ensued. Immediately after announcing their presence, the officers heard noises inside the apartment that might reasonably have indicated that evidence was being destroyed.97 Based on that suspicion, the officers forced the door open and entered the apartment.98 Once inside, the officers seized several people on the scene, conducted a Buie 99 protective sweep, and in the course of that search found marijuana, cocaine, drug paraphernalia, and cash in plain view.100 As it turned out, the initial suspect was not in the apartment, but three other people were, including the eventual respondent: Hollis King.101 King was convicted on several narcotics charges and appealed to the Supreme Court of Kentucky.102 Although skeptical that the sounds officers heard coming from the apartment were enough to justify an unwarranted entry under the emergency exception to the warrant clause, the Kentucky court assumed as much. 103 It nevertheless held that King’s conviction should be vacated because the officers created the emergency.104 In that court’s view, it was unreasonable from a Fourth Amendment perspective for officers to knock on the apartment door because it was foreseeable, given the circumstances, that doing so would create an emergency.105 The U.S. Supreme Court reversed. 106 In doing so, it rejected approaches adopted in lower courts that required assessing the reasonableness of law enforcement conduct holistically by looking at the totality of an evolving encounter that eventually resulted in a search or arrest. 107 The Court instead recommitted itself to assessing the reasonableness of officer conduct at each step of an encounter. 108 The Court therefore held that all the Fourth Amendment requires is that, at each stage of an evolving investigation or engagement, officers limit themselves to conduct that is reasonable based on what they know or observe.109 In so holding, the Court reaffirmed its longstanding commitment110 to an objective and synchronic assessment of Fourth Amendment reasonableness. The mosaic theory raises serious concerns when considered in the light of cases like King . Beyond the mathematical challenge of adding nothings to get something, the very idea of an additive or holistic approach to evaluating Fourth Amendment reasonableness runs contrary to the synchronic approach that is a foundation of long-standing Fourth Amendment analysis. B. Doctrinal Objections to the Mosaic Theory Page 139 The mosaic theory endorsed by the U.S. Court of Appeals for the District of Columbia and a majority of concurring Justices in United States v. Jones proposes nothing short of a revolution in Fourth Amendment law. Never before has the Court suggested that we can have reasonable expectations of privacy in certain quantities or aggregations of information even if we have no such expectations in the constituent parts. 111 As with any doctrinal revolution, the mosaic theory appears to require some blood on the floor. Specifically, adopting a mosaic approach to the Fourth Amendment may require abandoning or dramatically altering two important lines of Fourth Amendment law: the public observation doctrine112 and the third party doctrine. 113 To the extent that this is so, commitments to these doctrines, or simply to stare decisis, counsel caution before adopting a mosaic theory of Fourth Amendment privacy. Adopting a mosaic approach to quantitative privacy seems to require abandoning the public observation doctrine, which is often credited to the Supreme Court’s decision in United States v. Knotts. 114 In Knotts, the Court held that using a beeper device to track a suspect’s car on public streets did not constitute a “search” because the suspect lacked a reasonable expectation of privacy in his public movements.115 Although the beeper allowed officers to follow Knotts more efficiently and with fewer personnel, the Knotts Court specifically declined to hold that using technology raises any independent Fourth Amendment concerns simply because it makes it easier for law enforcement officers to conduct surveillance that they are otherwise entitled to do using traditional means.116 The parallels between Knotts and Jones are obvious. In both cases, law enforcement officers used a passive signaling device attached to a car. 117 In both cases, the devices revealed only movements on public streets.118 In both cases, those movements were exposed to public view.119 Given these similarities, Knotts would seem to control in a case like Jones, thus barring Fourth Amendment review of GPS-enabled tracking so long as the technology is only used to monitor movements in public.120 Should the Court eventually adopt a mosaic approach to assessing and protecting quantitative privacy, it would therefore seem obliged to overrule or modify Knotts and the long line of subsequent cases121 endorsing investigative-surveillance techniques and technologies that merely document what targets knowingly expose to public view.122 Among the most compelling examples of these potential disruptions is the effect of the mosaic theory on traditional human surveillance.123 Visual surveillance is a mainstay of targeted police investigations . Police officers routinely conduct “stake-outs,” sometimes using teams of officers and vehicles to track suspects as they move through public spaces . 124 Law enforcement agencies also aggregate information from informants to develop detailed accounts of suspects’ public movements.125 These practices are not only commonplace,126 they have been routinely endorsed by courts as well within Fourth Amendment bounds127—a view that is shared even among mosaic promoters128—because they document conduct and movements in which the suspect or target has no reasonable expectation of privacy.129 The mosaic theory puts these practices and the line of doctrine endorsing them in obvious jeopardy , particularly when officers are too successful and their investigations produce too much information.130 How, after all, are we to distinguish “between the supposed invasion by aggregation of data between the GPS-augmented surveillance and a purely visual surveillance of substantial length”?131 Page 140 In addition to the public observation doctrine, the mosaic theory also threatens to unsettle the “third party doctrine.”132 The Court has long held that citizens who share information with others assume the risk that what they share might be passed along to law enforcement.133 Applying this rule, the Court has held that there is no Fourth Amendment violation if a criminal confederate shares the confidences of his co-conspirators with police, 134 if a bank shares a customer’s financial records with law enforcement,135 or if a telephone company discloses records of phone calls customers make or receive.136 More recently, a New York court ruled that a customer of the social networking website Twitter 137 had no standing to challenge a lawful subpoena issued against the company for locational information embedded in his posts because he voluntarily shared that information with Twitter.138 As Justice Sotomayor, who expresses sympathy for some version of the mosaic theory in her Jones concurrence, points out, “[I]t may be necessary to reconsider the premise that an individual has no reasonable expectation of privacy in information voluntarily disclosed to third parties.”139 That is because we routinely share vast quantities of data with private agents, many of whom store it.140 Our Internet service providers track and keep detailed records of where we go on the internet. 141 Our chosen search engines gather information not only on our search patterns, but also where we go, what we look at, and what stimuli we react to while online. 142 For most of us, law enforcement would not need to install GPS-enabled devices on our persons or cars if they wanted to track us in the same way that officers tracked the defendants in Jones because we already carry GPS chips in our telephones, cars, and computers that pass along information about our movements to a wide range of third parties, from map services to social network applications and restaurant rating sites. 143 Moreover, these third parties are already in the habit of sharing much of the information they gather. Data brokers aggregate and analyze vast reservoirs of data from financial institutions, retailers, public records, social networking sites, and just about anywhere we interact with the physical or virtual worlds.144 The third party doctrine provides the Government with unfettered access to all of this data145—so much so that Chris Hoofnagle has coined the phrase “Big Brother’s Little Helpers” to describe data brokers like Acxiom,146 which aggregate data from public and third-party sources to compile detailed mosaics of information on anyone and everyone.147 The question hinders drug searches and seizures Kerr, 14 (Orin, Fred C. Stevenson Research Professor, George Washington University Law School , 12-18-14, Washington Post, “Two district courts adopt the mosaic theory of the Fourth Amendment”, https://www.washingtonpost.com/news/volokh-conspiracy/wp/2014/12/18/two-district-courts-adopt-themosaic-theory-of-the-fourth-amendment/, amp) Judge Lawson recognized that his approach raised a difficult question of line-drawing: How long is long enough for monitoring to constitute a search? He answers: [C]ourts have confronted similar problems in the past. For instance, how long may law enforcement detain property waiting for a drug detection dog to arrive for a sniff before the intrusion matures into a “seizure”? To find an answer, courts must “balance the nature and quality of the intrusion on the individual’s Fourth Amendment interests against the importance of the governmental interests alleged to justify the intrusion.” United States v. Place, 462 U.S. 696, 703 (1983). Mosaic making is key to drug enforcement Pascal, 14 Page 141 (Brian, research fellow with the University of California Hastings Law School Institute for Innovation Law and a fellow with Stanford Law School’s Center for Internet and Society, American Bar Association, Litigation: The Journal of the Section of Litigation, Vol. 40 No. 3, “How Technology Broke Privacy”, http://www.americanbar.org/publications/litigation_journal/201314/spring/how_technology_broke_privacy.html, amp) In 2004, the Washington, D.C., Metropolitan Police Department, working with the Federal Bureau of Investigation, began investigating nightclub owner Antoine Jones for possible narcotics violations . As part of their investigation, the officers installed a Global Positioning System (GPS) unit on Jones’s car and used it to track his movements without a warrant. In late 2011, the case of United States v. Jones reached the Supreme Court, and in January 2012, the Court held that this warrantless use of a GPS tracker violated Jones’s Fourth Amendment rights. The majority opinion relied primarily on a trespass argument, stating that it was the government’s placement of the device on Jones’s private property that generated the constitutional violation. Sifting through the various concurrences, it is also possible to tally five justices’ worth of support for a more expansive argument that has come to be known as the “mosaic theory,” a phrase first coined by law professor Orin Kerr. Under the mosaic theory, the emphasis would rest on the idea that Jones possessed a reasonable expectation of privacy in his physical location, and, regardless of method, it was improper for the police to acquire that information without a warrant. Though the mosaic theory is an attractive argument, it was not the basis for the majority opinion (though Justice Sotomayor’s concurrence relied on an effectively identical justification). By declining to explicitly accept the mosaic theory (or a similarly flexible approach), the Court ensured that its holding in Jones would be so narrow as to be nearly obsolete the day it was handed down . In an ever-increasing number of cities throughout the United States, police departments are installing “automated license plate readers” (ALPR, also called “automated number plate readers,” or ANPR, in Europe). ALPR systems are networks of cameras that capture the license plate of every car that drives by, along with a time stamp and geographical location. When the information is combined into a database and filtered properly, it is possible to track the movements of a car throughout a city without employing anything so clumsy as a physical GPS unit. In addition, it is possible to cross-reference the ALPR database with other police data sources. For example, if police receive a 911 call reporting gunshots, they could access the ALPR database and search for any vehicles registered to individuals who were arrested for gun crimes. An unlucky individual passing by a few blocks away might find himself the subject of a police investigation, based solely on the route he chose to drive and his past interactions with law enforcement. Hypothetical scenarios aside, there are three very real facts about ALPR systems that many privacy advocates find troubling. The first is that ALPR is indiscriminate: By design, it captures the license plate of every car that drives by. This means that information about the movements of every individual driving through an ALPR-enabled city lies buried in police databases, whether or not those individuals are targets of an investigation. And, make no mistake, these data sets can contain substantial details about an individual’s habits. They can reveal the times of day when a mother leaves for work and picks up her children, the fact that an individual visits a mental health professional on Thursday afternoons, or the location of the cheap bythe-hour hotel that two married individuals frequent for late-night trysts. Page 142 The second concern that ALPR systems raise is one of scale. Thirty years ago, it was comparatively expensive in terms of manpower and logistics to tail a suspect. If the police wanted to follow an individual’s movements, they had to devote officers to the task, and, if they were wrong, that time and that effort were entirely wasted. Today, the same ALPR system that can monitor a thousand cars can just as easily monitor a million. The scale of this surveillance is subject only to the technical limitations of the ALPR system, and, in practice, this is not much of a limitation at all. Modern systems can track almost every vehicle in a city, in something approaching real time, and they can store data long enough to allow police to review an individual’s movements over the course of prior weeks or months. Legal scholar Woodrow Hartzog has written much about how some level of obscurity is necessary to maintain basic privacy and freedom within a modern society, and ALPR systems push in exactly the opposite direction. See Woodrow Hartzog and Evan Selinger, “Obscurity: A Better Way to Think about Your Data Than ‘Privacy,’” Atlantic, Jan. 17, 2013. The third, and perhaps incongruous, difficulty with ALPR arises from the fact that these systems are almost certainly legal. It has long been an accepted legal doctrine that individuals have no reasonable expectation of privacy in their photographic image in a public place (see, e.g., Katz v. United States 389 U.S. 347 (1967)), and capturing the images of cars on public roads is all that ALPR systems do. As discussed above, these photos can paint a picture of an individual’s personal life far more detailed than anything that can be captured by a single telephoto lens. Despite this, much of Fourth Amendment law stubbornly focuses on single acts of capture rather than fully comprehending the power of aggregated information. For all their ubiquity and “creepiness,” at first glance ALPR systems seem a possible boon to defense attorneys. If these systems capture so many subjects so broadly, then they would be hugely capable in the discovery of reasonable doubt. After all, any halfway-competent defense attorney, upon learning that his or her client was charged on the basis of information derived from an ALPR database, would surely subpoena the contents of that database—perhaps the disclosure of this database might even be required under Brady v. Maryland. But prosecutors have recognized this possibility as well, and it is exceedingly unlikely that we will ever see ALPR evidence introduced directly in court. This information is used for investigatory purposes, and the case that the prosecutor presents to the jury is built on other information, even if it would have been impossible to uncover these facts without the starting point provided by the ALPR database. There is nothing inherently wrong with this practice: Bifurcating the investigation from the prosecution and presenting a coherent, clear story to the jury is a tactic as old as adversarial criminal procedure. However, when combined with the massive amount of information that law enforcement is able to gather about an individual from other sources (e.g., from the suspect’s mobile phone, as discussed in Yuri Mikulka’s and Sarah S. Brooks’s piece elsewhere in this issue), ALPR systems and tools like it have the potential to be put to use in a far more sinister way. This is not mere paranoid speculation: In an exclusive story from August 2013, Reuters uncovered information suggesting that the U.S. Drug Enforcement Agency (DEA), while investigating ordinary crimes unrelated to terrorism, based their investigations on tips received from a top-secret Special Operations Division (SOD) within the DEA. This division was initially created to combat Latin American drug cartels , and it partnered with such agencies as the Federal Bureau of Investigation, the Central Intelligence Agency, and the National Security Agency (NSA). However, because the activities of the SOD were secret, DEA agents were encouraged to use a technique known as “parallel construction” to recreate an investigative trail, excluding the SOD information. See John Shiffman & Kristina Cooke, “U.S. Directs Agents to Cover Up Program Used to Investigate Americans,” Reuters, Aug. 5, 2013. It is impossible to guess at how widespread this practice is, but it would be naïve to assume that the activities discussed in the Reuters article are the one and only instance in which information collected through the tools of international intelligence and counterterrorism was put to domestic use. Either way, the existence of Page 143 large databases of information only makes the practice of parallel construction easier than it has ever been before. It’s worth reiterating here two points I raised previously: We shed data constantly, especially in transactions mediated by electronic communications systems; and information in the aggregate is often far, far more powerful than the sum of its parts. Taken together, these ideas were the detonator that, in the past few years, sparked the explosive popularity of “big data” as a phrase, business model, national security asset , and philosophy. Mosaic making is instrumental to narcotics law enforcement Kerr, 12 (Orin, Fred C. Stevenson Research Professor, George Washington University Law School, 1-23-12, The Volokh Conspiracy, “What’s the Status of the Mosaic Theory After Jones?”, http://volokh.com/2012/01/23/whats-the-status-of-the-mosaic-theory-after-jones/, amp) In his majority opinion, Justice Scalia concludes that the mosaic theory need not be addressed, but that it is a “novelty” that raises “thorny problems” if embraced. Responding to Alito, Scalia writes: There is no precedent for the proposition that whether a search has occurred depends on the nature of the crime being investigated. And even accepting that novelty, it remains unexplained why a 4-week investigation a drug-trafficking conspiracy involving substantial amounts of cash and narcotics is not an “extraordinary offens[e]” which may permit longer observation . See post, at 13–14. What of a 2-day monitoring of a suspected purveyor of stolen electronics? Or of a 6-month monitoring of a suspected terrorist? We may have to grapple with these “vexing problems” in some future case where a classic trespassory search is not involved and resort must be had to Katz analysis; but there is no reason for rushing forward to resolve them is “surely” too long and why here. Page 144 --Cartels kill econ Cartel violence destroys the economy Hodgins 14 (Wesley, Peace, War, and Defense and International Relations, University of North Carolina. Chapel Hill, “Los Carteles de la Droga: Mexican Drug Cartels and the U.S.-Mexico Security Relationship” Global Security Studies, Summer 2014, Volume 5, Issue 3 // AKONG) The problem of the drug cartels must be examined within the context of the economic relationship between the United States and Mexico. Security of resources, both natural and manufactured, is critical to the interest of U.S. national security for domestic and international operations. The United States must maintain access. McCaffrey points out that Mexico is the twelfth largest economy in the world and is responsible for one-third of the U.S. imported oil. In addition, 18,000 companies have direct investment in the United States and are responsible for 47% of Mexico’s direct investment. Finally, Mexico is the source providing half of our 12 million undocumented illegal immigrants that cross the border to work agricultural jobs and other low-income employment. Over 1 million people cross the border into the United States daily (McCaffrey, 4). Therefore, it is obvious that the U.S. has a vested interest in maintaining productive economic ties and seeking to keep Mexico as a viable and stable state with their government in control. The alternative would be catastrophic. If drug cartel violence were to grow to such a level that middle class workers seek refuge and abandon their jobs across the border or in Mexico’s domestic sector, the U.S. could lose a critical part of its industry, leading to decreasing imports, less temporary employment, and foreign divestment out of their fear of violence. To a certain degree, this process has already begun. Because of the violence, in 2006, many middle- class working professionals began to leave behind their jobs and find refuge in either the U.S. or Canada for fear of the cartels. For example, 200,000 people left the city of Juarez that year, fearing for their lives amidst conflict between the cartels and Mexican law enforcement (McCaffrey, 4). There are serious economic considerations to be analyzed when evaluating the implications of Mexican drug cartels in the context of the U.S.-Mexico security relationship due to America’s vested interests in a stable and productive Mexico. Page 145 --Afghanistan Drugs Impact Effective law enforcement solves trafficking --- it’s improving now GAO 2015 --- Government Accountability Office (“Investigations of Major Drug Trafficking Organizations”) In response to a congressional request, GAO assessed Drug Enforcement Administration (DEA) efforts to [inhibit] immobilize major drug traffickers and their organizations. GAO stated that, because scarce federal resources must be directed primarily toward the elimination of criminal organizations responsible for supplying drugs, persons at the highest levels of trafficking enterprises must be detected and immobilized. GAO found that DEA has adopted various techniques for focusing its investigative efforts at the highest echelons of drug trafficking organizations, including a code classification system which categorizes violators. GAO found that federal law enforcement efforts aimed at [devastating] immobilizing major drug traffickers and their organizations have improved . It’s uniquely effective in Afghanistan Baker 11 --- James A Baker III Institute for Public Policy (“Unfinished Business in Afghanistan”, http://blog.chron.com/bakerblog/2011/07/the-dea%E2%80%99s-unfinished-business-in-afghanistan/)//trepka Why is the United States [is] investing so much in terms of DEA personnel, money and other resources into Afghanistan’s poppy fields ? The answer is as simple as it is counterintuitive: terrorism. As long as opium and heroin sales fuel terrorism, the United States has an imperative to stem the flow of those funds. The U.S. attacks beginning in October 2001 and subsequent invasion of Afghanistan led to the dismantling of the Taliban, an insurgent movement that supported the terrorist activities of Al Qaeda. Profits they derived from opium and heroin sales were used to fill the coffers of the Al Qaeda terrorist network, and the money was used to corrupt government officials in Afghanistan and fund terrorist activities throughout the world. As a result, opium cultivation has become one of Afghanistan’s primary sources of illegal revenue and a source of funding for terrorism. The United Nations Office on Drugs and Crime (UNODC) estimated in its World Drug Report 2011 that Afghanistan had the potential to produce 3,200 tons of opium, an amount of gum that could yield an equivalent of 390 tons of heroin. Despite a ban on cultivation of opium poppies enacted in January 2002 and government efforts to eradicate poppy fields, Afghanistan currently ranks first in the world for poppy cultivation and production. The UNODC also reports that the average price for opium in Afghanistan increased significantly between March 2010 and March 2011, to $274 per kilogram, an approximate 180 percent increase over the year before. The rise in prices was attributed to decreased production brought on by poppy blight, an agricultural disease that nearly decimated opium cultivation. The continued and increased revenues gained from the sale of Afghan opium and heroin will continue to be a source of funds for terrorist operations, much to the detriment of the United States. This is true despite the fact that heroin and other opiates produced in Afghanistan are consumed within the region and in countries along the supply chain as the drugs head towards the primary consumer market in Europe. The United Kingdom’s Serious Organized Crime Agency (SOCA) estimates that the majority of the heroin found in Britain is derived from Afghanistan. It is also important to note that heroin produced in Afghanistan continues to be smuggled into the United States, but in significantly smaller amounts than what is sold in Europe. The continued drug trade has caused DEA to shift its mission parameters and operate in Afghanistan as paramilitary war fighters amid the deadly fields of a terrorist war, creating “ mission creep ,” slipping away from serving as a “single-mission” agency. DEA’s current-day presence and warlike posture in Afghanistan also creates an unintended inversion of the Posse Comitatus Act, the provision of law that prohibits U.S. uniformed soldiers from acting in a domestic law enforcement capacity. Ironically, assigning U.S. federal law enforcement personnel to perform in a paramilitary capacity overseas tends to supplant the U.S. military forces that have also been working to rid the country of Afghan drug lords who fund terrorism. This now defines DEA in a new way: as a hybrid military force that was never envisioned in federal law enforcement prior to 9/11. Notwithstanding the reasons for removing U.S. military forces from the field of battle, DEA has made the right choice , the only choice that an agency can make — to step into that field of battle in defense of its nation “against all enemies, foreign and domestic.” Page 146 Increased drug trafficking wrecks Afghan stability Inkster, 12 (Nigel, Director of Transnational Threats and Political Risk at the International Institute for Strategic Studies, “Drugs: A war lost in Afghanistan”, Foreign Policy, 5/29/2012, http://afpak.foreignpolicy.com/posts/2012/05/29/drugs_a_war_lost_in_afghanistan, JKahn) The May 20 NATO summit in Chicago was dominated by the issue of Afghanistan. Amidst all the talk about withdrawing international combat troops by 2014, funding the Afghan National Security Forces beyond 2014, and a doubtful political settlement with the Taliban, one subject was absent from the formal agenda the drugs trade so entrenched as it is : drugs . Yet in few other countries is in Afghanistan. Accounting for between one-quarter and one-third of the national economy, it is an integral part of the insecurity blighting Afghan life for the past 30 years. Debate may continue for years as to whether the Western intervention in Afghanistan has made the world safer or more insecure in the post-9/11 era. But it has not only done nothing to reduce global supplies of illicit opium; rather, it has made the problem worse. The international drugs-control regime, in place since the 1961 Single Convention on Narcotic Drugs came into effect, rests on prohibiting use in consumer countries and reducing supply in producer states. In Afghanistan, the source of around 60 per cent of the planet's illicit opium and 85 per cent of heroin, the latter objective may never be achieved to any meaningful degree. The boom years for Afghan poppy cultivation began in the 1970s, thanks to political instability in Southeast Asia's fertile 'Golden Triangle' and bans on the crop in neighbouring Iran and Pakistan. The Soviet invasion in late 1979 gave local warlords an incentive to plant opium poppies to fund their insurgency against Moscow. In the three decades since, with few other sources of income, opium production has come to provide for up to half a million Afghan households. The poppy is a hardy, drought-resistant plant, much easier for farmers to grow than saffron and more profitable than wheat. Both have been offered as alternative crops, but with only limited take-up. The criminal networks that have sprung up around the drugs principal growing regions, the southern Pashtunare also Taliban strongholds . For all these reasons, NATO efforts to eradicate opium - either by aerial spraying or trade provide farmers with seeds, fertiliser and cash loans; in short they offer an alternative welfare system. The dominated provinces of Helmand and Kandahar, manually- have alienated the population. Indeed, they have often had to be abandoned in the face of popular resistance. Crop disease did more to reduce opium production in 2010 than NATO's counter-narcotics strategy. The United Nations recently reported there had been a 61 percent rebound in opium production in 2011, and prices were soaring. This is a worrying trend, which seems set to continue after NATO troops leave. Drug seizures, while rising, still account for less than 5% of opium produced. As a general rule, the United Nations estimates, law-enforcement agencies need to interdict about 70% of supplies to make the drugs trade less financially attractive to traffickers and dealers. In any circumstances, this is an extremely challenging objective. In the large swathes of Afghanistan where the central government and security forces wield no control, it is completely unrealistic. Meanwhile, no major trafficker has yet successfully been prosecuted due to a widespread culture of impunity. Alternative approaches have been proposed. Most recently, in May 2012, Tajik Interior Minister Ramazon Rakhimov proposed that opium should be purchased directly from Afghan farmers to either be used in the pharmaceutical industry or to be destroyed. He also called on other countries to do the same in a move he deemed essential to fight drug trafficking and narcotics-fuelled terrorism. But this option was tried in 2002 when the United Kingdom had the lead on narcotics reduction, and had to be abandoned in the face of evidence that the purchasing programme constituted a perverse incentive to increase production. Licit production of opium for medical purposes may be a long-term option for Afghanistan, but not while current conditions of high insecurity and pervasive corruption persist. In the West, the drugs scourge is mostly thought about in terms of the lives lost, opportunities wasted and the social disruption created through addiction. In , drugs create a shadow state, fuelling institutional corruption, instability, violence and human misery. The Taliban, which banned the planting of opium in 2001, was deriving an estimated U.S. $125 million per year from the business by 2009. It has been an equally important revenue stream for former warlords whose inclusion in the administration of President Hamid Karzai NATO's International Security Assistance Force (ISAF) has done little to oppose. Such individuals have a powerful vested interest in state weakness to the obvious fragile and impoverished nations such as Afghanistan detriment of good governance and institution-building. And all these actors are likely to maximise revenues from opium production in the run-up to the 2014 NATO/ISAF drawdown What drives it is its huge profitability, a consequence of continuing Western demand . No-one can confidently predict the consequences of changing the drugs prohibition regime. The to hedge against an uncertain future. A trade in which so many have vested interests will never be unwound simply or swiftly. current approach has not achieved the 1961 Single Convention's objectives. But has had the unintended consequence of perpetuating and increasing corruption and instability in parts of the world least equipped to deal with the consequences. Perhaps our collective experience in Afghanistan should serve as the basis for a serious rethink of global drugs policy? This would involve a cost/benefit analysis of current policies, scenario planning of the impact of alternative approaches and a much greater focus on demand reduction in consumer states. narcotics needs to be taken out of the silo it currently inhabits and looked at in the wider context of international security and development. The issue of That goes nuclear – Indo-Pak tensions and Iran Rubin, 11 (Joel, Director of Policy and Government Affairs, Ploughshares Fund, former congressional aide and diplomat, fellow at the State Department in both Near Eastern Affairs and Political-Military Affairs, Master’s degree in Public Policy and Business Administration from Carnegie Mellon University and a Bachelor’s degree in Politics from Brandeis University, Huffington Post, 77/2011, http://www.huffingtonpost.com/joel-rubin/middle-east-nuclear-threat_b_891178.html, JKahn) The national security calculus of keeping U.S. forces in Afghanistan has shifted. Any gains that we made from keeping 100,000 American soldiers in harm's way are now questionable, especially since al Qaeda has been dealt a significant blow with the killing of Osama bin Laden. President Obama's decision to end the surge by late next year only reinforces this reality. Yet many of the underlying sources of a region that has deep experience on nuclear matters -- with nuclear aspirant Iran bordering Afghanistan on one side and nuclear-armed Pakistan and India on the other -- the United States must take into account the potential for regional nuclear insecurity caused by a conflict and tension in South and Central Asia will remain after an American withdrawal. In poorly executed drawdown in Afghanistan. As much as we may like to, we can't just cut and run. So as the United States draws down its forces, we must take care to leave stable systems and relationships in place; failure to do so could exacerbate historic regional tensions and potentially create new national security risks. It is therefore essential that Washington policymakers create a comprehensive nuclear security strategy for the region as part of its Afghanistan withdrawal plans that lays the groundwork for regional stability. We have only to look to our recent history in the region to understand the importance of this approach. In the 1980s, the U.S. supported the Mujahedeen against the Soviet Union. When that conflict ended, we withdrew, only to see the rise of al Qaeda -- and its resultant Page 147 international terrorism -- in the 1990s because we didn't pull out responsibly from Afghanistan. Our choices now in Afghanistan will determine the shape of our security challenges in the region for the foreseeable future. And we can't afford for nuclear weapons to become to South and Central Asia in the 21st century what al Qaeda was in the 1990s to Afghanistan. To avoid such an outcome, several key objectives must be included in any Afghanistan withdrawal plan. First, current levels of regional insecurity -- which already are extremely high -- will continue to drive tensions, and quite possibly conflict, amongst the regional powers. Therefore, we must ensure the implementation of a regional approach to military withdrawal. These efforts must bring all relevant regional players to the table, particularly the nuclear and potentially nuclear states. Iran and all the countries bordering Afghanistan must be part of this discussion. Second, the United States must be mindful to not leave a governance vacuum inside Afghanistan. While it is clear that the current counter-insurgency policy being pursued in Afghanistan is not working at a pace that meets either Western or Afghan aspirations, it is still essential that Afghanistan not be allowed to implode. We do not need 100,000 troops to do this, and as the Afghanistan Study Group has recommended, credible political negotiations that emphasize power-sharing and political reconciliation must take place to keep the country intact while the United States moves out. Third, while the rationale for our presence in Afghanistan - to defeat al Qaeda -- has dissipated, a major security concern justifying our continued involvement in the region -- potential nuclear conflict between India and Pakistan -- will remain and may actually rise in importance. It is crucial that we keep a particularly close eye on these programs to ensure that all is done to prevent the illicit transfer or ill-use of nuclear weapons. Regardless of American troop levels in Afghanistan, the U.S. must maximize its military and intelligence relationships with these countries to continue to both understand their nuclear intentions and help prevent potential conflict. We must avoid a situation where any minor misunderstanding or even terrorist act, as happened in Mumbai in 2008, does not set off escalating tensions that lead to a nuclear exchange. Ultimately, the U.S. will one day leave Afghanistan -- and it may be sooner than anyone expects. The key here is to leave in a way that promotes regional stability and cooperation, not a power vacuum that could foster proxy conflicts. To ensure that our security interests are protected and that the region does not get sucked in to a new level of insecurity and tension, a comprehensive strategy to enhance regional security, maintain a stable Afghanistan, and keep a watchful eye on Pakistan and India is essential. Taking such steps will help us to depart Afghanistan in a responsible manner that protects our security interests, while not exacerbating the deep strategic insecurities of a region that has the greatest risk of arms races and nuclear conflict in the world. Page 148 Privacy Invoking “mosaic theory” prevents inevitable development of statutory privacy laws Kerr, 12 (Orin, Fred C. Stevenson Research Professor, George Washington University Law School, December 2012, Michigan Law Review, 111 Mich. L. Rev. 311, “ARTICLE: THE MOSAIC THEORY OF THE FOURTH AMENDMENT”, lexis, amp) A third difficulty with the mosaic theory is that it may interfere with the development of statutory privacy laws. As I have explained in another article 2 1 -and as Justice Alito suggested in his concurring opinion in Jones 219 -- Congress has significant institutional advantages over the courts in trying to regulate privacy in new technologies. Congress can act quickly, hold hearings, and consider expert opinion.220 Congress can draw arbitrary lines that don't fit easily within constitutional doctrine.2 21 And if Congress errs or facts change, Congress can amend its prior handiwork relatively easily.222 Congress can also regulate using sunset provisions that force the legislature to revisit the question in light of intervening experience. 23 For these reasons, legislative privacy laws have considerable institutional advantages over the products of the comparatively slow and less-informed judicial process. The mosaic approach could interfere with statutory solutions in two ways. First, the theory might discourage legislative action by fostering a sense that the courts have occupied the field . 224 When courts hear a controversial privacy case but rule that the Fourth Amendment does not apply, the judicial "no" identifies a problem for the legislature to address. The absence of judicial regulation invites legislative action . Prominent examples include the Right to Financial Privacy Act of 1978,225 passed in response to United States v. Miller;226 the Pen Register Statute, 227 passed in response to Smith v. Maryland;228 and the Privacy Protection Act of 1980,229 passed in response to Zurcher v. Stanford Daily.30 In all three instances, Congress responded to a Fourth Amendment ruling allowing a controversial investigatory practice by creating statutory protections . 23 ' The possibility of mosaic protection complicates the legislative picture because mosaic protections can overlap with possible statutory solutions and therefore render the case for statutory protection much less apparent.2 32 Page 149 Social network surveillance Broad application of mosaic theory blocks social network surveillance Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) Enter the mosaic theory with a focus on intimate associations . n51 While individual social networking communications would not be protected because of the Third Party Doctrine, in the aggregate, these communications are more than just a bundle of transmissions - together they are constitutive of an intimate relationship. If courts care about the government not interfering in these relationships in the face-to-face context, via direct application of intimate associational rights, they should similarly care about these relationships on the Internet when assessing Fourth Amendment protection. n52 This means finding that the underlying social networking communication passes the Fourth Amendment reasonable expectation of privacy test, because it is part-and-parcel of an intimate relationship. n53 Page 150 Terrorism More court trials regarding mosaic theory provide terrorists crucial information to plan attacks Davis and Albert, 11 (Charles and Michelle, Professor of Journalism at University of Missouri, April 2011, Vol. 25, No. 2, Continuum: Journal of Media & Cultural Studies, “Using secrecy to fight terrorism? Access, homeland security, and the ‘mosaic theory’ as a rationale for closure”, EbscoHost, amp) What is odd about this order is the thought that reclassifying previously released information could prove beneficial to national security, especially as this happened within the internet boom. Once information is available on the internet, it is extremely difficult to remove it completely. As the information was once available to the public, reclassifying it does not effectively protect it. The courts, however, consider mosaic theory a privileged defence of withholding information, and often defer to it in FOIA cases. Judicial deference to the mosaic theory requires three steps: support, or the evidence needed to back up the argument; specificity, or the extent the government must tailor the argument to fit the information in question; and plausibility, or the extent the argument fits the requirement of showing potential harm (Pozen 2005). In fact, the government believed that, because of the mosaic theory, information released during trials for the people accused in the 1993 World Trade Center bombings could have given alQaeda, and other people or groups involved, the knowledge necessary to conduct the attacks on 11 September 2001 (Pozen 2005). Mosaic making is key to stop terrorism—wouldve prevented 9/11 Pozen, 7 (David, JD Yale Law School, M. Sc. Oxford University, 2007, Yale Law Journal, “The Mosaic Theory, National Security, and the Freedom of Information Act”, http://www.yalelawjournal.org/pdf/358_fto38tb4.pdf, amp) As the mosaic theory has risen to prominence in the Bush Administration’s paradigm shift away from public disclosure, the theory itself has not changed; rather, the national security landscape has changed, and the theory has taken on new salience as a result. The dangers of adversarial mosaic-making were brutally underscored by the 9/11 attacks, as “[i]t is widely believed . . . that the public criminal trials of the men who attempted to blow up the World Trade Centers in 1993 made available information about government techniques for monitoring terrorists, as well as critical information about what it would take to attacks also highlighted our government’s failure at defensive mosaic-making , at “connecting the dots” that would have predicted the hijackings.110 Shifting the mosaic-making advantage back to the federal government will not be easy, however. The government now generates and manages more actually bring the towers down.”109 Conversely, the information than ever before, and is increasingly doing so in digital form, which permits users to process, share, and disseminate the data more easily. The Internet provides a ready medium for adversaries to locate and transfer this information, while datamining technologies, becoming more powerful and accessible over time, can help them extract useful knowledge from otherwise unwieldily large or complex data sets.111 Under Page 151 FOIA, agencies must provide documents in “any form or format requested” that is “readily reproducible,” including electronic formats.112 Courts have not directly considered whether the mosaic theory becomes more significant when applied to electronic records, but the Supreme Court has acknowledged in discussing personal privacy that, because the value of information increases with the facility with which one can use it, computer compilations pose special dangers.113 More broadly, in the post-9/11 national security landscape, intelligence gathering and analysis have become perhaps our most important strategic assets,114 while critical infrastructure data has become a key liability;115 communications and computer technologies have increased the volume, accessibility, and manipulability of sensitive knowledge and enabled more sophisticated scheming;116 new types of adversaries—more dispersed, harder to identify, and possibly more ruthless than their predecessors—have proliferated; and the specter of another attack on U.S. soil has framed political debate and dictated policymaking. Federal agencies are being pressed to expand information-sharing with each other,117 but to reduce informationsharing with the public.118 All of these developments have served to vitalize the role of information in national security strategy. That role, however, is characterized by uncertainty: As information implicating national security has become more heterogeneous and more abundant, we increasingly do not know what information matters, or who has it, or how to control it. As the Director of the University of Maryland’s Center for Information Policy has observed, “there are thousands of nodes of information in the United States and each does not know what it does not More than ever, mosaics usable for terrorism and counterterrorism abound. Seen in this light, the narrowing of FOIA and the expanding role of the know or what it needs to know.”119 mosaic theory become, normative judgments aside, more understandable. Congressional delegation is key to counterterrorism Pozen, 7 (David, JD Yale Law School, M. Sc. Oxford University, 2007, Yale Law Journal, “The Mosaic Theory, National Security, and the Freedom of Information Act”, http://www.yalelawjournal.org/pdf/358_fto38tb4.pdf, amp) If today’s terrorist threats are characterized by their simultaneous intensity and uncertainty, judicial reluctance to question mosaic theory claims might be seen as a rational response. Decisionmaking about information disclosure has always been constrained by the practical impossibility of measuring the costs and benefits of openness versus secrecy. This informational deficit exacerbates a tension that has always existed in FOIA between the goal of promoting transparent, accountable government and the imperative not to endanger national security in the process. Yet because the potential costs of an ill-advised FOIA disclosure, and the difficulties of evaluating what might constitute an illadvised disclosure, are seen to have increased after 9/11, the balancing calculus has shifted. Adversarial mosaic-making now seems especially dangerous and unpredictable. In response, post-9/11 courts applying delegation have upheld agencies’ highly speculative, highly generalized mosaic claims when disclosure would pose no evident danger; they have demanded little from the agencies in the way of support, specificity, or plausibility. Delegation errs, more so than deference, on the side of nondisclosure. In its caution, it instantiates a conservative vision of information policy, wherein executive agencies, not courts, should control information, and more control is presumed safer. For those who advocate utmost judicial deference to the Executive in times of emergency, and who see the present as such a time, delegation holds obvious appeal. Lest they compromise the War on terror, decisions like CNSS, North Jersey Media, and ACLU selfconsciously integrate the mosaic theory into, in the approving words of constitutional scholar John Yoo, “ a deferential standard of scrutiny that provides the political branches with the flexibility to Page 152 conduct war successfully.”180 By empowering the Executive with greater control over information, delegation sacrifices liberty, in the form of governmental transparency, for the sake of security. As with the shift in power from judiciary to executive, many accept this tradeoff in a time of emergency. From its coinage in Marchetti, Halkin, and Halperin, the mosaic theory has been a vehicle for increasing judicial deference. Now that this heightened deference accommodates the War on terror, it may—irrespective of the exceptional mosaic concerns arising after 9/11—appear particularly prudent and legitimate. An additional argument for delegation is prudential in a narrower sense: It economizes on administrative and judicial effort. FOIA requests routinely encompass thousands of pages of government records. Scouring all requested records for possible mosaics may consume substantial agency resources, especially if the agency does not know what information (and information technologies) adversaries possess. Although courts have traditionally been sensitive to such administrative burdens,181 they have demanded that agencies articulate a reasonably specific justification for each document or section withheld.182 Post-9/11 courts applying delegation, by contrast, have allowed information withholding under generic, categorical descriptions of mosaic consequences—in CNSS, recall, the government defended its mosaic claims with the exact declaration it had used in Detroit Free Press, and won. In a few pages of argument, that declaration swept all information about all detainees under the mosaic theory, sparing the government the burden of having to “describe, for each detainee or reasonably defined category of detainees, on what basis it may withhold their names and other information,” as Judge Tatel’s “more particularized approach” would have demanded.183 The D.C. Circuit was, in turn, spared the burden of having to evaluate such descriptions, which may have required extensive in camera review. The difference between deference and delegation is one of degree here, rather than kind; the mosaic theory deals in aggregates and conjectures and so can always act as a laborsaving device when the government does not control all of the mosaic’s components. Relative to standard deference under FOIA national security review, however, delegation saves more effort by extracting nearly all “particularity” from the process of asserting and analyzing mosaic defenses . The government needs mosaics to identify terrorists Denniston, 9 (Lyle, professor of journalism, legal journalist for 50 years, SCOTUS Blog, “Analysis: Dismantling a detention case, point by point”, http://www.scotusblog.com/2009/05/analysis-dismantling-a-detention-case-pointby-point/, amp) Kessler allowed the government to proceed on what is called “the mosaic theory” rather than requiring it to prove directly that Ahmed has been a terrorist — a much harder task. The “mosaic theory,” often used by the intelligence community to build a case, provides that single pieces of evidence that may not be strong when looked at singly can be examined together to form a convincing pattern — here, a pattern of terrorist activity. Page 153 Third Party Doctrine Adopting mosaic theory prevents use of the Third Party Doctrine Bedi, 14 (Monu, Assistant Professor, DePaul University College of Law. A.B. Dartmouth College, M.Phil. University of Cambridge, J.D. Harvard University, Boston University Law Review, December 2014, 94 B.U.L. Rev. 1809, “Social Networks, Government Surveillance, and the Fourth Amendment Mosaic Theory”, lexis, amp) 2. Rejection of the Public Disclosure and Third Party Doctrines The most troubling part of adopting the mosaic theory is that it requires the abandonment of, or dramatic alterations to, the Doctrines. The basic problem is the inherent conflict between the first and second models of reasonable expectation. While the Doctrines embrace a per se rule focusing solely on disclosure and why this vitiates privacy, the mosaic theory rests on society's opinion and what it deems reasonable. n223 Consider the Public Disclosure Doctrine. The fact that public movements are not protected under the Fourth Amendment is critical to law enforcement investigations. n224 Visual warrantless surveillance remains a central part of police surveillance. n225 It is not clear to what extent these practices will remain constitutional with the introduction of the mosaic theory. For instance, it is common for officers to track vehicles and aggregate information from various sources over a period of time. n226 As Gray and Citron point out, the "mosaic theory puts these practices and the line of doctrine endorsing them in obvious jeopardy, particularly when officers are too successful and their investigations produce too much information." n227 This danger is compounded by the fact that law enforcement may use a combination of visual and technology-based surveillance (a la Knotts) when investigating a suspect. "How, after all," ask Gray and Citron, "are we to distinguish "between the supposed invasion of aggregation of data between GPS-augmented surveillance and a purely visual surveillance of substantial length'?" n228 It won't do here to simply say that a specific duration of technology-dependent surveillance violates the expectation of privacy. The problem is that the Public Disclosure Doctrine treats all public movements the same, regardless of how much information is disclosed or how long it is observed. n229 To carve out exceptions based on what society thinks is unreasonable leaves vulnerable investigative techniques that are essential to effective law enforcement . The Third Party Doctrine would also be on shaky ground. Here, too, the [*1843] mosaic theory would upset the voluntary disclosure principle that stands at the heart of this doctrine. n230 Shifting the focus to what society or an individual deems reasonable (the first model of reasonable expectation of privacy) would surely frustrate the use of undercover informants or other surreptitious data collection techniques that do not require a warrant. Imagine a scenario where an informant is deep undercover for a significant period of time gaining the trust of a suspect. Or imagine an informant who dupes a suspect into allowing her into her home and disclosing private and incriminating information. Or perhaps the government simply acquires a wealth of financial records from a suspect's bank. Currently, all of these types of law enforcement tools do not trigger Fourth Amendment protection because the individual voluntarily discloses the information to another person or entity. n231 However, under the mosaic theory, none of these tactics are secure . n232 Societal expectations may find that these Page 154 methods, too, impinge on Fourth Amendment rights as they involve unreasonable duplicity and reveal private information. Police would thus find themselves in the new position of having to secure a warrant based on probable cause before engaging in these practices. For some, this conclusion may be welcomed, particularly in today's technological world where disclosures to various entities and individuals have become ubiquitous. n233 Justice Sotomayor, in fact, raises this possibility in her concurrence. n234 This Article does not take such a drastic approach, nor would such a course be desirable. Any such rejection would come at the cost of jettisoning or severely curtailing essential law enforcement investigative [*1844] techniques that have historically not been subject to warrant and probable cause requirements. n235 Page 155 Congress CPs Page 156 Notes Oversight Counterplan --- basically establishes a Congressional oversight committee to make sure that the data isn’t used for blackmail or violating privacy who reviews whether data collecting was legitimate after the fact. If you want to get around solvency deficits, consider establishing an independent agency to review decisions that’s not selected from Congresspeople. Penalties Counterplan --- this just provides an enforcement mechanism for the ExPost/Oversight Counterplan, creating penalties that arguably create disincentives to bad oversight. Terry Stops Counterplan --- rather than the aff’s narrow mandate, this lets us maintain broad surveillance for a short period, and then causes narrower surveillance in the future if we find out that someone’s a terrorist. The Oversight/Ex Post counterplan is the only one that really solves international perception/credibility advantages, like PRISM. Terry Stops are good against affs that target specific groups, like the Islamophobia or LGBT aff. Funneling CP = high people see first, disclose necessary to lower, etc. Solves a lot of the problems with leaks. The Other Planks are reasonably self-explanatory and are just explanations and clarifications of how an oversight committee could/should be constructed. Note: TSP = Terrorism Surveillance Program, NSA warrantless wiretapping created by Bush Page 157 Expost/Oversight CP Page 158 1NC Oversight CP An oversight committee solves --- it holds the Executive accountable and forces them disclose illegal surveillance Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka E. Oversight and Reporting Requirements Congress could by law require the Executive to report to congressional oversight committees all warrantless searches and electronic surveillance conducted in the United States. Indeed, today the Justice Department is required to tell Congress the total number of FISA warrant applications granted, modified, and denied. n200 Without warrants, the need for oversight is even greater; thus, Congress should require the Executive to report to it each time a warrantless domestic intelligence search occurs. Extending this requirement to the domestic intelligence context will ensure that an independent body reviews all executive actions - even those that would otherwise never come to light because of failure to prosecute. Finally, Congress should disclose any illegal surveillance to the subjects of that surveillance so that they can seek redress in court or in an administrative proceeding. Page 159 2NC Disclosure Specifically disclosing illegal search material prevents abuses in criminal trials Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka Currently, 50 U.S.C. § 1806(e) permits any person against whom FISA acquired information is or has been introduced in a criminal prosecution, to make a motion to "suppress the evidence obtained or derived from such electronic surveillance on the grounds that - (1) the information was unlawfully acquired; or (2) the surveillance was not made in conformity with an order of authorization or approval." n196 However, the acquired information is reviewed in camera and ex parte by the court and the evidence is disclosed to the defendant only where "such disclosure is necessary to make an accurate determination of the legality of the surveillance." n197 As asserted by the D.C. Circuit Court of Appeals in United States v. Belfield, disclosure of FISA acquired information may only occur where, upon initial review by the FISA court, the legality of the surveillance may have been complicated by "indications of possible misrepresentation of fact, vague identification of the persons to be surveilled, or surveillance records which include a significant amount of non-foreign intelligence information, calling into question compliance with the minimization standards contained in the order." n198 The Belfield court further clarified that the rarity of such [*227] disclosures to the targets of FISA surveillance is appropriate in light of the delicate and sensitive nature of foreign intelligence information. n199 While the interest of the government in maintaining secrecy regarding foreign intelligence gathering tactics is certainly valid, it cannot outweigh the interest in ensuring that a defendant receives a fair trial and is informed of the accusations against him, as guaranteed by the Sixth Amendment. n200 In Belfield, the court opined that the privacy rights of the individual, though not protected through mandatory disclosure of the evidence against him, were protected through the procedural oversight of FISA surveillances provided by the three branches of government. n201 However, in light of the numerous procedural and substantive flaws in FISA discussed in Part V and the factual misrepresentations made by the FBI in FISA applications, the current procedural oversight is ineffective in protecting the privacy interests of Americans and permits the abuse of FISA surveillances. n202 To remedy these issues, two possible solutions are available to the government. The first option is for Congress to amend FISA to ensure that the DOJ cannot use FISA surveillances as a means to escape the Fourth Amendment. Such amendments should include the reestablishment of the primary purpose standard or establishment of the sole purpose standard, defining those crimes which threaten national security, and allowing the FISA court to review the facts in the FISA order application to verify the connection with a foreign agent. The second option available is for an amendment to FISA bestowing upon every defendant prosecuted based on evidence obtained through FISA surveillances the ability to review the information used against him or her. Currently the law gives a FISA judge discretion to allow defendants [*228] to view the evidence against them. n203 By revoking the judge's discretion to disclose the information to the defendant and allowing for the evidence to be presented to the defendant upon the making of such a motion to disclose, the defendant would be able to make an informed challenge to the legality of the FISA surveillance against him, thereby protecting the integrity of the criminal justice system and discouraging wrongful convictions. To ensure that such an amendment will not create an unnecessary threat to national security, further procedures should be imposed to ensure that only the defendant and his attorney are able to review the evidence, and then only in a secure room from which the materials may not be removed. Additionally, any information revealing procedures and conduct of the government, not including the Page 160 specific information acquired, which is not available to the public, defendant. should be redacted and not made available to the Page 161 2NC Oversight Congressional oversight empirically limited abuse --- unfortunately, it expired in 2012 Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka This Article suggests that while there is potential for abuse if government officials violate the clear wording of the FAA (which allows warrantless surveillance of non-US persons reasonably believed to be outside the United States to gather foreign intelligence), the FAA contains enough ex post review mechanisms (in the forms of Congressional oversight committees and various inspectors general) that the Obama administration should allow the FAA to operate as-is, and reevaluate its effectiveness and protection of civil liberties when it expires in 2012 . At worst, ex post review is a terminal backstop to their solvency deficits Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka 2. Policy Benefits. - A proponent of a national security exception notes that "the repeal of FISA ... would simply effectuate the nation's return to its previous tradition." n114 Yet the obvious retort is that the very abuses detailed in the Church Committee report were a major product of that tradition. Still, the old tradition did have some benefits that can be obtained by coupling the ex post reasonableness role of reviewing courts with the political checks described above. For one, rather than shielding meaningful inquiry, as ex ante review can, ex post review may produce "a renewed focus on Fourth Amendment principles " n115 by both the judicial and political branches . Indeed, the more developed factual setting available in ex post review would help with the effort to define reasonableness. Further, it could be argued that since only a small number of people are likely to be affected by surveillance, and especially given that those affected are likely to be disfavored or underrepresented groups such as members of minority religions or immigrants, the political process cannot be trusted to perform oversight. Yet ex post judicial review would remain a powerful check if the government seeks to use FISA-gathered information in other legal settings, such as criminal trials , habeas corpus proceedings , or motions for prospective relief. Ex post reasonableness review thus provides an important backstop to the oversight process. A bipartisan, independent committee overcomes their solvency deficits Sugiyama and Perry 6 --- J.D.s from UMich Law School (Tara and Marisa, “THE NSA DOMESTIC SURVEILLANCE PROGRAM: AN ANALYSIS OF CONGRESSIONAL OVERSIGHT DURING AN ERA OF ONE-PARTY RULE”, 40 U. Mich. J.L. Reform 149, Lexis)//trepka Introduction On December 16, 2005, the New York Times sounded a fire alarm n1 when it revealed that, in response to the September 11, 2001 attacks, President George W. Bush had issued a secret executive order permitting the National Security Agency (NSA) to conduct warrantless surveillance on individuals within the United States to unearth nascent terrorist activity. n2 The ex ecutive o rder n3 purportedly authorized the NSA to monitor the telephone and email messages of tens of millions of unsuspecting individuals in its effort to track down links to Al Qaeda. n4 Almost immediately, [*150] various interest groups began to question the constitutionality of the NSA domestic surveillance program and to challenge whether the scope of the program violates the Foreign Intelligence Surveillance Act of 1978 (FISA). n5 Congress surveillance program largely by responded to the disclosure of the NSA domestic shirking its oversight duties . Undaunted by a unified executive branch that shunned oversight, n6 Democratic members of Congress repeatedly pressed for a comprehensive investigation into the surveillance program. n7 Lacking support from a majority of the Republican members of Congress, however, Democratic efforts Page 162 at oversight made little headway in breaching the unitary executive wall. n8 Part I of this Note introduces theoretical models that Congress may employ to conduct oversight of executive branch activities such as the NSA domestic surveillance program. Part II situates the NSA program within the context of FISA and the USA PATRIOT Act, discussing the controversy surrounding the legality of the program. Part III examines the strategy employed by the majority party, the minority party, and interest groups in seeking to conduct oversight of the NSA program, and the response of the executive branch to such efforts. Part IV concludes by analyzing lessons from the fire-alarm model and proposes alternative methods of congressional oversight. As illustrated in the case of the NSA domestic surveillance program, when a single party controls both the executive and the legislative branches, the fire-alarm model fails to provide sufficient congressional oversight, and short of future elections altering the balance of power, Congress should seek new methods that more readily engage bipartisan support and judicial review to oversee secret executive programs more effectively . Oversight increases intelligence effectiveness --- Congress’ institutional check prevents groupthink and solves public support Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka VI. The Future of Intelligence Oversight A. Current Proposals for Intelligence Oversight Reform As many commentators have agreed (and at least one noted), "the American intelligence infrastructure is in the midst of its most radical overhaul since the formation of the modern Intelligence Community following World War II." n310 Unlike intelligence reform seeking to reign in the rogue elephant, today's reform concerns "how to get [intelligence] agencies to be more aggressive - and how to get policymakers to use the results to better effect." n311 Hence, the debate over intelligence reform has centered on reforming those institutions or organizational impediments that hinder intelligence operations, rather than creating and empowering structures to ensure operations are conducted within the bounds of the law. n312 Oversight, however, is intrinsically tied to the conduct of intelligence operations. Conventional wisdom establishes an inverse relationship between oversight and operations : the more oversight, the more restricted the operations. This is not, however, a universal tenet. As an initial matter, oversight offers a broader perspective on the development and execution of intelligence operations. That is to say, the inclusion of a neutral party offers a check on the dangers of organizational group-think. This quality of oversight was recognized as early as 1956 when President Eisenhower organized the predecessor to the President's Foreign Intelligence Advisory Board, whose purpose [*761] is to provide "advice to the President concerning the quality and adequacy of intelligence collection, of analysis and estimates, of counterintelligence, and of other intelligence activities." n313 Oversight also serves the less intuitive role of actually facilitating intelligence operations . The American public is much more willing to permit unfettered and robust intelligence operations when they know institutional checks are in place to ensure operations are conducted in accordance with applicable laws and generally accepted public mores. n314 As discussed at length above, when this assumption of legality and morality is corrupted, the public reaction has proven formidable. n315 Thus, it is in the interests of the Intelligence Community to be subjected to a certain degree of oversight. n316 Congress, as a representative of the people, necessarily serves as the Intelligence Community's "honest broker." In this role, Congress must walk a fine line between beneficial and detrimental oversight. The history of congressional oversight, marked by wild oscillations of interest, demonstrates the inherent difficulty in this task. Following 9/11, various commissions and commentators found a myriad of issues with Congress's role in intelligence oversight, suggesting Congress has not yet found the appropriate balance. Solves executive abuse Rahdert 7 --- Professor of Law (Mark, “DOUBLE-CHECKING EXECUTIVE EMERGENCY POWER: LESSONS FROM HAMDI AND HAMDAN”, 80 Temp. L. Rev. 451, Lexis)//trepka Some might argue that the Court's insistence on affirmative congressional authorization was an unnecessary obstruction of executive authority, or that it amounted to an unnecessary formalism. Once again, I disagree. Requiring the President to get congressional approval is neither rude obstructionism nor formalistic cosmetics. It is part of the constitutional plan . Shared authority is as much a part of that plan as separation of powers. In the case of the emergency power double check, it ensures the coalescence of the two elected branches of government in all but purely temporary responses to crisis situations. As events transpired, one could argue that Hamdan, in particular, obliged Congress, by enacting the MCA, to take a measure of direct responsibility for the military justice aspects of the war against terror, effectively giving the people a voice about that war, and how it is being waged, in the 2006 elections. To Page 163 the extent the 2006 elections can be seen as a referendum on the handling of the war against terror, they were at least partly a referendum against some of the [*488] executive's more extreme measures in dealing with enemy combatants. In the future, that voice could be critical in preserving democracy from an autocratic presidency . n226 Key to preventing nuclear war Forrester 89 (Professor at Hastings College of the Law at University of California, 1989 [Ray, George Washington Law Review, August] [On the basis of this report, the startling fact is that one man alone has the ability to start a nuclear war. A basic theory--if not the basic theory of our Constitution--is that concentration of power in any one person, or one group, is dangerous to (hu)mankind. The Constitution, therefore, contains a strong system of checks and balances, starting with the separation of powers between the President, Congress, and the Supreme Court. The message is that no one of in what is probably the most dangerous governmental power ever possessed, we find the potential for world destruction lodged in the discretion of one person. them is safe with unchecked power. Yet, Proactive role prevents abuse Sugiyama and Perry 6 --- J.D.s from UMich Law School (Tara and Marisa, “THE NSA DOMESTIC SURVEILLANCE PROGRAM: AN ANALYSIS OF CONGRESSIONAL OVERSIGHT DURING AN ERA OF ONE-PARTY RULE”, 40 U. Mich. J.L. Reform 149, Lexis)//trepka Under the "police-patrol" model of congressional oversight, Congress takes a proactive role in examining actions of the executive branch to unearth evidence of maladministration. n12 Members of Congress may conduct this direct form of oversight by requesting documents from the executive branch, holding hearings, and commissioning reports. n13 The goal of this form of oversight is for members of Congress to identify , dissuade , and remedy any executive branch violations of legislative goals. n14 Page 164 AT: DA to Oversight Reform The link’s non-unique --- attempts at oversight reform are inevitable, it’s a question of effectiveness Harrington 7 --- J.D., Albany Law School of Union University (Alexandra, “PRESIDENTIAL POWERS REVISITED: AN ANALYSIS OF THE CONSTITUTIONAL POWERS OF THE EXECUTIVE AND LEGISLATIVE BRANCHES OVER THE REORGANIZATION AND CONDUCT OF THE EXECUTIVE BRANCH”, 44 Willamette L. Rev. 63, Lexis)//trepka F. Post-Cold War The immediate post-Cold War period was a time of relative relaxation, punctuated by the first Gulf War and several terrorist attacks within and beyond the United States. Support for the first Gulf War was broad-based and Congress was amenable to declaring war and allowing the Executive to conduct the war largely unfettered by congressional attempts at involvement. n118 President William Clinton's tenure saw the "peace dividend" idea applied by the Executive and the Legislature to facilitate the downsizing of the United States military. n119 Although controversial within largely conservative circles and among members of Congress from districts which were threatened by economic losses as a result, there was not a great deal of tension between the executive and the legislative branches regarding the decision to downsize. n120 Al-Qaeda's early attempts to damage United States-related targets, such as the U.S.S. Cole, the U.S. Embassy in Nairobi, Kenya, and even the 1993 World Trade Center bombing, attracted media attention but were largely handled within the U.S. intelligence community - and, in the case of the World Trade Center bombing, by the Justice Department and the court system - and there were few congressional attempts to encroach on the powers vested in the Executive in order to reign in this new threat to American stability. The sense of increased security which pervaded the United States during the initial post- Cold War period was shattered by the Al-Qaeda attacks of September 11, 2001. The September 11th attacks were quickly followed by a broad-based declaration of war against terrorists in general, and Afghanistan in particular. n121 Congress's unofficial declaration of war was open-ended and allowed the Administration great latitude in the pursuit of an atypical war. n122 The September 11th attacks also resulted in the enactment of the USA PATRIOT Act, granting the executive branch updated powers for the [*80] upcoming war on transnational terrorism. n123 In the wake of September 11th and the perceived governmental failures which became part of the public understanding of the attacks of that day, Congress has repeatedly attempted to find a way to reform its intelligence oversight structure. n124 However, no concrete revision system has been proposed or debated, and there are widely differing opinions over any method of reorganizing the congressional oversight committee structure as it relates to the Executive in general and the intelligence community in particular. n125 Page 165 AT: Judicial Bias Ex Post review is net better than warrant requirements Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka E. Warrants Protect Against Police Perjury and Judicial Bias Police perjury and judicial bias in ex post review are two significant problems that some argue the warrant requirement alleviates. By requiring review before the search, warrants ensure that the decision to approve a search is based upon the officer's knowledge at the time of the search and not upon reasons invented by that officer to justify the search at a suppression hearing or civil damages action. n159 Thus, many deem ex post review inadequate because it frequently is based upon the officer's recollection of the information he had at the time, which is manipulable. n160 Moreover, judicial bias may infect the ex post review process because it almost always occurs in the context of a suppression hearing. n161 The exclusionary rule, n162 and the fact that the police have proffered incriminating evidence against the suspect, creates a bias on the part of the judge to admit the evidence because if she does not, "the criminal is to go free because the constable has blundered." n163 This, combined with the incentive provided to the police to perjure themselves, n164 makes it likely that an unconstitutional search will go without a remedy. n165 That is, where the officer who conducts a search lies about the true rationale for his search, and the judge is biased in favor of that officer, the likelihood that an unconstitutional search will go unremedied increases substantially. Thus, both the police perjury and judicial bias problems provide strong support for maintaining the warrant requirement for domestic intelligence searches because without the warrant requirement, after-the-fact review at a damages action or suppression hearing would provide the main judicial review of these searches. If this ex post review is inadequate because of perjury or bias, then the Fourth Amendment's substantive protections would be rendered meaningless. Ultimately, however, neither of these arguments support maintaining the warrant requirement for domestic intelligence searches. First, the inherent [*372] bias against the searched in the ex parte warrant application process is greater than the potential for bias in after-the-fact review. Second, placing a higher evidentiary burden on the government to justify a warrantless search could alleviate any police perjury problems . Third, even if such bias and perjury occurs with enough frequency to seriously undermine ex post judicial review, the legitimate need of the government to obtain vital intelligence to prevent terrorist attacks outweighs the costs of such bias and lying. These responses are each discussed in turn below. Specifically, reverses bias and prevents perjury Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka First, the argument that warrants are necessary to protect against judicial bias in ex post review presumes that this bias outweighs the inherent bias in a warrant application . Warrants are issued before a search occurs, ensuring that they are based upon the officer's knowledge at the time and not on fictional reasons made up after the search to justify it. n166 Warrant applications are ex parte, however: the subject of the search has no say or representative to defend his or her position. n167 Thus, unlike after-the-fact review, warrant applications are inherently biased towards the government because the issuing magistrate only hears its side of the story . As noted above, when combined with deferential review of issued warrants, current policy defers to that biased judgment. n168 Adversarial review after the fact, then, ensures that the judge hears both sides of the story in evaluating the legality of a search. n169 And when that judge is unbiased, she can fairly view the arguments from both sides, not just one. Moreover, the adversarial process itself ensures that if the searching officer is lying, his justification for the search will be challenged by counsel . n170 In short, although bias and police perjury in after-the-fact review are problems, the bias inherent in ex parte warrant applications is just as significant. As such, the problem of judicial bias in after-the-fact review does not justify the warrant requirement. Page 166 Second, any concern that a police or intelligence officer will lie or distort her rationale for conducting a search in after-the-fact judicial review could be alleviated by placing a higher evidentiary burden on the Executive to justify a warrantless search. n171 Courts could adopt a rule that an intelligence [*373] officer's recollection of the events leading up to the search is not on its own enough to satisfy the Fourth Amendment's reasonableness standard. By requiring further evidence to demonstrate the government's knowledge prior to the search, the courts will ensure that a testifying intelligence officer is not making up a rationale ad hoc to justify an unreasonable search . Such corroboration could include emails or correspondence whose date can be authenticated or other time-verifiable evidence, so that the government's knowledge prior to the search could be ascertained. Importantly , though, this evidence would be necessary not for the government to show probable cause , as in a warrant application, but instead for a court to merely determine the search's overall reasonableness . Although one might respond that this would just shift the police perjury back further in time, this argument is unpersuasive because before the search occurs the officer does not know what it will turn up, making it difficult if not impossible for him to concoct a lie that will match what he actually finds during the search. Moreover, even if one worried that placing a higher burden on the government to justify a search would actually encourage police perjury because officers would need to fabricate more evidence to justify a search, requiring evidence that can with great certainty prove that the government had legitimate reasons ex ante to conduct a search mitigates this problem. Warrants ex post review. are simply not a prerequisite to protecting against police perjury in Page 167 AT: L/Flexibility DA A specific oversight committee solves, but avoids the flexibility net benefit Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka G. Other Solutions Congress or the Court doubtless could impose other solutions to protect Fourth Amendment interests in the absence of the warrant requirement. For instance, the Court could require heightened scrutiny of searches that implicate the First Amendment, n206 or it could require some corroboration of an officer's recollection of events that gave him reason to believe a search was reasonable. n207 Congress could establish an independent agency whose sole job is to police the intelligence agencies and ferret out illegal activity. For our purposes, the most important thing to note is that many, if not all, of these solutions could better protect Fourth Amendment interests than traditional warrants, while giving the Executive the authority and flexibility it needs to combat domestic national security threats. Page 168 AT: Not Credible Ex-post review locks in procedural safeguards that generate credible spillover Steinberg AND Estrin 14 --- Dean of Maxwell School of Citizenship and Public Affairs at Syracuse University AND Postdoctoral Associate at Yale (James and Miriam, “Harmonizing Policy and Principle: A Hybrid Model for Counterterrorism”, 7 J. Nat'l Security L. & Pol'y 161, Lexis)//trepka Such a formal process would also facilitate another important procedural safeguard , the use of ex post review of practices, both by the executive branch and Congress . The President's Intelligence Advisory Board, a group of outside independent intelligence advisors, could serve such a role within the executive branch. The executive branch would also share the intelligence record with the relevant committees of Congress, through the House and Senate intelligence committees for Title 50 operations and the armed services committees for Title 10 operations. The President is required by law to "ensure that the congressional intelligence committees are kept fully and currently informed of the intelligence activities of the United States," n208 but has the option to limit the reporting to the "Gang of Eight"--the leaders of the two parties in the Senate and House plus the chair and ranking minority members of the intelligence committees -- "[i]f the President determines that it is essential to limit access to the finding to meet extraordinary circumstances." n209 Because these individuals cannot share the info rmation with other members of their committees, discuss it with legal counsel, or even take notes during meetings, this avenue is not the most effective mechanism for congressional oversight of ongoing counterterrorism operations. n210 To make congressional review meaningful, the default of reporting to the full intelligence committees should be respected. These ex post reviews will help recalibrate policy in favor of detentions and away from targeting, and counter temptations to rely on lethal operations that are outside the review of courts. When the President announces that "America [*205] does not take strikes when we have the ability to capture individual terrorists; our preference is always to detain, interrogate, and prosecute," n211 it will be the responsibility of these groups to evaluate this claim against the dossier of intelligence reports the executive branch used to reach individual targeting decisions. Were alternatives to targeting explored, and was there a serious consideration to pursue them? How was the decision to target ultimately justified? These determinations are difficult, but our system enables them to be made through the checks and balances important assurances that the principles are not only articulated but are being respected , without interfering with the need for timely decision and while protecting confidentiality of sources and methods. Internal oversight through independent experts and external oversight through the democratically-elected houses of Congress will help ensure that targeting decisions are actually being carried out in line with the presidential guidelines, domestic and international law , and constitutional principles. of two separate political branches. These reviews can provide Page 169 AT: Theory Oversight is the key question for surveillance policymaking Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka VII. Conclusion Quite plainly, the balance of executive autonomy and legislative oversight has not been resolved. The revelation of the NSA program plainly illustrates this and perfectly reflects recent history which finds a predictable sequence: public support for operations followed by either an intelligence/military failure or revelations of intelligence improprieties, followed by public demands for regulation and restraints. International and domestic events, the conduct of the intelligence agencies, and the perceived threat to national security combine to fuel the public climate that in turn shapes the political response. The key to effective policy making in regard to intelligence regulations is striking a balance between the short-term national security needs of the country, the long-term national security needs of the country, the liberties guaranteed by our Constitution, and the desires of the American public. Page 170 AT: Unconstitutional Congressional oversight of the Executive is constitutional Sugiyama and Perry 6 --- J.D.s from UMich Law School (Tara and Marisa, “THE NSA DOMESTIC SURVEILLANCE PROGRAM: AN ANALYSIS OF CONGRESSIONAL OVERSIGHT DURING AN ERA OF ONE-PARTY RULE”, 40 U. Mich. J.L. Reform 149, Lexis)//trepka I. Theoretical Models of Congressional Oversight The Constitution does not explicitly vest Congress with plenary power to conduct investigative oversight of the executive branch. n9 The Supreme Court, however, has interpreted the Constitution as providing Congress with inherent power to oversee executive [*151] branch activities that may violate the will of Congress. n10 Accordingly, two primary models have emerged to guide members of Congress through the execution of their oversight duties: the police-patrol and the fire-alarm models of congressional oversight. n11 Page 171 AT: Unwilling Congress will do it --- depth report proves Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka The 9/11 Commission's report must be distinguished from the report produced by the congressional committee examining the events of 9/11. This latter report, entitled Joint Inquiry into Intelligence Community Activities Before and After the Terrorist Attacks of September 11, 2001 (Joint Inquiry Report), provided markedly different recommendations. n321 Absent among their findings, however, is any critical self-analysis. Of the report's sixteen "systemic findings" and four "related findings," none expressly discusses congressional failings or inefficiencies. n322 Further, one commentator has criticized the report as "a dismal failure." n323 The report is not, however, very presence of a robust report indicates a congressional willingness to engage in some degree of oversight. The 9/11 Commission fulfilled the without merit. As an initial matter, the desires of the vast majority of the American public; thus, the Joint Inquiry Report could have easily been written off as surplusage. Secondly, as discussed below, the Joint Inquiry Report does provide some valuable recommendations . And finally, the Joint Inquiry Report provides valuable insight into the mechanics of the intelligence committees. Through the individual statements of a number of junior senators, one can readily identify dissent and inefficiencies within the committees. n324 Page 172 Funneling CP Page 173 1NC Funneling Information funneling creates sufficient oversight and transparency Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka 2. Initial Reflections on Maximizing the Benefits and Minimizing the Costs of Secrecy and Openness Through Information Funneling Rules Information funneling rules offer the possibility of compromise between secrecy's costs and benefits. The implicit goal of such compromise is meaningful oversight that serves democratic and pragmatic ends while avoiding the costs to those ends of excessive transparency . The theoretical connection between information funneling and this goal is evident. Yet problems and uncertainties about funneling remain, as the NSA surveillance controversy exemplifies. While fool-proof rules surely are unattainable, improvements may be achieved through better attention to the theoretical concerns and goals underlying funneling and the connection between those factors and funneling rules' details. This section suggests several considerations that ought generally to inform the creation and application of funneling rules. a. Determining Who Should Receive Funneled Information Directives regarding to whom information is funneled should be reassessed to determine whether they match funneling's underlying purposes. The need for such reassessment is illustrated by the NSA surveillance controversy. It is reflected in the conflict over the adequacy of notifying only the Gang of Eight, rather than the full intelligence committees, of the program. n108 It also is reflected indirectly in post-revelation conflicts over whether the Senate Intelligence Committee should, like the Senate Judiciary Committee, hold hearings [*1071] on the program. n109 The latter suggests a related question over how to determine which committees should receive ongoing notice of intelligence activities. Two sets of concerns must be balanced to answer these questions. On the one hand, restrictions on who receives notice must not substantially undermine the very purpose of oversight. One complaint about Gang of Eight notifications, for example, is that the Gang of Eight as a group lacks the power to take recourse in response to what they've been told. n110 A closely related complaint is that the group's small size, combined with the absence of staffers in most briefings, makes meaningful deliberation and even adequate grasp of the issues unlikely. n111 On the other hand, requiring disclosure to broader groups could cause one of at least three negative impacts on oversight goals. First, it could cause leaking and thus endanger national security or discourage executive branch candor in the instant or future briefings. Second, it could enhance executive branch perceptions of the likelihood of leaks. Those perceptions, even if incorrect, might lead to a lack of executive branch candor or intransigence in providing witnesses or requested documents. Third, and most cynically, it could provide the executive branch with ex ante or ex post excuses for avoiding disclosures. In short, broader disclosure requirements might enable the administration more credibly to claim that it will not or did not share information with Congress in order to protect the American people. This analysis suggests two basic guidelines to follow in determining to whom information should be funneled. First, the powers to have notified group should be sufficient numerically and in terms of their capacities and a real chance to influence the programs of which they are informed. Similarly, the group should be sufficient in size and capacity to understand the information conveyed and to meaningfully deliberate about the same. Among other things, these points suggest that the practice of excluding congressional staff members from many intelligence briefings should be reconsidered . Second, the group must be restricted sufficiently to minimize both the actual and perceived chances of leaks . Means toward this goal might include some reassessment of security clearance requirements. Such means might also include better publicizing of any clearance or related measures to enhance the political viability of congressional information requests and the political costs of defying the same. Page 174 2NC Funneling Funneling solves Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka Introduction In December of 2005, the New York Times broke the story that the U.S. government had, since shortly after September 11, 2001, spied without warrants on international phone calls in apparent contravention of the Foreign Intelligence Surveillance Act (FISA). n1 Since the story broke, commentary has abounded as to its implications for the Constitution's separation of powers. Most commentary has debated whether the Bush administration indeed violated FISA and, if so, whether it was constitutionally empowered to do so under Article II of the Constitution. n2 Also raised, though to a much lesser degree, is whether the administration was statutorily required to inform the congressional intelligence committees of its warrantless surveillance program, whether it violated any such requirement, and whether such a violation would be constitutional. n3 [*1050] Whether the President adequately informed Congress of his actions is a question as significant and complex as whether those actions violate the law. In matters of congressional oversight generally, it is difficult and important to balance the respective values of information flow to the public, information flow between Congress and the President, and presidential discretion to act swiftly and secretly. And matters are substantially more complicated where national security is at issue. Both executive branch secrecy needs and congressional information needs often are heightened in this context. Also at issue is what role, if any, information flow to the public should play. A major statutory means to reconcile secrecy and openness needs in the context of inter-branch information-sharing - including in the statute governing information sharing about the warrantless surveillance program n4 - is what this Article calls an " information funnel" approach. Such an approach focuses on funneling information only to discrete groups of people. For example, statutory provisions generally require that intelligence programs be shared with the congressional intelligence committees. provisions permit certain narrowly defined covert actions to be reported only to the congressional leadership. n6 The intended benefits of funneling are intuitive. Funneling plainly is directed toward n5 Other statutory balancing secrecy needs and openness needs. It demands some inter-branch knowledge sharing without requiring full public or even full congressional access. There’s constitutional authority for broader information funneling --- their ev conflates executive authority with total secrecy Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka First, although "executive privilege" or equivalent terms appear nowhere in the constitutional text, the privilege's supporters argue that it is implicit in the President's Article II duties. n74 Specifically, supporters argue that the President cannot faithfully fulfill his duties to execute the law and to serve as Commander-in-Chief unless he can control dissemination of his office's information to ensure candid discussions with his advisors and to protect national security. n75 Second, supporters argue that history demonstrates that those who framed and ratified the Constitution expected the President to have the prerogative to keep secrets from Congress. Supporters argue, first, that this is demonstrated by a series of post-ratification incidents in which Presidents refused to disclose requested information. n76 They also rely [*1062] heavily on two Federalist Papers, one by Alexander Hamilton and one by John Jay. Each paper touts as a major advantage of the American presidency its relative capacity for secrecy as opposed to the diminished secret-keeping capacity of a multi-member body. n77 Elsewhere, I have explained in some detail why I believe that these arguments are incorrect and why statutorily based information requests cannot constitutionally be refused by the executive branch. n78 The following passage summarizes major aspects of the argument against a constitutional executive privilege and in favor of a congressional prerogative to demand information from the executive branch: n79 It simply does not follow from the executive branch's institutional skill at secret-keeping that it has a legal prerogative to keep secrets in the face of checking mechanisms, including congressional requests. Saikrishna Prakash makes this point in his analysis of executive privilege doctrine. Prakash points out that historical references to Presidential secrecy ""hardly demonstrate that the proposed executive would enjoy a constitutional right to an executive privilege.' The references instead serve only to describe "one of the common attributes of a single executive ... . In the ordinary course, the President would be able to keep some matters secret.' Whether the President has a constitutional right to Page 175 keep secrets in the face of Congressional requests is another matter." n80 Constitutional structure, text and history not only fail to equate Presidential secret-keeping capacity with a secret-keeping right, they indicate that Presidential capacity necessitates robust structural checking. As I have explained elsewhere, the Constitution designs a system that seems to leave room only for political branch secrecy that itself can be checked through the political process. n81 Thus, while the President has much capacity to engage in secret activities, secrecy's dangers are mitigated because Congress may pass legislation limiting such activities or permitting itself or others to obtain information under certain conditions. n82 This constitutional design is evidenced by a number of factors. First, there is a negative correlation between the relative openness of each political branch and the relative control that each branch has over the other. Congress is a relatively transparent and dialoguedriven branch, and its core tasks are to pass laws that the executive branch executes and [*1063] to oversee such execution . The executive branch, in contrast, is capable of much secrecy, but also is largely beholden to legislative directives in order to act . This creates a rather brilliant structure in which the executive branch can be given vast leeway to operate in secret, but remains subject to being overseen or otherwise restrained in its secrecy by the legislature. n83 Second, historical references to secrecy as an advantage of the unitary President particularly two widely cited Federalist papers - also cite accountability and the ability of other branches and the people to uncover wrongdoing as a major advantage of the unitary President. This indicates, again, a balanced constitutional design whereby Presidential secrecy is expected but remains on a leash of political accountability. n84 Third, the only explicit textual reference to secrecy occurs in Article I, § 5, of the Constitution, which requires Congress to keep journals of its proceedings, but allows each chamber to exempt "such Parts as may in their Judgment require Secrecy." n85 That fact by itself does not tell us very much, as one could argue that a secret-keeping prerogative is intrinsic in the President's executive and commander-in-chief duties. What it does reflect, however, is a constitutional structure that permits secrecy only under conditions that will ensure some political awareness of and ability to check such secrecy. "The very framing of the congressional secrecy provision as an exception to an openness mandate, combined with [a logical and historical] expectation that a large and deliberative legislative body generally will operate in sunlight ... suggest a framework wherein final decisions as to political secrecy are trusted only to bodies likely to face internal and external pressures against such secrecy." n86 Finally, an executive branch that can keep secrets but that can be reigned in by Congress reflects the most logical reconciliation of competing constitutional values. On the one hand, the Constitution clearly values transparency as an operative norm. This is evidenced by myriad factors, including the necessities of self-government , the First Amendment , and Article I 's detailed requirements for a relatively open and dialogic legislative process. n87 On the other hand, the Constitution reflects an understanding that secrecy sometimes is a necessary evil, evidenced both by the congressional secrecy allowance and by the President's structural secrecy capabilities. n88 Permitting executive branch secrecy, but requiring it to operate within legislative parameters themselves open and subject to revision, largely reconcile these two values. n89 Funneling rules uniquely balance secrecy with security Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka Conclusion It is crucial, perhaps now more than ever, to reconcile legitimate executive branch secrecy needs with the devastating political and practical consequences of an uninformed Congress and public. When national security information belongs exclusively to the executive branch, it becomes dangerously easy to persuade Congress and the public simply to ""trust the President because only he [He?] knows the facts.'" n221 Indeed, there are substantial political incentives for Congress n222 and psychological incentives for the public n223 to acquiesce in this view. Because funneling rules plainly are directed at balancing the advantages of openness and secrecy, they may be uniquely equipped not only to achieve this substantive end, but to overcome the political and psychological barriers to so doing. With respect to the former, carefully crafted Page 176 funneling rules might help to ensure necessary information-sharing while protecting national security and meaningful deliberation . With respect to the latter, openness rules can not be passed or enforced without sufficient political incentive on the part of the relevant players. By crafting improved funneling rules and vigorously championing them to the public, to others in Congress, and to executive branch officers, congresspersons can help to bolster and harness those incentives . Indeed, it is important for congresspersons not only to engage the public in seeking to pass new funneling rules, but to engage them regularly on matters of government secrecy and executive branch information-sharing. Ideally, funneling rules might have a dynamic and ongoing relationship with the political process. Government secrecy must have a degree of political resonance for funneling rules to be [*1090] crafted, improved and enforced in the first place. At the same time, their very existence and success may increase their political resonance and the political costs to politicians of violating them or acquiescing in their violation. In short, well crafted and publicly debated funneling rules hold some promise to attack unwarranted secrecy on two fronts. First, the rules themselves may be conducive to meaningful informationsharing. Second, the rules may become foci for an ongoing public debate on the risks of excessive government secrecy and the means to balance secrecy and openness. Should funneling rules help to awaken the public to the dangers of unchecked government secrecy, that may prove their most important and enduring contribution. Page 177 AT: Kills deliberation You’re wrong Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka The intrinsic and instrumental forms of the candor argument can be applied to intra-branch and inter-branch discussions alike. The arguments as applied to intra-executive branch discussions essentially mirror those made in the previous paragraph. As applied to discussions with Congress, the arguments are more complex. An course, would absolute anti-disclosure stance toward Congress, of make deliberations between the executive branch and Congress about non-public information impossible . On the other hand, more moderate disclosure limitations - for example, notifying only a small number of congresspersons and subjecting them to gag orders - might facilitate candid and robust deliberation between branches. The intrinsic and instrumental values of robust inter-branch deliberation might then be realized. Congressional oversight is key to deliberation --- independently solves interbranch relations Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka ii. Arguments Favoring Disclosures Broad disclosure rules arguably advance the intrinsic and instrumental benefits of deliberation within the executive branch and between the executive and legislative branches. Instrumentally, such rules may foster more substantive, productive and forthright executive branch deliberations because executive branch actors know that they may be held accountable for their roles in the same. inter-branch deliberations by providing Congress with information to facilitate meaningful oversight of the executive branch. The enhancement of intra-branch and inter-branch [*1070] deliberations has intrinsic value as well, given the constitutional Similarly, disclosures can improve significance of these deliberations in our indirect democracy. Solves public deliberation Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka Deliberations involving the public also are advanced by broad disclosure requirements. First, to the extent that information is disclosed publicly, public information flow is directly enhanced , which in turn elevates the likelihood of informed public discourse . Second, to the extent that information initially is disclosed non-publicly (say, to members of Congress) under liberal disclosure rules that make eventual public disclosure likely, informed public deliberations again are enhanced. Increased public deliberation of course is associated with the intrinsic and instrumental benefits of the same. Page 178 AT: Leaks Funneling solves leaks Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka [*1072] b. Determining What Conditions to Impose on Those to Whom Information Is Funneled As important as determining who to inform is deciding what restrictions should be imposed on information recipients. The same basic considerations apply in making this determination as in deciding who should receive information in the first place. That is, restrictions must not significantly undermine the capacity of the informed to assess and respond to the funneled information. At the same time, restrictions must sufficiently protect against national security risks , the perception of such risks and the overall likelihood of executive branch defiance. One method that can help to strike this balance is the use of successive information funnels. In other words, information might first be funneled to a small group that is not permitted indiscriminately to disclose information . That small group may, however, have the power through majority vote or some other constraining mechanism to determine that the information or parts thereof should be funneled on to a different group. Successive funneling is considered further in Part III. No leaks and even if there are, they don’t matter Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka 2. Rethinking the Circumstances in Which the Gang of Eight Provisions Can Be Used It is hard to justify limiting notice of intelligence activity to the Gang of Eight on the basis of reasonable fears of information leakage that could harm national security. Congress is considered to have a reliable track record for non-leakage n138 and it has a political incentive to avoid leaks in order to avoid blame by the executive branch for the same. n139 Furthermore, the intelligence committees have a variety of methods to protect classified information including staff clearance policies , nondisclosure policies for members and office security measures. n140 Executive branch claims of national security secrecy needs also must be taken with a grain of salt given historical indications that such claims are dramatically overused and that the executive branch itself routinely leaks classified information for political reasons. n141 Page 179 AT: Staff leaks No staff leaks --- so much security Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka 3. When If Ever Should Staff Be Excluded? Excluding staff from hearings seems no more reasonable from a security-based perspective than does excluding members. Staff employees work amidst the same physical security and under the same non-disclosure agreements as do members. Unlike also are subject to pre-clearance requirements . n147 Furthermore, staff presence necessary to make information-sharing meaningful. Complex information about intelligence programs may be incomprehensible to members, or members may simply lack the time to sift through and make members, they often is sense of the information, without staff assistance . n148 Page 180 Mandate Intelligence Clearance/Lower Standing CP Page 181 1NC Clearance/Lower Standing CP Intelligence clearance prevents national security objections, and lower standing solves privacy considerations Sugiyama and Perry 6 --- J.D.s from UMich Law School (Tara and Marisa, “THE NSA DOMESTIC SURVEILLANCE PROGRAM: AN ANALYSIS OF CONGRESSIONAL OVERSIGHT DURING AN ERA OF ONE-PARTY RULE”, 40 U. Mich. J.L. Reform 149, Lexis)//trepka These competing proposals represent differing views of the need to hold the Bush administration accountable and the ability of Congress effectively to oversee the NSA surveillance program. On one side, Senators Specter and Schumer seek to face the legal challenges head-on, presumably to hold the administration accountable for any actions taken outside the purview of the law. Judicial oversight may determine whether the surveillance program is legal under current law, but these answers may come too late to provide any real leverage against the administration or to curb the ongoing surveillance. On the other side, Senator DeWine and his supporters seek to rubber-stamp past and future surveillance in a manner that may be challenged on Fourth Amendment grounds. n273 Looking forward, effective oversight of the NSA surveillance program will likely require both judicial and congressional action. One prospective model of oversight would both monitor ongoing surveillance activities and provide a grievance mechanism for individuals [*188] who believe that they have been illegally targeted. Members of a DeWine-like committee investigating such grievance claims would have intelligence clearances authorizing them to review classified documents relating to the NSA surveillance program. This clearance requirement would assuage concerns of the administration regarding the sensitivity of the program and the need to keep what the government knows and how the government knows it a secret. The administration has thus far rejected ongoing oversight by the FISA court, but it might be persuaded to support a DeWine-like congressional committee that engages in oversight of the NSA program even if that committee also has the power to refer questions to the FISA court for review or for consultation. For instance, if both minority and majority members could seek declaratory opinions from the FISA court on matters within their review, but the FISA court was not a "required" avenue for approval, perhaps the administration would deem it a feasible means of oversight of the surveillance program. Alternatively, the newly-created committee could develop a proposal for streamlined FISA court review that would respond to the administration's concerns that the current FISA process is laborious and slow. A similar compromise would create a grievance mechanism for congressional constituents. A DeWine-like committee would be authorized to hear initial complaints , for example, from citizens or interest groups, and then would refer cases of suspected illegal activity to the FISA court for more searching review . The subsequent judicial review could include relaxed standing requirements n274 and be mandated for all cases referred by the committee. Outside of a change in party leadership or a successful legal challenge, the administration seems unlikely to accede to any judiciary review of the surveillance program. The best opportunity for change appears to be the upcoming midterm elections. If the Democrats can successfully take back either house in Congress, they will have significantly more leverage to pressure the administration to open the surveillance program to oversight. [*189] Conclusion In times such as these when one party controls both the executive and the legislative branches, the 2006 midterm elections may present the best opportunity to bring greater congressional oversight to secret executive programs. In the interim, Congress should take bipartisan steps to investigate domestic surveillance program and engage the judiciary in a review of the program. The duty of the executive branch to preserve national security and the interests of Congress in oversight are not mutually the NSA exclusive. The United States can and must fight terrorism in a manner that simultaneously preserves the separation of powers and upholds civil liberties. Page 182 Modify A1C CP Modifying the A1C registry solves and prevents the necessity of a court ruling Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka Easy modifications to the surveillance component of the A1C Registry surveillance would remove doubt about its constitutional status. For example, the program could be consent based , like Vermont's diabetes registry. n211 Consent would remove privacy concerns ; in addition, people who opt in to the program are presumably indicating that they would benefit from reminders about their health status. Alternatively (or additionally), the A1C Registry could identify patients by community or health center , instead of by name and [*1994] personal information. That method would enable city government to direct resources to the communities that need them most. Page 183 Other Planks Page 184 1NC Combine CP Combining authorization and appropriation authorities is key Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka failed to adopt virtually any of the 9/11 Commission recommendations concerning congressional-oversight reform. n317 This failure was largely the result 1. 9/11 Commission Recommendations and Legislation As noted above, Congress of organizational "turf wars" and partisan squabbling. n318 Many of the commission's recommendations, however, continue to receive support in Congress. [*762] The Senate version of the IRTPA passed the Senate ninety-six to two and would have implemented many of critically , the report urged the combination of congressional authorization and appropriation authorities. n320 the 9/11 Commission's recommendations. n319 Most Page 185 2NC Combine CP That solves --- facilitates interbranch cooperation and guarantees effective enforcement Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka 1. Committee Reorganization Congressional intelligence committees are presently operating at a suboptimal level of efficiency. A number of bureaucratic constructs have markedly reduced the ability of the committees to both ensure legal compliance and facilitate an aggressive and effective Intelligence Community. To wit, Congress should seek to address three internal areas for reform: (1) appropriations authority, (2) committee organization, and (3) classification and secrecy. a. Appropriations Authority Congress should adopt the recommendations of both the 9/11 Commission and the WMD Commission, and establish either a bicameral intelligence committee or combine the appropriations and authorizations authorities into a single committee in each chamber. n352 [*767] Presently, the authorizing authorities (i.e., the intelligence committees) have little say in the appropriation of intelligence monies. Due to the classified nature of the intelligence budget, the vast majority of the money is "hidden" within the DoD budget and is thus controlled by the defense committees rather than intelligence committees. n353 This arrangement presents a number of problems, summarized by one commentator as follows: First, the continuation of the status quo keeps intact the unusual degree of control over the intelligence budget by appropriators (who write the checks in the end) rather than authorizers (who write the bills outlining their respective budgets), even though only the latter have a full staff of experts at their disposal. Second, the continuation of the stares [sic] quo makes it more difficult for Negroponte and his successors to count on a unified budget process, since it forces the DNI to deal with multiple actors rather than a few individuals. That splintering of jurisdiction, in turn, will make any future attempts at intelligence reform more difficult to push through Congress. Third and last, the decision to keep the intelligence budget split up among separate, classified accounts means that appropriators themselves cannot transfer money among their respective subcommittees - say, from Defense over to the State Department's Bureau of Intelligence and Research or to the FBI to aid its counterterrorism efforts - even if they decide that such a transfer reflects an important priority. n354 The House Committee on Rules is presently considering House Resolution 25, which would create an appropriations subcommittee for intelligence. n355 This bill was referred to the House Committee on Rules on January 9, 2007. n356 There has been no action on this issue since. Indeed, the Intelligence Authorization Act for Fiscal Year 2006 did not address this issue. n357 The Senate bill is not entirely without merit as it: requires a response to a committee request for intelligence within fifteen days of the request, establishes the Office of the Inspector [*768] General of the Intelligence Community, and empowers nonstatutorily established inspectors general. n358 Page 186 1NC Committee Reforms Increase info-sharing, eliminate term limits for half of the committee, all committee members have same rights and privileges Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka b. Committee Organization Beyond the appropriations issues, Congress must address other lingering organizational issues such as internal information-sharing and term limits. The Joint Inquiry Report issued by Congress following the 9/11 attacks contained 190 pages of "additional views." n359 These comments were not so much notable for the additional, independent views on the Intelligence Community, but rather for their illustration of internal strife within the committees. Senators John Kyl and Pat Roberts detailed at length organizational issues with the manner in which the committee conducted its investigation. n360 Their comments bear a direct importance to both future investigations and the conduct of the committee operations generally. Their concerns dealt primarily with the hierarchical nature of the investigation and the retention of information and decision making by the "Big Four" the Chairman and Vice Chairman of the Senate Select Committee on Intelligence and the Chairman and Raking Member of the House Permanent Select Committee on Intelligence. n361 They note: It is difficult, however, for rank-and-file Members of the two committees to know how thorough or accurate the Report is because of the way the JIS and the "Big Four' conducted the inquiry, withholding information and decisions from the Members and SSCI and HPSCI staff throughout the process... . ... . The inquiry was conducted and overseen in a way that left rank-and-file Members at a distinct disadvantage ... . n362 The Senators then proceed to provide specific examples of "irregularities" in the conduct of the inquiry. n363 Plainly, if senators are publicly chastising the leadership, there must be major organizational issues to be addressed by the committees. This problem is further exasperated by the term both committees, which deny the congressmen the limits applicable to opportunity to [*769] forge stronger working relationships . These term limits were originally introduced to prevent congressional overseers from being co-opted by the organizations they were overseeing. n364 This prophylactic measure, however, presents a number of issues. The Intelligence Community is enormous in both terms of personnel and budget, and intelligence operations can be complex affairs running for many years. Furthermore, the oversight rules applying to different aspects of the Intelligence Community are highly specialized to intelligence law and are exceedingly complex. n365 Thus, by the time a new committee member has read into all the intelligence operations and fully understands the oversight rules, it is time for that member to leave . While the original reason for term limits remains a legitimate concern, the efficiencies wrought by this change would likely outweigh any potential for impropriety. Such improprieties could further be guarded against by providing for term limits on a small number of seats, thereby ensuring unbiased rotation of members on a regular basis. Such a scheme would only work, however, where the rotating members were afforded the same rights and privileges as the permanent members. Page 187 1NC Framework/Training Congress should establish a uniform framework for intelligence oversight, including guidance for training efforts Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka 2. Uniformity of Oversight In his testimony before the 9/11 Commission, former Congressman and co-chair of the 9/11 Commission, Lee Hamilton, succinctly identified a systemic problem in the Intelligence Community - a lack of unity. n373 The Joint Inquiry Report quoted his testimony as follows: "U.S. intelligence is governed by a set of disparate laws executive orders produced over the last fifty-five years. No and single one of these laws provides a comprehensive legal foundation for our massive intelligence establishment. This is a remarkable state of affairs in a country that takes the rule of law so seriously... . We need a statutory foundation for U.S. intelligence." n374 [*772] All executive agencies operate under the rubric of Executive Order 12,333; however, each agency has implemented it differently, thereby creating a patchwork of regulations that vary from agency to agency. The divergences between agencies are further exasperated by different education-oversight programs for each agency. n375 This, then, seriously hampers the ability of agencies to work with one another. Where oversight education is lacking, incomplete, or incorrect, legal misconceptions develop within the agency regarding what is and is not "legal." This issue is further complicated by the insular nature of the intelligence establishment, where each agency perpetuates its own misconceptions. n376 Congress should establish a uniform framework for intelligence oversight . This recommendation can take one of two forms. The first, recommended by Congressman Hamilton, would establish a " statutory foundation for U.S. intelligence." n377 The second would require Congress to establish organizations that would then ensure Community uniformity. The establishment of an inspector general and general counsel in the Office of the DNI, for instance, should significantly facilitate this effort. Further, in establishing a uniform framework for oversight rules, Congress should strive to issue clear guidance , free to the greatest extent possible from legalistic terms and textual constructs. n378 Congress should mandate and fund annual training on these regulations. Finally, Congress should establish a bipartisan task force, and require the DNI to do the same, designed to identify and address "legal misconceptions" that pervade the Intelligence Community. Page 188 1NC Increase People Increasing the number of people on a committee creates healthy competition that prevents complacency Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka 4. Which Committees Should Have Access to Information? The NSA surveillance controversy also exposed difficulties that arise when a committee with jurisdiction overlapping that of an intelligence committee wishes to hold hearings, but lacks background on or access to some of the complicated, classified matters involved. These difficulties arose, most notably, when the Senate Intelligence Committee declined to hold investigative hearings on the surveillance program, n153 while the Senate Judiciary Committee held several hearings to determine what had transpired and to consider responsive legislation. n154 The Senate Judiciary Committee does not receive statutorily required, ongoing notice as does (in theory) the Senate Intelligence Committee. Staff and member expertise and member clearance requirements also differ between the committees. n155 Detailed assessment of which committees, beyond the Intelligence Committees, should receive notice and on what basis they should receive it is beyond this Article's scope. It is, however, worth flagging the issue and suggesting two relevant factors that deserve consideration. First, there is the question of whether any committees beyond the [*1079] intelligence committees should receive statutorily mandated, ongoing intelligence updates. n156 Broader regular disclosures are not novel. Between 1974 and 1981, the President was required by statute to notify "between six and eight congressional committees of covert intelligence actions." n157 The statutory requirement was modified in 1981, "replacing the reporting requirement to as many as eight committees with a general requirement to keep the two intelligence committees fully and currently informed of intelligence activities." n158 A potential cost of broader required disclosures is that the content and frequency of disclosures generally will become diluted. This might be caused by increased executive branch intransigence based on real or pre-textual concerns about national security or intra-executive branch deliberative candor. On the other hand, broader disclosures could spread information to more committees and enable these committees to better do their intelligence related work. Broader disclosures also might create healthy intra-chamber competition between committees, reducing the possibility of complacency or capture on the part of a single, information-monopolizing committee. n159 Page 189 1NC In Writing/Release Later In-writing requirements force accountability, and releasing the info in 10 years forces privacy compliance Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka 2. Possible New Approaches a. Some Additions to In-Writing Requirements and Public Disclosure Rules Existing rules include some inwriting requirements and the possibility of eventual public disclosure. As noted, both devices have the potential to enhance accountability, although both have had limited impact thus far. There may be ways to build on these requirements to enhance their effectiveness without unduly risking increased executive branch intransigence. Two changes to the existing devices come to mind - one building on in-writing requirements and one building on public disclosure rules. With respect to the former, the executive branch presently must put most of its obligatorily disclosed information - including its regular reports to the intelligence committees and its covert action reporting - in writing. It might be worth exploring a parallel in-writing requirement reflecting congresspersons' responses to the information. Any such requirement should be vague and undemanding so as not to be too onerous or to discourage compliance something to the effect that: "Congresspersons receiving information must, in writing, acknowledge receipt of the same. In the same document, receiving congresspersons may record any responses on their part to the information, including any responsive actions taken or follow-up discussions had." Such requirements would be subject to the same confidentiality and security procedures to which written executive branch disclosures are subject. [*1087] The accountability-enhancing effect of in-writing requirements depends on the likelihood that others will, at some point, see the written information and draw from it views as to whether the executive branch complied with its obligations, whether congresspersons pushed for such compliance and whether individual congresspersons were engaged in the relevant debates. Existing successive funneling rules contribute to these ends. Serious consideration also should be given to creating presumptive public disclosure/de-classification dates for information funneled to the intelligence committees. This is analogous to the practice within the executive branch of placing presumptive de-classification dates on some information, with the presumption subject to reversal. n212 Presumptive disclosure dates might make the possibility of eventual public disclosure much more real to participants and enhance the likelihood of compliance and engagement . At the same time, the possibility of rebutting the presumption combined with sufficiently distant dates - say, 5-10 years after initial disclosure - should alleviate reasonable concerns about national security or the integrity of executive branch discussions. Existing provisions for public disclosure upon special committee or chamber action can serve as a backup mechanism for cases where immediate public disclosure is warranted. Page 190 1NC Vest Powers CP: Vest “emergency domestic surveillance" powers in a congressional intelligence committee Solves, mitigates inefficiency, and ensures SOP Mehta 7 --- J.D., Harvard Law (Jason, “ASSESSING THE ELECTRONIC SURVEILLANCE MODERNIZATION ACT (ESMA): DISTORTING, RATHER THAN BALANCING, THE NEED FOR FLEXIBLE ELECTRONIC SURVEILLANCE AND ROBUST CONGRESSIONAL OVERSIGHT”, 12 J. Tech. L. & Pol'y 225, Lexis)//trepka A more meaningful role for Congress could be preserved by allowing select congressional intelligence committees , and not the President, to determine when warrantless domestic emergency surveillance is appropriate. Forcing these congressional committees , rather than the President, to determine when to engage in warrantless electronic surveillance will necessarily create a " second sobering moment " and will require majoritian support. While one might argue that Congress may lack classified information about pending terrorist threats, there is no reason to believe that the President could not brief and persuade Congress to authorize warrantless surveillance without compromising sensitive information. Furthermore, in response to the claim that Congress often moves too slowly, the fear of congressional inefficiency should be militated when we speak of 15 member congressional committees (as opposed to 535 members of the full Congress). This separation of powers framework. proposal, for example, would more faithfully ensure a robust Page 191 Penalties CP Page 192 1NC Penalties That solves Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka B. Require Politically Accountable Executive Officials to Approve All Warrantless Domestic Surveillance FISA requires that the Attorney General approve any warrantless foreign intelligence surveillance in the United States. n193 This requirement should also be imposed on warrantless domestic intelligence searches because it accomplishes two objectives. First, it guarantees that the overzealous predilections of low-level intelligence officers do not drown out the legitimate privacy interests of those who are surveilled. Simply because the Attorney General is an executive officer does not mean that she would be less sympathetic to privacy concerns of surveillance subjects than would a judge. She is politically accountable, and thus must take into account how surveillance would impair the privacy of citizens if such surveillance were widespread. And further, it is just as possible for an executive officer as it is for a judge to be detached enough from the situation to make a neutral [*378] decision. n194 By interposing a high-level executive officer who can evaluate the search from the "big picture," requiring the Attorney General's approval functions much like a warrant, but without the burdensome process associated with obtaining one. Second, such a rule ensures that a politically accountable individual has the authority to decide to conduct a warrantless search. n195 Thus, if a search is conducted for an improper purpose, Congress and the electorate know whom to blame. For these reasons, Congress should require that the Attorney General or another high-ranking executive officer approve warrantless domestic intelligence searches. C. Harsh Penalties for Those Who Abuse Their Authority Just as harsh penalties deter individuals from committing crimes, penalties will deter those officials who abuse their authority to conduct warrantless surveillance or who misuse lawfully obtained information. n196 The power to conduct warrantless surveillance should not be taken lightly. Individuals conducting searches will come across personal information that should never become public knowledge unless necessary to protect the national security. n197 Thus, those officers who use information obtained through domestic intelligence to blackmail or intimidate subjects of surveillance should be exposed to criminal sanctions , including jail time and heavy monetary fines . Under such a regime, the abusive or malicious officer - who is not deterred by the ban on the use of evidence obtained via such surveillance in non-national security criminal prosecutions - will be deterred by the fear of punishment from misusing the information he has obtained through intelligence efforts. D. Expanded Whistleblower Protection for Insiders Who Expose Illegal Surveillance Expanded penalties for those who abuse intelligence-gathering authority are meaningless if those abuses never come to light . Honest intelligence officers who become aware of illegal surveillan ce or physical searches in violation of the Fourth Amendment should not be deterred from reporting such activity for fear of prosecution under laws that criminalize disclosure [*379] of confidential information or activity n198 or internal sanctions by their superiors. Over the years, Congress has exempted much of the intelligence community from whistleblower protection laws, which protect employees who report illegal activities that occur within their companies or government agencies. n199 Congress should expand whistleblower protection to cover intelligence officers who report unconstitutional searches and seizures. Page 193 2NC Penalties Increasing penalties prevents the worst abuses Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka F. Expanded Administrative Remedies for Violations of the Fourth Amendment At the Founding, the primary remedy for a violation of the Fourth Amendment was a civil damages action. n201 However, the increasingly costly and time-consuming nature of civil lawsuits, combined with the likelihood that damage awards will be low, could deter an individual who has suffered a violation of her Fourth Amendment rights from asserting them in court. n202 Therefore, Congress should expand administrative remedies to give these individuals meaningful opportunities to assert their rights. n203 Such remedies could take the form of citizen review boards that hear citizen [*380] complaints and issue punishments, n204 or they could replicate lawsuits in a less costly setting by allowing claims to be brought before an administrative law judge. Even if administrative remedies or civil actions for Fourth Amendment violations initially are costly, one should not discard such enforcement mechanisms as insufficient. Fourth Amendment law comes from the " ground up ," not the "top down," meaning that the courts fashion clearer rules by giving more concrete meaning to terms like "unreasonable" and "probable cause" in the specific factual situations of actual cases. n205 Thus, if warrants were deemphasized, the courts would then have to craft practical solutions outside the warrant and probable cause paradigm for Fourth Amendment problems time a body of law would develop around the centrality of civil and administrative damages to remedy Fourth Amendment violations, thereby allowing the Court to craft a Fourth Amendment jurisprudence that maximizes the that arise. Although there may be growing pains in the beginning, over effectiveness of these remedies. Page 194 Terry Stops CP Page 195 1NC Terry Stops Terry Stops solve Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka The FAA solves the technological problem associated with foreign-to-foreign communications being routed through America. Unfortunately, it does not appear to adequately address the concern that U.S. persons unaffiliated with foreign powers may be subjected to warrantless surveillance after being contacted by foreign terrorist suspects. For instance, if the purpose of the FAA was in part to solve the problems discussed in Part III concerning an overseas terrorist calling ten phone numbers in America, n259 it does not seem that the FAA resolves that issue. Under the FAA, while there is no need for a warrant to target the alleged overseas terrorist (who does not even need to be a terrorist but just a foreign national); n260 it does require the executive branch to obtain a [*309] FISA warrant before conducting follow-up surveillance on the U.S. person who answered the phone. n261 Under the FAA, as soon as the government targets a U.S. person (no matter where located), the executive must show probable cause that the U.S. person is an agent of a foreign power. n262 One solution to this problem is to use the equivalent of a "Terry stop" for electronic surveillance-a solution proposed by Kim Taipale, Executive Director of the Center for Advanced Studies in Science and Technology Policy. As Taipale explains, "where collateral U.S. person communications are intercepted incidental to a legitimate foreign intelligence intercept, there is no explicit way consistent with FISA ... to engage in follow up electronic surveillance to determine if probable cause exists to target the individual, even though the collateral intercept itself may give rise to a constitutionally reasonable suspicion." n263 Pursuant to the seminal case Terry v. Ohio, n264 a police officer can briefly detain a person for questioning and conduct a limited pat-down frisk if the officer has "reasonable suspicion" (a standard less than probable cause) to believe that the person may be involved in a crime. n265 If the Terry stop reveals additional evidence of a crime, that evidence can be used to justify probable cause and a full-scale search or arrest. n266 In the case of electronic surveillance, a "Terry stop" would allow an authorized period for additional monitoring or initial investigation of the U.S. person in contact with the alleged terrorist. n267 In other words, in the case of a terrorist who calls a U.S. person, the government could briefly perform follow-up surveillance on the U.S. person to determine whether the communications have any intelligence value. If this follow-up surveillance revealed that the U.S. person was an agent of a foreign power, then a traditional FISA warrant could be obtained based on probable cause. If the U.S. person's communication was innocent, then the follow-up surveillance would be minimized . Page 196 2NC Terry Stops Terry Stops ban evidence not for national security --- ensures it can’t be used against citizens --- that solves unrelated prosecutions which ensures rights Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka on the Use of Seized Evidence for Purposes Other than Domestic Intelligence or Counterterrorism One of the greatest potential abuses of a domestic intelligence exception to the warrant requirement would be to allow the exception to creep into everyday law enforcement. Indeed, it was this fear the Court A. Limitation addressed in the "special needs" cases by requiring that any police activity qualifying for the exception must not be for the "primary purpose" of law enforcement. n181 Because legitimate governmental interests outside of law enforcement overlap with criminal law - say, the government's legitimate concern with protecting its citizens prospectively from drunk drivers n182 or with protecting student athletes from the effects of drug use n183 - any exception to the [*376] warrant requirement potentially could be used as a mere pretext for easy solution to this problem exists: ban the use of evidence from a legal-but-warrantless domestic intelligence search in a criminal prosecution unrelated to the retrospective law enforcement. An national security. n184 If such a rule existed, an intelligence officer's incentive to use domestic intelligence as a pretext for mere law enforcement would vanish because doing so would be of no use in a later criminal prosecution. n185 Although this would not deter the rare intelligence officer who abuses his authority solely for reasons of caprice or malice, the warrant requirement also does not prevent this problem: if the officer is acting not to uncover evidence but merely to harass or surveil individuals for his own pleasure, he need not obtain a warrant because he knows no court will ever review his actions, and thus he will not be held to account for them unless he is later sued. n186 A ban on the use of evidence gathered in warrantless domestic intelligence searches in criminal prosecutions for crimes unrelated to national security, then, provides as much protection from overzealous intelligence gathering as one can hope for in this area. Were Congress not to enact such a ban, the Court could impose it via either the exclusionary rule or the "minimization principle." n187 One scholar argues that the Fourth Amendment's minimization requirement - where officers conducting a search are required to use procedures to limit the uncovering of private information unrelated to the subject matter of the search n188 - provides a constitutional basis for a ban on the use of evidence obtained from warrantless intelligence searches in criminal prosecutions for crimes unrelated to national security. n189 However, the minimization principle is designed to ensure that the government does not invade the constitutionally protected interests of the individual who is being surveilled. n190 Criminal activity, though, is not a constitutionally protected interest. n191 Thus, for this new constitutional argument to fit within the Court's Fourth [*377] Amendment jurisprudence, the Court would have to hold, for the first time, that even when the Executive uncovers unrelated criminal activity in the course of a lawful search, the fruits of that search could not be used to prosecute the unrelated criminality. This would be a fairly significant break from the Court's "plain view" doctrine. n192 Page 197 AT: Unconstitutional They’re compatible with the 4th amendment Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka This Terry stop surveillance approach is likely constitutional . The Supreme Court held in Keith that the standard of probable cause needed to obtain warrants for intelligence purposes could be different from the traditional standard used for law enforcement: "Different standards may be compatible with the Fourth Amendment if they are reasonable both in relation to the legitimate need [*312] of Government for intelligence information and the protected rights of our citizens." n278 Hence, there is an argument that one could reframe the question of probable cause from whether the target is an agent of a foreign power to whether the target has been contacted by a terrorist. In other words, the probable cause that FISA requires is probably higher than what is required under the Fourth Amendment. Page 198 Solves 4th Amendment Rights Congress solves Fourth Amendment Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Before proceeding further, it is important to note what this Comment does not do. Although this Comment's discussion of the efficacy of warrants and its ultimate finding that warrants should not be required for domestic intelligence surveillance could be used to justify foreign intelligence [*348] gathering - to buttress the legality of the National Security Agency (NSA) domestic spying program authorized by President Bush after 9/11 - this Comment in fact cuts the other way. While the rationales advanced in this piece support finding that the NSA program does not violate the Fourth Amendment, this Comment recognizes that Congress has the authority to regulate the intelligence- gathering apparatus of the executive branch ; n19 thus, the NSA program was illegal at its outset for the simple reason that it violated FISA. In arguing that the warrant requirement is an ineffective way to police intelligence activities and that it stifles legitimate intelligence gathering, this Comment proceeds in three parts. Part I discusses the history of the Warrant Clause of the Fourth Amendment, the case law surrounding the imposition of the warrant supported by probable cause "presumption," the exceptions to this presumption, and the maintenance of the warrant requirement for domestic intelligence searches. In particular, it focuses on the Court's atextual - although somewhat justified - imposition of the warrant requirement in the context of criminal investigations, and its unwise extension of that requirement to the national security arena. Part II analyzes several of the most prominent rationales for the warrant requirement in general, and specifically in the national security context. It argues that none of these rationales are sufficient to justify the warrant requirement for domestic intelligence searches. Finally, Part III argues that solutions other than the warrant requirement - some judicial, some legislative - can better protect Fourth Amendment interests. This Part discusses a few proposals that, due to the warrant presumption, have not received the attention they deserve. Ultimately, this Comment concludes that the Supreme Court should discard the warrant requirement for searches conducted in order to uncover information to prevent future domestic terrorist attacks. None of the usual arguments for why a warrant should be required justifies the warrant requirement in the domestic legislative and judicial means that would adequately protect the Fourth Amendment's values . In light of these alternatives, the warrant intelligence-gathering context. Moreover, there are a number of other requirement is unnecessary and impedes the government's access to the information it needs to prevent terrorist attacks. Congress is sufficient to create a spillover of Fourth Amendment values Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka III. Better Solutions to Intelligence-Gathering Abuse The Supreme Court, for better or worse, is the primary enforcer of the Fourth Amendment. Although this is understandable, given the Court's unique position and ability to check majoritarian excess that can lead to violations of civil liberties, it is unfortunate because it has created in Congress apathy toward its obligation to participate in the protection of Fourth Amendment values . n175 This failure on the part of Congress to properly assert itself in the enforcement of constitutional rights need not continue . The enactment of FISA is a case in point. Given the widespread acknowledgement that the Constitution does not require that the President conduct foreign intelligence [*375] surveillance in the United States pursuant to a warrant, n176 Congress - properly exercising its own powers in the foreign intelligence context - limited the President's authority in order to curb perceived intelligence-gathering abuse. n177 FISA requires the Executive to obtain a court order for surveillance, though such court orders are not Fourth Amendment warrants. n178 However, Congress did not hamstring the Executive by requiring court approval before the commencement of any and all electronic surveillance. In certain emergency situations, the Attorney General can authorize electronic surveillance for up to seventy-two hours before seeking court approval. n179 This is a practical recognition that intelligence gathering frequently requires the relaxation of the warrant requirement, but it still ensures that continued surveillance will be subject to congressional limitations. n180 Congress, then, has significant authority in the foreign intelligence arena to create such pragmatic solutions. There is no reason to assume Page 199 that it could not enact legislation like FISA that is applicable to domestic intelligence . Moreover, even in the absence of congressional action, the Court could impose solutions by tailoring existing doctrines. The remainder of this Part discusses examples of possible legislative and judicial solutions . Congress solves regulation of executive Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Further, the exclusionary rule mandates the exclusion of evidence seized unconstitutionally. Were the proposal advanced in this Comment to be adopted, however, evidence seized pursuant to a warrantless intelligence search would be constitutional - provided the search is reasonable. Thus, the exclusionary rule as currently understood would not require the exclusion of evidence seized pursuant to a warrantless intelligence-gathering search. However, if Congress fails to enact meaningful legislation to regulate the Executive's surveillance power, the Court should consider mandating the exclusion of the fruits of a warrantless domestic intelligence search in a prosecution for crimes unrelated to national security as a prophylactic measure to protect Fourth Amendment rights. In short, banning the use of such evidence removes any incentive for the executive branch to use its domestic intelligence powers to circumvent the normal limits on its criminal investigatory power. Congress is the body most appropriate to enact such a prohibition. However, should Congress prove unwilling to do so, and should it become clear that the Executive is indeed abusing its domestic intelligence power to further everyday criminal law enforcement, the Supreme Court should consider extending the exclusionary rule or "minimization principle" to combat such abuse. Oversight solves liberties Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka III. The Primacy of Political Checks In light of the limitations of ex ante judicial approval to protect civil liberties, it is necessary to consider an alternative approach . The most attractive solution is a framework that relies primarily on political checks. Such a system could force public consideration of the difficult weighing of liberty and security interests and ensure meaningful oversight of the government's conduct of surveillance. n89 Ultimately, a combination of the two bills that the two houses of Congress have passed, if modified in several respects, would do the best job of protecting liberties while enabling efficient and effective surveillance . Whereas the Senate bill is preferable for drawing back the role of the judiciary in ex ante approval, the House bill offers a host of potentially powerful oversight mechanisms that are necessary to protect civil liberties . Congressional oversight only facilitates broader privacy violations Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka This tension is perhaps particularly acute in the realm of intelligence operations and oversight where these powers are not expressly side believes their uninhibited participation is critical for national security. n16 This Article does not, however, seek to trade in a discussion of the legality of recent practices, but rather examines this dynamic relationship and, specifically, Congress's role in facilitating both legal and aggressive intelligence operations. All too often it seems the Executive has viewed Congress as an unwanted partner - interfering with delegated by the Constitution and each executive powers and meddling in affairs best left to the professionals in the various agencies within the United States Intelligence Community (Intelligence Community or Community). Congress has historically acquiesced, thus largely allowing the Executive to conduct intelligence operations without oversight. n17 Congress has rejected this historical generalization twice in the last fifty years: first, and most significantly, in response to the intelligence activities relating to Watergate n18 and the Vietnam War; n19 and then again, [*725] in the late 1980s, in response to the Iran-Contra Affair and other actions involving the Intelligence Community. n20 Page 200 Solves 14th Amendment Congress solves Fourteenth Amendment better --- the aff violates the constitution Mendenhall 15 --- staff attorney to Chief Justice Roy S. Moore of the Supreme Court of Alabama, adjunct professor at Faulkner University (Allen, “Is The Fourteenth Amendment Good?”, https://mises.org/library/fourteenthamendment-good)//trepka Ceding power to federal judges does not predispose them to liberty. Because Section Five of the Fourteenth Amendment permits Congress to pass amendments or enact laws dealing with state infringements on individual liberty, it isn't necessary or constitutionally sound for the federal judiciary to assume that role. Members of Congress, unlike federal judges who enjoy life tenure, are accountable to the voters in their states and are thus more likely to suffer from their infidelity to the Constitution. Constitution is a d-rule Stephen L. Carter, professor of law at Yale University, 1987, Brigham Young University Law Review, 1987 BYU L. Rev. 719, HeinOnline, p. 750-751 The problem with this use of our burgeoning public policy science, an inevitable one in an area of theory driven by instrumental rationality, is that the law itself is stripped of the aura of uniqueness which is assigned to it in liberal theory. The law becomes all too mutable, and is left as no more than one of the means that must be tested against its efficacy in achieving the desired end. The Constitution, which is after all a species of law, is thus quite naturally viewed as a political impediment to policy, a barrier that must be adjusted, through interpretation or amendment, more often than preservation of government under that Constitution is viewed as a desirable policy in itself. In this the modern student of policy is like the modern moral philosopher – and like a good number of constitutional theorists as well – in denigrating the value of preserving any particular process and exalting the desirable result. But constitutionalism assigns enormous importance to process, and consequently assigns costs, albeit perhaps intangible ones, to violating the constitutional process. For the constitutionalist , as for classical liberal democratic theory, the autonomy of the people themselves, not the achievement of some wellintentioned government policy, is the ultimate end for which the government exists. As a consequences, no violation of the means the people have approved for pursuit of policy—here, the means embodied in the structural provisions of the Constitution, can be justified through reference to the policy itself as the end. Page 201 Solves Deontology Failure to engage in comparative institutional analysis means vote neg on presumption – they make change less likely to occur Heminway, 05 (Joan, professor of law at the University of Tennessee, 10 Fordham J. Corp. & Fin. L. 225, lexis) This article offers a model for comparative institutional choice specifically for use in the context of federal corporate governance reforms. It also, however, constitutes part of the larger academic movement advocating comparative institutional analysis. Comparative institutional analysis is critically important to the work of scholars and other proponents of law reform. These rule proponents should not suggest changes in legal rules without also suggesting the vehicle for the suggested reforms. The determination of the appropriate rulemaking body should be accomplished by employing some rigorous form of comparative institutional analysis. In this regard, the framework included in this article is intended to endorse in full the views of Professor Neil Komesar when he says: [*384] Unless we do better with the difficult issues of institutional choice, any reforms, changes and proposals will remain illusory or cosmetic. We will continue to cycle through the same proposals with the same arguments. Today's policy will always have feet of clay and be replaced by yesterday's rejected panacea, which somehow reappears (without blemishes) as tomorrow's solution. Attempts to fashion proposals and programs cannot stop until we fully understand institutional choice. That understanding will be long in coming and is more likely to occur if judges, lawyers and law reformers seriously struggle with the subject as they make their decisions and proposals. It is that struggle that I hope for. I want those who make or seek to change law to seriously confront and address institutional choice and comparison . I recognize that, to do so, they will often have to rely on intuition and guesses. It is the responsibility of legal academics to provide deeper understanding of these central issues and, therefore, to improve the ability of those who struggle with these decisions. 581 Seriously none of their stuff assumes the CP—even deontologists agree that it’s a bad idea to choose an inefficient method Finnish, 1980 John Finnis, deontologist, teaches jurisprudence and constitutional Law. He has been Professor of Law & Legal Philosophy since 1989,1980, Natural Law and Natural Rights, pg. 111-2 The sixth requirement has obvious connections with the fifth, but introduces a new range of problems for practical reason, problems which go to the heart of ‘morality’. For this is the requirement that one bring about good in the world (in one’s own life and the lives of others) by actions that are efficient for their (reasonable) purpose (s). One must not waste one’s opportunities by using inefficient methods. One’s actions should be judged by their effectiveness, by their fitness for their purpose, by their utility, their consequences… There is a wide range of contexts in which it is possible and only reasonable to calculate, measure, compare, weigh, and assess the consequences of alternative decisions . Where a choice must be made it is reasonable to prefer human good to the good of animals. Where a choice must be made it is reasonable to prefer basic human goods (such as life) to merely instrumental goods (such as property). Where damage is inevitable, it is reasonable to prefer stunning to wounding, wounding to maiming, maiming to death: i.e. lesser rather than greater damage to one-and-the-same basic good in one-and-the-same instantiation. Where one way of participating in a human good includes both all the good aspects and effects of its alternative, and more, it is reasonable to prefer that way: a remedy that both relieves pain and heals is to be preferred to the one that merely relieves pain . Where a person or a society has created a personal or social hierarchy of practical norms and orientations, through reasonable choice of commitments, one can in many cases reasonably measure the benefits and disadvantages of alternatives . (Consider a man who ha decided to become a scholar, or a society that has decided to go to war.) Where one ~is considering objects or activities in which there is reasonably a market, the market provides a common denominator (currency) and enables a comparison to be made of prices, costs, and profits. Where there are alternative techniques or facilities for achieving definite, objectives, cost— benefit analysis will make possible a certain range of reasonable comparisons between techniques or facilities. Over a wide range of preferences and wants, it is reasonable for an individual or society to seek o maximize the satisfaction of those preferences or wants. Page 202 Solves Intelligence Framework Congressional constraints set the framework for intelligence gathering Steinberg AND Estrin 14 --- Dean of Maxwell School of Citizenship and Public Affairs at Syracuse University AND Postdoctoral Associate at Yale (James and Miriam, “Harmonizing Policy and Principle: A Hybrid Model for Counterterrorism”, 7 J. Nat'l Security L. & Pol'y 161, Lexis)//trepka [*161] INTRODUCTION In the ongoing and evolving response to terrorism, the United States has had to confront a threat that straddles the line between armed conflict and criminal enterprise. Like traditional warfare, the United States confronts adversaries with the avowed intention to harm the United States as a political entity and the capacity to inflict massive casualties and extensive economic and physical destruction. But unlike traditional armed conflict, the adversary represents no state, and its members wear no uniform announcing their membership in a hostile organization. In this respect, these organizations bear important similarities to criminal organizations. Twelve years have passed since the terrorist attacks on September 11. What started out as a concentrated response against one cohesive terrorist organization, al Qaeda, with a concentrated base in Afghanistan and Pakistan, began to spread as al Qaeda-supported affiliate organizations sprang up in the Arabian Peninsula, Somalia, and the Maghreb. But as U.S. counterterrorism efforts began to defeat al Qaeda's core -- killing its leader Osama bin-Laden and many in his senior leadership ranks -- the more diffuse affiliate groups continued to plot attacks aimed at the American homeland. Sometimes these affiliates planned attacks in coordination with the central al Qaeda organization, as the United States discovered when it intercepted communications between the leader of al Qaeda's Yemen-based offshoot and Osama bin Laden's successor, Ayman alZawahri, closing nineteen embassies across the Middle East and North Africa as a precaution against. n1 At other times, these terrorist groups have seemingly acted alone to strike at American and Western targets in their own neighborhoods, with localized attacks against the U.S. consulate in Benghazi and the BP oil facility in Algeria. Through Internet magazines and chat rooms, al Qaeda affiliates could radicalize individuals residing in America, and give them basic training to carry out small-scale attacks from their home base in American [*162] cities. n2 To deal with these unconventional threats, policymakers have employed a variety of sometimes controversial tools: some drawn from traditional warfare, some from crime fighting, and other, novel techniques developed to address this new kind of threat. These latter include indefinite detention without prosecution, "enhanced" interrogation, rendition to third countries, military tribunals, and targeted killing that successive U.S. administrations have sought to justify under domestic and international law. The variety of tools, and the choice between them, has been primarily driven by the varying objectives entailed in the conflict -- to punish bad actors, but more importantly to prevent future acts of terrorism by incapacitating the enemy, deterring others from joining their ranks and pursuing future attacks, and gathering intelligence to disrupt terrorist plots and dismantle terrorist networks. In practice, which tools are used and when is shaped not just by the exigencies of the threat, but also by constraints imposed by the Congress and the courts, as well as the executive branch's own evolving views on domestic and international law. These constraints are frequently driven by factors, including political calculation, that are not directly related to immediate counterterrorism objectives. The result is an operating environment in which the choice of tool is imperfectly related to the objective, and can lead to unwanted and undesirable outcomes -- for example, a policy environment that leads decisionmakers to favor killing rather than capturing the adversary for reasons unrelated to the safety of U.S. personnel, or that forces the detention of adversaries outside the United States rather than bringing them to the United States, which can strain U.S. foreign relations. Even after twelve years, only recently has there been an effort to develop a written framework to guide the U.S. response. President Obama recently announced the existence of classified Presidential Policy Guidance to govern use-of-force decisions inside the executive branch. n3 Even now, the public details on what rules would control decisions to detain or target remain slim, and the language of existing guidance seems to leave much room for flexible and permissive interpretation. This Article explores the tension between the policy objectives of this conflict (deterrence, incapacitation, and intelligence gathering ) and the traditional legal frameworks used to justify them (the law of war and the criminal justice model). Part I examines the rationale for these policy tools and the limitations of each of the traditional frameworks for this conflict, looking at where historical cases and American principles have drawn the line between security and [*163] liberty. Part II looks at the ways that, in this conflict, all three branches have worked at cross-purposes and deviated from what, from a policy perspective, would seem to be a more appropriate legal framework. Finally, Part III lays out the basic components of a hybrid model, in a way that allows for effective counterterrorism policy without sacrificing legality and principle. Page 203 Solves Online Privacy/Internet Freedom Congressional action solves broader online communications Semitsu 11 --- J.D., University of San Diego School of Law (Junichi, “ From Facebook to Mug Shot: How the Dearth of Social Networking Privacy Rights Revolutionized Online Government Surveillance”, http://poseidon01.ssrn.com/delivery.php?ID=18807008603110407107308900309410911000401109105206106101008612612602707 008600610711903701112506311600009810303007008009703011002007500703307200509411508512107902410300606503406700 0089064064116069086091118109096100123023124022127065104095103114020073&EXT=pdf&TYPE=2)//trepka Even though Facebook could do lots to improve its users‘ consumer privacy rights, the issues of privacy from government surveillance originate with the government, not Facebook. Regardless of what social networking will look like in 2024 or whether our clones will have new ways to tap into new networks, one fact seems inevitable: in the digital world, social networkers will still store, access, and disseminate personal information through a third party. A digital community on the magnitude of Facebook will likely depend on some entity that functions as the server or hub for the content. While peer-topeer networks suggest the possibility of direct communications without third party conduits, the very nature of the Internet makes it difficult to imagine a social network emerging in isolation without a person or entity hosting or facilitating the exchange. The resulting unreasonable expectation of privacy will thus follow those social networkers wherever they go unless there is congressional intervention or a judicial shift in how the Fourth Amendment is applied to online communications. Congressional statute is key to protect online privacy rights Semitsu 11 --- J.D., University of San Diego School of Law (Junichi, “ From Facebook to Mug Shot: How the Dearth of Social Networking Privacy Rights Revolutionized Online Government Surveillance”, http://poseidon01.ssrn.com/delivery.php?ID=18807008603110407107308900309410911000401109105206106101008612612602707 008600610711903701112506311600009810303007008009703011002007500703307200509411508512107902410300606503406700 0089064064116069086091118109096100123023124022127065104095103114020073&EXT=pdf&TYPE=2)//trepka D. Misplaced Trust Doctrine Another important spinoff of the plain view rule is the misplaced trust doctrine, which may apply when a Facebook user voluntarily discloses information to someone who turns out to be an undercover officer.143 Under this doctrine, a person who mistakenly places her trust in someone who turns out to be an informant or government agent does not maintain any privacy rights under the Fourth Amendment.144 The Court has repeatedly refused to adopt the rule that ―the Fourth Amendment protects a wrongdoer‘s misplaced belief that a person to whom he voluntarily confides his wrongdoing will not reveal it.‖ 145 Thus, the government has the authority to use undercover operatives to prevent crime.146 More specifically, the Ninth Circuit has held that government officials must be allowed to take on reasonable false identities in order to be more convincing in their undercover operations.147 Accordingly, undercover agents can use deception to procure consent to a search. In Hoffa v. United States, for example, the Court noted the possibility that someone will be observed by undercover officers is ―the kind of risk we necessarily assume‖ and ― inherent in the conditions of human society.‖ 148 While some questioned Hoffa‘s validity after Katz, the Court in United States v. White reaffirmed the rule that a person does not have any ―justifiable expectation of privacy‖ when making incriminating statements to an informer.149 No federal statute or court has yet had occasion to draw any boundaries or rules regulating undercover policing on the Internet. Thus, suppose that Semion Mogilevich, who is on the FBI‘s list of Top Ten Most Wanted Fugitives, has a Facebook page.150 Would a government agent be forbidden from creating a Facebook account in Semion‘s mother‘s name, uploading an actual photo of her, and naively hoping that he might divulge his whereabouts? While virtually every government agent to whom I asked this question concluded that this would be ―going too far,‖ neither the agents nor I have found any federal precedent restricting such a deceptive practice. Thus, only state law or a congressional statute can protect private conversations from being surreptitiously documented. For example, the Massachusetts Supreme Court interpreted Article 14 of the state‘s Declaration of Rights to mean that its citizens can reasonably expect that their private conversations held in private homes are not being electronically transmitted or recorded by undercover government agents.151 Page 204 Only statutory revisions protect internet freedom, privacy, and prevent crime --- here’s 6 recommendations Semitsu 11 --- J.D., University of San Diego School of Law (Junichi, “ From Facebook to Mug Shot: How the Dearth of Social Networking Privacy Rights Revolutionized Online Government Surveillance”, http://poseidon01.ssrn.com/delivery.php?ID=18807008603110407107308900309410911000401109105206106101008612612602707 008600610711903701112506311600009810303007008009703011002007500703307200509411508512107902410300606503406700 0089064064116069086091118109096100123023124022127065104095103114020073&EXT=pdf&TYPE=2)//trepka While the stifling of Facebook activity may be inconsequential, the need for a statutory revision is paramount. At stake is nothing less than the potential for the Internet to be a utopian marketplace of ideas and a global community that connects people in an otherwise-isolated digital world. As for statutory revisions, I propose the SCA be amended to require that any compelled disclosure of electronic information, including content on Facebook, require full warrant protection. This would require the government to demonstrate probable cause to a neutral magistrate. If, however, the government will still be allowed to conduct such searches with an administrative subpoena, the ECPA should require that subpoenas provide meaningful notice to the user to bring the privacy laws closer to the warrantless searches allowed in other contexts. To close these gaping holes in the current privacy laws, Congress must implement several changes. First, the Stored Communications Act needs to be revised to make clear that all forms of content that a person uploads to or disseminates through Facebook are covered. Given that Facebook reveals ―content‖ that may not neatly fit into the definition of ―electronic communications,‖ the statute should leave no doubt that all activity on Facebook—including wall postings, photo-sharing, or event-creating—will be protected. Moreover, in light of all the data that Facebook users provide when joining the site, the specific subscriber information or ―non-content‖ that can be disclosed without any judicial oversight should also be delineated. Second, the SCA must be amended to require the government to obtain a Section 2703(d) order for all remote computing services (in addition to electronic communications services). Thus, regardless of whether Facebook is serving as ―storage‖ or as a facilitator of messages, judicial supervision will be required if any content stored on the site will be disclosed to the government. Third, the SCA should also impose a court-order provision on non-governmental entities that compel production of the contents of electronic communications under § 2703.300 Without this judicial oversight, the voluntary disclosure doctrine would allow private entities to easily compel such production and hand it over to the government. Moreover, such an amendment would SCA should state that the exclusionary rule will apply to evidence obtained in violation of any of these statutory provisions, even if the evidence was eliminate the conflicting interpretations of the SCA. Fourth, the not obtained pursuant to a government search under the Fourth Amendment. Without this last component, the SCA, in the criminal context, will not extend any privacy protections beyond what the Fourth Amendment already guarantees. Fifth, to ensure that administrative subpoenas do not lead to unjustified intrusions of privacy on the Internet, federal law should ensure judicial safeguards in the form of a neutral magistrate who protects against over breadth and harassment and requires an explanation as to why a subpoena is necessary. Moreover, if a subpoena will not provide a user with notice and the chance to file a motion to quash, federal laws should limit the issuance of subpoenas to life-threatening crimes in which time is of the essence. Sixth, Congress should mandate encryption for those government and non-government entities that transmit sensitive or private information through the Internet. Since not all companies have the resources to do this, the government should invest in more advanced encryption technology and other cyber-security measures to ensure the highest safety of sensitive and private content transmitted through the Internet.301 Under the existing Third Party Doctrine , encryption would increase users‘ expectation of privacy because Facebook employees would not be able to view all user content. While law enforcement agencies might argue that this will frustrate efforts to crack down on cybercrime (and all other crime), such encryption measures will also minimize the crime or cyberterrorism that results when others with more nefarious motives gain access to such information. Page 205 Solves Perception --- Generic CP solves accountability Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka B. Using Political Safeguards in Practice In giving shape to a statutory framework that provides a set of political checks and balances, it is useful to delineate the various interests that ought to be protected. First, privacy should be safeguarded to the extent possible. Second, there is independent and functional value in encouraging public debate and conveying to the public a sense of responsibility for deciding the difficult issues at play. Third, there must be protection against unlawful executive action in order to give effect to Congress's intent to "assure the public that it could engage in constitutionally protected political dissent without fear of surveillance, thus facilitating the exercise of individual liberty that is fundamental to American society." n98 Public nature guarantees perception of credibility Sugiyama and Perry 6 --- J.D.s from UMich Law School (Tara and Marisa, “THE NSA DOMESTIC SURVEILLANCE PROGRAM: AN ANALYSIS OF CONGRESSIONAL OVERSIGHT DURING AN ERA OF ONE-PARTY RULE”, 40 U. Mich. J.L. Reform 149, Lexis)//trepka Classified programs pose peculiar issues with respect to oversight. Most traditional methods of formal oversight - hearings , investigations , and adjusting appropriations - are successful because of their public nature , particularly when Congress uses them in response to a fire alarm. n263 In the case of the NSA program, the system broke down both before and after the media sounded the fire alarm. Congressional leaders of both parties failed to object in any meaningful way when the administration informed them of the program in 2001. n264 The administration also alerted the two presiding judges of the FISA court to the existence of the program, but the judges failed to take any action or consult with their colleagues. n265 Subsequent efforts at oversight have been quashed by the majority, n266 and debate over the surveillance program is slowly dying down. Only effective oversight solves international credibility //AT: Hurts National Security Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka ii. Arguments Favoring Disclosure Arguments also can be advanced to the effect that secrecy often is at best unnecessary and at worst harmful to national security. To begin with, there is good reason to question the conventional assumption that there are volumes of information of which it would be dangerous for enemies to learn. Players from across the political spectrum long have suggested that much of the information classified in the United States should not be classified. n99 In one striking example, Erwin N. Griswold, the former solicitor general of the deeply United States who fought on behalf of the Nixon administration to restrain publication of the classified Pentagon Papers, acknowledged years after the litigation: "I have never seen any trace of a threat to the national security from the [Papers'] publication. Indeed, I have never seen it even suggested that there was such an actual threat." n100 In the same discussion, Griswold deemed it "apparent to any person who has considerable experience with classified material that there is massive overclassification and that the principal concern of the classifiers is not with national security , but rather with governmental embarrassment of one sort or another." n101 There are persuasive arguments not only that national security based secrecy needs are dramatically overstated , but that excessive secrecy hurts national security by encouraging poorly informed and under-vetted decision-making and diminishing the United States' Page 206 domestic and international credibility . As I have noted elsewhere: Countless scholars, journalists, legislators and executive branch officials have noted secrecy's judgment-clouding and security-hindering effects in relation to historic and current events . For examples of such criticism, one needs to look no further than commentary on the 2003 invasion of Iraq . It has been argued repeatedly that the reticence of the press and of Congress to ask [*1067] difficult questions prior to the invasion of Iraq combined with the Bush administration's penchant for secrecy created an insular White House environment in which debate was stifled, " groupthink" flourished , and questionable data on weapons of mass destruction were embraced while predictions of a peaceful, post-invasion Iraq similarly went unquestioned. ... . Similar concerns have been raised about the negative impact of secrecy on homeland security , both prior to, and in the wake of, 9-11. ... . Similar analyses about more distant historical events [including the Vietnam War and the Cold War] abound. ... . [There also is a risk] that secrecy not only will be misused by well-meaning yet overzealous officials, but that it will intentionally be misused by those set on manipulating public debate toward their own ends. Indeed, McCarthy's exploitation of government secrecy calls to mind Vice President Cheney's recent attempts to perpetuate the theory of a link between Al Qaeda and Saddam Hussein through vague public allusions to evidence in the administration's possession of which others, including the 9-11 Commission, supposedly were not aware. Similarly, concerns long have been raised about executive branch "spinning of information" through selective declassification or leakage of otherwise classified information. n102 Such points are manifest in responses to the administration's arguments for keeping the NSA surveillance program largely secret. For one thing, critics charge that no convincing explanation has been offered as to why it would have endangered national security to reveal the program's bare existence to the public, let alone to the congressional intelligence committees. n103 And while public details of the program remain too scarce as of mid-2007 to evaluate its effectiveness, efficacy concerns intrinsically are raised by the insular nature of the decision-making process that generated the program. n104 These efficacy concerns are exacerbated by post-revelation disclosures that raise questions about the program's reach, the adequacy of its oversight and mistakes that [*1068] might have occurred in administering it. n105 Oversight prevents unchecked surveillance --- creates moral authority aborad Heinrich 6/10/15 --- Office of the Senator (Martin, “Heinrich, Murphy, Schatz Unveil Forward-Looking, Pragmatic Foreign Policy Principles”, US Official News, Lexis)//trepka 5. Covert actions like unchecked domestic surveillance or large scale overseas CIA lethal operations must be constrained . The dramatic expansion of our intelligence apparatus post-9/11, which operates largely unseen and unchecked, requires greater oversight and restraint. Decisions about government surveillance , lethal drone strikes overseas, and interrogation techniques must be made in the light of day and subject to greater congressional oversight . We can start by consolidating authority for offensive counterterrorism operations at the Department of Defense instead of the CIA, which has more limited congressional oversight. We can also ensure that Congress has greater oversight of "crossover" operations that overlap committee jurisdictions by requiring briefings on operations to include members across all relevant committees. 6. We must practice what we preach regarding civil and human rights, and defend our values internationally. America's reputation as a beacon of freedom and opportunity is a powerful asset - we must continue to honor our bedrock values of individual liberty and equal treatment under the law. Inadequate respect for civil rights domestically robs from America the moral authority to root out human rights abuses, corruption, and violence abroad . Actions abroad that are illegal under U.S. law and out of step with American values, like torture, must be absolutely prohibited. Human rights and gender equality should not be viewed as secondary to security issues, but appropriately recognized as essential to long-term global peace and stability. We can and should do more to support those who are working to create cultures of tolerance. Page 207 Solves Perception --- I-Law Only Congress solves international perception- Court looks too divided Interview of Noah Feldman- CFR Adjunct Senior Fellow- October 10, 2008, Interviewer: Robert McMahon, Deputy Editor, CFR.org, The Supreme Court's Mixed Signals on International Law, http://www.cfr.org/publication/17509/supreme_courts_mixed_signals_on_international_law.html The U.S. Supreme Court ruled in March 2008 (Medellin v. Texas) that U.S. states were not bound by International Court of Justice judgment on staying the execution of a Mexican national, running counter to Bush administration wishes. In a separate judgment (PDF) (Boumediene v. Bush) in June 2008, the court gave Guantanamo Bay detainees the right to have federal judges review the reason for their detention. That also challenged the White House, this time on its policy of detaining non-enemy combatants. CFR Adjunct Senior Fellow Noah Feldman says the rulings could send confusing signals to the rest of the world about U.S. compliance with international obligations. On the death penalty case, he says, the most important foreign policy consequence is that "legal institutions of the United States including the Supreme Court are very nervous about submitting the United States to the judgment of these international bodies." You wrote in the New York Times Magazine that the U.S. Supreme Court's landmark rulings last term on the Medellin death penalty case and the Guantanamo Bay detainee policy were essentially about what sort of constitution we have, either outward facing or inward looking. What does it mean for U.S. foreign policy that the court seems to be divided down the middle on that question? It means that we're communicating a kind of schizophrenic vision to those who are watching closely abroad. That's not unheard of. Sometimes the president will be of one party and Congress of a different party and there are differences in the foreign policy that we're projecting as a result of that division. But it's starker in the case of legal materials because the Supreme Court really does have the final say. We don't exactly know in any given situation what Justice [Anthony] Kennedy, who is the swing vote right now, is planning on doing. Another thing that it communicates to the rest of the world is that this next election is enormously important because, depending on who is elected and which justices they name, we'll the death penalty ruling, it calls into question something like seventy other U.S. treaties of a similar nature. Going forward, does this mean Congress has to weigh in explicitly on these? Yes, with respect to the series of agreements, many of them bilateral but some of them multilateral. Potentially there are even more than those seventy if one extrapolates. In any case where the treaty is arguably ambiguous with respect to whether it should be treated as law in a U.S. court, it is now fairly clear that it will not be treated as law in the U.S. courts unless Congress weighs in. That means that if you're another country trying to figure out what we're going to do, your safest bet is to assume we're not going to apply that treaty in our own courts unless Congress makes a special determination to that effect. probably have a much more coherent picture in the next five years than we do today. So taking one of the rulings, The plan is perceived worse internationally – speaking with multiple voices in foreign policy kills our credibility Wilkinson, Circuit Judge on the U.S. Court of Appeals for the 4th Circuit, former Law Professor at the University of Virginia, & former Deputy Assistant Attorney General of the U.S. Department of Justice Civil Rights Division, 4 (The Honarable J. Harvie, “DEBATE: THE USE OF INTERNATIONAL LAW IN JUDICIAL DECISIONS,” Harvard Journal of Law & Public Policy, Spring, 27 Harv. J.L. & Pub. Pol'y 423) So judges must not wade, sua sponte, into international law's deep blue sea. Rather, we ought to ask: How does American law make foreign or international standards relevant? Why it is important that the United States speak with one, not multiple, voices in foreign affairs. The Constitution is explicit on this: Article I, Section 10 says that "no State shall enter into any Treaty [or] Alliance" with a foreign power. n9 The Constitution leaves the conduct of foreign and military affairs largely to the political branches -- not the courts. The diplomatic credibility of the United States would plummet if the actions and pronouncements of the executive and legislative branches in foreign and military matters were later repudiated and contradicted by judicial decree. Where courts go too far, in my view, is where they rely upon international (and mostly should we ask this threshold question? Because European) precedents when resolving important and contentious social issues. This "internationalization" of the Constitution on domestic social issues raises three types of problems. Page 208 Solves Prez Powers Page 209 Increases Prez Powers Congress solves prez powers better Plummer 6 --- J.D., Mississippi College School of Law, law clerk for Barnes of the Mississippi Court of Appeals (Brooke, “Domestic Spying: A Necessity in a Post-9/11 America or an Abuse of Presidential Power?”, Mississippi College Law Review, Lexis)//trepka C. Presidential Inherent Authority The seminal case on the subject of inherent presidential authority is that of Youngstown Sheet & Tube Co. v. Sawyer, n14 which revolved around whether it was within President Truman's constitutional authority to seize possession and operation of the nation's steel mills. President Truman offered as justification for his actions the need to prevent the "national catastrophe" that would have resulted from steel production halting in the United States. n15 The case is famous not for its majority opinion, which found that President Truman had acted outside of the power conferred upon him by the Constitution, but for Justice Jackson's concurrence, which delineated the following three zones of presidential power: n16 1. When the President acts pursuant to an express or implied authorization of Congress, his authority is at its maximum, for it includes all that he possesses in his own right plus all that Congress can delegate. In these circumstances, and in these only, may he be said (for what it may be worth), to personify the federal sovereignty. If his act is held unconstitutional under these circumstances, it usually means that the Federal Government as an undivided whole lacks power. A seizure executed by the President pursuant to an Act of Congress would be supported by the strongest presumptions and the widest latitude of judicial interpretation, and the burden of persuasion would rest heavily upon any who might attack it. n17 ... . 2. When the President acts in absence of either a congressional grant or denial of authority, he can only rely upon his [*307] own independent powers , but there is a zone of twilight in which he and Congress may have concurrent authority, or in which its distribution is uncertain. Therefore, congressional inertia, indifference, or quiescence may sometimes, at least as a practical matter, enable, if not invite, measures on independent presidential responsibility. In this area, any actual test of power is likely to depend on imperatives of events and contemporary imponderables rather than on abstract theories of law. n18 ... . 3. When the President takes measure incompatible with the express or implied will of Congress, his power is at its lowest ebb , for then he can rely only upon his own constitutional powers minus any constitutional powers of Congress over the matter. Courts can sustain exclusive Presidential control in such a case only [by] disabling the Congress from acting upon the subject. Presidential claim to a power at once so conclusive and preclusive must be scrutinized with caution, for what is at stake is the equilibrium established by our constitutional system. n19 Page 210 Decreases Prez Powers Congressional constraints undermine prez powers Harrington 7 --- J.D., Albany Law School of Union University (Alexandra, “PRESIDENTIAL POWERS REVISITED: AN ANALYSIS OF THE CONSTITUTIONAL POWERS OF THE EXECUTIVE AND LEGISLATIVE BRANCHES OVER THE REORGANIZATION AND CONDUCT OF THE EXECUTIVE BRANCH”, 44 Willamette L. Rev. 63, Lexis)//trepka B. Patterns of Congressional Usurpation and Reorganization As discussed above, the years since the end of World War II have seen a dramatic rise in the incidents of congressional involvement and attempted involvement in areas which were once recognized as the sole province of the Executive. n260 This represents more than a benign and vigorous attempt to do the duties vested in the legislative branch by the Constitution; rather, it represents a bipartisan attempt to enlarge congressional powers at the expense of the executive branch, particularly in the realm of national security , the military, and foreign policy. After World War II, Truman's decision to retain an intelligence operation similar to the OSS caused him to seek funding for the CIA, which in turn resulted in the National Security Act of 1947 and the creation of the CIA as a separate agency. n261 From this point on, Congress became increasingly interested in the activities of the American intelligence community; this interest frequently went beyond predictable appropriations reasons. n262 Requests for information on CIA and other intelligence community member activities during the 1960s and 1970s were made by various congressional committees. n263 When [*99] these requests were complied with, predictably, they revealed information which was startling and possibly repugnant to some in the public, the government, and the press, and resulted in the creation of an extensive notification protocol imposed by Congress on the President and members of the intelligence community whenever covert action was to be used. n264 These actions, though compelling sound bites for television news show appearances and constituent newsletters, directly interfered with the powers of the Executive to control national security, as vested in him by the constitutional Commander-in-Chief provision and recognized implicitly and explicitly for centuries. Intelligence operations have come under increasingly intense scrutiny from various members of Congress and there has been a chorus of requests for at least the basic elements of the intelligence community's budget to be declassified and released to the public despite explanations from those in the Executive and intelligence community which highlight the danger of doing so and the necessity of maintaining the current classified system. n265 At the same time, Congress imposed strict funding and budgetary restrictions on the intelligence community as a whole through such acts as the IRTPA, which requires that the DNI inform Congress prior to shifting money from one operation to another even after an internal, executive finding of necessity has already been made. n266 Congress has periodically attempted to reorganize the Executive and its constituent parts. n267 It achieved part of this goal in 2002, with the creation of DHS, and in 2004, with the creation of the DNI and its attempt to streamline the intelligence community overall. n268 This Article has already shown that the majority of the provisions in both of these acts were already provided for by Executive Orders issued by the President and, further, that these acts were enacted despite evidence that the best way to handle the perceived problems with the American intelligence community legislative branch encroachment upon the executive branch and its functions, these acts further usurped executive powers and prior to September 11th was through purely executive action. It is important to note that, in addition to the [*100] functions by attempting to legislate at least some aspects of the security classification process. Similarly, Congress created the War Powers Resolution in an attempt to reign in the powers of the Executive under the Commander-in-Chief Clause and its associated historical construction without regard to the strictures of the Constitution or its Framers regarding the primacy of the Executive in military affairs. n269 Although it has never been challenged in court, current and past members of Congress agree that the War Powers Resolution is inherently unconstitutional, and the signing statements of every President since Nixon indicate that this belief is shared by the executive branch regardless of party affiliation. n270 Recent attempts by Congress to use its appropriations powers to force the Executive to change its stance on and course in the Iraq war n271 are current illustrations of the fact that the same mindset which created the War Powers Resolution still exists in Congress today and that it has become so seethingly anti-Executive that it threatens to undermine the role of the President as the arbiter of American national security policy , military policy , and foreign policy . Further, scant attention has been paid to the question of whether the current "war on terrorism" is in fact a "war" which the Congress can declare or seek to control through measures other than appropriations restrictions. Using the legal definition of a declaration of war requires that a nation declare war on another nation. n272 While the war on terror has effectively targeted the former regimes in Afghanistan and Iraq, the current phase of the war is truly fighting terrorists of all nationalities, who have flocked to an ideology rather than a flag. This issue has not been properly addressed as members of Congress from both political parties have eagerly attempted to denigrate the presidency rather than determining the bounds of their own constitutional abilities. Page 211 AT: Circumvention Solves public engagement and forces effective review Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka 2. Public Engagement. - Putting Congress in the position of primary responsibility would have the effect not only of enabling it to exercise review, but in some ways of forcing it to do so. Congress would have to publicly debate and announce the applicable statutory standards, which, as noted, would mark a major departure from the TSP. This would require the public to give serious thought as to how to balance the competing demands in this area of the law. In addition, the American people would be able to demand accountability from their elected representatives to exercise adequate oversight . Thus, accountability could be demanded of both the overseeing Congress and the overseen Executive . Continual monitoring guarantees guideline adoption Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka 3. Preventing Unlawful Action. - Of primary importance in this area is Congress's continuing monitoring of the conduct of surveillance. In this regard, the House bill's provision of consistent inspectors general review and internal guideline adoption , along with the Commission it proposes, are quite helpful. Failure devastates intelligence Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka B. Recommendations Clearly the need for oversight reform in Congress is great. Congress's role in the oversight process is crucial in both ensuring compliance with the law and in facilitating a functional, aggressive, and efficient Intelligence Community. An inefficient oversight structure impairs intelligence operations. The recommendations contained herein are neither unique nor revolutionary, but rather a common sense distillation of various examinations of Congress's role. The risk of public disclosure enhances accountability Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka Nonetheless, there are some formal and informal factors that may enhance Congress' political incentives to conduct meaningful oversight . One set of formal requirements are the successive funneling rules described above in Subpart B. The possibility that a Committee majority might at some point vote to make information more widely available, even public, creates some incentive to act responsibly lest one's intransigence become widely known. Of course, these successive funneling requirements themselves run into political accountability problems. Such problems likely account for the fact that neither intelligence committee has used its formal power to publicize classified information. n204 Successive funneling rules might, however, contribute to a structure that facilitates political accountability overall. The impact of successive funneling rules, and the strength of an overall political accountability structure, might thus be heightened as other elements of the structure are enhanced. Another relevant set of Page 212 formal factors are requirements that some funneled information be in writing. Once information is in writing, it becomes harder for writers or recipients to distance themselves from it if it ever is revealed. The statutory funneling rules at present contain some in-writing requirements. For example, the intelligence agencies are required to "keep the congressional intelligence committees fully and currently informed of all ... significant anticipated intelligence activity and any significant intelligence failure." n205 Such reports must be in writing. n206 Similarly, certain Presidential findings must be made to justify a covert action and such findings generally must be submitted in writing to the intelligence committees. n207 While delays in notice or temporarily limited notice are permitted, such delays or limitations must eventually be explained in writing. n208 Factors less formal than statutory and committee rules can also impact political accountability. The political climate , of course, can be very significant. Indeed, the mid to late 1970s has been called a high point for congressional oversight of national security. This characterization is attributed largely to the well-known executive branch abuses, often under the guise of national security, of the late 1960s and [*1086] early 1970s. n209 These events are thought to have generated an unusually high public tolerance, even appetite, for oversight of the executive branch. n210 Of course, the political climate cannot by itself ensure effective oversight. Other necessary factors include a Congress that is not paralyzed from acting by partisanship or by other political disincentives. As Walter Mondale, who as a senator contributed substantially to the intelligence oversight of the 1970s notes, no one can force Congress to have courage. n211 Political and congressional cultures are crucial components of effective oversight . The relevant questions are what if anything might do done to improve oversight cultures and what role if any might formal rule changes play in such improvements. Page 213 AT: Classifying Stuff Good Declassification is key to transparency --- internal checks prevent their disads Ford 7 --- Assistant Professor of Law @ US Military Academy (Christopher, “Intelligence Demands in a Democratic State: Congressional Intelligence Oversight”, 81 Tul. L. Rev. 721, Lexis)//trepka c. Secrecy A comment from Congressman Tim Roemer concurrently illustrates two problems - information sharing within the committees and the overclassification of information: One of my great frustrations during my service on the Permanent Select Committee on Intelligence has been the degree to which access to information is restricted, either from the committee or within the committee, often for reasons that have little or no correlation to national security. Many times, these restrictions have the effect of impairing the ability of members of the committee to make fully informed decisions on important budgetary or policy matters ... . Classification should be for important national security reasons ... . n366 [*770] Congressman Roemer is not alone in his criticism. The Intelligence Community has been roundly criticized for overclassifying information. n367 Millions of documents are classified every year. n368 By some accounts, a majority of the classified information should not be classified. n369 Most obviously, this has a tendency to reduce the transparency of government - a principal the Court has strongly criticized. n370 Further, overclassification has the tendency to dilute the meaning of "secret." The idea is that, when everything is secret, nothing is secret. Finally, the costs associated with safekeeping, declassifying, or destroying such a volume of documents are tremendous. This issue was recently addressed by the Subcommittee on National Security, Emerging Threats, and International Relations in the House Committee on Government Reform; it succinctly summarized the problems arising from this issue: Overclassification ultimately incurs avoidable fiscal costs and compromises national security . Adversarial, versus automatic, declassifications procedures are cumbersome and time consuming. Safeguards for voluminous classified material require costly security measures. And government officials confronted with dizzyingly complex rules for numerous categories of classified information often [*771] cannot or do not distinguish truly significant security matters from routine material market secret out of an excess of caution or zeal. n371 Reducing the classification of documents and programs would thus produce significant cost savings and increased efficiency. A similar effect could be found by implementing more automatic declassification protocols. Closely related to the problem of overclassifying information is the exact opposite - " leaks " of national security information. As noted above, one of the traditional fears of the Executive is the leaking of information through Congress. This fear, of course, causes the executive to err on the side of caution when sharing sensitive information. As with free speech, this unnecessarily " chills " communication between Congress and the executive. As noted by a member of the Senate Committee composing the Joint Inquiry Report: "Congress should take decisive steps to help stem our contemporary culture of endemic "leaking' of national security information to the media, so as better to ensure that our analysts remain better informed about terrorists than the terrorists do about them." n372 Again, this internal checks. demands aggressive Page 214 AT: Courts Key Only Congress solves --- it spills over to the judiciary Rahdert 7 --- Professor of Law (Mark, “DOUBLE-CHECKING EXECUTIVE EMERGENCY POWER: LESSONS FROM HAMDI AND HAMDAN”, 80 Temp. L. Rev. 451, Lexis)//trepka The implications of this double-check method for the treatment of detainees in the war on terror depend heavily on congressional action, a result that is generally consistent with the aims of representative democracy. Responsibility falls in the first instance on the people's elected representatives to set the limits of executive authority in times of proclaimed national security crisis. When Congress takes an active role, the courts have the tools they need for an effective executive double check ; if Congress remains passive , however, there is relatively little the judiciary can do on its own to restrain executive emergency power. So far in the war on terror, Congress has shown a disinclination to assume an active limiting role. In light of the Detainee Treatment Act of 2005 ("DTA") n24 and the Military Commissions Act of 2006 ("MCA"), n25 the double-check theory thus may not have as much impact on the present administration's conduct of the war on terrorism as some of its critics may have hoped. n26 The military commissions and practices of detention that were once the objects of executive fiat have now become the artifacts of legislative policy - making the military commissions for trial of enemy combatants what in other contexts we call, with reason, "Article I courts." If there are to be any further restraints on their power, they must come from the judiciary acting alone against executive emergency power, a development that is arguably unprecedented in our history. Nevertheless, the double-check theory's influence has begun to reshape the power contours and political dynamics of the [*457] present situation, showing that it serves as a more-than-symbolic potential limit on future executive authority claims. We’ll turn their courts key claims – First, court credibility – internationalizing the Constitution undermines Court credibility and the perception of an independent judiciary Wilkinson, Circuit Judge on the U.S. Court of Appeals for the 4th Circuit, former Law Professor at the University of Virginia, & former Deputy Assistant Attorney General of the U.S. Department of Justice Civil Rights Division, 4 (The Honarable J. Harvie, “DEBATE: THE USE OF INTERNATIONAL LAW IN JUDICIAL DECISIONS,” Harvard Journal of Law & Public Policy, Spring, 27 Harv. J.L. & Pub. Pol'y 423) Where courts go too far, in my view, is where they rely upon international (and mostly European) precedents when resolving important and contentious social issues. This "internationalization" of the Constitution on domestic social issues raises three types of problems. The first is that an over-reliance on foreign precedents may serve to compromise judicial decisions in the eyes of the American public. Judges serve as unelected stewards of the Constitution whose power rests in part on their ability to persuade. While majorities may simmer [*426] when judges vindicate the rights of minorities, in the long run judges can promote respect for their decisions by appealing to principles that Americans can relate to as part of an American constitutional tradition. The counter-majoritarian difficulty is thus alleviated when judges draw upon when judges rely on foreign sources, especially for difficult constitutional they move the bases for judicial decision-making even farther from the realm of both democratic accountability and popular acceptance. They aggravate the risks already inherent in having unelected officials overrule popular enactments by creating the perception that foreign sentiment shapes domestic law. To be sure, examples from other countries may be illuminating. But the Court's legitimacy must ultimately rest on reliance and reference to the American Constitution and to American democratic; outcomes, from which their judicial authority springs. By relying on foreign laws and rulings over which the American people have no control -- either directly through the power of election or even indirectly through the process of judicial appointment -- judges risk estranging and disempowering the public. I fear that the internationalization of our constitutional values may thus undermine public acceptance of our judicial system. A closely related danger is that reliance on foreign precedents may stimulate popular perceptions that judges are out of touch with American culture. The risks of a common perception of judicial distance and removal should not be underestimated. The detachment and insulation which an independent judiciary properly enjoys should not be endangered by pronouncements that appear targeted at foreign and domestic elites rather than the American public at large. The power of persuasion which sustains judicial authority must not common principles and ideas that form our shared American heritage. But questions concerning domestic social issues, Page 215 neglect those very people whose acceptance of judicial decree is most essential. Americans treasure their diversity and their identity. The great Willa Cather novels, My Antonia and O Pioneers!, still play a prevalent role in the American psyche, and the distance from American to European modes of thought remains in some vital particulars more psychological than physical. The distinguished Harvard historian, Bernard Bailyn, has noted that the power of the American Constitution derived from the fact that its framers were proud and stubborn provincials, that they did not accept all the received wisdom of the Continent, and that, for example, the [*427] animating constitutional idea of dual and concurrent sovereignties actually rejected the contrary notions of the French theorist Montesquieu. n10 That flips all of their human rights and democracy internal links van Aelstyn, Counsel of Record for the Center for Justice & Accountability, 4 (Nicholas, Brief of the Center for Justice & Accountability, the International League for Human Rights, & Individual Advoacates for the Independence of the Judiciary in Emerging Democracies as Amici Curiae in Support of Petitioners, In the Supreme Court of the United States on Writ of Certiorari to the United States Court of Appeals for the D.C. Circuit, Fawzi Khalid Abdullah Fahad Al Odah et al., Petitioners v. United States of America et al., Respondents, & Shafiq Rasul et al., Petitioners v. George W. Bush, et al., Respondents, Supreme Court case numbers 03-334 and 03-343) Many of the newly independent governments that have proliferated over the past five decades have adopted these ideals. They have emerged from a variety of less-than-free contexts, including the end of European colonial rule in the 1950's and 1960's, the end of the Cold War and the breakup of the former Soviet Union in the late 1980's and 1990's, the disintegration of Yugoslavia, and the continuing turmoil in parts of Africa, Latin America and southern Asia. Some countries have successfully transitioned to stable and democratic forms of government that protect individual freedoms and human rights by means of judicial review by a strong and independent judiciary. Others have suffered the rise of tyrannical and oppressive rulers who consolidated their hold on power in part by diminishing or abolishing the role of the judiciary. And still others hang in the balance, struggling against the onslaught of tyrants to establish stable, democratic governments. In their attempts to shed their tyrannical pasts and to ensure the protection of individual rights, emerging democracies have consistently looked to the United States and its Constitution in fashioning frameworks that safeguard the independence of their judiciaries. See Ran Hirschl, The Political Origins of Judicial Empowerment through Constitutionalization: Lessons from Four Constitutional Revolutions, 25 Law & Soc. Inquiry 91, 92 (2000) (stating that of the “[m]any countries . . . [that] have engaged in fundamental constitutional reform over the past three decades,” nearly all adopted “a bill of rights and establishe[d] some form of active judicial review”). 19 Establishing judicial review by a strong and independent judiciary is a critical step in stabilizing and protecting these new democracies. See Christopher M. Larkins, Judicial Independence and Democratization: A Theoretical and Conceptual Analysis, 44 Am. J. Comp. L. 605, 605-06 (1996) (describing the judicial branch as having "a uniquely important role" in transitional countries, not only to "mediate conflicts between political actors but also [to] prevent the arbitrary exercise of government power; see also Daniel C. Prefontaine and Joanne Lee, The Rule of Law and the Independence of the Judiciary, International Centre for an independent judiciary is the key to upholding the rule of law in a free society . . . . Most countries in transition from dictatorships and/or statist economies recognize the need to create a more Criminal Law Reform and Criminal Justice Policy (1998) ("There is increasing acknowledgment that stable system of governance, based on the rule of law."), available at http://www.icclr.law.ubc.ca/Publications/Reports/RuleofLaw. pdf (last visited Jan. 8, 2004). Although the precise form of government differs among countries, “they ultimately constitute variations within, not from, the American model of constitutionalism . . . [a] specific set of fundamental rights and liberties has the status of supreme law, is entrenched against amendment or repeal . . . and is enforced by an independent court . . . .” Stephen Gardbaum, The New Commonwealth Model of Constitutionalism, 49 Am. J. Comp. L. 707, 718 (2001). This phenomenon became most notable worldwide after World War II when certain countries, such as Germany, Italy, and Japan, embraced independent judiciaries following their bitter experiences under totalitarian regimes. See id. at 714- 15; see also United States v. Then, many countries have adopted forms of judicial review, which — though different from ours in many particulars — unmistakably draw their origin and inspiration from American constitutional theory and practice. See generally Mauro Cappelletti, The Judicial Process in Comparative Perspective (Oxford: Clarendon Press, 1989).”). 56 F.3d 464, 469 (2d Cir. 1995) (Calabresi, J., concurring) (“Since World War II, It is a trend that continues to this day. 20 It bears mention that the United States has consistently affirmed and encouraged the establishment of independent judiciaries in emerging democracies. In September 2000, President Clinton observed that "[w]ithout the rule of law, elections simply offer a choice of dictators. . . . America's experience should be put to use to advance the rule of law, where democracy's roots are looking for room and strength to grow." Remarks at Georgetown University Law School, 36 Weekly Comp. Pres. Doc. 2218 (September 26, 2000), available at http://clinton6.nara.gov/2000/09/2000-09-26- remarks-by-president-at-georgetown-international-lawcenter. html. The United States acts on these principles in part through the assistance it provides to developing nations. For example, the United States requires that any country seeking assistance through the Millenium Challenge Account, a development assistance program instituted in 2002, must demonstrate, among other criteria, an "adherence to the rule of law." The White House noted that the rule of law is one of the "essential conditions for successful development" of these countries. See http://www.whitehouse.gov/infocus/developingnations (last visited Jan. 8, 2004).12 A few examples illustrate the influence of the United States model. On November 28, 1998, Albania adopted a new constitution, representing the culmination of eight years of democratic reform after the communist rule collapsed. In addition to protecting fundamental individual rights, the Albanian Constitution provides for an independent judiciary consisting of a Constitutional Court with final authority to determine the constitutional rights of individuals. Albanian Constitution, Article 125, Item 1 and Article 128; see also Darian Pavli, "A Brief 'Constitutional History' of Albania" available at http://www.ipls.org/services/others/chist.html (last visited Janaury 8, 2004); Jean-Marie Henckaerts & Stefaan Van der Jeught, Human Rights Protection Under the New Constitutions of Central Europe, 20 Loy. L.A. Int’l & Comp. L.J. 475 (Mar. 1998). In South Africa, the new constitutional judiciary plays a similarly important role, following generations of an oppressive apartheid regime. South Africa adopted a new constitution in 1996. Constitution of the Republic of South Africa, Explanatory Memorandum. It establishes a Constitutional Court which “makes the final decision whether an Act of Parliament, a provincial Act or conduct of the President is constitutional.” Id. at Chapter 8, Section 167, Item (5), available at http://www.polity.org.za/html/govdocs/constitution/saconst.html?r ebookmark=1 (last visited January 8, 2004); see also Justice Tholakele H. Madala, Rule Under Apartheid and the Fledgling Democracy in Post-Apartheid South Africa: The Role of the Judiciary, 26 N.C. J. Int’l L. & Com. Reg. 743 (Summer 2001). Afghanistan is perhaps the most recent example of a country struggling to develop a more democratic form of government. Adoption by the Loya Jirga of Afghanistan's new constitution on January 4, 2004 has been hailed as a milestone. See http://www.cbsnews.com/stories/2004/01/02/world/main59111 6.shtml (Jan 7, 2004). The proposed constitution creates a judiciary that, at least on paper, is "an independent organ of the state," with a Supreme Court empowered to review the constitutionality of laws at the request of the Government and/or the Courts. Afghan Const. Art. 116, 121 (unofficial English translation), available at http://www.hazara.net/jirga/AfghanConstitutionFinal.pdf (last visited January 8, 2004). See also Ron Synowitz, Afghanistan: Constitutional Commission Chairman Presents Karzai with Long-Delayed Draft Constitution (November 3, 2003), available at http://www.rferl.org/nca/features/2003/11/03112003164239.as p (last visited Jan. 8, 2004). B. Other Nations Have Curtailed Judicial Review During Times Of Crisis, Often Citing the United States' Example, And Individual Freedoms Have Diminished As A Result. While much of the world is moving to adopt the institutions necessary to secure individual rights, many still regularly abuse these rights. One of the hallmarks of tyranny is the lack of a strong and independent judiciary. Not surprisingly, where countries make the sad transition to tyranny, one of the first victims is the judiciary. Many of the rulers that go down that road justify their actions on the basis of national security and the fight against terrorism, and, disturbingly, many claim to be modeling their actions on the United States. Again, a few examples illustrate this trend. In Peru, one of former President Alberto Fujimori’s first acts in seizing control was to assume direct executive control of the judiciary, claiming that Page 216 it was justified by the threat of domestic terrorism. He then imprisoned thousands, refusing the right of the judiciary to intervene. International Commission of Jurists, Attacks on Justice 2000-Peru, August 13, 2001, available at http://www.icj.org/news.php3?id_article=2587&lang=en (last visited Jan. 8, 2004). In Zimbabwe, President Mugabe’s rise to dictatorship has been punctuated by threats of violence to and the co-opting of the judiciary. He now enjoys virtually total control over Zimbabweans' individual rights and the entire political system. R.W. Johnson, Mugabe’s Agents in Plot to Kill Opposition Chief, Sunday Times (London), June 10, 2001; International Commission of Jurists, Attacks on Justice 2002— Zimbabwe, August 27, 2002, available at http://www.icj.org/news.php3?id_article=2695&lang=en (last visited Jan. 8, 2004). While Peru and Zimbabwe represent an extreme, the independence of the judiciary is under assault in less brazen ways in a variety of countries today. A highly troubling aspect of this trend is the fact that in many of these instances 23 those perpetuating the assaults on the judiciary have pointed to the United States’ model to justify their actions. Indeed, many have specifically referenced the United States’ actions in detaining persons in Guantánamo Bay. For example, Rais Yatim, Malaysia's "de facto law minister" explicitly relied on the detentions at Guantánamo to justify Malaysia's detention of more than 70 suspected Islamic militants for over two years. Rais stated that Malyasia's detentions were "just like the process in Guantánamo," adding, "I put the equation with Guantánamo just to make it graphic to you that this is not simply a Malaysian style of doing things." Sean Yoong, "Malaysia Slams Criticism of Security Law Allowing Detention Without Trial," Associated Press, September 9, 2003 (available from Westlaw at 9/9/03 APWIRES 09:34:00). Similarly, when responding to a United States Government human rights report that listed rights violations in Namibia, Namibia's Information Permanent Secretary Mocks Shivute cited the Guantánamo Bay detentions, claiming that "the US government was the worst human rights violator in the world." BBC Monitoring, March 8, 2002, available at 2002 WL 15938703. Nor is this disturbing trend limited to these specific examples. At a recent conference held at the Carter Center in Atlanta, President Carter, specifically citing the Guantánamo Bay detentions, noted that the erosion of civil liberties in the United States has "given a blank check to nations who are inclined to violate human rights already." Doug Gross, "Carter: U.S. human rights missteps embolden foreign dictators," Associated Press Newswires, November 12, 2003 (available from Westlaw at 11/12/03 APWIRES 00:30:26). At the same conference, Professor Saad Ibrahim of the American University in Cairo (who was jailed for seven years after exposing fraud in the Egyptian election process) said, "Every dictator in the world is using what the United States has done under the Patriot Act . . . to justify their past violations of human rights and to declare a license to continue to violate human rights." Id. Likewise, Shehu Sani, president of the Kaduna, Nigeriabased Civil Rights Congress, wrote in the International 24 Herald Tribune on September 15, 2003 that "[t]he insistence by the Bush administration on keeping Taliban and Al Quaeda captives in indefinite detention in Guantánamo Bay, Cuba, instead of in jails in the United States — and the White House's preference for military tribunals over regular courts — helps create a free license for tyranny in Africa. It helps justify Egypt's move to detain human rights campaigners as threats to national security, and does the same for similar measures by the governments of Ivory Coast, Cameroon and Burkina Faso." Available at http://www.iht.com/ihtsearch.php?id=109927&owner=(IHT)&dat the U S sets an important example e=20030121123259. In our uni-polar world, nited tates obviously on these issues. As reflected in the foundational documents of the United Nations and many other such agreements, the international community has consistently affirmed the value of an independent judiciary to the defense of universally recognized human rights. In the crucible of actual practice within nations, many have looked to the United States model when developing independent judiciaries with the ability to check executive power in the defense of individual rights. Yet others have justified abuses by reference to the conduct of the United States. Far more influential than the words of Montesquieu and Madison are the actions of the United States. This case starkly presents the question of which model this Court will set for the world. CONCLUSION Much of the world models itself after this country’s two hundred year old traditions — and still more on its day to day implementation and expression of those traditions. To say that a refusal to exercise jurisdiction in this case will have global implications is not mere rhetoric. Resting on this Court’s decision is not only the necessary role this Court has historically played in this country. Also at stake are the freedoms that many in emerging democracies around the globe seek to ensure for their peoples. The aff’s ruling creates a slippery slope Wilkinson, Circuit Judge on the U.S. Court of Appeals for the 4th Circuit, former Law Professor at the University of Virginia, & former Deputy Assistant Attorney General of the U.S. Department of Justice Civil Rights Division, 4 (The Honarable J. Harvie, “DEBATE: THE USE OF INTERNATIONAL LAW IN JUDICIAL DECISIONS,” Harvard Journal of Law & Public Policy, Spring, 27 Harv. J.L. & Pub. Pol'y 423) In recent cases, comparative analysis has appeared to be a one-way ratchet toward expansion of individual rights and toward restriction of democratic prerogatives. The countries that take a more traditionalist view of social questions are almost never referred to. And foreign experiences seem to be consulted only on issues in which the United States is more traditional than other nations. Is this fair? Is this balanced? Again, my point today pertains not to results reached in recent decisions but the course on which courts are newly embarked presents the oldest form of legal danger -- that of a treacherous and slippery slope. to methodology. I hope there will be some recognition that That turns the case and locks in ineffective foreign policy Nzelibe, Law Professor at Chicago, 4 (Jide, Bigelow Fellow & Lecturer in Law at the University of Chicago Law School, “The Uniqueness of Foreign Affairs,” Iowa Law Review, March, 89 Iowa L. Rev. 941) In many circumstances, the political question doctrine can be justified by the fact that the costs of judicial intervention in foreign affairs are considerably high while the benefits, if any, are entirely speculative . At first glance, this rationale seems problematic because any attempt to calculate the costs of judicial intervention would likely encounter methodological difficulties, especially since there seems to be no clear criteria for comparing judicial versus political branch performance in foreign affairs controversies. Nonetheless, there are certain institutional considerations that warrant a intervention in foreign affairs controversies is likely to impose serious costs on the administration of foreign policy. One such consideration involves the fact that the courts are not capable of understanding or conclusion that judicial controlling the effects of their decisions on foreign countries, nor do they have any control over the reaction of foreign countries to their decisions. The second, yet related, consideration is that the various remedial devices available to the courts - injunctions, writs, declaratory relief, and contempt orders - are particularly ill-suited to matters relating to foreign affairs. a. Assessing the Costs of Judicial Page 217 Intervention The costs associated with judicial error are most evident in cases involving controversies over the allocation of war powers. First, the nature of such controversies often requires immediate attention , and it may prove costly for the political branches to await the outcome of a judicial determination. Second, to the extent that a determination will turn on whether the executive branch has produced sufficient evidence to warrant the commencement of military hostilities without congressional authorization, the consequences of judicial error can be extremely high, if not catastrophic. Imagine, for instance, that the Supreme Court sets forth a standard for war powers controversies that requires the President to demonstrate that a foreign country imposes an imminent threat to national security before he can commence military hostilities without congressional authorization. If the Court errs in its assessment of the severity of an external threat, its judgment could leave the country defenseless in the event of an attack. Such difficulties underscore an important difference [*993] between domestic controversies and foreign controversies. In a domestic controversy, the costs of judicial error are rarely so immediate and guaranteed to impact a wide number of the U.S. citizenry. It is also true that in the domestic context, the courts often have ample opportunity, over time, to correct any prior interpretive errors. This risk of judicial error is implicit in the decisions that treated the legality of the Vietnam War as a political question. For example, with respect as to whether the President's decision to mine the harbors of North Vietnam constituted an unauthorized escalation of war under the War Powers Act, the Second Circuit articulated the risk of that court's involvement in these terms: Judges, deficient in military knowledge, lacking vital information upon which to assess the nature of battlefield decisions, and sitting thousands of miles from the field of action, cannot reasonably or appropriately determine whether a specific military operation constitutes an "escalation" of the war or is merely a new tactical approach within a continuing strategic plan ... Are the courts required to oversee the conduct of the war on a daily basis, away from the scene of action? In this instance, it was the President's view that the mining of North Vietnam's harbors was necessary to preserve the lives of American soldiers in South Vietnam and to bring the war to a close. History will tell whether or not that assessment was correct, but without the benefit of such extended hindsight we are powerless to know. n225 Using this framework, the court concluded that political branches were better equipped to handle the foreign affairs and war strategy questions before it. One might object and argue that the circumstances described above would only apply when war or imminent threats to national security issues are at stake. While national security concerns best illustrate the dangers of judicial intervention, framing this factor exclusively in terms of war is not appropriate. First, as explained in Section A above, it is often difficult to separate national security issues from other soft diplomacy concerns. n226 Second, and more importantly, the costs of judicial intervention stem not so much from the fact that war may be a factor, but that the courts are incapable of predicting whether foreign nations may be affected by a judicial decision, or how such nations may react to such a decision. This latter consideration extends to issues affecting international trade and commerce, as well as international security. As explained by Justice Brennan in Container [*994] Corp. of America v. Franchise Tax Board, n227 a case involving a tax dispute, "this Court has little competence in determining precisely when foreign nations will be offended by particular acts." n228 In the absence of a more precise understanding of the foreign interests that may be adversely affected by a judicial determination, the courts have appropriately left the resolution of such foreign affairs disputes to the political branches. Retaliation devastates the courts ability to solve any problem Carrington, Alabama Law, 99 (Paul, “Restoring Vitality to State and Local Politics by Correcting the Excessive Independence of the Supreme Court,” Alabama Law Review, Winter, v. 50, p. 411) courts assuming the role of third chamber to bicameral legislatures invite political attack threatening their own independence, thereby diminishing their competence for the more humdrum, but more essential, work of enforcing legal rights and duties. When high courts displace legislatures as cockpits for partisan struggle, there is no organ remaining that is qualified by disinterest to decide "cases and controversies" involving politically sensitive matters by applying law to fact. For all these reasons, Justices who are "pragmatists" in the contemporary, permissive sense threaten the political stability of the Republic and thereby indirectly threaten our civil liberties, civil rights, and market capitalism, all of which depend on the political stability the Republic affords. Third, Congress is key to solvency --- there’s no standing to address domestic surveillance in court which means the aff gets rolled back NCC 13 --- National Constitution Center Staff (“Podcast: Kerr, Rotenberg on NSA domestic surveillance”, http://blog.constitutioncenter.org/2013/10/audio-kerr-rotenberg-on-warrantless-surveillance/)//trepka Kerr also believes there are problems with Section 215, but the issues should be dealt with by Congress or the FISA court—and not the U.S. Supreme Court. In February 2013, the Supreme Court said, in a 5-4 decision , that government warrantless surveillance laws can’t be challenged in court, Page 218 because plaintiffs don’t have standing to sue over secret procedures that they are unaware of directly. Domestic surveillance falls in legislative powers Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka opponents argue that Congress and the President share powers in both military and domestic affairs, that domestic surveillance falls well within Congress' legislative powers, and that the President thus must conduct any operations On the constitutional points, within FISA's parameters. n25 B. Administration Disclosures to Congresspersons Prior to the Program's Public Revelation Also discussed in the wake of the program's public revelation, though much less so, is whether the administration adequately informed Congress about the program before it became public. Prior to the program's public revealing, the administration notified only members of the Congressional leadership, or "Gang of Eight," consisting of "the chairmen and ranking minority members of the congressional intelligence committees, the Speaker and minority leader of the House of Representatives, and the majority and minority leaders of the Senate." n26 Opponents charge that the administration was obligated to inform the full intelligence committees. n27 Opponents also argue that notification occurred under such constrained conditions that informed members had no means to seek recourse in response to the information. n28 [*1054] 1. Limiting Notice to the Gang of Eight The legal dimensions of notification are shaped largely by the National Security Act of 1947, as amended. The intelligence community's current statutory disclosure responsibilities include requirements that the President "ensure that the congressional intelligence committees are kept fully and currently informed of ... intelligence activities ... including any significant anticipated intelligence activity" n29 and that the Director of National Intelligence [DNI] and the intelligence agency heads similarly "keep the congressional intelligence committees fully and currently informed of all intelligence activities," including through written reports on "significant anticipated intelligence activity." n30 In carrying out these duties, the DNI must show "due regard for the protection from unauthorized disclosure of classified information relating to sensitive intelligence sources and methods or other exceptionally sensitive matters." n31 A separate statutory provision requires "Presidential approval and reporting of covert actions." n32 Covert actions are distinct from intelligence activities. The former is limited to "an activity or activities of the United States Government to influence political, economic, or military conditions abroad, where it is intended that the role of the United States Government will not be apparent or acknowledged publicly." n33 Covert actions do not include "activities the primary purpose of which is to acquire intelligence." n34 While the intelligence committees generally must be notified of covert actions, n35 initial notice may be limited to the Gang of Eight n36 where the President deems such limitation "essential ... to meet extraordinary circumstances affecting vital interests of the United States." n37 When initial notice is restricted to the Gang of Eight, "the President shall fully inform the congressional intelligence committees in a timely fashion and shall provide a statement of the reasons for not giving prior notice." n38 Page 219 AT: L/NB --- Military DA Only Congressional authorizations allowed tailored restrictions --- the Courts undermines executive flexibility Harvard Law Review 8 (“SHIFTING THE FISA PARADIGM: PROTECTING CIVIL LIBERTIES BY ELIMINATING EXANTE JUDICIAL APPROVAL”, 121 Harv. L. Rev. 2200, Lexis)//trepka A. Conceptualizing a System of Political Checks At present, there appears to be a problem of circularity in justifying FISA: those who fear allowing the courts to impact national security argue that they are not active enough to impact it anyway, while those who fear abrogation of civil liberties argue that ex ante judicial approval is needed. As one commentator notes, "the fear that a judicial review requirement would prevent the government from conducting surveillance seems overblown in light of the fact that the FISA court grants virtually all of the government's requests." n90 In effect, this [*2216] leaves the difficult decisions to the Executive but does not provide the political accountability necessary to permit the public to influence the way the Executive makes its choices. Moreover, a focus on "political judgments" would also maintain the flexibility the government needs to ensure the continued vitality of the nation that protects those liberties. The testimony during the initial FISA hearings of two former Attorneys General, themselves responsible for authorizing foreign intelligence surveillance in the pre-FISA arrangement, is instructive. Former Attorney General Ramsey Clark observed that "we greatly exaggerate the safety and value of" a requirement that "all wiretaps ... be approved by a judicial officer." Arguing that "the idea that there can be a meticulous review of these applications by the Judiciary is contrary to our experience," he put primary emphasis on political checks through reporting requirements and congressional oversight and standard-setting. n91 Additionally, former Attorney General Elliot Richardson noted the "important role in assuring that this sensitive tool is not abused" to be played by the Senate, via both direct oversight and the confirmation of the Attorney General and Director of the FBI. n92 More importantly, the legislative history suggests that the most consequential element of FISA is not its judicial review provisions. Rather, FISA's crucial move was to institute a reliance on the use of "public laws, publicly debated and adopted, which specify under what circumstances and under what restrictions electronic surveillance for foreign intelligence purposes can be conducted." n93 The reliance on political checks proposed in this Note avoids the problem identified by Congress when that "the substantial safeguards respecting foreign intelligence electronic surveillance [then] embodied in classified Attorney General procedures" [*2217] were not enough to overcome "the inappropriateness of relying solely on executive branch discretion to safeguard civil liberties." n94 Here, the Executive is subject not merely to internally created standards that it might change or ignore at will, but also to those set down by the statute , which were themselves created it initially enacted FISA and raised by the TSP - through the public "weighing of important public policy concerns" that Congress performs. n95 Congress is better situated constitutionally and better equipped institutionally to make the sort of value judgments and political determinations that are necessary to fulfill FISA's purposes. If "the government may abuse FISA in situations like that involving the L.A. Eight, when intrusive electronic surveillance is undertaken based on political activities, rather than on support for terrorist activities," n96 it seems that Congress will be much better than courts at sniffing out such violations and fashioning broader and more flexible remedie s. If one hopes to realize the core purpose of FISA - as described by the ACLU, "to prevent future presidents from intercepting the "international communications of American citizens whose privacy ought to be protected under [our] Constitution' ever again" n97 - then a approach is needed. new Page 220 AT: L/NB --- Terror DA Maintaining warrantless surveillance still maintains privacy --- implementing a new oversight mechanism would deter and prevent abuse without undermining counterterror Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka Judge Posner suggests a more radical approach. He would allow warrantless international and domestic surveillance of Americans without basis on any ex ante predicate standard or an attenuated standard, like a "reason to believe that the surveillance might yield clues to terrorist identities, plans, or connections." n269 Yet, Judge Posner notes that the more watered-down the predicate standard, the less meaningful role it plays in deterring abuse: "If all that the government is required to state in its application is that it thinks an interception might yield intelligence information, judges will have no basis for refusing to grant the application." n270 Instead, Judge Posner would rely more on ex post reporting mechanisms to control abuse. n271 He would also prevent law enforcement personnel from using information gleaned by warrantless surveillance for most non-national security related crimes . n272 For example, if an intelligence officer overheard a man discussing a murder (not related to terrorism), the officer would have to minimize and ignore such communication as it would not be related to national security. As review and Posner explains, "it is more important that the public tolerate extensive national security surveillance of communications, than that an occasional run-of-the-mill crime go unpunished because intelligence officers were not permitted to share evidence of such a crime with law enforcement authorities." n273 In other words, Posner's solution would rely on minimal, if any, ex ante review mechanisms and instead rely on extensive ex post reviews to deter and prevent governmental abuse of warrantless surveillance information. Under the Fourth Amendment, warrants require probable cause. n274 Some argue that the warrant requirement is unworkable in the national security context. For example, if the initial determination of an individual's status as a foreign power agent requires surveillance, then probable cause for such surveillance will rarely exist . And, although the Fourth Amendment does not require warrants in all cases, surveillance must at least be reasonable under the circumstances. n275 As attorney David Rivken notes: [*311] While the Executive can constitutionally carry out a "reasonable" search that infringes on personal privacy, a warrant cannot be granted by a court absent "probable cause." Applying the higher probable cause standard would mean that NSA could only surveil the conversations of full-fledged al Qaeda agents, leaving invaluable conversations among al Qaeda sympathizers unmonitored. n276 Therefore, similar to Posner's approach, Rivken recommends political accountability to deal with abuses but not necessarily ex ante reviews based on probable cause. He suggests that Congress cut off the funds for NSA surveillance as one way to control NSA abuses. n277 Programmatic surveillance is constitutional --- oversight solves abuse and prevents terror Blum 9 --- attorney for the Department of Homeland Security, M.A. in security studies, J.D. from UChicago (Stephanie, “ WHAT REALLY IS AT STAKE WITH THE FISA AMENDMENTS ACT OF 2008 AND IDEAS FOR FUTURE SURVEILLANCE REFORM”, 18 B.U. Pub. Int. L.J. 269, Lexis)//trepka Page 221 Similarly, in terms of the other hypothetical situations discussed in Section III, n279 the question could be rephrased as "whether probable cause that wiretapping all 1000 apartments would stop the attack, or whether wiretapping the phones in Georgetown would avert a nuclear disaster." Such an approach would, indeed, be lawful. According to Posner, the Supreme Court has suggested that a dragnet search of every car in an area to locate a bomb would not violate the Fourth Amendment , even though there would not be probable cause or even reasonable suspicion to suspect any individual car. n280 Posner believes that the Court would reason that the delay, inconvenience, and privacy intrusion to the drivers would be outweighed by the danger of a bomb. n281 The situation involving surveillance to stop a nuclear bomb is even more compelling. In sum, when evaluating the FAA and considering additional surveillance reform, Congress should consider creating a policy that allows officials to investigate mere contacts with terrorists without first requiring probable cause to believe that the contact is an agent of a foreign power. One possible reform could change when intelligence officials are required to use the probable cause standard. Another way, as suggested by Judge Posner, would be to relax the ex ante inquiry and allow widespread warrantless surveillance but rely more heavily on ex post mechanisms to deter and detect abuse . n282 B. Incidental Communications of U.S. Persons Under the FAA, the potential exists that vast numbers of incidental communications made by U.S. persons will be acquired, especially because the executive can conduct warrantless surveillance of foreign nationals overseas who may happen to communicate with a U.S. person. While the FAA requires minimization procedures, as explained in Part IV, there are plenty of exceptions. n283 One way to obviate the concerns of civil libertarians, who worry that information obtained through warrantless surveillance used to gather foreign intelligence could be used to prosecute domestic crimes, is to add statutory language limiting the crimes that could be prosecuted using evidence gathered under the FAA. In other words, officials could use information concerning terrorism for [*313] prosecution, but information concerning crimes unrelated to terrorism would not be given to law enforcement officials. Law professor Banks proposes a solution calling it an "exclusionary rule for FISA." n284 Under this proposal, the "government would be prevented from using FISA-obtained information as evidence in a prosecution of a target for a so-called collateral crime-one having nothing to do with terrorism or national security." n285 Such an exclusionary rule might mitigate potential abuse of the acquisitions of incidental U.S. communications pursuant to the FAA and would not undermine national security. A second potential problem with collecting vast amounts of data concerns efficacy. Jerry Berman and Lara Flint from the Center of Democracy and Technology argue that September 11 was not a result of lacking the right intelligence but rather a result of the government not making effective use of the information already in its possession, and failing to adequately share information among government agencies. n286 Berman and Flint argue, "granting the government broader authority to collect vastly greater volumes of information without particularized suspicion could exacerbate this problem." n287 Journalist James Bamford reaches a similar conclusion: "Those involved in the warrantless eavesdropping operation soon began to realize its limitations. By gaining speed and freedom, they sacrificed order and understanding." n288 Part of the challenge is recognizing when incidental When the purpose of surveillance is to gather intelligence about international terrorism, greater flexibility in acquiring and storing information is necessary, because innocent-sounding conversations may later prove to be highly significant, and because individual items of information, not apparently significant when taken in isolation, may become highly significant when considered together over time. n289 communications become foreign intelligence. As the court noted in United States v. Rahman: Page 222 AT: Not Competitive The federal government is divided into three branches. Rotunda 01 Richard Rotunda, professor of law at the University of Illinois, 2001; 18 Const. Commentary 319, “The Commerce Clause, the Political Question Doctrine, and Morrison,” L/N The Framers sought to protect liberty by creating a central government of enumerated powers. They divided power between the state and federal governments, and they further divided power within the federal government by splitting it among the three branches of government, and they further divided the legislative power (the power that the Framers most feared) by splitting it between two Houses of Congress. n12 Decks solvency Elmore 80 R.F. Elmore, professor of public affairs at University of Washington, 1980 [Political science quarterly, pg. 605, (m7,06)] Analysis of policy choices matters very little if the mechanism for implementing those choices is poorly understood. In answering the question, “What percentage of the work of achieving a desired governmental action is done when the preferred analytic alternative has been identified?” Allison estimated that in the normal case, it was about 10 percent, leaving the remaining 90 percent in the realm of implementation. Policy making education is found at the agency and implementation level Schuck 99 Peter H. Schuck, Professor, Yale Law School, and Visiting Professor, New York Law School, Spring (“Delegation and Democracy” – Cardozo Law Review) http://www.constitution.org/ad_state/schuck.htm God and the devil are in the details of policymaking, as they are in most other important things—and the details are to be found at the agency level. This would remain true, moreover, even if the nondelegation doctrine were revived and statutes were written with somewhat greater specificity, for many of the most significant impacts on members of the public would still be indeterminate until the agency grappled with and defined them. Finally, the agency is often the site in which public participation is most effective. This is not only because the details of the regulatory impacts are hammered out there. It is also because the agency is where the public can best educate the government about the true nature of the problem that Congress has tried to address. Only the interested parties, reacting to specific agency proposals for rules or other actions, possess (or have the incentives to ac-quire) the information necessary to identify, explicate, quantify, and evaluate the real-world consequences of these and alternative proposals. Even when Congress can identify the first-order effects of the laws that it enacts, these direct impacts seldom exhaust the laws’ policy consequences. Indeed, first-order effects of policies usually are less significant than the aggregate of more remote effects that ripple through a complex, interrelated, opaque society. When policies fail, it is usually not because the congressional purpose was misunderstood. More commonly, they fail because Congress did not fully appreciate how the details of policy implementation would confound its purpose. Often, however, this knowledge can only be gained through active public participation in the policymaking process at the agency level where these implementation issues are most clearly focused and the stakes in their correct resolution are highest. Which agency is the core question of domestic surveillance Cooper 7 --- Washington Times, senior fellow with the American Civil Rights Union (Horace, “Strike this down”, http://www.washingtontimes.com/news/2007/oct/23/strike-this-down/)//trepka In the wake of President Bush’s veto of the State Children’s Health Insurance Program (SCHIP), Congress is preparing for another showdown with the White House. But this time the dispute won’t be over health care spending for children, instead the dispute has consequences for all Americans because it is over which branch of government is best suited to know which ground rules are needed for fighting the war on terror. The specific conflict is over proposed amendments to the Page 223 Foreign Intelligence Surveillance Act (FISA) but the broader issue is the distinct differences between the Congress and the President when it comes to national security. Undoubtedly Article I of the Constitution provides a robust role for Congress in these matters: Congress has the authority “to declare War, grant letters of Marque and Reprisal, and make rules concerning Captures on Land and Water.” Furthermore Congress is given explicit power to fund and organize the military, legislate international rules of commerce and punish piracy. But crucially, its authority is dispersed among the two chambers and its powers are best read as setting policy on broad terms. On the other hand, Article II of the Constitution reveals the primacy of executive authority when it comes to the day to day handling of national security threats. Article II vests in the presidency the commander in chief power as well as foreign relations authority, executive order authority and related emergency powers. This combination makes the presidency ideally suited to assess and carry out our nation’s national security needs. The tension between policy setting and day to day implementation is reflected in the dispute over amendments to the FISA act of 1978. After nearly 20 years, Congress this summer passed amendments that modernized the act by expressly granting the president broad authority to use today’s cutting-edge technology to engage in international surveillance. But now some in Congress want to roll back that authority. That would be a dangerous mistake. The new rules work and provide the right balance between civil liberties and national security. Presently, the president is authorized to surveil foreigners without going to the Foreign Intelligence Surveillance Court (FISC) for permission. Additionally, to protect Americans, the law requires the DOJ to develop and submit to the FISA court a set of procedures the president will use in making determinations of who is a foreigner. Furthermore, the law authorizes the director of national Intelligence and the attorney general to require private companies to assist in surveillance of foreign intelligence targets. And finally, the amendments provide those firms a broad grant of immunity from lawsuits as a result of their assistance. Unfortunately these changes were temporary, as the act expires in February 2008. Worse yet, however is a “replacement” measure being pushed by Rep. John Conyers — the inaptly named “Restore Act of 2007.” This bill, which is rapidly making its way through Congress, represents an aggressive and unhelpful assertion of congressional authority. It will cripple our nation’s ability to engage in international electronic intelligence gathering and is a powerful argument for why the framers believed the executive must take the lead in matters of national security. Instead of maintaining the distinction between foreign and domestic intelligence , the so-called Restore Act would force both foreign and domestic surveillance to be reviewed by the Foreign Intelligence Surveillance Court. Not only would this process needlessly delay and in many instances eliminate altogether the gathering of vital intelligence, it rests on dubious constitutional grounds as it encroaches on the president’s independent authority to engage in international surveillance of foreigners without coordination with Congress or courts. Perhaps most egregiously, this measure would for the first time cover the American military thereby disrupting their access to actionable intelligence even when needed in a battlefield setting. Congress vs the Supreme Court is critical in determining questions of decreasing domestic surveillance NCC 13 --- National Constitution Center Staff (“Podcast: Kerr, Rotenberg on NSA domestic surveillance”, http://blog.constitutioncenter.org/2013/10/audio-kerr-rotenberg-on-warrantless-surveillance/)//trepka How should Congress and the Supreme Court settle questions about warrantless surveillance by the NSA? Does the secret court that rules on NSA cases need reforms? Orin Kerr of George Washington University and Marc Rotenberg of the Electronic Privacy Information Center joined the National Constitution Center’s Jeffrey Rosen on Wednesday to discuss these and other critical privacy issues in an audio interview. Under Section 215 of the Patriot Act and measures extending the act, the National Security Agency is allowed to collect bulk communications records without a warrant. The NSA gets permission from the secret Foreign Intelligence Surveillance Act court to take such actions, in the form of blanket requests that are renewed periodically. Rotenberg’s organization, EPIC, is challenging the legality of the bulk collection of telephone warrant . Kerr also believes there are problems with Section 215, but the issues should be dealt with by Congress or the FISA court—and not the U.S. Supreme Court. records under Section 215 without the issuance of a Page 224 Other CPs Page 225 Uniqueness CP for Warrants Bad Courts should remove the warrant requirement for domestic intelligence gathering Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Conclusion Purely domestic intelligence searches present the confluence of two important factors: the government's heightened need for information to protect its citizens from terrorist attacks, and the Supreme Court's reliance on warrants as an integral part of Fourth Amendment doctrine. The two factors conflict : a warrant requirement hampers the ability of the government to gather the intelligence it needs to protect its citizens. The Supreme Court, however, could easily alleviate the burden placed on legitimate intelligence gathering by casting aside the warrant requirement and its attendant probable cause standard when it stands in the way of gathering information needed to protect against future terrorist attacks or other threats to national security. Warrants are impotent in deterring or preventing constitutional violations in the intelligence-gathering context while imposing considerable costs on the government. Bowing to both common sense and the President's constitutional authority, the courts have recognized such an exception in connection with foreign intelligence. Given the threat posed by domestic terrorists and the pliant nature of reasonableness under the Fourth Amendment, the Court should extend an exception to the warrant requirement for domestic intelligence gathering in light of the government's heightened need for counterterrorism intelligence. Page 226 Grounds CP --- FISA Courts can rule on SOP doctrine, first, or fourth amendment Plummer 6 --- J.D., Mississippi College School of Law, law clerk for Barnes of the Mississippi Court of Appeals (Brooke, “Domestic Spying: A Necessity in a Post-9/11 America or an Abuse of Presidential Power?”, Mississippi College Law Review, Lexis)//trepka In response to the Government's contention that Hamdi supports the notion that the AUMF constitutes congressional authorization of the NSA program, the court took special note of the Hamdi Court's ruling that, although a citizen of the United States may be detained as an enemy combatant, "such a citizen must be given Fifth Amendment rights to contest his classification, including notice and the opportunity to be heard by a neutral magistrate." n64 Interpreting this language as a mandate that the Constitution be followed regardless of any activity authorized by the AUMF, the court concluded that, even if the AUMF supercedes FISA, the NSA program still violates the Separation of Powers doctrine and the First and Fourth Amendments to the Constitution. n65 Finally, with regard to the Government's reliance on the President's inherent authority, the court found that, because the office of the President of the United States was created by the Constitution, "all 'inherent powers' must derive from that Constitution;" thus, relying again on Hamdi, the court found [*312] that the actions of the Executive branch are subject to the First and Fourth Amendments and that, even in times of war, the President is not free to disregard the explicit requisites of the Constitution. n66 In light of these findings, the court permanently enjoined the NSA domestic spying program; n67 however, the Sixth Circuit Court of Appeals subsequently stayed the injunctions pending appeal, finding that the Government had demonstrated "a substantial likelihood of success on the merits." n68 Page 227 Grounds CP --- Health Surveillance Rule on 4th Amendment Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka TEXT: [*1951] Introduction Lawmakers, academics, and the American public have expressed increasing concern about three features of government surveillance: comprehensive and intimate surveillance of individuals, the creation of large databases to which sophisticated data mining techniques can be applied, and the targeting of politically vulnerable domestic communities. To date, concern about government surveillance and data collection has focused primarily on security surveillance. n1 Comparable recent developments in government public health surveillance have received little attention in contrast. n2 The history of public health surveillance and interventions has been extensively studied, n3 but most chapters of that history focus on communicable diseases. n4 The model of public health surveillance that [*1952] was developed to fight communicable disease has two components: conducting nonconsensual, intimate surveillance of persons with a particular disease or health condition and maintaining databases of individually-identified information. n5 Historically, this enabled government interventions that prevented the spread of contagious disease. n6 This model was traditionally justified both by the nature of the risk created by communicable diseases and by the efficacy of government interventions to mitigate that risk. n7 Today, non-communicable chronic diseases and obesity present the most serious threats to public health and health care costs, n8 and public health surveillance programs have accordingly begun to target them. n9 Notably, government agencies have begun to target non-communicable, chronic diseases through what I call the "emergent" model of public health surveillance. In the emergent model, the government (i) conducts nonconsensual, ongoing, and intimate surveillance of a large number of people because they have a non-communicable health condtion and (ii) maintains individually-identified databases of the information gathered. The problem is that emergent government surveillance programs invade a very intimate sphere of personal privacy, despite the fact that the original justifications for doing so do not apply to non- [*1953] communicable, non-exposure related conditions. Moreover, proponents of emergent programs have not articulated a satisfactory alternative justification for significantly invading the privacy of people with non-communicable health conditions. This Note has three parts. In Part I, I briefly summarize the salient features of public health surveillance programs in the United States. Against that baseline, I describe New York City's A1C Registry as the paradigm of emergent public health surveillance and explain why emergent programs are likely to proliferate. In Part II, I argue that emergent intrude upon a privacy interest forms of public health surveillance that courts should recognize as fundamental for purposes of the Fourteenth Amendment's Due Process Clause. The argument proceeds in two parts. First, despite a widespread assumption to the contrary, judicial precedent does not require highly deferential review of emergent programs. Although federal courts reviewing privacy-based challenges to public health programs have historically applied deferential standards of review, n10 those programs differ in essential respects from emergent public health surveillance. Furthermore, several opinions suggest that a more stringent standard of review would apply if the scope of surveillance increased, as I argue that it has. Second, comparable features of security surveillance programs have raised considerable public concern and have prompted some courts to expand the scope of privacy protections under the Fourth Amendment . Given the dearth of commentary on emergent public health surveillance programs, recent Fourth Amendment jurisprudence and critical commentary developed in the context of security surveillance provide useful guideposts . In particular, these paradigms help to delineate the privacy interest at stake in emergent public health surveillance programs. Part II concludes by explaining that, because they infringe upon a fundamental interest, emergent programs should receive strict scrutiny. In Part III, I propose several factors to include in the constitutional analysis of emergent public health surveillance programs. Most important, the narrow tailoring requirement that would apply under a strict scrutiny analysis should examine the likelihood that the public health interventions enabled by the challenged surveillance program are effective. In the context of non-contagious diseases, efficacy should mean improvement or risk reduction in the health of the population targeted for surveillance. Applying the proposed analysis to [*1954] New York's A1C Registry, I conclude that the program may be unconstitutional. Page 228 K Stuff Page 229 Legalism Bad Legal reforms can’t prevent the ever-expanding surveillance state Lynch 7 --- J.D. (Matthew, “CLOSING THE ORWELLIAN LOOPHOLE: THE PRESENT CONSTITUTIONALITY OF BIG BROTHER AND THE POTENTIAL FOR A FIRST AMENDMENT CURE”, 5 First Amend. L. Rev. 234, Lexis)//trepka This Article explores two questions. First, it asks whether the United States Supreme Court's current interpretation of the Constitution protects us from Big Brother; that is, could a system of government surveillance on an Orwellian scale - instigated by another major terrorist attack in the United States - survive judicial scrutiny under current Supreme Court precedent? To answer this question, the Article evaluates potential challenges to Big Brother under the Fourth , Fifth , and First Amendments. Disturbingly, it finds that all leave open the possibility of constitutionality . In other words, under the right conditions and under current precedent, no constitutional provision stands firmly between American citizens and Big Brother. Page 230 Terror Talk Bad --- Privacy Their narrative of terrorists turns the privacy advantage Lynch 7 --- J.D. (Matthew, “CLOSING THE ORWELLIAN LOOPHOLE: THE PRESENT CONSTITUTIONALITY OF BIG BROTHER AND THE POTENTIAL FOR A FIRST AMENDMENT CURE”, 5 First Amend. L. Rev. 234, Lexis)//trepka The setting of George Orwell's 1984 is nothing short of a nightmare , a dystopian vision of a totalitarian world where democratic values exist in name only, and the near-total absence of privacy bends people's behavior, their conversations, and even their minds toward the government's will. From an American perspective, Orwell's fictional characters live under a sort of anti-Constitution. The Framers obviously did not have the benefit of his cautionary tale when they wrote the Constitution and its Bill of Rights, but their words and explanatory documents reflect the same fears. American courts have never weighed the constitutionality of Big Brother because the government has never implemented such a surveillance program, at least not on the scale that Orwell imagined. Voters have never seriously demanded it, and the government has never before possessed the technological means to make it a reality. Now that such means are at the government's disposal, Big Brother has never been closer to realization. From GPS-tracking and satellite-communications intercepts to facial-recognition cameras and data-mining software, the government has the means to eavesdrop on virtually any facet of human life. The persistence and growth of clandestine crimes and societal threats - from mere software pirating to terrorism and drug trafficking - creates pressure and temptation for government to use this ever-improving technology more broadly . The latent nature of such crimes, combined with their high publicity, creates such public paranoia that citizens are often willing to trade liberty for an increased sense of security. Page 231 Aff Stuff Page 232 AT: Disease DA Disease surveillance fails --- structural issues Phalkey et al 13 --- Institute of Public Health, University of Heidelberg (Revati, also with Shelby Yamamoto and Michael Marx from the same institution, and Pradip Awate from the Integrated Disease Surveillance Project in Maharashta, “Challenges with the implementation of an Integrated Disease Surveillance and Response (IDSR) system: systematic review of the lessons learned”, http://heapol.oxfordjournals.org/content/early/2013/12/20/heapol.czt097.full)//trepka Introduction: Despite a realistic strategy and availability of resources, multiple challenges still overwhelm countries grappling with the challenges of communicable disease surveillance . The Integrated Disease Surveillance and Response (IDSR) strategy is by far the most pragmatic strategy in resource-poor settings. The objective of this study was to systematically review and document the lessons learned and the challenges identified with the implementation of the IDSR in low- and middle-income countries and to identify the main barriers that contribute to its sub-optimal functioning. Methods: A systematic review of literature published in English using Web of Knowledge, PubMed, and databases of the World Health Organization (WHO) and the Centers for Disease Control (CDC) between 1998 and 2012 was undertaken. Additionally, manual reference and grey literature searches were conducted. Citations describing core and support functions or the quality attributes of the IDSR as described by WHO and CDC were included in the review. Results: Thirty-three assessment studies met the inclusion criteria. IDSR strategy has been best adopted and implemented in the WHO–AFRO region. Although significant progress is made in overcoming gaps still exist . Mixed challenges with core and support IDSR functions were observed across countries. Main issues identified include non-sustainable financial resources , lack of co-ordination, inadequate training and turnover of peripheral staff, erratic feedback , inadequate supervision from the next level, weak laboratory capacities coupled with unavailability of job aids (case definitions/reporting formats), and poor availability of communication and transport systems the challenges identified with vertical disease surveillance strategies, particularly at the periphery. Best outcomes in core functions and system attributes were reported when support surveillance functions performed optimally. Apart from technical and technological issues, human resources and the health care system structures that receive the IDSR determine its output. Conclusions: The challenges identified with IDSR implementation are largely ‘systemic’. IDSR will best benefit from skill-based training of personnel and strengthening of the support surveillance functions alongside health care infrastructures at the district level. Page 233 AT: Federalism DA Gay marriage thumps AP 6/26/15 (“Neb. Lawmakers React to Gay Marriage Ruling”, http://www.knopnews2.com/home/headlines/Neb-LawmakersReact-to-Gay-Marriage-Ruling--310077891.html)//trepka Today five Supreme Court Justices created a new constitutional right based upon sexual choices. The Constitution doesn’t speak , one way or the other, to the question of same-sex marriage. Under our system of federalism , the definition of marriage as a male-female union is properly a matter of state law. I agree with Chief Justice Robert’s contention that “The majority’s decision is an act of will, not legal judgment. The right it announces has no basis in the Constitution or this Court’s precedent.” The Court overstepped its proper role in our system of government. Instead of interpreting and applying the law, the Court invented a new constitutional right . Nothing in the Constitution mandates a nationwide redefinition of marriage. Sadly, the Court stripped all Americans of our freedom to debate and decide marriage policy through the democratic process. The freedom to democratically address the most pressing social issues of the day is the heart of liberty. The Court took that freedom from the people. Triggers precedent links Hunter 7/2/15 --- Politico (Jack, “Republicans are too angry about gay marriage”, http://www.politico.com/magazine/story/2015/07/republicans-gay-marriage-angry-119711.html)//trepka Rand Paul’s libertarian reaction also charted a more tolerant conservative course. But were Bush, Rubio and Paul’s reactions good enough to drown out the others? What do most Americans—who overwhelming support gay marriage—think today about the Republicans’ collective response to this court decision? As a libertarian conservative, I too had concerns about what this court decision could mean for federalism and what kind of precedent it set. Roberts’ constitutional concerns also give me pause. Still, I was pleased with the outcome. I wrote on my Facebook page, “All politics aside, I’m very happy for gay Americans and my country today.” Triggers their 14th amendment links Shapiro 6/27/15 --- senior fellow in constitutional studies and editor-in-chief of the Cato Supreme Court Review at The Cato Institute (Ilya, “Gay Marriage Is Here. Now What?”, http://thefederalist.com/2015/06/27/gay-marriage-ishere-now-what/)//trepka Just because today’s opinion was expected by nearly everyone doesn’t make it any less momentous. In sometimes-soaring rhetoric Kennedy explains that the Fourteenth Amendment’s guarantee of both substantive liberty and equality means there is no further valid reason to deny this particular institution, the benefit of these particular laws, to gay and lesbian couples. Okay, fair enough: there’s a constitutional right for gay and lesbian couples to get marriage licenses—at least so long as everyone else gets them. (We’ll set aside the question of why the government is involved in marriage in the first place for a later time.) Page 234 AT: Warrants Bad DA Warrants are required for domestic intelligence now --- takes out their disad Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka Despite the unanimity of judicial opinion that a warrant is not required for foreign intelligence searches, n56 the Supreme Court has not extended the warrant exception to the domestic intelligence arena . Instead, its 1972 decision in the Keith case remains the controlling authority governing domestic intelligence searches. n57 In Keith, the Attorney General authorized warrantless electronic surveillance of three individuals who the government believed were involved in a conspiracy to blow up government property and who were ultimately indicted for such activity. n58 The defendants moved to suppress the evidence obtained through this warrantless surveillance, and the district court granted their motion. n59 Before the Supreme Court, the government argued that the wiretaps were required "to gather intelligence information deemed necessary to protect the nation from attempts of domestic organizations to attack and subvert the existing structure of the Government," n60 [*354] and that because of this, the surveillance was a "reasonable exercise of the President's power ... to protect the national security." n61 The Court held that the searches at issue were unconstitutional because they were conducted without a warrant. n62 The Court reasoned that the ultimate issue was "the "reasonableness' of the search ... in question, and the way in which that "reasonableness' derives content and meaning through reference to the warrant clause." n63 With this warrant presumption as the backdrop, the Court turned to the President's constitutional authority. Justice Powell, writing for the Court, found that "implicit in [the President's duty to preserve, protect and defend the Constitution of the United States] is the power to protect our Government against those who would subvert or overthrow it by unlawful means," n64 and that electronic surveillance could be a vital tool in such an endeavor. n65 Powell also noted that numerous Presidents since Harry Truman had sanctioned similar surveillance. n66 Although acknowledging the seriousness of domestic threats and the need of the government to have the means necessary to combat them, Powell observed that there is, "understandably, a deep-seated uneasiness and apprehension that this capability will be used to intrude upon cherished privacy of law-abiding citizens." n67 Powell also pointed out that national security surveillance can implicate freedom of expression protected by the First Amendment and may thus require greater scrutiny under the Fourth Amendment n68: "History abundantly documents the tendency of Government - however benevolent and benign its motives - to view with suspicion those who most fervently dispute its policies." n69 With these competing interests in mind, Powell concluded that the issues were "whether the needs of citizens for privacy and free expression may not be better protected by requiring a warrant before such surveillance is undertaken" n70 and "whether a warrant requirement would unduly frustrate the efforts of Government to protect itself from acts of subversion and overthrow directed against it." n71 The Court bluntly found that the Fourth Amendment interests could not be adequately protected without warrants because the Executive may improperly give greater weight to its need to [*355] gather incriminating information than to the privacy interests of citizens. n72 The " inherent vagueness of the domestic security concept," n73 the breadth of the reach of intelligence gathering, and its potential to stifle political dissent , Powell explained, all counseled against an exception to the warrant requirement for domestic intelligence gathering. n74 Page 235 AT: Mosaic DA --- No I/L Courts defer to other agencies regarding mosaic theory Davis and Albert, 11 (Charles and Michelle, Professor of Journalism at University of Missouri, April 2011, Vol. 25, No. 2, Continuum: Journal of Media & Cultural Studies, “Using secrecy to fight terrorism? Access, homeland security, and the ‘mosaic theory’ as a rationale for closure”, EbscoHost, amp) The court ruled in favour of US Customs, and when Coastal filed a narrowed FOIA request later, US Customs claimed there were no documents that fit the parameters of the narrowed request, and the motion was denied. In the written opinion, the court cites its hesitancy to disclose the requested information because ‘the information requested, in combination with other information, could reasonably be used to circumvent the law’ (Coastal Delivery Corp. 2003). This is a fine example of the ‘mosaic theory’ at work: the ‘other information’ referred to by the court is not specified; neither is how the law could possibly be circumvented by the combination of information. The records of package examinations at a Long Beach seaport, combined with unknown bits of information, could put the seaport and perhaps other ports in jeopardy. In this case, given the vague, suggestive wording of the court’s opinion, the claim seems far-fetched. But the mosaic theory is not something the courts usually question. Indeed, the entire concept of the mosaic theory evades any easy judicial classification, as it relies on secrecy to justify greater secrecy, and rejects by its very imposition attempts at specificity (Wells 2006). Mosaic theory received judicial deference from its first appearance in US court law. In the decision for US v. Marchetti (1972), the mosaic theory was used to prevent a CIA agent from publishing a tellall book. Chief Judge Clement Hayworth cited that in terms of mosaic theory, judges should defer to agency expertise and avoid review completely. This created a precedent for mosaic theory in court. Post-9/11, FOIA law was deemed a liability to national security, as it could release information that could be combined with other information with dangerous results. In 2003, President Bush issued executive order 13292, which rescinded President Clinton’s limitation to President Reagan’s 1982 executive order, which wrote mosaic theory into law. Bush’s order reintroduced presumption of harm to national security from the release of information related to foreign governments and permitted the reclassification of previously declassified information in the name of national security (Pozen 2005). Precedent cements judicial deference Pozen, 5 (David, JD Yale Law School, M. Sc. Oxford University, 2007, Yale Law Journal, “The Mosaic Theory, National Security, and the Freedom of Information Act”, http://www.yalelawjournal.org/pdf/358_fto38tb4.pdf, amp) Taken together, then, Marchetti, Halkin, and Halperin, in introducing the mosaic theory to use it to bolster judicial deference on two levels: They present the theory as a general reason for courts to fear disclosure and mistrust their own judgment; and they treat mosaic arguments as a unique rationale for nondisclosure, with lower requirements for specificity and support. The opinions’ bracing rhetoric, moreover, tints the theory with an element of mystery and malice. This logic and language continue to undergird mosaic theory jurisprudence, as essentially every subsequent opinion applying the theory has cited Marchetti, Halkin, national security law, and/or Halperin as key precedent, often excerpting the passages quoted above. Page 236 AT: Mosaic DA --- Privacy Turn Triggering judicial resolution of mosaic theory is key to privacy Gray and Citron, 13 (David--Associate Professor, University of Maryland Francis King Carey School of Law, Danielle Keats--Lois K. Macht Research Professor of Law, University of Maryland Francis King Carey School of Law, Affiliate Scholar, Stanford Center on Internet and Society, Affiliate Fellow, Yale Information Society Project, North Carolina Journal of Law & Technology, Spring 2013, 14 N.C. J.L. & Tech. 381, “ARTICLE: A Shattered Looking Glass: The Pitfalls and Potential of the Mosaic Theory of Fourth Amendment Privacy”, lexis, amp) This Article has attempted to advance debates after United States v. Jones about the conceptual, doctrinal, and practical issues that attend the mosaic theory of Fourth Amendment privacy. The discussion has not produced a clear conclusion. Rather, the goal has been to elaborate the major objections raised against the mosaic theory to provide guidance for mosaic advocates. Although it is beyond the scope of the present the core insights that drive the theory warrant that further development. 253 At its core, the mosaic theory documents perfectly reasonable expectations that we will not be forced to live in a surveillance state or to abide constant, indiscriminate surveillance conducted by the Government or its private proxies. 254 That this expectation has firm footing in the Fourth Amendment we take to be a proposition that is constitutionally unproblematic. 255 The devil may well be in the details, but to the extent the mosaic theory is understood as a way to conceptualize these privacy interests and corollary privacy harms, the game is well worth the candle . Article to advance a mosaic-based proposal, Page 237 AT: Mosaic DA --- AT: Law/Terror Judicial mosaic theory rulings carve out a balanced role for mosaic making that preserves law enforcement—public solves terrorism info gathering Pozen, 7 (David, JD Yale Law School, M. Sc. Oxford University, 2007, Yale Law Journal, “The Mosaic Theory, National Security, and the Freedom of Information Act”, http://www.yalelawjournal.org/pdf/358_fto38tb4.pdf, amp) Courts should, moreover, consider the flip side of the mosaic theory: Just as the NSA connects the dots for counterterrorism, the public too can mosaic-make, and thereby respond more intelligently to threats. Likewise, courts should consider not only how information technologies might facilitate adversarial mosaic-making, but also how they might combat such activity. Finally, judges would benefit from a new tool, special masters with intelligence backgrounds, when faced with particularly speculative mosaic arguments. The mosaic theory deserves a central place in information-control policy, but a carefully Conscientious judges can restore reason and moderation to the theory's use. No one else will . circumscribed place; there are serious costs to overusing as well as underusing it. Page 238 AT: Ex Post CP Can’t solve racism Fenske 8 --- J.D. Candidate (Dan, “ALL ENEMIES, FOREIGN AND DOMESTIC: ERASING THE DISTINCTION BETWEEN FOREIGN AND DOMESTIC INTELLIGENCE GATHERING UNDER THE FOURTH AMENDMENT”, 102 Nw. U.L. Rev. 343, Lexis)//trepka In short, although preventing invidious racial discrimination is a legitimate concern in the intelligence-gathering domain, warrants do little to solve the problem while imposing real costs. To be sure, ex post review by courts and political responses have frequently proven insufficient to protect minorities from discrimination . Undoubtedly more than just lawsuits or political pressure is needed to combat racism in intelligence gathering. What is important for the purposes of this Comment, however, is merely that warrants offer few marginal benefits compared to after-the-fact judicial review. Page 239 AT: Funneling CP Funneling fails --- it’s not credible and no one can act based on the information Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka This Article agrees that funneling is a theoretically and practically important means of reconciling secrecy and openness needs but contends that funneling has not, in fact, been taken seriously enough. The purpose and utility of funneling have been underexplored, and funneling's propriety and implications thus are poorly understood. Questions remain, for example, over whether funneling requirements infringe on the separation of powers and thus need not always be obeyed. n7 And it is uncertain what if anything should follow from information funneling - whether, for example, those with whom information is shared should be able to take some action in response to what they learn. n8 Disclosure undermines democratic deliberation --- that devastates rule of law Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka b. Democratic Deliberation and Related Values The other major value invoked in debates about national security disclosures can be called democratic deliberation. This value encompasses at least three different types of deliberations: intra-executive branch deliberations, deliberations between Congress and the executive branch, and deliberations that include the public. Unlike national security, democratic deliberation is not necessarily an end in itself. On the one hand, one can draw upon political and constitutional theory for the view that public knowledge, dialogic participation and input through voting has intrinsic value. n106 Similarly, interbranch dialogue - and to a lesser extent intra-branch dialogue - can contribute to intrinsically valuable public knowledge and participation by generating and spreading information and dialogue that might make its way to the public. Furthermore, to the extent that ours is not a direct democracy but a system in which voters are represented by deliberating government branches, deliberations within and among these branches may have intrinsic value. On the other hand, democratic deliberation of all three kinds can be instrumental means of reaching other values, including national security, by increasing the intellectual input that goes into decisionmaking. Democratic deliberation also can contribute to the rule of law by spreading knowledge of illegalities that might then be challenged politically or in courts. i. Arguments Against Disclosures A common deliberation-based argument against less likely to be candid, robust and productive when participants know that their statements may be shared disclosures is the candor argument discussed earlier. n107 That is, disclosures and related discussions are with others. This [*1069] argument can take both instrumental and intrinsic forms that parallel those made about democratic deliberation generally. Instrumentally, the argument is that decision-making quality will be compromised by stunted deliberations . This can negatively impact national security or other ends toward which the decision-making is directed. One also might find intrinsic value, in an indirect democracy, in robust, candid exchanges within government branches. Rule of law is an impact filter --- solves the escalation of nuclear war Rhyne ’58 [(Former President of the American Bar Assosciation). “Law Day Speech for Voice of America; Text of the original radio broadcast by Charles S. Rhyne Delivered on the first Law Day, May 1, 1958” http://www.abanet.org/publiced/lawday/rhyne58.html //wyo-jamie] rule of law has enabled [hu]mankind to live together peacefully within nations and it is clear that this same rule of law offers our best hope as a mechanism to achieve and maintain peace between nations. The lawyer is the technician in man’s relationship to man. There exists a worldwide challenge to our profession to develop law to replace weapons before the dreadful holocaust of nuclear war overtake our people. History teaches that the Page 240 AT: Legislation CP Congressional restraints do nothing in the face of broader NSA surveillance CFDP 13 --- Center for Foreign and Defense Policy (“International Anger Grows Over NSA Spying”, http://www.foreignpolicy.us/international-anger-grows-over-nsa-spying/)//trepka WASHINGTON, October 26, 2013 — The National Security Administration exists to gather information. It does this mostly by electronic means. This does not mean it has any justification for hacking Angela Merkel’s cell phone or looking through the bank data of European citizens. Documents released by Edward Snowden show an NSA acting without restraint . It goes far beyond anything that should have been authorized and seems to include extensive monitoring of millions of phone calls and emails every month in friendly countries. Almost every day another story breaks about outrage in other countries over the extent of the NSA’s intrusion into the communications privacy of their citizens, businesses and political leaders. The level of outrage generated by these practices is still growing, but has already resulted in formal complaints from key American allies like Germany, France, Mexico and Brazil. The European Parliament has held a hearing on NSA spying and has threatened to withdraw support for the Terrorist Finance Tracking Program if it was a factor in NSA intrusion into European bank records. While wiretaps and data surveillance of United States citizens are theoretically limited by FISA, it places no restrictions on U.S. intelligence gathering operations overseas . We have already seen the NSA ignore these restrictions within our own borders, and with even fewer limits on their operations in Europe , it has apparently been unrestrained even by common sense in its intelligence gathering. Common sense suggests that the NSA at least respect the privacy rights guaranteed to citizens of allied countries as they would those of U.S. citizens. The rights described in the Bill of Rights are not exclusive to American citizens. They are just a codification of universal rights which are recognized by the United Nations, the European Union, and most civilized countries. Foreign citizens who are outraged about the NSA’s snooping in their communications are justifiably angry, and more so in the case of their political leaders whose communications are sensitive and should be granted appropriate respect. The German chancellor, members of the European Parliament and the President of France are not terrorist or criminal suspects, yet their communications have been monitored just like those of more common citizens of their countries. The NSA has apparently hacked former Mexican President Felipe Calderon’s email, as well as emails of other elected officials in that country. Mexico is lodging a formal protest with the United States government. France’s interior minister, Manuel Vallas, described the revelations as “shocking” and said that “such practices, if proven, do not have their place between allies and partners.” Chancellor Angela Merkel of Germany said that “Spying among friends is never acceptable.” She called President Obama personally after hearing that her cell phone may have been targeted and hacked by the NSA. French Prime Minister Jean-Marc Ayrault asked for the issue to be added to the agenda of the meeting of the European Commission. EC Vice President Vivianne Reding expressed the opinion that “Data protection must apply to everyone — whether we are talking about citizens’ e-mails or Angela Merkel’s mobile phone.” She is pushing for the adoption of Europe-wide legislation to protect the rights of all citizens from unwarranted surveillance by any government. Dutch Prime Minister Mark Rutte characterized the NSA surveillance of European citizens as “not acceptable.” Finnish Prime Minister Jyrki Katainen asked the United States to provide “a guarantee that this will never happen again.” Brazil’s Foreign Minister Antonio Patriota expressed “deep concern at the report that electronic and telephone communications of Brazilian citizens are being the object of espionage by organs of American intelligence,” and said that Brazil would seek U.N. intervention to protect the privacy rights of citizens. Brazilian President Dilma Rousseff cancelled an official visit to Washington because of the scandal. Some anger has also been directed at countries like Sweden and Great Britain, which have cooperated with the NSA or provided locations for their communications monitoring facilities. The NSA was established in an earlier era when mass communication was much more primitive and limited. When it invaded someone’s privacy, it was almost always with a clear objective and usually with specific accountability and oversight. As technology has become more advanced and more integrated, the NSA’s ability to acquire information has grown beyond anything that could have been imagined a generation ago, and the agency seems to have developed the ethos that if something can be done, then they should do it. We have a Constitution and laws because sometimes people don’t know where to draw sensible limits on their actions. The prohibitions in the Bill of Rights are broad and inclusive. They ought to be enough, but sometimes when new crimes or abuses of power are invented, we need new laws to apply the general ideas of the Bill of Rights to a specific situation. If there were ever a time to write a specific law protecting privacy rights from government intrusion, this is it. This administration and Congress have paid little attention to the protests of citizens within the United States. A huge rally is scheduled for Saturday on the national mall, organized by over 100 public interest groups to draw attention to this issue. Yet the only member of Congress speaking is Republican Representative Justin Amash, who has become well known as a champion of privacy rights. Where is Judiciary Committee Chairman Bob Goodlatte, whose hearings on the NSA this summer seem to have been designed to brush this issue under the rug? Alienating friendly nations around the world because we have violated the rights of their citizens and their leaders and threatened their own national security could rapidly become a serious problem. Maybe if our government will not listen to the complaints of our own citizens, it will respond to pressure from our unhappy friends and allies overseas. No one likes what the NSA has become. It has exceeded its mandate . It has violated the Bill of Rights. It has violated international law. Only Supreme Court rulings solves surveillance --- otherwise constitutional justifications will allow circumvention AP 2014 (Kimberly Dozier, “US spy court: NSA to keep collecting phone records”, http://phys.org/news/2014-01-spy-court-nsa.html)//trepka secretive U.S. spy court has ruled again that the National Security Agency can keep collecting every American's telephone records every day, in the midst of dueling decisions in two other federal courts about whether the (AP)—A surveillance program is constitutional. The Foreign Intelligence Surveillance Court on Friday renewed the NSA phone collection program, said Shawn Turner, a spokesman for the Office of the Director of National Intelligence. Such periodic requests are somewhat formulaic but required since the program started in 2006. The latest approval was the first since two conflicting court decisions about whether the program is lawful and since a presidential advisory panel recommended that the NSA no longer be allowed to collect and store the phone records and search them without obtaining separate court approval for each search. In a statement, Turner said that 15 judges on the U.S. Foreign Intelligence Surveillance Court on 36 occasions over the past seven years have approved the NSA's collection of U.S. phone records as lawful. Also Friday, government lawyers turned to U.S. Court of Appeals for the District that threatens the NSA phone records program. The opposing lawyer who spearheaded the effort that led to the ruling said he hopes to take the issue directly to the of Columbia Circuit to block one federal judge's decision Supreme Court . The Justice Department filed a one-page notice of appeal asking the appeals court to overturn U.S. District Judge Richard Leon's ruling last month that the program was likely unconstitutional. The government's move had been expected. Larry Klayman, who filed the class-action suit against President Barack Obama and top administration national security officials, said he intends to petition the federal appeals court next week to send the case directly to the Supreme Court. Klayman said the move was justified because the NSA case was a matter of great public importance. "There are exigent circumstances here," Klayman said. "We can't allow this situation to continue. The NSA's continuing to spy on everybody." Turner said U.S. intelligence agencies would Page 241 be willing to modify the phone records surveillance program to provide additional privacy and civil liberties protections as long as it was still operationally beneficial. He said the Obama administration was carefully evaluating the advisory panel's recent recommendations. Judges sitting on the secretive spy court have repeatedly approved the program for 90-day periods. They also have repeatedly upheld the constitutionality of the program—a judicial bulwark that held strong until Leon's surprise decision last month. Leon said the NSA's program was "almost Orwellian ," a reference to writer George Orwell's futuristic novel "1984," and that there was little evidence the operation had prevented terrorist attacks. He ruled against the government but agreed to postpone shutting down the program until the government could appeal. In a separate case involving the same NSA phone records program, a district judge in New York last month upheld the government's data collection as lawful. The American Civil Liberties Union, which lost that case, said this week it will appeal to a federal appeals court in New York. The NSA empirically ignores Congressional legislation to end surveillance ZenMate 7/11/15 (“Secret Court Ignores Congress”, https://blog.zenmate.com/secret-court-ignores-congress/)//trepka On June 29, a secret court ruled that a federal court and Congress were wrong to end the NSA's bulk collection of phone metadata; therefore, the mass surveillance can carry on as before — for now. National Journal reports: "The Foreign Intelligence Surveillance Court [FISC] approved a government request to renew the dragnet collection of U.S. phone metadata for an additional five months. In his opinion, FISC judge Michael W. Mosman ruled, “Second Circuit rulings are not binding on the F.I.S.C. and this court respectfully disagrees with that court’s analysis, especially in view of the intervening enactment of the U.S.A. Freedom Act.” That’s right. The government to spy on citizens, gave court, established specifically to judge the merits of applications by the a green light to the NSA to keep spying on Americans, ignoring completely the fact that Congress cut off the bulk surveillance the people, and the plain language of the Fourth Amendment to the Constitution. program on June 1, the will of The NSA will lie to Congress --- empirics Fung 14 --- WashPost (Brian, “Darrell Issa: James Clapper lied to Congress about NSA and should be fired”, https://www.washingtonpost.com/blogs/theswitch/wp/2014/01/27/darrell-issa-james-clapper-lied-to-congress-about-nsa-and-should-be-fired/)//trepka A group of congressmen led by Rep. Darrell Issa (R-Calif.) is pushing for President Obama to fire James Clapper, the director of national intelligence , who they say misled Congress about the extent of the NSA's surveillance activity. The lawmakers called Clapper's position "incompatible" with the administration's effort to restore trust in the NSA, according to a letter sent to the White House Monday. The group is mostly Republican, but includes one Democrat, Rep. Alan Grayson (Fla.). "Director Clapper continues to hold his position despite lying to Congress under oath about the existence of bulk data collection programs in March 2013," the letter reads. "Asking Director Clapper, and other federal intelligence officials who misrepresented programs to Congress and the courts, to report to you on needed reforms ... is not a credible solution." Last year at a hearing on surveillance, Sen. Ron Wyden asked Clapper whether the NSA collected "any type of data at all on millions or hundreds of millions of Americans” — to which Clapper said "No, sir ... not wittingly.” Monday's letter to Obama also called out the administration for not addressing what it called the NSA's attempts to circumvent and undermine encryption standards that protect secure online communications, an issue that civil liberties advocates have also addressed in the wake of Obama's NSA reform speech this month. Page 242 AT: Oversight CP --- FISA Oversight fails --- perceived as a rubber stamp Pike 7 --- J.D. from Hofstra (Josh, “THE IMPACT OF A KNEE-JERK REACTION: THE PATRIOT ACT AMENDMENTS TO THE FOREIGN INTELLIGENCE SURVEILLANCE ACT AND THE ABILITY OF ONE WORD TO ERASE ESTABLISHED CONSTITUTIONAL REQUIREMENTS”, 36 Hofstra L. Rev. 185, Lexis)//trepka To remedy these noted abuses, Senator Leahy recommended more effective congressional oversight , in addition to the increased FBI resources and tools to effectively conduct its domestic counterterrorism measures. n221 Though the Senator's suggested remedies would help to resolve the problem, due to the recurrence of the FBI's abuse of power, congressional oversight alone is not a sufficient remedy. To permanently resolve the issues noted, further procedural safeguards , such as those suggested in Part VI.A, are required to ensure that the FISA court operates as an intrusive and thorough check of the FBI's FISA applications rather than a rubber stamp for the abuse of American's civil liberties. n222 Page 243 AT: Oversight CP --- Generic Oversight fails --- gets co-opted Ackerman 13 --- national security editor for Guardian US (Spencer, “Intelligence committee urged to explain if they withheld crucial NSA document”, http://www.theguardian.com/world/2013/aug/14/nsa-intelligence-committee-under-pressuredocument)//trepka "The congressional committees charged with oversight of the intelligence community have long been captive to, and protective of, the intelligence agencies," said Danielle Brian, executive director of the Project on Government Oversight. "Many of the congressional staff, in fact, come from those agencies . This latest revelation demonstrates the harm caused by that conflict of interest. When the congressional oversight committee is more loyal to the agency it oversees than to the legislative chamber its members were elected to serve in, the public's interest is seriously compromised ." Aftergood made a similar institutional is a deeper failure here by the intelligence oversight committees to accurately represent the range of opinions on intelligence policy," he said. "Even post-Snowden, HPSCI held one open hearing on surveillance policy with no witness providing a critical perspective. Over point. "There in the Senate, the [Senate intelligence committee] has held no open hearings on the subject. Oversight fails --- Congress falls in line with the executive Sugiyama and Perry 6 --- J.D.s from UMich Law School (Tara and Marisa, “THE NSA DOMESTIC SURVEILLANCE PROGRAM: AN ANALYSIS OF CONGRESSIONAL OVERSIGHT DURING AN ERA OF ONE-PARTY RULE”, 40 U. Mich. J.L. Reform 149, Lexis)//trepka B. Alternatives and Suggestions for Improvement Congress possesses many alternatives to the fire-alarm model for conducting oversight, n259 but members of Congress are unlikely to use these methods unless they somehow advance the goals of the party in power. As the 2006 midterm elections approach and Democrats seek to shift the balance of power in their favor, they should seek to mobilize interest groups and their political constituencies to press for answers about the NSA surveillance program. Rather than using the most politically contentious methods of oversight, such as censure or calling for an independent counsel, minority members need to find creative approaches to oversight that may allow both parties to benefit. Bipartisanship often works most effectively when the goals of the majority and minority align. For example, Congress held hearings about the intelligence leading to the Iraq war arguably because both parties stood to gain political ground. n260 With the NSA surveillance program, however, the administration has polarized the issue by framing it in terms of security . This approach plays on public fears of terrorism and targets those who seek to challenge the authority of the administration. If Democrats could successfully reframe the issue in a way that serves the national political agenda of the majority, they could potentially achieve greater oversight of the NSA program. Circumvention decks CP solvency Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka Yet one can infer a sub-textual argument that the Constitution demands leeway for the President to circumvent statutory disclosure requirements that he deems antithetical to national Page 244 security. This point follows from the administration's support generally for a strong constitutional executive privilege to keep secrets. n42 The point also seems implicit in the administration's many references to the need for secrecy regarding the warrantless surveillance program's existence. The administration makes such arguments with respect both to Congress as a whole n43 and to the full intelligence committees' memberships. n44 The arguments are relevant to the [*1056] administration's statutory disclosure obligations only if they either justify invoking a statutory exemption from disclosure or if the administration unilaterally may adjust its disclosure obligations as it deems necessary. Considering that the administration references the need for secrecy about the program regularly and generally - apart from its statutory interpretation point, - and considering the administration's support for executive privilege, its references seem at least partly to reflect the view that it constitutionally may circumvent disclosure obligations as it deems necessary. Won’t comply --- empirics Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka The warrantless surveillance controversy thus reflects at least two sets of problems with the existing system of information sharing. First, administrations do not necessarily comply with statutory directives to share information, and individual congresspersons may acquiesce in, even facilitate , such noncompliance. These phenomena appear grounded in the view that the Constitution gives the President discretion not to comply or at least in the view that this constitutional interpretation is politically acceptable, even popular, and that challenging it poses political dangers. Even where Congress attempts to balance secrecy's dangers and benefits through funneling requirements, then, such requirements are unlikely to be consistently effective . A strong defense of Congress' constitutional prerogative to impose information disclosure requirements thus is in order. Second, while there seems to be broad agreement that information funneling of some kind is a desirable tool, there has been relatively little care paid to the details of such funneling and to the principles that should underscore those details. This problem is manifest in disputes between the administration, which argues that its briefings to the Gang of Eight about the warrantless surveillance program were meaningful, and administration opponents who charge that such briefings were mere "check the box" exercises that offered no avenue for responsive congressional action. The problem similarly is manifest in disputes over the sufficiency of disclosures by the administration after the [*1061] program came to the public's attention. Congressional oversight devastates national security Kitrosser 8 --- Associate Professor @ University of Minnesota Law School (Heidi, “THE DOMESTIC COMMANDER IN CHIEF: CONGRESSIONAL OVERSIGHT OF NATIONAL SECURITY ACTIVITIES: IMPROVING INFORMATION FUNNELS”, 29 Cardozo L. Rev. 1049, Lexis)//trepka 1. Secrecy's Costs and Benefits in the Context of Congressional Oversight of National Security Activities It is hardly news that secrecy has costs and benefits. n90 What is striking about these costs and benefits is that they often consist not only of competing values (e.g., democratic openness versus national security) but also of competing means of achieving the same value (e.g., national security through openness versus national security through secrecy). n91 Additionally, inter-value and intravalue competition can exist and impact one another simultaneously. For example, openness paradoxically can be furthered by secrecy to the extent that candor may more likely emerge in a closed, confidential conversation than in a public one. At the same time, the degree to which confidentiality furthers candor may fluctuate with the extent to which those disclosing information believe (or credibly can argue) that wider disclosures would harm national security. This example also raises the question of whether the openness fostered by confidentiality serves related ends such as accountability or security, or whether the secretive nature of the disclosures stymies their ability to further ends beyond themselves. The various values at stake - whether competing against one another or generating competition over the best means to achieve the same value - can be grouped into two rough categories. As indicated [*1065] by the immediately preceding examples, those categories are national security and democratic deliberation. Subsections (a) and (b) elaborate on the contents of each category and major arguments regarding how secrecy advances and inhibits each one. a. National Security and Related Values The protection of national security is a key value invoked in debates over the advisability of sharing information with Congress. n92 The value encompasses the protection of national security and means toward that end. Such means might include, for Page 245 example, ensuring efficiency and sound judgment in national security operations, facilitating the cooperation of allied nations and the support of the American people, and preventing enemies of the nation from learning information that could help them in their anti-U.S. operations. i. Arguments against Disclosure Throughout history, members of the executive branch have argued that national security would be harmed by their acquiescing to congressional requests for information . n93 The potential reach of such arguments is exemplified by claims that publicly debating wartime strategy with Congress threatens national security by undermining troop morale and popular support. n94 Another argument made against information disclosures is that disclosures hinder the efficacy of internal executive branch operations and deliberations and thus ultimately hurt national security. n95 This is a subset of more general executive branch concerns to the effect that candor and efficacy in intraexecutive branch deliberations are impacted negatively by participants' awareness that they might be disclosed. n96 Of course, the most intuitive and ubiquitous argument for withholding information is that the information could help enemy nations, persons or organizations. It follows that the information must remain a closely guarded secret to prevent it from falling into enemies' hands . This argument pervades political discourse over the recent NSA surveillance controversies. As noted earlier, for example, the Bush [*1066] Administration argues that it could not have sought specific legislation to authorize the warrantless surveillance program without "informing our enemies about what we are doing and how we are doing it." n97 And they claim that national security has been damaged by press reports on the program, as such reports "remind" the enemy that "we are involved in some kind of surveillance." n98 Reports don’t happen often enough Mehta 7 --- J.D., Harvard Law (Jason, “ASSESSING THE ELECTRONIC SURVEILLANCE MODERNIZATION ACT (ESMA): DISTORTING, RATHER THAN BALANCING, THE NEED FOR FLEXIBLE ELECTRONIC SURVEILLANCE AND ROBUST CONGRESSIONAL OVERSIGHT”, 12 J. Tech. L. & Pol'y 225, Lexis)//trepka E. Revision of Congressional Oversight Provisions One of the express goals of ESMA is to provide greater congressional oversight to the President's use of domestic surveillance. ESMA envisions a greater role for Congress in several ways. First, ESMA would require that, semiannually, the Attorney General " fully inform the Permanent Select Committee on Intelligence of the House of Representatives and the Select Committee on Intelligence of the Senate on electronic surveillance conducted without a court order." n71 Currently, there is no statutory requirement mandating this report to Congress. Second, ESMA would enhance congressional oversight by amending the National Security Act of 1947. n72 In particular, ESMA would amend section 413 of the Act to affirmatively allow the Chair of each of the congressional intelligence committee to inform, on a bipartisan basis, "all members or any individual members of such committee, and any essential staff of such committee" of a report submitted under 50 U.S.C. §§ 413(a) or (b) ("Reporting of intelligence activities other than covert actions," "Presidential approval and reporting of covert actions"). n73 Similarly, ESMA would amend sections 413(a) and 413(b) to allow for similar sharing and consultation among congressional intelligence committees. This replaces the current system where only the Chair and Vice-Chair receive this information. Ostensibly, ESMA's drafters included these provisions to ensure bipartisan information exchange. Page 246 AT: Oversight CP --- Health Monitoring Regulation alone can’t solve oppression Hoppin 12 --- J.D., New York University School of Law (Margaret, “NOTE: OVERLY INTIMATE SURVEILLANCE: WHY EMERGENT PUBLIC HEALTH SURVEILLANCE PROGRAMS DESERVE STRICT SCRUTINY UNDER THE FOURTEENTH AMENDMENT”, 87 N.Y.U.L. Rev. 1950, Lexis)//trepka 3. Targeting Politically Vulnerable Domestic Communities Security surveillance programs that target politically vulnerable domestic communities for dragnet surveillance have prompted widespread concern in the last decade, although legal challenges to national security programs generally have not reached a decision on the merits. n141 For example, politicians and advocacy groups responded promptly to the revelation that New York City Police Department surveillance programs targeted Arab and Muslim communities in the Northeast. n142 Some politicians publicly declared that the programs were "disturbing" and said they would not have allowed such a [*1979] program if they had known about it. n143 Academics and academic institutions expressed similar concern and criticism. n144 Community leaders petitioned the New Jersey Attorney General to investigate a New Jersey-based surveillance program and give "a full accounting" of ongoing surveillance. n145 In the context of security surveillance, one commentator advocates robust constitutional privacy protections because "legislative efforts to regulate surveillance may ... insufficiently protect the privacy of certain politically unpopular minorities, like Muslim-Americans." n146 Like Arab and Muslim Americans in the security surveillance context, n147 people with diabetes, obesity, and certain other chronic conditions are politically vulnerable in the health surveillance context. Diabetes " disproportionately affects black and Latino New Yorkers, [and] ... those living in low-income households and neighborhoods," both with respect to its prevalence and the rates and severity of related complications. n148 The same is true of obesity and obesity-related health problems. n149 In addition, many chronic conditions, including diabetes, are "often perceived as a self-inflicted problem among the elderly who are sedentary and obese." n150 The argument that governments have "a legitimate interest in controlling [*1980] medical and social costs of individuals' unhealthy behaviors that are borne by society at large" n151 may be used to justify inappropriate privacy invasions, especially given that public discourse about obesity is infused with moral condemnation. n152 Judicial recognition that emergent programs infringe upon constitutionally protected privacy rights would require governments to develop substantive (instead of rhetorical) justifications for deploying the most invasive types of public health surveillance against vulnerable populations or, alternatively, to modify those surveillance programs. Page 247 AT: Oversight CP --- Perm The perm is the only way to solve SOP and the aff Rahdert 7 --- Professor of Law (Mark, “DOUBLE-CHECKING EXECUTIVE EMERGENCY POWER: LESSONS FROM HAMDI AND HAMDAN”, 80 Temp. L. Rev. 451, Lexis)//trepka Both the legislative and judicial checks have roots in precedent and practice. Foremost, they follow Justice Jackson's famous categorical analysis of executive power in Steel Seizure, in that they are the legislative and judicial corollaries to his appraisal of executive authority. n22 Indeed, the recent enemy combatant cases read like an extensive commentary on Jackson's Steel Seizure [*456] concurrence. n23 Effectively, they require two-branch cooperation either to sustain executive authority or to constrain it. Alone, either branch's check has limited capacity to restrain executive authority. When exercised together, however, their double check stands as a potent guarantee against extravagant assertions of executive emergency power. When this double check has been deployed, as it was particularly in Hamdan, it results in relatively searching review of executive emergency national security claims, rather than the extreme deference to executive judgment that those claims have sometimes received, and it subjects executive discretion to constraint through meaningful legislative oversight. Maintaining SOP is a d-rule Branum 02 [Tara, Former Editor of the Texas Review of Law & Politics, “President or King? The Use and Abuse of Executive Orders in Modern-Day America,” Lexis] The second consideration addressed by the Court is similar to the first, and it emphasizes the stated belief of the Founders that preservation of a separation of powers is essential “to preclude the exercise of arbitrary power.” 386 Justice Kennedy recently expressed this sentiment: [*77] Separation of powers was designed to implement a fundamental insight: Concentration of power in the hands of a single branch is a threat to liberty. The Federalist states the axiom in these explicit terms: “The accumulation of all powers, legislative, executive, and judiciary, in the same hands . . . may justly be pronounced the very definition of tyranny. ” 387 Separation of powers is “the absolutely central guarantee of a just Government ” 388 and is therefore endorsed and protected “as a vital check against tyranny.” 389 Page 248 AT: Terry Stops CP Links to all our legitimacy offense and can’t solve --- prefer best data Fagan† and Geller†† 15 --- † Isidor and Seville Sulzbacher Professor of Law, Columbia Law School AND †† Clinical Associate Professor and Director, Applied Quantitative Research Program, Department of Sociology, New York University (Isidor and Seville, “Following the Script: Narratives of Suspicion in Terry Stops in Street Policing”, https://lawreview.uchicago.edu/sites/lawreview.uchicago.edu/files/uploads/82_1/03%20Fagan%20and%20Geller_SYMP_Internet.pd f)//trepka Regulation of Terry stops of pedestrians by police requires articulation of the reasonable and individualized bases of suspicion that motivate their actions. Nearly five decades after Terry, courts have found it difficult to articulate the boundaries or parameters of reasonable suspicion. The behavior and appearances of individuals combine with the social and spatial contexts in which police observe them to create an algebra of suspicion . Police can proceed to approach and temporarily detain a person at a threshold of suspicion that courts have been unable and perhaps unwilling to articulate. The result has been sharp tensions within Fourth Amendment doctrine as to what is reasonable, why, and in what circumstances. The jurisprudence of suspicion is no clearer today than it was in the aftermath of Terry. This issue has taken center stage in both litigation and policy debates on the constitutionality of the stop-and-frisk policing regime in New York City. Under this regime, police state the bases of suspicion using a menu of codified stop rationales with supplemental text narratives to record their descriptions of suspicious behaviors or circumstances that produced actionable suspicion. Evidence from 4.4 million stops provides an empirical basis to assess the revealed preferences of police officers as to the bases for these Terry stops. Analyses of this evidence reveal narratives of suspicion beyond the idiosyncrasies of the individual case that police use to justify their actions. First, we identify patterns of articulated suspicion. Next, we show the individual factors and social conditions that shape how those patterns are applied. We also show how patterns evolve over time and become clearer and more refined across a wide range of police stops. That refinement seems to follow the capacious interpretative room created by four decades of post-Terry Fourth Amendment jurisprudence. Next, we assess the extent of constitutional compliance and examine the neighborhood and individual factors that predict noncompliance. The results suggest that the observed patterns of narratives have evolved into shared narratives or scripts of suspicion, and that these patterns are specific to suspect race and neighborhood factors. We conclude that scripts are expressions of the norms within the everyday organizational exercise of police discretion and that these scripts defeat the requirement of individualization inherent in case law governing Fourth Amendment stops.