PROJECT OVERVIEW - Fort Hays State University
advertisement

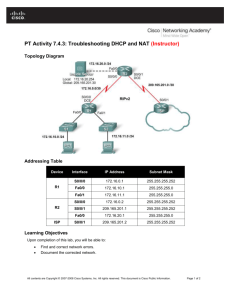
Tiger Net Challenge Computer Networking Competition Project CAPSTONE 2013 FINAL PROJECT SUBMITTED BY: Yusuf Hashem Brittany Kaup Abdulrhman Almutiry Ali Asire TABLE OF CONTENTS PROJECT OVERVIEW................................................................ 3 TROUBLESHOOTING SEGMENT.................................................3-14 Part one (novice): Troubleshooting part one (novice) Damaging the network Part two (intermediate) Troubleshooting part two (intermediate) Damaging the network Part three (advanced) Troubleshooting part three (advanced) Damaging the network DESIGN A NETWORK SEGMENT……………………………………………15 WEBSITE................................................................................... 17 PRIZES.............................................................................. 17 LEARNING EXPERIENCES......................................................... 18 PROJECT OVERVIEW TigerNet Challenge is a team of Information Networking and Telecommunications (INT) seniors that are currently enrolled at Fort Hays State University. The team consisted of Yusuf Hashem, Brittany Kaup, Abdulrhman Almutiry, Ali Asire, and Abulelah Alawdan. In January 2013, the team was assigned to put together a networking challenge that would have participants test their skill sets when it came to computer networking, as part of the team’s capstone project. In fact, the challenge tests participants not only in their computer networking skills, but also their project management, decision making, and budgeting skills. The team’s goal was to come up with a two computer networks that was designed in Packet Tracer. Packet Tracer is a Cisco program that simulates computer networks in order to train and educate potential IT majors and employees. The TigerNet Challenege was announced to 14 different states by our sponsor, Kevin Shaffer. The team put together two different computer networking segments. The first segment consisted of a troubleshooting module, and the second segment consisted of design a network module. The troubleshooting segment of the TigerNet Challenge consisted of a small network built in Packet Tracer. It was designed with three different difficulty levels. The levels are Novice, Intermediate, and Advanced. A written scenario was put together in a Microsoft Word document in order to explain the segment. The troubleshooting part had participants go through a number of issues that was created by the team in the Packet Tracer. The participants should have a minimum to intermediate knowledge of computer networking skills in order to have completed this segment. In addition to the troubleshooting segment, the create a network segment was included into the challenge. This segment was designed in a way to give competitors an idea of how a real life company would expand their network. The network design segment had the team come up with a scenario that included a fake company that wanted to expand their computer network in according to their requirements. This means that competitors had the freedom to expand the network in any way they saw fit as long as they followed the rules put by the team. The rules were presented to the competitors in a Microsoft Word document. The document explained the requirements that the company sought after in an expansion for their network. TROUBLESHOOTING SEGMENT The troubleshooting network was put together mainly by Abdulrhman Almutiry. The team met with Professor Kevin Shaffer to go over the architecture of the network that would later on be used for the challenge. We have come to an agreement to design it in a way that it would incorporate three different levels of difficulties. Each difficulty would incorporate different computer networking concepts that contenders must solve. The three levels are novice, intermediate, and advanced. The instructions were written in a Microsoft Word document and distributed through our website (http://www.dzblaster.com/). The contenders would download the instructions along with the trouble shooting segment built in Packet Tracer versions 5.3.3. The instructions were written as a scenario in a help desk for PC troubleshooting. The idea was that a group of amateur networkers were hired in order to put together a computer network for a company. They did a very poor job and it is the job of the participant to correct the mistakes that was done by these amateurs. Part one (novice): In this part of the troubleshooting segment, the network was composed of a 2620XM router (router 1) that was cabled to a 2950-24 switch with a straight through cable on interface Fa0/0 with an IP address of 192.168.0.1/24. The switch was then cabled with a straight through cable to the three PCs. Each PC had the following information: Hosts IP address Subnet Mask Default Gateway PC 10 192.168.1.3 255.255.255.0 192.168.1.2 PC 11 192.168.1.4 255.255.255.0 192.168.1.2 PC 12 192.168.1.5 255.255.255.0 192.168.1.2 Troubleshooting part one (novice): After putting the novice network together, we decided to damage the network and make it unable to communicate with each other or any other device on the network. This part of the challenge had the participants fix the following issues on the network with accordance to the TigerNet Challenge’s scenario. This is an example taken from the troubleshooting segment explanation file. The Company has reported the following: The hosts on the network are unable to ping each other. The hosts are unable to ping the default gateway. Fix the issue so that these hosts are able to ping each other and the router. There seems to be a password on router 1, console and enable, figure it out and mention it in your written report. Damaging the network: The TigerNet Challenge team has performed the following in order to damage the network so that the participants may troubleshoot the network. The router was secure with a password that can be answered through reading the banner of the day message. o Q. So you want to access the router do you know the port number for HTTP. If you know that, for privileged EXEC Mode, you should know the HTTPS port number? Answer 80 for EXEC mode access. Answer 443 for Privileged EXEC Mode access. The interface Fa0/0 from router to switch was shut down and the cable was exchanged with a crossover cable. The cables from the switch to the three PCs were all exchanged with cross over cables. On PC 10, the subnet mask was exchanged with a 255.255.255.252, and the default gate way was exchanged with 192.168.1.1. On PC 11, the subnet mask was exchanged with a 255.255.255.252, and the default gate way was exchanged with 192.168.1.9. On PC 12, the subnet mask was exchanged with a 255.255.255.252, and the default gate way was exchanged with 192.168.1.4. The team used a 255.255.255.252 subnet mask that only accommodates two useable IP address on a network. The competitors needed to subnet the addresses successfully in order to find out the right subnet address for the hosts. The default gateway address can be found on the router that is connected to the switch. The participants must put the network back together in order for the hosts to ping the router. Also, they must write a detailed report of any change they have conducted on this part of the troubleshooting network. Part two (intermediate): In this part of the troubleshooting segment, the network was composed of a 2811 router (router6) that was cabled to a 2950T-24 (switch4) switch with a straight through cable on interface Fa0/0 with an IP address of 192.168.10.1/28. The switch was then cabled with a cross-over cable to another 2950T-24 switch (Switch3). Switch4 is connected to 4 PCs using a straight through cable. Switch3 is connected to 3 PCs using a straight through cable as well. VLAN 10 and 15 were created in both switches. VLAN Trunking Protocol (VTP) was implemented in both switches to share the VLAN database between switches. Lastly, we placed a 2620XM router (router2) to connect the Intermediate network to the global network on Serial 1\2. For this to happen, RIPv2 was used in both router6 and router2 to fully connect the Intermediate LAN to the global network. To make the two VLANs work, we had to configure router6 and the switches with proper configuration. First, in order to make the two VLANs able to ping each other, we had to use InterVLAN (Router-on-A-Stick) concept. Therefore, we created sub-interfaces on router6 Fa0/0 interface to serve as the VLANs gateway. Second, we configured router6 to be the DHCP server for both VLANs. Third, we changed the encapsulation protocol for the trunk link between router6 and Switch4 to be dot1q. For InterVLAN to work properly, links between switch and router or switch must be trunk link. Therefore on Switch4 and Switch3, we set the links in between to be Trunk and member of the Native VLAN (VLAN 1). Also, we created VLAN 10 and assigned Fa0/3 - Fa0/5 interfaces to it, while Fa0/2 was assigned to be member of VLAN 15. Further, we established VTP protocol on Switch4 and made it the server for the VTP domain to share the VLAN information with Switch3. On Switch3, we assigned Fa0/2 - Fa0/3 interfaces to be member of VLAN 15, while Fa0/1 was assigned to be member of VLAN 10. Also, VTP was established for Switch3 in a client mode to receive VLAN information from the VTP server (Switch4). For addressing purpose, we set Router6 to be the DHCP server to allocate IP addresses for every PC in the network. Each PC had the following information: Hosts VLAN IP address Subnet Mask Default Gateway PC 1 10 192.168.10.x* 255.255.255.240 192.168.10.1 PC 2 15 192.168.15.x 255.255.255.240 192.168.15.1 PC 3 15 192.168.15.x 255.255.255.240 192.168.15.1 PC 0 15 192.168.15.x 255.255.255.240 192.168.15.1 PC 7 10 192.168.10.x 255.255.255.240 192.168.10.1 PC 8 10 192.168.10.x 255.255.255.240 192.168.10.1 PC 9 10 192.168.10.x 255.255.255.240 192.168.10.1 * IP addresses were dynamically assigned by the DHCP server. Troubleshooting part two (intermediate): After putting the intermediate network together, we decided to damage the network and make VLANs unable to communicate with each other. This part of the challenge had the participants fix the following issues on the network with accordance to the TigerNet Challenge’s scenario. This is an example taken from the troubleshooting segment’s explanation file. The Company has reported the following: HELP DESK needs the two VLANs, 10 and 15, to be able to ping each other. The amateur group has setup the VLANs on the switches, however, VLANs weren’t able to ping each other. Actually, PCs on the same VLAN but different switches are not able to ping each other too! PCs in both VLANs were setup using static IPs. Please setup router6 to be the DHCP server to provide the network addressing dynamically. While using DHCP, Please reserve the first usable IP in the subnet for the gateway interface. Use the most practical routing protocol on router 2 and router6 so the intermediate network is fully connected to router 2. Fix the issue so that these hosts are able to ping each other and both router 2 and 6. Damaging the network: The TigerNet Challenge team has performed the following in order to damage the network so that the participants may troubleshoot the network. The router2 was secure with a password that can be answered through reading the banner of the day message. o Q. So you wanna access the router ;) do you know the port number for FTP. if you know that, for privileged EXEC Mode, u should know TELNET port number Answer 21 for EXEC mode access. Answer 23 for Privileged EXEC Mode access. The interface Fa0/0 from router6 to switch was changed to be encapsulated with ARPA protocol instead of dot1q encapsulation. The sub-interfaces were replaced with one main interface. Fa0/0 on router6 was assigned with 192.168.10.1 IP address. Fa0/1 on Switch4 that is going to router6 was assigned to VLAN 10 and set to be access port. Fa0/6 on Switch4 that is going to Switch3 was set to be access port. Fa0/4 on Switch3 that is going to Switch4 was set to be access port. PCs were assigned addresses statically instead of using router6 as the DHCP server. All PCs were assigned 192.168.10.1 as their defult gateway address. RIPv2 was removed from router2 and replaced with RIPv1 with no other routing information. RIPv2 was removed from router6 completely. The participants must put the network back together in order for the hosts in different VLANs to ping each other and both router2 and router6. Also, they must write a detailed report of any change they have conducted on this part of the troubleshooting network. Part three (advanced): In this part of the troubleshooting segment, the team decided to implement a DSL connection in Packet Tracer. We decided that this would be a great idea, because we wanted to give participants a more visual feeling of accomplishment. When working with routers and switches, the idea is to get all hosts connected and communicating with each other. What we did with the DSL connection, was to add a host (PC) that wanted to open a website on its web browser. The site that we decided to go with was a fake https://www.google.com/ put together on a DNS server in Packet Tracer. If the participants were able to fully troubleshoot the advanced network, they had to go into the host PC, open the web browser, and type in https://www.google.com/. If they succeed, they will see a small HTTP page pop up. The network was composed of a 1841 (router 3) router that was cabled to a 2950-24 switch with a straight through cable on interface Fa0/1 with an IP address of 192.168.1.254/24. The switch was then cabled with a straight through cable to another router that acted as an ISP (internet service provider) from the switch’s Fa0/2 interface to the ISP’s Fa0/1 with an IP address of 192.168.1.1/30. The ISP router was then cabled to a server (Server 0) with a straight through cable on interface Fa1/0. We decided to use a Vlan 10 on interface Fa1/0 with an IP address of 10.10.10.1/24 to confuse the participants. The team decided to add a password on the ISP router to give participants a sense of security when it comes to accessing routers of this importance to a network. on the ISP router, the team added the following commands to insure a connection to the server and the Cloud: on the ISP router: o ip dhcp excluded-address 1.1.1.1 o ip dhcp pool Internet_Users. o network 1.1.1.0 255.255.255.0 o default-router 1.1.1.1 o dns-server 10.10.10.2 Interface FastEthernet0/0: o ip address 1.1.1.1 255.255.255.0 o duplex auto. o speed auto. o ipv6 ospf cost 1. o no cdp enable. Interface FastEthernet0/1: o ip address 192.168.1.1 255.255.255.252 o duplex auto. o speed auto. Interface FastEthernet1/0: o switchport access vlan 10 o switchport mode access o spanning-tree portfast Interface Vlan10: o IP address 10.10.10.1 255.255.255.0 Passwords: o line con 0 password 01100001 We then decided to add a Cloud (Cloud 0) to the ISP’s router through Fa0/0 with an IP address of 1.1.1.1/24 while using a straight through cable between the ISP and the Cloud. the cloud used will emulate the internet in packet tracer in order to have the participants reach the fake Google website. from the Cloud, the team has connected two DSL Modems. The Cloud has the modems cabled with a standard copper phone cable connected to the Cloud’s modem interfaces. Modem 4, is then connected to a 1841 router (Home router) with a straight through cable on interface Fa0/0 with an IP address of 1.1.1.2/24. The Home router is then connected to a host (PC 13) through the Home router’s Fa0/0/0 interface with a Vlan 20 and IP address of 192.168.0.1/24. The team added the following commands on the Home router to insure an internet connection to the Cloud: On the Home Router: o IP dhcp excluded-address 192.168.0.1 o IP dhcp pool users o network 192.168.0.0 255.255.255.0 o default-router 192.168.0.1 o dns-server 10.10.10.2 Interface FastEthernet0/0: o ip address dhcp o ip nat outside o duplex auto o speed auto o ip nat inside source list 1 interface FastEthernet0/0 overload o access-list 1 permit 192.168.0.0 0.0.0.255 interface Vlan20 o ip address 192.168.0.1 255.255.255.0 o ip nat inside The host (PC 13) will pull a DHCP address from the the Home router in order to add more hosts to the network. This emulates a real life connection to the internet when people constantly add new devices and their devices are given IP addresses through DHCP from their ISP provider. Troubleshooting part three (advanced): After putting the advanced network together, we decided to damage the network and make it unable to communicate with each other or any other device on the network. We also made sure that the participants were not able to browse the fake Google website that was served on the DNS server (10.10.10.2). This part of the challenge had the participants fix the following issues on the network with accordance to the TigerNet Challenge’s scenario. This is an example taken from the troubleshooting segment’s explanation file: The Company has reported the following: The amateurs have constructed a failed DSL connection. Your job is to re connect these devices and make them working again. The amateurs have put passwords on the routers, they were nice enough to leave hints in the message of the day of the router. The routers should be the DHCP server. There seems to be issues with the vlan 10 between the router and the server. The ISP router is not able to connect the internet between Server0 and the Cloud0. ISP router should be a DHCP server with a DHCP pool called Internet_Users. There also seems to be trouble with the server, the web page is not being served to the clients. The home_rtr needs a DHCP pool known as Users You will also need to expand the network through modem 5 with one router and a host. The router should be similar to the home_rtr. Your goal is to make the PCs extract DHCP from the routers and open the website www.google.com from the host PCs. Damaging the network: The TigerNet Challenge team has performed the following in order to damage the network so that the participants may troubleshoot the network: First Step: The ISP router was secure with a password that can be answered through reading the banner of the day message. o Q. So, you want to access the route? You will need to know the binary number that represents a lower case letter a: Answer 01100001 for EXEC mode access. ISP Router to Server0 through interface Fa1/0: o ISP(config)#int fa1/0 o ISP(config-if)#shutdown o ISP VLan 10 shutdown between Server0 and ISP Router o ISP(config)#int vlan 10 o ISP(config-if)#shutdown o Removed DHCP fromt the ISP Router o ISP(config)#no ip dhcp pool Internet_Users Second Step: Server0 o Power off o Removed : IP address: 10.10.10.2 Subnet mask: 255.255.255.0 Default gateway: DNS server: Third step: ISP Router to Cloud0 Fa0/0: 10.10.10.1 10.10.10.2 o Shutdown the ISP int fa0/0 port down ISP(config)#int fa0/0 ISP(config-if)#shutdown Turned off cloud Cloud modem 4 removed under DSL Cloud modem 5 removed under DSL Interface Ethernet 6 switched from DSL to Cable Fourth step: DSL Modem: o Shutdown modem Fifth step: Home router o Password console on Home router, the ASCII code that represents the capital letter W Shut down vlan20 from 0/0/1 to 0/0/3 o Home_rtr(config)#int fa0/0 Home_rtr(config-if-range)#shutdown Shut down vlan 20 o Home_rtr(config)#int vlan 20 Home_rtr(config-if)#shutdown Home_rtr(config)#int range fa 0/0/1 - 3 o Answer: 01010111 Home_rtr(config-if)#shutdown Shutdown int fa0/0/0 o Home_rtr(config)#int fa0/0/0 Home_rtr(config-if)#shutdown Removed DHCP o Home_rtr(config)#no ip dhcp pool users o Removed cable o Removed Ethernet port. Sixth step: PC The advanced part of the troubleshooting segment was built so that the competitors had to solve each problem correctly in order to have the host PC open the fake Google website on the web browser. If one of the command lines were not entered correctly, the network would still flash green in Packet Tracer. This indicates that there is a connection between two or more physical devices, but if the host is not able to ping the other devices on the network then the participant has not put the network back together correctly. Trouble shooting segment example DESIGN A NETWORK SEGMENT The design a network segment was put together by the TigerNet Challenge team in order to encourage participants to put their current knowledge of computer networking to the test. It is designed mainly by the team’s leader, Yusuf Hashem. The segment is composed of a network put together in Packet Tracer. The team decided to come up with another scenario that would explain to the participants what was required from them in order to complete the segment. The scenario was based on a fake company that was located in Kansas city, KS. The company sought to expand its computer network in order to accommodate for an expansion in the company’s buildings. The company wanted to expand its research and development department, as well as its financial department. Each expansion of these departments, challenged the participants in these areas: Topology Devices Connections Expansion The company required that each expansion needed to meet a certain number of rules. These rules challenged the participant’s knowledge of expansion and hardware capabilities when it came to expanding the company’s network. The objectives of expanding the network: Objectives for the new R&D department: A class B IP address (172.18.X.X) that will accommodate 300 hosts Expand the network 400 meters (1312 feet) east of the company 5 PCs, two of these PCs must have audio capabilities (hearing and speaking) An access point with 4 devices on it (an IP phone, a wireless printer with 2.4GHZ wireless connection, a Tablet, and a laptop connected wirelessly ) Enable practical routing protocols. Explain your work in a Word File or PDF. Objectives for the new financial department: A class B IP address (172.19.X.X) that will accommodate 1023 hosts Expand the network 400 meters (1312 feet) east of the company Simulate a DSL connection in the department. 5 PCs, two of these PCs must have audio capabilities (hearing and speaking) An access point with 4 devices on it (an IP phone, a wireless printer with 2.4GHZ wireless connection, a Tablet, and a laptop) Enable practical routing protocols. Explain your work in a Word File or PDF. Each participant will also have to research each device, cable, protocol used, and price of whatever they did to expand the network. This part challenges them to put their research skills to the test in order to grasp an understanding of financial planning in a company. It will teach them to be cost efficient and become more economical when it comes to growing and expanding a company’s communication department. A participant must think before using any device to expand the network. They must make sure to follow these steps and explain them in great detail to the company: Type of Ethernet cabling used between cabled devices. The advantages of the cable you chose over the others available. The devices you used to expand the network. The advantages of the devices you chose over other possible devices. A personal statement to the company how to better expand their company. A budget explaining how much it cost you to expand this network. Show your work for the subnetting that you performed Design a network segment example WEBSITE The website to the project Tiger net Challenge was designed by Brittany Kaup made up of different varieties such as PHP, CSS, and HTML. It should be noted that the majority of the site was made by scratch and with a clean slate by Brittany. The template was the first thing that needed to be made. She started off by using Notepad ++ to write out the building blocks for the code. The CSS page was made to handle such items in the page like tables, charts, pictures, and the wrapper. Those items were essential to the essence of the page. The next part of the site that was important to make was the Logos, as logos are important to any part and page of the website. The logos were hand made on Paint and Dreamweaver. They were made to incorporate the FHSU logo along with the name of the challenge that was being presented. The photos were found by running various searches on the internet and were used with permission by the owners. One photo was placed on every page to make the page stand out and not look boring and drab. The next thing she had to consider was whether or not to change the font color. When it comes to website, she decided to go for the black and yellow and keep the colors set mainly to the FHSU colors. There are places where the color is set to red or green. The red font is for announcements that were vital for the contestants to know and the green color was for the winners. The sign up page was made for the contestants to sign up for the challenge so that the group can know who is participating and where they are from. Even though Brittany has knowledge in PHP she doesn’t have a very strong skill to it. Since the site needed to be done quickly, we had to hire our friend Tony Anthony so that the PHP could be done in a quick and efficient way. He made that part of the site for us. The final site looked great and was quickly launched into the World Wide Web. The feedback to the site has been positive. PRIZES In order to have people take our challenge, we had to offer something in return. We decided to have four different prizes for people whom took our challenge. The prizes were as follow: 1st place would receive a $50 gift card to Wal-Mart and a plaque 2nd place would receive a $25gift card to Wal-Mart and a plaque 3rd place would receive a plaque. All other participants would receive a certificate of participation. LEARNING EXPERINCES Tiger Net challenge was a success in the eyes of the team. We couldn’t have worked without each other’s different skill set. Each person on the team brought their own knowledge and experiences to help put together a great competition that others would enjoy taking to show off their networking skills. We approached this competition in a professional way by meeting two to three times a week at minimum. Each group meeting would last at least 4 to 5 hours. The group would also work individually at an estimated 3 to 5 hours extra weekly. In each group meeting, all of us would learn something new when it came to web design and computer networking LEARNING EXPERIENCES THROUGHT THE PROJECT In the first two weeks of the Cap Stone class, our team was clueless what project to tackle. We then decided to go with Tiger Net Challenge that was held before us by another group of computer networkers at Fort Hays State University. We were very confident in taking on this role of being the latest team to design the competition. Our team learned that we should assign each person a designated role towards the challenge in order to keep things tidy and neat. The members with the most knowledge in computer networking would take on the designing of the troubleshooting and design a network segment, while members who had better web skills would design the website. Other members acted as liaisons between our sponsors in order to gain guidance from them to make our competition more professional. We decided to have one or two of the members meet with our sponsors so that they could have an easier time relating with a familiar face rather than having to restate the same information to another person at each meeting. Doing this helped the group reach a better understanding with our sponsor, Kevin Schaffer. The team found it better to communicate with one another through cell phones and Facebook.com. it was the best way to start communicating because within Facebook, we were able to initiate a group and post our findings, important dates, files, questions, and other useful information that the group could utilize at the same time. Later on, we had to use another method of communication in order to incorporate files on to our website to allow participants to download the files needed to take the challenge. We used http://www.mediafire.com to upload the instruction and Packet Tracer files to our website. We found it easier and more practical to use this method since it did not require more coding on our website. Not everyone was familiar with this file sharing site at the beginning of the project, but we quickly adapted to it and learned to use it more productively. TROUBLESHOOTING This segment of the project gave us a lot of experience working with packet tracer. In the beginning, only a couple of us were proficient enough to use this program. But after using it over and over again, we have some of our team members have become very proficient in using this program and have gone beyond the teachings within the curriculum taught at the university. Packet Tracer gave us an emulated experience in building networks from scratch. It is not as good as real head on equipment experience, but it gives us the joy to deal with equipment that otherwise we might have never had the pleasure of working with in real life. The troubleshooting segment allowed the team to gain more experience in the following concepts: Network architecture Topology Designing Cabling hardware Using new equipment with familiar ones Using different protocols in accordance with one another. It was a joy for us to see our network built up in Packet racer, the difficult part was trying to make the damage repairable. It was easy to go in Packet Trace and rip out the cables and exchange them with incompatible ones, or use DHCP on a router and then have it removed. The real challenge was in wording these concepts in a scenario that would allow competitors to fully understand what was needed from them to complete the segment. It took a lot of research in order for us to use the certain aspects of each of the three levels that was put into this segment. Each part was thought ought carefully and tested numerous times before implementing it into the challenge. We ran the test by ATSO in Fort Hays State University before sending it out. We received pretty much negative feedback and had to scrap what we had and start over. After that, we had a stronger and more professional looking network that competitors mostly ranked as a challenging competition. DESIGN A NETWORK This part of the challenge taught the team more than just computer networking. It taught us the value of business and how companies think, we learn more about requirements that are set forth by a company when they are looking to expand their network. The team also learned that when expanding, it will cost money to do so. We had to look up prices of devices that we dealt with in an emulated environment that we didn’t know how much it would actually cost. It was shocking to learn how expensive some of the equipment actually was. It made us think more economical and green when it came to expanding a network of this size. We learned that each expand demand a number of equipment and protocols that needed to go together in order to have the company satisfied with the final result. It was also a way to educate the competitors about how a real company would ask for a blueprint of their thoughts before actually starting the expansion. It was a useful method to teach us new skills when it came to budgeting, and financial skills while still keeping a consistent network through expansion.